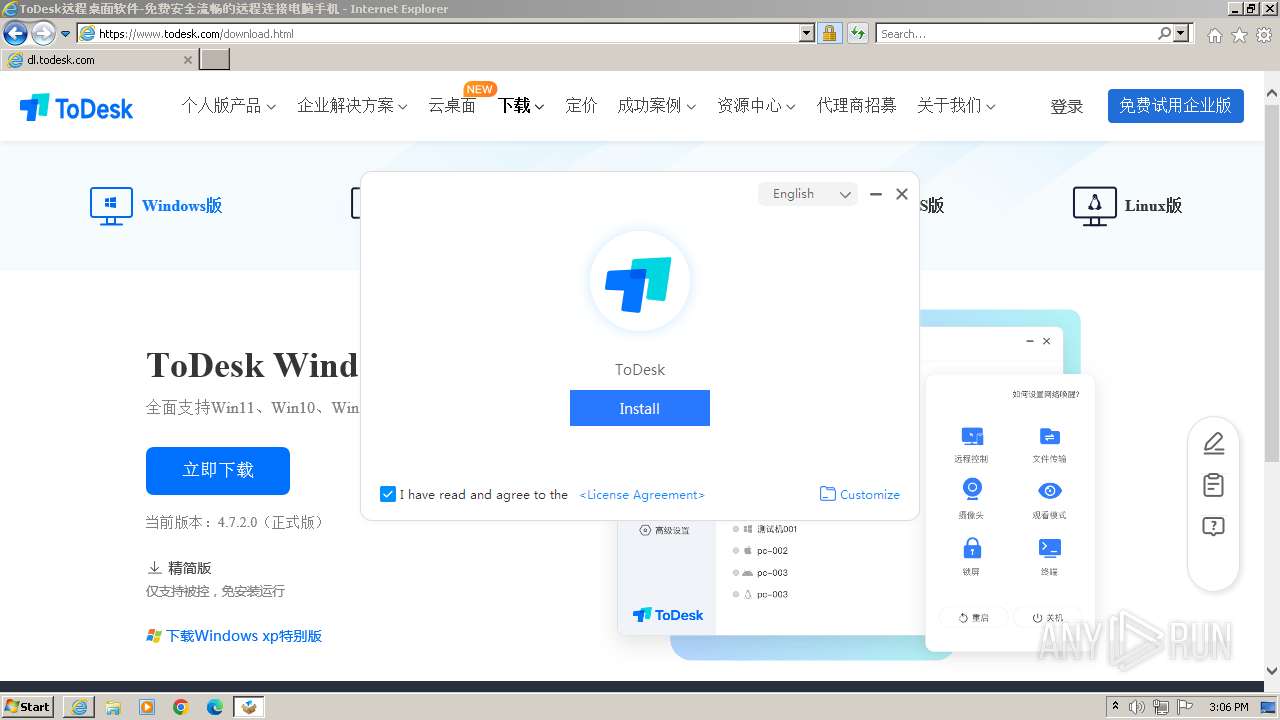
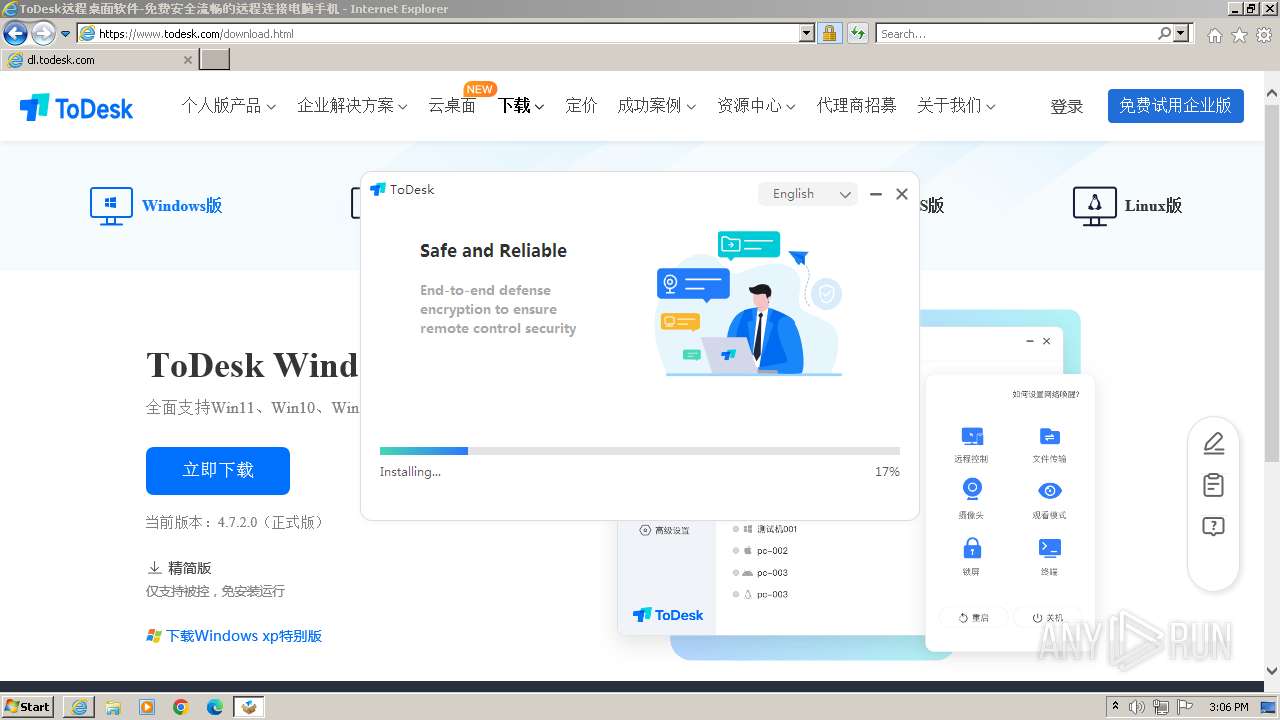
| URL: | www.todesk.com |
| Full analysis: | https://app.any.run/tasks/07559294-9ca6-4d43-9522-ac6002e61290 |
| Verdict: | Malicious activity |
| Analysis date: | November 10, 2023, 15:03:16 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MD5: | 0E1654A3395A66A7F45C4A45ED06CBA8 |
| SHA1: | 8BE2ECB870278C2074D88F482EFBA39E4D0881EB |
| SHA256: | 8CC9465B77E4F5BE55BB2E7029040ACF744133A16CB20917F712EEEE4B54C3A1 |
| SSDEEP: | 3:EUiZI:v |
MALICIOUS
Drops the executable file immediately after the start
- ToDesk_Setup.exe (PID: 3816)
SUSPICIOUS
Process requests binary or script from the Internet
- inst.exe (PID: 2376)
Connects to the server without a host name
- inst.exe (PID: 2376)
Reads the Internet Settings
- inst.exe (PID: 2376)
The process creates files with name similar to system file names
- ToDesk_Setup.exe (PID: 3816)
Starts application with an unusual extension
- ToDesk_Setup.exe (PID: 3816)
Starts CMD.EXE for commands execution
- ns83FE.tmp (PID: 476)
- ns8390.tmp (PID: 3780)
- ns84F9.tmp (PID: 2120)
- ns8567.tmp (PID: 2856)
Malware-specific behavior (creating "System.dll" in Temp)
- ToDesk_Setup.exe (PID: 3816)
Starts SC.EXE for service management
- cmd.exe (PID: 272)
- cmd.exe (PID: 988)
- cmd.exe (PID: 2836)
- cmd.exe (PID: 2940)
Drops a system driver (possible attempt to evade defenses)
- ToDesk_Setup.exe (PID: 3816)
Process drops legitimate windows executable
- ToDesk_Setup.exe (PID: 3816)
Uses NETSH.EXE to delete a firewall rule or allowed programs
- ns914F.tmp (PID: 2920)
- ns9289.tmp (PID: 3000)
- ns9365.tmp (PID: 2520)
Uses NETSH.EXE to add a firewall rule or allowed programs
- ns9440.tmp (PID: 3328)
- ns951C.tmp (PID: 2896)
- ns96C4.tmp (PID: 3980)
- ns97A0.tmp (PID: 3472)
- ns95F8.tmp (PID: 3836)
- ns987B.tmp (PID: 3532)
Executes as Windows Service
- ToDesk.exe (PID: 3904)
Application launched itself
- ToDesk.exe (PID: 3904)
INFO
Reads the computer name
- wmpnscfg.exe (PID: 3424)
- wmpnscfg.exe (PID: 4068)
- inst.exe (PID: 2376)
- ToDesk_Setup.exe (PID: 3816)
- ToDesk.exe (PID: 3588)
- ToDesk.exe (PID: 3904)
- ToDesk.exe (PID: 900)
- ToDesk.exe (PID: 3352)
Checks supported languages
- wmpnscfg.exe (PID: 4068)
- wmpnscfg.exe (PID: 3424)
- inst.exe (PID: 2376)
- ToDesk_Setup.exe (PID: 3816)
- ns8390.tmp (PID: 3780)
- ns84F9.tmp (PID: 2120)
- ns83FE.tmp (PID: 476)
- ns8567.tmp (PID: 2856)
- ns914F.tmp (PID: 2920)
- ns9289.tmp (PID: 3000)
- ns9440.tmp (PID: 3328)
- ns9365.tmp (PID: 2520)
- ns95F8.tmp (PID: 3836)
- ns96C4.tmp (PID: 3980)
- ns97A0.tmp (PID: 3472)
- ns987B.tmp (PID: 3532)
- ToDesk.exe (PID: 3588)
- ToDesk.exe (PID: 3904)
- ToDesk.exe (PID: 900)
- ns951C.tmp (PID: 2896)
- ToDesk.exe (PID: 3352)
The process uses the downloaded file
- iexplore.exe (PID: 3416)
Application launched itself
- iexplore.exe (PID: 3416)
Reads the machine GUID from the registry
- wmpnscfg.exe (PID: 4068)
- wmpnscfg.exe (PID: 3424)
- ToDesk.exe (PID: 3588)
- ToDesk.exe (PID: 3904)
- ToDesk.exe (PID: 3352)
Manual execution by a user
- wmpnscfg.exe (PID: 3424)
- wmpnscfg.exe (PID: 4068)
Drops the executable file immediately after the start
- iexplore.exe (PID: 3456)
- iexplore.exe (PID: 3416)
Create files in a temporary directory
- ToDesk_Setup.exe (PID: 3816)
Creates files in the program directory
- ToDesk_Setup.exe (PID: 3816)
- ToDesk.exe (PID: 3904)
Creates files or folders in the user directory
- ToDesk.exe (PID: 3352)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
98
Monitored processes
41
Malicious processes
3
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 272 | cmd.exe /c sc delete ToDesk_Service | C:\Windows\System32\cmd.exe | — | ns83FE.tmp | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 1060 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 372 | netsh advfirewall firewall delete rule name="ToDesk_Session" | C:\Windows\System32\netsh.exe | — | ns9365.tmp | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Network Command Shell Exit code: 1 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 476 | "C:\Users\admin\AppData\Local\Temp\nsq7249.tmp\ns83FE.tmp" cmd.exe /c sc delete ToDesk_Service | C:\Users\admin\AppData\Local\Temp\nsq7249.tmp\ns83FE.tmp | — | ToDesk_Setup.exe | |||||||||||
User: admin Integrity Level: HIGH Exit code: 1060 Modules
| |||||||||||||||
| 856 | sc stop ToDesk_Service | C:\Windows\System32\sc.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: A tool to aid in developing services for WindowsNT Exit code: 1060 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 900 | "C:\Program Files\ToDesk\ToDesk.exe" --hide --localPort=35600 | C:\Program Files\ToDesk\ToDesk.exe | — | ToDesk.exe | |||||||||||
User: admin Company: 海南有趣科技有限公司 (www.todesk.com) Integrity Level: MEDIUM Description: ToDesk远程控制客户端 Exit code: 1 Version: 4.7.2.0 Modules
| |||||||||||||||
| 988 | cmd.exe /c sc stop ToDesk_Service | C:\Windows\System32\cmd.exe | — | ns8390.tmp | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 1060 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 1416 | sc stop ToDesk_Service | C:\Windows\System32\sc.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: A tool to aid in developing services for WindowsNT Exit code: 1060 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1696 | "C:\Users\admin\Downloads\ToDesk_Setup.exe" | C:\Users\admin\Downloads\ToDesk_Setup.exe | — | inst.exe | |||||||||||
User: admin Company: ToDesk Remote Desktop Integrity Level: MEDIUM Description: ToDesk Exit code: 3221226540 Modules
| |||||||||||||||
| 2100 | sc delete ToDesk_Service | C:\Windows\System32\sc.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: A tool to aid in developing services for WindowsNT Exit code: 1060 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2120 | "C:\Users\admin\AppData\Local\Temp\nsq7249.tmp\ns84F9.tmp" cmd.exe /c sc stop ToDesk_Service | C:\Users\admin\AppData\Local\Temp\nsq7249.tmp\ns84F9.tmp | — | ToDesk_Setup.exe | |||||||||||
User: admin Integrity Level: HIGH Exit code: 1060 Modules
| |||||||||||||||
Total events
22 872
Read events
22 390
Write events
474
Delete events
8
Modification events
| (PID) Process: | (3416) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPDaysSinceLastAutoMigration |
Value: 0 | |||
| (PID) Process: | (3416) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPLastLaunchHighDateTime |
Value: 30847387 | |||
| (PID) Process: | (3416) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\UrlBlockManager |
| Operation: | write | Name: | NextCheckForUpdateHighDateTime |
Value: 30847437 | |||
| (PID) Process: | (3416) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (3416) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
| (PID) Process: | (3416) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\Main |
| Operation: | write | Name: | CompatibilityFlags |
Value: 0 | |||
| (PID) Process: | (3416) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (3416) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
| (PID) Process: | (3416) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 1 | |||
| (PID) Process: | (3416) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 0 | |||
Executable files
36
Suspicious files
54
Text files
128
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3456 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\57C8EDB95DF3F0AD4EE2DC2B8CFD4157 | binary | |
MD5:2B5CA27F0CEFF6CF39BCAE7753C2E357 | SHA256:AD2DAD270EB16FB27E2FEC2E92C6A15CA39281693D459560976E23029EA826CE | |||
| 3456 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\9D3EDE6CADAA3B22ADE14C3C7C385BF2 | binary | |
MD5:D4AC09CAD30BF68BFECB3806D6F961A3 | SHA256:1FF5105DDB08A7F81E2E904848A12E1C13CA50A57B3BAC8DC5C926C44DD65B69 | |||
| 3456 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\B039FEA45CB4CC4BBACFC013C7C55604_50D7940D5D3FEDD8634D83074C7A46A3 | binary | |
MD5:2EC9685F2CC88FECBB91B4610CD6CCEA | SHA256:64D94864F5CAB19BBCCA5B97870FA23D740D51664CCEE5619C6C650FB7ECA049 | |||
| 3456 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\MFAQUS6V\a120e66[1].css | text | |
MD5:EF22191F4D0FD6462759A05590A7A6C8 | SHA256:07CC309EF9BE2ABBB3B408E9BFEBB44E69FBC4D4D7BE3AD24DB65EF74ED6157A | |||
| 3456 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\YTOWV792\lowerie[1].js | text | |
MD5:3E17417830B6B2D267AC4BE15CDFF50C | SHA256:C7451FE71899775FF2657D79EC961CF259BAE9B043D13ADA7E0541940313E98B | |||
| 3456 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\MFAQUS6V\7ETCDF68.htm | html | |
MD5:0F242E8BCEE47A1C9DC22ABAD90C994C | SHA256:8770D3E5129B5B2EB04E47A9F5CB6E62A59ED9F7942544FCA7F99D554A043FAC | |||
| 3456 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\5IWPIAR9\5b795eb[1].css | text | |
MD5:450FFFC741045A9CF1F4AA38152B006B | SHA256:D99AC24A3EEF6605FA8C0595B20F54A07B79B9EBF6CB8F9E5698FF22B950BD9D | |||
| 3456 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\MFAQUS6V\cc64c71[1].css | text | |
MD5:14D0B997107A2D0CCFA581AE7CEE0C10 | SHA256:5DF55F6B4ED7FB81021D3534EDD82906BE4DE72EFB52A3BDB49B1CB5EBD585BF | |||
| 3456 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\DY534W2X\start[1].js | text | |
MD5:D7FDF29967134AD092DC9FEBB582A579 | SHA256:49DA596D3DD9E85C66FAB92A800D8C842880B20B9BA70BA55D49FF7A6EDCCDDB | |||
| 3456 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\9D3EDE6CADAA3B22ADE14C3C7C385BF2 | binary | |
MD5:FD25D03A3DADE1A345FABD445BCB7FFD | SHA256:220983245AF90D8C9A12BB7A66146F9B67B2376F7330F53624E622EF8D0ABC74 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
20
TCP/UDP connections
95
DNS requests
47
Threats
2
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
2376 | inst.exe | GET | — | 116.177.242.69:80 | http://update.todesk.com/windows/ToDesk_Setup_4.7.2.0_x86.exe | unknown | — | — | unknown |
3456 | iexplore.exe | GET | 302 | 43.152.26.221:80 | http://www.todesk.com/ | unknown | — | — | unknown |
3416 | iexplore.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | binary | 471 b | unknown |
3416 | iexplore.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAqvpsXKY8RRQeo74ffHUxc%3D | unknown | binary | 471 b | unknown |
3416 | iexplore.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEA177el9ggmWelJjG4vdGL0%3D | unknown | binary | 471 b | unknown |
2376 | inst.exe | GET | 200 | 43.138.245.192:80 | http://43.138.245.192/client.php?p=win7&x=32&d=2376 | unknown | binary | 324 b | unknown |
3416 | iexplore.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | binary | 471 b | unknown |
3456 | iexplore.exe | GET | 200 | 104.18.20.226:80 | http://ocsp2.globalsign.com/rootr3/ME4wTDBKMEgwRjAJBgUrDgMCGgUABBT1nGh%2FJBjWKnkPdZIzB1bqhelHBwQUj%2FBLf6guRSSuTVD6Y5qL3uLdG7wCDQHuXyId%2FGI71DM6hVc%3D | unknown | binary | 1.40 Kb | unknown |
3456 | iexplore.exe | GET | 200 | 142.250.185.227:80 | http://ocsp.pki.goog/gsr1/MFEwTzBNMEswSTAJBgUrDgMCGgUABBS3V7W2nAf4FiMTjpDJKg6%2BMgGqMQQUYHtmGkUNl8qJUC99BM00qP%2F8%2FUsCEHe9DWzbNvka6iEPxPBY0w0%3D | unknown | binary | 1.41 Kb | unknown |
3456 | iexplore.exe | GET | 200 | 142.250.185.227:80 | http://ocsp.pki.goog/gtsr1/ME4wTDBKMEgwRjAJBgUrDgMCGgUABBQwkcLWD4LqGJ7bE7B1XZsEbmfwUAQU5K8rJnEaK0gnhS9SZizv8IkTcT4CDQIDvFNZazTHGPUBUGY%3D | unknown | binary | 724 b | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
3456 | iexplore.exe | 43.152.26.221:80 | www.todesk.com | ACE | DE | unknown |
3456 | iexplore.exe | 43.152.26.221:443 | www.todesk.com | ACE | DE | unknown |
3456 | iexplore.exe | 184.24.77.202:80 | ctldl.windowsupdate.com | Akamai International B.V. | DE | unknown |
3456 | iexplore.exe | 104.18.20.226:80 | ocsp2.globalsign.com | CLOUDFLARENET | — | shared |
3456 | iexplore.exe | 104.18.21.226:80 | ocsp2.globalsign.com | CLOUDFLARENET | — | shared |
3456 | iexplore.exe | 142.250.185.227:80 | ocsp.pki.goog | GOOGLE | US | whitelisted |
3456 | iexplore.exe | 142.250.186.168:443 | www.googletagmanager.com | GOOGLE | US | unknown |
3456 | iexplore.exe | 175.43.23.247:443 | todeskcdnspeed.todesk.com | CHINA UNICOM China169 Backbone | CN | unknown |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
www.todesk.com |
| unknown |
ctldl.windowsupdate.com |
| whitelisted |
ocsp2.globalsign.com |
| whitelisted |
ocsp.globalsign.com |
| whitelisted |
www.googletagmanager.com |
| whitelisted |
todeskcdnspeed.todesk.com |
| unknown |
ocsp.pki.goog |
| whitelisted |
filespeed.3dgali.com |
| unknown |
region1.analytics.google.com |
| whitelisted |
stats.g.doubleclick.net |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2376 | inst.exe | Potential Corporate Privacy Violation | AV POLICY HTTP request for .exe file with no User-Agent |
2376 | inst.exe | Potential Corporate Privacy Violation | ET POLICY PE EXE or DLL Windows file download HTTP |
Process | Message |
|---|---|
inst.exe | C:\Users\admin\Downloads\ |
inst.exe | C:\Users\admin\Downloads\ToDesk_Setup.exe.tmp |
inst.exe | C:\Users\admin\Downloads\ToDesk_Setup.exe |
inst.exe | C:\Users\admin\Downloads\ToDesk_Setup.exe |
inst.exe | C:\Users\admin\Downloads\ |
inst.exe | C:\Users\admin\Downloads\ToDesk_Setup.exe.tmp |
ToDesk_Setup.exe | Window, forcegditext, true
|
ToDesk_Setup.exe | Window, showshadow, false
|
ToDesk_Setup.exe | Window, bktrans, true
|
ToDesk_Setup.exe | Window, shadowimage, images/shadow.png
|