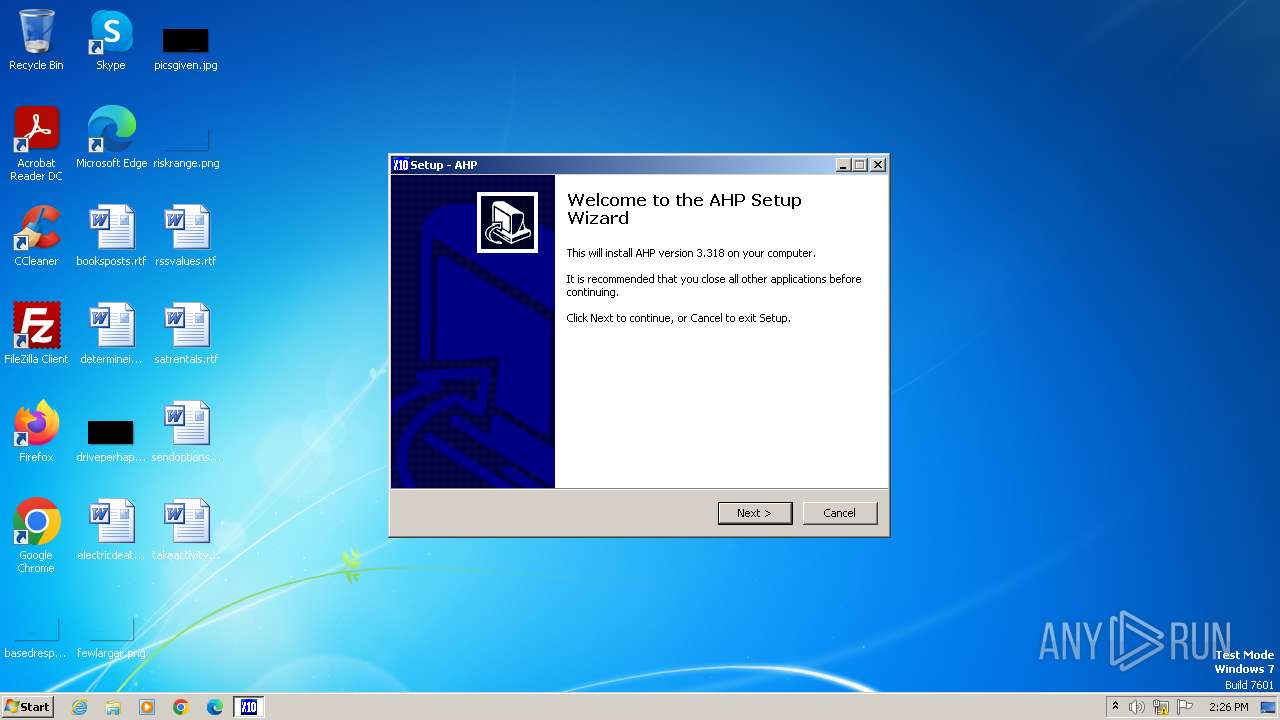
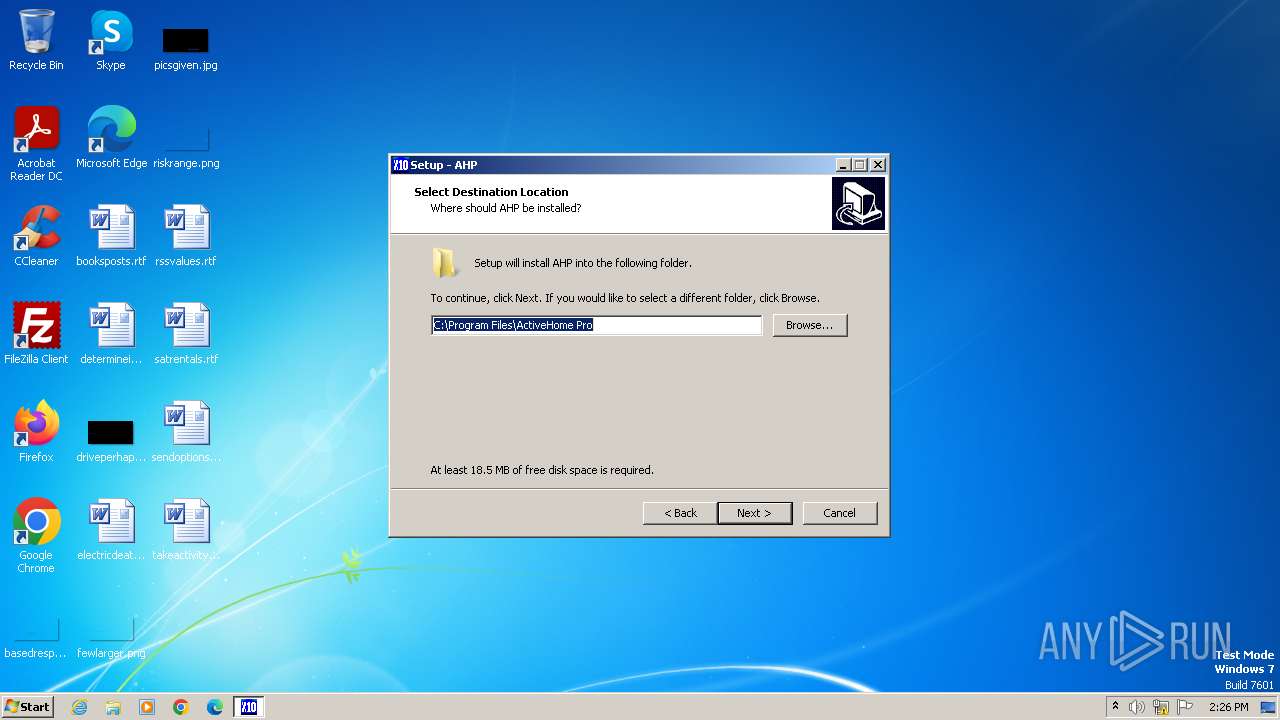
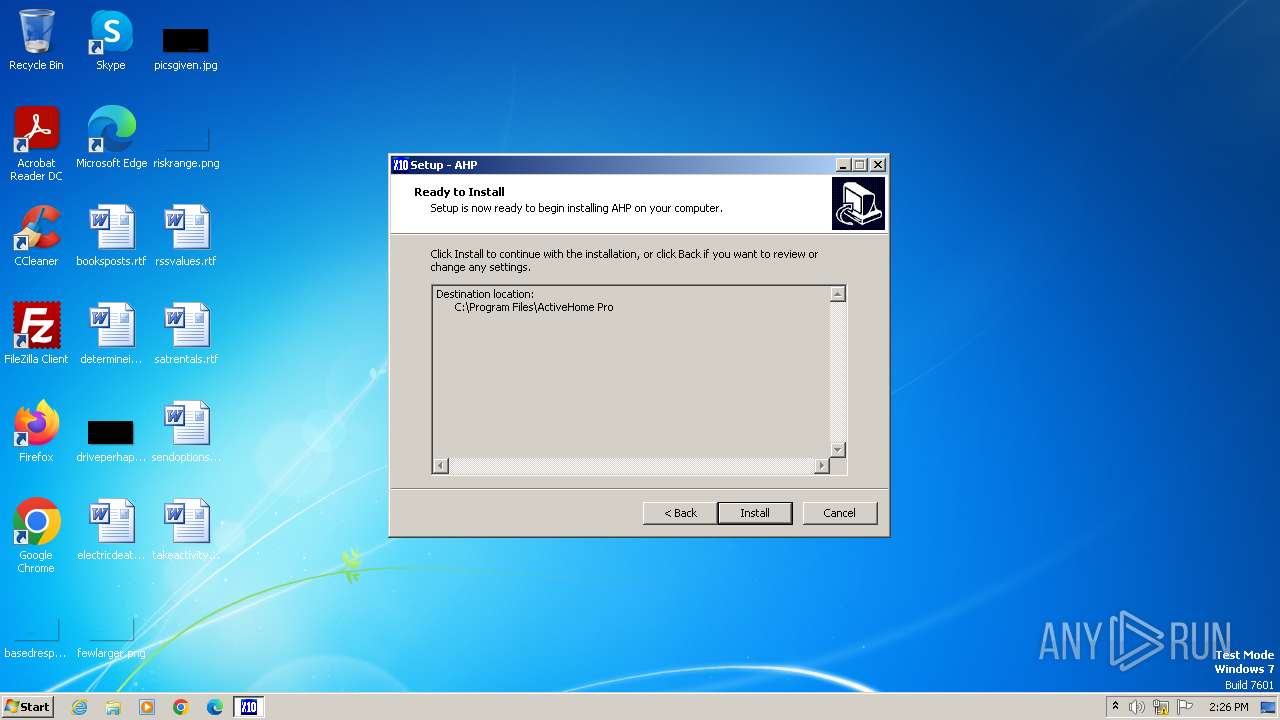
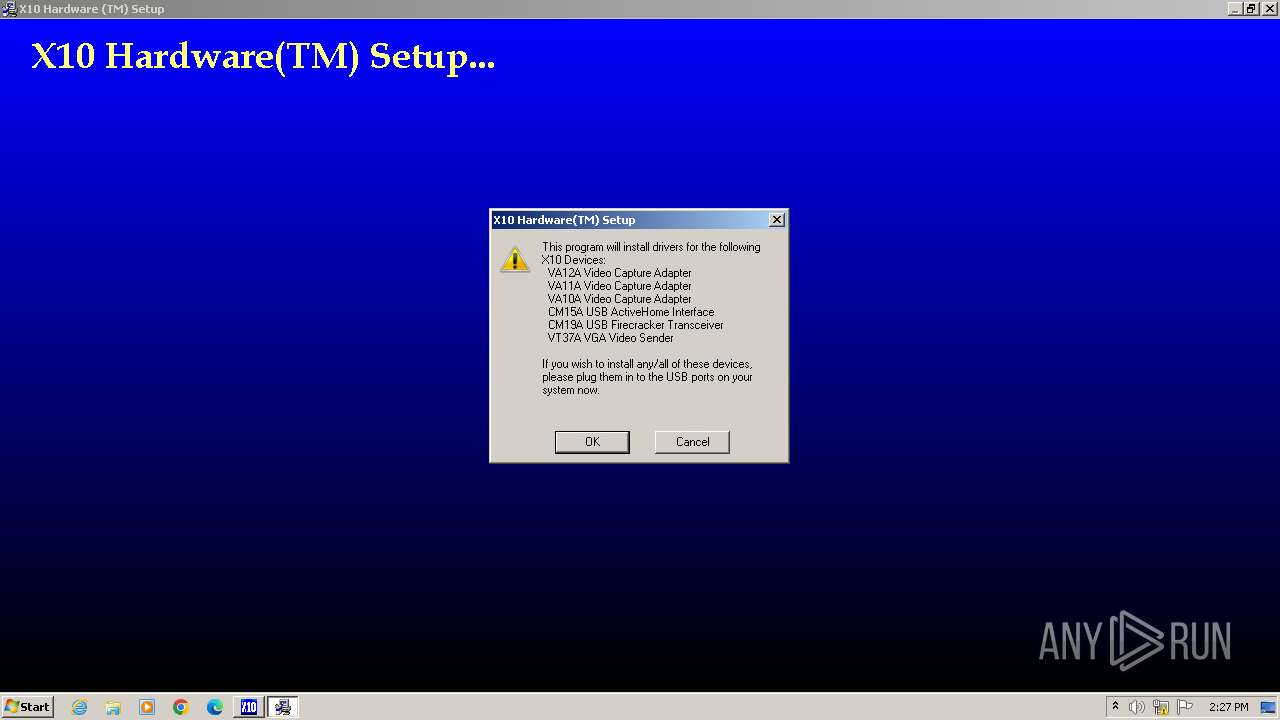
| File name: | AHP_3.318.exe |
| Full analysis: | https://app.any.run/tasks/095062f9-5b33-44f1-9b6f-968b6041ee00 |
| Verdict: | Malicious activity |
| Analysis date: | June 17, 2024, 13:26:19 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows |
| MD5: | 8DE5BA92AEE0ACDC0028BF2FBFAD7CCF |
| SHA1: | A4F44B92A8577AEA4C71C63923CA603196C66693 |
| SHA256: | 8C95BD7C406511F4C66B5A346B82BFF761FAF2C8374650D07FE05C094FEBB43F |
| SSDEEP: | 196608:pYU4ghwGpm7+iSCzFj8pyvLAJ/L32BYtnm:Tm7+iSG8U+gCnm |
MALICIOUS
Drops the executable file immediately after the start
- AHP_3.318.exe (PID: 3976)
- AHP_3.318.exe (PID: 1020)
- AHP_3.318.tmp (PID: 2104)
- GLBABD2.tmp (PID: 2116)
- x10drivers.exe (PID: 124)
- DIFxCMD.exe (PID: 1872)
- drvinst.exe (PID: 1184)
- ahscript_setup.exe (PID: 1864)
- drvinst.exe (PID: 1424)
- x10nets_updater.exe (PID: 1844)
- x10nets_updater.tmp (PID: 1932)
Creates a writable file in the system directory
- GLBABD2.tmp (PID: 2116)
- drvinst.exe (PID: 1184)
- drvinst.exe (PID: 1424)
Registers / Runs the DLL via REGSVR32.EXE
- ahscript_setup.exe (PID: 1864)
SUSPICIOUS
Executable content was dropped or overwritten
- AHP_3.318.exe (PID: 1020)
- AHP_3.318.exe (PID: 3976)
- AHP_3.318.tmp (PID: 2104)
- x10drivers.exe (PID: 124)
- GLBABD2.tmp (PID: 2116)
- drvinst.exe (PID: 1184)
- DIFxCMD.exe (PID: 1872)
- ahscript_setup.exe (PID: 1864)
- drvinst.exe (PID: 1424)
- x10nets_updater.exe (PID: 1844)
- x10nets_updater.tmp (PID: 1932)
Process drops legitimate windows executable
- AHP_3.318.tmp (PID: 2104)
- GLBABD2.tmp (PID: 2116)
- x10nets_updater.tmp (PID: 1932)
Reads the Windows owner or organization settings
- AHP_3.318.tmp (PID: 2104)
- x10nets_updater.tmp (PID: 1932)
The process drops C-runtime libraries
- GLBABD2.tmp (PID: 2116)
Starts application with an unusual extension
- x10drivers.exe (PID: 124)
- GLBABD2.tmp (PID: 2116)
- ahscript_setup.exe (PID: 1864)
Drops a system driver (possible attempt to evade defenses)
- GLBABD2.tmp (PID: 2116)
- DIFxCMD.exe (PID: 1872)
- drvinst.exe (PID: 1184)
- drvinst.exe (PID: 1424)
- ahscript_setup.exe (PID: 1864)
Creates a software uninstall entry
- GLBABD2.tmp (PID: 2116)
Searches for installed software
- GLBABD2.tmp (PID: 2116)
Creates files in the driver directory
- drvinst.exe (PID: 1184)
- drvinst.exe (PID: 1424)
Creates or modifies Windows services
- GLBABD2.tmp (PID: 2116)
Checks Windows Trust Settings
- drvinst.exe (PID: 1184)
- drvinst.exe (PID: 1424)
Creates/Modifies COM task schedule object
- GLJAC12.tmp (PID: 552)
- GLJAC12.tmp (PID: 304)
- GLJAC12.tmp (PID: 1060)
- rundll32.exe (PID: 768)
- regsvr32.exe (PID: 1660)
- GLJECF3.tmp (PID: 1800)
- GLJAC12.tmp (PID: 1628)
Reads security settings of Internet Explorer
- ahscript_setup.exe (PID: 1864)
Reads the Internet Settings
- ahscript_setup.exe (PID: 1864)
INFO
Checks supported languages
- AHP_3.318.tmp (PID: 3992)
- AHP_3.318.exe (PID: 3976)
- AHP_3.318.exe (PID: 1020)
- AHP_3.318.tmp (PID: 2104)
- x10drivers.exe (PID: 124)
- GLBABD2.tmp (PID: 2116)
- DIFxCMD.exe (PID: 1872)
- drvinst.exe (PID: 1184)
- DIFxCMD.exe (PID: 1772)
- GLJAC12.tmp (PID: 1628)
- GLJAC12.tmp (PID: 304)
- GLJAC12.tmp (PID: 552)
- rundll32.exe (PID: 728)
- GLJAC12.tmp (PID: 1060)
- ahscript_setup.exe (PID: 1864)
- rundll32.exe (PID: 768)
- drvinst.exe (PID: 1424)
- GLJECF3.tmp (PID: 1800)
- x10nets_updater.exe (PID: 1844)
- x10nets_updater.tmp (PID: 1932)
Reads the computer name
- AHP_3.318.tmp (PID: 3992)
- AHP_3.318.tmp (PID: 2104)
- GLBABD2.tmp (PID: 2116)
- DIFxCMD.exe (PID: 1872)
- drvinst.exe (PID: 1184)
- DIFxCMD.exe (PID: 1772)
- ahscript_setup.exe (PID: 1864)
- GLJAC12.tmp (PID: 1628)
- rundll32.exe (PID: 768)
- drvinst.exe (PID: 1424)
- GLJECF3.tmp (PID: 1800)
- x10nets_updater.tmp (PID: 1932)
Create files in a temporary directory
- AHP_3.318.exe (PID: 3976)
- AHP_3.318.exe (PID: 1020)
- AHP_3.318.tmp (PID: 2104)
- x10drivers.exe (PID: 124)
- GLBABD2.tmp (PID: 2116)
- DIFxCMD.exe (PID: 1872)
- ahscript_setup.exe (PID: 1864)
- x10nets_updater.exe (PID: 1844)
- x10nets_updater.tmp (PID: 1932)
Creates a software uninstall entry
- AHP_3.318.tmp (PID: 2104)
- x10nets_updater.tmp (PID: 1932)
Creates files in the program directory
- AHP_3.318.tmp (PID: 2104)
- GLBABD2.tmp (PID: 2116)
- ahscript_setup.exe (PID: 1864)
- x10nets_updater.tmp (PID: 1932)
Reads the machine GUID from the registry
- DIFxCMD.exe (PID: 1872)
- drvinst.exe (PID: 1184)
- DIFxCMD.exe (PID: 1772)
- ahscript_setup.exe (PID: 1864)
- drvinst.exe (PID: 1424)
Reads the software policy settings
- drvinst.exe (PID: 1184)
- drvinst.exe (PID: 1424)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Inno Setup installer (71.1) |
|---|---|---|
| .exe | | | Win32 Executable Delphi generic (9.1) |
| .scr | | | Windows screen saver (8.4) |
| .dll | | | Win32 Dynamic Link Library (generic) (4.2) |
| .exe | | | Win32 Executable (generic) (2.9) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 1992:06:19 22:22:17+00:00 |
| ImageFileCharacteristics: | No relocs, Executable, No line numbers, No symbols, Bytes reversed lo, 32-bit, Bytes reversed hi |
| PEType: | PE32 |
| LinkerVersion: | 2.25 |
| CodeSize: | 40448 |
| InitializedDataSize: | 15360 |
| UninitializedDataSize: | - |
| EntryPoint: | 0xa5f8 |
| OSVersion: | 1 |
| ImageVersion: | 6 |
| SubsystemVersion: | 4 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 0.0.0.0 |
| ProductVersionNumber: | 0.0.0.0 |
| FileFlagsMask: | 0x003f |
| FileFlags: | (none) |
| FileOS: | Win32 |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | Neutral |
| CharacterSet: | Unicode |
| Comments: | This installation was built with Inno Setup. |
| CompanyName: | tuicemen software |
| FileDescription: | AHP Setup |
| FileVersion: | |
| LegalCopyright: | |
| ProductName: | AHP |
| ProductVersion: | 3.318 |
Total processes
55
Monitored processes
21
Malicious processes
13
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 124 | "C:\Users\admin\AppData\Local\Temp\is-L0958.tmp\x10drivers.exe" | C:\Users\admin\AppData\Local\Temp\is-L0958.tmp\x10drivers.exe | AHP_3.318.tmp | ||||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
| 304 | "C:\Users\admin\AppData\Local\Temp\GLJAC12.tmp" C:\Program Files\Common Files\X10\Common\xcap.ax | C:\Users\admin\AppData\Local\Temp\GLJAC12.tmp | — | GLBABD2.tmp | |||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
| 552 | "C:\Users\admin\AppData\Local\Temp\GLJAC12.tmp" C:\Program Files\Common Files\X10\Common\x10lv.dll | C:\Users\admin\AppData\Local\Temp\GLJAC12.tmp | — | GLBABD2.tmp | |||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
| 728 | C:\PROGRA~1\COMMON~1\X10\Common\rundll32.exe /REGSERVER | C:\Program Files\Common Files\X10\Common\rundll32.exe | — | GLBABD2.tmp | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows host process (Rundll32) Exit code: 0 Version: 6.0.6000.16386 (vista_rtm.061101-2205) Modules
| |||||||||||||||
| 768 | "C:\PROGRA~1\COMMON~1\X10\Common\rundll32.exe" C:\PROGRA~1\COMMON~1\X10\Common\x10net.dll,EntryPoint -RegServiceAuto | C:\Program Files\Common Files\X10\Common\rundll32.exe | — | ahscript_setup.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows host process (Rundll32) Exit code: 0 Version: 6.0.6000.16386 (vista_rtm.061101-2205) Modules
| |||||||||||||||
| 1020 | "C:\Users\admin\AppData\Local\Temp\AHP_3.318.exe" /SPAWNWND=$20134 /NOTIFYWND=$20138 | C:\Users\admin\AppData\Local\Temp\AHP_3.318.exe | AHP_3.318.tmp | ||||||||||||
User: admin Company: tuicemen software Integrity Level: HIGH Description: AHP Setup Version: Modules
| |||||||||||||||
| 1060 | "C:\Users\admin\AppData\Local\Temp\GLJAC12.tmp" C:\Program Files\Common Files\X10\DriverInstall\VA10A Video Capture\NUVISION.AX | C:\Users\admin\AppData\Local\Temp\GLJAC12.tmp | — | GLBABD2.tmp | |||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
| 1184 | DrvInst.exe "4" "0" "C:\Users\admin\AppData\Local\Temp\{4304a8bf-fafa-571f-bbcd-233778772e5e}\x10ufx2.inf" "0" "6e3c2c63b" "00000064" "WinSta0\Default" "000003F8" "208" "C:\PROGRA~1\COMMON~1\X10\DriverInstall\Wireless Transceivers" | C:\Windows\System32\drvinst.exe | svchost.exe | ||||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Driver Installation Module Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1424 | DrvInst.exe "4" "0" "C:\Users\admin\AppData\Local\Temp\{2242204f-c4ff-1c8b-dcd7-9e35bc149f34}\x10ufx2.inf" "0" "69b723a83" "00000330" "WinSta0\Default" "000003F8" "208" "C:\PROGRA~1\COMMON~1\X10\DRIVER~1\Wireless Transceivers" | C:\Windows\System32\drvinst.exe | svchost.exe | ||||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Driver Installation Module Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1628 | "C:\Users\admin\AppData\Local\Temp\GLJAC12.tmp" C:\Program Files\Common Files\X10\Common\x10net.dll | C:\Users\admin\AppData\Local\Temp\GLJAC12.tmp | — | GLBABD2.tmp | |||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
Total events
23 326
Read events
19 628
Write events
3 607
Delete events
91
Modification events
| (PID) Process: | (2104) AHP_3.318.tmp | Key: | HKEY_CURRENT_USER\Software\Microsoft\RestartManager\Session0000 |
| Operation: | write | Name: | Owner |
Value: 3808000026CF66F7B9C0DA01 | |||
| (PID) Process: | (2104) AHP_3.318.tmp | Key: | HKEY_CURRENT_USER\Software\Microsoft\RestartManager\Session0000 |
| Operation: | write | Name: | SessionHash |
Value: 30B655AECC4903112F9924CF83000177EFD6CC45CE160B59D1FCE5060383D43C | |||
| (PID) Process: | (2104) AHP_3.318.tmp | Key: | HKEY_CURRENT_USER\Software\Microsoft\RestartManager\Session0000 |
| Operation: | write | Name: | Sequence |
Value: 1 | |||
| (PID) Process: | (2104) AHP_3.318.tmp | Key: | HKEY_CURRENT_USER\Software\Microsoft\RestartManager\Session0000 |
| Operation: | write | Name: | RegFiles0000 |
Value: C:\Users\admin\AppData\Local\Temp\is-L0958.tmp\x10drivers.exe | |||
| (PID) Process: | (2104) AHP_3.318.tmp | Key: | HKEY_CURRENT_USER\Software\Microsoft\RestartManager\Session0000 |
| Operation: | write | Name: | RegFilesHash |
Value: 994FACE6FE1997A1BC760C4D336A46DCC48FC032F87C51929C98D7C17CFF599E | |||
| (PID) Process: | (2104) AHP_3.318.tmp | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall\{7E1B8A7A-AEE1-439B-A61F-56D8C1D4AE6D}_is1 |
| Operation: | write | Name: | Inno Setup: Setup Version |
Value: 5.5.4 (a) | |||
| (PID) Process: | (2104) AHP_3.318.tmp | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall\{7E1B8A7A-AEE1-439B-A61F-56D8C1D4AE6D}_is1 |
| Operation: | write | Name: | Inno Setup: App Path |
Value: C:\Program Files\ActiveHome Pro | |||
| (PID) Process: | (2104) AHP_3.318.tmp | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall\{7E1B8A7A-AEE1-439B-A61F-56D8C1D4AE6D}_is1 |
| Operation: | write | Name: | InstallLocation |
Value: C:\Program Files\ActiveHome Pro\ | |||
| (PID) Process: | (2104) AHP_3.318.tmp | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall\{7E1B8A7A-AEE1-439B-A61F-56D8C1D4AE6D}_is1 |
| Operation: | write | Name: | Inno Setup: Icon Group |
Value: ActiveHome Pro | |||
| (PID) Process: | (2104) AHP_3.318.tmp | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall\{7E1B8A7A-AEE1-439B-A61F-56D8C1D4AE6D}_is1 |
| Operation: | write | Name: | Inno Setup: User |
Value: admin | |||
Executable files
159
Suspicious files
54
Text files
53
Unknown types
22
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2104 | AHP_3.318.tmp | C:\Users\admin\AppData\Local\Temp\is-L0958.tmp\is-ECFUN.tmp | executable | |
MD5:A3F0ABD75C6F9A05F6F986EC0E759F20 | SHA256:260204AA1DB9CA1A45D170BDE7BB729A2C3FE82018052784B4517A9940859E58 | |||
| 1020 | AHP_3.318.exe | C:\Users\admin\AppData\Local\Temp\is-6HKPJ.tmp\AHP_3.318.tmp | executable | |
MD5:FBBD611263E14C1500D4600228B68318 | SHA256:C81B4C66A5D44F8805510435FF9F472B6ED0D5DD53F241AFABB5EA874C594544 | |||
| 2104 | AHP_3.318.tmp | C:\Users\admin\AppData\Local\Temp\is-L0958.tmp\is-R12SR.tmp | executable | |
MD5:B118C0B9DE2349A40F2CEB8F3570E7A3 | SHA256:7CCCC256F37F11C00D8F1F2C024248BF6C469E8F1D8C853ABCEA9486C36A8E08 | |||
| 2104 | AHP_3.318.tmp | C:\Program Files\ActiveHome Pro\unins000.exe | executable | |
MD5:457676D5A9341597A40D728F8AAFECA5 | SHA256:51468D255ADFA8B54D94F39DEFACE0330DF411789EC4E0748C26A182F1A565F3 | |||
| 3976 | AHP_3.318.exe | C:\Users\admin\AppData\Local\Temp\is-7VB9Q.tmp\AHP_3.318.tmp | executable | |
MD5:FBBD611263E14C1500D4600228B68318 | SHA256:C81B4C66A5D44F8805510435FF9F472B6ED0D5DD53F241AFABB5EA874C594544 | |||
| 2104 | AHP_3.318.tmp | C:\Users\admin\AppData\Local\Temp\is-L0958.tmp\x10drivers.exe | executable | |
MD5:B118C0B9DE2349A40F2CEB8F3570E7A3 | SHA256:7CCCC256F37F11C00D8F1F2C024248BF6C469E8F1D8C853ABCEA9486C36A8E08 | |||
| 2104 | AHP_3.318.tmp | C:\Users\admin\AppData\Local\Temp\is-L0958.tmp\_isetup\_shfoldr.dll | executable | |
MD5:92DC6EF532FBB4A5C3201469A5B5EB63 | SHA256:9884E9D1B4F8A873CCBD81F8AD0AE257776D2348D027D811A56475E028360D87 | |||
| 2104 | AHP_3.318.tmp | C:\Program Files\ActiveHome Pro\ActiveHome Pro.chm | binary | |
MD5:18CD89C190FA73E761986488F2FE3649 | SHA256:FC69DF6F2B432879AC3CE293224FF79FC089DA0CDC487C63F5CCABD6434B9DF3 | |||
| 2104 | AHP_3.318.tmp | C:\Program Files\ActiveHome Pro\is-4UO0D.tmp | — | |
MD5:— | SHA256:— | |||
| 2104 | AHP_3.318.tmp | C:\Program Files\ActiveHome Pro\AHXANT.log | — | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
4
DNS requests
0
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
— | — | 224.0.0.252:5355 | — | — | — | unknown |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
1088 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |