| File name: | E3978DC6335A4DB076E973FF2DEE7A0FDA1B6803FC61842CCDEED90362200F09.zip |
| Full analysis: | https://app.any.run/tasks/eac763db-b51e-4d17-a592-204f12c00a84 |
| Verdict: | Malicious activity |
| Analysis date: | August 17, 2019, 19:13:41 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v2.0 to extract |
| MD5: | AFAD4C5C84EDB23BE762CB8C28365865 |
| SHA1: | 3512CB391F6F65A672692ED4B10E166BFA11A447 |
| SHA256: | 8DB420BEE885855F19816161E0CA9FF55F9D05AFB70EB43B757336D081B8A1E3 |
| SSDEEP: | 6144:CfufPqy4FTd9PHCiznTGgFj18XOnzaC/cN3sSxaBF2PH2E5on52VmIt6yjnS6:SuKXh96yTGc18+nzA8SxLH1DVmmrS6 |
MALICIOUS
Application was dropped or rewritten from another process
- E3978DC6335A4DB076E973FF2DEE7A0FDA1B6803FC61842CCDEED90362200F09.exe (PID: 4048)
- E3978DC6335A4DB076E973FF2DEE7A0FDA1B6803FC61842CCDEED90362200F09.exe (PID: 2748)
Starts NET.EXE for service management
- E3978DC6335A4DB076E973FF2DEE7A0FDA1B6803FC61842CCDEED90362200F09.exe (PID: 4048)
- E3978DC6335A4DB076E973FF2DEE7A0FDA1B6803FC61842CCDEED90362200F09.exe (PID: 2748)
SUSPICIOUS
Executable content was dropped or overwritten
- E3978DC6335A4DB076E973FF2DEE7A0FDA1B6803FC61842CCDEED90362200F09.exe (PID: 4048)
Creates files in the program directory
- E3978DC6335A4DB076E973FF2DEE7A0FDA1B6803FC61842CCDEED90362200F09.exe (PID: 4048)
INFO
Manual execution by user
- E3978DC6335A4DB076E973FF2DEE7A0FDA1B6803FC61842CCDEED90362200F09.exe (PID: 4048)
- E3978DC6335A4DB076E973FF2DEE7A0FDA1B6803FC61842CCDEED90362200F09.exe (PID: 2748)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 20 |
|---|---|
| ZipBitFlag: | 0x0009 |
| ZipCompression: | Deflated |
| ZipModifyDate: | 2019:08:17 18:54:22 |
| ZipCRC: | 0xae3cf67c |
| ZipCompressedSize: | 380464 |
| ZipUncompressedSize: | 790528 |
| ZipFileName: | E3978DC6335A4DB076E973FF2DEE7A0FDA1B6803FC61842CCDEED90362200F09 |
Total processes
57
Monitored processes
15
Malicious processes
2
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 2248 | C:\Windows\system32\net1 stop "samss" /y | C:\Windows\system32\net1.exe | — | net.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Net Command Exit code: 2 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 2484 | "C:\Windows\System32\net.exe" stop "audioendpointbuilder" /y | C:\Windows\System32\net.exe | — | E3978DC6335A4DB076E973FF2DEE7A0FDA1B6803FC61842CCDEED90362200F09.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Net Command Exit code: 2 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2508 | "C:\Windows\System32\net.exe" stop "samss" /y | C:\Windows\System32\net.exe | — | E3978DC6335A4DB076E973FF2DEE7A0FDA1B6803FC61842CCDEED90362200F09.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Net Command Exit code: 2 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2744 | C:\Windows\system32\net1 stop "samss" /y | C:\Windows\system32\net1.exe | — | net.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Net Command Exit code: 2 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 2748 | "C:\Users\admin\Desktop\E3978DC6335A4DB076E973FF2DEE7A0FDA1B6803FC61842CCDEED90362200F09.exe" | C:\Users\admin\Desktop\E3978DC6335A4DB076E973FF2DEE7A0FDA1B6803FC61842CCDEED90362200F09.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: HIGH Description: hexedit_demo MFC Application Exit code: 0 Version: 1, 0, 0, 1 Modules
| |||||||||||||||
| 3228 | "C:\Windows\System32\net.exe" stop "samss" /y | C:\Windows\System32\net.exe | — | E3978DC6335A4DB076E973FF2DEE7A0FDA1B6803FC61842CCDEED90362200F09.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Net Command Exit code: 2 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3276 | C:\Windows\system32\net1 stop "audioendpointbuilder" /y | C:\Windows\system32\net1.exe | — | net.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Net Command Exit code: 2 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
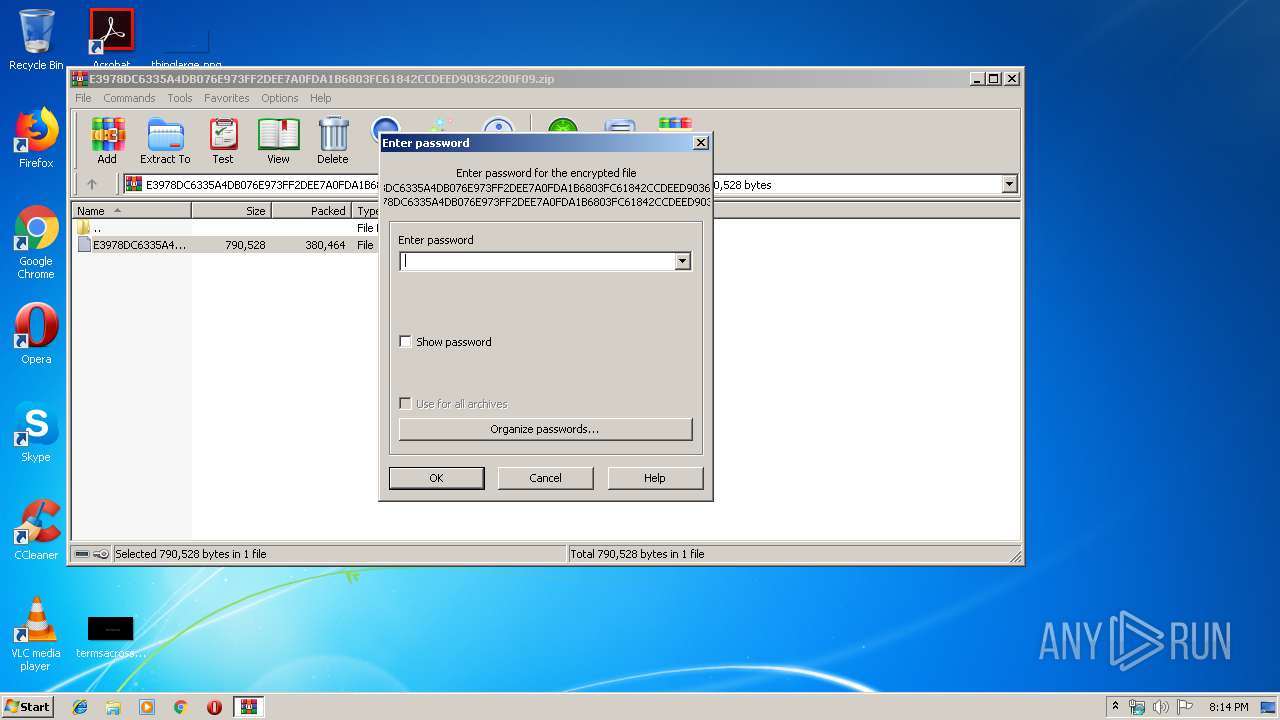
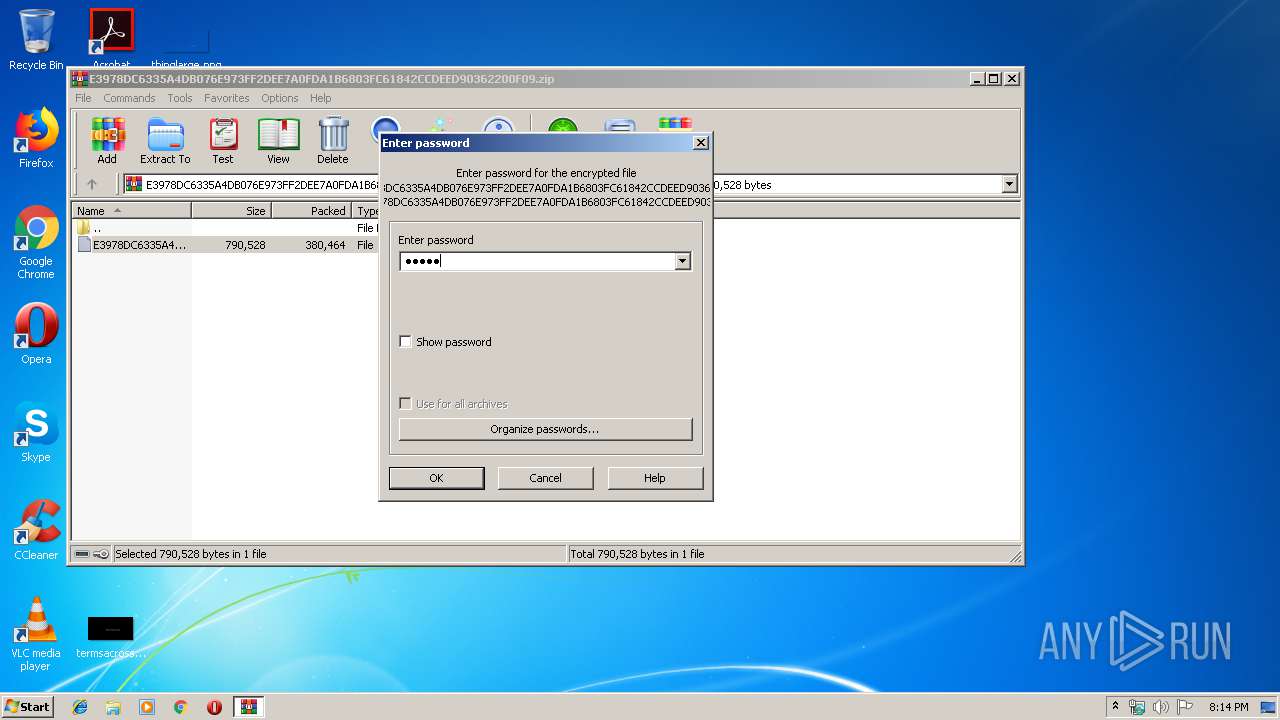
| 3400 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\AppData\Local\Temp\E3978DC6335A4DB076E973FF2DEE7A0FDA1B6803FC61842CCDEED90362200F09.zip" | C:\Program Files\WinRAR\WinRAR.exe | — | explorer.exe | |||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.60.0 Modules
| |||||||||||||||
| 3576 | C:\Windows\system32\net1 stop "audioendpointbuilder" /y | C:\Windows\system32\net1.exe | — | net.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Net Command Exit code: 2 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 3880 | "C:\Windows\System32\net.exe" stop "audioendpointbuilder" /y | C:\Windows\System32\net.exe | — | E3978DC6335A4DB076E973FF2DEE7A0FDA1B6803FC61842CCDEED90362200F09.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Net Command Exit code: 2 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
Total events
555
Read events
538
Write events
17
Delete events
0
Modification events
| (PID) Process: | (3400) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (3400) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (3400) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\72\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (3400) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\E3978DC6335A4DB076E973FF2DEE7A0FDA1B6803FC61842CCDEED90362200F09.zip | |||
| (PID) Process: | (3400) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (3400) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (3400) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (3400) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (3400) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface |
| Operation: | write | Name: | ShowPassword |
Value: 0 | |||
| (PID) Process: | (4048) E3978DC6335A4DB076E973FF2DEE7A0FDA1B6803FC61842CCDEED90362200F09.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 0 | |||
Executable files
52
Suspicious files
82
Text files
19
Unknown types
4
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3400 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRb3400.24376\E3978DC6335A4DB076E973FF2DEE7A0FDA1B6803FC61842CCDEED90362200F09 | — | |
MD5:— | SHA256:— | |||
| 4048 | E3978DC6335A4DB076E973FF2DEE7A0FDA1B6803FC61842CCDEED90362200F09.exe | C:\Users\admin\AppData\Local\VirtualStore\Program Files\Adobe\Acrobat Reader DC\Liesmich.htm | — | |
MD5:— | SHA256:— | |||
| 4048 | E3978DC6335A4DB076E973FF2DEE7A0FDA1B6803FC61842CCDEED90362200F09.exe | C:\Users\admin\AppData\Local\VirtualStore\Program Files\Adobe\Acrobat Reader DC\Reader\AcroApp\CAT\Combine_R_RHP.aapp | — | |
MD5:— | SHA256:— | |||
| 4048 | E3978DC6335A4DB076E973FF2DEE7A0FDA1B6803FC61842CCDEED90362200F09.exe | C:\Users\admin\AppData\Local\VirtualStore\Program Files\Adobe\Acrobat Reader DC\Llegiu-me.htm | — | |
MD5:— | SHA256:— | |||
| 4048 | E3978DC6335A4DB076E973FF2DEE7A0FDA1B6803FC61842CCDEED90362200F09.exe | C:\Users\admin\AppData\Local\VirtualStore\Program Files\Adobe\Acrobat Reader DC\Reader\AcroApp\CAT\Edit_R_RHP.aapp | — | |
MD5:— | SHA256:— | |||
| 4048 | E3978DC6335A4DB076E973FF2DEE7A0FDA1B6803FC61842CCDEED90362200F09.exe | C:\Users\admin\AppData\Local\VirtualStore\Program Files\Adobe\Acrobat Reader DC\Reader\AcroApp\CAT\MoreTools.aapp | — | |
MD5:— | SHA256:— | |||
| 4048 | E3978DC6335A4DB076E973FF2DEE7A0FDA1B6803FC61842CCDEED90362200F09.exe | C:\Users\admin\AppData\Local\VirtualStore\Program Files\Adobe\Acrobat Reader DC\Reader\AcroApp\CAT\Home.aapp | — | |
MD5:— | SHA256:— | |||
| 4048 | E3978DC6335A4DB076E973FF2DEE7A0FDA1B6803FC61842CCDEED90362200F09.exe | C:\Users\admin\AppData\Local\VirtualStore\Program Files\Adobe\Acrobat Reader DC\Reader\AcroApp\CAT\Viewer.aapp | — | |
MD5:— | SHA256:— | |||
| 4048 | E3978DC6335A4DB076E973FF2DEE7A0FDA1B6803FC61842CCDEED90362200F09.exe | C:\Users\admin\AppData\Local\VirtualStore\Program Files\Adobe\Acrobat Reader DC\Reader\AcroApp\CAT\Certificates_R.aapp | — | |
MD5:— | SHA256:— | |||
| 4048 | E3978DC6335A4DB076E973FF2DEE7A0FDA1B6803FC61842CCDEED90362200F09.exe | C:\Users\admin\AppData\Local\VirtualStore\Program Files\Adobe\Acrobat Reader DC\Reader\AcroApp\CHS\Home.aapp | — | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
0
DNS requests
0
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report