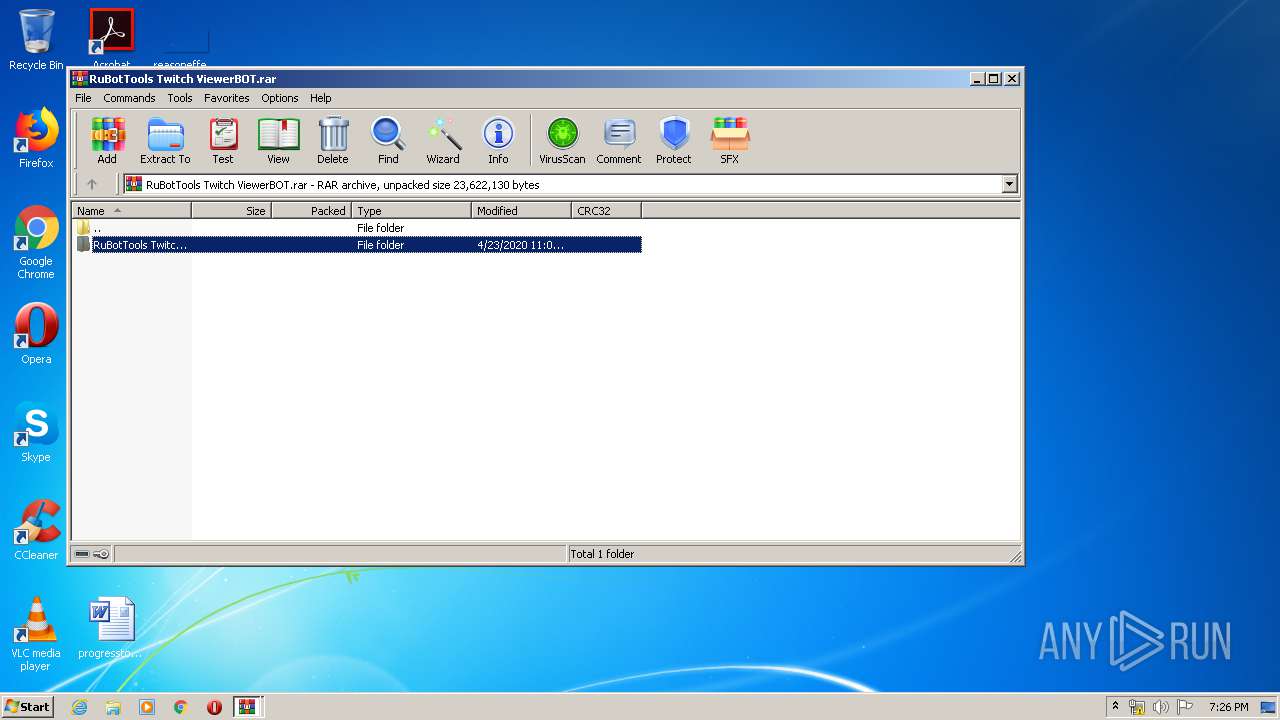
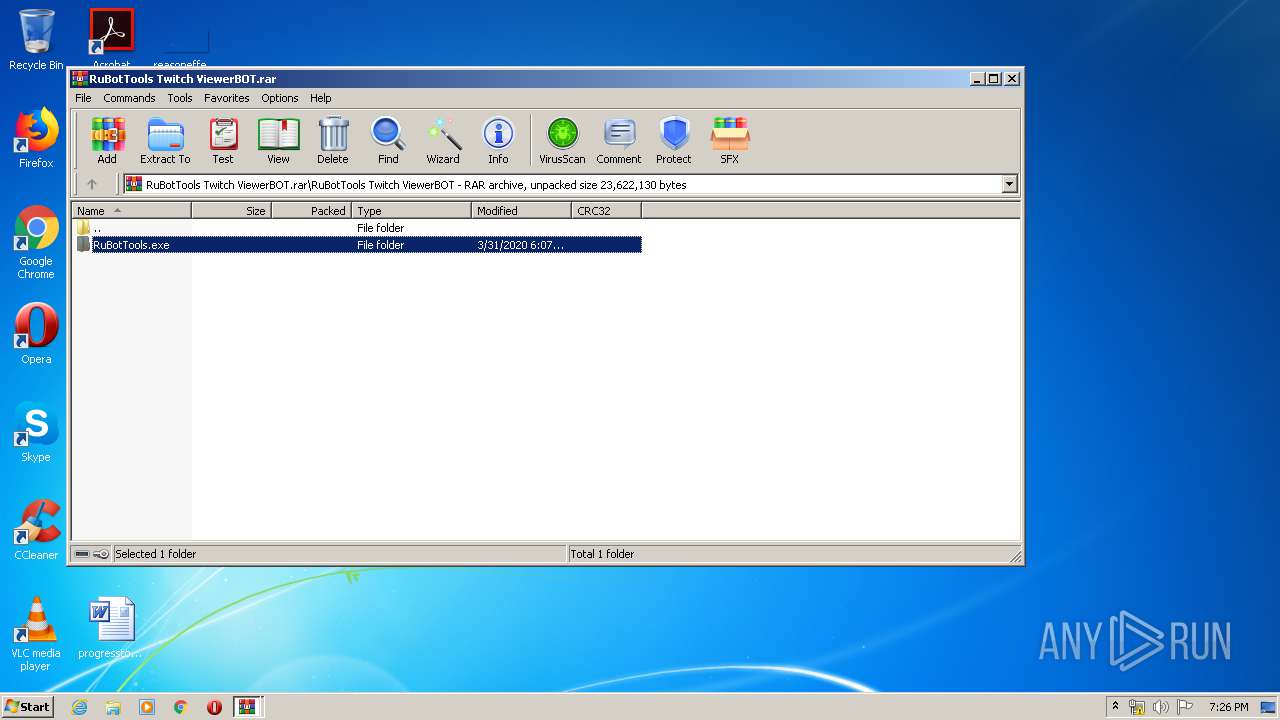
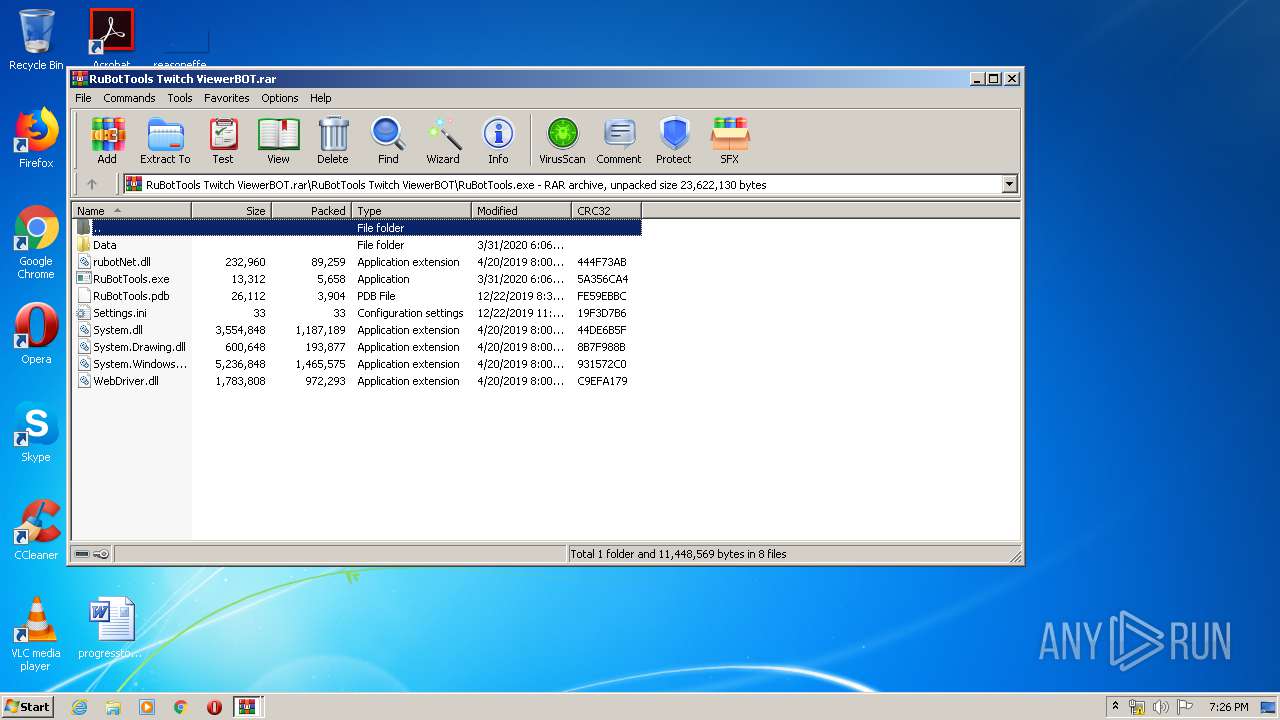
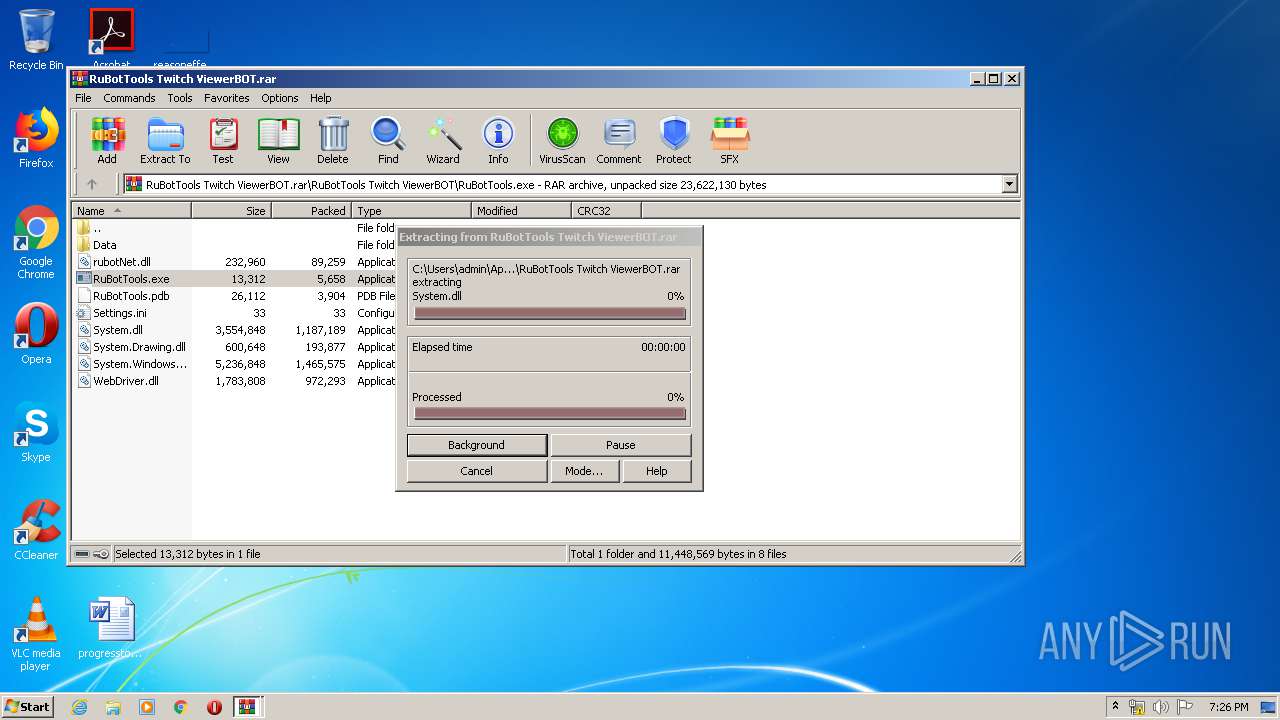
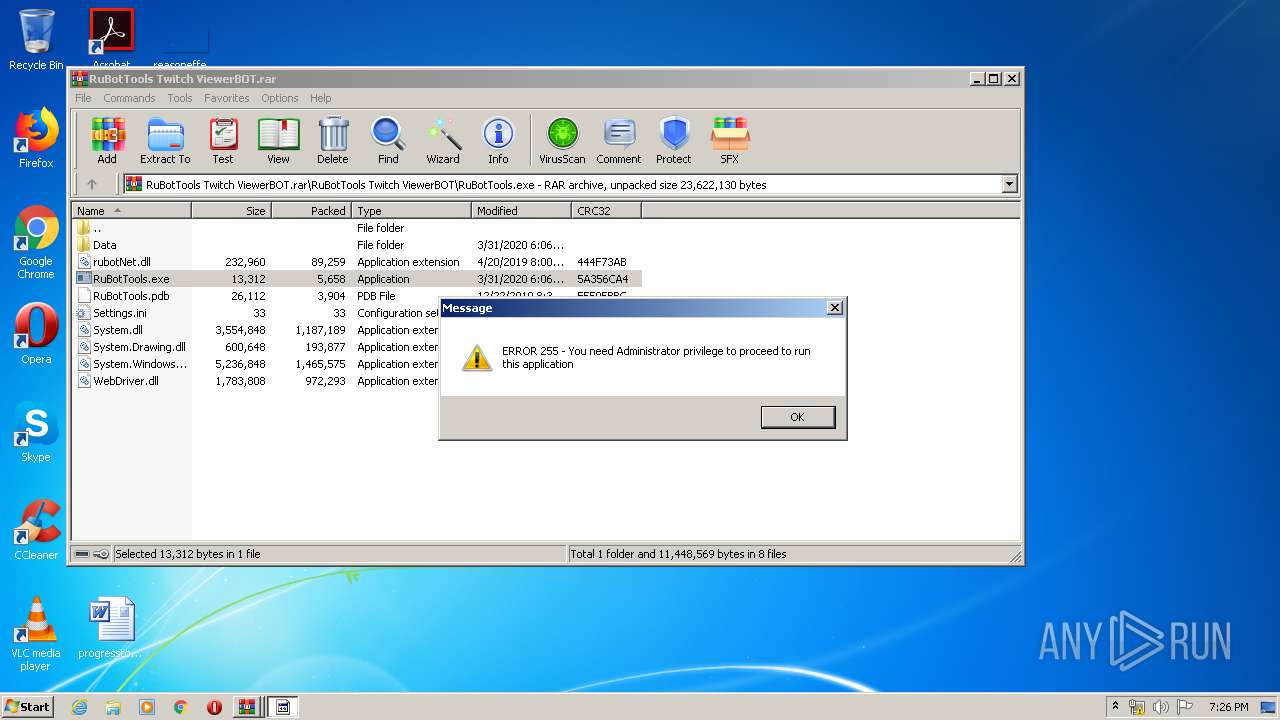
| File name: | Archive-0e45.zip |
| Full analysis: | https://app.any.run/tasks/7ae7599f-8909-4495-9b22-3eeeba4960af |
| Verdict: | Malicious activity |
| Analysis date: | May 30, 2020, 18:25:45 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v2.0 to extract |
| MD5: | C23C69BDAB63099F1B0EE16631D299C0 |
| SHA1: | 0F41EE8DE5D78530774C8D9D7AFDA261C90D26B6 |
| SHA256: | 8CB369CF3BA0300A96C3CBD2507F39959F08FA901171FA79F7E082DDA7BFFB9B |
| SSDEEP: | 98304:+/mTQ3nUnSGZOUIaZJ/QCYcFxspQ5nVa9H6hcDh5A+MUzbGf3nUnSGZOUIa8J/Ee:KBjGIYQHcGSW62/IjGIjEHcGSW62yh |
MALICIOUS
Application was dropped or rewritten from another process
- RuBotTools.exe (PID: 1004)
- RuTools.exe (PID: 860)
Loads dropped or rewritten executable
- RuBotTools.exe (PID: 1004)
- RuTools.exe (PID: 860)
Writes to a start menu file
- RuBotTools.exe (PID: 1004)
SUSPICIOUS
Application launched itself
- WinRAR.exe (PID: 2732)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 2880)
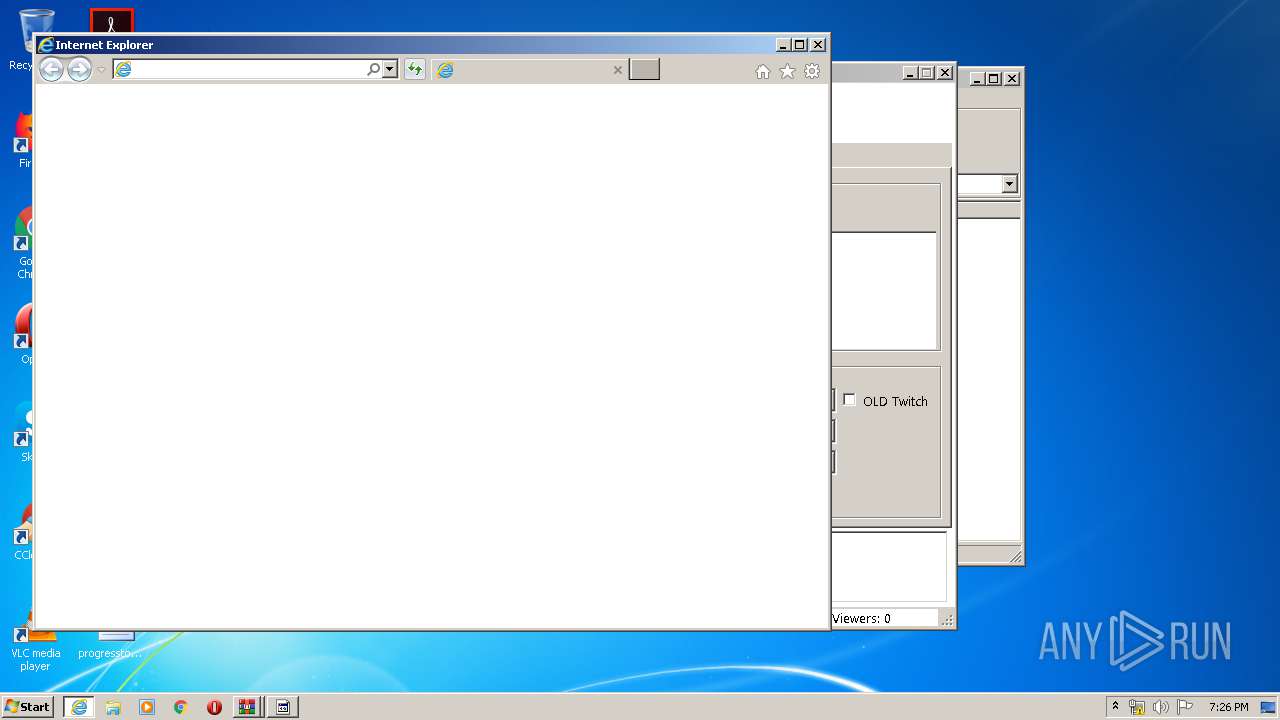
Starts Internet Explorer
- RuTools.exe (PID: 860)
Creates files in the user directory
- RuBotTools.exe (PID: 1004)
INFO
Dropped object may contain Bitcoin addresses
- WinRAR.exe (PID: 2880)
- iexplore.exe (PID: 2416)
Creates files in the user directory
- iexplore.exe (PID: 2416)
Changes internet zones settings
- iexplore.exe (PID: 3936)
Reads internet explorer settings
- iexplore.exe (PID: 2416)
Reads Internet Cache Settings
- iexplore.exe (PID: 2416)
- iexplore.exe (PID: 3936)
Application launched itself
- iexplore.exe (PID: 3936)
Reads settings of System Certificates
- iexplore.exe (PID: 3936)
- iexplore.exe (PID: 2416)
Adds / modifies Windows certificates
- iexplore.exe (PID: 3936)
Changes settings of System certificates
- iexplore.exe (PID: 3936)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 20 |
|---|---|
| ZipBitFlag: | 0x0808 |
| ZipCompression: | None |
| ZipModifyDate: | 2020:04:24 10:31:05 |
| ZipCRC: | 0x7e8bb955 |
| ZipCompressedSize: | 8509164 |
| ZipUncompressedSize: | 8509164 |
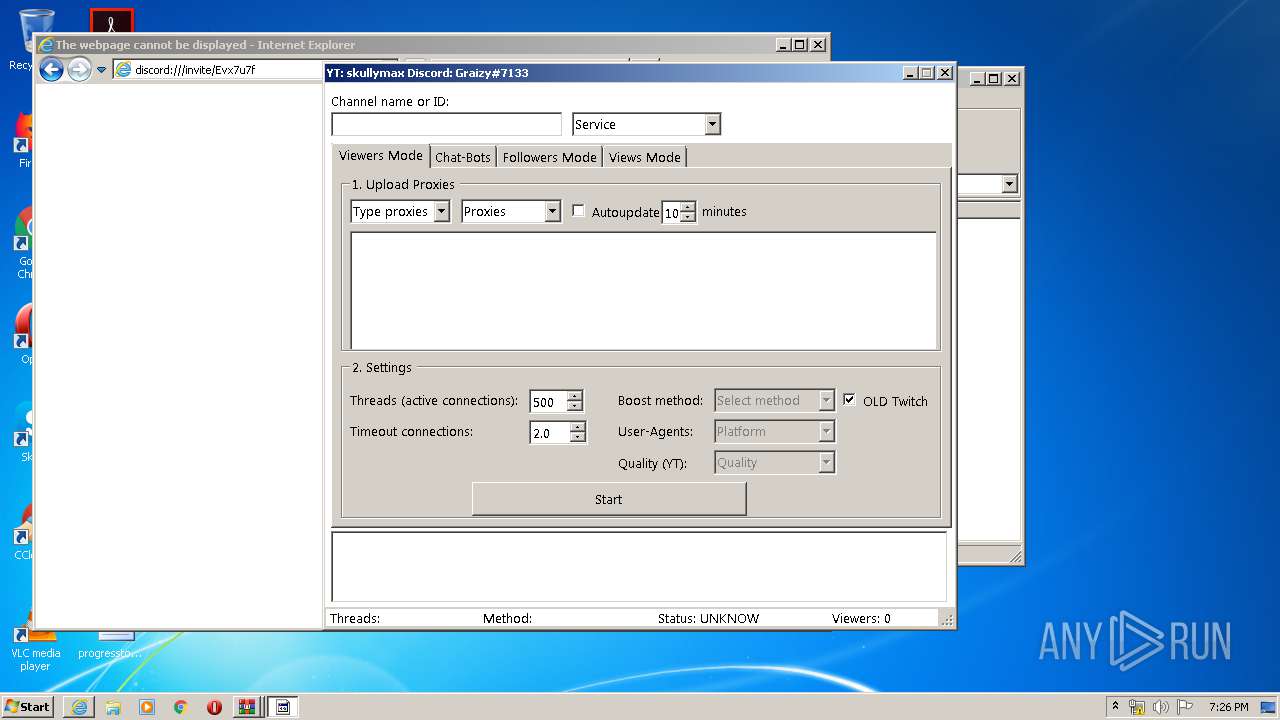
| ZipFileName: | RuBotTools Twitch ViewerBOT.rar |
Total processes
42
Monitored processes
6
Malicious processes
1
Suspicious processes
3
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
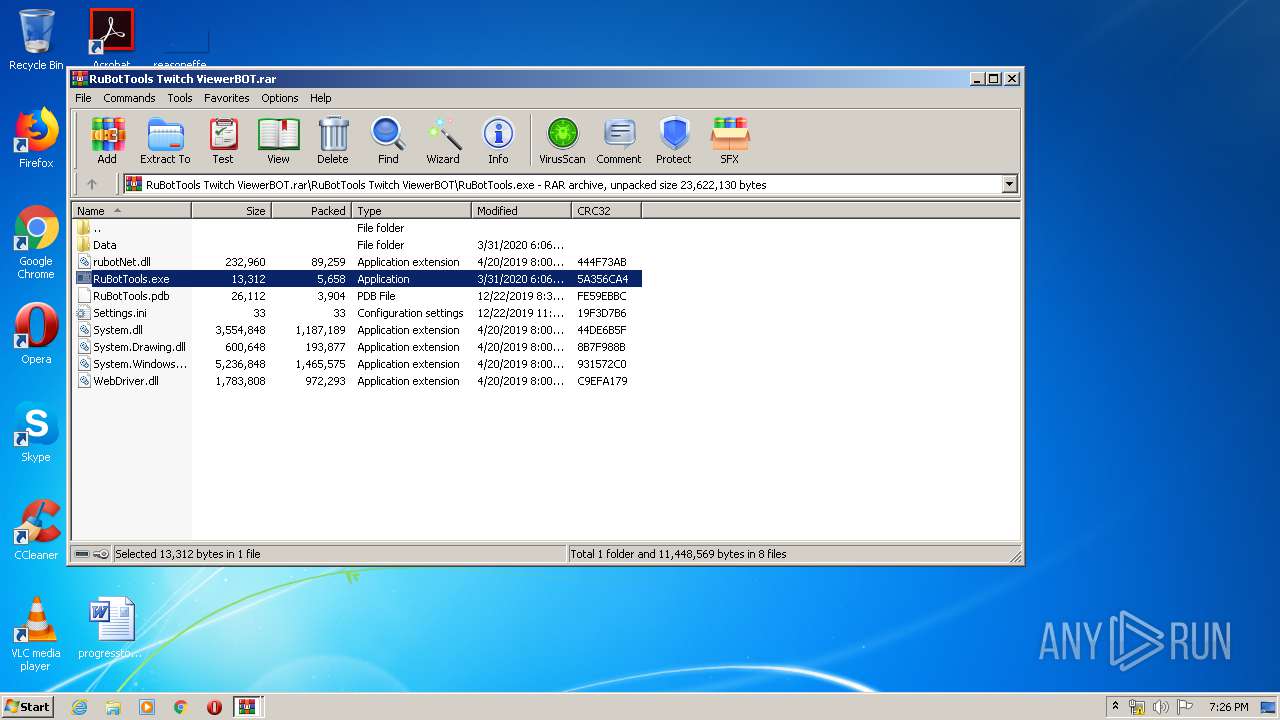
| 860 | "C:\Users\admin\AppData\Local\Temp\Rar$EXa2880.2888\RuBotTools Twitch ViewerBOT\RuBotTools.exe\Data\RuTools.exe" | C:\Users\admin\AppData\Local\Temp\Rar$EXa2880.2888\RuBotTools Twitch ViewerBOT\RuBotTools.exe\Data\RuTools.exe | — | WinRAR.exe | |||||||||||
User: admin Company: RuBot.OVH Integrity Level: MEDIUM Description: RuBot_Tools Exit code: 0 Version: 6.6.7.0 Modules
| |||||||||||||||
| 1004 | "C:\Users\admin\AppData\Local\Temp\Rar$EXa2880.1800\RuBotTools Twitch ViewerBOT\RuBotTools.exe\RuBotTools.exe" | C:\Users\admin\AppData\Local\Temp\Rar$EXa2880.1800\RuBotTools Twitch ViewerBOT\RuBotTools.exe\RuBotTools.exe | WinRAR.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Description: interface Exit code: 0 Version: 1.0.0.0 Modules
| |||||||||||||||
| 2416 | "C:\Program Files\Internet Explorer\iexplore.exe" SCODEF:3936 CREDAT:267521 /prefetch:2 | C:\Program Files\Internet Explorer\iexplore.exe | iexplore.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Internet Explorer Exit code: 0 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
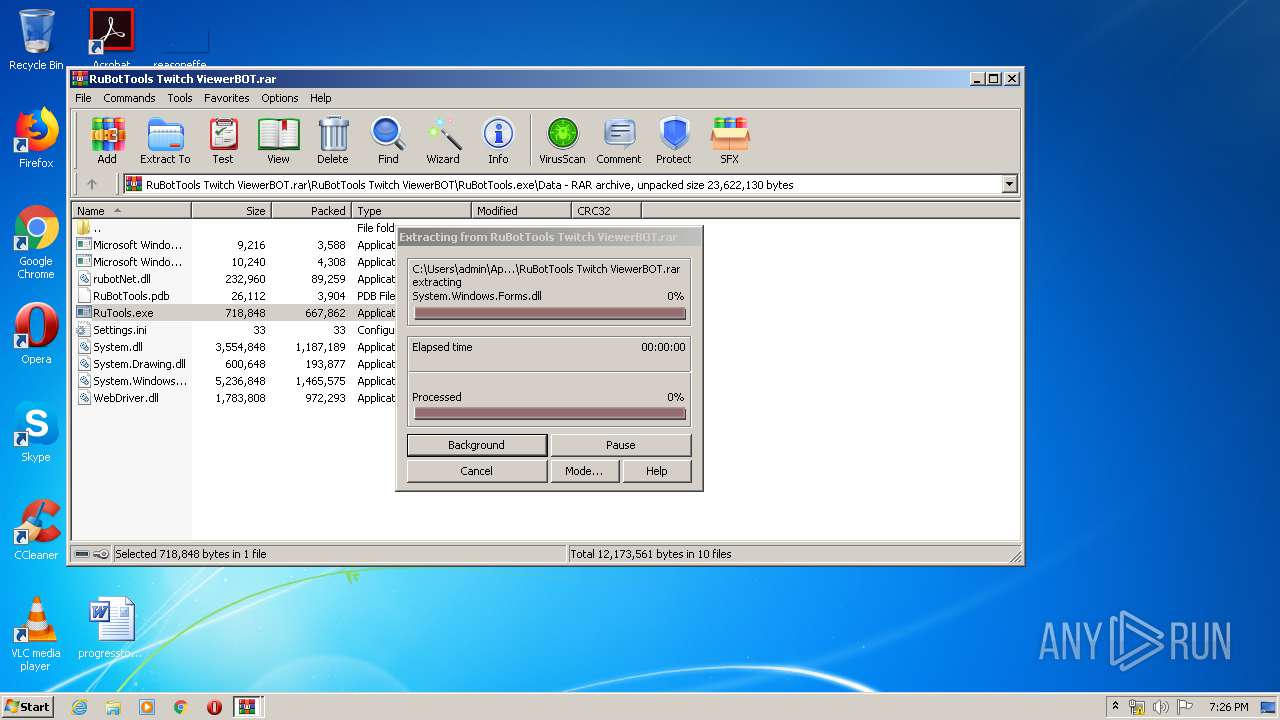
| 2732 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\AppData\Local\Temp\Archive-0e45.zip" | C:\Program Files\WinRAR\WinRAR.exe | — | explorer.exe | |||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.60.0 Modules
| |||||||||||||||
| 2880 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\AppData\Local\Temp\Rar$DIa2732.511\RuBotTools Twitch ViewerBOT.rar" | C:\Program Files\WinRAR\WinRAR.exe | WinRAR.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.60.0 Modules
| |||||||||||||||
| 3936 | "C:\Program Files\Internet Explorer\iexplore.exe" https://discord.gg/Evx7u7f | C:\Program Files\Internet Explorer\iexplore.exe | RuTools.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Internet Explorer Exit code: 0 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
Total events
6 512
Read events
1 726
Write events
3 213
Delete events
1 573
Modification events
| (PID) Process: | (2732) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (2732) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (2732) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\12F\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (2732) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\12F\52C64B7E |
| Operation: | write | Name: | @C:\Windows\system32\NetworkExplorer.dll,-1 |
Value: Network | |||
| (PID) Process: | (2732) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\Archive-0e45.zip | |||
| (PID) Process: | (2732) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (2732) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (2732) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (2732) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (2732) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 0 | |||
Executable files
28
Suspicious files
14
Text files
37
Unknown types
19
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2732 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DIa2732.511\RuBotTools Twitch ViewerBOT.rar | — | |
MD5:— | SHA256:— | |||
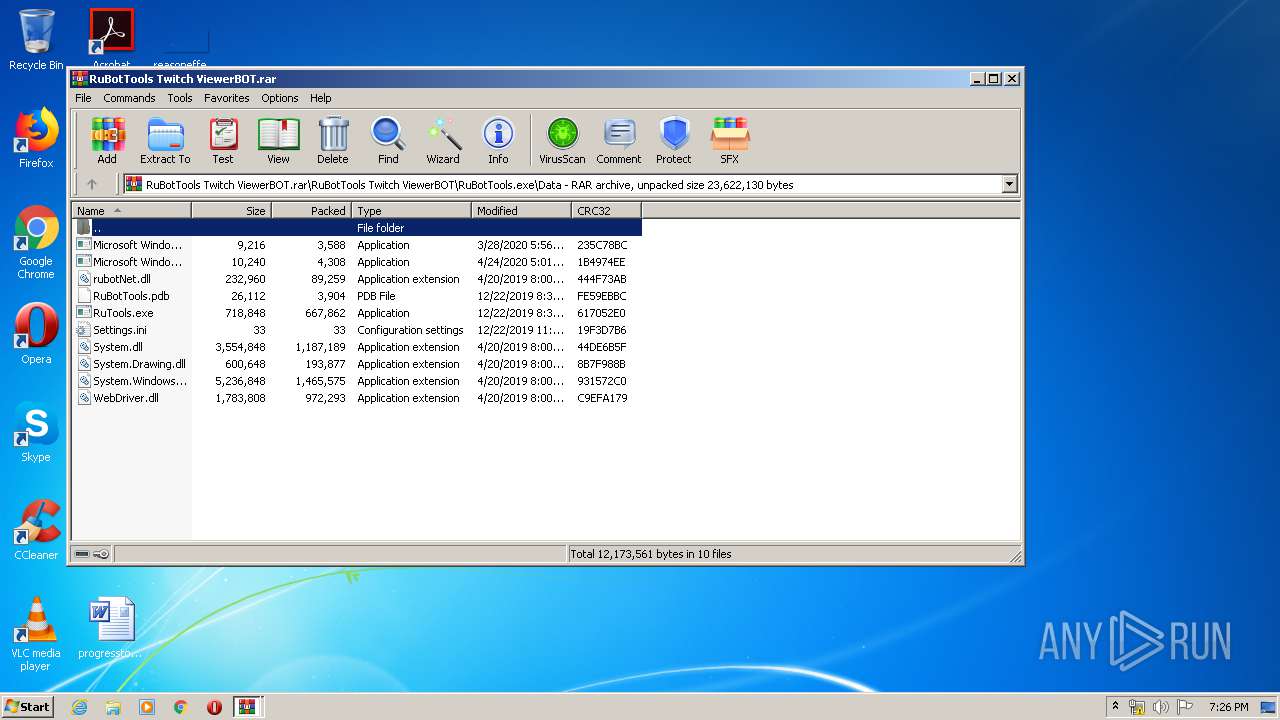
| 2880 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa2880.1800\RuBotTools Twitch ViewerBOT\RuBotTools.exe\RuBotTools.exe | executable | |
MD5:— | SHA256:— | |||
| 1004 | RuBotTools.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Start Menu\Programs\Startup\Microsoft Startup.lnk | lnk | |
MD5:— | SHA256:— | |||
| 2880 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa2880.1800\RuBotTools Twitch ViewerBOT\RuBotTools.exe\Data\RuBotTools.pdb | pdb | |
MD5:341857FE147A98E1D9762558F79C5462 | SHA256:096EFB49057785421801697431324917531C58D0B82BEB17A04954E90B81128A | |||
| 2880 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa2880.1800\RuBotTools Twitch ViewerBOT\RuBotTools.exe\Data\Microsoft Windows Protocol Monitor.exe | executable | |
MD5:61FCE223872024B0ECB0BB2A7FFB7C47 | SHA256:4B5069B9708A8E97B17AF6AA96CF2112877A675B4DBC1F6DBC2601B494B35D11 | |||
| 2880 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa2880.1800\RuBotTools Twitch ViewerBOT\RuBotTools.exe\Data\RuTools.exe | executable | |
MD5:DD77563B285AA93793C04C2EDDCA3708 | SHA256:671C0DC9A209FAEB501C7C17E7D9014D97C8B22000EFAFE8E4F215CA26ED89CA | |||
| 2880 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa2880.1800\RuBotTools Twitch ViewerBOT\RuBotTools.exe\Data\Microsoft Windows Protocol Services Host.exe | executable | |
MD5:7E4EC49968CDFEB455C1F56C5A944287 | SHA256:C68300968C576203725E09EDF1AC9B069B903EE06A4321C8C8FE5582898C10E4 | |||
| 2880 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa2880.1800\RuBotTools Twitch ViewerBOT\RuBotTools.exe\Data\Settings.ini | text | |
MD5:B9A2CA72F3080F67A4078EC056FA37D9 | SHA256:32B9AA24C0E5B6001BDFF069E58ED0C366A8EF4E2C5DE4B6F9AEAD572FCCF4F6 | |||
| 2880 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa2880.1800\RuBotTools Twitch ViewerBOT\RuBotTools.exe\Data\System.dll | executable | |
MD5:C4327ED4F66AA82D06291392EE738EFD | SHA256:C622798E5ECB5FFF65B90250A53B9FFDDAD686595177943BEF7D0FD8F44896F8 | |||
| 2880 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa2880.1800\RuBotTools Twitch ViewerBOT\RuBotTools.exe\Data\rubotNet.dll | executable | |
MD5:631EE3DF926389070956071F2B17F2C5 | SHA256:7D8908D90FD3EDE3C0A72A2BF7847CB96A7182552B1999280EACC31CDBD29EA8 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
9
TCP/UDP connections
15
DNS requests
8
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
2416 | iexplore.exe | GET | 200 | 151.139.128.14:80 | http://ocsp.comodoca.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBRTtU9uFqgVGHhJwXZyWCNXmVR5ngQUoBEKIz6W8Qfs4q8p74Klf9AwpLQCEBblhnjgcJQ5S9%2FbTvymO98%3D | US | der | 471 b | whitelisted |
2416 | iexplore.exe | GET | 200 | 151.139.128.14:80 | http://ocsp.comodoca.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBRTtU9uFqgVGHhJwXZyWCNXmVR5ngQUoBEKIz6W8Qfs4q8p74Klf9AwpLQCEBblhnjgcJQ5S9%2FbTvymO98%3D | US | der | 471 b | whitelisted |
2416 | iexplore.exe | GET | 200 | 151.139.128.14:80 | http://ocsp.comodoca4.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTOpjOEf6LG1z52jqAxwDlTxoaOCgQUQAlhZ%2FC8g3FP3hIILG%2FU1Ct2PZYCEDsJGKKiFxWJllawuNqPxXw%3D | US | der | 278 b | whitelisted |
2416 | iexplore.exe | GET | 200 | 151.139.128.14:80 | http://ocsp.comodoca4.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrJdiQ%2Ficg9B19asFe73bPYs%2BreAQUdXGnGUgZvJ2d6kFH35TESHeZ03kCEFslzmkHxCZVZtM5DJmpVK0%3D | US | der | 313 b | whitelisted |
2416 | iexplore.exe | GET | 200 | 151.139.128.14:80 | http://ocsp.comodoca4.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrJdiQ%2Ficg9B19asFe73bPYs%2BreAQUdXGnGUgZvJ2d6kFH35TESHeZ03kCEFslzmkHxCZVZtM5DJmpVK0%3D | US | der | 313 b | whitelisted |
2416 | iexplore.exe | GET | 200 | 151.139.128.14:80 | http://ocsp.comodoca4.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTOpjOEf6LG1z52jqAxwDlTxoaOCgQUQAlhZ%2FC8g3FP3hIILG%2FU1Ct2PZYCEDsJGKKiFxWJllawuNqPxXw%3D | US | der | 278 b | whitelisted |
3936 | iexplore.exe | GET | 200 | 204.79.197.200:80 | http://www.bing.com/favicon.ico | US | image | 237 b | whitelisted |
2416 | iexplore.exe | GET | 200 | 151.139.128.14:80 | http://ocsp.comodoca4.com/MFIwUDBOMEwwSjAJBgUrDgMCGgUABBTOpjOEf6LG1z52jqAxwDlTxoaOCgQUQAlhZ%2FC8g3FP3hIILG%2FU1Ct2PZYCEQCML6NXQdejdBJDG5j4aa9U | US | der | 280 b | whitelisted |
2416 | iexplore.exe | GET | 200 | 151.139.128.14:80 | http://ocsp.comodoca4.com/MFIwUDBOMEwwSjAJBgUrDgMCGgUABBTOpjOEf6LG1z52jqAxwDlTxoaOCgQUQAlhZ%2FC8g3FP3hIILG%2FU1Ct2PZYCEQCML6NXQdejdBJDG5j4aa9U | US | der | 280 b | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
3936 | iexplore.exe | 204.79.197.200:80 | www.bing.com | Microsoft Corporation | US | whitelisted |
2416 | iexplore.exe | 162.159.135.234:443 | discord.gg | Cloudflare Inc | — | shared |
2416 | iexplore.exe | 151.139.128.14:80 | ocsp.comodoca.com | Highwinds Network Group, Inc. | US | suspicious |
— | — | 162.159.135.232:443 | discord.com | Cloudflare Inc | — | malicious |
2416 | iexplore.exe | 162.159.135.232:443 | discord.com | Cloudflare Inc | — | malicious |
DNS requests
Domain | IP | Reputation |
|---|---|---|
discord.gg |
| whitelisted |
ocsp.comodoca.com |
| whitelisted |
ocsp.comodoca4.com |
| whitelisted |
discord.com |
| whitelisted |
api.bing.com |
| whitelisted |
www.bing.com |
| whitelisted |