| download: | 046d-c52b-4002-ui_x32.exe |
| Full analysis: | https://app.any.run/tasks/d82eaf09-d74d-4189-95df-dff21cfaa4db |
| Verdict: | Suspicious activity |
| Analysis date: | February 12, 2020, 23:09:22 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows, Nullsoft Installer self-extracting archive |
| MD5: | 7C9CD91288979B5232C59B0D462F68BC |
| SHA1: | 6591EC795356554B3CE1A1D18D620828C31EE75F |
| SHA256: | 8C9B4329DA8F6B7EE2AE95ACA65268D788548F8B22C3C507A977C7FEBCA9C75E |
| SSDEEP: | 6144:ze34IgKrbNcQD0kSJ96HcoYa++9uy6n1l3J2i9J0W6i7NNSB:OxBcQDynWYaF9U1SW2WTGB |
MALICIOUS
Loads dropped or rewritten executable
- 046d-c52b-4002-ui_x32.exe (PID: 3368)
SUSPICIOUS
Executable content was dropped or overwritten
- 046d-c52b-4002-ui_x32.exe (PID: 3368)
INFO
Manual execution by user
- explorer.exe (PID: 1928)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | NSIS - Nullsoft Scriptable Install System (94.8) |
|---|---|---|
| .exe | | | Win32 Executable MS Visual C++ (generic) (3.4) |
| .dll | | | Win32 Dynamic Link Library (generic) (0.7) |
| .exe | | | Win32 Executable (generic) (0.5) |
| .exe | | | Generic Win/DOS Executable (0.2) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2009:06:06 23:41:59+02:00 |
| PEType: | PE32 |
| LinkerVersion: | 6 |
| CodeSize: | 24064 |
| InitializedDataSize: | 164864 |
| UninitializedDataSize: | 1024 |
| EntryPoint: | 0x30fa |
| OSVersion: | 4 |
| ImageVersion: | 6.1 |
| SubsystemVersion: | 4 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 1.0.0.0 |
| ProductVersionNumber: | 1.0.0.0 |
| FileFlagsMask: | 0x0000 |
| FileFlags: | (none) |
| FileOS: | Win32 |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | English (U.S.) |
| CharacterSet: | ASCII |
| CompanyName: | Logitech |
| CompanyWebsite: | http://www.logitech.com |
| FileDescription: | - |
| FileVersion: | 1 |
| LegalCopyright: | - |
| ProductName: | LogiUI Pak |
| ProductVersion: | 1 |
Summary
| Architecture: | IMAGE_FILE_MACHINE_I386 |
|---|---|
| Subsystem: | IMAGE_SUBSYSTEM_WINDOWS_GUI |
| Compilation Date: | 06-Jun-2009 21:41:59 |
| Detected languages: |
|
| CompanyName: | Logitech |
| CompanyWebsite: | http://www.logitech.com |
| FileDescription: | - |
| FileVersion: | 1.0 |
| LegalCopyright: | - |
| ProductName: | LogiUI Pak |
| ProductVersion: | 1.0 |
DOS Header
| Magic number: | MZ |
|---|---|
| Bytes on last page of file: | 0x0090 |
| Pages in file: | 0x0003 |
| Relocations: | 0x0000 |
| Size of header: | 0x0004 |
| Min extra paragraphs: | 0x0000 |
| Max extra paragraphs: | 0xFFFF |
| Initial SS value: | 0x0000 |
| Initial SP value: | 0x00B8 |
| Checksum: | 0x0000 |
| Initial IP value: | 0x0000 |
| Initial CS value: | 0x0000 |
| Overlay number: | 0x0000 |
| OEM identifier: | 0x0000 |
| OEM information: | 0x0000 |
| Address of NE header: | 0x000000D8 |
PE Headers
| Signature: | PE |
|---|---|
| Machine: | IMAGE_FILE_MACHINE_I386 |
| Number of sections: | 5 |
| Time date stamp: | 06-Jun-2009 21:41:59 |
| Pointer to Symbol Table: | 0x00000000 |
| Number of symbols: | 0 |
| Size of Optional Header: | 0x00E0 |
| Characteristics: |
|
Sections
Name | Virtual Address | Virtual Size | Raw Size | Charateristics | Entropy |
|---|---|---|---|---|---|
.text | 0x00001000 | 0x00005C4C | 0x00005E00 | IMAGE_SCN_CNT_CODE, IMAGE_SCN_MEM_EXECUTE, IMAGE_SCN_MEM_READ | 6.44011 |
.rdata | 0x00007000 | 0x0000129C | 0x00001400 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ | 5.04684 |
.data | 0x00009000 | 0x00025C58 | 0x00000400 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ, IMAGE_SCN_MEM_WRITE | 4.801 |
.ndata | 0x0002F000 | 0x00015000 | 0x00000000 | IMAGE_SCN_CNT_UNINITIALIZED_DATA, IMAGE_SCN_MEM_READ, IMAGE_SCN_MEM_WRITE | 0 |
.rsrc | 0x00044000 | 0x00008758 | 0x00008800 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ | 5.41993 |
Resources
Title | Entropy | Size | Codepage | Language | Type |
|---|---|---|---|---|---|
1 | 5.22401 | 947 | UNKNOWN | English - United States | RT_MANIFEST |
2 | 5.61959 | 4264 | UNKNOWN | English - United States | RT_ICON |
3 | 4.84061 | 3752 | UNKNOWN | English - United States | RT_ICON |
4 | 6.16608 | 2216 | UNKNOWN | English - United States | RT_ICON |
5 | 3.91942 | 1640 | UNKNOWN | English - United States | RT_ICON |
6 | 5.42186 | 1384 | UNKNOWN | English - United States | RT_ICON |
7 | 5.58096 | 1128 | UNKNOWN | English - United States | RT_ICON |
8 | 3.74963 | 744 | UNKNOWN | English - United States | RT_ICON |
9 | 3.01957 | 296 | UNKNOWN | English - United States | RT_ICON |
103 | 2.73226 | 132 | UNKNOWN | English - United States | RT_GROUP_ICON |
Imports
ADVAPI32.dll |
COMCTL32.dll |
GDI32.dll |
KERNEL32.dll |
SHELL32.dll |
USER32.dll |
VERSION.dll |
ole32.dll |
Total processes
38
Monitored processes
2
Malicious processes
0
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1928 | "C:\Windows\explorer.exe" | C:\Windows\explorer.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Explorer Exit code: 1 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3368 | "C:\Users\admin\AppData\Local\Temp\046d-c52b-4002-ui_x32.exe" | C:\Users\admin\AppData\Local\Temp\046d-c52b-4002-ui_x32.exe | explorer.exe | ||||||||||||
User: admin Company: Logitech Integrity Level: MEDIUM Exit code: 0 Version: 1.0 Modules
| |||||||||||||||
Total events
363
Read events
357
Write events
6
Delete events
0
Modification events
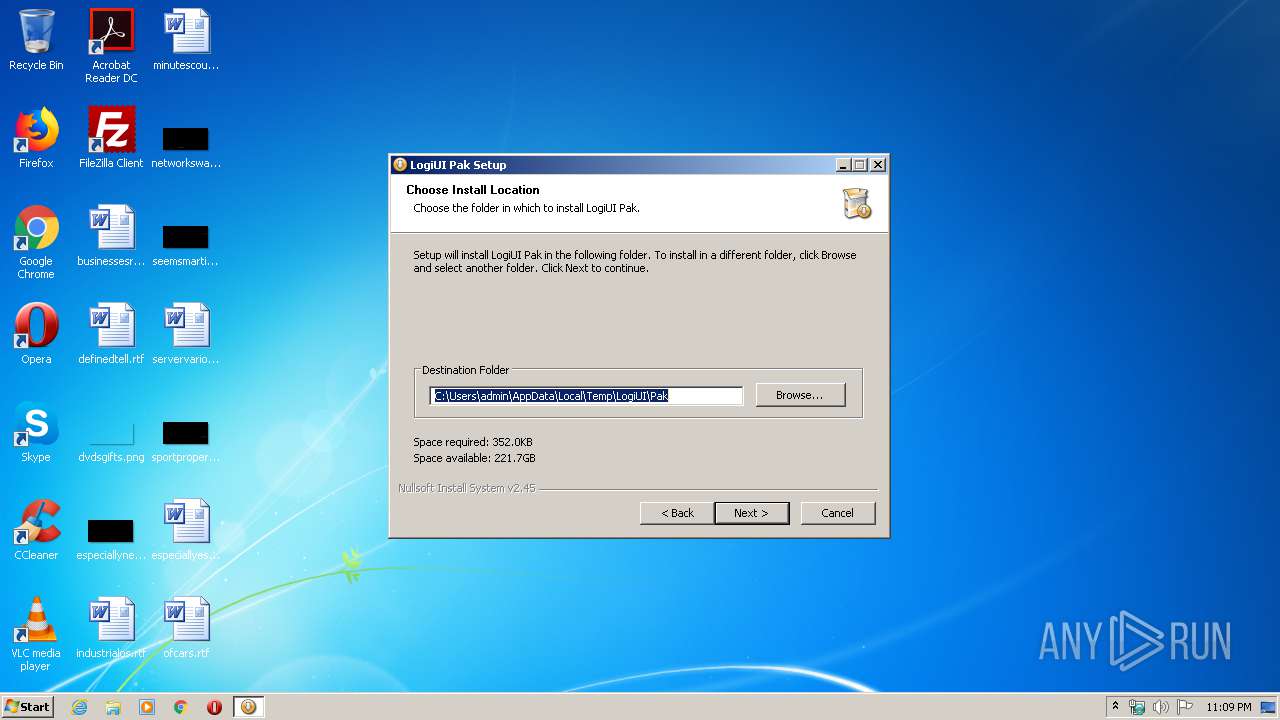
| (PID) Process: | (3368) 046d-c52b-4002-ui_x32.exe | Key: | HKEY_CURRENT_USER\Software\LogiShrd\DownloadAssistant |
| Operation: | write | Name: | UIPath |
Value: C:\Users\admin\AppData\Local\Temp\LogiUI\Pak | |||
| (PID) Process: | (3368) 046d-c52b-4002-ui_x32.exe | Key: | HKEY_CURRENT_USER\Software\LogiShrd\DownloadAssistant |
| Operation: | write | Name: | UIRemove |
Value: C:\Users\admin\AppData\Local\Temp\LogiUI\Pak\uninstall.exe | |||
| (PID) Process: | (3368) 046d-c52b-4002-ui_x32.exe | Key: | HKEY_CURRENT_USER\Software\LogiUI Pak\Components |
| Operation: | write | Name: | UI |
Value: 1 | |||
| (PID) Process: | (3368) 046d-c52b-4002-ui_x32.exe | Key: | HKEY_CURRENT_USER\Software\LogiUI Pak |
| Operation: | write | Name: | Path |
Value: C:\Users\admin\AppData\Local\Temp\LogiUI\Pak | |||
| (PID) Process: | (3368) 046d-c52b-4002-ui_x32.exe | Key: | HKEY_CURRENT_USER\Software\LogiUI Pak |
| Operation: | write | Name: | StartMenuGroup |
Value: LogiLang Pak | |||
| (PID) Process: | (3368) 046d-c52b-4002-ui_x32.exe | Key: | HKEY_CURRENT_USER\Software\LogiUI Pak |
| Operation: | write | Name: | InstallerLanguage |
Value: 1033 | |||
Executable files
5
Suspicious files
0
Text files
71
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3368 | 046d-c52b-4002-ui_x32.exe | C:\Users\admin\AppData\Local\Temp\LogiUI\Pak\css\smart.css | text | |
MD5:7B44642D05E86363B6990E5F4705280C | SHA256:ED7A8CF7F99B93548BE6A411F6830E7828B95F1375F1FF20E4470624C5E54A54 | |||
| 3368 | 046d-c52b-4002-ui_x32.exe | C:\Users\admin\AppData\Local\Temp\nsn68A6.tmp\LangDLL.dll | executable | |
MD5:A401E590877EF6C928D2A97C66157094 | SHA256:2A7F33EF64D666A42827C4DC377806AD97BC233819197ADF9696AED5BE5EFAC0 | |||
| 3368 | 046d-c52b-4002-ui_x32.exe | C:\Users\admin\AppData\Local\Temp\LogiUI\Pak\html\download.html | html | |
MD5:B3D9AF593F899BB58E5FF6C4EF3F5EDF | SHA256:EEBA727806E499979B8395C9AD9ED300106B4B9E5D38CF474A5EB3BC23515889 | |||
| 3368 | 046d-c52b-4002-ui_x32.exe | C:\Users\admin\AppData\Local\Temp\LogiUI\Pak\html\welcome.html | html | |
MD5:93CE18E0377BA6E703796C07DBA0D58C | SHA256:101B62F65FC8E516DB383DD9D60AD4BDEDF7201C51E05B1929A8DEC0C58AFDEC | |||
| 3368 | 046d-c52b-4002-ui_x32.exe | C:\Users\admin\AppData\Local\Temp\LogiUI\Pak\img\alert.gif | image | |
MD5:A170E07967DD99C9E84C4011A80C20B1 | SHA256:CAED83B08D2C62FDB9FA08EC3155E894B4FC4D005CCD68E22B148177B4B20CB4 | |||
| 3368 | 046d-c52b-4002-ui_x32.exe | C:\Users\admin\AppData\Local\Temp\LogiUI\Pak\img\key_1.jpg | image | |
MD5:99477AFD3105C19F5D41188E6D3FBFC7 | SHA256:ADC24A6443D82CE62A1F6BDBFE11C3C6102A2B75CBB66BFF67D72198518705F6 | |||
| 3368 | 046d-c52b-4002-ui_x32.exe | C:\Users\admin\AppData\Local\Temp\LogiUI\Pak\html\finish.html | html | |
MD5:0E1DCE7EB340612A5D6A615A9358F8B8 | SHA256:4329BEC0D447A05FF19E9E25E99D08B31F4B20149045A853918F9464EF01DF21 | |||
| 3368 | 046d-c52b-4002-ui_x32.exe | C:\Users\admin\AppData\Local\Temp\LogiUI\Pak\img\footer_image.gif | image | |
MD5:8D9A7B17C1A555578B1D56092A7F03C4 | SHA256:8ED2C93336CE3B785B0AB661BAA67735565DE9548B1A34FC5CED4CC6C8F4DCC4 | |||
| 3368 | 046d-c52b-4002-ui_x32.exe | C:\Users\admin\AppData\Local\Temp\LogiUI\Pak\img\close_inactive.gif | image | |
MD5:A74490278EA0434640EC8F4814C0A3EC | SHA256:4E72B2A8F4D1248E0C5BCC6EBE3BFA1DCBEB675C295C7C0DE79B9FE48A57CC79 | |||
| 3368 | 046d-c52b-4002-ui_x32.exe | C:\Users\admin\AppData\Local\Temp\LogiUI\Pak\css\basic-quickflips.css | text | |
MD5:D47CCCDABFD347C1E75C61D452B85087 | SHA256:F5A652DD45B7B3C4DCCA5C05A88ECFC5542DA48CDF155F02A095931537E8C904 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
0
DNS requests
0
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report