| File name: | KMS_Suite.v9.EN.rar |
| Full analysis: | https://app.any.run/tasks/062646af-0c01-4178-9b41-8705879e46af |
| Verdict: | Malicious activity |
| Analysis date: | August 01, 2023, 23:29:34 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/x-rar |
| File info: | RAR archive data, v5 |
| MD5: | 985DDBCD777D4C8D55C30FE03A35CA56 |
| SHA1: | BB62C4A4EFE68C776EE715BC4C050300E02C946C |
| SHA256: | 8D792A7C132D0EBF6384F1C16D34E325B1E1CC90D6A8A90F62F972B7CAA80391 |
| SSDEEP: | 6144:d4rRk56Nzfm+T/PZYHcVc70WA8OoEdgCw9kYE/lOL9EYmAn:aRSkC+z2HcuQJx/G9jm2 |
MALICIOUS
Starts Visual C# compiler
- powershell.exe (PID: 620)
Application was dropped or rewritten from another process
- center.exe (PID: 2056)
- DisableX.exe (PID: 2520)
SUSPICIOUS
Starts POWERSHELL.EXE for commands execution
- cmd.exe (PID: 896)
- cmd.exe (PID: 3284)
Uses .NET C# to load dll
- powershell.exe (PID: 620)
The process bypasses the loading of PowerShell profile settings
- cmd.exe (PID: 896)
- cmd.exe (PID: 3284)
Probably obfuscated PowerShell command line is found
- cmd.exe (PID: 896)
Possibly malicious use of IEX has been detected
- cmd.exe (PID: 896)
Executable content was dropped or overwritten
- expand.exe (PID: 2468)
- csc.exe (PID: 3932)
- xcopy.exe (PID: 2192)
Executing commands from ".cmd" file
- cmd.exe (PID: 896)
Application launched itself
- cmd.exe (PID: 896)
- cmd.exe (PID: 3284)
Reads the Internet Settings
- cmd.exe (PID: 3284)
- wscript.exe (PID: 1736)
- WMIC.exe (PID: 3276)
- WMIC.exe (PID: 3744)
- WMIC.exe (PID: 2816)
Starts CMD.EXE for commands execution
- cmd.exe (PID: 896)
- cmd.exe (PID: 3284)
The process executes VB scripts
- cmd.exe (PID: 3284)
Uses WMIC.EXE to obtain operating system information
- cmd.exe (PID: 2476)
- cmd.exe (PID: 3936)
- cmd.exe (PID: 3900)
Using 'findstr.exe' to search for text patterns in files and output
- cmd.exe (PID: 3284)
INFO
Manual execution by a user
- cmd.exe (PID: 896)
Checks supported languages
- mode.com (PID: 2028)
- csc.exe (PID: 3932)
- cvtres.exe (PID: 4032)
- mode.com (PID: 4064)
- center.exe (PID: 2056)
- mode.com (PID: 3212)
- DisableX.exe (PID: 2520)
- mode.com (PID: 3548)
- mode.com (PID: 3016)
The process checks LSA protection
- csc.exe (PID: 3932)
- cvtres.exe (PID: 4032)
- WMIC.exe (PID: 3276)
- WMIC.exe (PID: 2816)
- WMIC.exe (PID: 3744)
Create files in a temporary directory
- cvtres.exe (PID: 4032)
- csc.exe (PID: 3932)
- xcopy.exe (PID: 2192)
- expand.exe (PID: 2468)
Reads the machine GUID from the registry
- csc.exe (PID: 3932)
- cvtres.exe (PID: 4032)
The executable file from the user directory is run by the CMD process
- center.exe (PID: 2056)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .rar | | | RAR compressed archive (v5.0) (61.5) |
|---|---|---|
| .rar | | | RAR compressed archive (gen) (38.4) |
Total processes
79
Monitored processes
40
Malicious processes
6
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 620 | powershell -nop -c $f=[IO.File]::ReadAllText($env:0)-split':bat2file\:.*';iex($f[1]); X(1) | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows PowerShell Exit code: 0 Version: 10.0.14409.1005 (rs1_srvoob.161208-1155) Modules
| |||||||||||||||
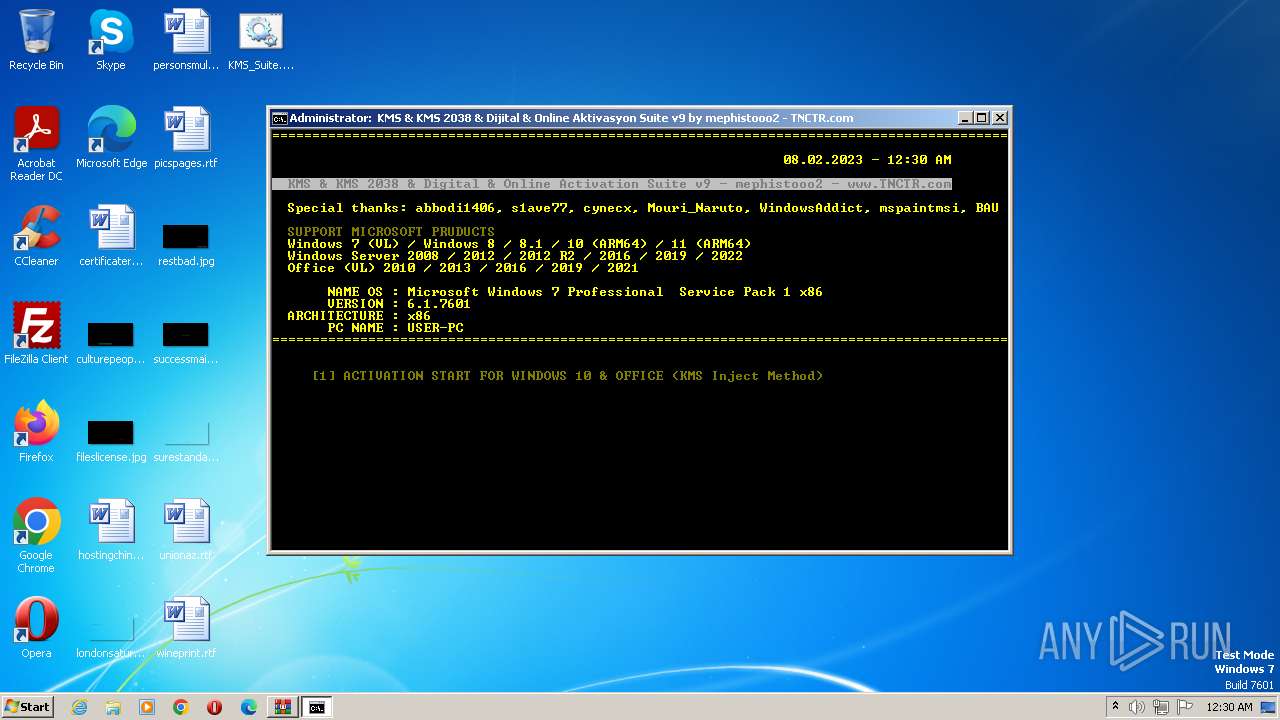
| 896 | "C:\Windows\System32\cmd.exe" /C "C:\Users\admin\Desktop\KMS_Suite.v9.EN.cmd" | C:\Windows\System32\cmd.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 1108 | findstr /v /a:7 /R "^f7f81a39-5f63-5b42-9efd-1f13b5431005quot; " [4] WINDOWS & OFFICE ACTIVATION STATUS CHECK" nul | C:\Windows\System32\findstr.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Find String (QGREP) Utility Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1600 | cmd /v:on /c echo(^!param^! | C:\Windows\System32\cmd.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 1640 | findstr /v /a:6 /R "^f7f81a39-5f63-5b42-9efd-1f13b5431005quot; " [1] ACTIVATION START FOR WINDOWS 10 & OFFICE (KMS Inject Method)" nul | C:\Windows\System32\findstr.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Find String (QGREP) Utility Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1736 | "C:\Windows\System32\WScript.exe" "C:\Users\admin\AppData\Local\Temp\7660\bin\DisableX.vbs" | C:\Windows\System32\wscript.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Microsoft ® Windows Based Script Host Exit code: 0 Version: 5.8.7600.16385 Modules
| |||||||||||||||
| 1820 | findstr /v /a:4 /R "^f7f81a39-5f63-5b42-9efd-1f13b5431005quot; " [6] EXIT" nul | C:\Windows\System32\findstr.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Find String (QGREP) Utility Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1868 | choice /C:123456 /N /M "YOUR CHOICE :" | C:\Windows\System32\choice.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Offers the user a choice Exit code: 3 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2028 | mode con cols=78 lines=3 | C:\Windows\System32\mode.com | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: DOS Device MODE Utility Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2056 | center.exe kF5nJ4D92hfOpc8 | C:\Users\admin\AppData\Local\Temp\7660\bin\center.exe | — | cmd.exe | |||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
Total events
5 159
Read events
5 133
Write events
26
Delete events
0
Modification events
| (PID) Process: | (2972) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\178\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (2972) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\virtio_ivshmem_master_build.zip | |||
| (PID) Process: | (2972) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\Win7-KB3191566-x86.zip | |||
| (PID) Process: | (2972) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Desktop\phacker.zip | |||
| (PID) Process: | (2972) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (2972) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (2972) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (2972) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (3284) cmd.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (3284) cmd.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
Executable files
28
Suspicious files
8
Text files
46
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2972 | WinRAR.exe | C:\Users\admin\Desktop\KMS_Suite.v9.EN.cmd | text | |
MD5:F9906448D778C93D1B96F87E92E9B436 | SHA256:54C33E9C26EF68F0521CB6D6A416FCD2A6C22537D49ADE62DB6935CCC4129927 | |||
| 620 | powershell.exe | C:\Users\admin\AppData\Local\Temp\upvfgn0e.cmdline | text | |
MD5:33EEF255057DC4DD34D89B0227047C77 | SHA256:11E03977AD4EFD2AA13604234C0E2279D935F071BBFBF88580D9003771DDC536 | |||
| 4032 | cvtres.exe | C:\Users\admin\AppData\Local\Temp\RESB409.tmp | binary | |
MD5:46FADE9A871F85B51D58EE07C3486052 | SHA256:273B403C67C715C18DB57A1ED1F8AF4BA21C900AFBBB471368CC758BE3EF4438 | |||
| 620 | powershell.exe | C:\Users\admin\AppData\Local\Temp\upvfgn0e.0.cs | text | |
MD5:047F0CF592670E8FCA358F12E4CD5A89 | SHA256:32E77D9085AD9EA0FD1EB5A9556E29CB42F5D3016CCF9853F3C39D358F479978 | |||
| 3932 | csc.exe | C:\Users\admin\AppData\Local\Temp\CSC7C4C80CBEC8E4D64A72DAF288DFE9EF.TMP | binary | |
MD5:E81F9EFA8884F7CF35C0B107E31218D8 | SHA256:94D72360481D58AB66E7BD9E96C30F51469D7407FF45225FCDB4814B8BF7EDA8 | |||
| 620 | powershell.exe | C:\Users\admin\AppData\Local\Temp\1 | compressed | |
MD5:2F3B771C22DB25813A4530B5BAE62636 | SHA256:9B6B0BDEDBC8B408D93F5FC4FC69605CE6547894D9B0A263920CD8911D2B44B4 | |||
| 2468 | expand.exe | C:\Users\admin\AppData\Local\Temp\KMS_Suite\bin\DisableX.exe | executable | |
MD5:00C9837407663587C69DF18793248D52 | SHA256:09933212238BC7D0CCE57469F9927C0325D5670B21FC7787428574C4A52E5F6D | |||
| 2468 | expand.exe | C:\Users\admin\AppData\Local\Temp\KMS_Suite\bin\Digital\OEM_Digital\$OEM$\$\Setup\Scripts\SETUPCOMPLETE.cmd | text | |
MD5:90A53A1DA9510C250BA348F06B3CDC50 | SHA256:3541AF0D0A371C198A15383364B53DAAB8346D8D4F3ED25C6C9C562D83F98421 | |||
| 2468 | expand.exe | C:\Users\admin\AppData\Local\Temp\KMS_Suite\KMS_Suite.cmd | text | |
MD5:1F6C48CA9B559F73A8CD4D147E0BB5AD | SHA256:85FD9262766F7C4E3D7696FF816F9DB88C81A0988C08565E5309F5A096BEE7B5 | |||
| 2468 | expand.exe | C:\Users\admin\AppData\Local\Temp\KMS_Suite\bin\center.exe | executable | |
MD5:0A847EAFDDC4529388E1A1B291354CF8 | SHA256:69533D9B66B840B4764F901CD6A502D12453B604617A841F4C2C602FC87DF255 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
4
DNS requests
0
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
2640 | svchost.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
1088 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |