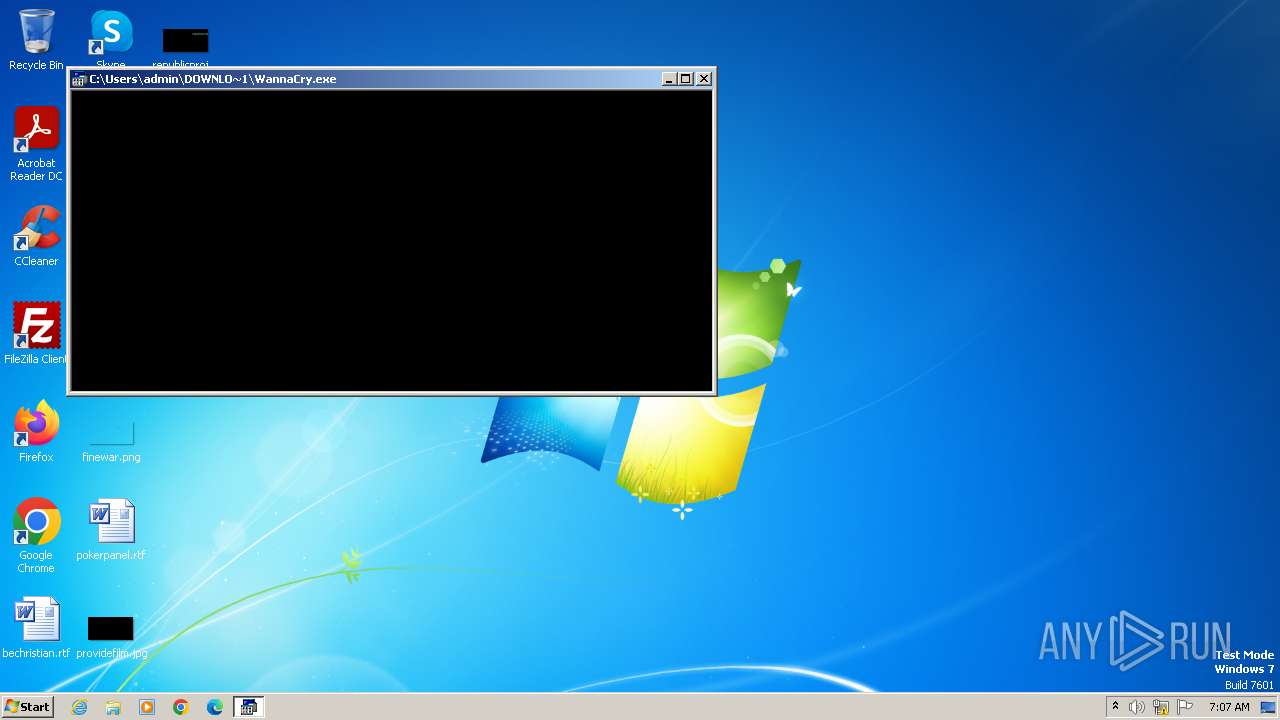
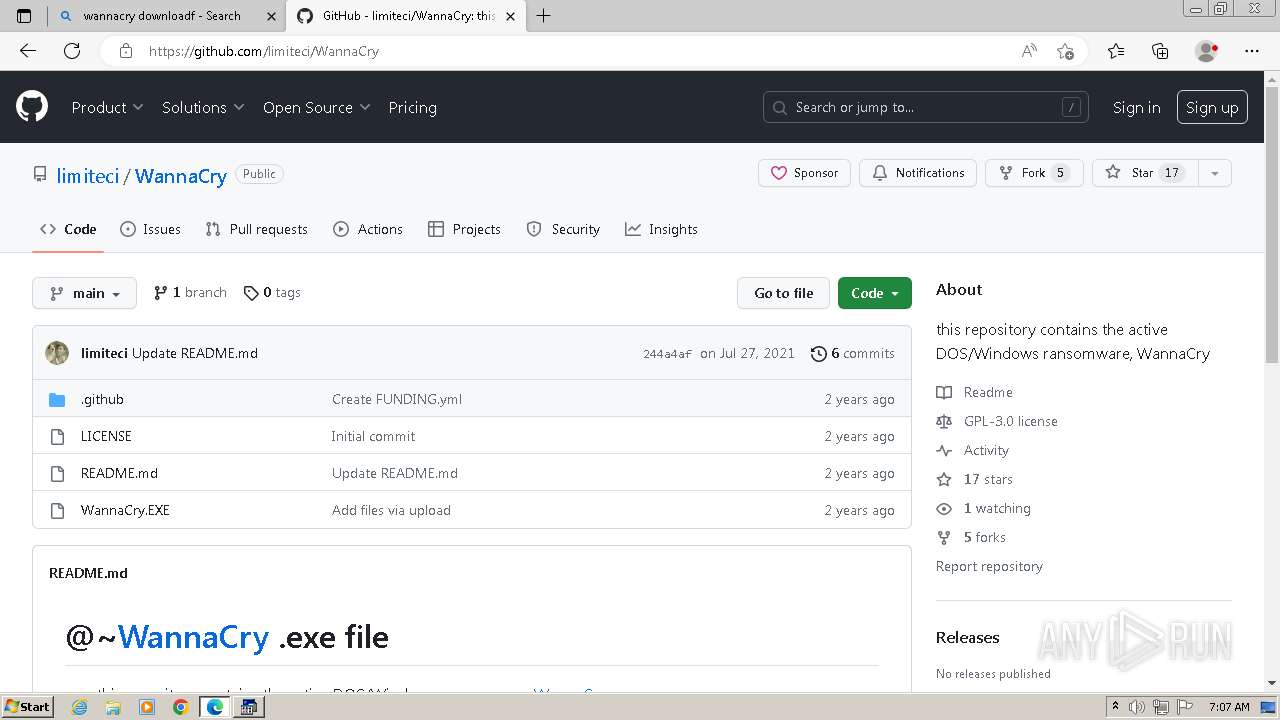
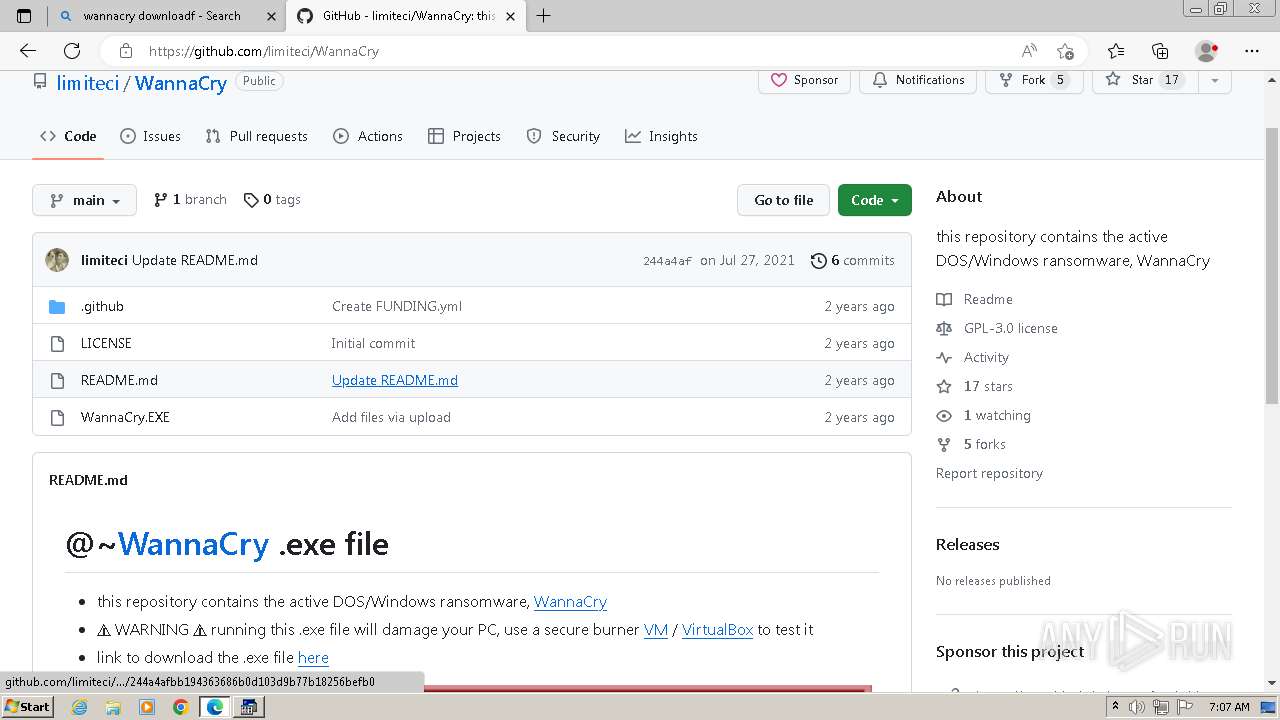
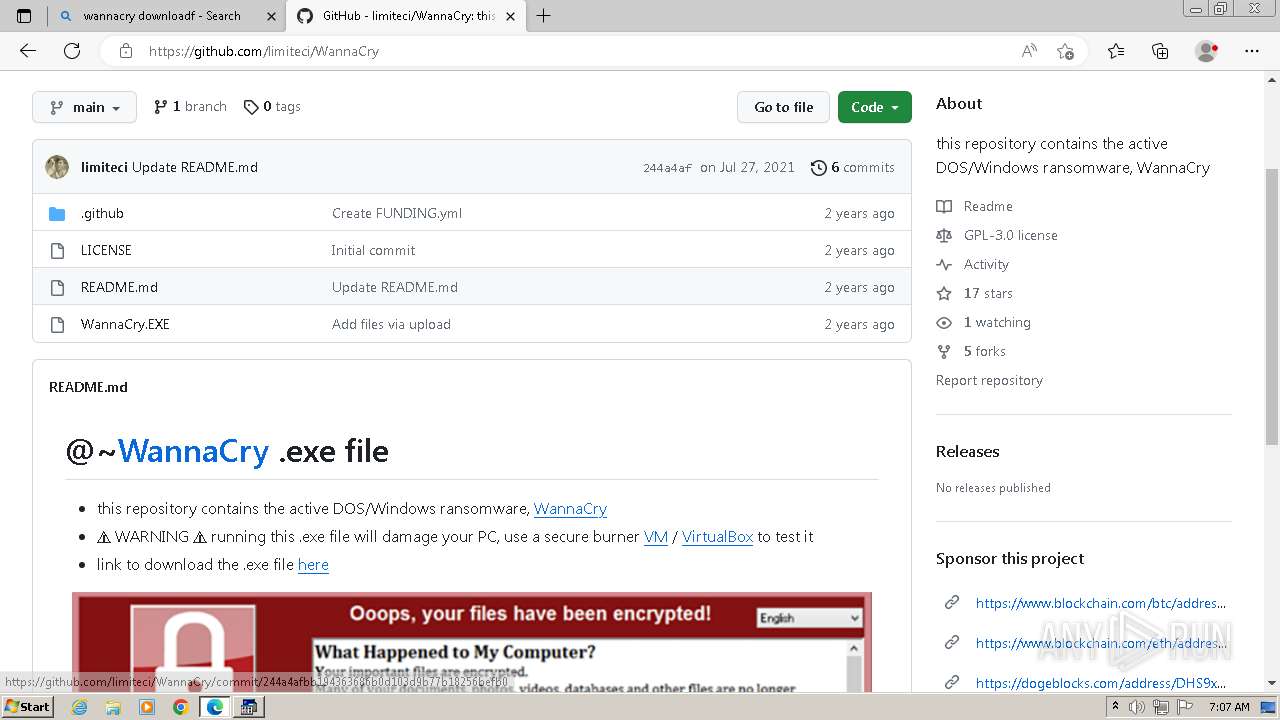
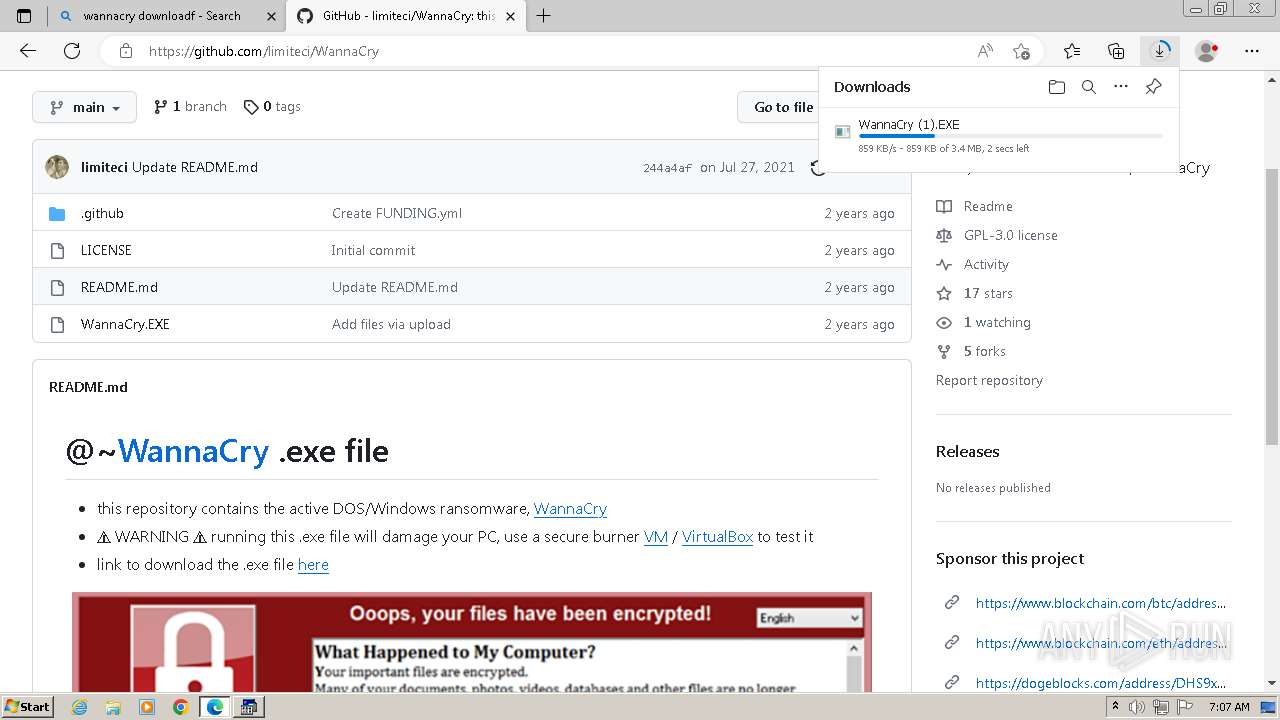
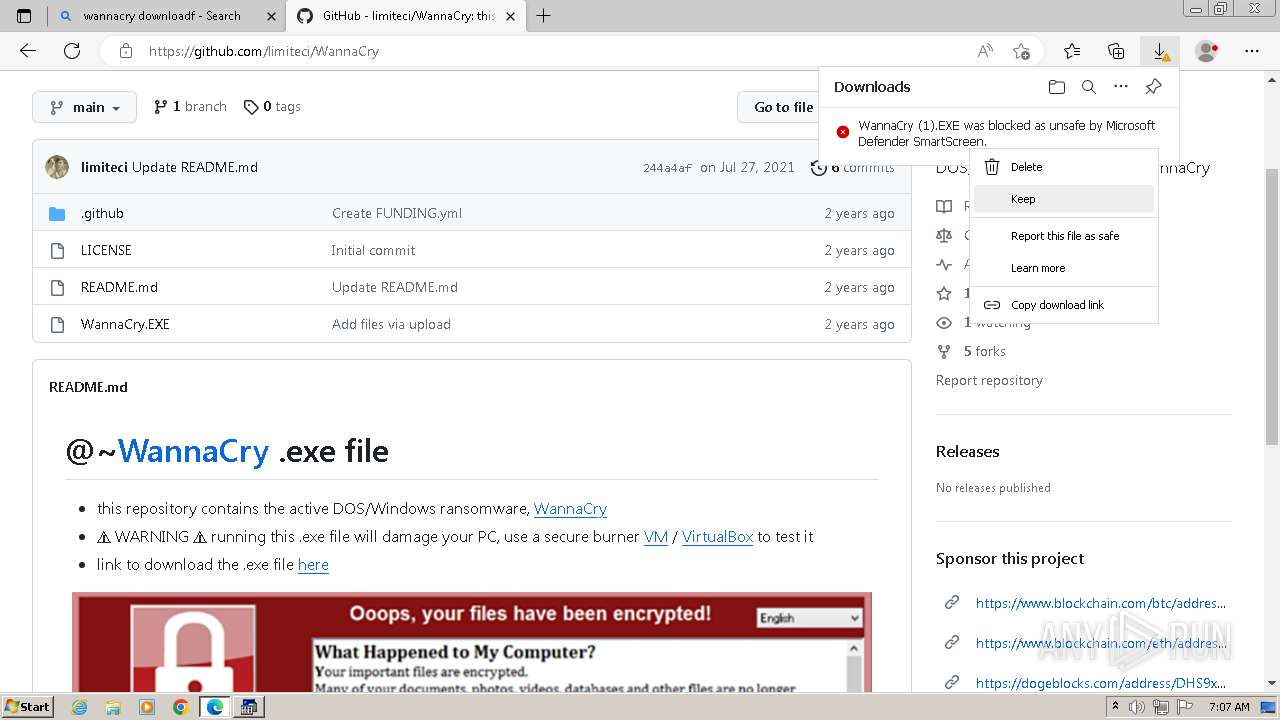
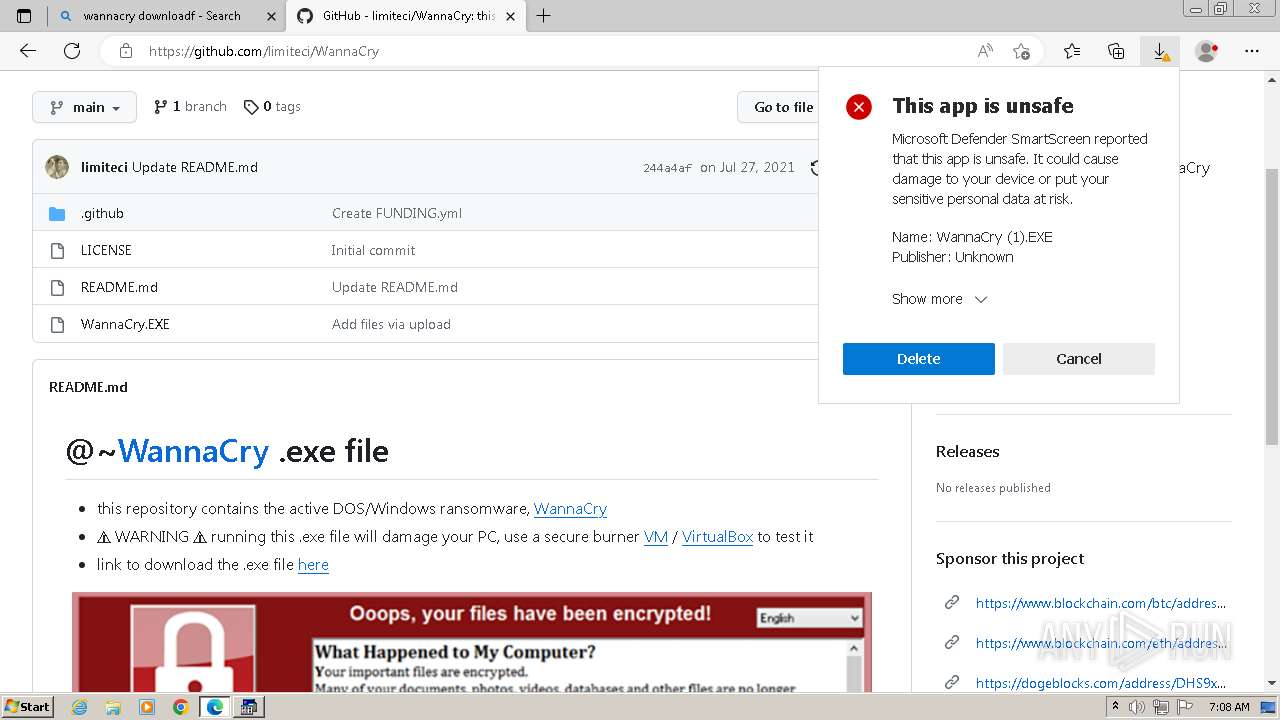
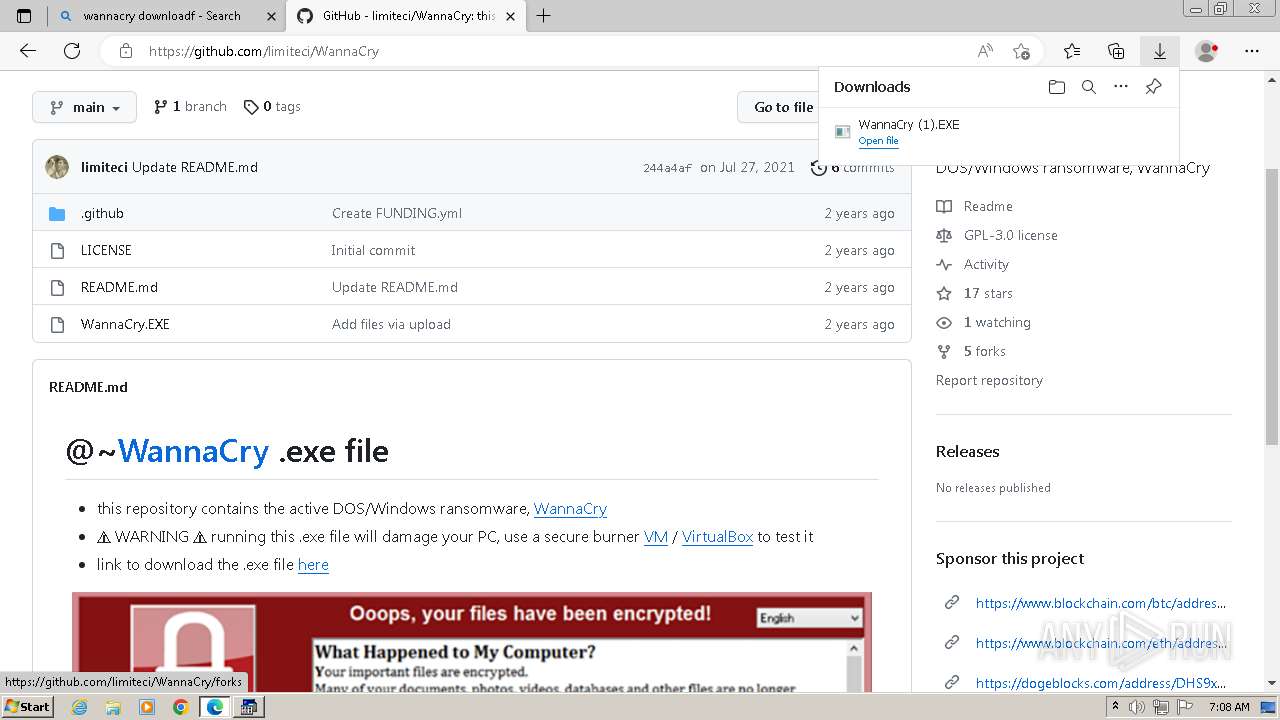
| download: | /Da2dalus/The-MALWARE-Repo/blob/master/Ransomware/WannaCry.exe |
| Full analysis: | https://app.any.run/tasks/aec8b866-b090-44d5-aab3-f3ac1bd7c173 |
| Verdict: | Malicious activity |
| Analysis date: | December 15, 2023, 07:06:55 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/json |
| File info: | JSON data |
| MD5: | D9BEB9106D4AE290E1E8131150AF768B |
| SHA1: | F5EC44FAC1C70D6540E58E597B9041B8008CD9F9 |
| SHA256: | 8D0EA6FA89C2D0762F90191700AF8B35C1AFBCE7FDD9EC9C42E0DA5704E14726 |
| SSDEEP: | 192:OuYX9bvbpN9xFtXtXbZZbVpbX8vHtf9g2Aa5z6UA:OuYX9bvbpN9xFtXtXbZZbVpbX4V9gvIc |
MALICIOUS
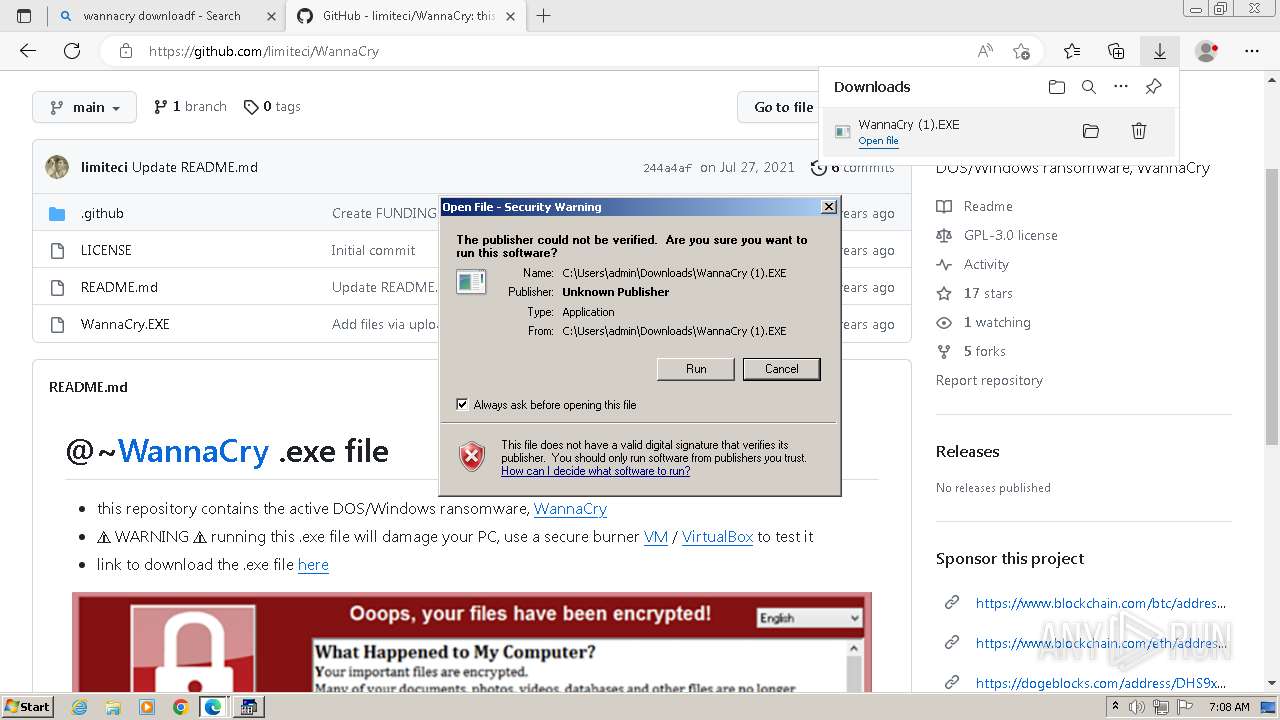
Drops the executable file immediately after the start
- WannaCry (1).EXE (PID: 3612)
SUSPICIOUS
Process drops legitimate windows executable
- msedge.exe (PID: 2316)
- msedge.exe (PID: 2184)
- WannaCry (1).EXE (PID: 3612)
Uses ATTRIB.EXE to modify file attributes
- WannaCry (1).EXE (PID: 3612)
Uses ICACLS.EXE to modify access control lists
- WannaCry (1).EXE (PID: 3612)
Executing commands from a ".bat" file
- WannaCry (1).EXE (PID: 3612)
Starts CMD.EXE for commands execution
- WannaCry (1).EXE (PID: 3612)
INFO
Reads the computer name
- wmpnscfg.exe (PID: 1984)
- WannaCry (1).EXE (PID: 3612)
Checks supported languages
- wmpnscfg.exe (PID: 1984)
- WannaCry (1).EXE (PID: 3612)
- taskdl.exe (PID: 3172)
Manual execution by a user
- wmpnscfg.exe (PID: 1984)
- msedge.exe (PID: 2184)
The process uses the downloaded file
- msedge.exe (PID: 3064)
- msedge.exe (PID: 2184)
The dropped object may contain a URL to Tor Browser
- WannaCry (1).EXE (PID: 3612)
Drops the executable file immediately after the start
- msedge.exe (PID: 2316)
- msedge.exe (PID: 2184)
Dropped object may contain TOR URL's
- WannaCry (1).EXE (PID: 3612)
Reads the machine GUID from the registry
- WannaCry (1).EXE (PID: 3612)
Application launched itself
- msedge.exe (PID: 2184)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
EXIF
JSON
| PayloadAllShortcutsEnabled: | - |
|---|---|
| PayloadBlobCsv: | null |
| PayloadBlobCsvError: | null |
| PayloadBlobDependabotInfoConfigFilePath: | null |
| PayloadBlobDependabotInfoConfigurationNoticeDismissed: | null |
| PayloadBlobDependabotInfoCurrentUserCanAdminRepo: | - |
| PayloadBlobDependabotInfoDismissConfigurationNoticePath: | /settings/dismiss-notice/dependabot_configuration_notice |
| PayloadBlobDependabotInfoNetworkDependabotPath: | /Da2dalus/The-MALWARE-Repo/network/updates |
| PayloadBlobDependabotInfoRepoAlertsPath: | /Da2dalus/The-MALWARE-Repo/security/dependabot |
| PayloadBlobDependabotInfoRepoOwnerIsOrg: | - |
| PayloadBlobDependabotInfoRepoSecurityAndAnalysisPath: | /Da2dalus/The-MALWARE-Repo/settings/security_analysis |
| PayloadBlobDependabotInfoShowConfigurationBanner: | - |
| PayloadBlobDiscussionTemplate: | null |
| PayloadBlobDisplayName: | WannaCry.exe |
| PayloadBlobDisplayUrl: | https://github.com/Da2dalus/The-MALWARE-Repo/blob/master/Ransomware/WannaCry.exe?raw=true |
| PayloadBlobHeaderInfoBlobSize: | 224 KB |
| PayloadBlobHeaderInfoDeleteInfoDeleteTooltip: | You must be signed in to make or propose changes |
| PayloadBlobHeaderInfoEditInfoEditTooltip: | You must be signed in to make or propose changes |
| PayloadBlobHeaderInfoGhDesktopPath: | https://desktop.github.com |
| PayloadBlobHeaderInfoGitLfsPath: | null |
| PayloadBlobHeaderInfoIsCSV: | - |
| PayloadBlobHeaderInfoIsRichtext: | - |
| PayloadBlobHeaderInfoLineInfoTruncatedLoc: | null |
| PayloadBlobHeaderInfoLineInfoTruncatedSloc: | null |
| PayloadBlobHeaderInfoMode: | file |
| PayloadBlobHeaderInfoOnBranch: | |
| PayloadBlobHeaderInfoShortPath: | 73b33e1 |
| PayloadBlobHeaderInfoSiteNavLoginPath: | /login?return_to=https%3A%2F%2Fgithub.com%2FDa2dalus%2FThe-MALWARE-Repo%2Fblob%2Fmaster%2FRansomware%2FWannaCry.exe |
| PayloadBlobHeaderInfoToc: | null |
| PayloadBlobImage: | - |
| PayloadBlobIsCodeownersFile: | null |
| PayloadBlobIsPlain: | - |
| PayloadBlobIsValidLegacyIssueTemplate: | - |
| PayloadBlobIssueTemplate: | null |
| PayloadBlobIssueTemplateHelpUrl: | https://docs.github.com/articles/about-issue-and-pull-request-templates |
| PayloadBlobLanguage: | null |
| PayloadBlobLanguageID: | null |
| PayloadBlobLarge: | - |
| PayloadBlobLoggedIn: | - |
| PayloadBlobNewDiscussionPath: | /Da2dalus/The-MALWARE-Repo/discussions/new |
| PayloadBlobNewIssuePath: | /Da2dalus/The-MALWARE-Repo/issues/new |
| PayloadBlobPlanSupportInfoRepoIsFork: | null |
| PayloadBlobPlanSupportInfoRepoOwnedByCurrentUser: | null |
| PayloadBlobPlanSupportInfoRequestFullPath: | /Da2dalus/The-MALWARE-Repo/blob/master/Ransomware/WannaCry.exe |
| PayloadBlobPlanSupportInfoShowFreeOrgGatedFeatureMessage: | null |
| PayloadBlobPlanSupportInfoShowPlanSupportBanner: | null |
| PayloadBlobPlanSupportInfoUpgradeDataAttributes: | null |
| PayloadBlobPlanSupportInfoUpgradePath: | null |
| PayloadBlobPublishBannersInfoDismissActionNoticePath: | /settings/dismiss-notice/publish_action_from_dockerfile |
| PayloadBlobPublishBannersInfoDismissStackNoticePath: | /settings/dismiss-notice/publish_stack_from_file |
| PayloadBlobPublishBannersInfoReleasePath: | /Da2dalus/The-MALWARE-Repo/releases/new?marketplace=true |
| PayloadBlobPublishBannersInfoShowPublishActionBanner: | - |
| PayloadBlobPublishBannersInfoShowPublishStackBanner: | - |
| PayloadBlobRawBlobUrl: | https://github.com/Da2dalus/The-MALWARE-Repo/raw/master/Ransomware/WannaCry.exe |
| PayloadBlobRawLines: | null |
| PayloadBlobRenderImageOrRaw: | |
| PayloadBlobRenderedFileInfo: | null |
| PayloadBlobRichText: | null |
| PayloadBlobShortPath: | null |
| PayloadBlobStylingDirectives: | null |
| PayloadBlobSymbols: | null |
| PayloadBlobTabSize: | 8 |
| PayloadBlobTopBannersInfoActionsOnboardingTip: | null |
| PayloadBlobTopBannersInfoCitationHelpUrl: | https://docs.github.com/en/github/creating-cloning-and-archiving-repositories/creating-a-repository-on-github/about-citation-files |
| PayloadBlobTopBannersInfoGlobalPreferredFundingPath: | null |
| PayloadBlobTopBannersInfoOverridingGlobalFundingFile: | - |
| PayloadBlobTopBannersInfoRepoName: | The-MALWARE-Repo |
| PayloadBlobTopBannersInfoRepoOwner: | Da2dalus |
| PayloadBlobTopBannersInfoShowDependabotConfigurationBanner: | - |
| PayloadBlobTopBannersInfoShowInvalidCitationWarning: | - |
| PayloadBlobTruncated: | - |
| PayloadBlobViewable: | - |
| PayloadBlobWorkflowRedirectUrl: | null |
| PayloadCopilotAccessAllowed: | - |
| PayloadCopilotInfo: | null |
| PayloadCsrf_tokensDa2dalusThe-MALWARE-RepobranchesPost: | agU4i4GgoAFGzP5McyNTLexBERG20AJLoeKhhTWUqpMf_YR2WFNRJKQR978iRpjh04yiY-slO9577nmpxJQU-A |
| PayloadCsrf_tokensrepospreferencesPost: | s4ciHE1y9-dJSPIcv6SPxc_PtgWRPYYqgZE045pZvkBrkmzoGE7NGwHG0n5R5T3H5Cb_p34KX7Zo3DXZWFl7dg |
| PayloadCurrentUser: | null |
| PayloadFileTreeItemsContentType: |
|
| PayloadFileTreeItemsName: |
|
| PayloadFileTreeItemsPath: |
|
| PayloadFileTreeTotalCount: | 16 |
| PayloadFileTreeRansomwareItemsContentType: |
|
| PayloadFileTreeRansomwareItemsName: |
|
| PayloadFileTreeRansomwareItemsPath: |
|
| PayloadFileTreeRansomwareTotalCount: | 27 |
| PayloadFileTreeProcessingTime: | 7.524909 |
| PayloadPath: | Ransomware/WannaCry.exe |
| PayloadReducedMotionEnabled: | null |
| PayloadRefInfoCanEdit: | - |
| PayloadRefInfoCurrentOid: | e8ddc517b4ecd80728e0acef1c558fad9a1c888a |
| PayloadRefInfoListCacheKey: | v0:1592036907.0 |
| PayloadRefInfoName: | master |
| PayloadRefInfoRefType: | branch |
| PayloadRepoCreatedAt: | 2020-06-13T08:28:25.000Z |
| PayloadRepoCurrentUserCanPush: | - |
| PayloadRepoDefaultBranch: | master |
| PayloadRepoId: | 271970028 |
| PayloadRepoIsEmpty: | - |
| PayloadRepoIsFork: | - |
| PayloadRepoIsOrgOwned: | - |
| PayloadRepoName: | The-MALWARE-Repo |
| PayloadRepoOwnerAvatar: | https://avatars.githubusercontent.com/u/63458929?v=4 |
| PayloadRepoOwnerLogin: | Da2dalus |
| PayloadRepoPrivate: | - |
| PayloadRepoPublic: | |
| PayloadSymbolsExpanded: | - |
| PayloadTreeExpanded: | |
| Title: | The-MALWARE-Repo/Ransomware/WannaCry.exe at master · Da2dalus/The-MALWARE-Repo |
Total processes
75
Monitored processes
35
Malicious processes
2
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 188 | "C:\Program Files\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=chrome.mojom.UtilWin --lang=en-US --service-sandbox-type=none --mojo-platform-channel-handle=3604 --field-trial-handle=1336,i,17804747323816950425,18166820728399474514,131072 /prefetch:8 | C:\Program Files\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Edge Exit code: 0 Version: 109.0.1518.115 Modules
| |||||||||||||||
| 916 | icacls . /grant Everyone:F /T /C /Q | C:\Windows\System32\icacls.exe | — | WannaCry (1).EXE | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 924 | "C:\Program Files\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=edge_collections.mojom.CollectionsDataManager --lang=en-US --service-sandbox-type=collections --mojo-platform-channel-handle=4528 --field-trial-handle=1336,i,17804747323816950425,18166820728399474514,131072 /prefetch:8 | C:\Program Files\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 109.0.1518.115 Modules
| |||||||||||||||
| 1556 | "C:\Windows\system32\ntvdm.exe" -i1 | C:\Windows\System32\ntvdm.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: NTVDM.EXE Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1736 | "C:\Program Files\Microsoft\Edge\Application\msedge.exe" --type=renderer --disable-gpu-compositing --lang=en-US --js-flags=--ms-user-locale= --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=23 --mojo-platform-channel-handle=4484 --field-trial-handle=1336,i,17804747323816950425,18166820728399474514,131072 /prefetch:1 | C:\Program Files\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 109.0.1518.115 Modules
| |||||||||||||||
| 1872 | "C:\Program Files\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=asset_store.mojom.AssetStoreService --lang=en-US --service-sandbox-type=asset_store_service --mojo-platform-channel-handle=3816 --field-trial-handle=1336,i,17804747323816950425,18166820728399474514,131072 /prefetch:8 | C:\Program Files\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 109.0.1518.115 Modules
| |||||||||||||||
| 1984 | "C:\Program Files\Windows Media Player\wmpnscfg.exe" | C:\Program Files\Windows Media Player\wmpnscfg.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Media Player Network Sharing Service Configuration Application Exit code: 0 Version: 12.0.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2060 | attrib +h . | C:\Windows\System32\attrib.exe | — | WannaCry (1).EXE | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Attribute Utility Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2184 | "C:\Program Files\Microsoft\Edge\Application\msedge.exe" --profile-directory=Default | C:\Program Files\Microsoft\Edge\Application\msedge.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Edge Exit code: 0 Version: 109.0.1518.115 Modules
| |||||||||||||||
| 2252 | "C:\Program Files\Microsoft\Edge\Application\msedge.exe" --type=renderer --disable-gpu-compositing --lang=en-US --js-flags=--ms-user-locale= --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=26 --mojo-platform-channel-handle=4816 --field-trial-handle=1336,i,17804747323816950425,18166820728399474514,131072 /prefetch:1 | C:\Program Files\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 109.0.1518.115 Modules
| |||||||||||||||
Total events
3 959
Read events
3 915
Write events
43
Delete events
1
Modification events
| (PID) Process: | (2184) msedge.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Edge\BLBeacon |
| Operation: | write | Name: | failed_count |
Value: 0 | |||
| (PID) Process: | (2184) msedge.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Edge\BLBeacon |
| Operation: | write | Name: | state |
Value: 1 | |||
| (PID) Process: | (2184) msedge.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Edge\ThirdParty |
| Operation: | write | Name: | StatusCodes |
Value: 01000000 | |||
| (PID) Process: | (2184) msedge.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Edge\BLBeacon |
| Operation: | write | Name: | state |
Value: 2 | |||
| (PID) Process: | (2184) msedge.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\EdgeUpdate\ClientState\{56EB18F8-B008-4CBD-B6D2-8C97FE7E9062} |
| Operation: | write | Name: | dr |
Value: 1 | |||
| (PID) Process: | (2184) msedge.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Edge\StabilityMetrics |
| Operation: | write | Name: | user_experience_metrics.stability.exited_cleanly |
Value: 1 | |||
| (PID) Process: | (2184) msedge.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\EdgeUpdate\ClientStateMedium\{56EB18F8-B008-4CBD-B6D2-8C97FE7E9062}\LastWasDefault |
| Operation: | write | Name: | S-1-5-21-1302019708-1500728564-335382590-1000 |
Value: 8A1A1F2B695E2F00 | |||
| (PID) Process: | (2184) msedge.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Edge |
| Operation: | write | Name: | UsageStatsInSample |
Value: 1 | |||
| (PID) Process: | (2184) msedge.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\EdgeUpdate\ClientStateMedium\{56EB18F8-B008-4CBD-B6D2-8C97FE7E9062} |
| Operation: | write | Name: | usagestats |
Value: 1 | |||
| (PID) Process: | (2184) msedge.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\EdgeUpdate\ClientStateMedium\{56EB18F8-B008-4CBD-B6D2-8C97FE7E9062} |
| Operation: | write | Name: | urlstats |
Value: 1 | |||
Executable files
42
Suspicious files
1 139
Text files
116
Unknown types
1
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2184 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\commerce_subscription_db\LOG.old~RF211c22.TMP | — | |
MD5:— | SHA256:— | |||
| 2184 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\commerce_subscription_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 2184 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\EdgePushStorageWithConnectTokenAndKey\LOG.old~RF211c51.TMP | — | |
MD5:— | SHA256:— | |||
| 2184 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\EdgePushStorageWithConnectTokenAndKey\LOG.old | — | |
MD5:— | SHA256:— | |||
| 2184 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\LOG.old~RF211c90.TMP | — | |
MD5:— | SHA256:— | |||
| 2184 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\LOG.old | — | |
MD5:— | SHA256:— | |||
| 2184 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\Session Storage\LOG.old | text | |
MD5:AA87E3E91C255D17ED464CAB6C93C80C | SHA256:5E1C0D9217284C819583F549F063E5EF89B3D4C2A660396E3B5B4ADE8B13997C | |||
| 2184 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\Local Storage\leveldb\LOG.old~RF211c9f.TMP | text | |
MD5:08BB7AA32D5D133695D6AFF014B63310 | SHA256:326727FC6EE38D4D0C7FB581214F75495FDCAAF81A9C47A58B39DD747F215FDC | |||
| 1556 | ntvdm.exe | C:\Users\admin\AppData\Local\Temp\scsF8AD.tmp | text | |
MD5:4C361DEA398F7AEEF49953BDC0AB4A9B | SHA256:06D61C23E6CA59B9DDAD1796ECCC42C032CD8F6F424AF6CFEE5D085D36FF7DFD | |||
| 2184 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Last Version | text | |
MD5:61FE7896F9494DCDF53480A325F4FB85 | SHA256:ACFD3CD36E0DFCF1DCB67C7F31F2A5B9BA0815528A0C604D4330DFAA9E683E51 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
65
DNS requests
106
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
1080 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
2588 | svchost.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
2184 | msedge.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
2316 | msedge.exe | 204.79.197.203:443 | ntp.msn.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
2316 | msedge.exe | 204.79.197.239:443 | edge.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | unknown |
2316 | msedge.exe | 13.107.42.16:443 | config.edge.skype.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
2316 | msedge.exe | 23.53.42.187:443 | assets.msn.com | Akamai International B.V. | DE | unknown |
2316 | msedge.exe | 2.21.20.133:443 | img-s-msn-com.akamaized.net | Akamai International B.V. | DE | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
ntp.msn.com |
| whitelisted |
edge.microsoft.com |
| whitelisted |
config.edge.skype.com |
| whitelisted |
assets.msn.com |
| whitelisted |
img-s-msn-com.akamaized.net |
| whitelisted |
sb.scorecardresearch.com |
| shared |
th.bing.com |
| whitelisted |
www.bing.com |
| whitelisted |
api.msn.com |
| whitelisted |
c.bing.com |
| whitelisted |