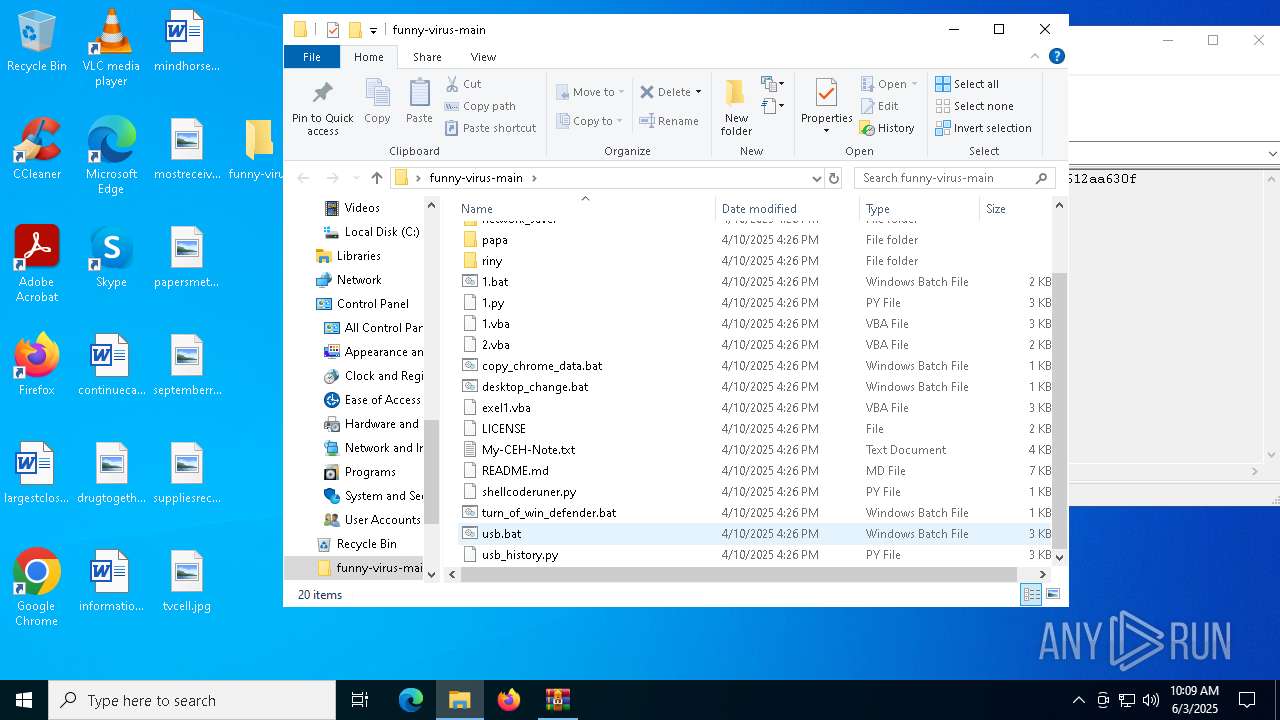
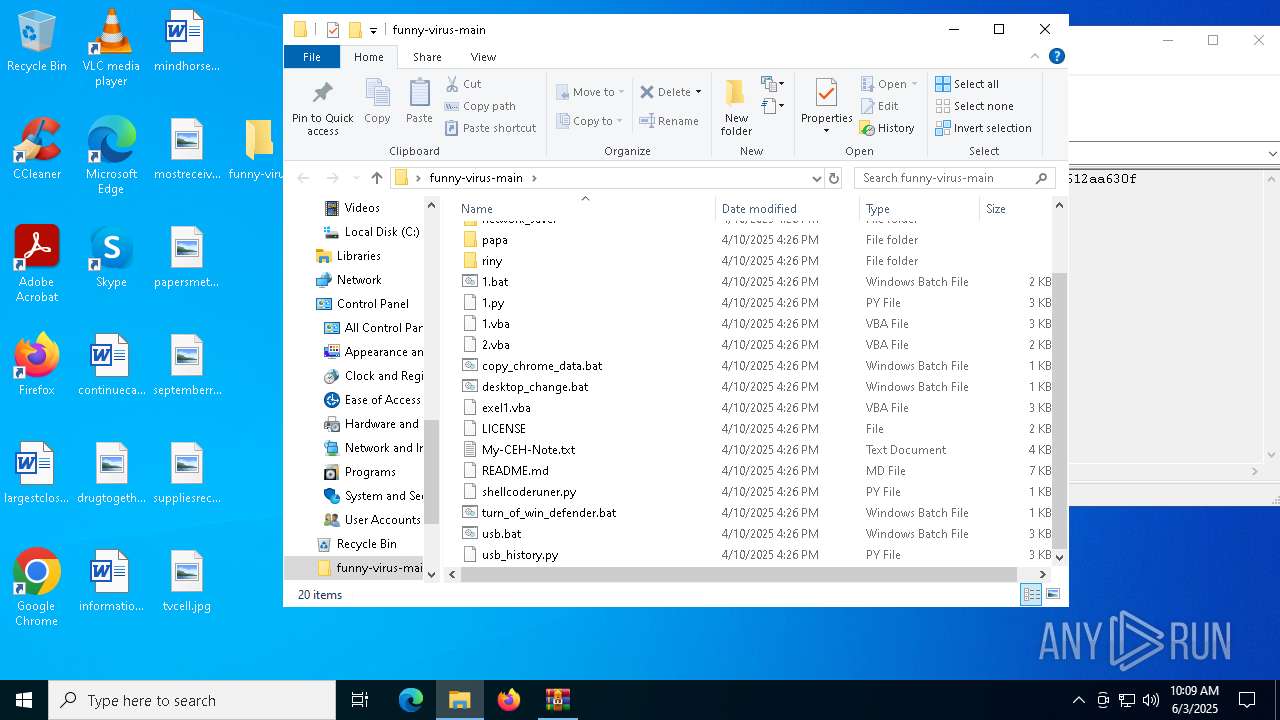
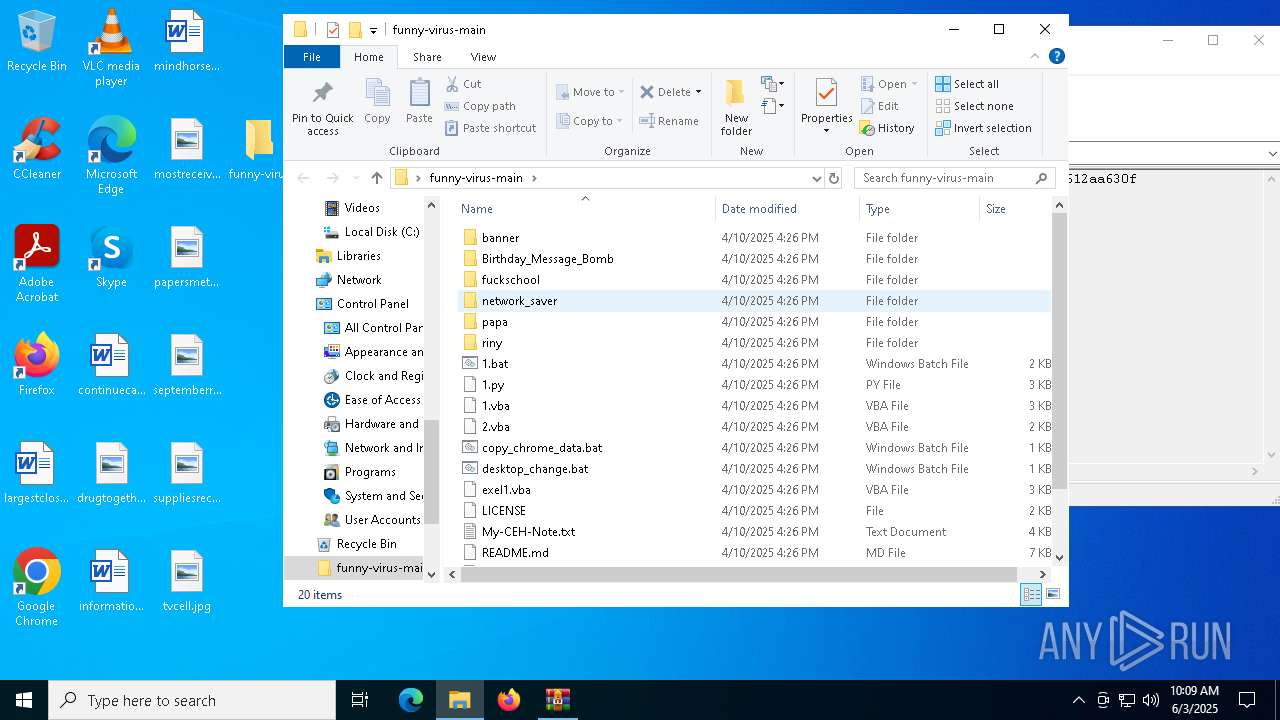
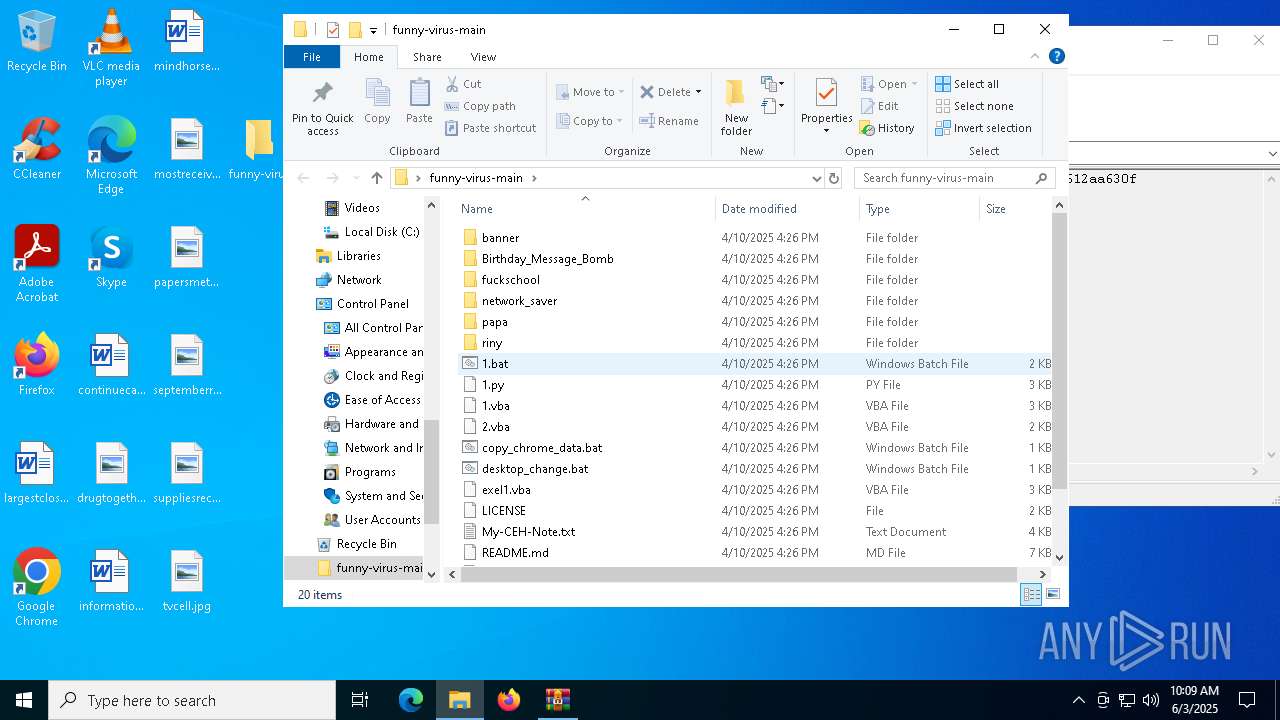
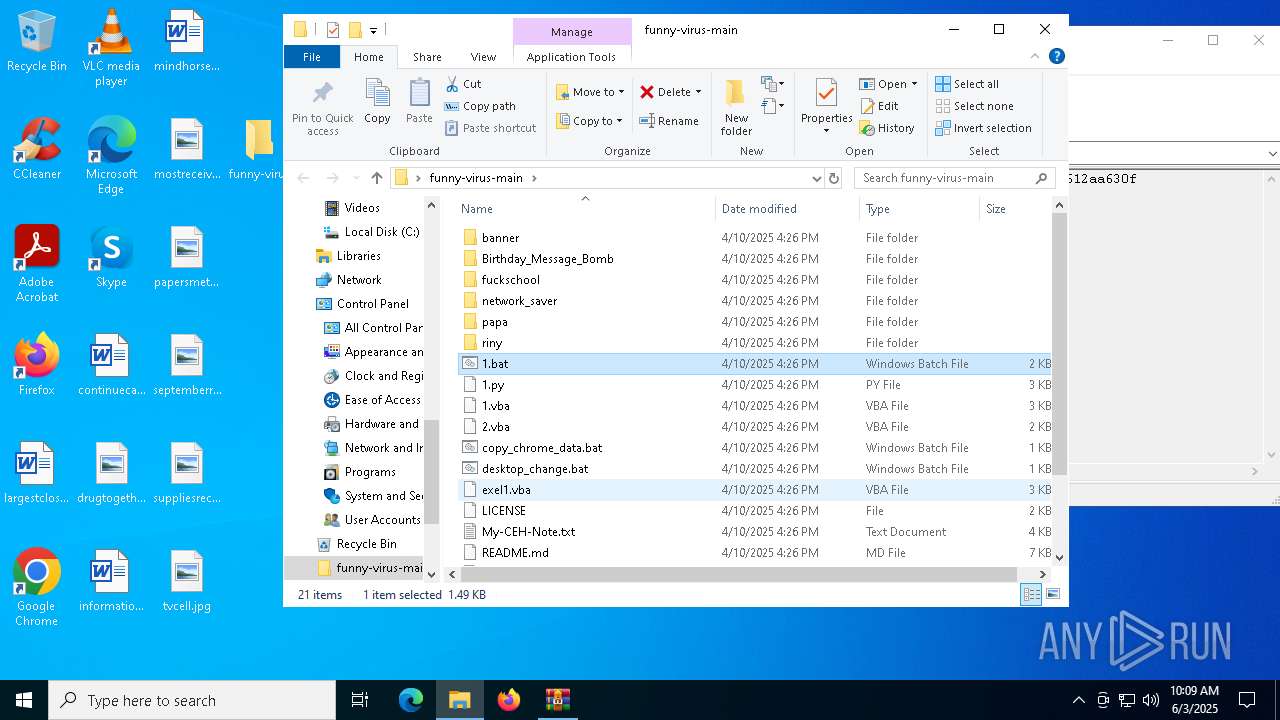
| File name: | funny-virus-main.zip |
| Full analysis: | https://app.any.run/tasks/3509416c-ab01-445a-8437-6c6c09c93e8f |
| Verdict: | Malicious activity |
| Analysis date: | June 03, 2025, 10:09:03 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v1.0 to extract, compression method=store |
| MD5: | 7ED0DC5D448D1B64BC9C9D9ABE635195 |
| SHA1: | 36E54354A28C685F528183948597F454C0079A1F |
| SHA256: | 8DB8417904F66581604AB0E54D0B8102B3A13D63BF6216DBE22014F1B4A3D7D6 |
| SSDEEP: | 1536:qEdHgyTootc+L46O1A9KJp9Av6UG0da0YXdLzku:nHfTooV4h1V9AfTdapXdLzT |
MALICIOUS
No malicious indicators.SUSPICIOUS
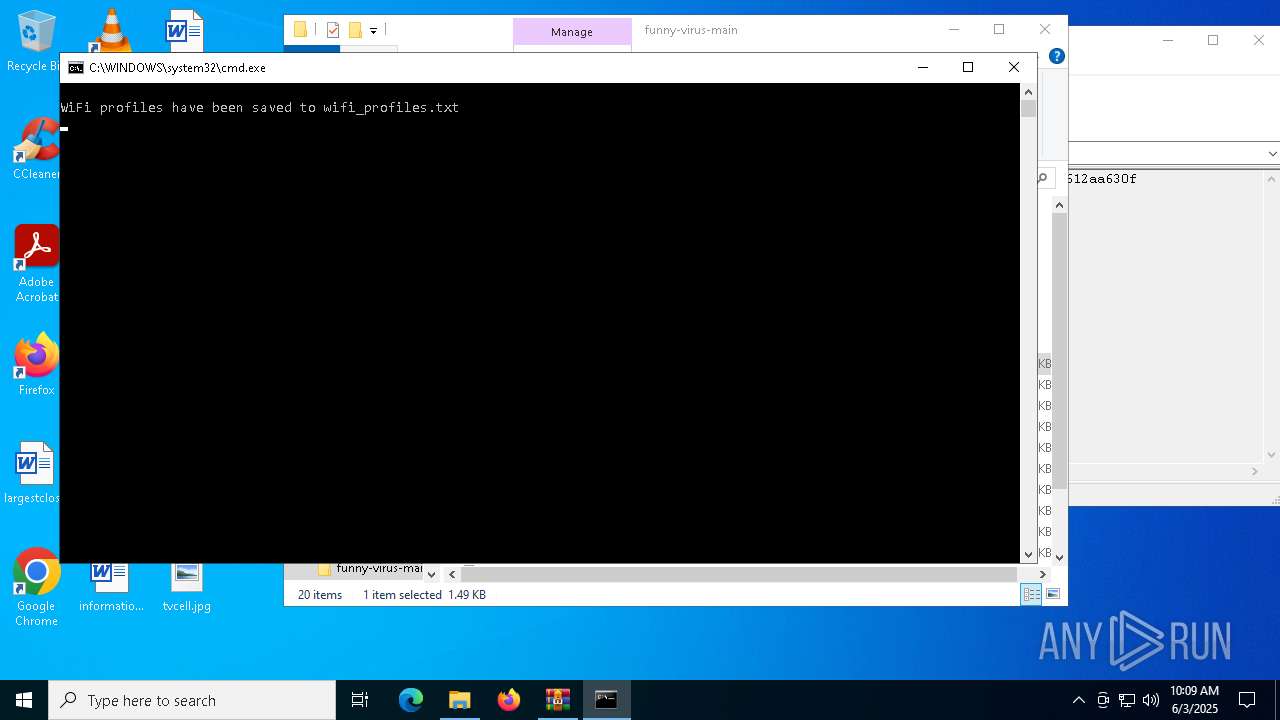
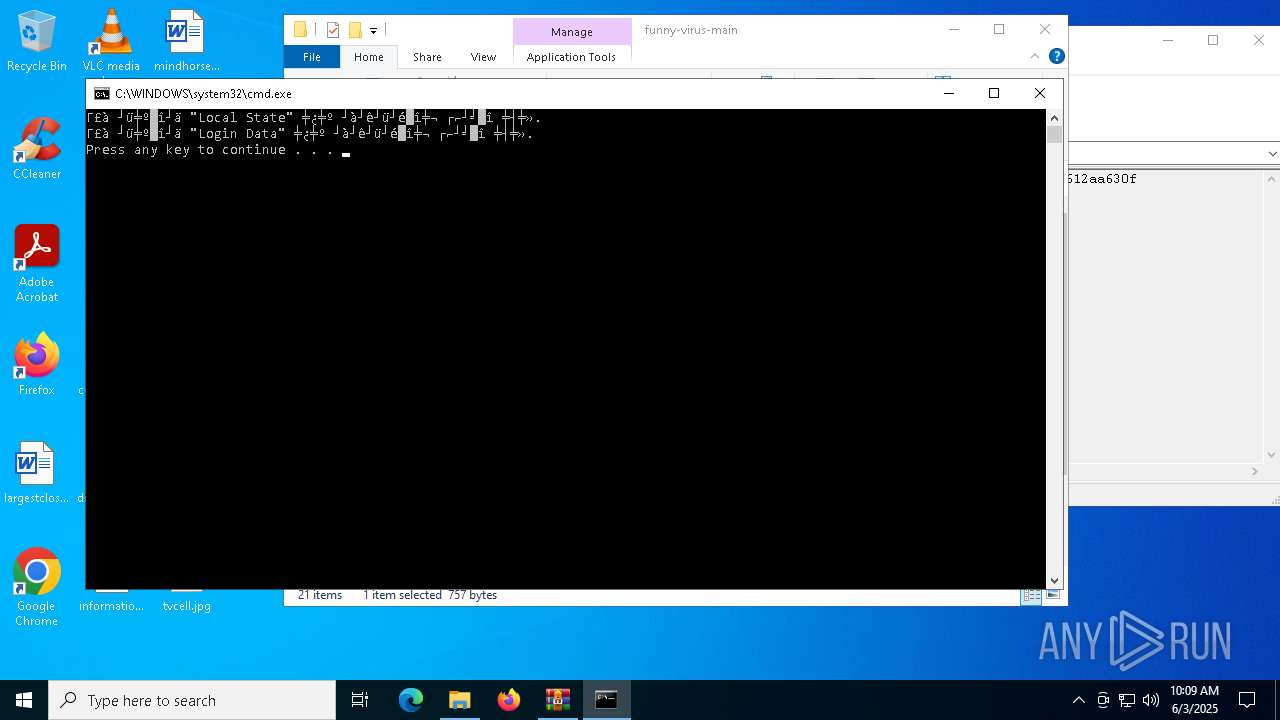
Starts CMD.EXE for commands execution
- cmd.exe (PID: 6368)
- powershell.exe (PID: 8144)
Application launched itself
- cmd.exe (PID: 6368)
Uses NETSH.EXE to obtain data on the network
- cmd.exe (PID: 2152)
Uses TIMEOUT.EXE to delay execution
- cmd.exe (PID: 6368)
Starts process via Powershell
- powershell.exe (PID: 8144)
Starts NET.EXE to display or manage information about active sessions
- net.exe (PID: 8188)
- cmd.exe (PID: 7340)
- cmd.exe (PID: 7808)
- net.exe (PID: 7936)
Starts POWERSHELL.EXE for commands execution
- cmd.exe (PID: 7340)
Executing commands from a ".bat" file
- powershell.exe (PID: 8144)
Uses REG/REGEDIT.EXE to modify registry
- cmd.exe (PID: 7808)
Uses RUNDLL32.EXE to load library
- cmd.exe (PID: 7808)
Uses ATTRIB.EXE to modify file attributes
- cmd.exe (PID: 7808)
INFO
Manual execution by a user
- cmd.exe (PID: 6368)
- cmd.exe (PID: 6852)
- cmd.exe (PID: 7340)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 10 |
|---|---|
| ZipBitFlag: | - |
| ZipCompression: | None |
| ZipModifyDate: | 2025:04:10 09:26:56 |
| ZipCRC: | 0x00000000 |
| ZipCompressedSize: | - |
| ZipUncompressedSize: | - |
| ZipFileName: | funny-virus-main/ |
Total processes
150
Monitored processes
23
Malicious processes
0
Suspicious processes
4
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1452 | C:\WINDOWS\System32\rundll32.exe C:\WINDOWS\System32\shell32.dll,SHCreateLocalServerRunDll {9aa46009-3ce0-458a-a354-715610a075e6} -Embedding | C:\Windows\System32\rundll32.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows host process (Rundll32) Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2152 | C:\WINDOWS\system32\cmd.exe /c netsh wlan show profiles | C:\Windows\System32\cmd.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2568 | netsh wlan show profiles | C:\Windows\System32\netsh.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Network Command Shell Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3304 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5624 | timeout /t 1 | C:\Windows\System32\timeout.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: timeout - pauses command processing Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
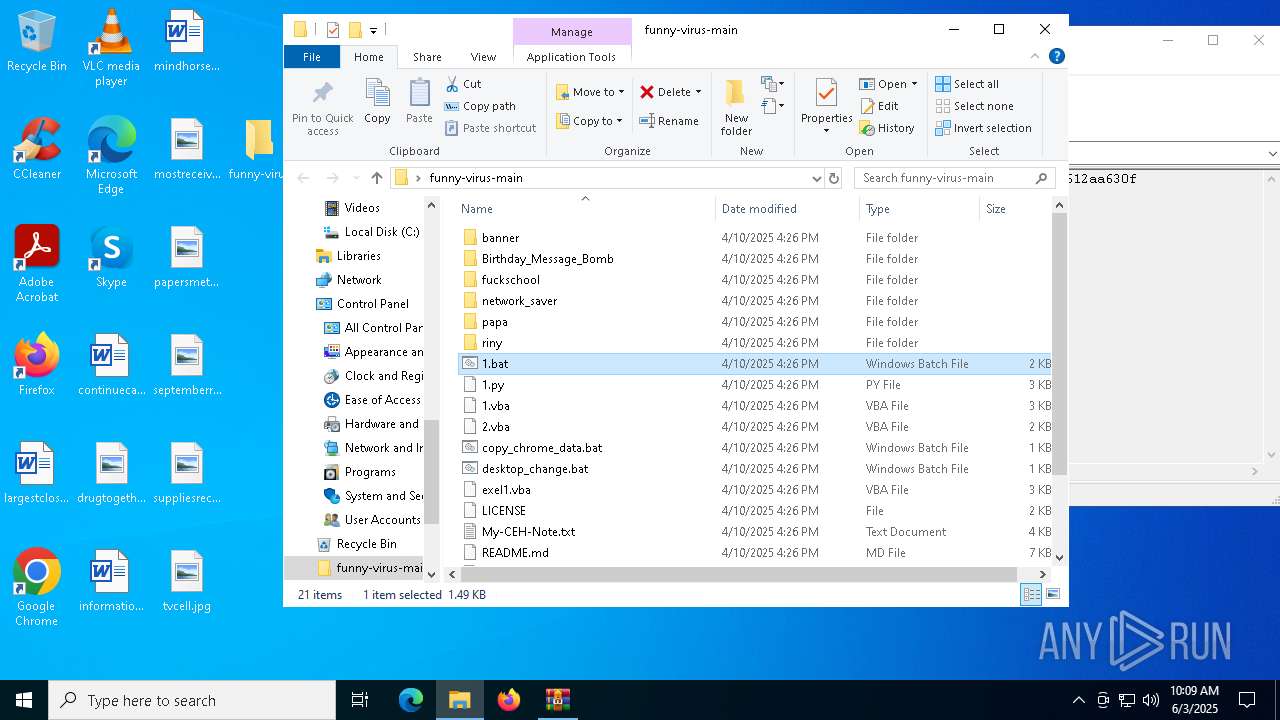
| 6368 | C:\WINDOWS\system32\cmd.exe /c ""C:\Users\admin\Desktop\funny-virus-main\1.bat" " | C:\Windows\System32\cmd.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6712 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
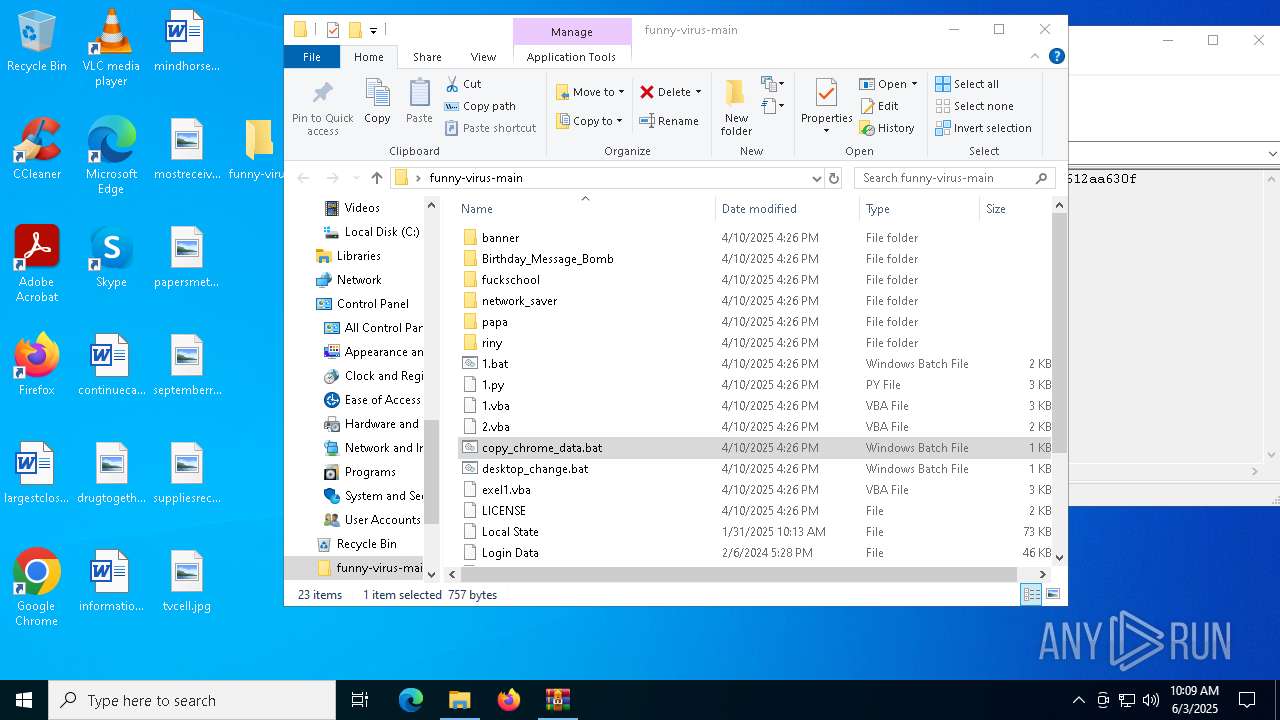
| 6852 | C:\WINDOWS\system32\cmd.exe /c ""C:\Users\admin\Desktop\funny-virus-main\copy_chrome_data.bat" " | C:\Windows\System32\cmd.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6988 | "C:\Program Files\WinRAR\WinRAR.exe" C:\Users\admin\AppData\Local\Temp\funny-virus-main.zip | C:\Program Files\WinRAR\WinRAR.exe | — | explorer.exe | |||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Version: 5.91.0 Modules
| |||||||||||||||
| 7216 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
6 607
Read events
6 598
Write events
9
Delete events
0
Modification events
| (PID) Process: | (6988) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\preferences.zip | |||
| (PID) Process: | (6988) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\chromium_ext.zip | |||
| (PID) Process: | (6988) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\omni_23_10_2024_.zip | |||
| (PID) Process: | (6988) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\funny-virus-main.zip | |||
| (PID) Process: | (6988) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (6988) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (6988) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (6988) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (7876) reg.exe | Key: | HKEY_CURRENT_USER\Control Panel\Desktop |
| Operation: | write | Name: | Wallpaper |
Value: C:\path\to\your\image.jpg | |||
Executable files
0
Suspicious files
3
Text files
47
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 6988 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa6988.16580\funny-virus-main\1.py | text | |
MD5:BADCC7B1424D2211765D12352B74E2B2 | SHA256:CA30EED660D8AA95F5712DDA06A466591EE78E927B7280FB56CE98A3BE85C3B2 | |||
| 6988 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa6988.16580\funny-virus-main\1.vba | text | |
MD5:73153B01647EC7BFB013F2A97312E772 | SHA256:2511D44A527173871289AC9594701C23D3D475AF0AEF8B185FE2A9AB0DF28C5E | |||
| 6988 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa6988.16580\funny-virus-main\Birthday_Message_Bomb\superstar.py | text | |
MD5:FCC4F409E1AF454F98E30E73E6D9E14A | SHA256:A9AD6B5BDEEADDBAEA1B001E2F58770ECF3ECE60FCAAF5ACEE7BEA47E7520940 | |||
| 6988 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa6988.16580\funny-virus-main\Birthday_Message_Bomb\hacker_popups.py | text | |
MD5:81043C6519A18A721CFCAB86A0140E17 | SHA256:55019EA7DB107E0173380D8AAFDC03F771DD1E938A7776C27420CEC23734D87D | |||
| 6988 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa6988.16580\funny-virus-main\README.md | text | |
MD5:E712E9BF09AA504BBF7B4189089BE7DC | SHA256:6262BA072C7C1686B89581BBC12140A49C387EBB20AE6F20EB2E4375FFDF2D39 | |||
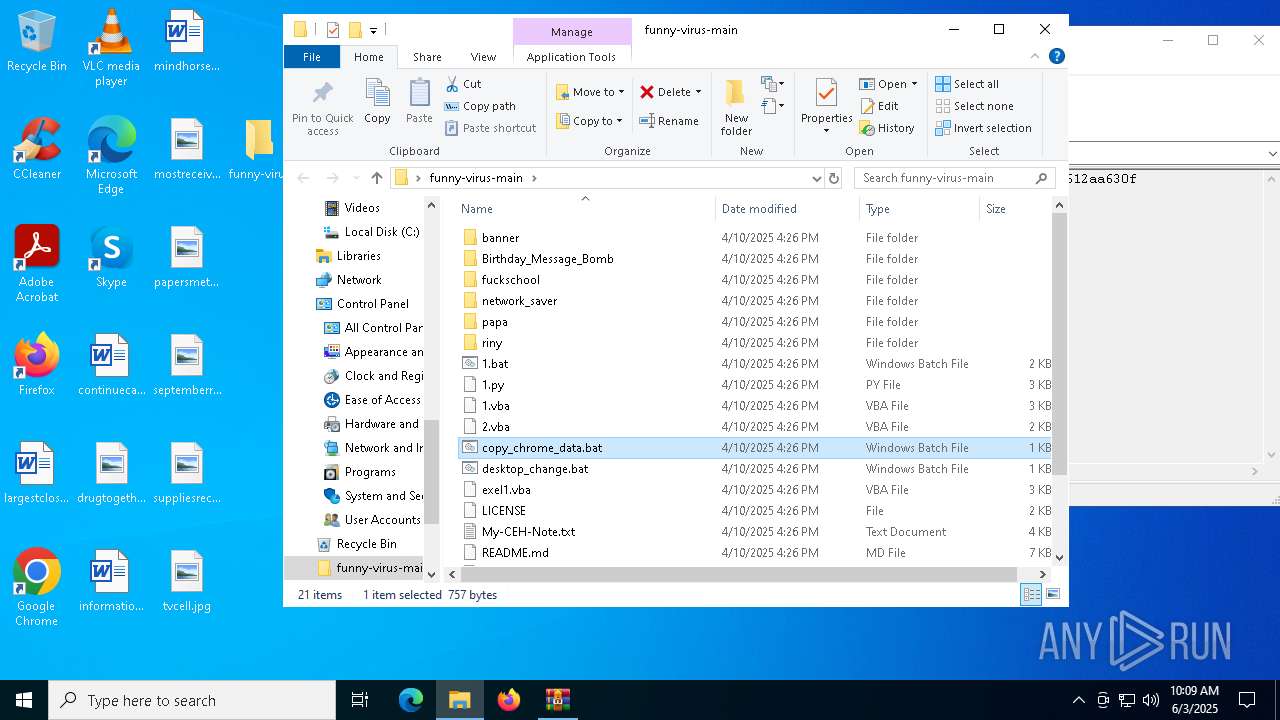
| 6988 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa6988.16580\funny-virus-main\desktop_change.bat | text | |
MD5:0769701F9F9D4D6B286E763B7DDF9320 | SHA256:7D62B4988303A734CA8FEC19692D5BFE9DF617F283393F20782DAA1FE3BC000D | |||
| 6988 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa6988.16580\funny-virus-main\banner\fsociety.py | text | |
MD5:02AD64A16CA5B5FFC73D3231A1471169 | SHA256:A0E82F9E4299A5A585B18C49FD27B6D35E5E54DB68F192BD247D8AC66A58A455 | |||
| 6988 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa6988.16580\funny-virus-main\1.bat | text | |
MD5:9683524A98709469287BD162BB5E200E | SHA256:E4F260CC3993E1EAAC7302FC9D928F71E88B47FCE3E987E26AC5AB432F614ABB | |||
| 6988 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa6988.16580\funny-virus-main\fuckschool\fuckschool.bat | text | |
MD5:1FD1CCBDE93B2B2ED0DFC495B57D4A38 | SHA256:085FDC9CF27BC98AAC87F62ED2020E4C05F3AB411BA6AA8228CC1B7E0C2BF949 | |||
| 6988 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa6988.16580\funny-virus-main\network_saver\network_saver.bat | text | |
MD5:1D913538AD2BDE68F3C8156A1295E27F | SHA256:1E63482E41A91922A3B99926CE51E55F910B4A1BF82E998D04F40F75E74C1CC8 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
7
TCP/UDP connections
20
DNS requests
12
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
7552 | svchost.exe | GET | 200 | 23.216.77.28:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
7552 | svchost.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
7000 | SIHClient.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
5496 | MoUsoCoreWorker.exe | GET | 200 | 23.216.77.28:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
5496 | MoUsoCoreWorker.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
6544 | svchost.exe | GET | 200 | 184.30.131.245:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
7000 | SIHClient.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
7864 | RUXIMICS.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
— | — | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
5496 | MoUsoCoreWorker.exe | 23.216.77.28:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
7552 | svchost.exe | 23.216.77.28:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
5496 | MoUsoCoreWorker.exe | 23.35.229.160:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
7552 | svchost.exe | 23.35.229.160:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
7552 | svchost.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
6544 | svchost.exe | 40.126.31.2:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |