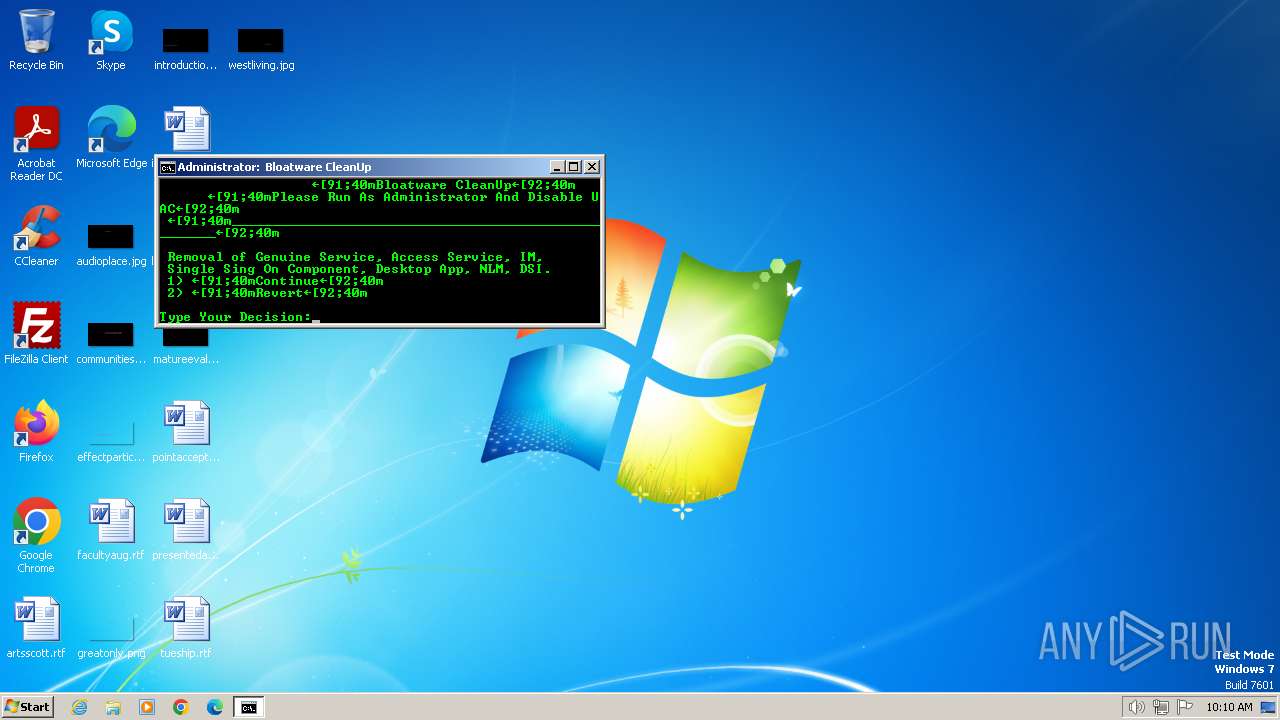
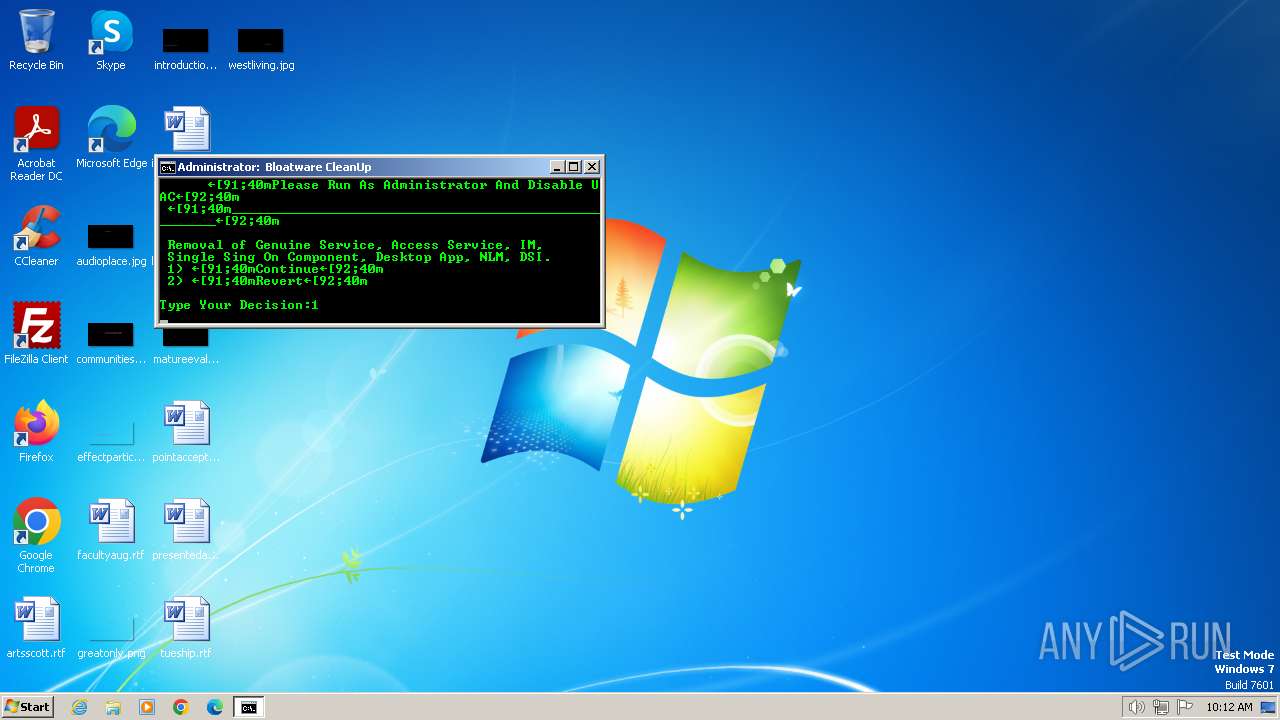
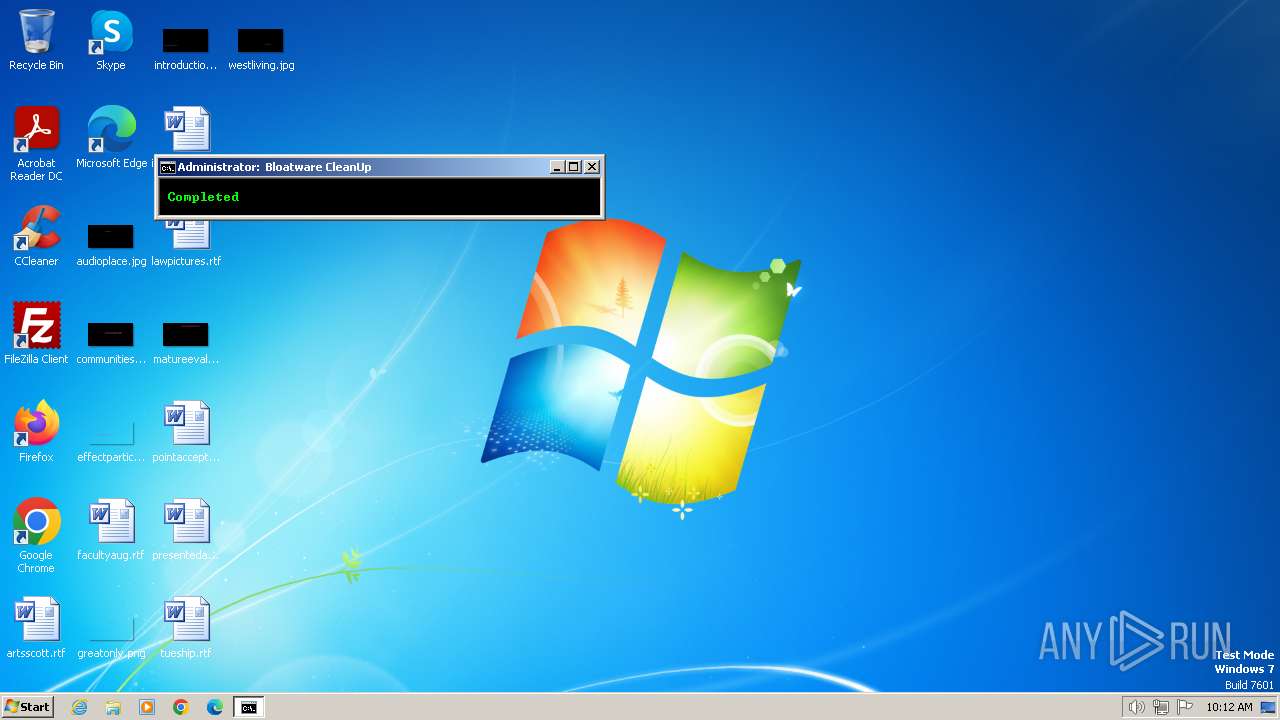
| File name: | Bloatware CleanUp.exe |
| Full analysis: | https://app.any.run/tasks/218c910c-ff2e-4fd5-9437-7f65fa001633 |
| Verdict: | Malicious activity |
| Analysis date: | December 28, 2023, 10:10:06 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows, UPX compressed |
| MD5: | 30BC3A4843995DB743E3CE3F43CB1CD2 |
| SHA1: | DDDFCA415D3A7B0C1E3F44B70D72F38C8D7E47EB |
| SHA256: | 8CA203F91FBDC5FD20F63FC8409CE52785852306DE1922F8C14F5D1CE0C01820 |
| SSDEEP: | 3072:i3pox1w8FCoFjKej0u/Dt1XWhlPhoutPFLtVBjnmATFUJgsL:i58u8PFjcurvXUlPhoSPvfTZpwgG |
MALICIOUS
Starts NET.EXE for service management
- net.exe (PID: 3148)
- cmd.exe (PID: 1772)
- net.exe (PID: 3240)
SUSPICIOUS
Starts CMD.EXE for commands execution
- Bloatware CleanUp.exe (PID: 2040)
- cmd.exe (PID: 1432)
- cmd.exe (PID: 1772)
Reads the Internet Settings
- Bloatware CleanUp.exe (PID: 2040)
Executing commands from a ".bat" file
- Bloatware CleanUp.exe (PID: 2040)
- cmd.exe (PID: 1432)
Starts application with an unusual extension
- cmd.exe (PID: 1432)
- cmd.exe (PID: 1772)
Uses REG/REGEDIT.EXE to modify registry
- cmd.exe (PID: 1432)
- cmd.exe (PID: 1772)
Uses TASKKILL.EXE to kill process
- cmd.exe (PID: 1772)
Starts SC.EXE for service management
- cmd.exe (PID: 1772)
Starts POWERSHELL.EXE for commands execution
- cmd.exe (PID: 1772)
The process bypasses the loading of PowerShell profile settings
- cmd.exe (PID: 1772)
Runs PING.EXE to delay simulation
- cmd.exe (PID: 1772)
INFO
Drops the executable file immediately after the start
- Bloatware CleanUp.exe (PID: 2040)
Reads the computer name
- Bloatware CleanUp.exe (PID: 2040)
- msiexec.exe (PID: 2260)
Checks supported languages
- Bloatware CleanUp.exe (PID: 2040)
- chcp.com (PID: 864)
- mode.com (PID: 2032)
- chcp.com (PID: 1316)
- mode.com (PID: 2128)
- mode.com (PID: 1112)
- msiexec.exe (PID: 2260)
Create files in a temporary directory
- Bloatware CleanUp.exe (PID: 2040)
Application launched itself
- cmd.exe (PID: 1432)
- cmd.exe (PID: 1772)
Reads the machine GUID from the registry
- msiexec.exe (PID: 2260)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Generic Win/DOS Executable (50) |
|---|---|---|
| .exe | | | DOS Executable Generic (49.9) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2012:12:31 01:38:38+01:00 |
| ImageFileCharacteristics: | No relocs, Executable, 32-bit |
| PEType: | PE32 |
| LinkerVersion: | 8 |
| CodeSize: | 57344 |
| InitializedDataSize: | 176128 |
| UninitializedDataSize: | 258048 |
| EntryPoint: | 0x4cf60 |
| OSVersion: | 4 |
| ImageVersion: | - |
| SubsystemVersion: | 4 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 0.0.0.0 |
| ProductVersionNumber: | 0.0.0.0 |
| FileFlagsMask: | 0x0000 |
| FileFlags: | (none) |
| FileOS: | Win32 |
| ObjectFileType: | Unknown |
| FileSubtype: | - |
| LanguageCode: | Russian |
| CharacterSet: | Unicode |
| CompanyName: | - |
| FileDescription: | - |
| LegalCopyright: | - |
| LegalTrademarks: | - |
| InternalName: | - |
| ProductName: | - |
| OriginalFileName: | - |
| FileVersion: | - |
| ProductVersion: | - |
| Comments: | - |
| PrivateBuild: | - |
| SpecialBuild: | - |
Total processes
86
Monitored processes
47
Malicious processes
3
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 864 | chcp 1254 | C:\Windows\System32\chcp.com | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Change CodePage Utility Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1112 | mode con: cols=55 lines=12 | C:\Windows\System32\mode.com | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: DOS Device MODE Utility Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1124 | sc delete AutodeskDesktopApp | C:\Windows\System32\sc.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: A tool to aid in developing services for WindowsNT Exit code: 1060 Version: 6.1.7600.16385 (win7_rtm.090713-1255) | |||||||||||||||
| 1232 | Powershell -nop -c "Get-WmiObject -Query ' select * from Win32_Product where Name like \"%Autodesk Genuine Service%\" ' | ForEach-Object { ($_).Uninstall()}" | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows PowerShell Exit code: 0 Version: 10.0.14409.1005 (rs1_srvoob.161208-1155) Modules
| |||||||||||||||
| 1316 | chcp 1254 | C:\Windows\System32\chcp.com | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Change CodePage Utility Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1432 | C:\Windows\system32\cmd.exe /c ""C:\Users\admin\AppData\Local\Temp\Bloatware\Bloatware.bat" " | C:\Windows\System32\cmd.exe | — | Bloatware CleanUp.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 1540 | Where /R "C:\Program Files\Autodesk" "Acad.exe" /F | C:\Windows\System32\where.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Where - Lists location of files Exit code: 2 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1544 | C:\Windows\system32\cmd.exe /c Where /R "C:\Program Files\Autodesk" "Acad.exe" /F 2>Nul | C:\Windows\System32\cmd.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 2 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 1624 | fltmc | C:\Windows\System32\fltMC.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Filter Manager Control Program Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1772 | "cmd.exe" /x /d /r set "f0=C:\Users\admin\AppData\Local\Temp\Bloatware\Bloatware.bat" &call "C:\Users\admin\AppData\Local\Temp\Bloatware\Bloatware.bat" | C:\Windows\System32\cmd.exe | cmd.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
Total events
2 329
Read events
2 321
Write events
8
Delete events
0
Modification events
| (PID) Process: | (2040) Bloatware CleanUp.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (2040) Bloatware CleanUp.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
| (PID) Process: | (2040) Bloatware CleanUp.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 1 | |||
| (PID) Process: | (2040) Bloatware CleanUp.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 0 | |||
Executable files
0
Suspicious files
8
Text files
3
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3688 | powershell.exe | C:\Users\admin\AppData\Local\Temp\xlbhcoif.nxf.ps1 | binary | |
MD5:C4CA4238A0B923820DCC509A6F75849B | SHA256:— | |||
| 1232 | powershell.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\PowerShell\ModuleAnalysisCache | binary | |
MD5:6675EDE59684F4A119D2E5DA282AFBE6 | SHA256:5026C5EE8FA9ACB21718BF1FAD563C0A3FD5BC79327611FDF9C4ABD2647CE829 | |||
| 3792 | powershell.exe | C:\Users\admin\AppData\Local\Temp\jqpde4bi.0ds.ps1 | binary | |
MD5:C4CA4238A0B923820DCC509A6F75849B | SHA256:— | |||
| 3792 | powershell.exe | C:\Users\admin\AppData\Local\Temp\30efan5i.nii.psm1 | binary | |
MD5:C4CA4238A0B923820DCC509A6F75849B | SHA256:— | |||
| 2040 | Bloatware CleanUp.exe | C:\Users\admin\AppData\Local\Temp\Bloatware\Revert.reg | text | |
MD5:72BDC09123165856D2ED4AD9DF667608 | SHA256:64FF0B75F8EBDEE88BE800D0B4DF097EB15C0C11902E903D6BB5650DF76AB667 | |||
| 1232 | powershell.exe | C:\Users\admin\AppData\Local\Temp\npi54u3i.kur.ps1 | binary | |
MD5:C4CA4238A0B923820DCC509A6F75849B | SHA256:— | |||
| 1232 | powershell.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\PowerShell\StartupProfileData-NonInteractive | binary | |
MD5:446DD1CF97EABA21CF14D03AEBC79F27 | SHA256:A7DE5177C68A64BD48B36D49E2853799F4EBCFA8E4761F7CC472F333DC5F65CF | |||
| 3688 | powershell.exe | C:\Users\admin\AppData\Local\Temp\lphmy30d.a1o.psm1 | binary | |
MD5:C4CA4238A0B923820DCC509A6F75849B | SHA256:— | |||
| 2040 | Bloatware CleanUp.exe | C:\Users\admin\AppData\Local\Temp\Bloatware\Bloatware.reg | text | |
MD5:697FA22F59C6C24CA9BA1FEEEF158D6B | SHA256:1EF616893165155B17B649277F7661B4A86909905F49ED6D318D4DF27EEDA68E | |||
| 2040 | Bloatware CleanUp.exe | C:\Users\admin\AppData\Local\Temp\Bloatware\Bloatware.bat | text | |
MD5:277077C220E9A625D79EB0661B933A9C | SHA256:FC239F9C3F47F97C85EFDF7730161221C5487F833F5C4A4FCC04A768141749AD | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
4
DNS requests
0
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
1080 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |