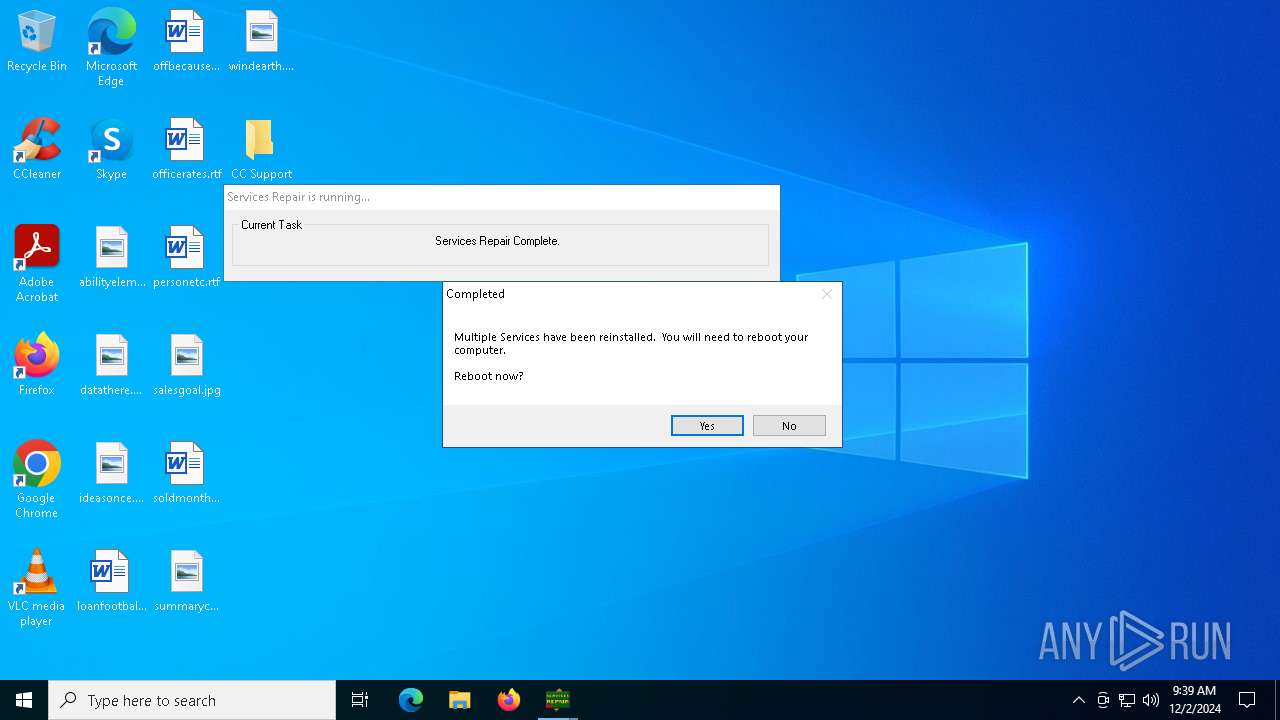
| File name: | ServicesRepair.exe |
| Full analysis: | https://app.any.run/tasks/4f70d7d9-0428-4ccd-ba98-9043a63c41f2 |
| Verdict: | Malicious activity |
| Analysis date: | December 02, 2024, 09:38:43 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/vnd.microsoft.portable-executable |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows, 4 sections |
| MD5: | FFF0BD7669C420AF07BF6E6C1DF7CA3D |
| SHA1: | 0342FE4E93ECA8929CCA6ECE39FC708233723FD6 |
| SHA256: | 8CABC5DFDA708D6C6FB7E3EAEE83C050DD913DA623012CFE2D50C3709F7038C5 |
| SSDEEP: | 98304:eZJ3XNrYQ9Om9OLkYrD79ZWL98WvQnC9qi1PfvLKMMjWnOhJgsPfhltJQ/trv9It:ilakXnI0k |
MALICIOUS
No malicious indicators.SUSPICIOUS
Reads security settings of Internet Explorer
- ServicesRepair.exe (PID: 6188)
Application launched itself
- ServicesRepair.exe (PID: 6188)
- cmd.exe (PID: 6336)
Executable content was dropped or overwritten
- ServicesRepair.exe (PID: 6360)
- ServicesRepair_x64.exe (PID: 6404)
Likely accesses (executes) a file from the Public directory
- ServicesRepair_x64.exe (PID: 6404)
- cmd.exe (PID: 6336)
Executing commands from a ".bat" file
- ServicesRepair_x64.exe (PID: 6404)
Starts CMD.EXE for commands execution
- ServicesRepair_x64.exe (PID: 6404)
- cmd.exe (PID: 6336)
Using 'findstr.exe' to search for text patterns in files and output
- cmd.exe (PID: 6336)
INFO
Checks supported languages
- ServicesRepair.exe (PID: 6188)
- ServicesRepair.exe (PID: 6360)
Reads mouse settings
- ServicesRepair.exe (PID: 6188)
- ServicesRepair.exe (PID: 6360)
Reads the computer name
- ServicesRepair.exe (PID: 6188)
- ServicesRepair.exe (PID: 6360)
Process checks computer location settings
- ServicesRepair.exe (PID: 6188)
Create files in a temporary directory
- ServicesRepair.exe (PID: 6360)
The process uses AutoIt
- ServicesRepair_x64.exe (PID: 6404)
Checks operating system version
- cmd.exe (PID: 6336)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win32 Executable MS Visual C++ (generic) (42.2) |
|---|---|---|
| .exe | | | Win64 Executable (generic) (37.3) |
| .dll | | | Win32 Dynamic Link Library (generic) (8.8) |
| .exe | | | Win32 Executable (generic) (6) |
| .exe | | | Generic Win/DOS Executable (2.7) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2012:01:29 21:32:28+00:00 |
| ImageFileCharacteristics: | No relocs, Executable, Large address aware, 32-bit |
| PEType: | PE32 |
| LinkerVersion: | 10 |
| CodeSize: | 526336 |
| InitializedDataSize: | 449536 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x165c1 |
| OSVersion: | 5 |
| ImageVersion: | - |
| SubsystemVersion: | 5 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 1.0.0.3 |
| ProductVersionNumber: | 3.3.8.1 |
| FileFlagsMask: | 0x0000 |
| FileFlags: | (none) |
| FileOS: | Win32 |
| ObjectFileType: | Unknown |
| FileSubtype: | - |
| LanguageCode: | English (British) |
| CharacterSet: | Unicode |
| FileVersion: | 1.0.0.3 |
Total processes
138
Monitored processes
15
Malicious processes
4
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1476 | C:\WINDOWS\system32\cmd.exe /S /D /c" ver " | C:\Windows\System32\cmd.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1876 | findstr /i "6\.1\." | C:\Windows\System32\findstr.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Find String (QGREP) Utility Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2076 | findstr /i "5\.1\." | C:\Windows\System32\findstr.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Find String (QGREP) Utility Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3848 | C:\WINDOWS\system32\cmd.exe /S /D /c" ver " | C:\Windows\System32\cmd.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5000 | findstr /i "5\.2\." | C:\Windows\System32\findstr.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Find String (QGREP) Utility Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5776 | C:\WINDOWS\system32\cmd.exe /S /D /c" ver " | C:\Windows\System32\cmd.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6092 | findstr /i "6\.0\." | C:\Windows\System32\findstr.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Find String (QGREP) Utility Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
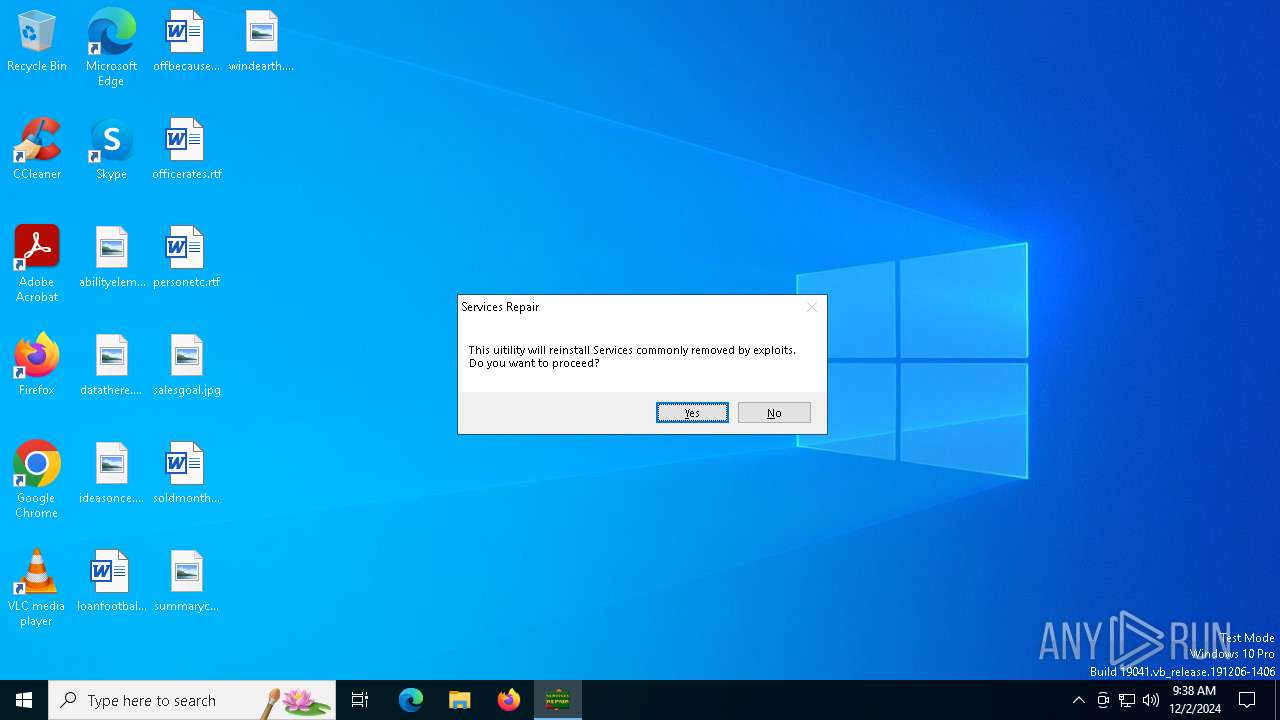
| 6188 | "C:\Users\admin\AppData\Local\Temp\ServicesRepair.exe" | C:\Users\admin\AppData\Local\Temp\ServicesRepair.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Version: 1.0.0.3 Modules
| |||||||||||||||
| 6224 | C:\WINDOWS\system32\cmd.exe /S /D /c" ver " | C:\Windows\System32\cmd.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6228 | findstr /i "5\.0\." | C:\Windows\System32\findstr.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Find String (QGREP) Utility Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
3 156
Read events
3 155
Write events
1
Delete events
0
Modification events
| (PID) Process: | (6404) ServicesRepair_x64.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Shell Extensions\Cached |
| Operation: | write | Name: | {2781761E-28E0-4109-99FE-B9D127C57AFE} {56FFCC30-D398-11D0-B2AE-00A0C908FA49} 0xFFFF |
Value: 0100000000000000D49228199E44DB01 | |||
Executable files
2
Suspicious files
4
Text files
42
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
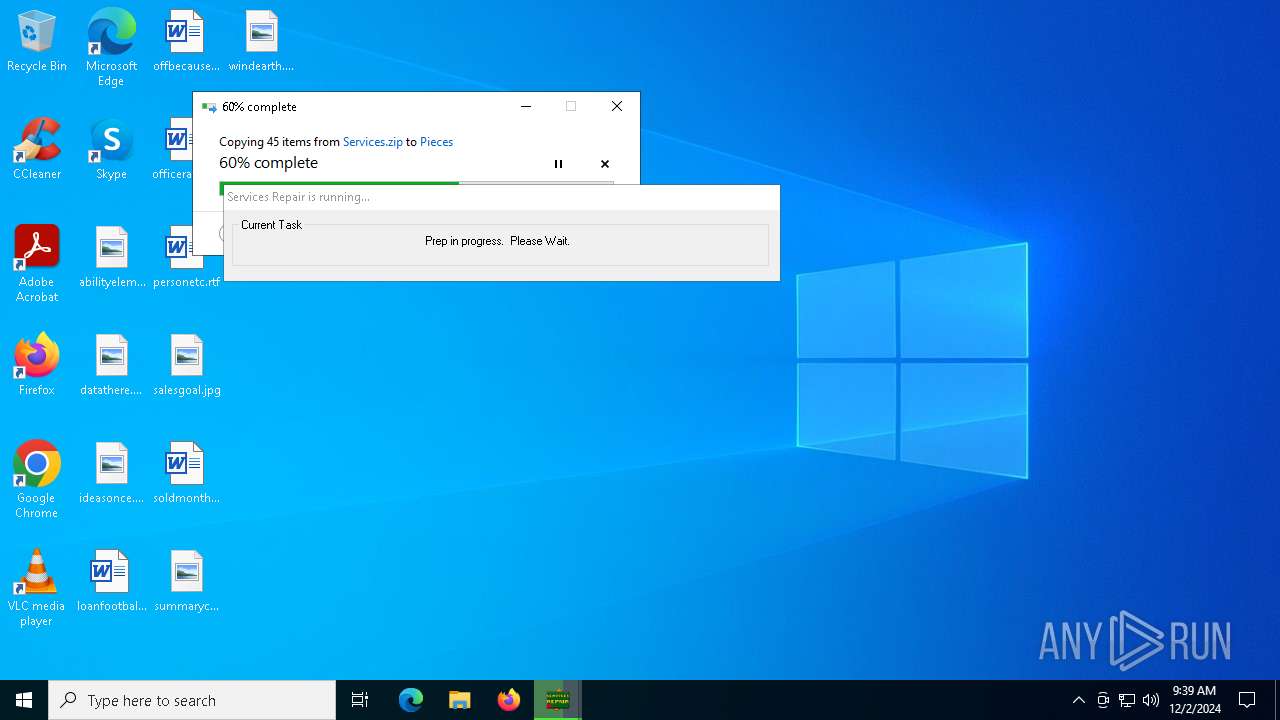
| 6404 | ServicesRepair_x64.exe | C:\Users\Public\Desktop\CC Support\Tools\ServicesRepair\Pieces\Vista\MpsSvc.sddl | csv | |
MD5:7AC4D8802167DF52586B56DCA97F4427 | SHA256:9405A54B494999BBD88091CEEA225580EB812ABA1380878EE547FB61CA770ABC | |||
| 6404 | ServicesRepair_x64.exe | C:\Users\admin\AppData\Local\Temp\aut1711.tmp | compressed | |
MD5:CAC0A919FE55CAAFFAC56BAEFC037444 | SHA256:F0C2B05BABF6298623DA73D62A289BE9A3408D30E982E5875D385617C15CA775 | |||
| 6360 | ServicesRepair.exe | C:\Users\admin\AppData\Local\Temp\aut6E5D.tmp | binary | |
MD5:8325AC325F2578553805F5B37776FD53 | SHA256:199BDB022C83FC0EC1A62B874B4494B8B96734505A3E989BCD1E7B0A9A32C6FC | |||
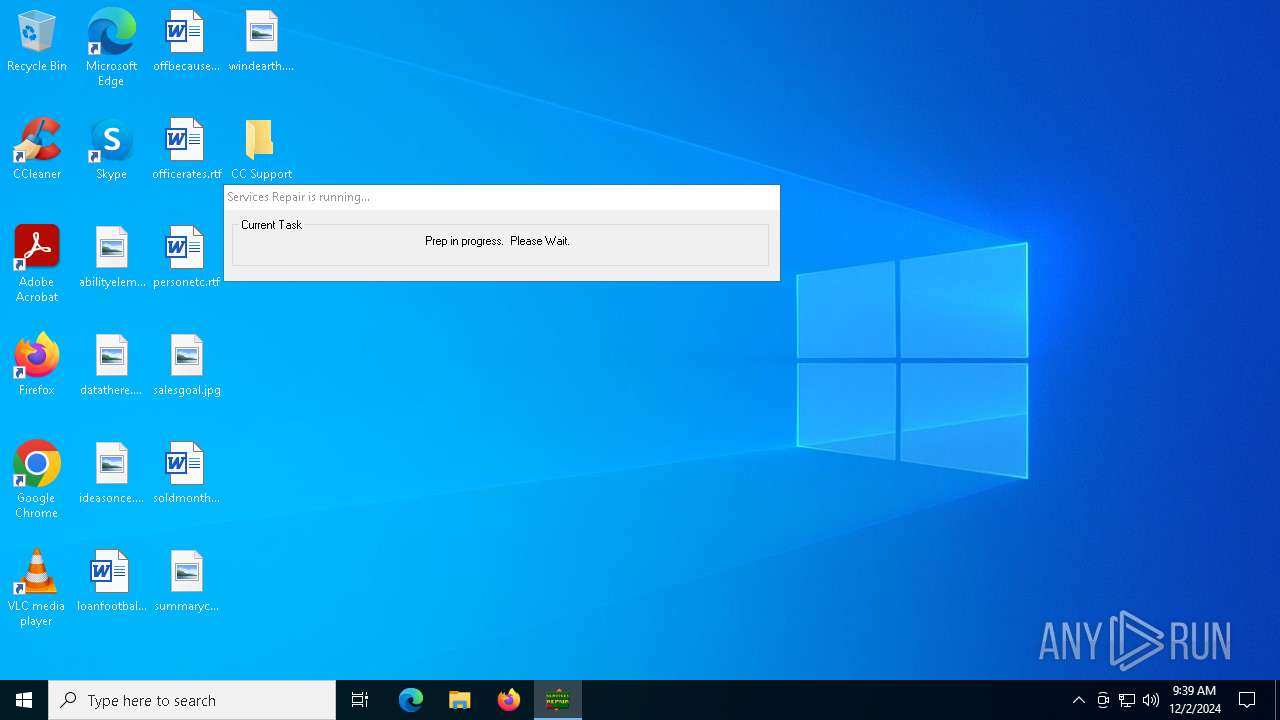
| 6360 | ServicesRepair.exe | C:\Users\Public\Desktop\CC Support\Tools\ServicesRepair\ServicesRepair_x64.exe | executable | |
MD5:59607B33D860CF4D337A4E4851738A76 | SHA256:403835920FD16B7AB6D0A7D22353F82173C69D184D6FF1CC7BC21B5E6BF52D6C | |||
| 6404 | ServicesRepair_x64.exe | C:\Users\Public\Desktop\CC Support\Tools\ServicesRepair\Pieces\Vista\BFE.reg | text | |
MD5:6756B96C03986B62E63E6A0288518F1A | SHA256:DD2683C26BFCF24673459FE9AF53C0CD5A42F57296A9CF66F6C62D01484F9F92 | |||
| 6404 | ServicesRepair_x64.exe | C:\Users\Public\Desktop\CC Support\Tools\ServicesRepair\Pieces\Vista\BITS.sddl | csv | |
MD5:577096DEA76E3E93153BB8D8F347FE8D | SHA256:D1E2E5F769D83ECD5E158B0BE0341FD05D2E97B898BCC45BE052398B6B7500E2 | |||
| 6404 | ServicesRepair_x64.exe | C:\Users\Public\Desktop\CC Support\Tools\ServicesRepair\Pieces\Vista\MpsSvc.reg | text | |
MD5:9A9B4947097FF4A7C70239A104B7A393 | SHA256:087FF8469B6FE6214911173D18910609766ECC8AB0F00D43B3FCBDF963ED8C80 | |||
| 6404 | ServicesRepair_x64.exe | C:\Users\Public\Desktop\CC Support\Tools\ServicesRepair\Pieces\Vista\BITS.reg | text | |
MD5:5D98D98CE0B5194C7A8CDC2C26664EF5 | SHA256:8CB65B887A98CCEC084E2E6A3E224C9D34562939BE53752954F559CE387A0303 | |||
| 6404 | ServicesRepair_x64.exe | C:\Users\Public\Desktop\CC Support\Tools\ServicesRepair\Pieces\Vista\iphlpsvc.sddl | csv | |
MD5:497297A89AFE5E8213343C068C4AE3A2 | SHA256:6929A657D7339093366F03A477A2EA533C907C91A21FDC20C3EC5C86DD872D98 | |||
| 6404 | ServicesRepair_x64.exe | C:\Users\Public\Desktop\CC Support\Tools\ServicesRepair\Pieces\Vista\SharedAccess.reg | text | |
MD5:3DA9DA0977239CC2EB81204D13DFB803 | SHA256:3ED8ECF62E7206154DB6250CD42AD45C016D04CF40848EED81634F867F7AD00E | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
9
TCP/UDP connections
33
DNS requests
16
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
— | — | GET | 200 | 2.16.164.49:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 2.16.164.49:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
5064 | SearchApp.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
1176 | svchost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
7048 | SIHClient.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
6732 | backgroundTaskHost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | whitelisted |
7048 | SIHClient.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
— | — | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
— | — | 2.16.164.49:80 | crl.microsoft.com | Akamai International B.V. | NL | whitelisted |
— | — | 95.101.149.131:80 | www.microsoft.com | Akamai International B.V. | NL | whitelisted |
— | — | 2.23.209.189:443 | — | Akamai International B.V. | GB | unknown |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
188 | svchost.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
5064 | SearchApp.exe | 2.23.209.182:443 | — | Akamai International B.V. | GB | unknown |
5064 | SearchApp.exe | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
1176 | svchost.exe | 20.190.159.71:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
login.live.com |
| whitelisted |
go.microsoft.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |
arc.msn.com |
| whitelisted |