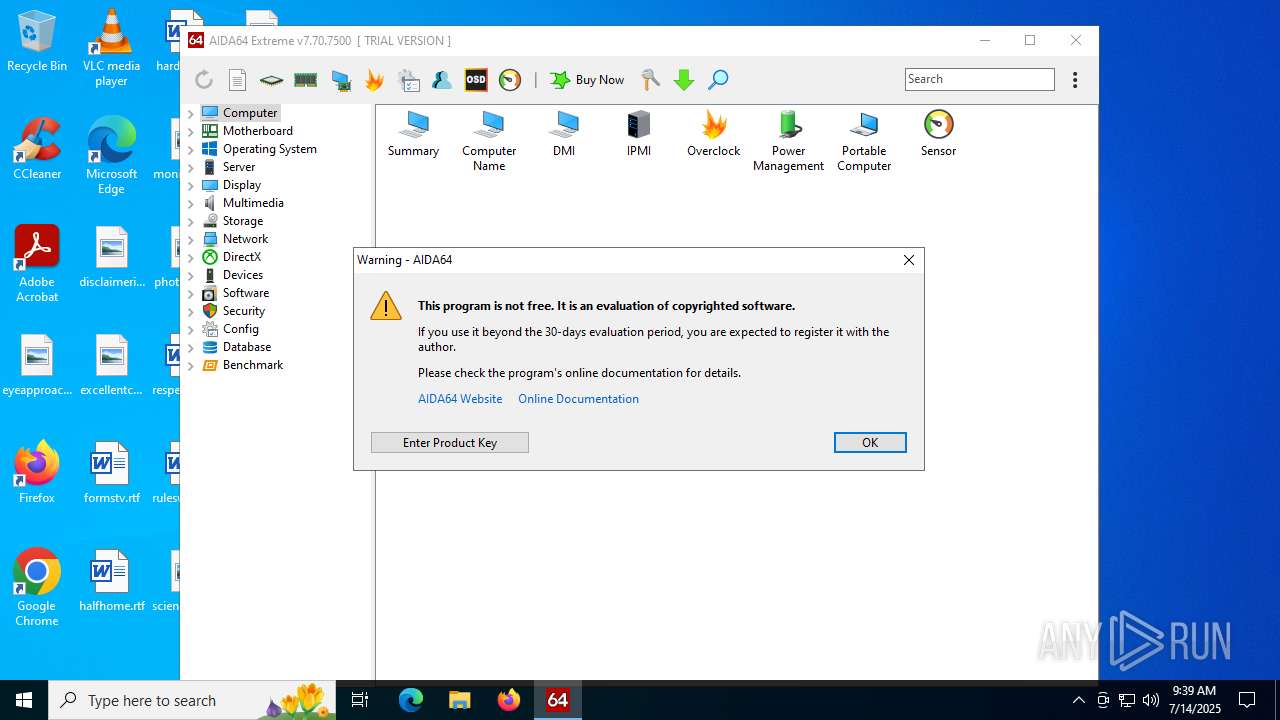
| File name: | GPU-Z 2.66.0.exe |
| Full analysis: | https://app.any.run/tasks/b24fdc1e-526d-49af-8dfd-2a68a80b48bd |
| Verdict: | Malicious activity |
| Analysis date: | July 14, 2025, 09:38:09 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/vnd.microsoft.portable-executable |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows, UPX compressed, 3 sections |
| MD5: | 5B84A2D40DF4A1D561F8268B7385ECEE |
| SHA1: | C343C67213FE74D41102745D3051FCDF7E2C03FD |
| SHA256: | 8C9C0ABA50E5C6A393C3D701A1A3B138195AD0D3CE589C9ECA1469920FC3172B |
| SSDEEP: | 98304:wvG8iRbXRjhDyvtnhzfO6pTixrwvIajvouw3MXhrRyhKKUXQJVUGkTw0ftG8X67q:HKe7xT/R6mtPdJCT |
MALICIOUS
No malicious indicators.SUSPICIOUS
Drops a system driver (possible attempt to evade defenses)
- GPU-Z 2.66.0.exe (PID: 5884)
- aida64extreme770.tmp (PID: 1564)
Executable content was dropped or overwritten
- GPU-Z 2.66.0.exe (PID: 5884)
- aida64extreme770.exe (PID: 4788)
- aida64extreme770.exe (PID: 1632)
- aida64extreme770.tmp (PID: 1564)
Reads security settings of Internet Explorer
- GPU-Z 2.66.0.exe (PID: 5884)
- aida64extreme770.tmp (PID: 3460)
- aida64.exe (PID: 3388)
There is functionality for taking screenshot (YARA)
- GPU-Z 2.66.0.exe (PID: 5884)
- aida64.exe (PID: 3388)
Process drops legitimate windows executable
- aida64extreme770.tmp (PID: 1564)
Reads the Windows owner or organization settings
- aida64extreme770.tmp (PID: 1564)
- aida64.exe (PID: 3388)
Creates a software uninstall entry
- aida64.exe (PID: 3388)
Reads the BIOS version
- aida64.exe (PID: 3388)
Uses RUNDLL32.EXE to load library
- ie4uinit.exe (PID: 6512)
Reads the date of Windows installation
- aida64.exe (PID: 3388)
The process checks if it is being run in the virtual environment
- aida64.exe (PID: 3388)
Write to the desktop.ini file (may be used to cloak folders)
- aida64.exe (PID: 3388)
Searches for installed software
- aida64.exe (PID: 3388)
INFO
The sample compiled with english language support
- GPU-Z 2.66.0.exe (PID: 5884)
- aida64extreme770.tmp (PID: 1564)
Checks supported languages
- GPU-Z 2.66.0.exe (PID: 5884)
- aida64extreme770.exe (PID: 4788)
- aida64extreme770.tmp (PID: 3460)
- aida64extreme770.exe (PID: 1632)
- aida64extreme770.tmp (PID: 1564)
- aida64.exe (PID: 3388)
Create files in a temporary directory
- GPU-Z 2.66.0.exe (PID: 5884)
- aida64extreme770.exe (PID: 4788)
- aida64extreme770.exe (PID: 1632)
- aida64extreme770.tmp (PID: 1564)
Creates files or folders in the user directory
- GPU-Z 2.66.0.exe (PID: 5884)
Reads the computer name
- GPU-Z 2.66.0.exe (PID: 5884)
- aida64extreme770.tmp (PID: 3460)
- aida64extreme770.tmp (PID: 1564)
- aida64.exe (PID: 3388)
Reads the software policy settings
- GPU-Z 2.66.0.exe (PID: 5884)
- slui.exe (PID: 4804)
Reads the machine GUID from the registry
- GPU-Z 2.66.0.exe (PID: 5884)
Checks proxy server information
- GPU-Z 2.66.0.exe (PID: 5884)
- slui.exe (PID: 4804)
- aida64.exe (PID: 3388)
UPX packer has been detected
- GPU-Z 2.66.0.exe (PID: 5884)
- aida64.exe (PID: 3388)
Manual execution by a user
- WinRAR.exe (PID: 856)
- aida64extreme770.exe (PID: 4788)
Process checks computer location settings
- aida64extreme770.tmp (PID: 3460)
- aida64.exe (PID: 3388)
Creates files in the program directory
- aida64extreme770.tmp (PID: 1564)
- aida64.exe (PID: 3388)
Detects InnoSetup installer (YARA)
- aida64extreme770.exe (PID: 4788)
- aida64extreme770.tmp (PID: 3460)
- aida64extreme770.exe (PID: 1632)
- aida64extreme770.tmp (PID: 1564)
Compiled with Borland Delphi (YARA)
- aida64extreme770.tmp (PID: 3460)
- aida64extreme770.tmp (PID: 1564)
- slui.exe (PID: 4804)
- splwow64.exe (PID: 3844)
Creates a software uninstall entry
- aida64extreme770.tmp (PID: 1564)
AIDA64 mutex has been found
- aida64.exe (PID: 3388)
Reads security settings of Internet Explorer
- ie4uinit.exe (PID: 6512)
- splwow64.exe (PID: 3844)
Reads Environment values
- aida64.exe (PID: 3388)
Reads CPU info
- aida64.exe (PID: 3388)
Disables trace logs
- aida64.exe (PID: 3388)
Reads Windows Product ID
- aida64.exe (PID: 3388)
Reads mouse settings
- aida64.exe (PID: 3388)
Process checks whether UAC notifications are on
- aida64.exe (PID: 3388)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | UPX compressed Win32 Executable (76) |
|---|---|---|
| .exe | | | Win32 Executable (generic) (12.6) |
| .exe | | | Generic Win/DOS Executable (5.6) |
| .exe | | | DOS Executable Generic (5.6) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2025:05:29 10:15:59+00:00 |
| ImageFileCharacteristics: | Executable, 32-bit |
| PEType: | PE32 |
| LinkerVersion: | 14.16 |
| CodeSize: | 11206656 |
| InitializedDataSize: | 57344 |
| UninitializedDataSize: | 42303488 |
| EntryPoint: | 0x3308220 |
| OSVersion: | 5.1 |
| ImageVersion: | - |
| SubsystemVersion: | 5.1 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 2.66.0.0 |
| ProductVersionNumber: | 2.66.0.0 |
| FileFlagsMask: | 0x003f |
| FileFlags: | (none) |
| FileOS: | Win32 |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | Unknown (0019) |
| CharacterSet: | Windows, Cyrillic |
| CompanyName: | TechPowerUp (www.techpowerup.com) |
| FileDescription: | GPU-Z - Video card Information Utility |
| FileVersion: | 2.66.0.0 |
| InternalName: | GPU-Z.exe |
| LegalCopyright: | (c) 2007-2025 TechPowerUp (www.techpowerup.com) |
| OriginalFileName: | GPU-Z.exe |
| ProductName: | GPU-Z - Video card Information Utility |
| ProductVersion: | 2.66.0.0 |
Total processes
164
Monitored processes
15
Malicious processes
5
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 856 | "C:\Program Files\WinRAR\WinRAR.exe" x -iext -ow -ver -- "C:\Users\admin\Desktop\aida.64extreme.7.70.rar" C:\Users\admin\Desktop\aida.64extreme.7.70\ | C:\Program Files\WinRAR\WinRAR.exe | — | explorer.exe | |||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.91.0 Modules
| |||||||||||||||
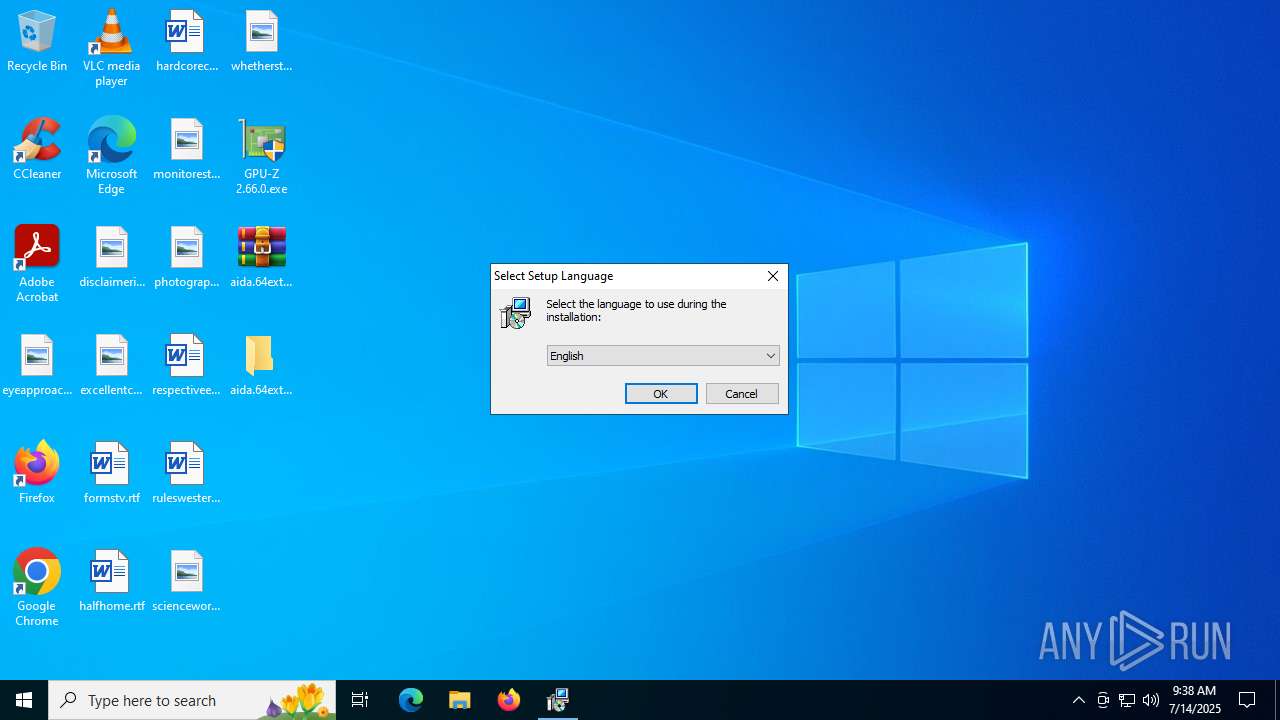
| 1564 | "C:\Users\admin\AppData\Local\Temp\is-BNM6M.tmp\aida64extreme770.tmp" /SL5="$B02EE,58875891,56832,C:\Users\admin\Desktop\aida.64extreme.7.70\aida.64extreme.7.70\aida64extreme770.exe" /SPAWNWND=$90338 /NOTIFYWND=$50320 | C:\Users\admin\AppData\Local\Temp\is-BNM6M.tmp\aida64extreme770.tmp | aida64extreme770.exe | ||||||||||||
User: admin Company: FinalWire Ltd. Integrity Level: HIGH Description: Setup/Uninstall Exit code: 0 Version: 51.52.0.0 Modules
| |||||||||||||||
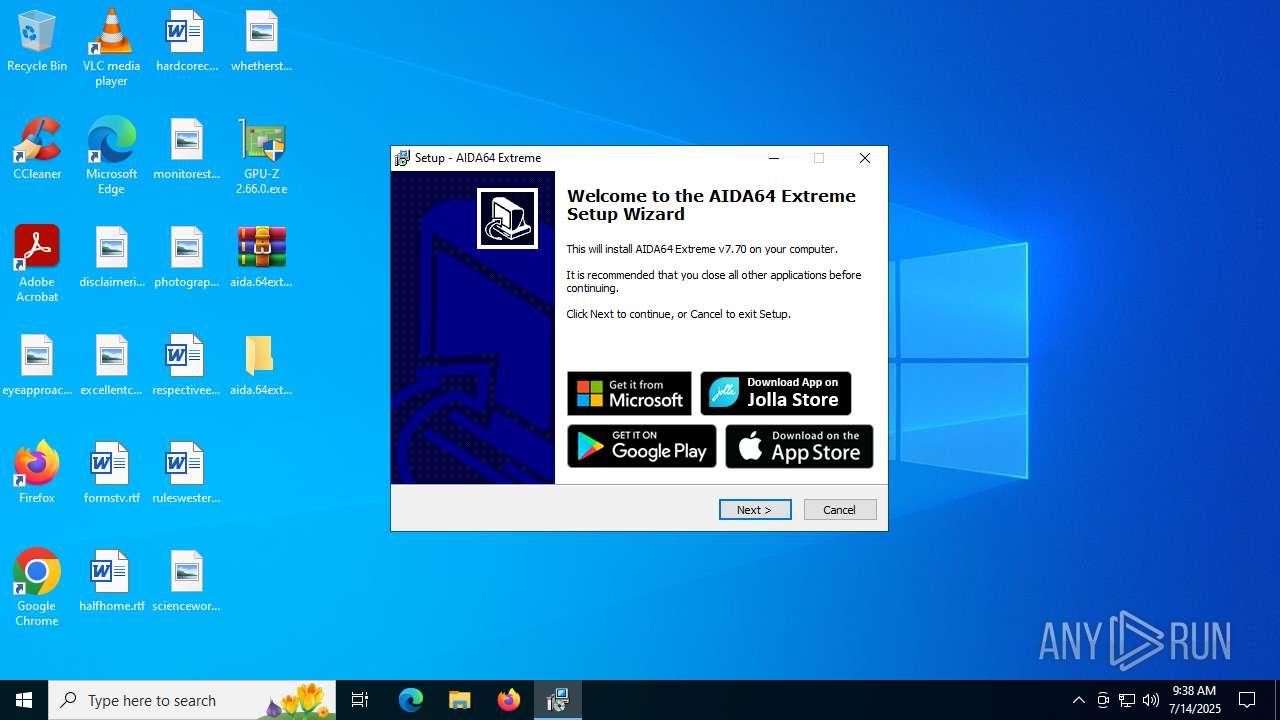
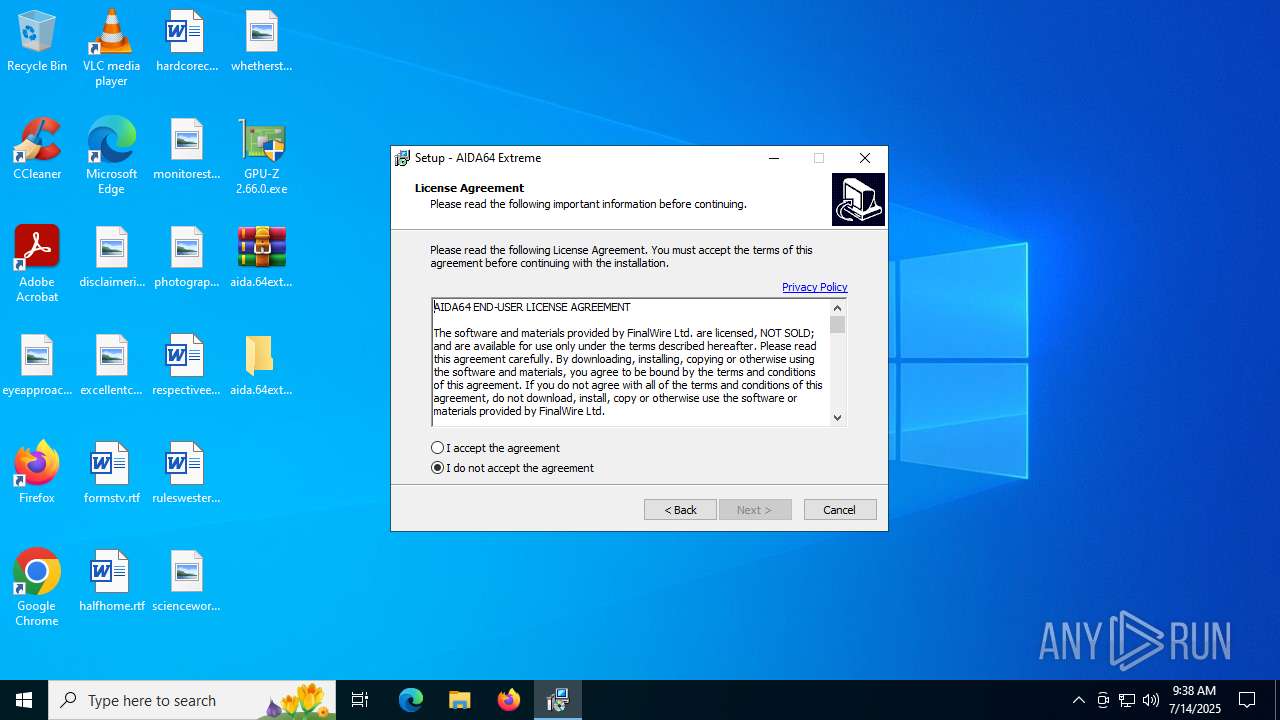
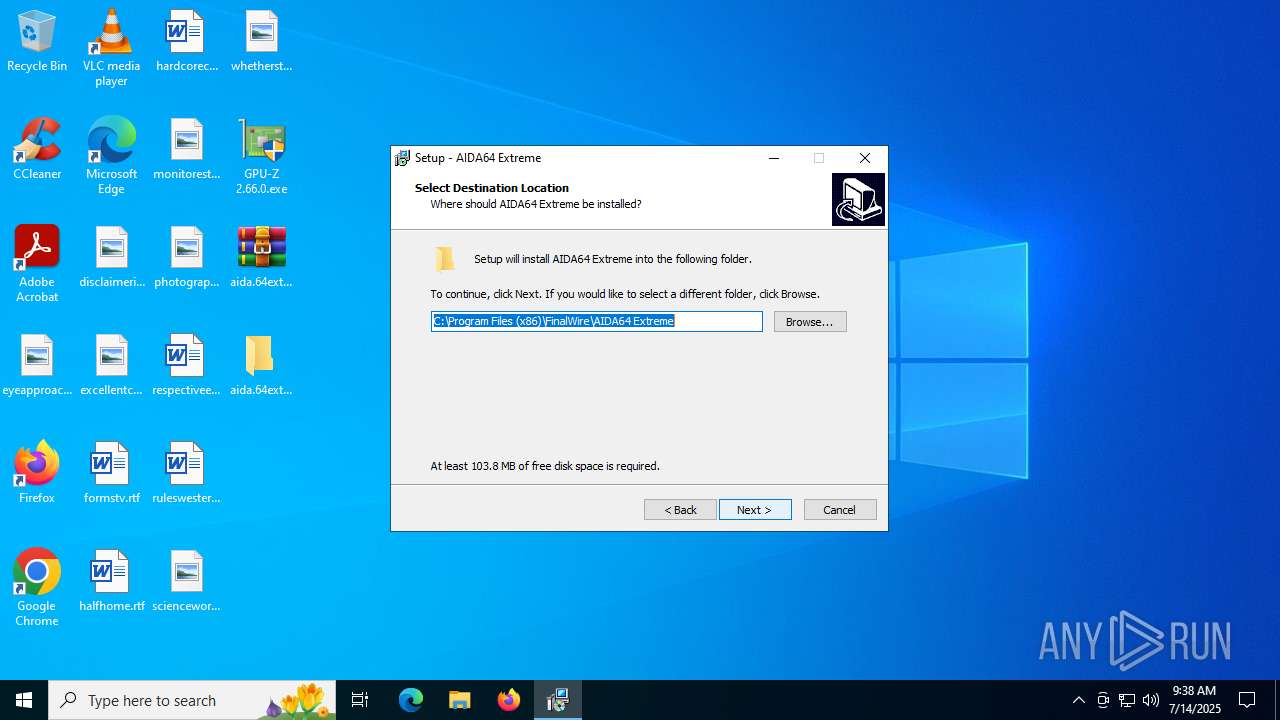
| 1632 | "C:\Users\admin\Desktop\aida.64extreme.7.70\aida.64extreme.7.70\aida64extreme770.exe" /SPAWNWND=$90338 /NOTIFYWND=$50320 | C:\Users\admin\Desktop\aida.64extreme.7.70\aida.64extreme.7.70\aida64extreme770.exe | aida64extreme770.tmp | ||||||||||||
User: admin Company: FinalWire Ltd. Integrity Level: HIGH Description: AIDA64 Extreme Exit code: 0 Version: 7.70.7500.0 Modules
| |||||||||||||||
| 3388 | "C:\Program Files (x86)\FinalWire\AIDA64 Extreme\aida64.exe" | C:\Program Files (x86)\FinalWire\AIDA64 Extreme\aida64.exe | aida64extreme770.tmp | ||||||||||||
User: admin Company: FinalWire Ltd. Integrity Level: HIGH Description: AIDA64 Extreme Version: 7.70.7500 Modules
| |||||||||||||||
| 3460 | "C:\Users\admin\AppData\Local\Temp\is-P0D1T.tmp\aida64extreme770.tmp" /SL5="$50320,58875891,56832,C:\Users\admin\Desktop\aida.64extreme.7.70\aida.64extreme.7.70\aida64extreme770.exe" | C:\Users\admin\AppData\Local\Temp\is-P0D1T.tmp\aida64extreme770.tmp | — | aida64extreme770.exe | |||||||||||
User: admin Company: FinalWire Ltd. Integrity Level: MEDIUM Description: Setup/Uninstall Exit code: 0 Version: 51.52.0.0 Modules
| |||||||||||||||
| 3844 | C:\WINDOWS\System32\rundll32.exe C:\WINDOWS\System32\shell32.dll,SHCreateLocalServerRunDll {9aa46009-3ce0-458a-a354-715610a075e6} -Embedding | C:\Windows\System32\rundll32.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows host process (Rundll32) Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3844 | C:\WINDOWS\splwow64.exe 12288 | C:\Windows\splwow64.exe | — | aida64.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Print driver host for applications Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4788 | "C:\Users\admin\Desktop\aida.64extreme.7.70\aida.64extreme.7.70\aida64extreme770.exe" | C:\Users\admin\Desktop\aida.64extreme.7.70\aida.64extreme.7.70\aida64extreme770.exe | explorer.exe | ||||||||||||
User: admin Company: FinalWire Ltd. Integrity Level: MEDIUM Description: AIDA64 Extreme Exit code: 0 Version: 7.70.7500.0 Modules
| |||||||||||||||
| 4804 | C:\WINDOWS\System32\slui.exe -Embedding | C:\Windows\System32\slui.exe | svchost.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Activation Client Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5884 | "C:\Users\admin\Desktop\GPU-Z 2.66.0.exe" | C:\Users\admin\Desktop\GPU-Z 2.66.0.exe | explorer.exe | ||||||||||||
User: admin Company: TechPowerUp (www.techpowerup.com) Integrity Level: HIGH Description: GPU-Z - Video card Information Utility Exit code: 2 Version: 2.66.0.0 Modules
| |||||||||||||||
Total events
28 486
Read events
28 378
Write events
106
Delete events
2
Modification events
| (PID) Process: | (5884) GPU-Z 2.66.0.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\techPowerUp\GPU-Z |
| Operation: | write | Name: | Install_Dir |
Value: no | |||
| (PID) Process: | (5884) GPU-Z 2.66.0.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Content |
| Operation: | write | Name: | CachePrefix |
Value: | |||
| (PID) Process: | (5884) GPU-Z 2.66.0.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (5884) GPU-Z 2.66.0.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
| (PID) Process: | (5884) GPU-Z 2.66.0.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\techPowerUp\GPU-Z |
| Operation: | write | Name: | WindowPos |
Value: 295,70 | |||
| (PID) Process: | (5884) GPU-Z 2.66.0.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\techPowerUp\GPU-Z |
| Operation: | write | Name: | LastCardIndex |
Value: 0 | |||
| (PID) Process: | (856) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (856) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (856) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (856) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
Executable files
63
Suspicious files
16
Text files
97
Unknown types
12
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 856 | WinRAR.exe | C:\Users\admin\Desktop\aida.64extreme.7.70\aida.64extreme.7.70\aida64extreme770.exe | — | |
MD5:— | SHA256:— | |||
| 5884 | GPU-Z 2.66.0.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\B2FAF7692FD9FFBD64EDE317E42334BA_D7393C8F62BDE4D4CB606228BC7A711E | binary | |
MD5:B9DC0195668292E1DA3AF1E68A8395C0 | SHA256:09FD366E17F6C469C711F97723F9C145E6221F3DB06AC9BBEE51D9AC2A7710FE | |||
| 5884 | GPU-Z 2.66.0.exe | C:\Users\admin\AppData\Local\Temp\GPU-Z-v2.sys | executable | |
MD5:D4320487BF3021F2F2AFCFC43D652A69 | SHA256:9AF0B89C5C54EB66E5A660B61AEE7C1A25B1C92E20A310D8B16552ABCF90C0B5 | |||
| 856 | WinRAR.exe | C:\Users\admin\Desktop\aida.64extreme.7.70\aida.64extreme.7.70\КАК АКТИВИРОВАТЬ!!!.txt | text | |
MD5:11BB4F6C20F11EA41022E64CC268E8C2 | SHA256:CD7C7D7CD0501D64684853D10478824E896FA3AD42363A595B7EC28C2E9EEBDF | |||
| 5884 | GPU-Z 2.66.0.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\07CEF2F654E3ED6050FFC9B6EB844250_3431D4C539FB2CFCB781821E9902850D | binary | |
MD5:48125928356018D26E19142D7F36D391 | SHA256:6F029C9E1082423F0F23205DEB06FEA3E988074247F78275AF56EC3C9BB90407 | |||
| 856 | WinRAR.exe | C:\Users\admin\Desktop\aida.64extreme.7.70\aida.64extreme.7.70\aida64.ini | text | |
MD5:2443EF30159A77B7AF75F9773CDFEFD0 | SHA256:28640F0A034680861668D13353C18FFA94B3AE41CD947CE40A2D02B28414F376 | |||
| 5884 | GPU-Z 2.66.0.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\07CEF2F654E3ED6050FFC9B6EB844250_3431D4C539FB2CFCB781821E9902850D | der | |
MD5:20FDCD92B9CB1883A690D5182497E645 | SHA256:13AF1C63450EEB38071E026332E1A911DE95474E3B168C64563FF97BCA71A430 | |||
| 5884 | GPU-Z 2.66.0.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\F649BE5F074D767215B12950C48C907C | binary | |
MD5:136655D8C09F57CB07E86A5E5D91E8A4 | SHA256:FFDA8AC589F66914474127DE08B21095033E6B7AD390D4E838022DF84F47D3CB | |||
| 1564 | aida64extreme770.tmp | C:\Users\admin\AppData\Local\Temp\is-98AE3.tmp\ios_100.bmp | image | |
MD5:44DFCC45FB934DA6782168F6C03F00A4 | SHA256:1CEA5F212804A6AF116773B6FA70E03271951BC5CEE76B4367C0E58B9F021B5E | |||
| 5884 | GPU-Z 2.66.0.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\F649BE5F074D767215B12950C48C907C | der | |
MD5:EEA38F3D0A5EC778C1D6D2C7AB729D75 | SHA256:8888F2DD73D94C7241EF84264F1738F238D6091D6AAE3B18CC14C75B136D758B | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
10
TCP/UDP connections
34
DNS requests
26
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
1268 | svchost.exe | GET | 200 | 23.55.110.193:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
1268 | svchost.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
5884 | GPU-Z 2.66.0.exe | GET | 200 | 172.64.149.23:80 | http://ocsp.comodoca.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBRTtU9uFqgVGHhJwXZyWCNXmVR5ngQUoBEKIz6W8Qfs4q8p74Klf9AwpLQCEDlyRDr5IrdR19NsEN0xNZU%3D | unknown | — | — | whitelisted |
5884 | GPU-Z 2.66.0.exe | GET | 200 | 172.64.149.23:80 | http://ocsp.usertrust.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTNMNJMNDqCqx8FcBWK16EHdimS6QQUU3m%2FWqorSs9UgOHYm8Cd8rIDZssCEH1bUSa0droR23QWC7xTDac%3D | unknown | — | — | whitelisted |
5884 | GPU-Z 2.66.0.exe | GET | 200 | 172.64.149.23:80 | http://ocsp.sectigo.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBRDC9IOTxN6GmyRjyTl2n4yTUczyAQUjYxexFStiuF36Zv5mwXhuAGNYeECEHN9Y6q%2B3V1xSVihftvH1Bk%3D | unknown | — | — | whitelisted |
2764 | svchost.exe | GET | 200 | 2.23.77.188:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
5564 | SIHClient.exe | GET | 200 | 2.23.246.101:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
5564 | SIHClient.exe | GET | 200 | 2.23.246.101:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
2940 | svchost.exe | GET | 200 | 2.23.197.184:80 | http://x1.c.lencr.org/ | unknown | — | — | whitelisted |
3756 | backgroundTaskHost.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEA77flR%2B3w%2FxBpruV2lte6A%3D | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
1268 | svchost.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
5944 | MoUsoCoreWorker.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
7092 | RUXIMICS.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
1268 | svchost.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
1268 | svchost.exe | 23.55.110.193:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
1268 | svchost.exe | 95.101.149.131:80 | www.microsoft.com | Akamai International B.V. | NL | whitelisted |
5884 | GPU-Z 2.66.0.exe | 216.158.237.92:443 | www.gpu-z.com | IS-AS-1 | US | unknown |
5884 | GPU-Z 2.66.0.exe | 172.64.149.23:80 | ocsp.comodoca.com | CLOUDFLARENET | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
www.gpu-z.com |
| unknown |
ocsp.comodoca.com |
| whitelisted |
ocsp.usertrust.com |
| whitelisted |
ocsp.sectigo.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
Threats
Process | Message |
|---|---|
GPU-Z 2.66.0.exe | in CXCrashHandler
|
GPU-Z 2.66.0.exe | in ~CXCrashHandler
|