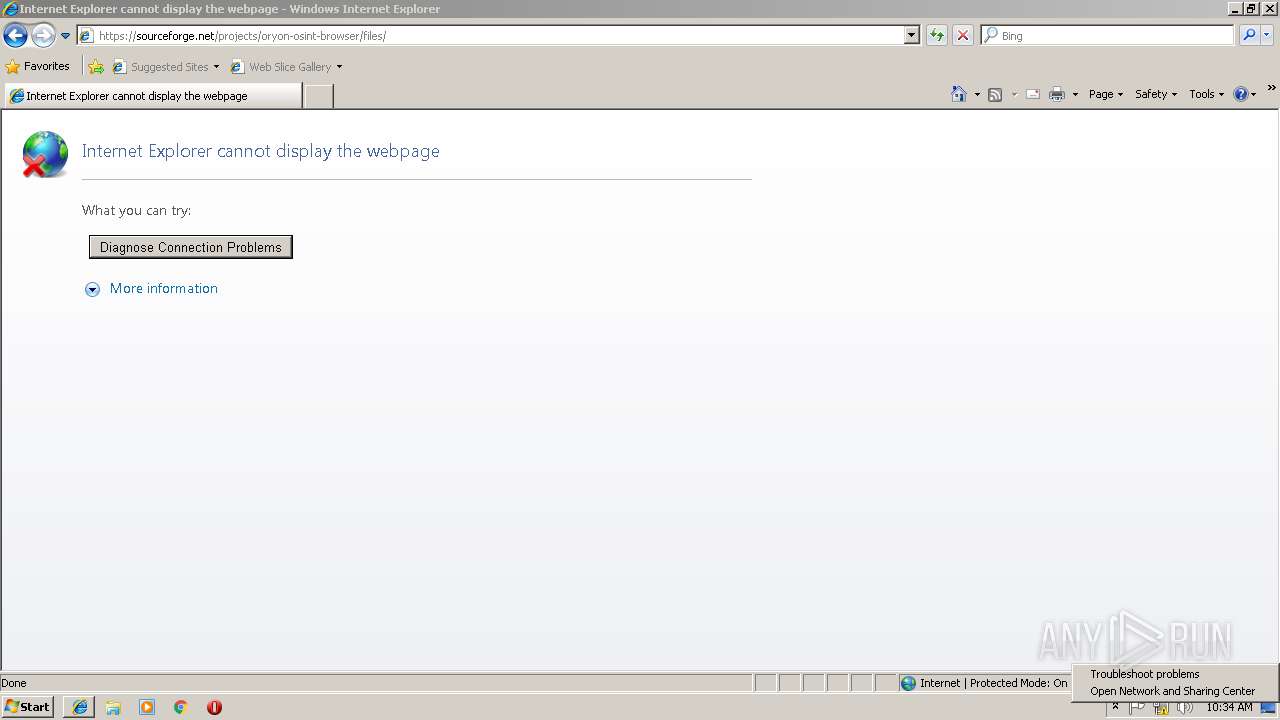
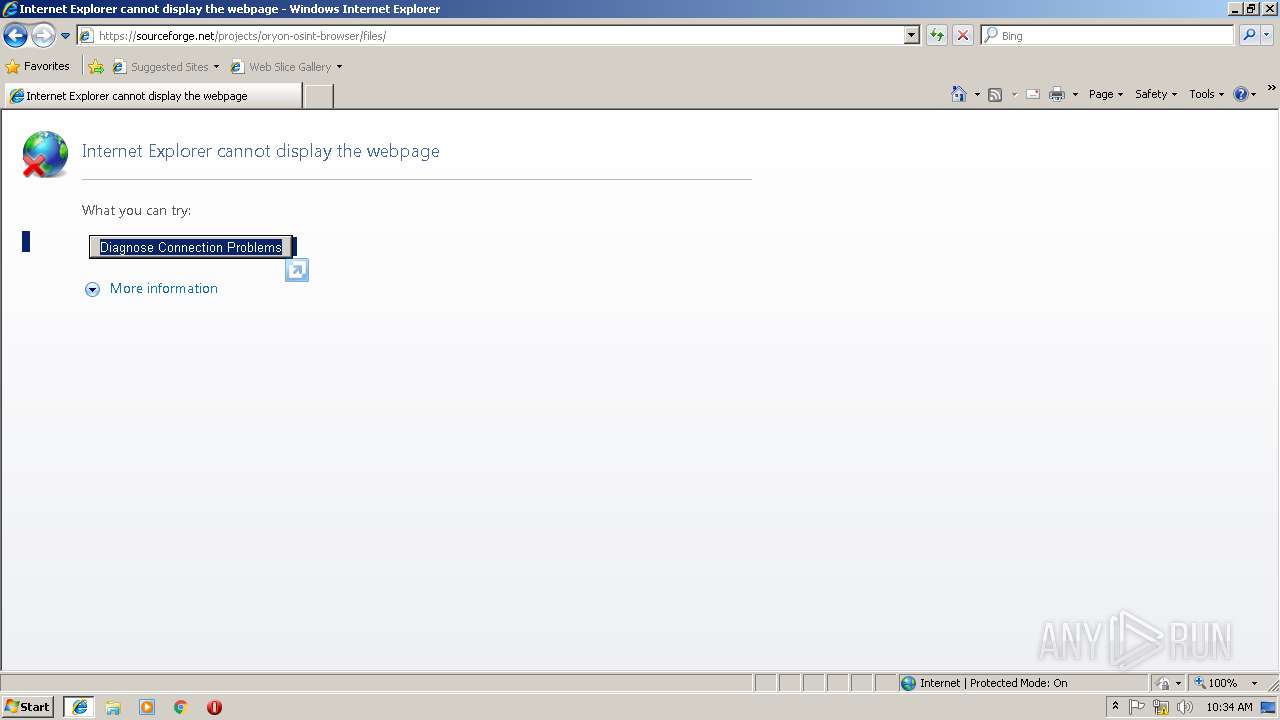
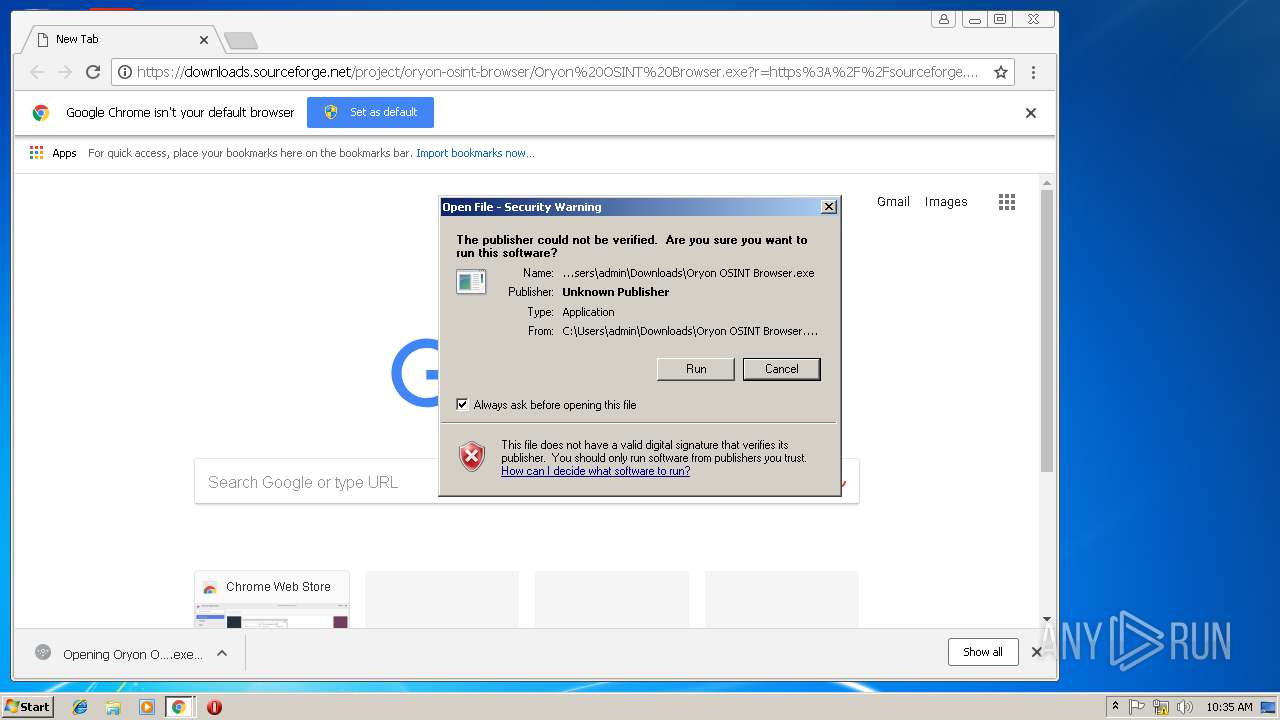
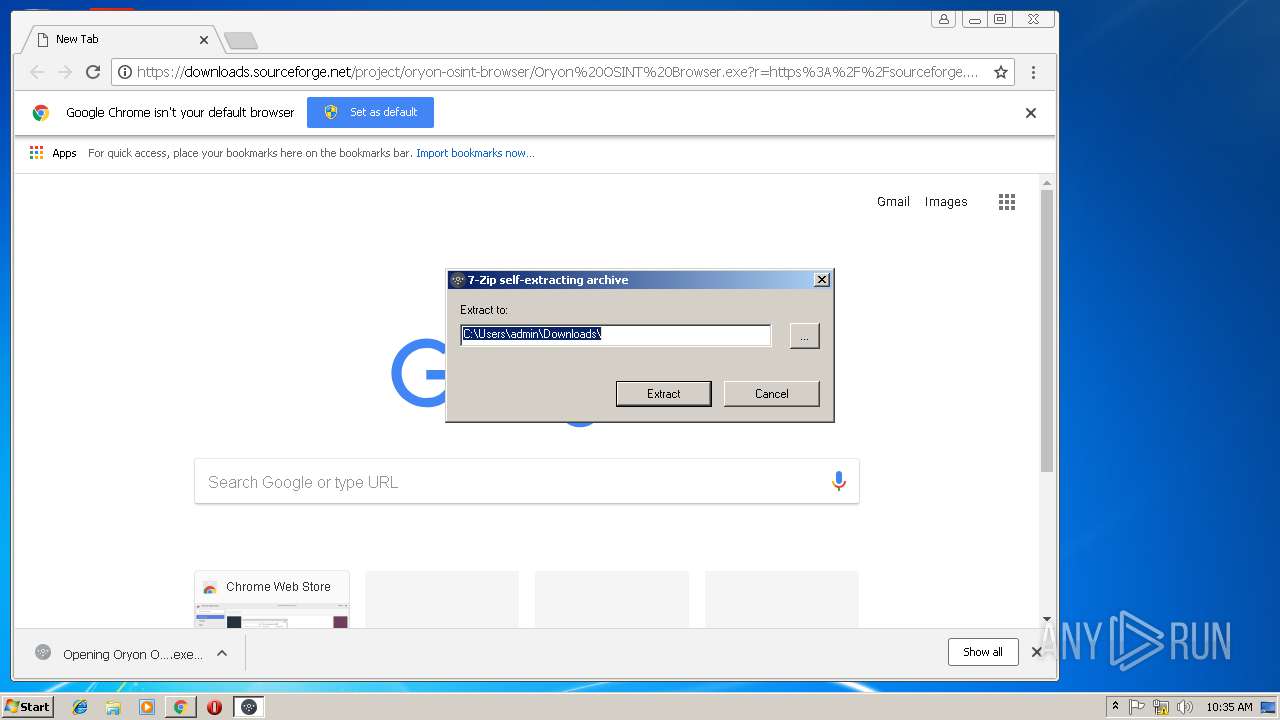
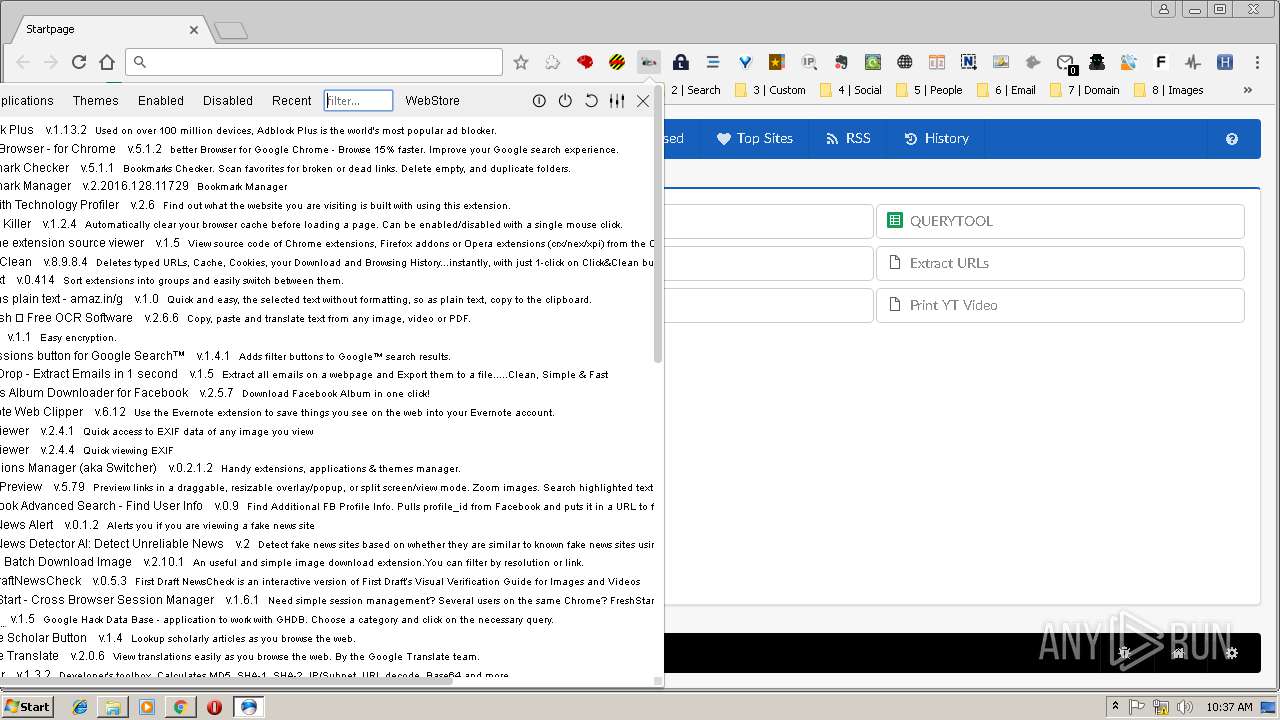
| URL: | https://sourceforge.net/projects/oryon-osint-browser/files/Oryon%20OSINT%20Browser.exe/download |
| Full analysis: | https://app.any.run/tasks/46999310-7009-43b3-8880-9c7c591f28e7 |
| Verdict: | Malicious activity |
| Analysis date: | January 11, 2019, 10:32:54 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MD5: | F269CB90185A7916F89B1DDA8DDAD132 |
| SHA1: | BB052E55815E85F92FD5156C4C186964E14A636A |
| SHA256: | 8D561C03EC18AFBF597BEAD9A39AEF968B0DB22EC63B2C0015D4A8E22A2F51D5 |
| SSDEEP: | 3:N8HCGSuLAuUtYWKR8tXhJmscEAwSHkBLz:2iGnCtYWjtP21kB/ |
MALICIOUS
Application was dropped or rewritten from another process
- Oryon OSINT Browser.exe (PID: 932)
- oryon.exe (PID: 2328)
- chrome.exe (PID: 3592)
- chrome.exe (PID: 3836)
- chrome.exe (PID: 3900)
- chrome.exe (PID: 3008)
- chrome.exe (PID: 2776)
- chrome.exe (PID: 3532)
- chrome.exe (PID: 3724)
- chrome.exe (PID: 3880)
- chrome.exe (PID: 3164)
- chrome.exe (PID: 2252)
- chrome.exe (PID: 3048)
- chrome.exe (PID: 1440)
- chrome.exe (PID: 3256)
- chrome.exe (PID: 3992)
- chrome.exe (PID: 4060)
- chrome.exe (PID: 4008)
- chrome.exe (PID: 2224)
- chrome.exe (PID: 3448)
- chrome.exe (PID: 3548)
- chrome.exe (PID: 3808)
- chrome.exe (PID: 2712)
- chrome.exe (PID: 3132)
- chrome.exe (PID: 3248)
- chrome.exe (PID: 3720)
Loads dropped or rewritten executable
- chrome.exe (PID: 3592)
- chrome.exe (PID: 3836)
- chrome.exe (PID: 3900)
- chrome.exe (PID: 3008)
- chrome.exe (PID: 3532)
- chrome.exe (PID: 3880)
- chrome.exe (PID: 3164)
- chrome.exe (PID: 2252)
- chrome.exe (PID: 3724)
- chrome.exe (PID: 1440)
- chrome.exe (PID: 3992)
- chrome.exe (PID: 3808)
- chrome.exe (PID: 4060)
- chrome.exe (PID: 2776)
- chrome.exe (PID: 4008)
- chrome.exe (PID: 2224)
- chrome.exe (PID: 3548)
- chrome.exe (PID: 3132)
- chrome.exe (PID: 2712)
- chrome.exe (PID: 3448)
- chrome.exe (PID: 3048)
- chrome.exe (PID: 3256)
- chrome.exe (PID: 3248)
SUSPICIOUS
Executable content was dropped or overwritten
- chrome.exe (PID: 3140)
- Oryon OSINT Browser.exe (PID: 932)
Application launched itself
- chrome.exe (PID: 3592)
Creates files in the user directory
- chrome.exe (PID: 3592)
INFO
Application launched itself
- iexplore.exe (PID: 2968)
- chrome.exe (PID: 3140)
Changes internet zones settings
- iexplore.exe (PID: 2968)
Reads internet explorer settings
- iexplore.exe (PID: 3260)
Reads Internet Cache Settings
- iexplore.exe (PID: 3260)
- chrome.exe (PID: 3140)
Creates files in the user directory
- iexplore.exe (PID: 2968)
Reads settings of System Certificates
- chrome.exe (PID: 3140)
Dropped object may contain Bitcoin addresses
- Oryon OSINT Browser.exe (PID: 932)
Dropped object may contain TOR URL's
- Oryon OSINT Browser.exe (PID: 932)
- chrome.exe (PID: 3592)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
77
Monitored processes
43
Malicious processes
16
Suspicious processes
4
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 900 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=964,13744467964472207367,3940503210350438802,131072 --enable-features=PasswordImport --service-pipe-token=5C9755F34DB115D99C5FEB81C871F6E7 --lang=en-US --extension-process --enable-offline-auto-reload --enable-offline-auto-reload-visible-only --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --service-request-channel-token=5C9755F34DB115D99C5FEB81C871F6E7 --renderer-client-id=3 --mojo-platform-channel-handle=2080 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google Inc. Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 68.0.3440.106 Modules
| |||||||||||||||
| 932 | "C:\Users\admin\Downloads\Oryon OSINT Browser.exe" | C:\Users\admin\Downloads\Oryon OSINT Browser.exe | chrome.exe | ||||||||||||
User: admin Company: Igor Pavlov Integrity Level: MEDIUM Description: 7z SFX Exit code: 0 Version: 16.02 Modules
| |||||||||||||||
| 1008 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=964,13744467964472207367,3940503210350438802,131072 --enable-features=PasswordImport --disable-gpu-compositing --service-pipe-token=C0875E1E6FB962B3532A411BC23E66ED --lang=en-US --enable-offline-auto-reload --enable-offline-auto-reload-visible-only --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --service-request-channel-token=C0875E1E6FB962B3532A411BC23E66ED --renderer-client-id=8 --mojo-platform-channel-handle=3904 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google Inc. Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 68.0.3440.106 Modules
| |||||||||||||||
| 1440 | "C:\Users\admin\Downloads\Oryon OSINT Browser\Iron\chrome.exe" --type=renderer --field-trial-handle=1520 --primordial-pipe-token=43C48DB7EEC7E0030660C684C44CEBCA --lang=en-US --user-data-dir="C:\Users\admin\Downloads\Oryon OSINT Browser\Profile" --extension-process --enable-offline-auto-reload --enable-offline-auto-reload-visible-only --enable-pinch --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --content-image-texture-target=0,0,3553;0,1,3553;0,2,3553;0,3,3553;0,4,3553;0,5,3553;0,6,3553;0,7,3553;0,8,3553;0,9,3553;0,10,3553;0,11,3553;0,12,3553;0,13,3553;0,14,3553;0,15,3553;1,0,3553;1,1,3553;1,2,3553;1,3,3553;1,4,3553;1,5,3553;1,6,3553;1,7,3553;1,8,3553;1,9,3553;1,10,3553;1,11,3553;1,12,3553;1,13,3553;1,14,3553;1,15,3553;2,0,3553;2,1,3553;2,2,3553;2,3,3553;2,4,3553;2,5,3553;2,6,3553;2,7,3553;2,8,3553;2,9,3553;2,10,3553;2,11,3553;2,12,3553;2,13,3553;2,14,3553;2,15,3553;3,0,3553;3,1,3553;3,2,3553;3,3,3553;3,4,3553;3,5,3553;3,6,3553;3,7,3553;3,8,3553;3,9,3553;3,10,3553;3,11,3553;3,12,3553;3,13,3553;3,14,3553;3,15,3553 --disable-accelerated-video-decode --disable-webrtc-hw-vp8-encoding --disable-gpu-compositing --service-request-channel-token=43C48DB7EEC7E0030660C684C44CEBCA --renderer-client-id=10 --mojo-platform-channel-handle=1964 /prefetch:1 | C:\Users\admin\Downloads\Oryon OSINT Browser\Iron\chrome.exe | — | chrome.exe | |||||||||||
User: admin Integrity Level: LOW Description: SRWare Iron Exit code: 0 Version: 57.0.3000.0 Modules
| |||||||||||||||
| 2116 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=gpu-process --field-trial-handle=964,13744467964472207367,3940503210350438802,131072 --enable-features=PasswordImport --gpu-preferences=KAAAAAAAAACAAwBAAQAAAAAAAAAAAGAAEAAAAAAAAAAAAAAAAAAAACgAAAAEAAAAIAAAAAAAAAAoAAAAAAAAADAAAAAAAAAAOAAAAAAAAAAQAAAAAAAAAAAAAAAKAAAAEAAAAAAAAAAAAAAACwAAABAAAAAAAAAAAQAAAAoAAAAQAAAAAAAAAAEAAAALAAAA --service-request-channel-token=0728F94DF502D49354E02E7463A880D9 --mojo-platform-channel-handle=988 --ignored=" --type=renderer " /prefetch:2 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google Inc. Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 68.0.3440.106 Modules
| |||||||||||||||
| 2208 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=964,13744467964472207367,3940503210350438802,131072 --enable-features=PasswordImport --disable-gpu-compositing --service-pipe-token=2F0F0DB9B14DB6738FD79A47DA314BDF --lang=en-US --instant-process --enable-offline-auto-reload --enable-offline-auto-reload-visible-only --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --service-request-channel-token=2F0F0DB9B14DB6738FD79A47DA314BDF --renderer-client-id=6 --mojo-platform-channel-handle=3552 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google Inc. Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 68.0.3440.106 Modules
| |||||||||||||||
| 2224 | "C:\Users\admin\Downloads\Oryon OSINT Browser\Iron\chrome.exe" --type=renderer --field-trial-handle=1520 --primordial-pipe-token=3F05AB157A7F45A69A91B984E83DF862 --lang=en-US --user-data-dir="C:\Users\admin\Downloads\Oryon OSINT Browser\Profile" --extension-process --enable-offline-auto-reload --enable-offline-auto-reload-visible-only --enable-pinch --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --content-image-texture-target=0,0,3553;0,1,3553;0,2,3553;0,3,3553;0,4,3553;0,5,3553;0,6,3553;0,7,3553;0,8,3553;0,9,3553;0,10,3553;0,11,3553;0,12,3553;0,13,3553;0,14,3553;0,15,3553;1,0,3553;1,1,3553;1,2,3553;1,3,3553;1,4,3553;1,5,3553;1,6,3553;1,7,3553;1,8,3553;1,9,3553;1,10,3553;1,11,3553;1,12,3553;1,13,3553;1,14,3553;1,15,3553;2,0,3553;2,1,3553;2,2,3553;2,3,3553;2,4,3553;2,5,3553;2,6,3553;2,7,3553;2,8,3553;2,9,3553;2,10,3553;2,11,3553;2,12,3553;2,13,3553;2,14,3553;2,15,3553;3,0,3553;3,1,3553;3,2,3553;3,3,3553;3,4,3553;3,5,3553;3,6,3553;3,7,3553;3,8,3553;3,9,3553;3,10,3553;3,11,3553;3,12,3553;3,13,3553;3,14,3553;3,15,3553 --disable-accelerated-video-decode --disable-webrtc-hw-vp8-encoding --disable-gpu-compositing --service-request-channel-token=3F05AB157A7F45A69A91B984E83DF862 --renderer-client-id=15 --mojo-platform-channel-handle=2084 /prefetch:1 | C:\Users\admin\Downloads\Oryon OSINT Browser\Iron\chrome.exe | — | chrome.exe | |||||||||||
User: admin Integrity Level: LOW Description: SRWare Iron Exit code: 0 Version: 57.0.3000.0 Modules
| |||||||||||||||
| 2252 | "C:\Users\admin\Downloads\Oryon OSINT Browser\Iron\chrome.exe" --type=renderer --field-trial-handle=1520 --primordial-pipe-token=1CD924427661C6095DB1A9F4DC67F6A5 --lang=en-US --user-data-dir="C:\Users\admin\Downloads\Oryon OSINT Browser\Profile" --extension-process --enable-offline-auto-reload --enable-offline-auto-reload-visible-only --enable-pinch --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --content-image-texture-target=0,0,3553;0,1,3553;0,2,3553;0,3,3553;0,4,3553;0,5,3553;0,6,3553;0,7,3553;0,8,3553;0,9,3553;0,10,3553;0,11,3553;0,12,3553;0,13,3553;0,14,3553;0,15,3553;1,0,3553;1,1,3553;1,2,3553;1,3,3553;1,4,3553;1,5,3553;1,6,3553;1,7,3553;1,8,3553;1,9,3553;1,10,3553;1,11,3553;1,12,3553;1,13,3553;1,14,3553;1,15,3553;2,0,3553;2,1,3553;2,2,3553;2,3,3553;2,4,3553;2,5,3553;2,6,3553;2,7,3553;2,8,3553;2,9,3553;2,10,3553;2,11,3553;2,12,3553;2,13,3553;2,14,3553;2,15,3553;3,0,3553;3,1,3553;3,2,3553;3,3,3553;3,4,3553;3,5,3553;3,6,3553;3,7,3553;3,8,3553;3,9,3553;3,10,3553;3,11,3553;3,12,3553;3,13,3553;3,14,3553;3,15,3553 --disable-accelerated-video-decode --disable-webrtc-hw-vp8-encoding --disable-gpu-compositing --service-request-channel-token=1CD924427661C6095DB1A9F4DC67F6A5 --renderer-client-id=6 --mojo-platform-channel-handle=1896 /prefetch:1 | C:\Users\admin\Downloads\Oryon OSINT Browser\Iron\chrome.exe | — | chrome.exe | |||||||||||
User: admin Integrity Level: LOW Description: SRWare Iron Exit code: 0 Version: 57.0.3000.0 Modules
| |||||||||||||||
| 2252 | "C:\Windows\explorer.exe" | C:\Windows\explorer.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Explorer Exit code: 1 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2328 | "C:\Users\admin\Downloads\Oryon OSINT Browser\oryon.exe" | C:\Users\admin\Downloads\Oryon OSINT Browser\oryon.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Version: 1.0.0.0 Modules
| |||||||||||||||
Total events
2 926
Read events
2 198
Write events
717
Delete events
11
Modification events
| (PID) Process: | (2968) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\Main |
| Operation: | write | Name: | CompatibilityFlags |
Value: 0 | |||
| (PID) Process: | (2968) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 0 | |||
| (PID) Process: | (2968) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 1 | |||
| (PID) Process: | (2968) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\Zones |
| Operation: | write | Name: | SecuritySafe |
Value: 1 | |||
| (PID) Process: | (2968) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings |
| Operation: | write | Name: | ProxyEnable |
Value: 0 | |||
| (PID) Process: | (2968) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\Connections |
| Operation: | write | Name: | SavedLegacySettings |
Value: 4600000069000000010000000000000000000000000000000000000000000000C0E333BBEAB1D301000000000000000000000000020000001700000000000000FE800000000000007D6CB050D9C573F70B000000000000006D00330032005C004D00530049004D004700330032002E0064006C000100000004AA400014AA4000040000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000002000000C0A8016400000000000000000000000000000000000000000800000000000000805D3F00983740000008000002000000000000600000002060040000B8A94000020000008802000060040000B8A9400004000000F8010000B284000088B64000B84B400043003A000000000000000000000000000000000000000000 | |||
| (PID) Process: | (2968) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\Recovery\Active |
| Operation: | write | Name: | {4D3A58EB-158C-11E9-BAD8-5254004A04AF} |
Value: 0 | |||
| (PID) Process: | (2968) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Ext\Stats\{2670000A-7350-4F3C-8081-5663EE0C6C49}\iexplore |
| Operation: | write | Name: | Type |
Value: 4 | |||
| (PID) Process: | (2968) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Ext\Stats\{2670000A-7350-4F3C-8081-5663EE0C6C49}\iexplore |
| Operation: | write | Name: | Count |
Value: 3 | |||
| (PID) Process: | (2968) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Ext\Stats\{2670000A-7350-4F3C-8081-5663EE0C6C49}\iexplore |
| Operation: | write | Name: | Time |
Value: E307010005000B000A00210010000001 | |||
Executable files
18
Suspicious files
295
Text files
5 369
Unknown types
235
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2968 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\RB73MZ6Y\favicon[1].ico | — | |
MD5:— | SHA256:— | |||
| 2968 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\Internet Explorer\Services\search_{0633EE93-D776-472f-A0FF-E1416B8B2E3A}.ico | — | |
MD5:— | SHA256:— | |||
| 2968 | iexplore.exe | C:\Users\admin\AppData\Local\Temp\StructuredQuery.log | text | |
MD5:— | SHA256:— | |||
| 2968 | iexplore.exe | C:\Users\admin\AppData\Local\Temp\~DFB92C42F60E1F550D.TMP | — | |
MD5:— | SHA256:— | |||
| 2968 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\RB73MZ6Y\favicon[3].png | image | |
MD5:9FB559A691078558E77D6848202F6541 | SHA256:6D8A01DC7647BC218D003B58FE04049E24A9359900B7E0CEBAE76EDF85B8B914 | |||
| 2968 | iexplore.exe | C:\Users\admin\AppData\Local\Temp\~DFFC5CA003676CFDFD.TMP | — | |
MD5:— | SHA256:— | |||
| 3260 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\OCDM6JB6\ErrorPageTemplate[1] | text | |
MD5:F4FE1CB77E758E1BA56B8A8EC20417C5 | SHA256:8D018639281B33DA8EB3CE0B21D11E1D414E59024C3689F92BE8904EB5779B5F | |||
| 2968 | iexplore.exe | C:\Users\admin\AppData\Local\Temp\~DFF88396D9C7F29E19.TMP | — | |
MD5:— | SHA256:— | |||
| 3260 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\U2ZG9DE0\noConnect[1] | image | |
MD5:3CB8FACCD5DE434D415AB75C17E8FD86 | SHA256:6976C426E3AC66D66303C114B22B2B41109A7DE648BA55FFC3E5A53BD0DB09E7 | |||
| 3260 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\PP6KS563\errorPageStrings[1] | text | |
MD5:1A0563F7FB85A678771450B131ED66FD | SHA256:EB5678DE9D8F29CA6893D4E6CA79BD5AB4F312813820FE4997B009A2B1A1654C | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
1
TCP/UDP connections
30
DNS requests
15
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
2968 | iexplore.exe | GET | 200 | 13.107.21.200:80 | http://www.bing.com/favicon.ico | US | image | 237 b | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
2968 | iexplore.exe | 204.79.197.200:80 | www.bing.com | Microsoft Corporation | US | whitelisted |
3260 | iexplore.exe | 216.105.38.13:443 | sourceforge.net | American Internet Services, LLC. | US | malicious |
2968 | iexplore.exe | 13.107.21.200:80 | www.bing.com | Microsoft Corporation | US | whitelisted |
3140 | chrome.exe | 172.217.16.131:443 | www.gstatic.com | Google Inc. | US | whitelisted |
3140 | chrome.exe | 216.58.205.227:443 | clientservices.googleapis.com | Google Inc. | US | whitelisted |
3140 | chrome.exe | 216.58.208.42:443 | safebrowsing.googleapis.com | Google Inc. | US | whitelisted |
3140 | chrome.exe | 216.58.206.3:443 | ssl.gstatic.com | Google Inc. | US | whitelisted |
3140 | chrome.exe | 172.217.22.110:443 | apis.google.com | Google Inc. | US | whitelisted |
3140 | chrome.exe | 172.217.18.13:443 | accounts.google.com | Google Inc. | US | whitelisted |
3140 | chrome.exe | 216.58.208.36:443 | www.google.com | Google Inc. | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
www.bing.com |
| whitelisted |
sourceforge.net |
| whitelisted |
clientservices.googleapis.com |
| whitelisted |
www.gstatic.com |
| whitelisted |
www.google.de |
| whitelisted |
safebrowsing.googleapis.com |
| whitelisted |
accounts.google.com |
| shared |
ssl.gstatic.com |
| whitelisted |
apis.google.com |
| whitelisted |
www.google.com |
| malicious |
Threats
Process | Message |
|---|---|
chrome.exe | RecursiveDirectoryCreate( C:\Users\admin\Downloads\Oryon OSINT Browser\Profile directory exists )
|