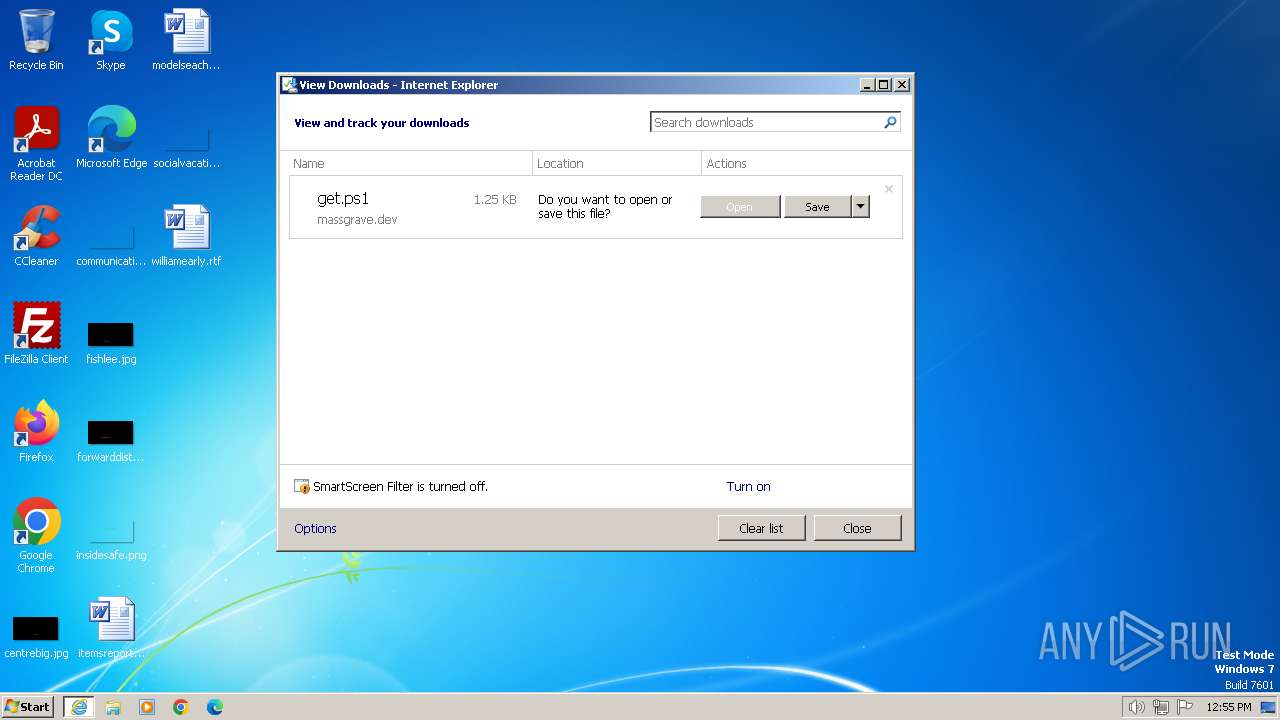
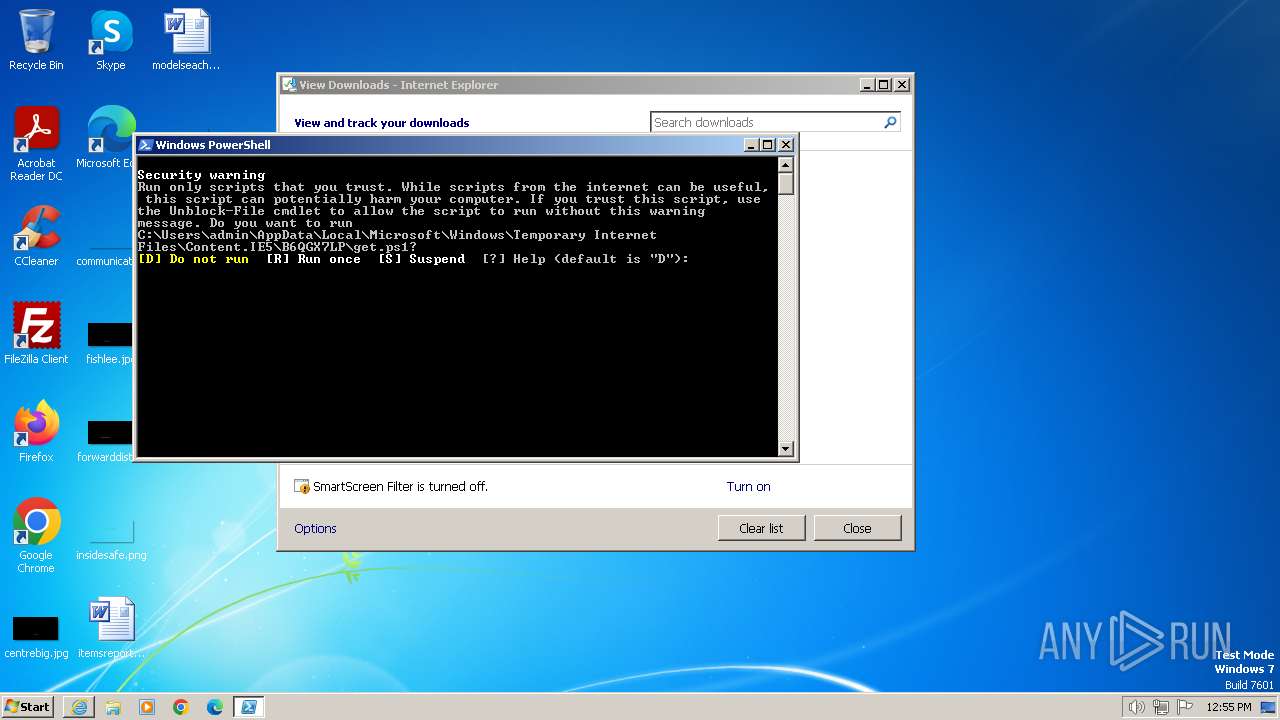
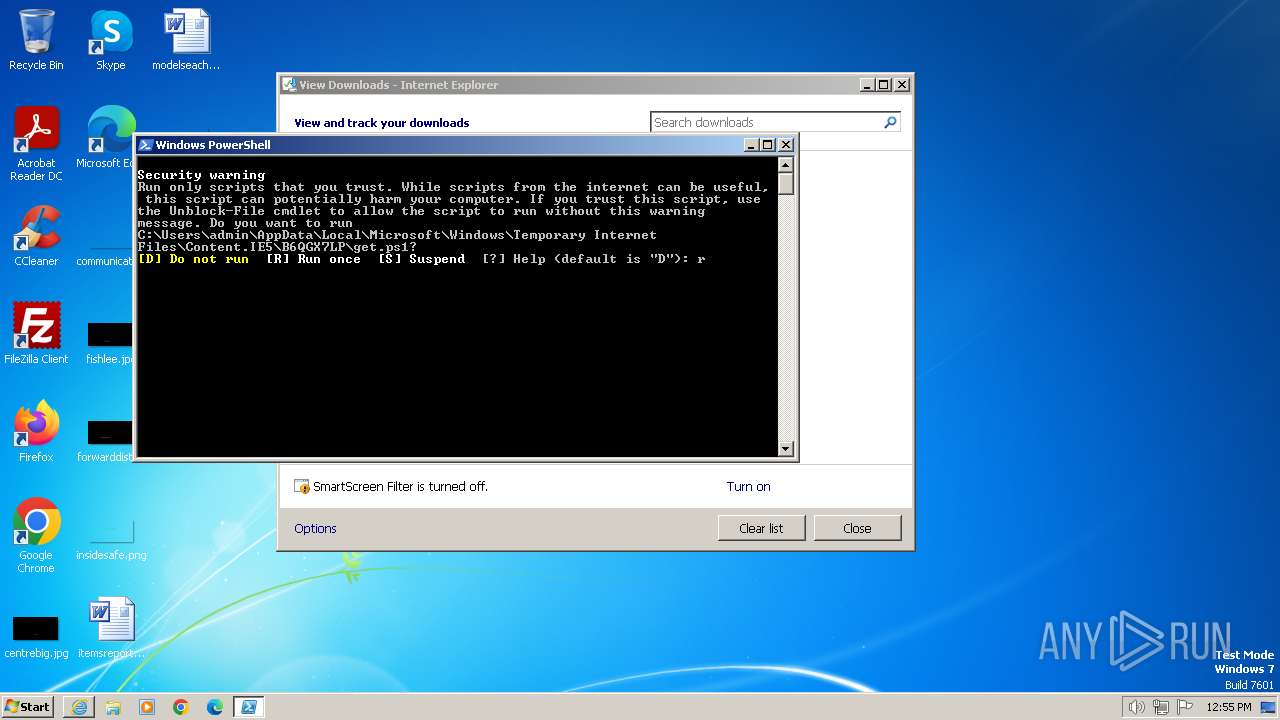
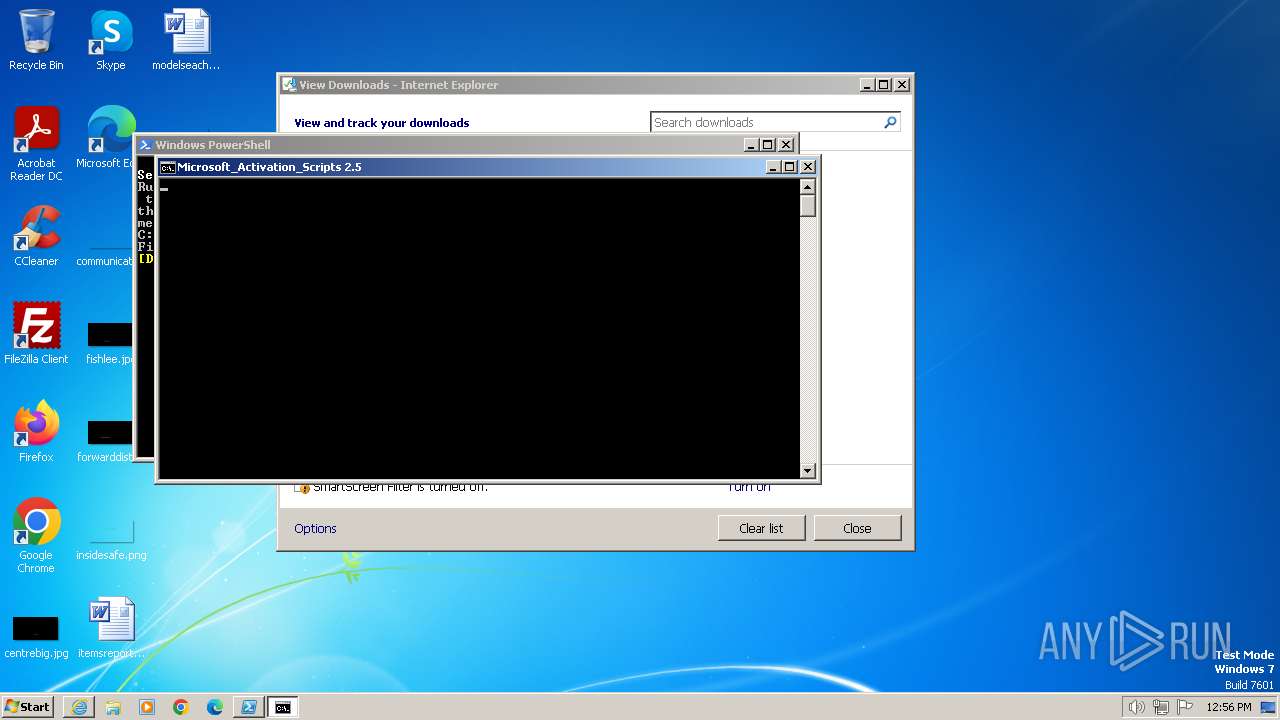
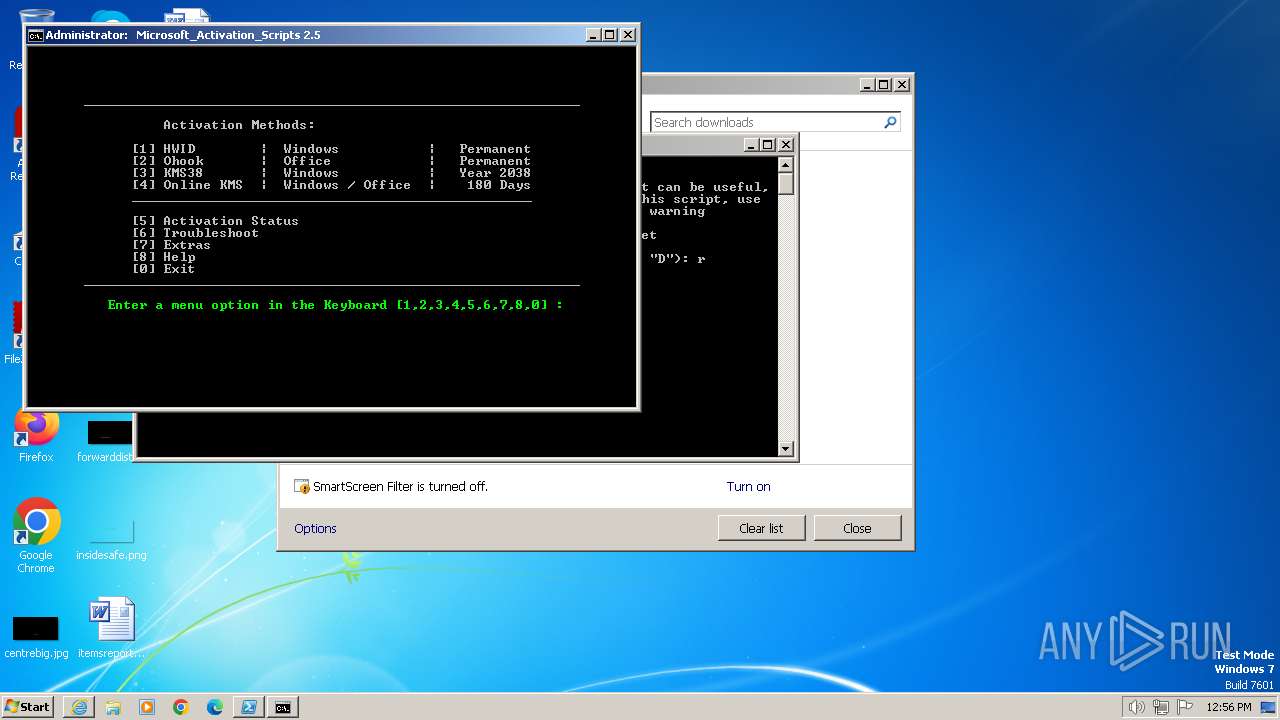
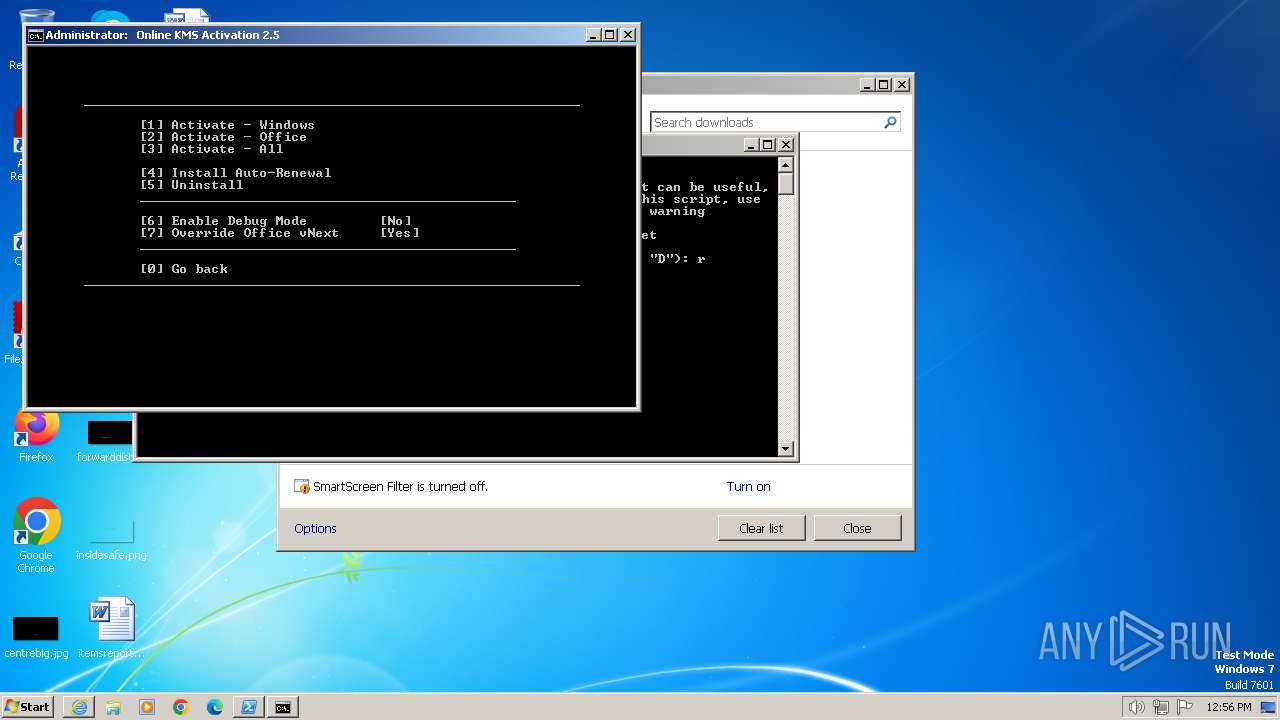
| URL: | https://massgrave.dev/get.ps1 |
| Full analysis: | https://app.any.run/tasks/d9e85153-6a4a-42e4-a525-af002649b1cc |
| Verdict: | Malicious activity |
| Analysis date: | February 09, 2024, 12:55:43 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MD5: | BCBF57484548C313A8E38595A4FFC964 |
| SHA1: | 5994D10E1A7E80F6F80BE3ECD77D2ED66C03D215 |
| SHA256: | 8DA67755D5AE41AF347E207E4151C1F394E856525CEBA222DB9E8428E126EFA8 |
| SSDEEP: | 3:N8a0KrTn:2a00n |
MALICIOUS
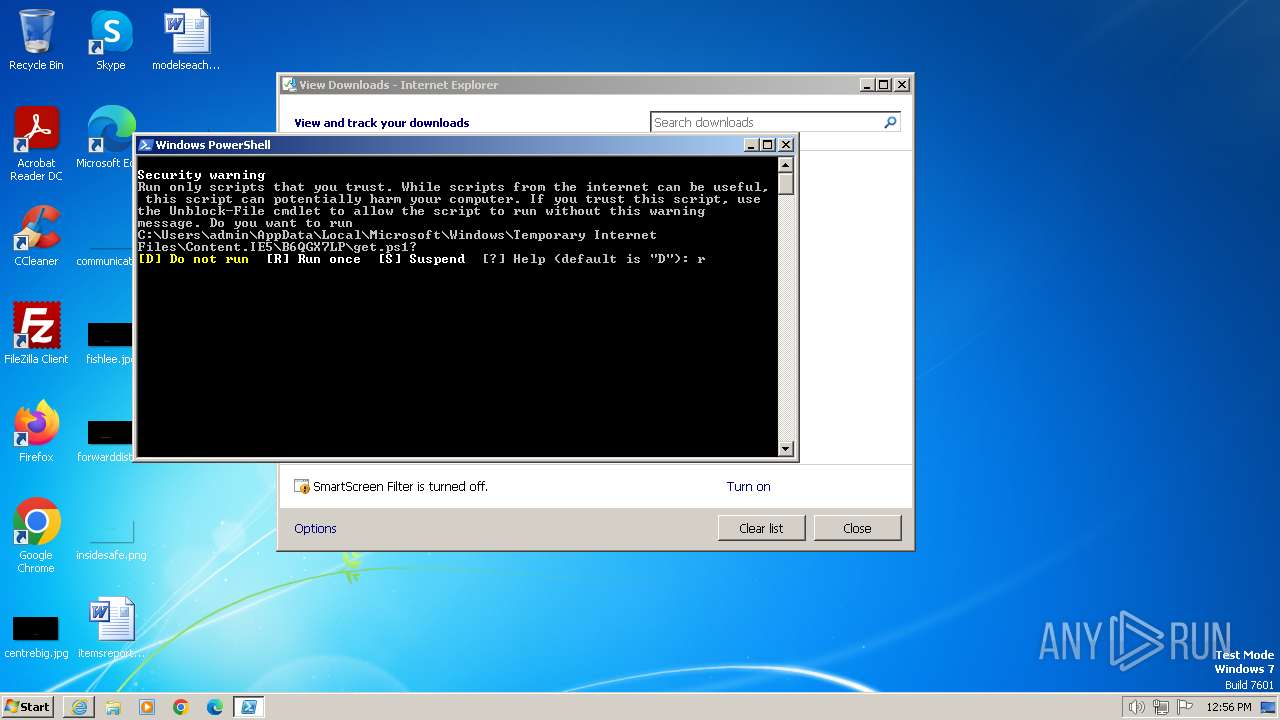
Starts POWERSHELL.EXE for commands execution
- iexplore.exe (PID: 3672)
Starts NET.EXE for service management
- cmd.exe (PID: 2484)
- net.exe (PID: 1820)
SUSPICIOUS
Reads the Internet Settings
- powershell.exe (PID: 3936)
- powershell.exe (PID: 1888)
- WMIC.exe (PID: 1192)
- WMIC.exe (PID: 3260)
- WMIC.exe (PID: 2388)
- WMIC.exe (PID: 2972)
- WMIC.exe (PID: 1792)
- WMIC.exe (PID: 2588)
- WMIC.exe (PID: 984)
- WMIC.exe (PID: 1900)
- WMIC.exe (PID: 2020)
- WMIC.exe (PID: 1592)
The process executes Powershell scripts
- iexplore.exe (PID: 3672)
Starts POWERSHELL.EXE for commands execution
- cmd.exe (PID: 956)
- cmd.exe (PID: 2484)
The Powershell connects to the Internet
- powershell.exe (PID: 3936)
Application launched itself
- cmd.exe (PID: 956)
- cmd.exe (PID: 2484)
Executing commands from ".cmd" file
- cmd.exe (PID: 956)
- powershell.exe (PID: 1888)
- cmd.exe (PID: 2484)
- powershell.exe (PID: 3936)
Starts CMD.EXE for commands execution
- cmd.exe (PID: 956)
- powershell.exe (PID: 1888)
- cmd.exe (PID: 2484)
- powershell.exe (PID: 3936)
Unusual connection from system programs
- powershell.exe (PID: 3936)
Using 'findstr.exe' to search for text patterns in files and output
- cmd.exe (PID: 2484)
- cmd.exe (PID: 956)
Starts SC.EXE for service management
- cmd.exe (PID: 2484)
- cmd.exe (PID: 956)
Uses WMIC.EXE to obtain computer system information
- cmd.exe (PID: 2484)
Uses REG/REGEDIT.EXE to modify registry
- cmd.exe (PID: 2484)
Starts NET.EXE to map network drives
- cmd.exe (PID: 2484)
Uses WMIC.EXE to obtain Windows Installer data
- cmd.exe (PID: 2484)
- cmd.exe (PID: 2660)
- cmd.exe (PID: 948)
Uses WMIC.EXE to obtain service application data
- cmd.exe (PID: 2992)
INFO
The process uses the downloaded file
- iexplore.exe (PID: 3672)
- powershell.exe (PID: 3936)
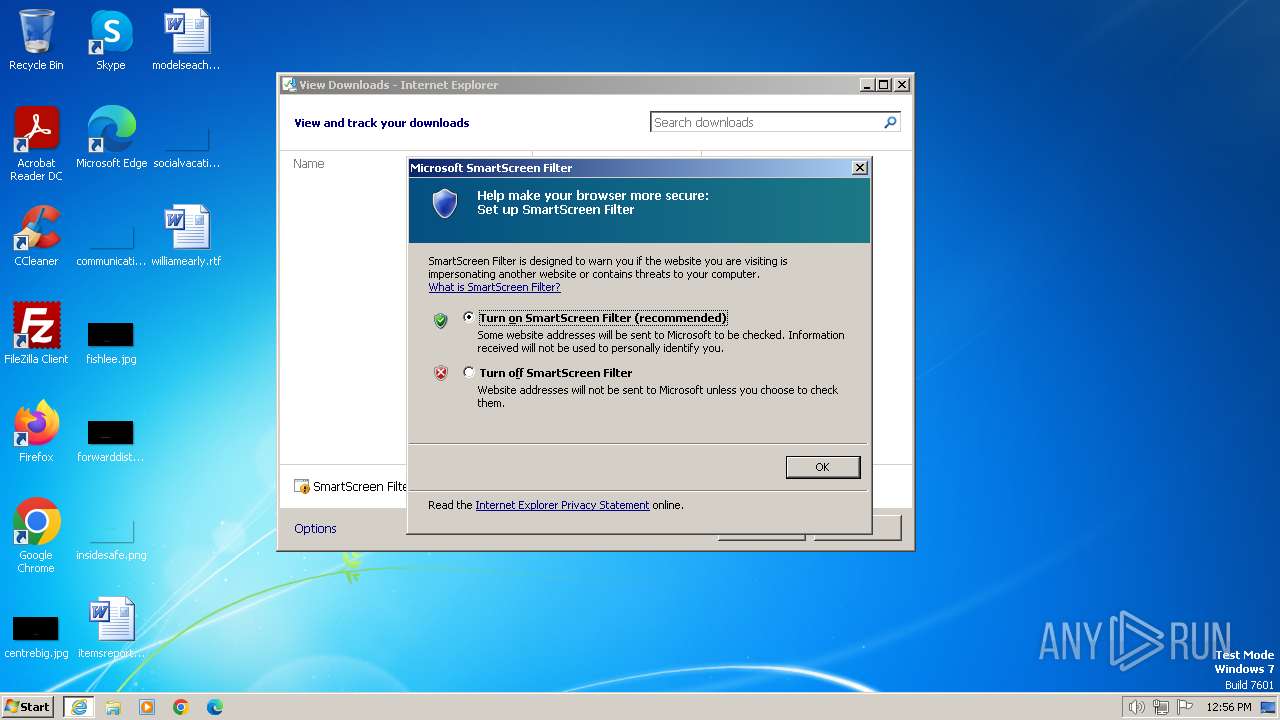
Modifies the phishing filter of IE
- iexplore.exe (PID: 3672)
Application launched itself
- iexplore.exe (PID: 3672)
Checks operating system version
- cmd.exe (PID: 956)
- cmd.exe (PID: 2484)
Checks supported languages
- mode.com (PID: 2568)
- mode.com (PID: 3564)
- mode.com (PID: 292)
- mode.com (PID: 3148)
- mode.com (PID: 2092)
Reads Microsoft Office registry keys
- reg.exe (PID: 2184)
- reg.exe (PID: 2488)
- reg.exe (PID: 3912)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
225
Monitored processes
180
Malicious processes
5
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 292 | mode con cols=98 lines=31 | C:\Windows\System32\mode.com | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: DOS Device MODE Utility Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 296 | C:\Windows\system32\cmd.exe /S /D /c" echo "-el" " | C:\Windows\System32\cmd.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 316 | find /i "/S" | C:\Windows\System32\find.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Find String (grep) Utility Exit code: 1 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 392 | reg delete "HKLM\SOFTWARE\Microsoft\Windows NT\CurrentVersion\SoftwareProtectionPlatform" /f /v DisableKeyManagementServiceHostCaching | C:\Windows\System32\reg.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Registry Console Tool Exit code: 1 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 392 | reg delete "HKLM\SOFTWARE\Microsoft\Windows NT\CurrentVersion\SoftwareProtectionPlatform\55c92734-d682-4d71-983e-d6ec3f16059f" /f | C:\Windows\System32\reg.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Registry Console Tool Exit code: 1 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 448 | C:\Windows\system32\cmd.exe /S /D /c" echo "127.69.2.5" " | C:\Windows\System32\cmd.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 480 | find "127.69" | C:\Windows\System32\find.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Find String (grep) Utility Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 680 | sc query Null | C:\Windows\System32\sc.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: A tool to aid in developing services for WindowsNT Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 696 | find /i "STOPPED" | C:\Windows\System32\find.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Find String (grep) Utility Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 752 | sc query sppsvc | C:\Windows\System32\sc.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: A tool to aid in developing services for WindowsNT Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
Total events
45 385
Read events
45 164
Write events
175
Delete events
46
Modification events
| (PID) Process: | (3672) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPDaysSinceLastAutoMigration |
Value: 1 | |||
| (PID) Process: | (3672) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPLastLaunchLowDateTime |
Value: | |||
| (PID) Process: | (3672) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPLastLaunchHighDateTime |
Value: 31087447 | |||
| (PID) Process: | (3672) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\UrlBlockManager |
| Operation: | write | Name: | NextCheckForUpdateLowDateTime |
Value: | |||
| (PID) Process: | (3672) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\UrlBlockManager |
| Operation: | write | Name: | NextCheckForUpdateHighDateTime |
Value: 31087447 | |||
| (PID) Process: | (3672) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Content |
| Operation: | write | Name: | CachePrefix |
Value: | |||
| (PID) Process: | (3672) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (3672) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
| (PID) Process: | (3672) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\Main |
| Operation: | write | Name: | CompatibilityFlags |
Value: 0 | |||
| (PID) Process: | (3672) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
Executable files
0
Suspicious files
23
Text files
20
Unknown types
7
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3672 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\B6QGX7LP\get.ps1 | text | |
MD5:993B9C88C73AC1E74472E0CC9E8970DD | SHA256:D3234E767F52807C6A8D8C7222EC0701A5435FF1C0FAF96A32CA7B41DF395952 | |||
| 3952 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\B2FAF7692FD9FFBD64EDE317E42334BA_89854CA6A0F0936A4D2ECA78845CEA25 | der | |
MD5:DE279EF11368DD24578007E81E086851 | SHA256:9ACCB850299742BAE8334CC8C9A56722E864244C6C9D6942E23E5B7F42426FC1 | |||
| 3672 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Internet Explorer\Recovery\Active\{8D1DF1A5-C74A-11EE-AE0A-12A9866C77DE}.dat | binary | |
MD5:9664C3354D8BF1CC543EDA9B18741953 | SHA256:CD8D2BCC03897F45B9C5FDEB7394572C0E8898FD7328790C40E10BA0EC1CFF13 | |||
| 3936 | powershell.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\d93f411851d7c929.customDestinations-ms~RF17fee2.TMP | binary | |
MD5:0268C3470C936E6FBAC2945B9E1C2099 | SHA256:DF2AF58E8879B48826D8A418ED3B02CC8D484BCFC231C5B7A11BD153ED3998E9 | |||
| 3952 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\D0E1C4B6144E7ECAB3F020E4A19EFC29_03D1B482EE3032A122274428715A4E19 | binary | |
MD5:74F313F34006D25065C9EF556619F57B | SHA256:308E6A9E15D804174983626FC5A508F30490DDE0BBA569DA8EF5798B9BB1FF28 | |||
| 3952 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\B6QGX7LP\get.ps1.v3k9p51.partial | text | |
MD5:993B9C88C73AC1E74472E0CC9E8970DD | SHA256:D3234E767F52807C6A8D8C7222EC0701A5435FF1C0FAF96A32CA7B41DF395952 | |||
| 3952 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\MFAQUS6V\get[1].ps1 | text | |
MD5:993B9C88C73AC1E74472E0CC9E8970DD | SHA256:D3234E767F52807C6A8D8C7222EC0701A5435FF1C0FAF96A32CA7B41DF395952 | |||
| 3672 | iexplore.exe | C:\Users\admin\AppData\Local\Temp\~DFC86EE5303878FF27.TMP | binary | |
MD5:3A5BA565B43128602F74939DF6D8FF79 | SHA256:571D57821A583383D9CB82F9D7D73CBF73C169AA3EBAC2D099D3D9F6DC4C7CD7 | |||
| 3672 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\B6QGX7LP\get.ps1.v3k9p51.partial:Zone.Identifier | text | |
MD5:FBCCF14D504B7B2DBCB5A5BDA75BD93B | SHA256:EACD09517CE90D34BA562171D15AC40D302F0E691B439F91BE1B6406E25F5913 | |||
| 3936 | powershell.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\d93f411851d7c929.customDestinations-ms | binary | |
MD5:42E3956892291F5EE35E1B989213EF05 | SHA256:D4E6947871B5FD00AD32F8707479DD6EC92AB65D8C6D157B1C0C3D99D575E468 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
13
TCP/UDP connections
25
DNS requests
16
Threats
3
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
3952 | iexplore.exe | GET | 304 | 23.53.42.40:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?f78d505714a595e3 | unknown | — | — | unknown |
3952 | iexplore.exe | GET | 304 | 23.53.42.40:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?545e1839169dd0e6 | unknown | — | — | unknown |
3952 | iexplore.exe | GET | 200 | 172.64.149.23:80 | http://ocsp.comodoca.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBRTtU9uFqgVGHhJwXZyWCNXmVR5ngQUoBEKIz6W8Qfs4q8p74Klf9AwpLQCEFZnHQTqT5lMbxCBR1nSdZQ%3D | unknown | binary | 1.42 Kb | unknown |
3952 | iexplore.exe | GET | 200 | 172.64.149.23:80 | http://ocsp.usertrust.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSr83eyJy3njhjVpn5bEpfc6MXawQQUOuEJhtTPGcKWdnRJdtzgNcZjY5oCECO3bePBuysaUZYeCOq3ZOg%3D | unknown | binary | 979 b | unknown |
1080 | svchost.exe | GET | 200 | 23.53.42.41:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/authrootstl.cab?0754c686571bd23f | unknown | compressed | 65.2 Kb | unknown |
1080 | svchost.exe | GET | 304 | 23.53.42.41:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?624d1ab720bef5f8 | unknown | compressed | 65.2 Kb | unknown |
3672 | iexplore.exe | GET | 304 | 23.53.42.41:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?e55f0cb727843010 | unknown | — | — | unknown |
3672 | iexplore.exe | GET | 304 | 23.53.42.41:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?719f0b64dcb4a601 | unknown | — | — | unknown |
3672 | iexplore.exe | GET | 304 | 23.53.42.41:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?b0be6f4ad90be2e5 | unknown | — | — | unknown |
3672 | iexplore.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | binary | 471 b | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
3952 | iexplore.exe | 5.45.97.157:443 | massgrave.dev | netcup GmbH | DE | unknown |
3952 | iexplore.exe | 23.53.42.40:80 | ctldl.windowsupdate.com | Akamai International B.V. | DE | unknown |
1080 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |
3952 | iexplore.exe | 172.64.149.23:80 | ocsp.comodoca.com | CLOUDFLARENET | US | unknown |
3936 | powershell.exe | 185.199.108.133:443 | raw.githubusercontent.com | FASTLY | US | unknown |
1080 | svchost.exe | 23.53.42.41:80 | ctldl.windowsupdate.com | Akamai International B.V. | DE | unknown |
3672 | iexplore.exe | 152.199.19.161:443 | r20swj13mr.microsoft.com | EDGECAST | US | whitelisted |
3672 | iexplore.exe | 23.53.42.41:80 | ctldl.windowsupdate.com | Akamai International B.V. | DE | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
massgrave.dev |
| unknown |
ctldl.windowsupdate.com |
| whitelisted |
ocsp.comodoca.com |
| whitelisted |
ocsp.usertrust.com |
| whitelisted |
raw.githubusercontent.com |
| shared |
updatecheck.massgrave.dev |
| unknown |
kms.zhuxiaole.org |
| unknown |
kms.moeyuuko.top |
| unknown |
r20swj13mr.microsoft.com |
| whitelisted |
iecvlist.microsoft.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
3952 | iexplore.exe | Misc activity | ET INFO Observed ZeroSSL SSL/TLS Certificate |
3952 | iexplore.exe | Misc activity | ET INFO Observed ZeroSSL SSL/TLS Certificate |
1080 | svchost.exe | Potentially Bad Traffic | ET DNS Query to a *.top domain - Likely Hostile |