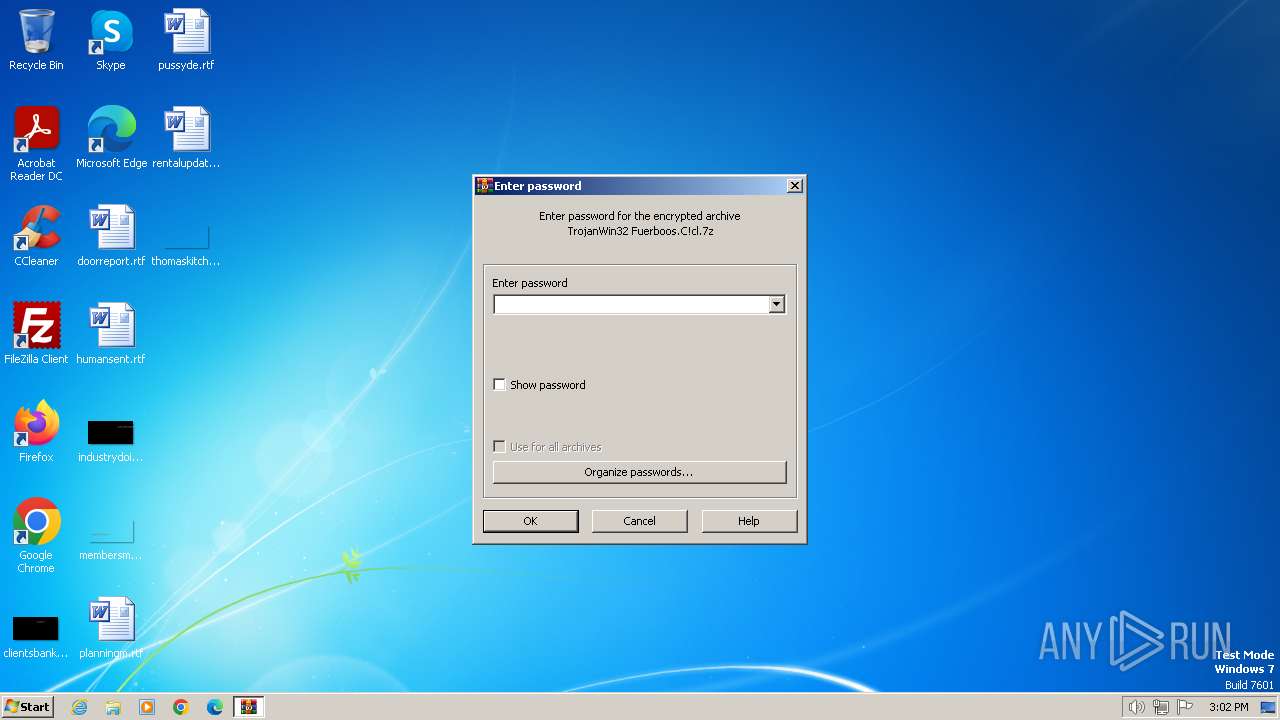
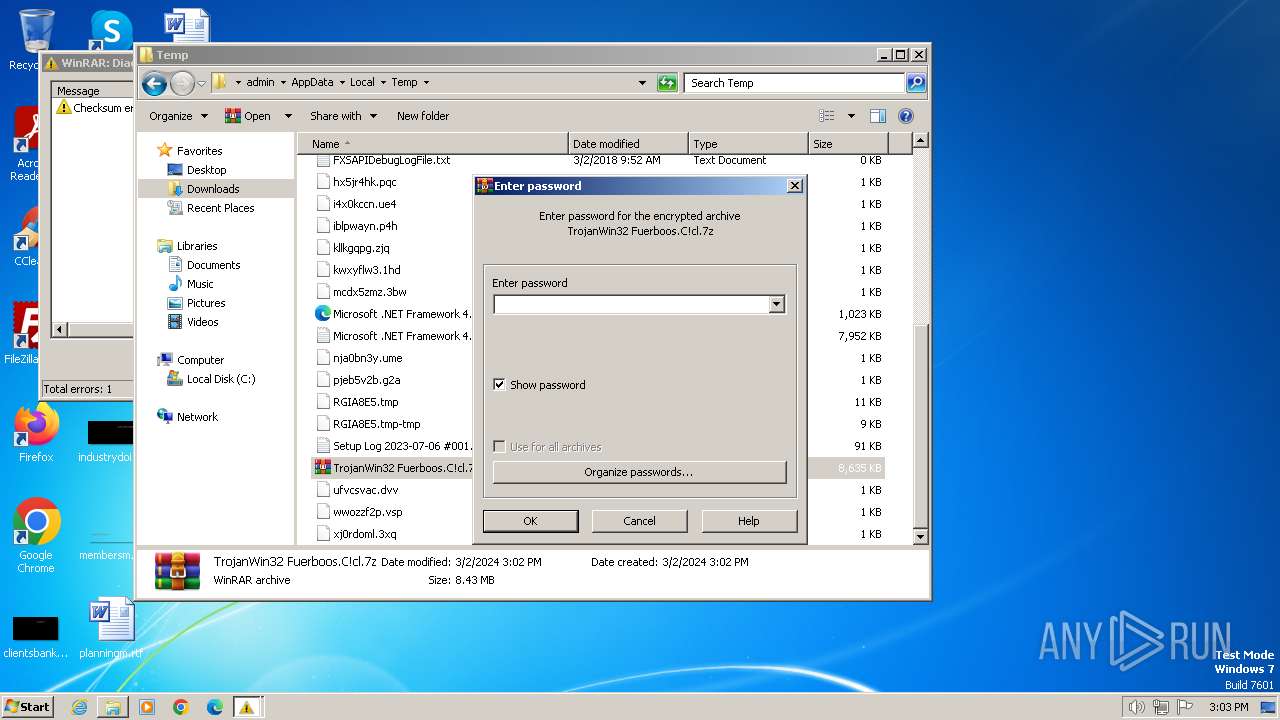
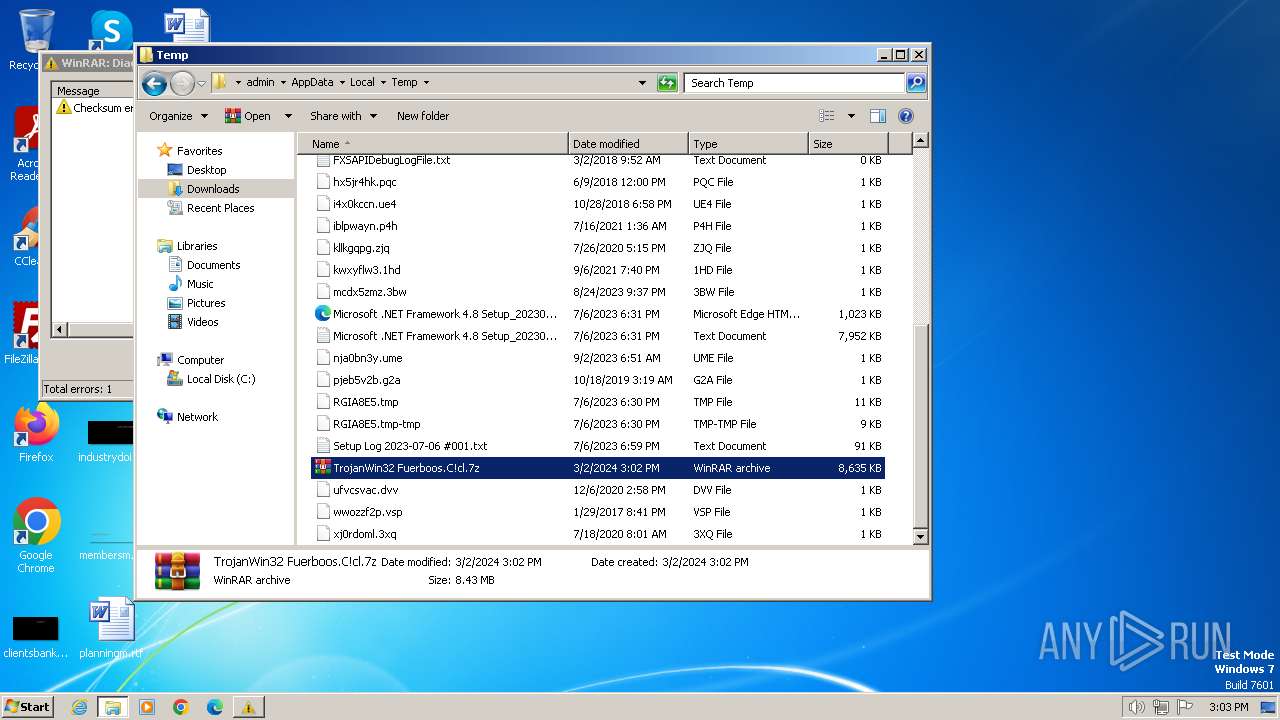
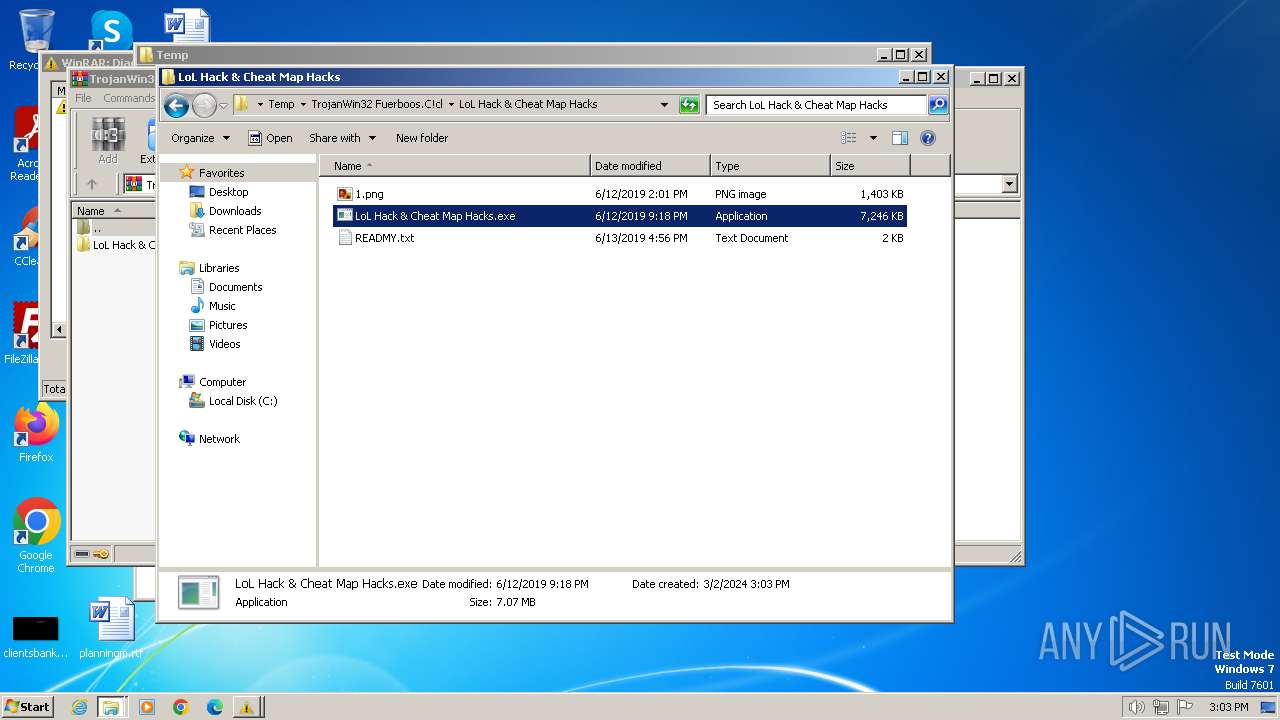
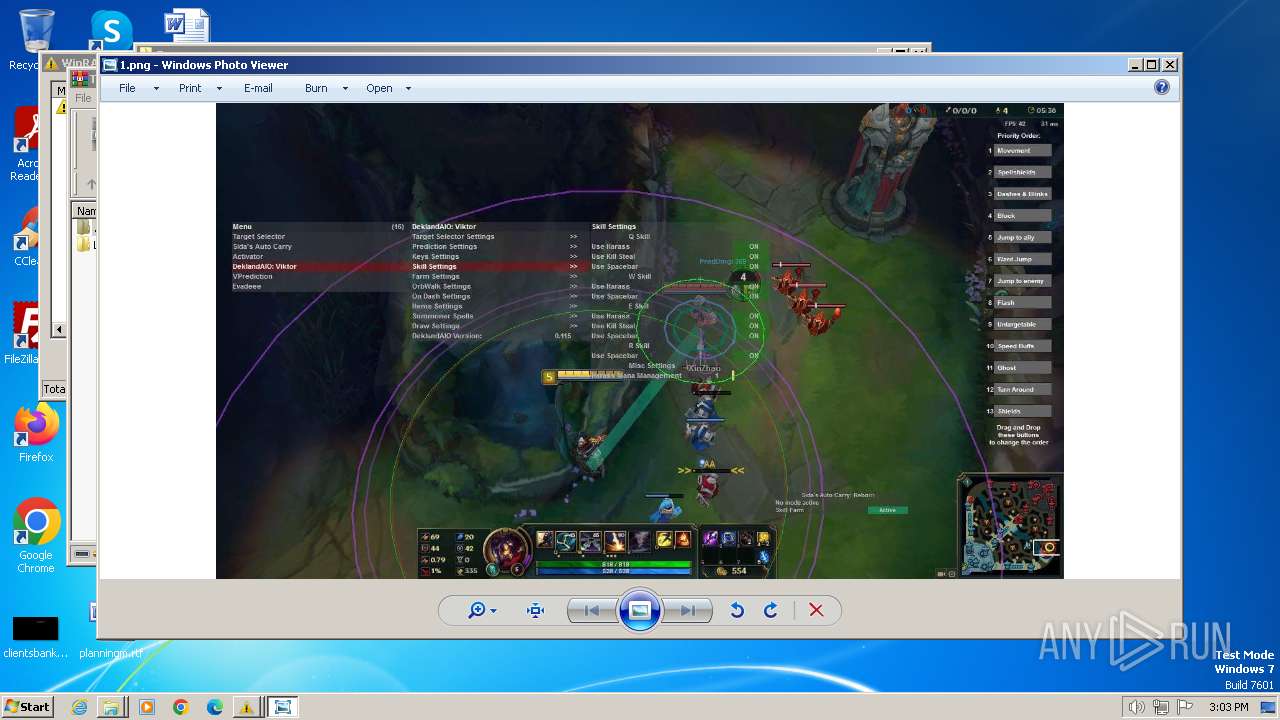
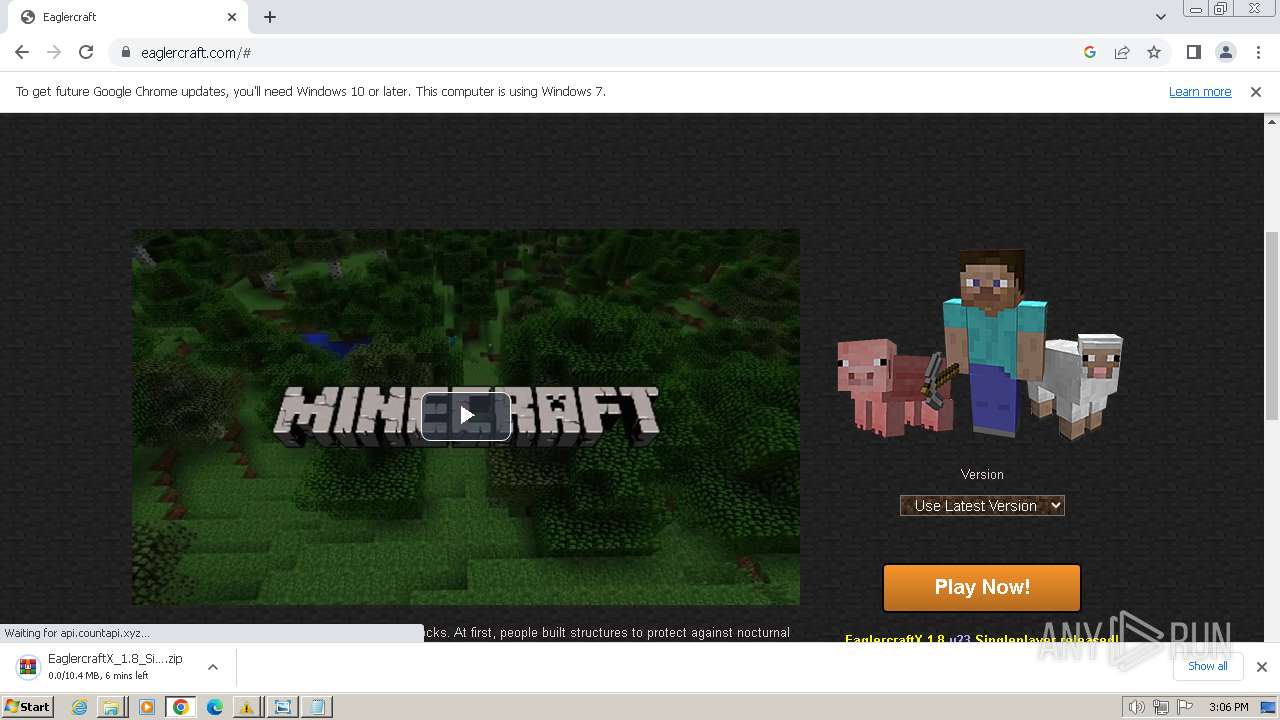
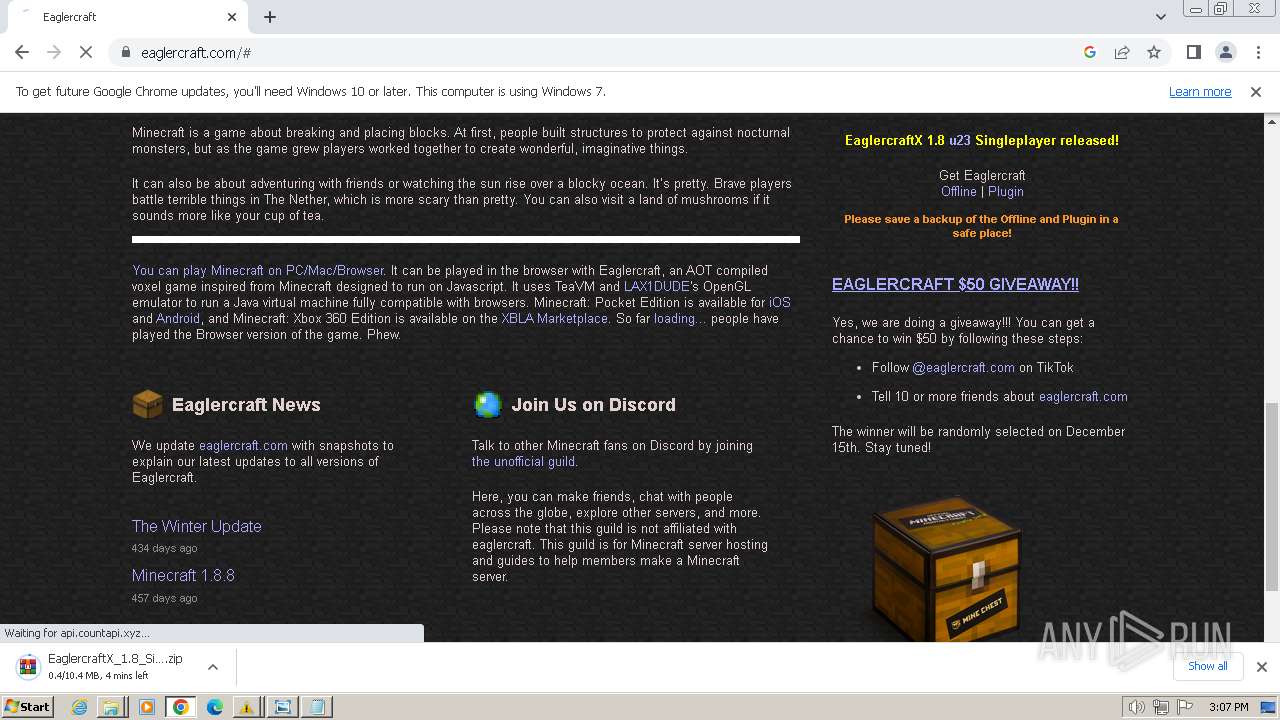
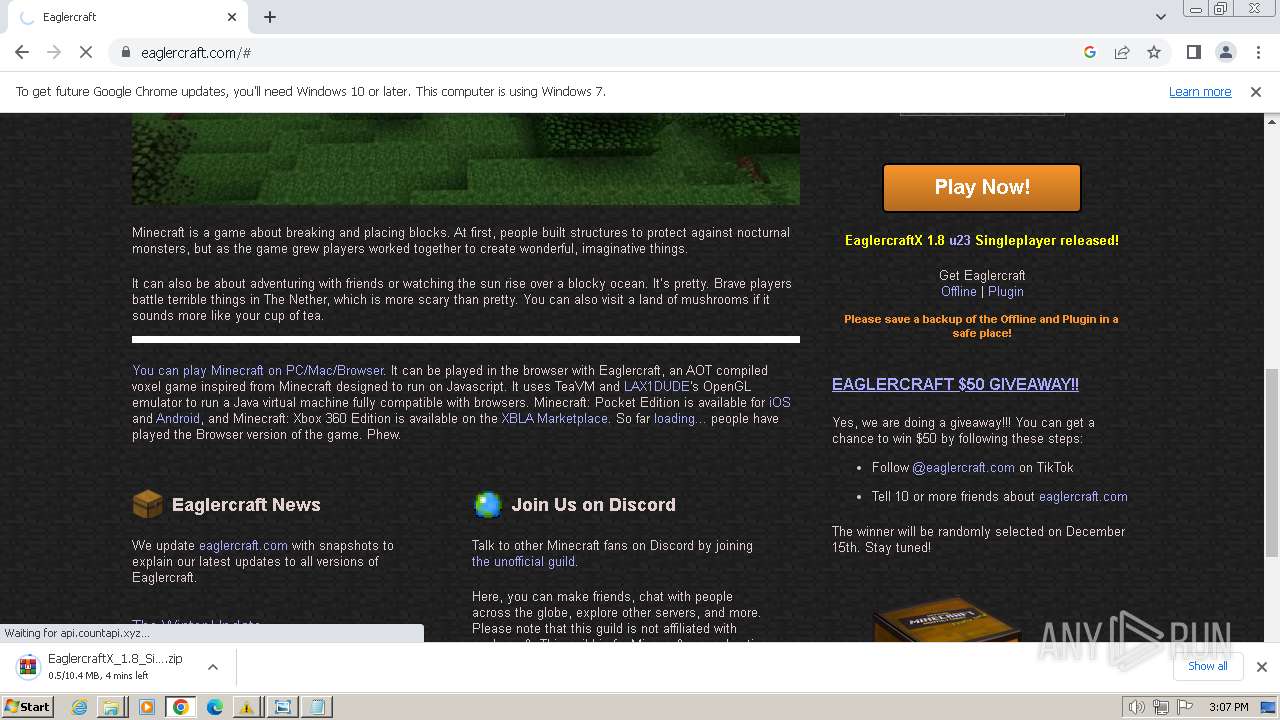
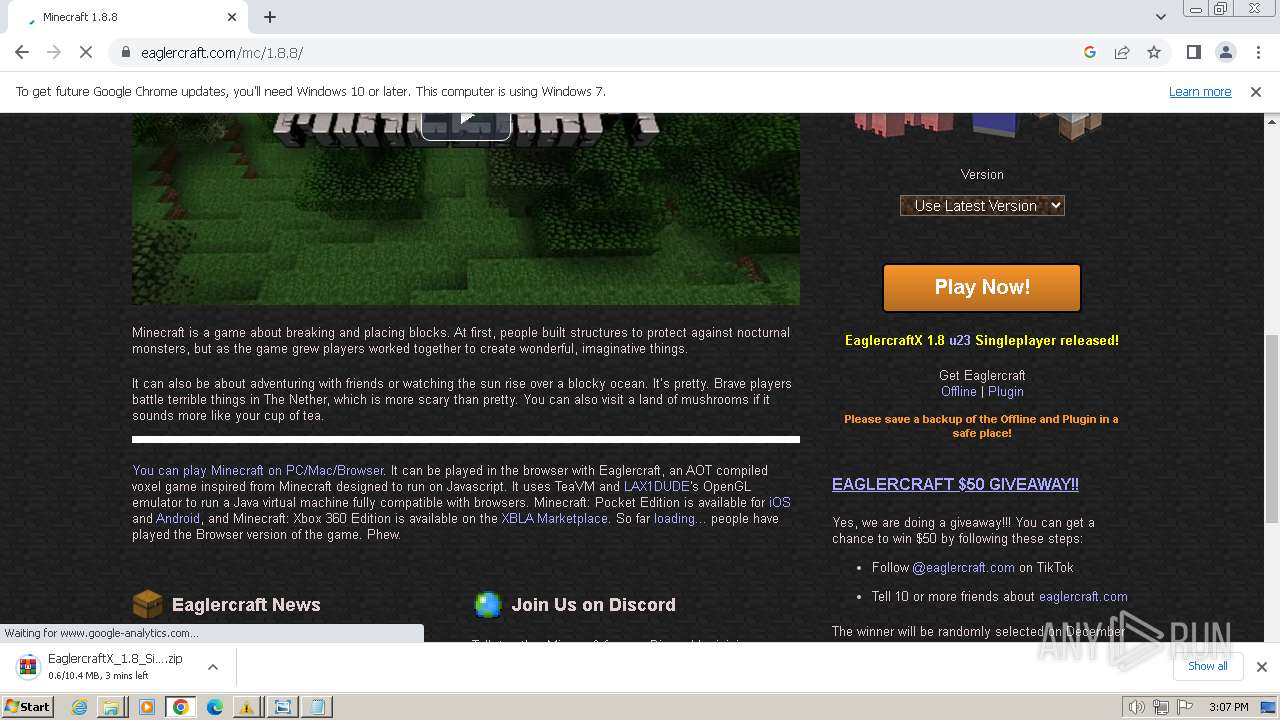
| File name: | TrojanWin32 Fuerboos.C!cl.7z |
| Full analysis: | https://app.any.run/tasks/45e9fa57-4a2e-4e93-a78c-16c6a1ecae77 |
| Verdict: | Malicious activity |
| Analysis date: | March 02, 2024, 15:02:34 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/x-7z-compressed |
| File info: | 7-zip archive data, version 0.4 |
| MD5: | 1AD2165D24FD5EC578EB4D7FAAFB9D00 |
| SHA1: | FDA3BC4585AAA73E02DD5CA7336A5802F343BCC6 |
| SHA256: | 8C889E0AA50C5ED1B05658AFA302C4001C18D784100E312F2962FAC72E572B38 |
| SSDEEP: | 98304:8A1syg4tAS4dGuI3bl7cxfSaSmJB+VOgfzSdoLU5sy8q2PYko6J6Yl+hIz7QSbUr:Jw4z1954aQBFEG |
MALICIOUS
No malicious indicators.SUSPICIOUS
Reads the BIOS version
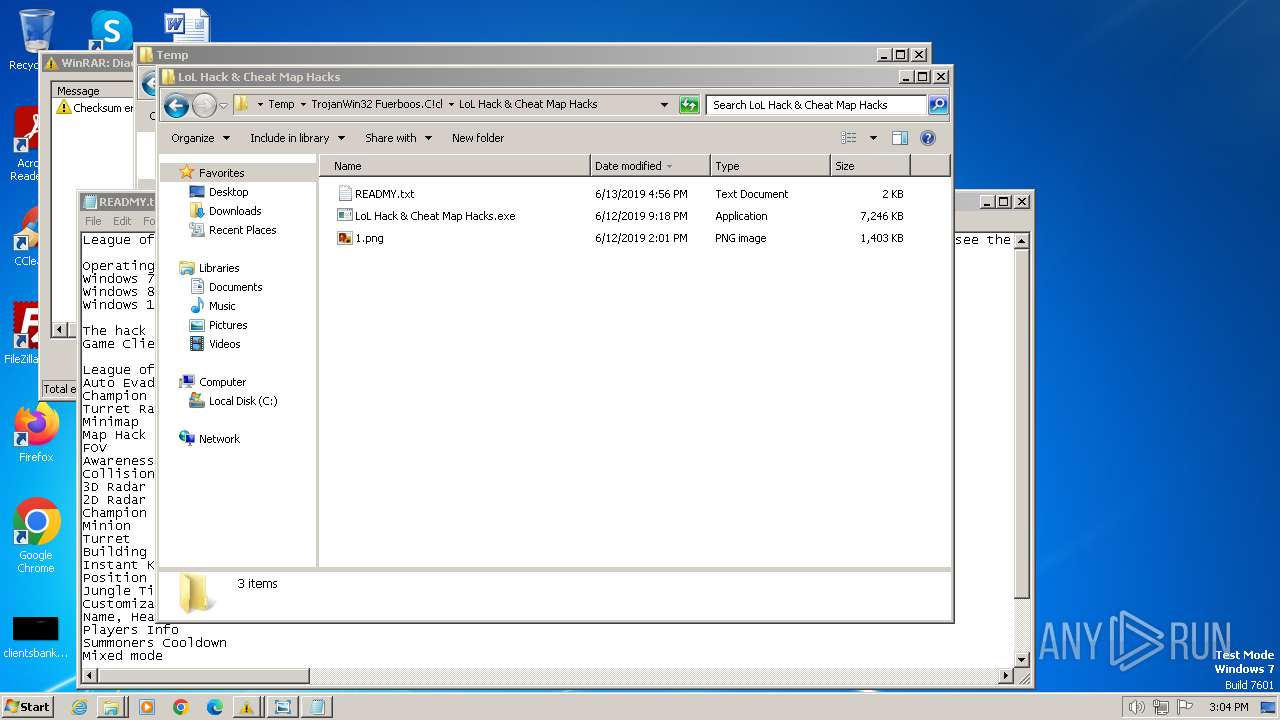
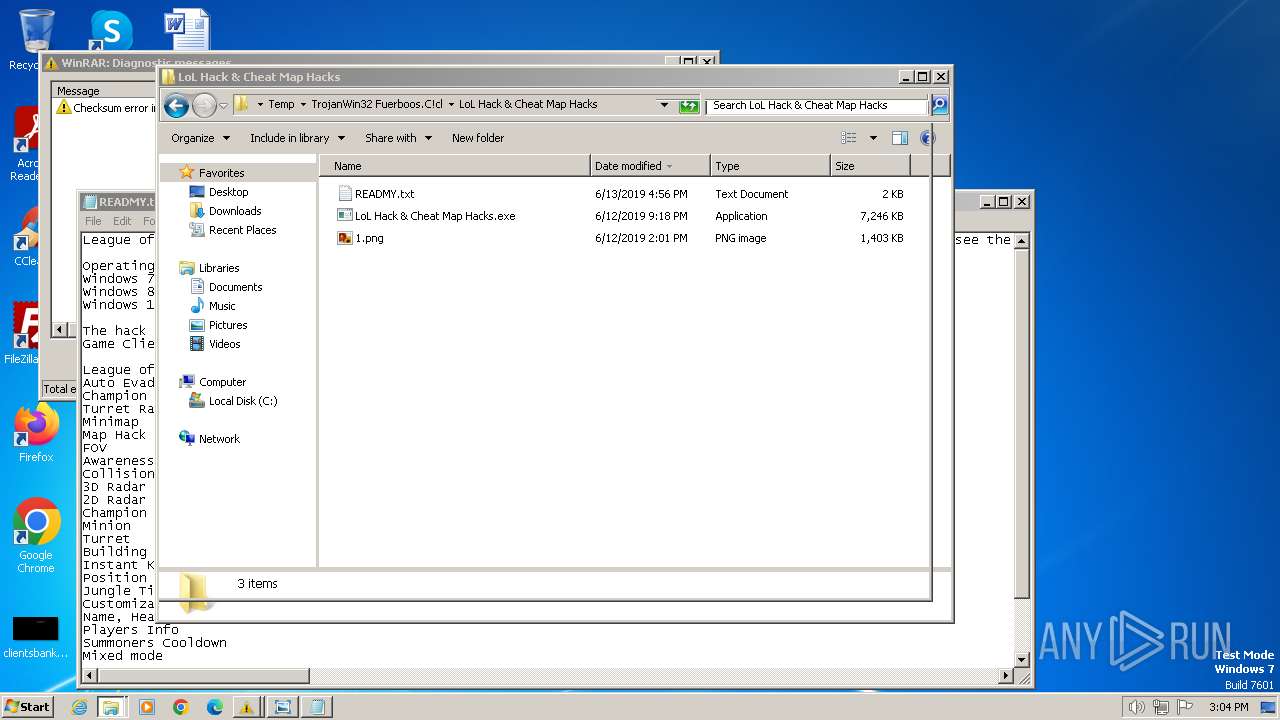
- LoL Hack & Cheat Map Hacks.exe (PID: 1368)
- LoL Hack & Cheat Map Hacks.exe (PID: 1560)
Reads the Internet Settings
- LoL Hack & Cheat Map Hacks.exe (PID: 1560)
- LoL Hack & Cheat Map Hacks.exe (PID: 1368)
Reads security settings of Internet Explorer
- LoL Hack & Cheat Map Hacks.exe (PID: 1560)
- LoL Hack & Cheat Map Hacks.exe (PID: 1368)
INFO
Drops the executable file immediately after the start
- WinRAR.exe (PID: 3276)
Manual execution by a user
- WinRAR.exe (PID: 3276)
- notepad.exe (PID: 2060)
- LoL Hack & Cheat Map Hacks.exe (PID: 1560)
- LoL Hack & Cheat Map Hacks.exe (PID: 1368)
- chrome.exe (PID: 2324)
Checks supported languages
- LoL Hack & Cheat Map Hacks.exe (PID: 1368)
- LoL Hack & Cheat Map Hacks.exe (PID: 1560)
Reads the computer name
- LoL Hack & Cheat Map Hacks.exe (PID: 1560)
- LoL Hack & Cheat Map Hacks.exe (PID: 1368)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 3276)
Reads product name
- LoL Hack & Cheat Map Hacks.exe (PID: 1560)
- LoL Hack & Cheat Map Hacks.exe (PID: 1368)
Reads the machine GUID from the registry
- LoL Hack & Cheat Map Hacks.exe (PID: 1560)
- LoL Hack & Cheat Map Hacks.exe (PID: 1368)
Reads Environment values
- LoL Hack & Cheat Map Hacks.exe (PID: 1560)
- LoL Hack & Cheat Map Hacks.exe (PID: 1368)
Checks proxy server information
- LoL Hack & Cheat Map Hacks.exe (PID: 1560)
- LoL Hack & Cheat Map Hacks.exe (PID: 1368)
Application launched itself
- chrome.exe (PID: 2324)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .7z | | | 7-Zip compressed archive (v0.4) (57.1) |
|---|---|---|
| .7z | | | 7-Zip compressed archive (gen) (42.8) |
Total processes
77
Monitored processes
34
Malicious processes
2
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 240 | C:\Windows\system32\DllHost.exe /Processid:{76D0CB12-7604-4048-B83C-1005C7DDC503} | C:\Windows\System32\dllhost.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: COM Surrogate Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 268 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --disable-gpu-compositing --lang=en-US --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=26 --mojo-platform-channel-handle=3284 --field-trial-handle=1212,i,3592892698500761146,468727817502186048,131072 --disable-features=OptimizationGuideModelDownloading,OptimizationHints,OptimizationHintsFetching,OptimizationTargetPrediction /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 109.0.5414.120 Modules
| |||||||||||||||
| 796 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --disable-gpu-compositing --lang=en-US --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=20 --mojo-platform-channel-handle=2424 --field-trial-handle=1212,i,3592892698500761146,468727817502186048,131072 --disable-features=OptimizationGuideModelDownloading,OptimizationHints,OptimizationHintsFetching,OptimizationTargetPrediction /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 109.0.5414.120 Modules
| |||||||||||||||
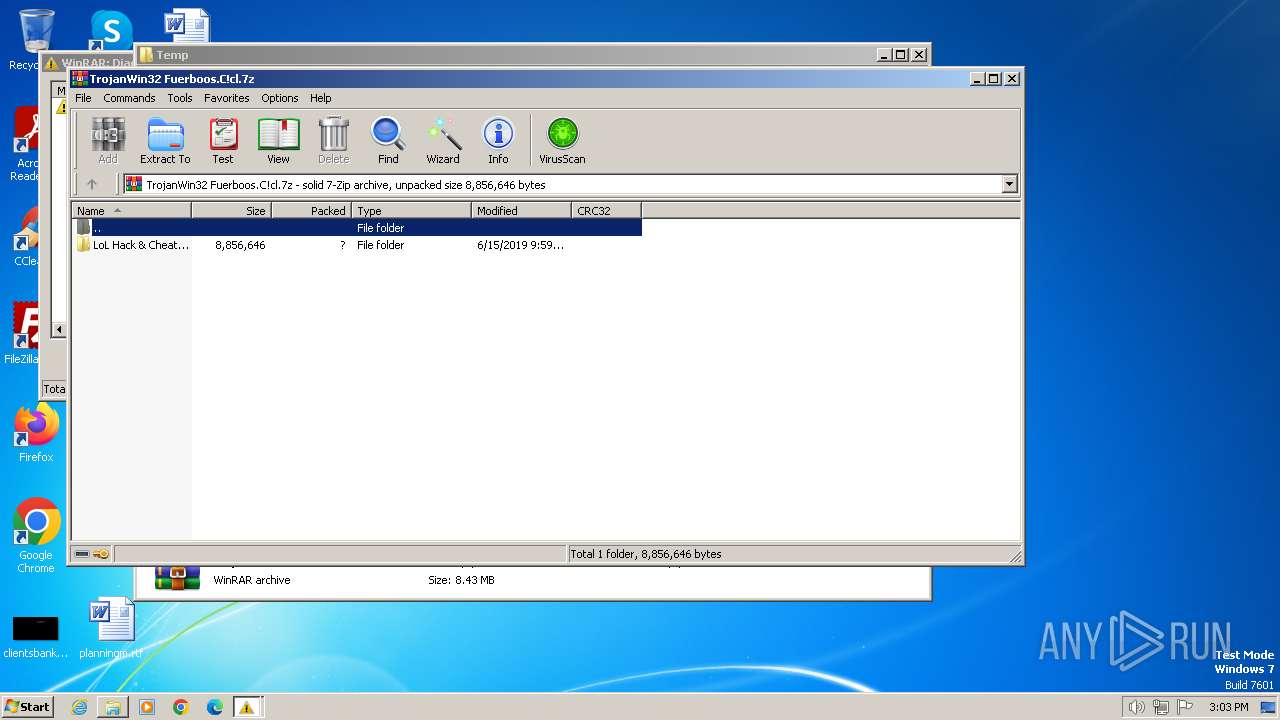
| 1368 | "C:\Users\admin\AppData\Local\Temp\TrojanWin32 Fuerboos.C!cl\LoL Hack & Cheat Map Hacks\LoL Hack & Cheat Map Hacks.exe" | C:\Users\admin\AppData\Local\Temp\TrojanWin32 Fuerboos.C!cl\LoL Hack & Cheat Map Hacks\LoL Hack & Cheat Map Hacks.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 1560 | "C:\Users\admin\AppData\Local\Temp\TrojanWin32 Fuerboos.C!cl\LoL Hack & Cheat Map Hacks\LoL Hack & Cheat Map Hacks.exe" | C:\Users\admin\AppData\Local\Temp\TrojanWin32 Fuerboos.C!cl\LoL Hack & Cheat Map Hacks\LoL Hack & Cheat Map Hacks.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 1792 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=crashpad-handler "--user-data-dir=C:\Users\admin\AppData\Local\Google\Chrome\User Data" /prefetch:7 --monitor-self-annotation=ptype=crashpad-handler "--database=C:\Users\admin\AppData\Local\Google\Chrome\User Data\Crashpad" --url=https://clients2.google.com/cr/report --annotation=channel= --annotation=plat=Win32 --annotation=prod=Chrome --annotation=ver=109.0.5414.120 --initial-client-data=0xc8,0xcc,0xd0,0x9c,0xd4,0x6bc58b38,0x6bc58b48,0x6bc58b54 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 109.0.5414.120 Modules
| |||||||||||||||
| 1796 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=gpu-process --gpu-preferences=UAAAAAAAAADgAAAYAAAAAAAAAAAAAAAAAABgAAAAAAAwAAAAAAAAAAAAAAAQAAAAAAAAAAAAAAAAAAAAAAAAAEgAAAAAAAAASAAAAAAAAAAYAAAAAgAAABAAAAAAAAAAGAAAAAAAAAAQAAAAAAAAAAAAAAAOAAAAEAAAAAAAAAABAAAADgAAAAgAAAAAAAAACAAAAAAAAAA= --mojo-platform-channel-handle=1092 --field-trial-handle=1212,i,3592892698500761146,468727817502186048,131072 --disable-features=OptimizationGuideModelDownloading,OptimizationHints,OptimizationHintsFetching,OptimizationTargetPrediction /prefetch:2 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 109.0.5414.120 Modules
| |||||||||||||||
| 2016 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --disable-gpu-compositing --lang=en-US --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=14 --mojo-platform-channel-handle=2420 --field-trial-handle=1212,i,3592892698500761146,468727817502186048,131072 --disable-features=OptimizationGuideModelDownloading,OptimizationHints,OptimizationHintsFetching,OptimizationTargetPrediction /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 109.0.5414.120 Modules
| |||||||||||||||
| 2024 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --disable-gpu-compositing --lang=en-US --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=25 --mojo-platform-channel-handle=4152 --field-trial-handle=1212,i,3592892698500761146,468727817502186048,131072 --disable-features=OptimizationGuideModelDownloading,OptimizationHints,OptimizationHintsFetching,OptimizationTargetPrediction /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 109.0.5414.120 Modules
| |||||||||||||||
| 2060 | "C:\Windows\system32\NOTEPAD.EXE" C:\Users\admin\AppData\Local\Temp\TrojanWin32 Fuerboos.C!cl\LoL Hack & Cheat Map Hacks\READMY.txt | C:\Windows\System32\notepad.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Notepad Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
Total events
21 941
Read events
21 780
Write events
147
Delete events
14
Modification events
| (PID) Process: | (2160) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (2160) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (2160) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\182\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (2160) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface |
| Operation: | write | Name: | ShowPassword |
Value: 1 | |||
| (PID) Process: | (3276) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (3276) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (3276) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\182\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (3276) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface |
| Operation: | write | Name: | ShowPassword |
Value: 1 | |||
| (PID) Process: | (3276) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\phacker.zip | |||
| (PID) Process: | (3276) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\Win7-KB3191566-x86.zip | |||
Executable files
1
Suspicious files
54
Text files
56
Unknown types
83
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2324 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\commerce_subscription_db\LOG.old~RF19a668.TMP | — | |
MD5:— | SHA256:— | |||
| 2324 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\commerce_subscription_db\LOG.old | — | |
MD5:— | SHA256:— | |||
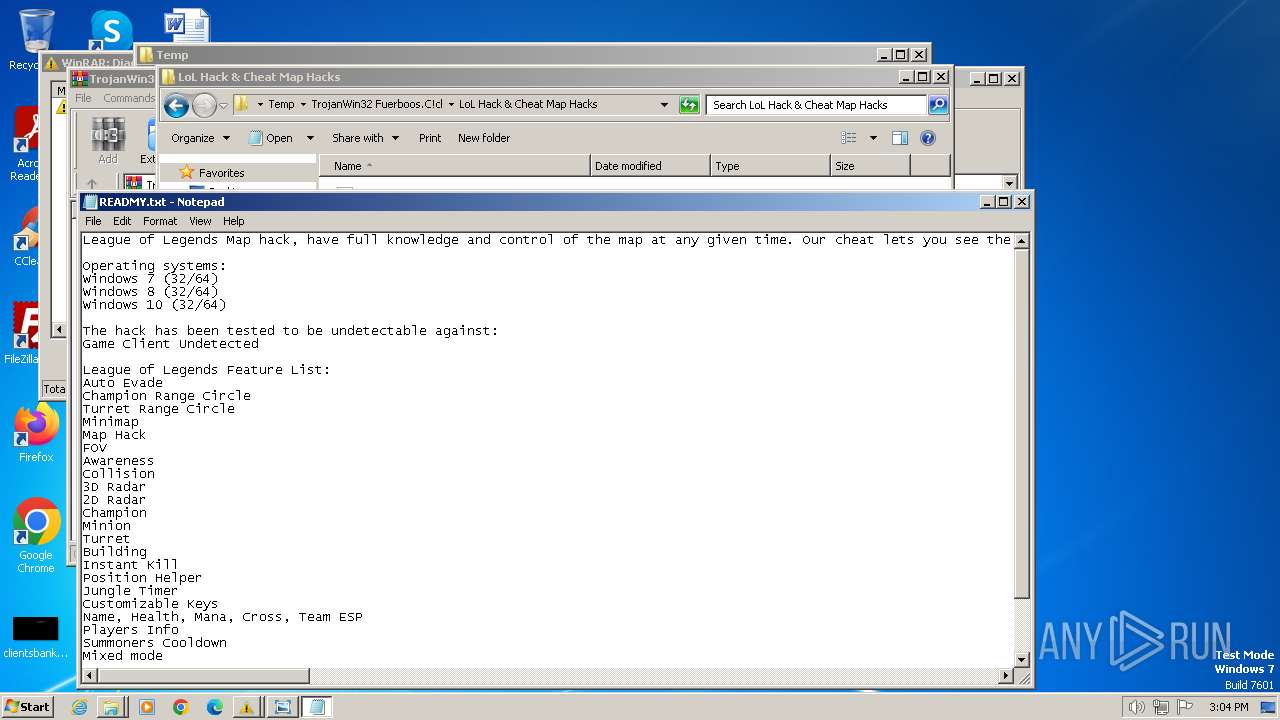
| 3276 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\TrojanWin32 Fuerboos.C!cl\LoL Hack & Cheat Map Hacks\READMY.txt | text | |
MD5:268381AB69B85369F404E49A9291CE1C | SHA256:783B5148F0636F89CAA61EA22BE2003C0F9AFB7FB8F2A88F89B087D9EFEBBD83 | |||
| 2324 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Crashpad\settings.dat | binary | |
MD5:9C016064A1F864C8140915D77CF3389A | SHA256:0E7265D4A8C16223538EDD8CD620B8820611C74538E420A88E333BE7F62AC787 | |||
| 2324 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\Session Storage\LOG.old | text | |
MD5:E53573A93829681410D5E7DBB1B61C78 | SHA256:A82D28F2C1E22A2AE0ABC5F5AF0CC8EE7AD913BAB3A0BF84CE6D8D23F67E06A3 | |||
| 2324 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\Local Storage\leveldb\LOG.old | text | |
MD5:AD0DB8476493577A67FA94A162B646C4 | SHA256:304FB5B4FD83D4A9FF1EF4CF20232A1783169C148297BFE37ED24A1D22A74F2B | |||
| 2324 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\coupon_db\LOG.old~RF19a907.TMP | — | |
MD5:— | SHA256:— | |||
| 2324 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\coupon_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 2324 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\Sync Data\LevelDB\LOG.old | text | |
MD5:ECD3386BCC950E73B86EB128A5F57622 | SHA256:C9A068EAFBC587EDFC89392F64DDD350EEB96C5CF195CDB030BAB8F6DD33833B | |||
| 2324 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\Site Characteristics Database\LOG.old~RF19a677.TMP | text | |
MD5:05CF4C3C5148DA6355D3561A9EAA5E8A | SHA256:8D720243F6876898E4F197C8867C4CEE69F1C7335C55B8A29C120B1028D93E41 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
29
TCP/UDP connections
102
DNS requests
172
Threats
15
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
856 | svchost.exe | HEAD | 403 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome_component/k4ldha5kevpu7qn7k4s3mznvgu_4.10.2710.0/oimompecagnajdejgnnjijobebaeigek_4.10.2710.0_win32_ad2kbvs6jks3au5dsxn7cqflsiiq.crx3 | unknown | — | — | unknown |
856 | svchost.exe | GET | 206 | 142.250.74.174:80 | http://dl.google.com/release2/chrome_component/k4ldha5kevpu7qn7k4s3mznvgu_4.10.2710.0/oimompecagnajdejgnnjijobebaeigek_4.10.2710.0_win32_ad2kbvs6jks3au5dsxn7cqflsiiq.crx3 | unknown | binary | 6.66 Kb | unknown |
856 | svchost.exe | GET | 206 | 142.250.74.174:80 | http://dl.google.com/release2/chrome_component/k4ldha5kevpu7qn7k4s3mznvgu_4.10.2710.0/oimompecagnajdejgnnjijobebaeigek_4.10.2710.0_win32_ad2kbvs6jks3au5dsxn7cqflsiiq.crx3 | unknown | binary | 8.36 Kb | unknown |
856 | svchost.exe | GET | 206 | 142.250.74.174:80 | http://dl.google.com/release2/chrome_component/k4ldha5kevpu7qn7k4s3mznvgu_4.10.2710.0/oimompecagnajdejgnnjijobebaeigek_4.10.2710.0_win32_ad2kbvs6jks3au5dsxn7cqflsiiq.crx3 | unknown | binary | 34.6 Kb | unknown |
856 | svchost.exe | GET | 206 | 142.250.74.174:80 | http://dl.google.com/release2/chrome_component/k4ldha5kevpu7qn7k4s3mznvgu_4.10.2710.0/oimompecagnajdejgnnjijobebaeigek_4.10.2710.0_win32_ad2kbvs6jks3au5dsxn7cqflsiiq.crx3 | unknown | binary | 17.7 Kb | unknown |
856 | svchost.exe | GET | 206 | 142.250.74.174:80 | http://dl.google.com/release2/chrome_component/k4ldha5kevpu7qn7k4s3mznvgu_4.10.2710.0/oimompecagnajdejgnnjijobebaeigek_4.10.2710.0_win32_ad2kbvs6jks3au5dsxn7cqflsiiq.crx3 | unknown | binary | 48.9 Kb | unknown |
856 | svchost.exe | GET | 206 | 142.250.74.174:80 | http://dl.google.com/release2/chrome_component/k4ldha5kevpu7qn7k4s3mznvgu_4.10.2710.0/oimompecagnajdejgnnjijobebaeigek_4.10.2710.0_win32_ad2kbvs6jks3au5dsxn7cqflsiiq.crx3 | unknown | binary | 58.7 Kb | unknown |
856 | svchost.exe | GET | 206 | 142.250.74.174:80 | http://dl.google.com/release2/chrome_component/k4ldha5kevpu7qn7k4s3mznvgu_4.10.2710.0/oimompecagnajdejgnnjijobebaeigek_4.10.2710.0_win32_ad2kbvs6jks3au5dsxn7cqflsiiq.crx3 | unknown | binary | 245 Kb | unknown |
856 | svchost.exe | GET | 206 | 142.250.74.174:80 | http://dl.google.com/release2/chrome_component/k4ldha5kevpu7qn7k4s3mznvgu_4.10.2710.0/oimompecagnajdejgnnjijobebaeigek_4.10.2710.0_win32_ad2kbvs6jks3au5dsxn7cqflsiiq.crx3 | unknown | binary | 165 Kb | unknown |
856 | svchost.exe | GET | 206 | 142.250.74.174:80 | http://dl.google.com/release2/chrome_component/k4ldha5kevpu7qn7k4s3mznvgu_4.10.2710.0/oimompecagnajdejgnnjijobebaeigek_4.10.2710.0_win32_ad2kbvs6jks3au5dsxn7cqflsiiq.crx3 | unknown | binary | 190 Kb | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
1080 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |
2324 | chrome.exe | 239.255.255.250:1900 | — | — | — | unknown |
2588 | chrome.exe | 142.250.74.35:443 | clientservices.googleapis.com | GOOGLE | US | whitelisted |
2588 | chrome.exe | 142.250.148.84:443 | accounts.google.com | GOOGLE | US | unknown |
2588 | chrome.exe | 142.250.74.100:443 | www.google.com | GOOGLE | US | whitelisted |
2324 | chrome.exe | 224.0.0.251:5353 | — | — | — | unknown |
2588 | chrome.exe | 142.250.74.99:443 | update.googleapis.com | GOOGLE | US | whitelisted |
2588 | chrome.exe | 142.250.74.78:443 | encrypted-tbn0.gstatic.com | GOOGLE | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
xp1lht2kd6h.icu |
| unknown |
clientservices.googleapis.com |
| whitelisted |
accounts.google.com |
| shared |
www.google.com |
| whitelisted |
update.googleapis.com |
| whitelisted |
encrypted-tbn0.gstatic.com |
| whitelisted |
www.gstatic.com |
| whitelisted |
content-autofill.googleapis.com |
| whitelisted |
fonts.gstatic.com |
| whitelisted |
www.googleapis.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
1080 | svchost.exe | Potentially Bad Traffic | ET INFO DNS Query for Suspicious .icu Domain |
2588 | chrome.exe | Not Suspicious Traffic | INFO [ANY.RUN] Cloudflare Network Error Logging (NEL) |
2588 | chrome.exe | Not Suspicious Traffic | INFO [ANY.RUN] Cloudflare turnstile CAPTCHA challenge |
2588 | chrome.exe | Not Suspicious Traffic | INFO [ANY.RUN] Cloudflare turnstile CAPTCHA challenge |
2588 | chrome.exe | Not Suspicious Traffic | INFO [ANY.RUN] Firebase Web App Development Platform (firebaseio .com) |
2588 | chrome.exe | Misc activity | ET HUNTING IPFS Gateway Domain in DNS Lookup (ipfs .dweb .link) |
2588 | chrome.exe | Misc activity | ET HUNTING IPFS Gateway Domain in DNS Lookup (ipfs .dweb .link) |
2588 | chrome.exe | Misc activity | ET HUNTING IPFS Gateway Domain in DNS Lookup (ipfs .dweb .link) |
2588 | chrome.exe | Misc activity | ET HUNTING Observed IPFS Gateway Domain (ipfs .dweb .link) in TLS SNI |
2588 | chrome.exe | Misc activity | ET HUNTING Observed IPFS Gateway Domain (ipfs .dweb .link) in TLS SNI |
Process | Message |
|---|---|
LoL Hack & Cheat Map Hacks.exe |
%s------------------------------------------------
--- WinLicense Professional ---
--- (c)2012 Oreans Technologies ---
------------------------------------------------
|
LoL Hack & Cheat Map Hacks.exe |
%s------------------------------------------------
--- WinLicense Professional ---
--- (c)2012 Oreans Technologies ---
------------------------------------------------
|