| File name: | Win32.Turla.zip |
| Full analysis: | https://app.any.run/tasks/a3ded2bc-2cba-490d-991d-c9867ce8fb2d |
| Verdict: | Malicious activity |
| Analysis date: | April 04, 2018, 14:56:35 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v2.0 to extract |
| MD5: | 806F6D32670941011893896069BCEDD8 |
| SHA1: | 35707652D59A7BAD8ACE752711A56B393D315342 |
| SHA256: | 8D83CC02582A4549AFA69341E5AD6A82533652D065CCA5114B5CDED5191A7AB2 |
| SSDEEP: | 12288:uyx+95VDkhf9cZ5p1dpPyvwobI8m9MCTIA:v+vVDkR9I3lyHbBm9MCsA |
MALICIOUS
Application loaded dropped or rewritten executable
- explorer.exe (PID: 1632)
- SearchProtocolHost.exe (PID: 3104)
- rundll32.exe (PID: 2844)
- rundll32.exe (PID: 3736)
Runs app for hidden code execution
- explorer.exe (PID: 1632)
SUSPICIOUS
Starts CMD.EXE for commands execution
- explorer.exe (PID: 1632)
INFO
No info indicators.
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 20 |
|---|---|
| ZipBitFlag: | 0x0009 |
| ZipCompression: | Deflated |
| ZipModifyDate: | 2000:01:01 01:00:00 |
| ZipCRC: | 0x1266f8e2 |
| ZipCompressedSize: | 7058 |
| ZipUncompressedSize: | 28665 |
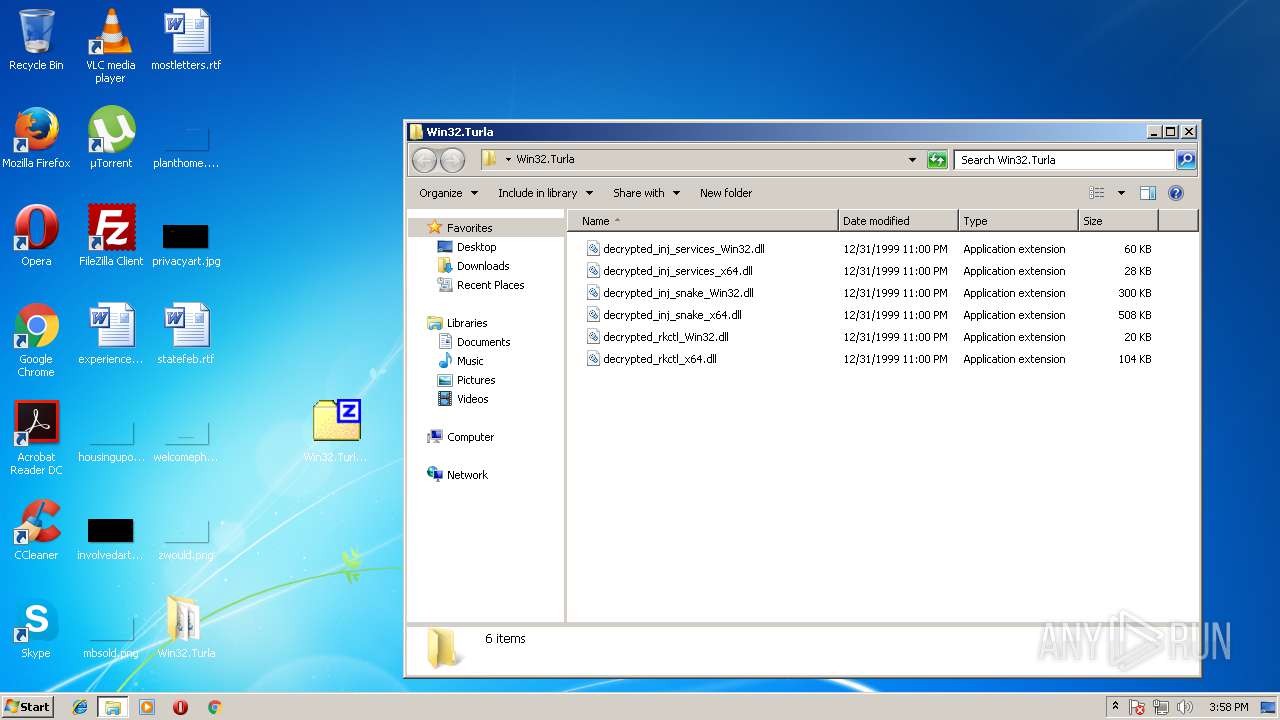
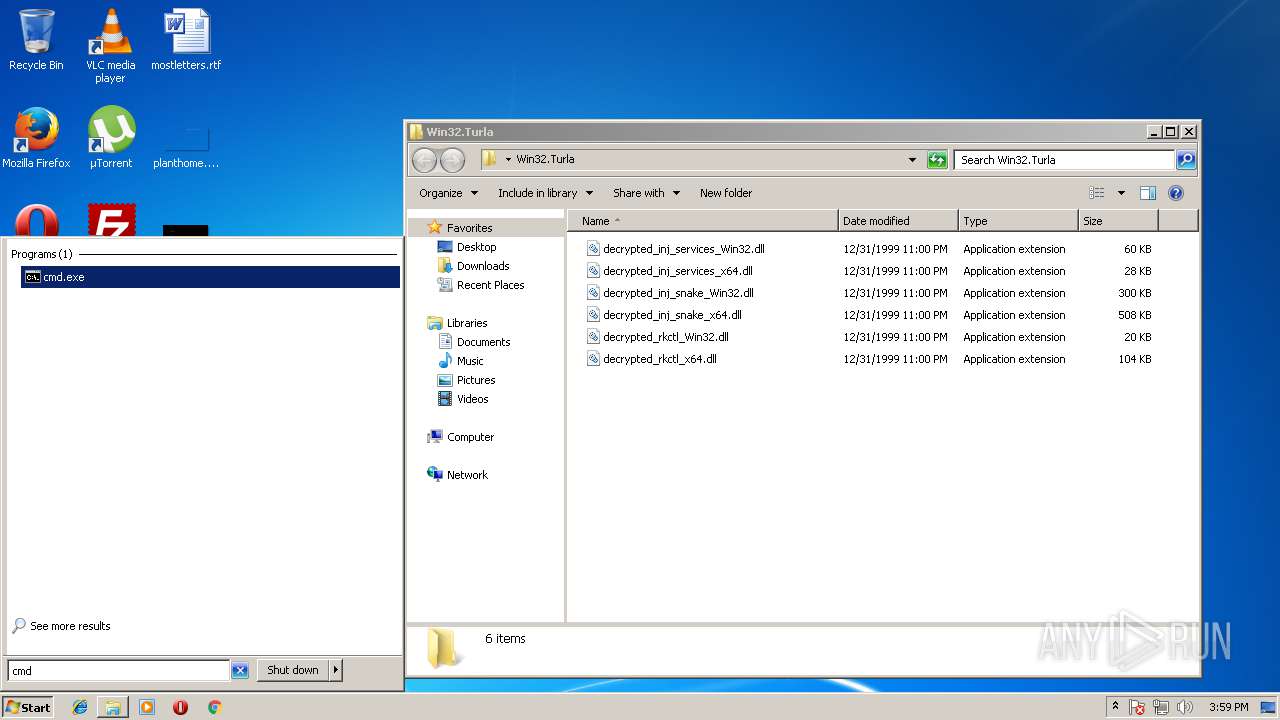
| ZipFileName: | decrypted_inj_services_x64.dll |
Total processes
48
Monitored processes
9
Malicious processes
4
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
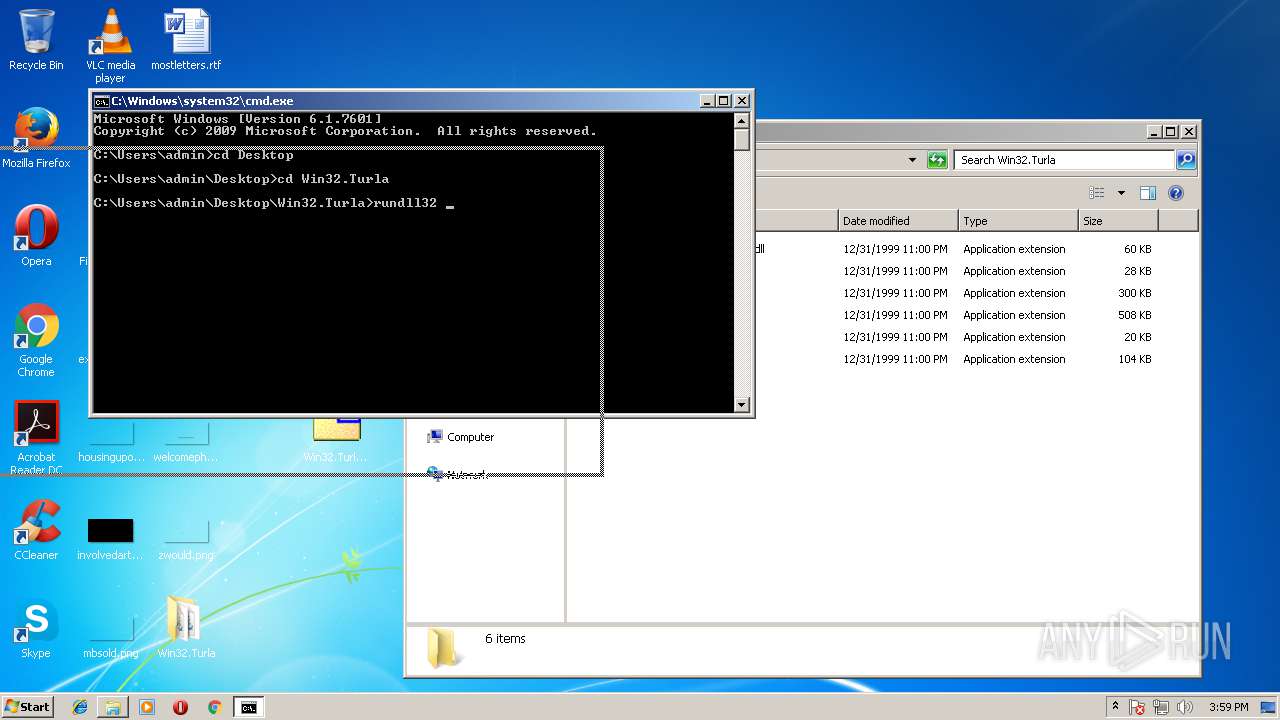
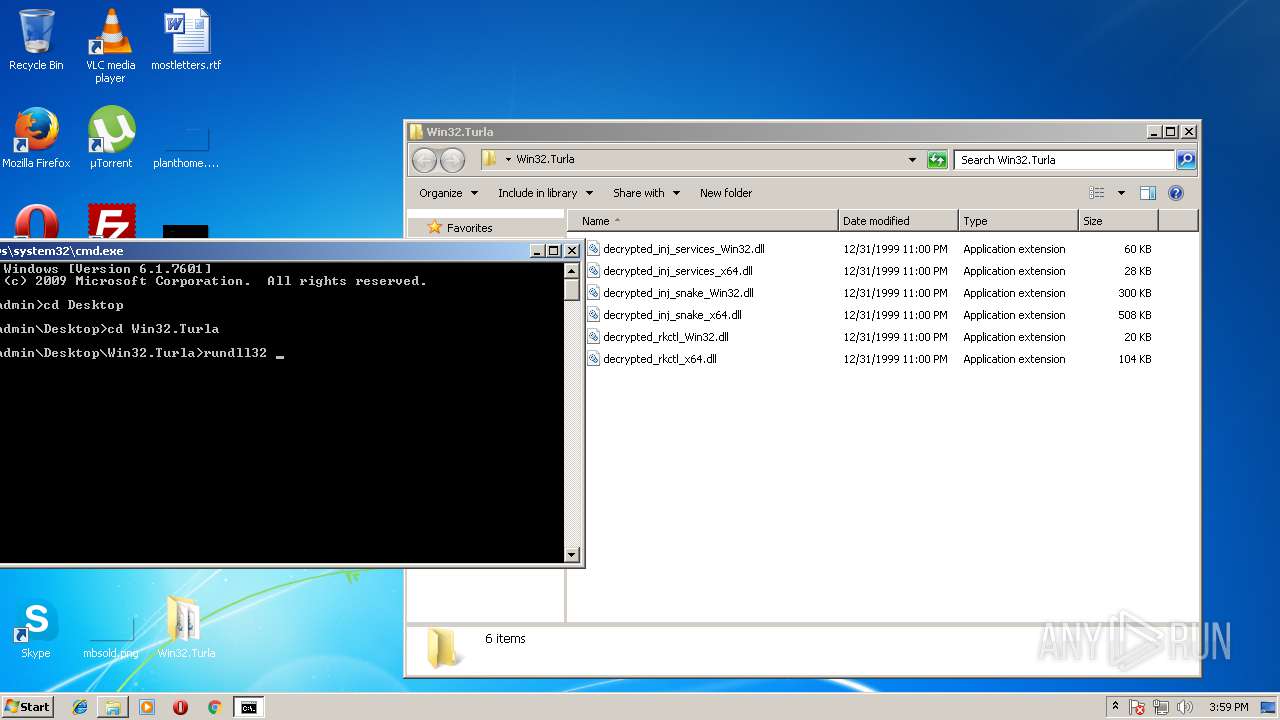
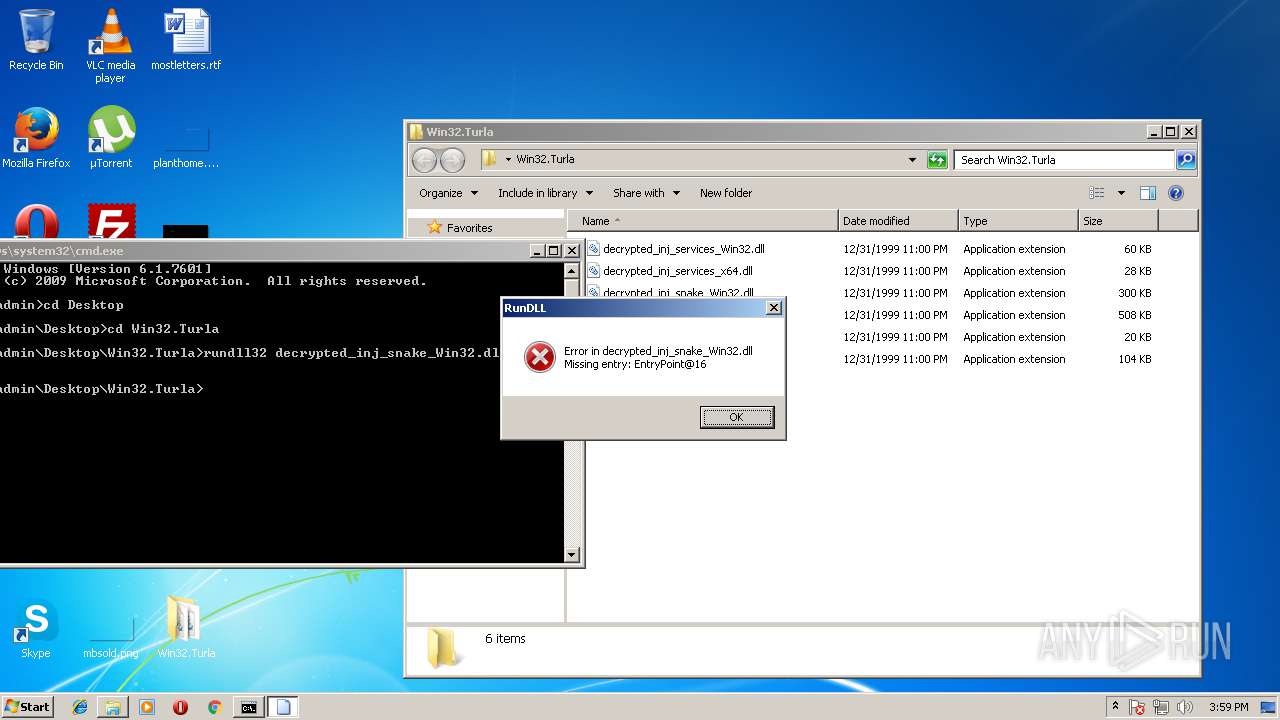
| 608 | "C:\Windows\system32\rundll32.exe" C:\Windows\system32\shell32.dll,OpenAs_RunDLL C:\Users\admin\Desktop\Win32.Turla\decrypted_inj_snake_Win32.dll | C:\Windows\system32\rundll32.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows host process (Rundll32) Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1300 | "C:\Program Files\7-Zip\7zFM.exe" "C:\Users\admin\AppData\Local\Temp\Win32.Turla.zip" | C:\Program Files\7-Zip\7zFM.exe | — | explorer.exe | |||||||||||
User: admin Company: Igor Pavlov Integrity Level: MEDIUM Description: 7-Zip File Manager Exit code: 0 Version: 16.04 Modules
| |||||||||||||||
| 1632 | C:\Windows\Explorer.EXE | C:\Windows\explorer.exe | — | — | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Explorer Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1980 | "C:\Windows\system32\cmd.exe" | C:\Windows\system32\cmd.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 3221225786 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 2640 | "C:\Windows\explorer.exe" | C:\Windows\explorer.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Explorer Exit code: 1 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
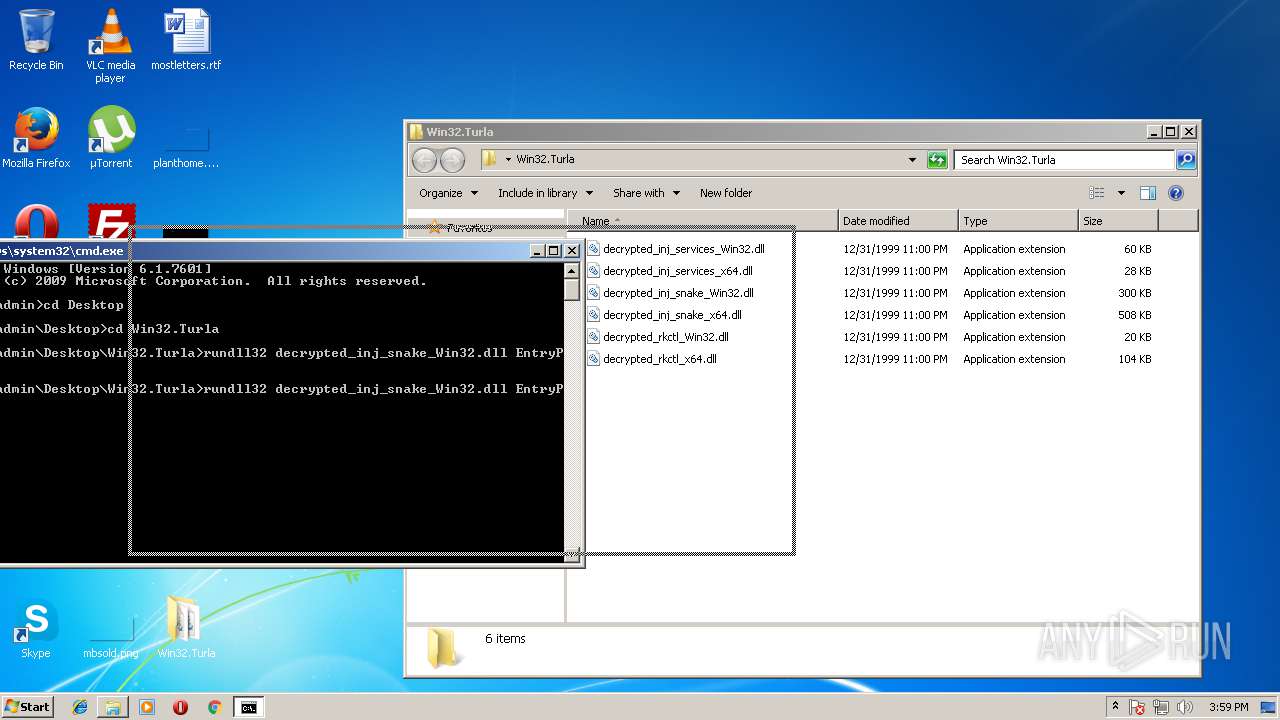
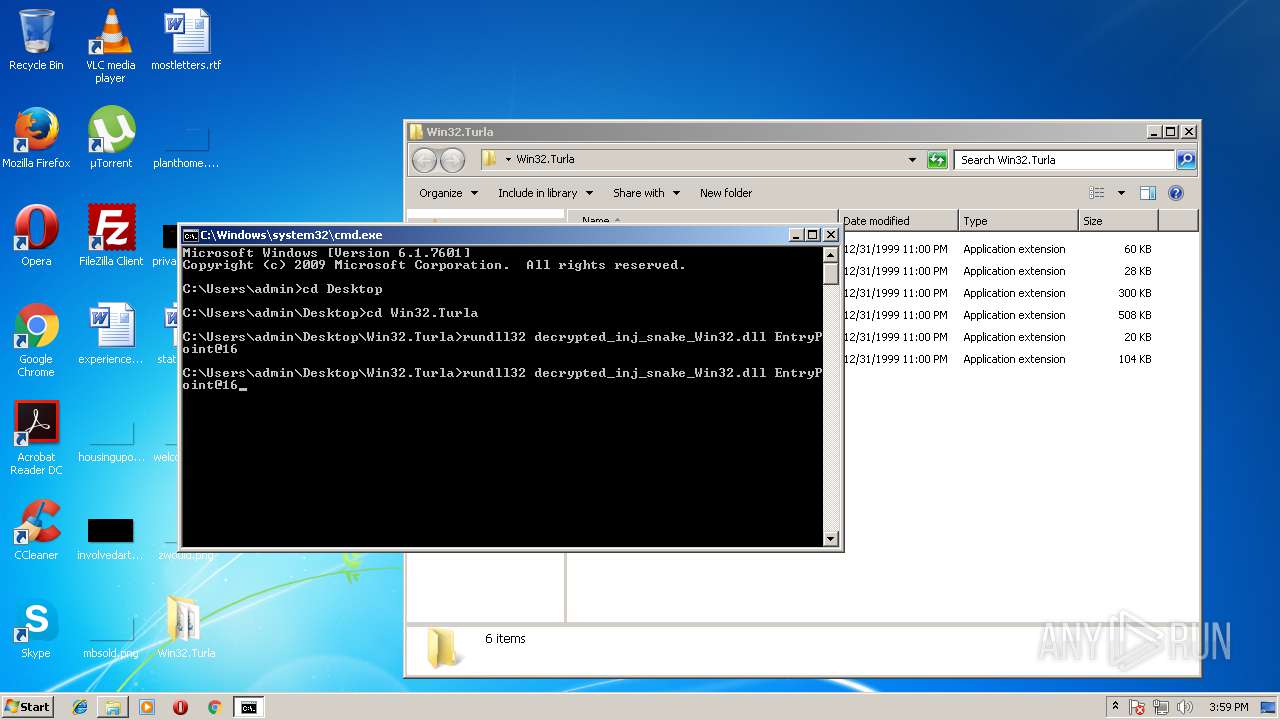
| 2844 | rundll32 decrypted_inj_snake_Win32.dll EntryPoint@16 | C:\Windows\system32\rundll32.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows host process (Rundll32) Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3104 | "C:\Windows\system32\SearchProtocolHost.exe" Global\UsGthrFltPipeMssGthrPipe6_ Global\UsGthrCtrlFltPipeMssGthrPipe6 1 -2147483646 "Software\Microsoft\Windows Search" "Mozilla/4.0 (compatible; MSIE 6.0; Windows NT; MS Search 4.0 Robot)" "C:\ProgramData\Microsoft\Search\Data\Temp\usgthrsvc" "DownLevelDaemon" | C:\Windows\system32\SearchProtocolHost.exe | — | SearchIndexer.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Microsoft Windows Search Protocol Host Exit code: 0 Version: 7.00.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3736 | rundll32 decrypted_inj_snake_Win32.dll EntryPoint@16 | C:\Windows\system32\rundll32.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows host process (Rundll32) Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3956 | "C:\Program Files\7-Zip\7zG.exe" x -o"C:\Users\admin\Desktop\Win32.Turla\" -spe -slp- -an -ai#7zMap17117:80:7zEvent3234 | C:\Program Files\7-Zip\7zG.exe | explorer.exe | ||||||||||||
User: admin Company: Igor Pavlov Integrity Level: MEDIUM Description: 7-Zip GUI Exit code: 0 Version: 16.04 Modules
| |||||||||||||||
Total events
4 036
Read events
3 512
Write events
524
Delete events
0
Modification events
| (PID) Process: | (1300) 7zFM.exe | Key: | HKEY_CURRENT_USER\Software\7-Zip\FM |
| Operation: | write | Name: | FolderShortcuts |
Value: | |||
| (PID) Process: | (1300) 7zFM.exe | Key: | HKEY_CURRENT_USER\Software\7-Zip\FM |
| Operation: | write | Name: | FolderHistory |
Value: 43003A005C00550073006500720073005C00610064006D0069006E005C0041007000700044006100740061005C004C006F00630061006C005C00540065006D0070005C00570069006E00330032002E005400750072006C0061002E007A00690070005C006400650063007200790070007400650064005F0069006E006A005F00730065007200760069006300650073005F00570069006E00330032002E0064006C006C005C00000043003A005C00550073006500720073005C00610064006D0069006E005C0041007000700044006100740061005C004C006F00630061006C005C00540065006D0070005C00570069006E00330032002E005400750072006C0061002E007A00690070005C000000 | |||
| (PID) Process: | (1300) 7zFM.exe | Key: | HKEY_CURRENT_USER\Software\7-Zip\FM |
| Operation: | write | Name: | PanelPath0 |
Value: C:\Users\admin\AppData\Local\Temp\ | |||
| (PID) Process: | (1300) 7zFM.exe | Key: | HKEY_CURRENT_USER\Software\7-Zip\FM |
| Operation: | write | Name: | FlatViewArc0 |
Value: 0 | |||
| (PID) Process: | (1300) 7zFM.exe | Key: | HKEY_CURRENT_USER\Software\7-Zip\FM |
| Operation: | write | Name: | PanelPath1 |
Value: | |||
| (PID) Process: | (1300) 7zFM.exe | Key: | HKEY_CURRENT_USER\Software\7-Zip\FM |
| Operation: | write | Name: | FlatViewArc1 |
Value: 0 | |||
| (PID) Process: | (1300) 7zFM.exe | Key: | HKEY_CURRENT_USER\Software\7-Zip\FM |
| Operation: | write | Name: | ListMode |
Value: 771 | |||
| (PID) Process: | (1300) 7zFM.exe | Key: | HKEY_CURRENT_USER\Software\7-Zip\FM |
| Operation: | write | Name: | Position |
Value: 6400000021000000240400001602000000000000 | |||
| (PID) Process: | (1300) 7zFM.exe | Key: | HKEY_CURRENT_USER\Software\7-Zip\FM |
| Operation: | write | Name: | Panels |
Value: 0100000000000000DA010000 | |||
| (PID) Process: | (1300) 7zFM.exe | Key: | HKEY_CURRENT_USER\Software\7-Zip\FM\Columns |
| Operation: | write | Name: | 7-Zip.PE |
Value: 0100000004000000010000000400000001000000A00000000700000001000000640000000800000001000000640000004D00000001000000640000002F00000001000000640000002400000001000000640000003000000001000000640000001F0000000100000064000000200000000100000064000000 | |||
Executable files
6
Suspicious files
1
Text files
0
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3956 | 7zG.exe | C:\Users\admin\Desktop\Win32.Turla\decrypted_inj_snake_x64.dll | executable | |
MD5:2B47AD7DF9902AAA19474723064EE76F | SHA256:152C867667517A0EC0B3231BEECE8FF46FF954BFC2493CA3BDFDFC6EA6B1BDE9 | |||
| 1632 | explorer.exe | C:\Users\admin\Desktop\Win32.Turla.zip | compressed | |
MD5:806F6D32670941011893896069BCEDD8 | SHA256:8D83CC02582A4549AFA69341E5AD6A82533652D065CCA5114B5CDED5191A7AB2 | |||
| 3956 | 7zG.exe | C:\Users\admin\Desktop\Win32.Turla\decrypted_inj_services_x64.dll | executable | |
MD5:5F8F3CF46719AFA7EB5F761CDD18B63D | SHA256:A15C351B940046BC80C8D0A69B8D5F6C4198CB20F68AD830DC3B1036BA8D34E4 | |||
| 3956 | 7zG.exe | C:\Users\admin\Desktop\Win32.Turla\decrypted_inj_snake_Win32.dll | executable | |
MD5:F57C84E22E9E6EAA6CBD9730D7C652DC | SHA256:564EE49A4703DE53BFA1BDC6A5B71F111EA23E38A6FF441E0BF2FF7C28D95525 | |||
| 3956 | 7zG.exe | C:\Users\admin\Desktop\Win32.Turla\decrypted_rkctl_Win32.dll | executable | |
MD5:3C1A8991E96F4C56AE3E90FB6F0AE679 | SHA256:9611D0B1837E933B9D938E19791B757AA56669EC75B8FD671BDD1371EEDE03BB | |||
| 3956 | 7zG.exe | C:\Users\admin\Desktop\Win32.Turla\decrypted_rkctl_x64.dll | executable | |
MD5:B46C792C8E051BC5C9D4CECAB96E4C30 | SHA256:4C8B2E001DBF9E8B285C79514319E0A14DBB839998DD4D643D51FB11767D0CF9 | |||
| 3956 | 7zG.exe | C:\Users\admin\Desktop\Win32.Turla\decrypted_inj_services_Win32.dll | executable | |
MD5:AAC56BAFF4BE3DB02378F11B9844DCB5 | SHA256:099AD10B55E74E1B99424D8E739107534004BA5B1E6C051CF8B942ED32DABCA6 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
0
DNS requests
0
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report