| File name: | JitsiMeetOutlook-install-script.bat |
| Full analysis: | https://app.any.run/tasks/900c8aa3-b996-4751-a3e2-fb45b2b09d51 |
| Verdict: | Malicious activity |
| Analysis date: | October 20, 2020, 10:17:14 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | text/x-msdos-batch |
| File info: | DOS batch file, ASCII text |
| MD5: | A7ABB1A8DCE9390D894675EBAE1F81F3 |
| SHA1: | 740DBA459CF67677534DE118C4CFEAE0B460D974 |
| SHA256: | 8D64D0230CC3121030665F9A016A202828D6DF5C5A1ACCCEE9A25CD4F7E51631 |
| SSDEEP: | 24:jmq96ol2SbBltDwEdlnE0+AFP0+ME0++Yu/t/WTYQTRWWgP9iLXnY3K23A5pcXDw:Kq95H5du5S5v5G9WcQT4WgliLXnY3BUz |
MALICIOUS
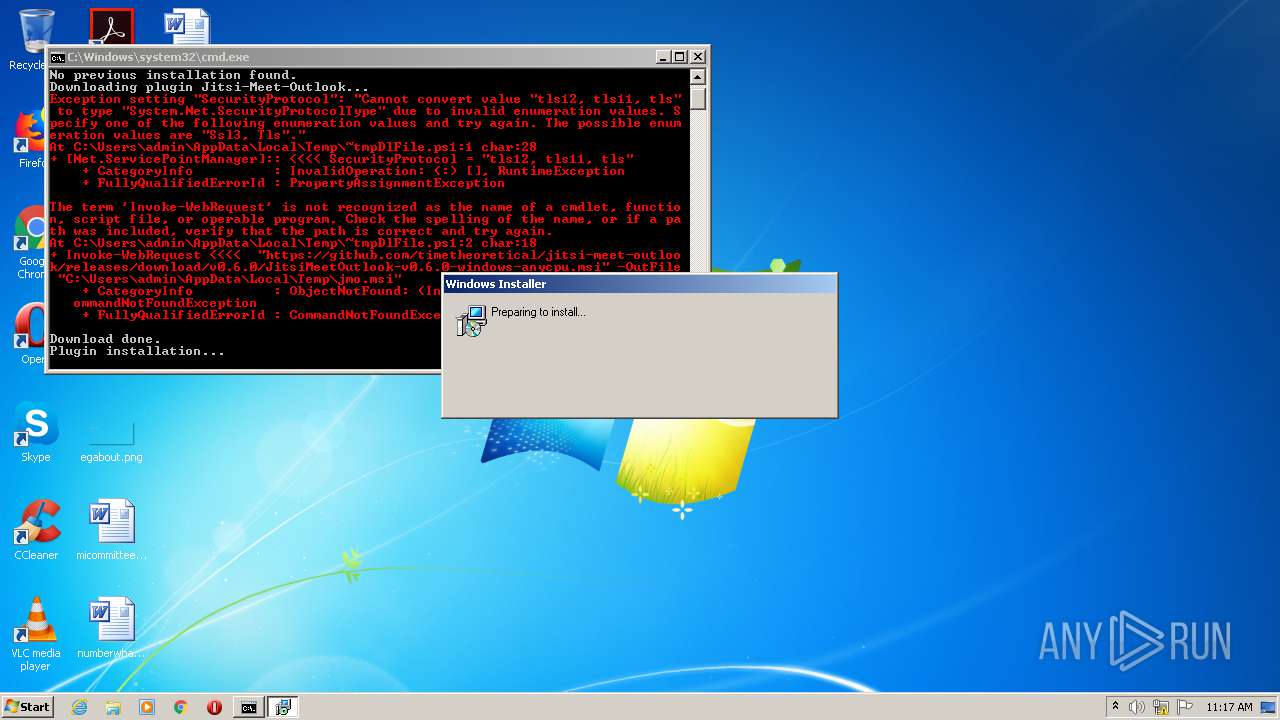
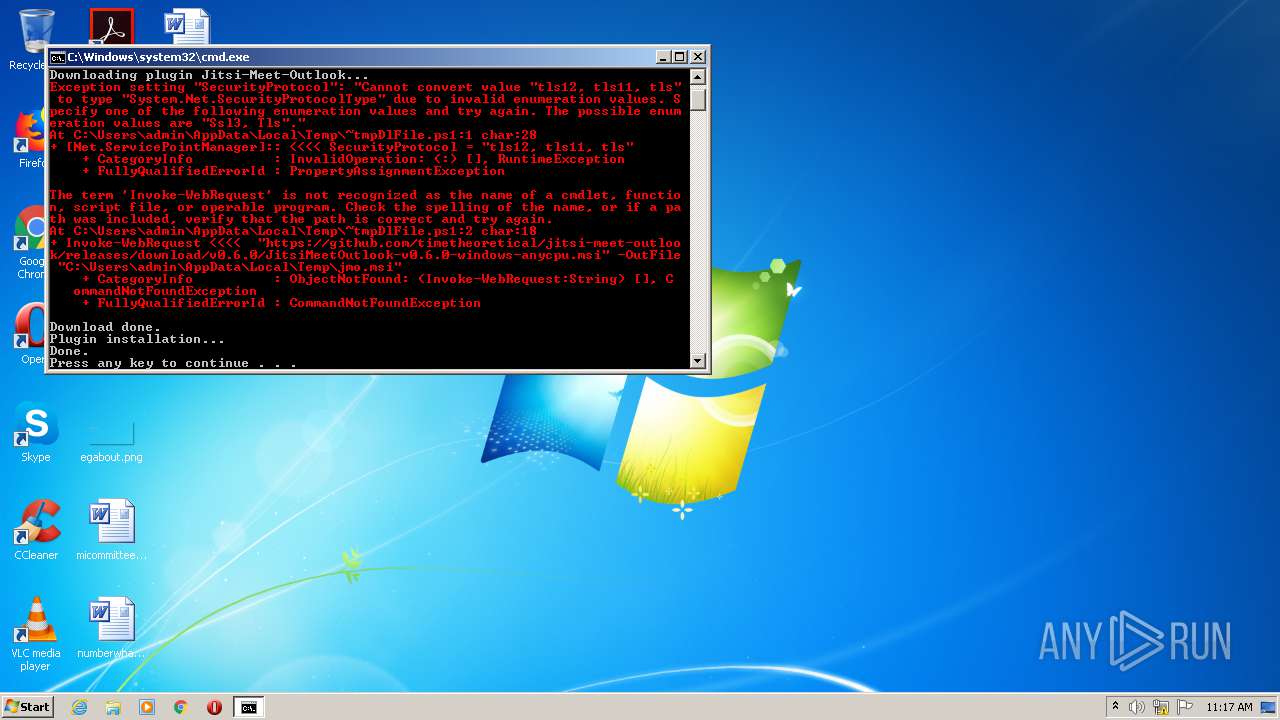
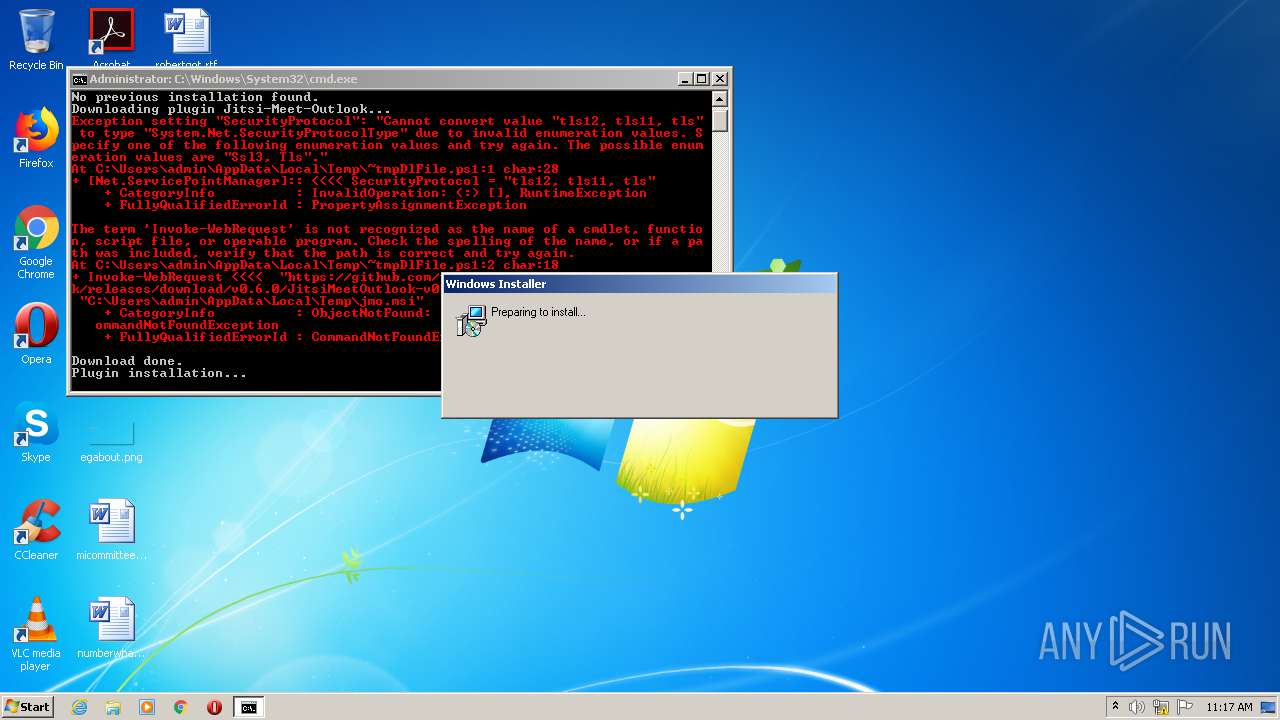
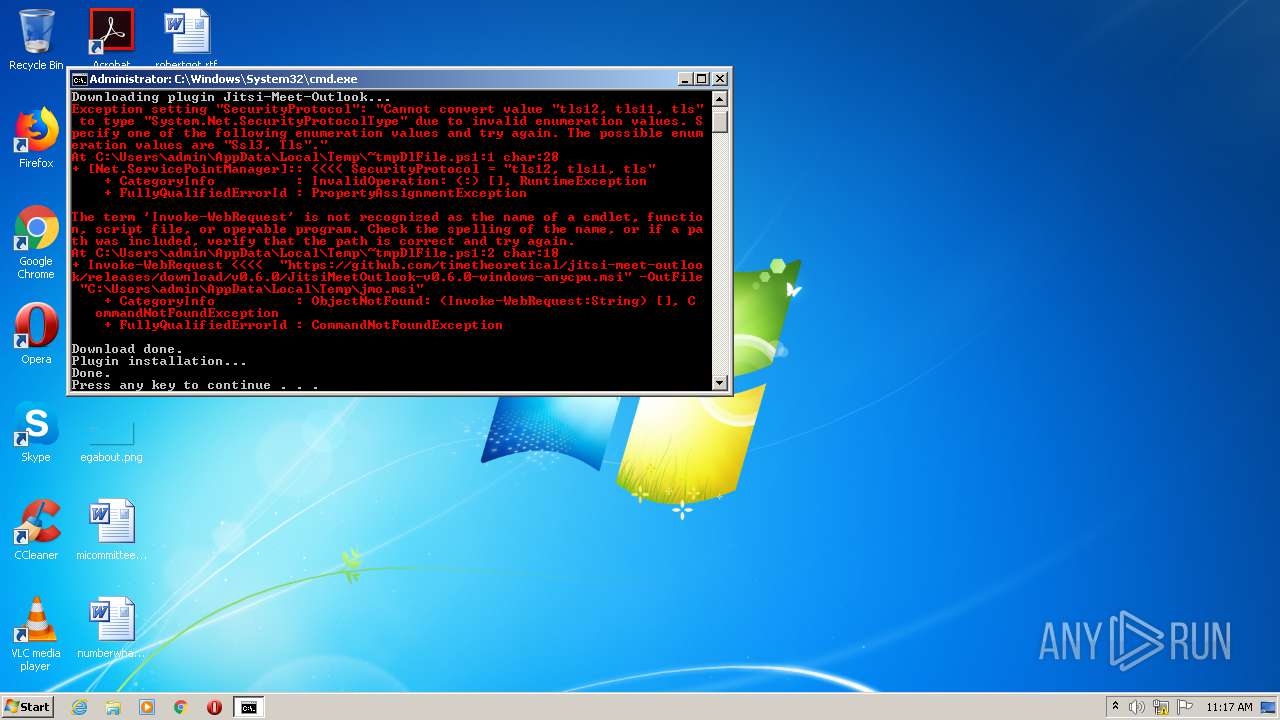
Executes PowerShell scripts
- cmd.exe (PID: 2284)
- cmd.exe (PID: 1700)
SUSPICIOUS
Starts Microsoft Installer
- cmd.exe (PID: 2284)
- cmd.exe (PID: 1700)
Creates files in the user directory
- powershell.exe (PID: 2636)
- powershell.exe (PID: 3644)
INFO
Manual execution by user
- cmd.exe (PID: 1700)
- OUTLOOK.EXE (PID: 860)
Reads internet explorer settings
- OUTLOOK.EXE (PID: 860)
Reads Internet Cache Settings
- OUTLOOK.EXE (PID: 860)
Creates files in the user directory
- OUTLOOK.EXE (PID: 860)
Reads Microsoft Office registry keys
- OUTLOOK.EXE (PID: 860)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
51
Monitored processes
8
Malicious processes
2
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 860 | "C:\Program Files\Microsoft Office\Office14\OUTLOOK.EXE" | C:\Program Files\Microsoft Office\Office14\OUTLOOK.EXE | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Outlook Exit code: 0 Version: 14.0.6025.1000 Modules
| |||||||||||||||
| 1700 | "C:\Windows\System32\cmd.exe" /C "C:\Users\admin\Desktop\JitsiMeetOutlook-install-script.bat" | C:\Windows\System32\cmd.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 2284 | cmd /c ""C:\Users\admin\Desktop\JitsiMeetOutlook-install-script.bat" " | C:\Windows\system32\cmd.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 2368 | msiexec /i "C:\Users\admin\AppData\Local\Temp\jmo.msi" TARGETDIR="C:\Program Files\Jitsi Meet Outlook" DOMAIN="domain:port" ROOMID="default_room" REQNAME="False" NOAUDIO="False" NOVIDEO="False" LANG="en" /passive | C:\Windows\system32\msiexec.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows® installer Exit code: 1619 Version: 5.0.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2636 | Powershell -ExecutionPolicy Bypass -Command "& 'C:\Users\admin\AppData\Local\Temp\~tmpDlFile.ps1'" | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3292 | msiexec /i "C:\Users\admin\AppData\Local\Temp\jmo.msi" TARGETDIR="C:\Program Files\Jitsi Meet Outlook" DOMAIN="domain:port" ROOMID="default_room" REQNAME="False" NOAUDIO="False" NOVIDEO="False" LANG="en" /passive | C:\Windows\system32\msiexec.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows® installer Exit code: 1619 Version: 5.0.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3644 | Powershell -ExecutionPolicy Bypass -Command "& 'C:\Users\admin\AppData\Local\Temp\~tmpDlFile.ps1'" | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows PowerShell Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3744 | C:\Windows\system32\msiexec.exe /V | C:\Windows\system32\msiexec.exe | — | services.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows® installer Exit code: 0 Version: 5.0.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
Total events
2 617
Read events
1 849
Write events
733
Delete events
35
Modification events
| (PID) Process: | (2636) powershell.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\13B\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (3644) powershell.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\13B\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (860) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1033 |
Value: Off | |||
| (PID) Process: | (860) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1041 |
Value: Off | |||
| (PID) Process: | (860) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1046 |
Value: Off | |||
| (PID) Process: | (860) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1036 |
Value: Off | |||
| (PID) Process: | (860) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1031 |
Value: Off | |||
| (PID) Process: | (860) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1040 |
Value: Off | |||
| (PID) Process: | (860) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1049 |
Value: Off | |||
| (PID) Process: | (860) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 3082 |
Value: Off | |||
Executable files
0
Suspicious files
6
Text files
38
Unknown types
2
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2636 | powershell.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\2H7EWUCUE7MJ0IAF6JKO.temp | — | |
MD5:— | SHA256:— | |||
| 3644 | powershell.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\GJMT3FP2QBRTID31VVL8.temp | — | |
MD5:— | SHA256:— | |||
| 860 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Temp\CVR96A7.tmp.cvr | — | |
MD5:— | SHA256:— | |||
| 860 | OUTLOOK.EXE | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\CYWUP4P6X3UZVF64SPT8.temp | — | |
MD5:— | SHA256:— | |||
| 2284 | cmd.exe | C:\Users\admin\AppData\Local\Temp\~tmpDlFile.ps1 | text | |
MD5:— | SHA256:— | |||
| 3644 | powershell.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\d93f411851d7c929.customDestinations-ms | binary | |
MD5:— | SHA256:— | |||
| 860 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Temp\msoA9E3.tmp | — | |
MD5:— | SHA256:— | |||
| 2636 | powershell.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\d93f411851d7c929.customDestinations-ms | binary | |
MD5:— | SHA256:— | |||
| 3644 | powershell.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\d93f411851d7c929.customDestinations-ms~RF2d6e4f.TMP | binary | |
MD5:— | SHA256:— | |||
| 2636 | powershell.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\d93f411851d7c929.customDestinations-ms~RF2d3fad.TMP | binary | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
1
TCP/UDP connections
1
DNS requests
1
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
860 | OUTLOOK.EXE | GET | 404 | 64.4.26.155:80 | http://config.messenger.msn.com/config/msgrconfig.asmx?op=GetOlcConfig | US | xml | 345 b | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
— | — | 64.4.26.155:80 | config.messenger.msn.com | Microsoft Corporation | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
config.messenger.msn.com |
| whitelisted |