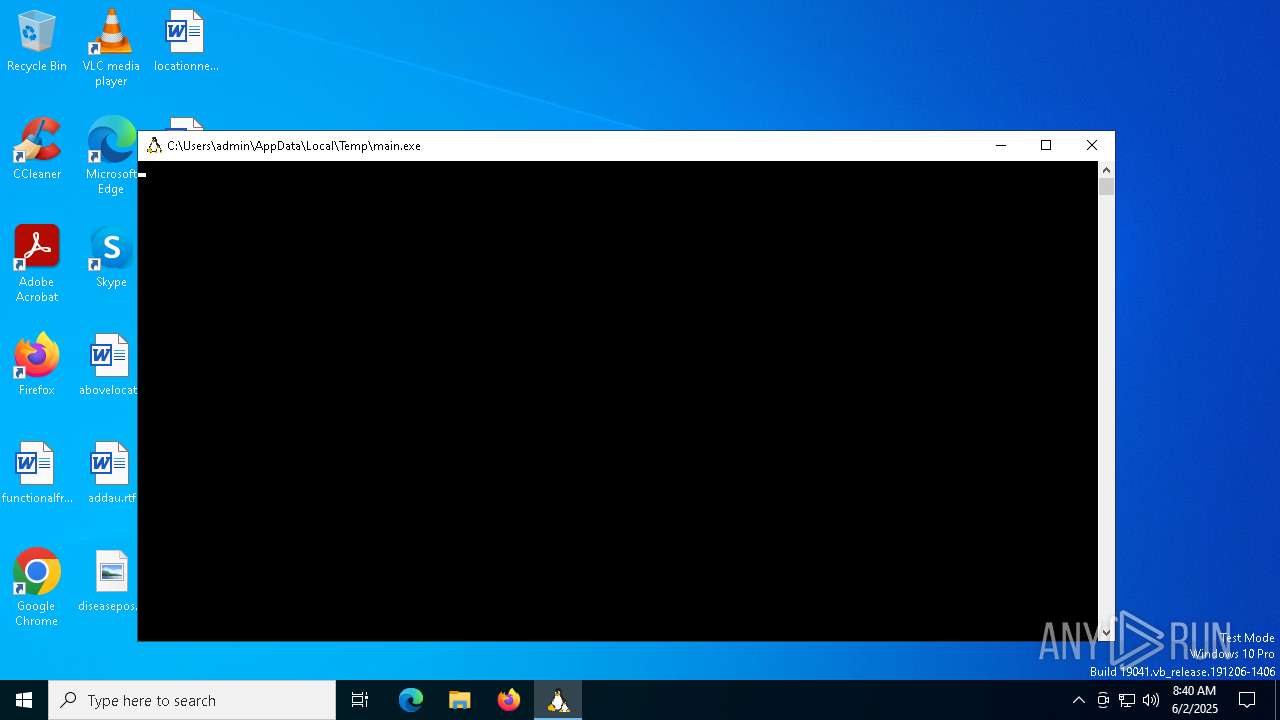
| File name: | main.exe |
| Full analysis: | https://app.any.run/tasks/f3d874fa-35bb-4919-b4c1-67fe45d81c9a |
| Verdict: | Malicious activity |
| Analysis date: | June 02, 2025, 08:40:00 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/vnd.microsoft.portable-executable |
| File info: | PE32+ executable (console) x86-64, for MS Windows, 7 sections |
| MD5: | 3E6FF94F3DE542BF127BD038BEC971D5 |
| SHA1: | 3583170EDE2552EC41DB5D487FBE3633B9915A4D |
| SHA256: | 8C88D225ED289603AC71DD7373CD63E6107B52540115AD1E40D45103E81C49E0 |
| SSDEEP: | 98304:9/0CnjbSNAnYRO4Y6ZhkDQet54nHZUj0vNQLFZfQpyJoic3yjHFGZ+O2EwToSriH:wc881mwWE/kiiikh |
MALICIOUS
No malicious indicators.SUSPICIOUS
The process drops C-runtime libraries
- main.exe (PID: 5972)
Process drops legitimate windows executable
- main.exe (PID: 5972)
Executable content was dropped or overwritten
- main.exe (PID: 5972)
Process drops python dynamic module
- main.exe (PID: 5972)
Application launched itself
- main.exe (PID: 5972)
Loads Python modules
- main.exe (PID: 7316)
Starts CMD.EXE for commands execution
- main.exe (PID: 7316)
Windows service management via SC.EXE
- sc.exe (PID: 5392)
Starts SC.EXE for service management
- cmd.exe (PID: 3124)
INFO
Checks supported languages
- main.exe (PID: 5972)
- main.exe (PID: 7316)
Reads the computer name
- main.exe (PID: 5972)
- main.exe (PID: 7316)
The sample compiled with english language support
- main.exe (PID: 5972)
Create files in a temporary directory
- main.exe (PID: 5972)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win64 Executable (generic) (87.3) |
|---|---|---|
| .exe | | | Generic Win/DOS Executable (6.3) |
| .exe | | | DOS Executable Generic (6.3) |
EXIF
EXE
| MachineType: | AMD AMD64 |
|---|---|
| TimeStamp: | 2025:06:02 08:07:58+00:00 |
| ImageFileCharacteristics: | Executable, Large address aware |
| PEType: | PE32+ |
| LinkerVersion: | 14.43 |
| CodeSize: | 178688 |
| InitializedDataSize: | 219136 |
| UninitializedDataSize: | - |
| EntryPoint: | 0xc380 |
| OSVersion: | 6 |
| ImageVersion: | - |
| SubsystemVersion: | 6 |
| Subsystem: | Windows command line |
Total processes
129
Monitored processes
6
Malicious processes
1
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 3124 | C:\WINDOWS\system32\cmd.exe /c "sc query "DbgSvc"" | C:\Windows\System32\cmd.exe | — | main.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4020 | "C:\Users\admin\AppData\Local\Temp\main.exe" | C:\Users\admin\AppData\Local\Temp\main.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 3221226540 Modules
| |||||||||||||||
| 5392 | sc query "DbgSvc" | C:\Windows\System32\sc.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Service Control Manager Configuration Tool Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5972 | "C:\Users\admin\AppData\Local\Temp\main.exe" | C:\Users\admin\AppData\Local\Temp\main.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: HIGH Modules
| |||||||||||||||
| 6032 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | main.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 7316 | "C:\Users\admin\AppData\Local\Temp\main.exe" | C:\Users\admin\AppData\Local\Temp\main.exe | — | main.exe | |||||||||||
User: admin Integrity Level: HIGH Modules
| |||||||||||||||
Total events
217
Read events
217
Write events
0
Delete events
0
Modification events
Executable files
57
Suspicious files
1
Text files
0
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 5972 | main.exe | C:\Users\admin\AppData\Local\Temp\_MEI59722\_hashlib.pyd | executable | |
MD5:3E540EF568215561590DF215801B0F59 | SHA256:0ED7A6ED080499BC6C29D7113485A8A61BDBA93087B010FCA67D9B8289CBE6FA | |||
| 5972 | main.exe | C:\Users\admin\AppData\Local\Temp\_MEI59722\_lzma.pyd | executable | |
MD5:D63E2E743EA103626D33B3C1D882F419 | SHA256:7C2D2030D5D246739C5D85F087FCF404BC36E1815E69A8AC7C9541267734FC28 | |||
| 5972 | main.exe | C:\Users\admin\AppData\Local\Temp\_MEI59722\_decimal.pyd | executable | |
MD5:21FCB8E3D4310346A5DC1A216E7E23CA | SHA256:9A0E05274CAD8D90F6BA6BC594261B36BFBDDF4F5CA6846B6367FE6A4E2FDCE4 | |||
| 5972 | main.exe | C:\Users\admin\AppData\Local\Temp\_MEI59722\_ssl.pyd | executable | |
MD5:689F1ABAC772C9E4C2D3BAD3758CB398 | SHA256:D3A89AA7E4A1DF1151632A8A5CAF338C4DDDB674EC093BFDBC122ADC9DB28A97 | |||
| 5972 | main.exe | C:\Users\admin\AppData\Local\Temp\_MEI59722\_ctypes.pyd | executable | |
MD5:29873384E13B0A78EE9857604161514B | SHA256:3CC8500A958CC125809B0467930EBCCE88A09DCC0CEDD7A45FACF3E332F7DB33 | |||
| 5972 | main.exe | C:\Users\admin\AppData\Local\Temp\_MEI59722\_socket.pyd | executable | |
MD5:566CB4D39B700C19DBD7175BD4F2B649 | SHA256:77EBA293FE03253396D7BB6E575187CD026C80766D7A345EB72AD92F0BBBC3AA | |||
| 5972 | main.exe | C:\Users\admin\AppData\Local\Temp\_MEI59722\api-ms-win-core-errorhandling-l1-1-0.dll | executable | |
MD5:5DB4B10081A52D02D078401FA62DCE20 | SHA256:FE9EC4E8C35C485E093CCBC1FAC402C9077A620F3139DD041E2E5E68115EC189 | |||
| 5972 | main.exe | C:\Users\admin\AppData\Local\Temp\_MEI59722\api-ms-win-core-file-l1-1-0.dll | executable | |
MD5:B914966BC29D1C55A656071AD9E592AA | SHA256:35A8879678F63635E2D4D41DEC511B0E71AB8E5B8BF7F8B92AC615E4452D2AF8 | |||
| 5972 | main.exe | C:\Users\admin\AppData\Local\Temp\_MEI59722\api-ms-win-core-datetime-l1-1-0.dll | executable | |
MD5:A672B1D8CE985E4A8DA41E0DE58A0E76 | SHA256:55E6F9CEE657B6A25F68AEA8A22ECB606DC5C25F69993EB023A452295BE6D2A8 | |||
| 5972 | main.exe | C:\Users\admin\AppData\Local\Temp\_MEI59722\api-ms-win-core-debug-l1-1-0.dll | executable | |
MD5:256B413DCEEB13889ACB526962ACE692 | SHA256:7D7F5F231EEEC067A841E4CAE009D9FEB9B5FA0D8FD49EE889BF812B802B9F64 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
2
TCP/UDP connections
4
DNS requests
3
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
— | — | GET | 200 | 23.53.40.176:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
4164 | svchost.exe | 40.127.240.158:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | IE | unknown |
6544 | svchost.exe | 20.190.159.23:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | IE | unknown |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
google.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |