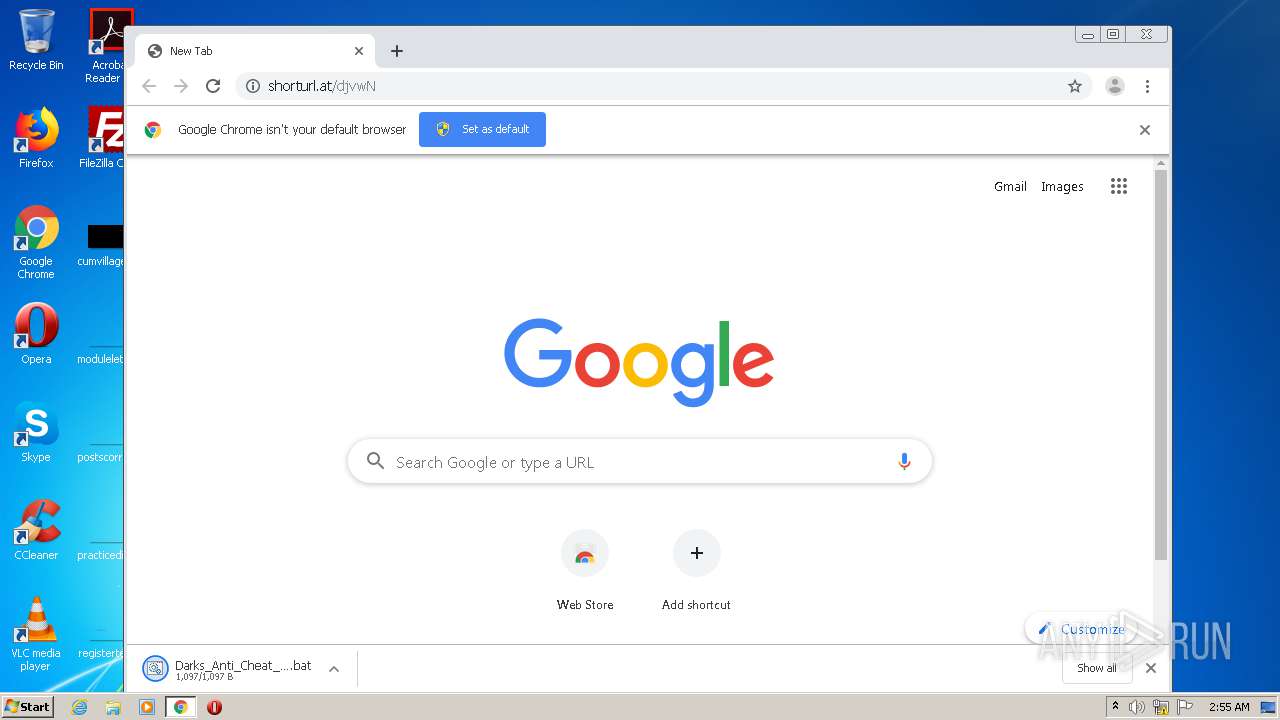
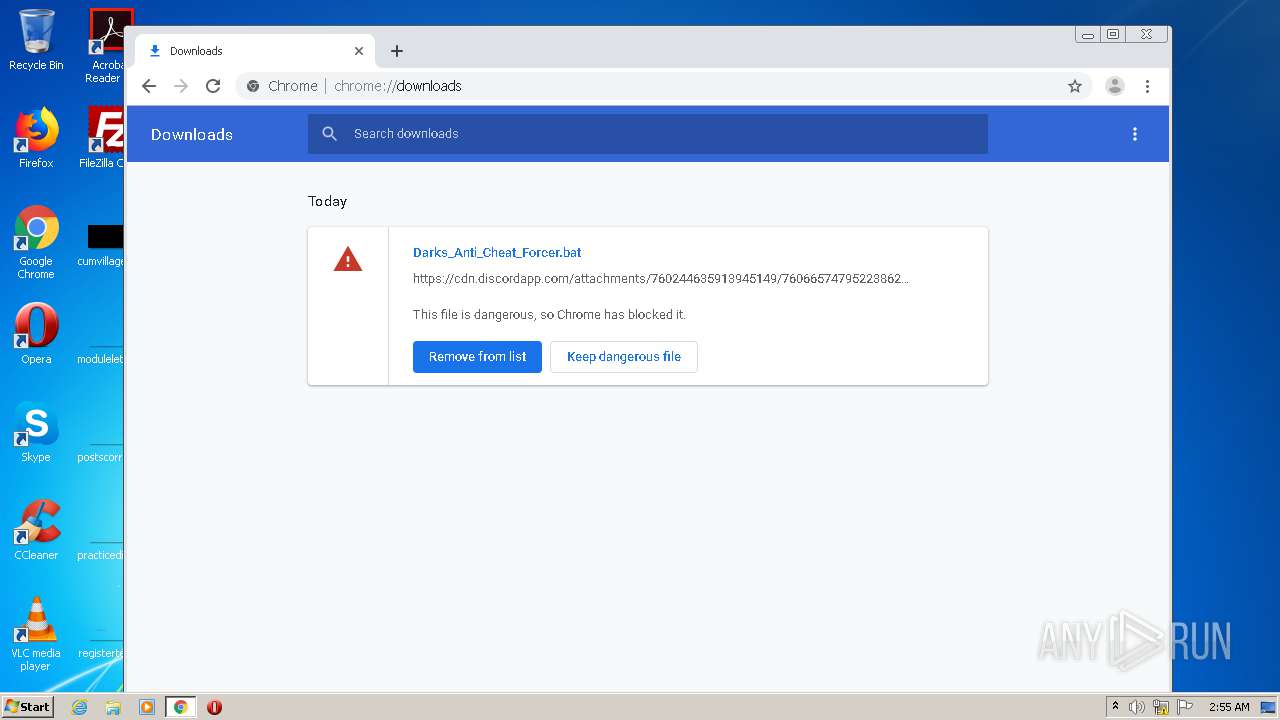
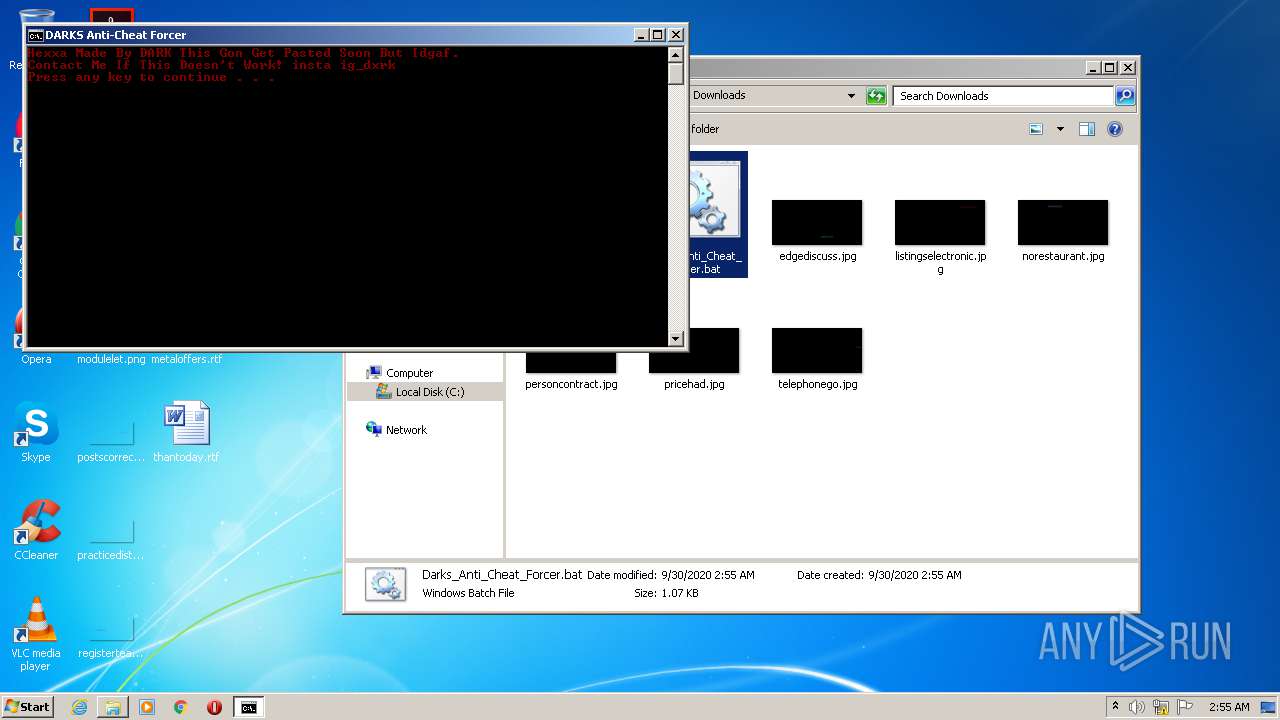
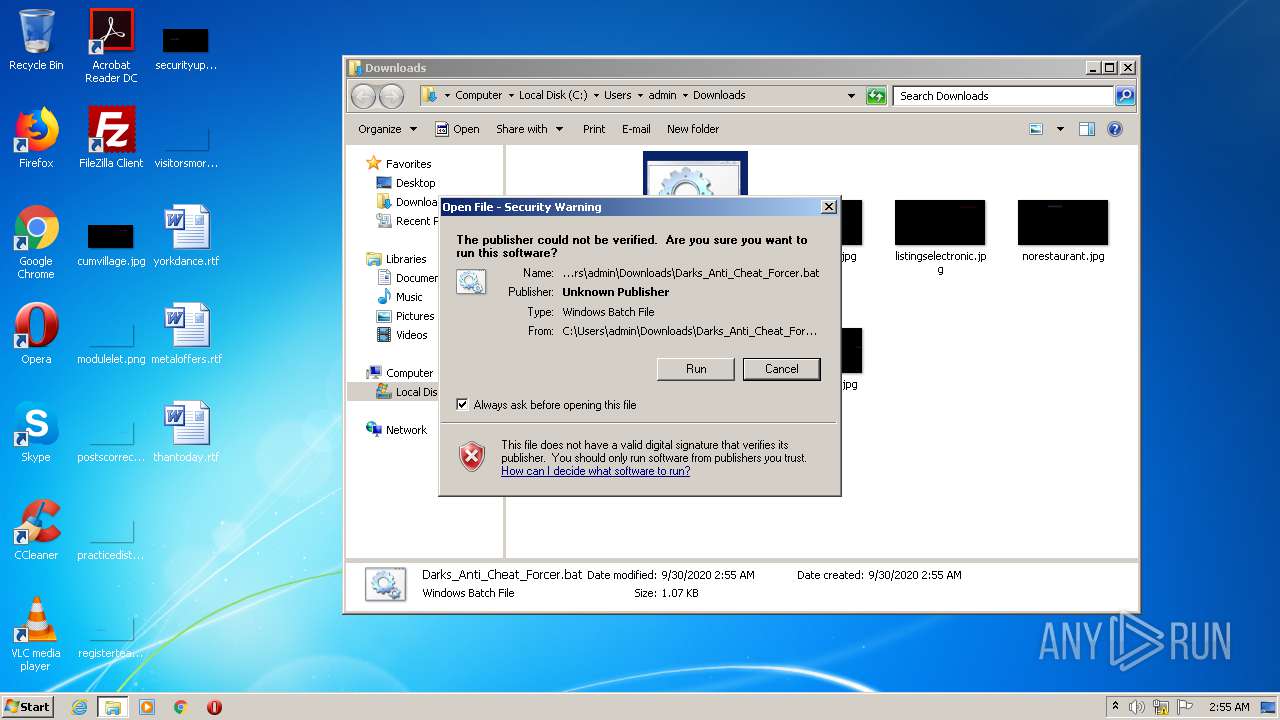
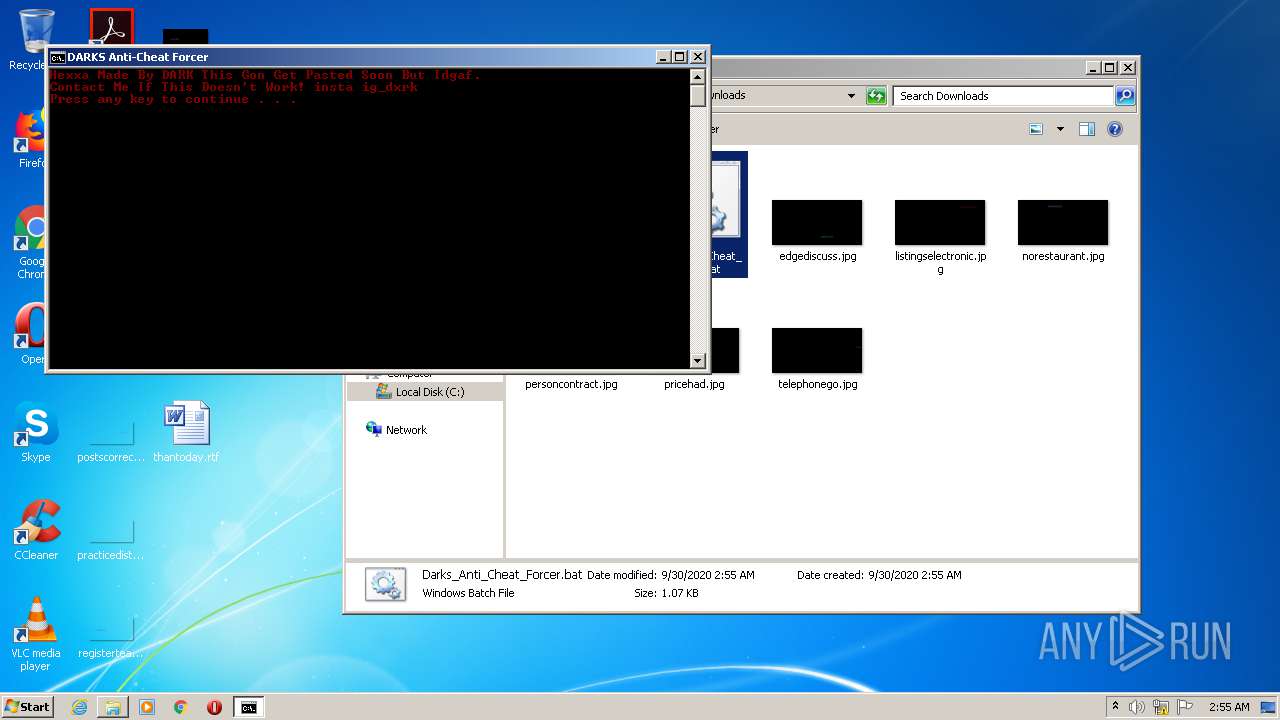
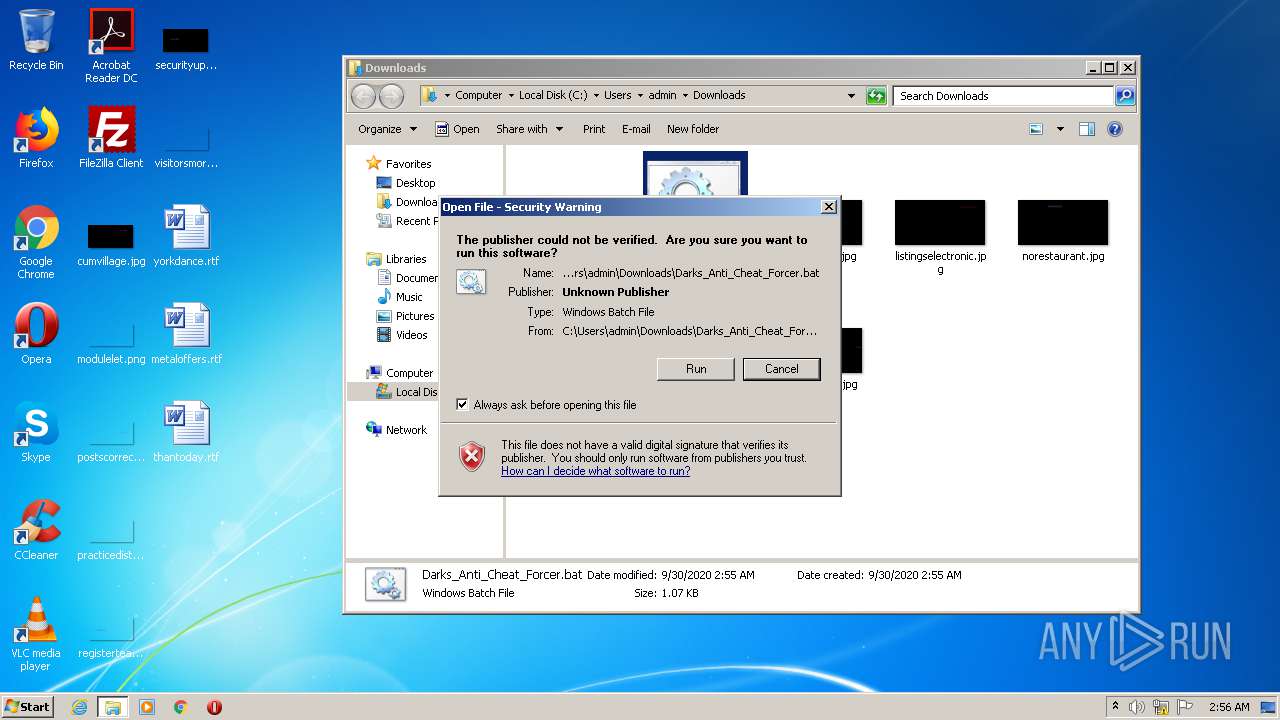
| File name: | Darks_Anti_Cheat_Forcer.bat |
| Full analysis: | https://app.any.run/tasks/0edc580c-6a63-4166-a485-8bb3e8c85a6b |
| Verdict: | Malicious activity |
| Analysis date: | September 30, 2020, 01:53:45 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | text/plain |
| File info: | ASCII text, with CRLF line terminators |
| MD5: | 2DF48BFA5F454CC697A1E624B038C4F3 |
| SHA1: | 1E9384ACF4893FFFBCC79E38B695F40F6D656399 |
| SHA256: | 8D766D27B96257EDCB5C1300C7D965C91C52CB6F8D27894A1C913F07E27506F3 |
| SSDEEP: | 12:89sIdgXgQWEE7ZUMvxMUMUWUMU4xUMU4Q9ztGcbIAUCiByAuNB3DnVeMSBx4G9tG:8TgwQwp9zrzNUaIFvByRbz6rvVEorvBM |
MALICIOUS
No malicious indicators.SUSPICIOUS
Uses TASKKILL.EXE to kill process
- cmd.exe (PID: 2896)
- cmd.exe (PID: 3656)
- cmd.exe (PID: 604)
- cmd.exe (PID: 3356)
INFO
Application launched itself
- chrome.exe (PID: 4032)
Reads the hosts file
- chrome.exe (PID: 4032)
- chrome.exe (PID: 2112)
Reads settings of System Certificates
- chrome.exe (PID: 2112)
Manual execution by user
- cmd.exe (PID: 3656)
- chrome.exe (PID: 4032)
- cmd.exe (PID: 604)
- cmd.exe (PID: 3356)
Reads Internet Cache Settings
- chrome.exe (PID: 4032)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
82
Monitored processes
38
Malicious processes
0
Suspicious processes
2
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 184 | taskkill /f /im FortniteClient-Win64-Shipping_BE | C:\Windows\system32\taskkill.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Terminates Processes Exit code: 128 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 604 | cmd /c ""C:\Users\admin\Downloads\Darks_Anti_Cheat_Forcer.bat" " | C:\Windows\system32\cmd.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 255 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 700 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=gpu-process --field-trial-handle=1020,8019145158480000674,12942599980220728279,131072 --enable-features=PasswordImport --disable-gpu-sandbox --use-gl=disabled --gpu-preferences=KAAAAAAAAADgAAAgAQAAAAAAAAAAAGAAAAAAAAAAAAAIAAAAAAAAACgAAAAEAAAAIAAAAAAAAAAoAAAAAAAAADAAAAAAAAAAOAAAAAAAAAAQAAAAAAAAAAAAAAAFAAAAEAAAAAAAAAAAAAAABgAAABAAAAAAAAAAAQAAAAUAAAAQAAAAAAAAAAEAAAAGAAAA --service-request-channel-token=6608482067373091398 --mojo-platform-channel-handle=3200 /prefetch:2 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 892 | taskkill /f /im FortniteLauncher.exe | C:\Windows\system32\taskkill.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Terminates Processes Exit code: 128 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 988 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=1020,8019145158480000674,12942599980220728279,131072 --enable-features=PasswordImport --disable-gpu-compositing --lang=en-US --enable-offline-auto-reload --enable-offline-auto-reload-visible-only --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --service-request-channel-token=12836800910178525282 --renderer-client-id=11 --no-v8-untrusted-code-mitigations --mojo-platform-channel-handle=3652 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 1492 | taskkill /f /im FortniteLauncher.exe | C:\Windows\system32\taskkill.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Terminates Processes Exit code: 128 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1780 | taskkill /f /im FortniteClient-Win64-Shipping_EAC | C:\Windows\system32\taskkill.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Terminates Processes Exit code: 128 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1920 | taskkill /f /im FortniteLauncher.exe | C:\Windows\system32\taskkill.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Terminates Processes Exit code: 128 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1932 | taskkill /f /im FortniteClient-Win64-Shipping_EAC | C:\Windows\system32\taskkill.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Terminates Processes Exit code: 128 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2028 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=1020,8019145158480000674,12942599980220728279,131072 --enable-features=PasswordImport --lang=en-US --enable-offline-auto-reload --enable-offline-auto-reload-visible-only --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --service-request-channel-token=12479223386062856491 --renderer-client-id=7 --no-v8-untrusted-code-mitigations --mojo-platform-channel-handle=2344 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
Total events
764
Read events
666
Write events
94
Delete events
4
Modification events
| (PID) Process: | (4032) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\BLBeacon |
| Operation: | write | Name: | failed_count |
Value: 0 | |||
| (PID) Process: | (4032) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\BLBeacon |
| Operation: | write | Name: | state |
Value: 2 | |||
| (PID) Process: | (4032) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\ThirdParty |
| Operation: | write | Name: | StatusCodes |
Value: | |||
| (PID) Process: | (4032) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\ThirdParty |
| Operation: | write | Name: | StatusCodes |
Value: 01000000 | |||
| (PID) Process: | (4032) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\BLBeacon |
| Operation: | write | Name: | state |
Value: 1 | |||
| (PID) Process: | (3144) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\BrowserExitCodes |
| Operation: | write | Name: | 4032-13245904505447250 |
Value: 259 | |||
| (PID) Process: | (4032) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Update\ClientState\{8A69D345-D564-463c-AFF1-A69D9E530F96} |
| Operation: | write | Name: | dr |
Value: 1 | |||
| (PID) Process: | (4032) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome |
| Operation: | write | Name: | UsageStatsInSample |
Value: 0 | |||
| (PID) Process: | (4032) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\BrowserExitCodes |
| Operation: | delete value | Name: | 3228-13245745346152343 |
Value: 0 | |||
| (PID) Process: | (4032) chrome.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Google\Update\ClientStateMedium\{8A69D345-D564-463C-AFF1-A69D9E530F96} |
| Operation: | write | Name: | usagestats |
Value: 0 | |||
Executable files
0
Suspicious files
22
Text files
89
Unknown types
10
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 4032 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\BrowserMetrics\BrowserMetrics-5F73E579-FC0.pma | — | |
MD5:— | SHA256:— | |||
| 4032 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\ce05fced-53ed-4fcd-a56c-e47dab5a1e23.tmp | — | |
MD5:— | SHA256:— | |||
| 4032 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\data_reduction_proxy_leveldb\000046.dbtmp | — | |
MD5:— | SHA256:— | |||
| 4032 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\Sync Data\LevelDB\LOG.old | text | |
MD5:— | SHA256:— | |||
| 4032 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\Site Characteristics Database\LOG.old | text | |
MD5:— | SHA256:— | |||
| 4032 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\BudgetDatabase\LOG.old | text | |
MD5:— | SHA256:— | |||
| 4032 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\Feature Engagement Tracker\AvailabilityDB\LOG.old | — | |
MD5:— | SHA256:— | |||
| 4032 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\Site Characteristics Database\LOG.old~RF3cb707.TMP | text | |
MD5:— | SHA256:— | |||
| 4032 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\data_reduction_proxy_leveldb\LOG.old | text | |
MD5:— | SHA256:— | |||
| 4032 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\Sync Data\LevelDB\LOG.old~RF3cb6f8.TMP | text | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
1
TCP/UDP connections
14
DNS requests
12
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
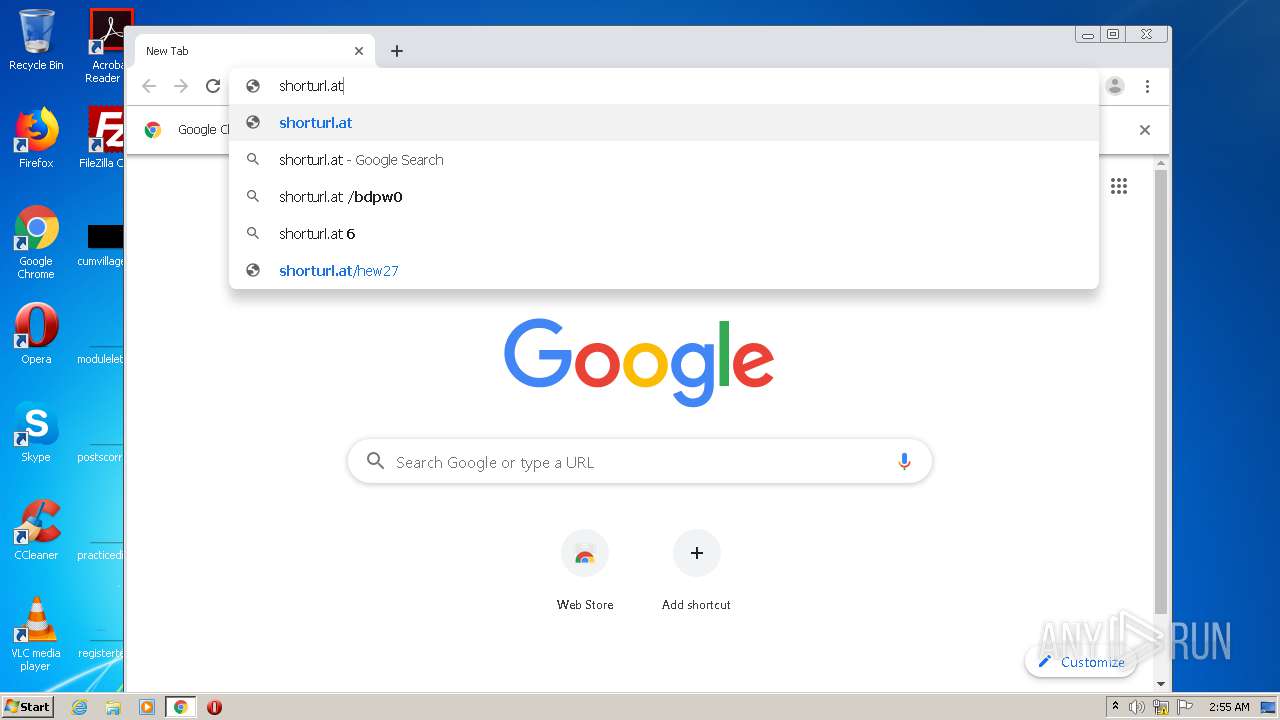
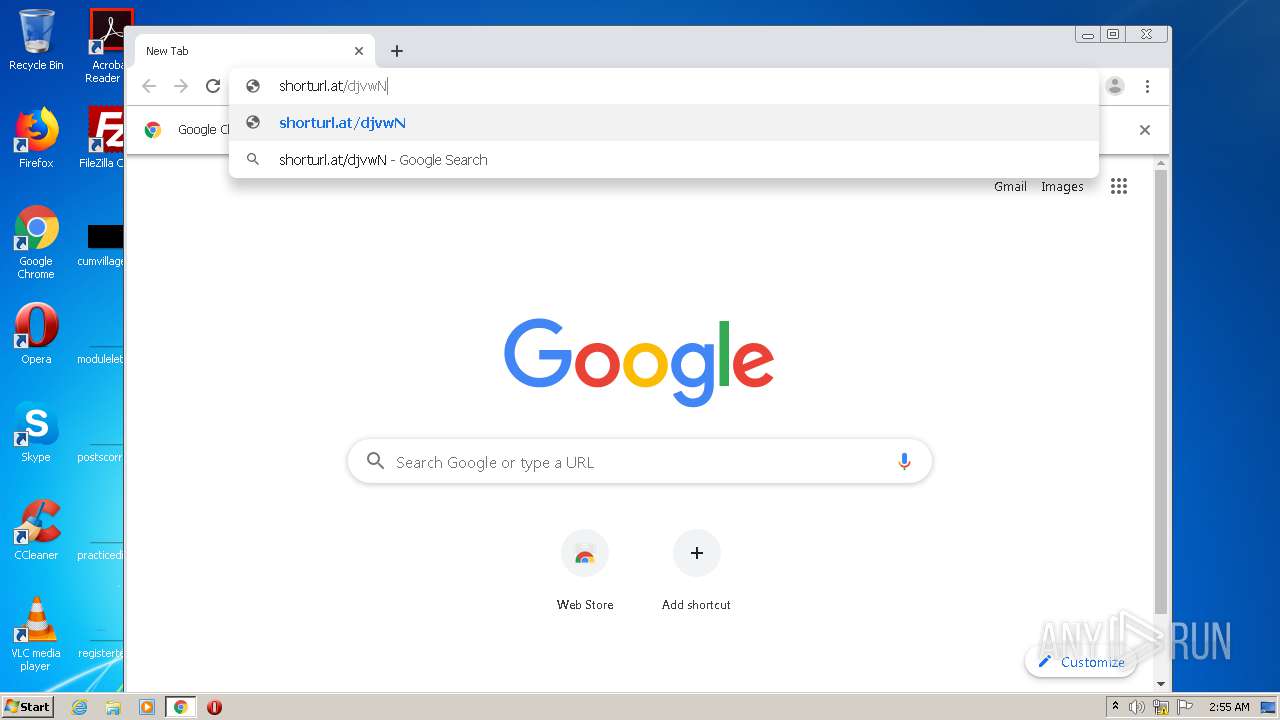
2112 | chrome.exe | GET | 301 | 104.24.116.24:80 | http://shorturl.at/djvwN | US | html | 237 b | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
2112 | chrome.exe | 142.250.74.195:443 | clientservices.googleapis.com | Google Inc. | US | whitelisted |
2112 | chrome.exe | 172.217.22.77:443 | accounts.google.com | Google Inc. | US | whitelisted |
2112 | chrome.exe | 216.58.208.36:443 | www.google.com | Google Inc. | US | whitelisted |
2112 | chrome.exe | 172.217.21.202:443 | fonts.googleapis.com | Google Inc. | US | whitelisted |
2112 | chrome.exe | 216.58.208.46:443 | clients2.google.com | Google Inc. | US | whitelisted |
2112 | chrome.exe | 104.24.116.24:80 | shorturl.at | Cloudflare Inc | US | unknown |
2112 | chrome.exe | 216.58.207.35:443 | ssl.gstatic.com | Google Inc. | US | whitelisted |
2112 | chrome.exe | 216.58.212.174:443 | safebrowsing.google.com | Google Inc. | US | whitelisted |
2112 | chrome.exe | 104.24.117.24:443 | shorturl.at | Cloudflare Inc | US | unknown |
2112 | chrome.exe | 172.217.16.174:443 | sb-ssl.google.com | Google Inc. | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
clientservices.googleapis.com |
| whitelisted |
accounts.google.com |
| shared |
www.google.com |
| malicious |
fonts.gstatic.com |
| whitelisted |
fonts.googleapis.com |
| whitelisted |
clients2.google.com |
| whitelisted |
ssl.gstatic.com |
| whitelisted |
shorturl.at |
| whitelisted |
www.shorturl.at |
| whitelisted |
cdn.discordapp.com |
| shared |