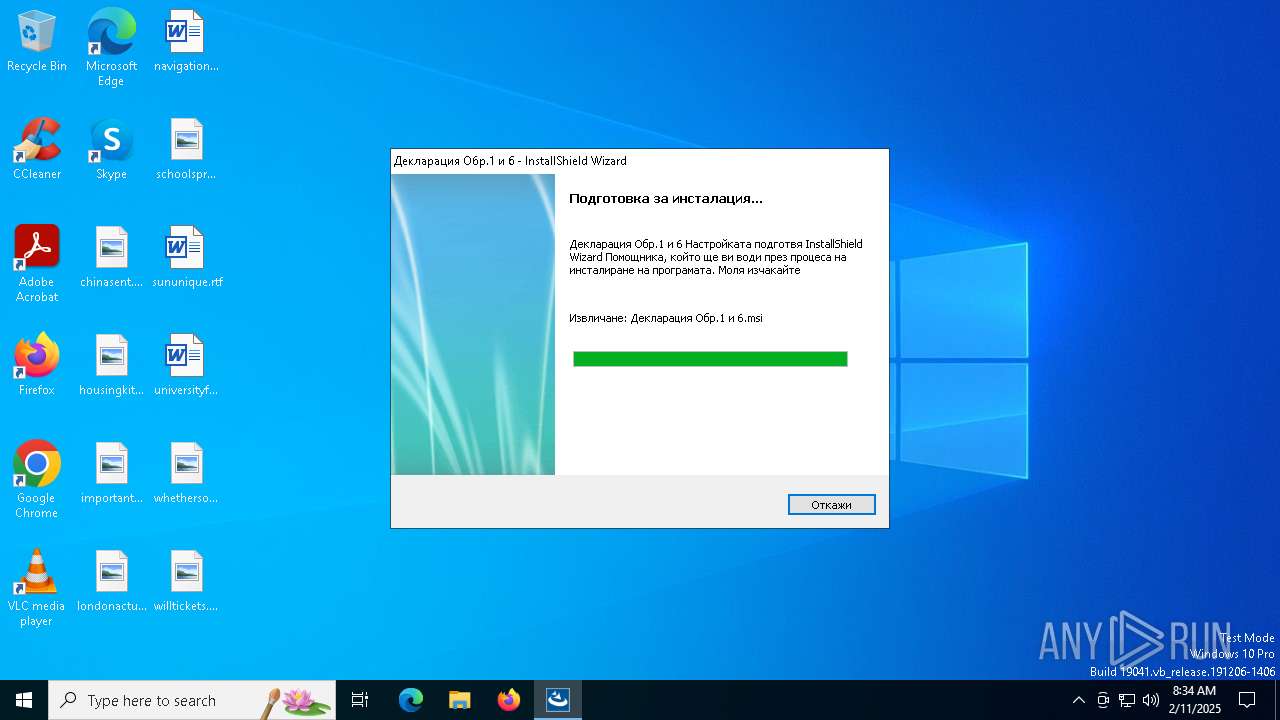
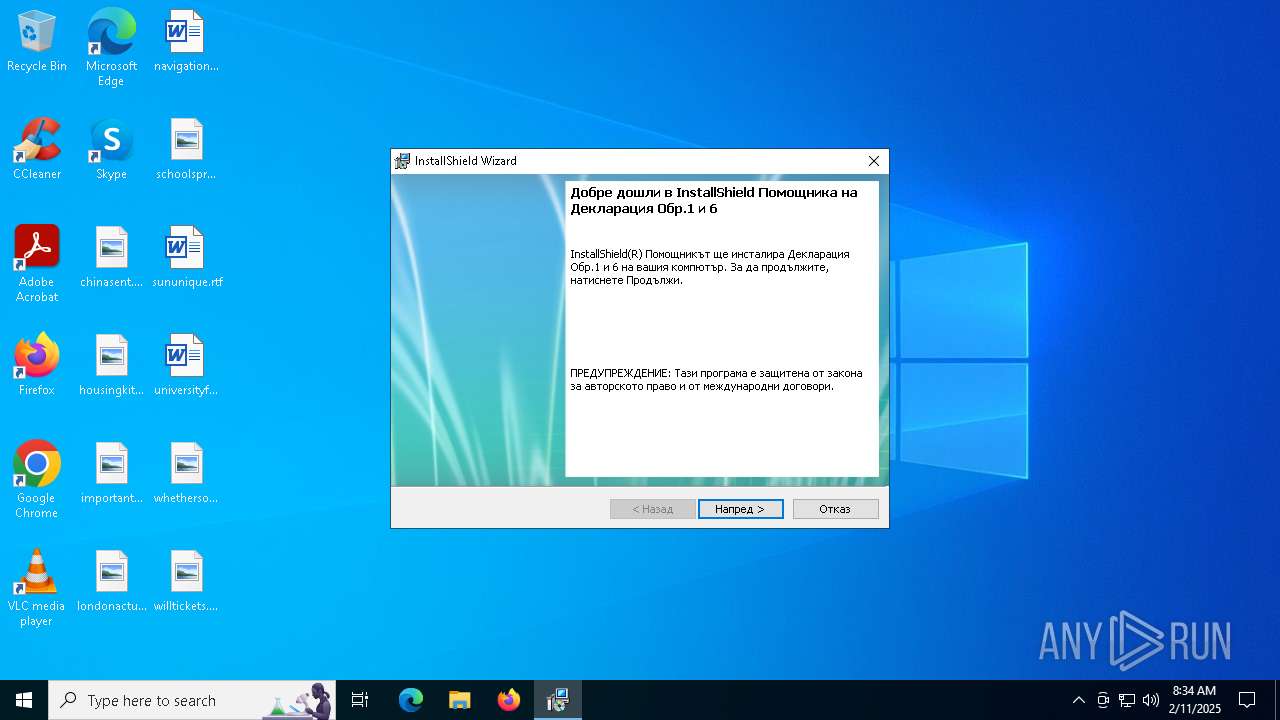
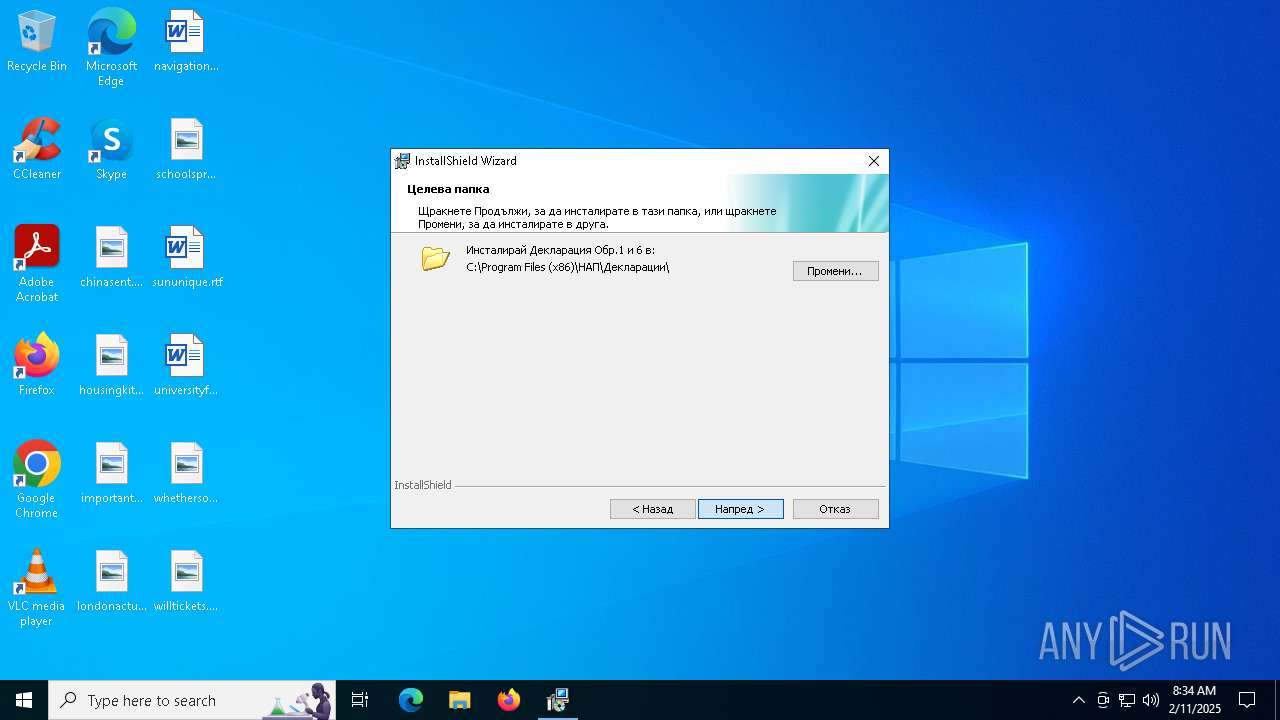
| File name: | Inst_D1_6_v1702.exe |
| Full analysis: | https://app.any.run/tasks/25a658ab-c107-48fc-b4e6-58e7726c7fa7 |
| Verdict: | Malicious activity |
| Analysis date: | February 11, 2025, 08:34:03 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Indicators: | |
| MIME: | application/vnd.microsoft.portable-executable |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows, 5 sections |
| MD5: | DE8D7110E5C532F6657493F47603CB54 |
| SHA1: | F47851FD5CAD050D1BBAFB0A5087DFCF4DC1585E |
| SHA256: | 8D07D3B25566B6B9F80CE735B93C52EE031A54C73F54DDC3D2629C9DD4BEB530 |
| SSDEEP: | 98304:1ed0fakKCF5Tf+S+PIC3RkSh04DNIyAjxL536l90fn/F5eZnrTQjAkuzTPhu2lB4:N8LE |
MALICIOUS
Executing a file with an untrusted certificate
- Inst_D1_6_v1702.exe (PID: 5880)
- Inst_D1_6_v1702.exe (PID: 5592)
- DEKL1.exe (PID: 3960)
- DEKL1.exe (PID: 5856)
- DEKL1.exe (PID: 6284)
SUSPICIOUS
Executable content was dropped or overwritten
- Inst_D1_6_v1702.exe (PID: 5880)
- Inst_D1_6_v1702.exe (PID: 5592)
Starts itself from another location
- Inst_D1_6_v1702.exe (PID: 5880)
Reads the Windows owner or organization settings
- msiexec.exe (PID: 4204)
Uses RUNDLL32.EXE to load library
- explorer.exe (PID: 7056)
Executes application which crashes
- DEKL1.exe (PID: 3960)
- DEKL1.exe (PID: 5856)
There is functionality for taking screenshot (YARA)
- Inst_D1_6_v1702.exe (PID: 5592)
- Inst_D1_6_v1702.exe (PID: 5880)
INFO
Checks supported languages
- Inst_D1_6_v1702.exe (PID: 5880)
- Inst_D1_6_v1702.exe (PID: 5592)
- SearchApp.exe (PID: 5064)
- msiexec.exe (PID: 4204)
- DEKL1.exe (PID: 3960)
- DEKL1.exe (PID: 5856)
The sample compiled with english language support
- Inst_D1_6_v1702.exe (PID: 5880)
- msiexec.exe (PID: 4204)
Reads the computer name
- Inst_D1_6_v1702.exe (PID: 5880)
- Inst_D1_6_v1702.exe (PID: 5592)
- msiexec.exe (PID: 4204)
- DEKL1.exe (PID: 3960)
- DEKL1.exe (PID: 5856)
Create files in a temporary directory
- Inst_D1_6_v1702.exe (PID: 5880)
- Inst_D1_6_v1702.exe (PID: 5592)
Reads the machine GUID from the registry
- SearchApp.exe (PID: 5064)
Process checks computer location settings
- SearchApp.exe (PID: 5064)
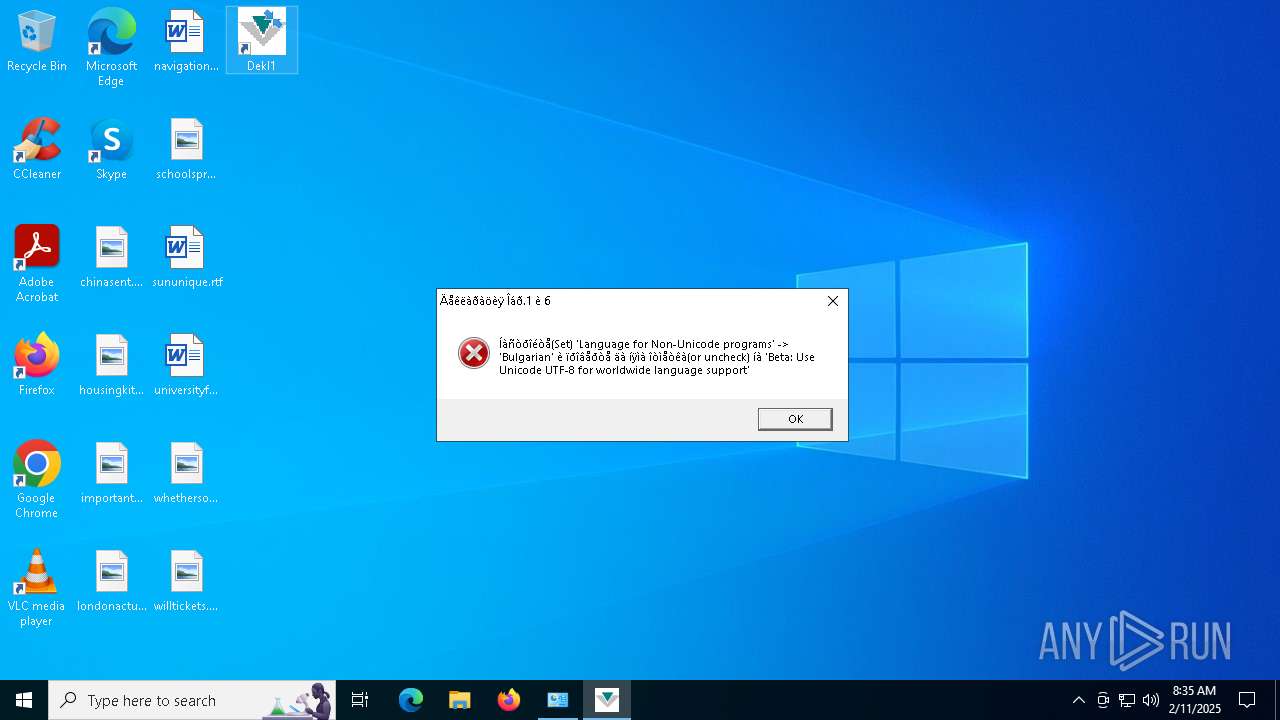
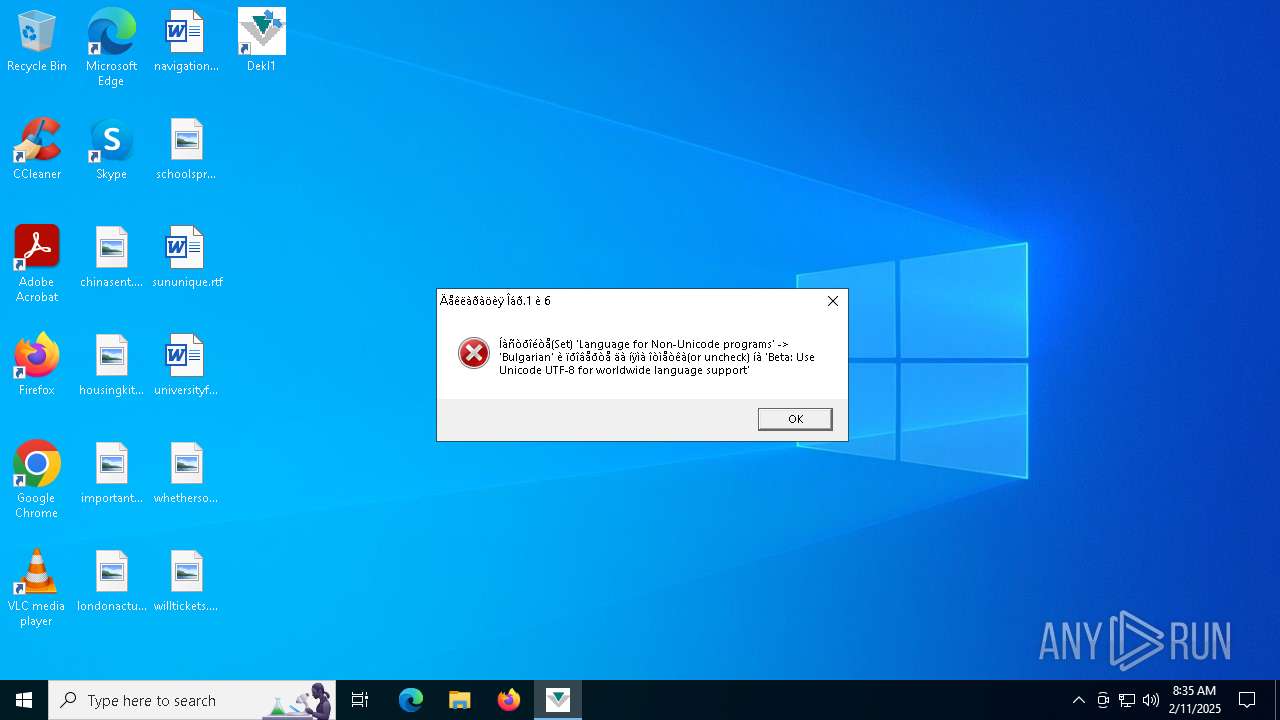
The sample compiled with bulgarian language support
- msiexec.exe (PID: 4204)
Creates a software uninstall entry
- msiexec.exe (PID: 4204)
Manual execution by a user
- DEKL1.exe (PID: 3960)
- DEKL1.exe (PID: 6284)
- DEKL1.exe (PID: 5856)
Reads security settings of Internet Explorer
- explorer.exe (PID: 7056)
- dllhost.exe (PID: 5240)
Reads the software policy settings
- dllhost.exe (PID: 5240)
- WerFault.exe (PID: 2408)
- WerFault.exe (PID: 6796)
- SearchApp.exe (PID: 5064)
Executable content was dropped or overwritten
- msiexec.exe (PID: 4204)
Checks transactions between databases Windows and Oracle
- rundll32.exe (PID: 6308)
- rundll32.exe (PID: 6032)
Creates files or folders in the user directory
- WerFault.exe (PID: 2408)
- WerFault.exe (PID: 6796)
Checks proxy server information
- WerFault.exe (PID: 2408)
- WerFault.exe (PID: 6796)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win64 Executable (generic) (64.6) |
|---|---|---|
| .dll | | | Win32 Dynamic Link Library (generic) (15.4) |
| .exe | | | Win32 Executable (generic) (10.5) |
| .exe | | | Generic Win/DOS Executable (4.6) |
| .exe | | | DOS Executable Generic (4.6) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2018:09:20 13:06:54+00:00 |
| ImageFileCharacteristics: | Executable, 32-bit |
| PEType: | PE32 |
| LinkerVersion: | 11 |
| CodeSize: | 476672 |
| InitializedDataSize: | 617984 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x4523a |
| OSVersion: | 5.1 |
| ImageVersion: | - |
| SubsystemVersion: | 5.1 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 17.2.0.0 |
| ProductVersionNumber: | 17.2.0.0 |
| FileFlagsMask: | 0x003f |
| FileFlags: | (none) |
| FileOS: | Win32 |
| ObjectFileType: | Dynamic link library |
| FileSubtype: | - |
| LanguageCode: | English (U.S.) |
| CharacterSet: | Unicode |
| CompanyName: | НАП |
| FileDescription: | Setup Launcher Unicode |
| FileVersion: | 17.02 |
| InternalName: | Setup |
| LegalCopyright: | Copyright (c) 2018 Flexera. All Rights Reserved. |
| OriginalFileName: | InstallShield Setup.exe |
| ProductName: | Декларация Обр.1 и 6 |
| ProductVersion: | 17.02 |
| InternalBuildNumber: | 185990 |
| ISInternalVersion: | 24.0.573 |
| ISInternalDescription: | Setup Launcher Unicode |
Total processes
159
Monitored processes
20
Malicious processes
2
Suspicious processes
4
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 940 | C:\WINDOWS\system32\explorer.exe | C:\Windows\SysWOW64\explorer.exe | — | Inst_D1_6_v1702.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Explorer Exit code: 0 Version: 10.0.19041.3758 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2408 | C:\WINDOWS\SysWOW64\WerFault.exe -u -p 5856 -s 652 | C:\Windows\SysWOW64\WerFault.exe | DEKL1.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Problem Reporting Exit code: 0 Version: 10.0.19041.3996 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3732 | "C:\WINDOWS\system32\MSIEXEC.EXE" /i "C:\Users\admin\AppData\Local\Temp\{64EADA0C-25D4-4901-9F7A-DA935BC51EC7}\Декларация Обр.1 и 6.msi" SETUPEXEDIR="C:\Users\admin\AppData\Local\Temp" SETUPEXENAME="Inst_D1_6_v1702.exe" | C:\Windows\SysWOW64\msiexec.exe | — | Inst_D1_6_v1702.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows® installer Exit code: 0 Version: 5.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3960 | "C:\Program Files (x86)\НАП\Декларации\Обр1_6\DEKL1.exe" | C:\Program Files (x86)\НАП\Декларации\Обр1_6\DEKL1.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Description: DEKL1 MFC Application Exit code: 3221225477 Version: 17, 0, 2, 0 Modules
| |||||||||||||||
| 3988 | C:\WINDOWS\system32\DllHost.exe /Processid:{514B5E31-5596-422F-BE58-D804464683B5} | C:\Windows\System32\dllhost.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: COM Surrogate Exit code: 0 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4204 | C:\WINDOWS\system32\msiexec.exe /V | C:\Windows\System32\msiexec.exe | services.exe | ||||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows® installer Version: 5.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5064 | "C:\WINDOWS\SystemApps\Microsoft.Windows.Search_cw5n1h2txyewy\SearchApp.exe" -ServerName:CortanaUI.AppX8z9r6jm96hw4bsbneegw0kyxx296wr9t.mca | C:\Windows\SystemApps\Microsoft.Windows.Search_cw5n1h2txyewy\SearchApp.exe | svchost.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Search application Version: 10.0.19041.3996 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5240 | C:\WINDOWS\system32\DllHost.exe /Processid:{514B5E31-5596-422F-BE58-D804464683B5} | C:\Windows\System32\dllhost.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: COM Surrogate Exit code: 0 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5588 | "C:\WINDOWS\System32\rundll32.exe" werconcpl.dll, LaunchErcApp -queuereporting | C:\Windows\System32\rundll32.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows host process (Rundll32) Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5592 | C:\Users\admin\AppData\Local\Temp\{64EADA0C-25D4-4901-9F7A-DA935BC51EC7}\Inst_D1_6_v1702.exe /q"C:\Users\admin\AppData\Local\Temp\Inst_D1_6_v1702.exe" /tempdisk1folder"C:\Users\admin\AppData\Local\Temp\{64EADA0C-25D4-4901-9F7A-DA935BC51EC7}" /IS_temp | C:\Users\admin\AppData\Local\Temp\{64EADA0C-25D4-4901-9F7A-DA935BC51EC7}\Inst_D1_6_v1702.exe | Inst_D1_6_v1702.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
Total events
36 099
Read events
34 909
Write events
1 093
Delete events
97
Modification events
| (PID) Process: | (5064) SearchApp.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\CurrentVersion\AppContainer\Storage\microsoft.windows.search_cw5n1h2txyewy\SOFTWARE\Microsoft\Speech_OneCore\Isolated\A1hdl50UVDh2ZbG324Nx-6fZgntcGnHOs5kHLdmaJYE\HKEY_CURRENT_USER\SOFTWARE\Microsoft\Speech_OneCore\Recognizers |
| Operation: | write | Name: | DefaultTokenId |
Value: HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Speech_OneCore\Recognizers\Tokens\MS-1033-110-WINMO-DNN | |||
| (PID) Process: | (5064) SearchApp.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Search\Flighting |
| Operation: | delete value | Name: | CachedFeatureString |
Value: | |||
| (PID) Process: | (5064) SearchApp.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\SearchSettings |
| Operation: | write | Name: | IsMSACloudSearchEnabled |
Value: 0 | |||
| (PID) Process: | (5064) SearchApp.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\SearchSettings |
| Operation: | write | Name: | IsAADCloudSearchEnabled |
Value: 0 | |||
| (PID) Process: | (5064) SearchApp.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Search |
| Operation: | write | Name: | CortanaStateLastRun |
Value: 850BAB6700000000 | |||
| (PID) Process: | (5064) SearchApp.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\SearchSettings |
| Operation: | write | Name: | SafeSearchMode |
Value: 1 | |||
| (PID) Process: | (5064) SearchApp.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\CurrentVersion\AppContainer\Storage\microsoft.windows.search_cw5n1h2txyewy\Internet Explorer\DOMStorage\bing.com |
| Operation: | write | Name: | Total |
Value: 51223 | |||
| (PID) Process: | (5064) SearchApp.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Search\Flighting |
| Operation: | write | Name: | CachedFeatureString |
Value: | |||
| (PID) Process: | (5064) SearchApp.exe | Key: | \REGISTRY\A\{ee080948-b2ea-145a-6870-f9164b908eb9}\LocalState |
| Operation: | write | Name: | BINGIDENTITY_PROP_USEREMAIL |
Value: 00002EB4A4BA5F7CDB01 | |||
| (PID) Process: | (5064) SearchApp.exe | Key: | \REGISTRY\A\{ee080948-b2ea-145a-6870-f9164b908eb9}\LocalState |
| Operation: | write | Name: | BINGIDENTITY_PROP_ACCOUNTTYPETEXT |
Value: 00002EB4A4BA5F7CDB01 | |||
Executable files
13
Suspicious files
93
Text files
223
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 5592 | Inst_D1_6_v1702.exe | C:\Users\admin\AppData\Local\Temp\{64EADA0C-25D4-4901-9F7A-DA935BC51EC7}\Setup.INI | text | |
MD5:D07E0EB617F730CF7C40A00F12D41A6C | SHA256:ADCBB0B34754ACDFFC5D77CFBA72A6B115D3CB588000203AE565B093AC2A683B | |||
| 5880 | Inst_D1_6_v1702.exe | C:\Users\admin\AppData\Local\Temp\~648A.tmp | text | |
MD5:D07E0EB617F730CF7C40A00F12D41A6C | SHA256:ADCBB0B34754ACDFFC5D77CFBA72A6B115D3CB588000203AE565B093AC2A683B | |||
| 5592 | Inst_D1_6_v1702.exe | C:\Users\admin\AppData\Local\Temp\{64EADA0C-25D4-4901-9F7A-DA935BC51EC7}\0x0402.ini | text | |
MD5:CC9BC6AD5ACC94F2E2C238E7F3F10358 | SHA256:B6E838CC1C177818D4C93ECA05E2A8970CC140DDA04A4F685B0EEC84349E26A7 | |||
| 5880 | Inst_D1_6_v1702.exe | C:\Users\admin\AppData\Local\Temp\{64EADA0C-25D4-4901-9F7A-DA935BC51EC7}\_ISMSIDEL.INI | text | |
MD5:B3145D1F24BB88AA62D17F704C38188F | SHA256:2035C2BF5F1423E8BBC03AE989E2F3745E16E2CEE4088C662BD2B195185E50AD | |||
| 5064 | SearchApp.exe | C:\Users\admin\AppData\Local\Packages\Microsoft.Windows.Search_cw5n1h2txyewy\AC\Microsoft\CryptnetUrlCache\MetaData\26C212D9399727259664BDFCA073966E_F9F7D6A7ECE73106D2A8C63168CDA10D | binary | |
MD5:7351C4D34D018E80E581E4E0E90E820D | SHA256:D86B0587CA13EAC81104BF0A0DF08CC62790F04BEC54EAEC28777453347AFA4D | |||
| 5592 | Inst_D1_6_v1702.exe | C:\Users\admin\AppData\Local\Temp\~6584.tmp | text | |
MD5:D07E0EB617F730CF7C40A00F12D41A6C | SHA256:ADCBB0B34754ACDFFC5D77CFBA72A6B115D3CB588000203AE565B093AC2A683B | |||
| 5064 | SearchApp.exe | C:\Users\admin\AppData\Local\Packages\Microsoft.Windows.Search_cw5n1h2txyewy\AC\Microsoft\Internet Explorer\DOMStore\ZWUI0EBX\www.bing[1].xml | text | |
MD5:38933441DD01BBC7561215029695F858 | SHA256:E9754EC97E81BD5887644F6F5B3CCD66428A2CD1E30A67DBDBC7A3603FDE9733 | |||
| 5880 | Inst_D1_6_v1702.exe | C:\Users\admin\AppData\Local\Temp\~646A.tmp | text | |
MD5:D07E0EB617F730CF7C40A00F12D41A6C | SHA256:ADCBB0B34754ACDFFC5D77CFBA72A6B115D3CB588000203AE565B093AC2A683B | |||
| 5592 | Inst_D1_6_v1702.exe | C:\Users\admin\AppData\Local\Temp\{64EADA0C-25D4-4901-9F7A-DA935BC51EC7}\Декларация Обр.1 и 6.msi | executable | |
MD5:4A1015847F36C05F643CB3D6363CF22F | SHA256:792D11496BA6C48D7A38AAB5D028136ED164CEDE61FE6FC51AFC4B20C072F4C9 | |||
| 5064 | SearchApp.exe | C:\Users\admin\AppData\Local\Packages\Microsoft.Windows.Search_cw5n1h2txyewy\AC\AppCache\5Y734AMR\67\FgBbpIj0thGWZOh_xFnM9i4O7ek[1].css | text | |
MD5:908111EB0FFB1360D5DD61279C21703E | SHA256:1ED87CF425DED994B05A842271AB4D28A76F399E571688CF2E7B186F70DC3059 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
18
TCP/UDP connections
54
DNS requests
27
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
— | — | GET | 200 | 23.48.23.147:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
4712 | MoUsoCoreWorker.exe | GET | 200 | 23.48.23.147:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
1356 | svchost.exe | GET | 200 | 23.48.23.147:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
5064 | SearchApp.exe | GET | 200 | 184.30.131.245:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
5064 | SearchApp.exe | GET | 200 | 184.30.131.245:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | whitelisted |
6100 | SystemSettings.exe | GET | 200 | 184.30.131.245:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
1176 | svchost.exe | GET | 200 | 184.30.131.245:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
6100 | SystemSettings.exe | GET | 200 | 184.30.131.245:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAUZZSZEml49Gjh0j13P68w%3D | unknown | — | — | whitelisted |
5064 | SearchApp.exe | GET | 200 | 184.30.131.245:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAUZZSZEml49Gjh0j13P68w%3D | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
5064 | SearchApp.exe | 92.123.104.22:443 | — | Akamai International B.V. | DE | unknown |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
— | — | 51.124.78.146:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
— | — | 23.48.23.147:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
— | — | 23.35.229.160:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
1356 | svchost.exe | 23.48.23.147:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
4712 | MoUsoCoreWorker.exe | 23.48.23.147:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
5064 | SearchApp.exe | 92.123.104.24:443 | — | Akamai International B.V. | DE | unknown |
5064 | SearchApp.exe | 184.30.131.245:80 | ocsp.digicert.com | AKAMAI-AS | US | whitelisted |
5064 | SearchApp.exe | 204.79.197.222:443 | fp.msedge.net | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
www.microsoft.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
fp.msedge.net |
| whitelisted |
www.bing.com |
| whitelisted |
cxcs.microsoft.net |
| whitelisted |
settings-win.data.microsoft.com |
| whitelisted |
th.bing.com |
| whitelisted |
login.live.com |
| whitelisted |
go.microsoft.com |
| whitelisted |
browser.pipe.aria.microsoft.com |
| whitelisted |