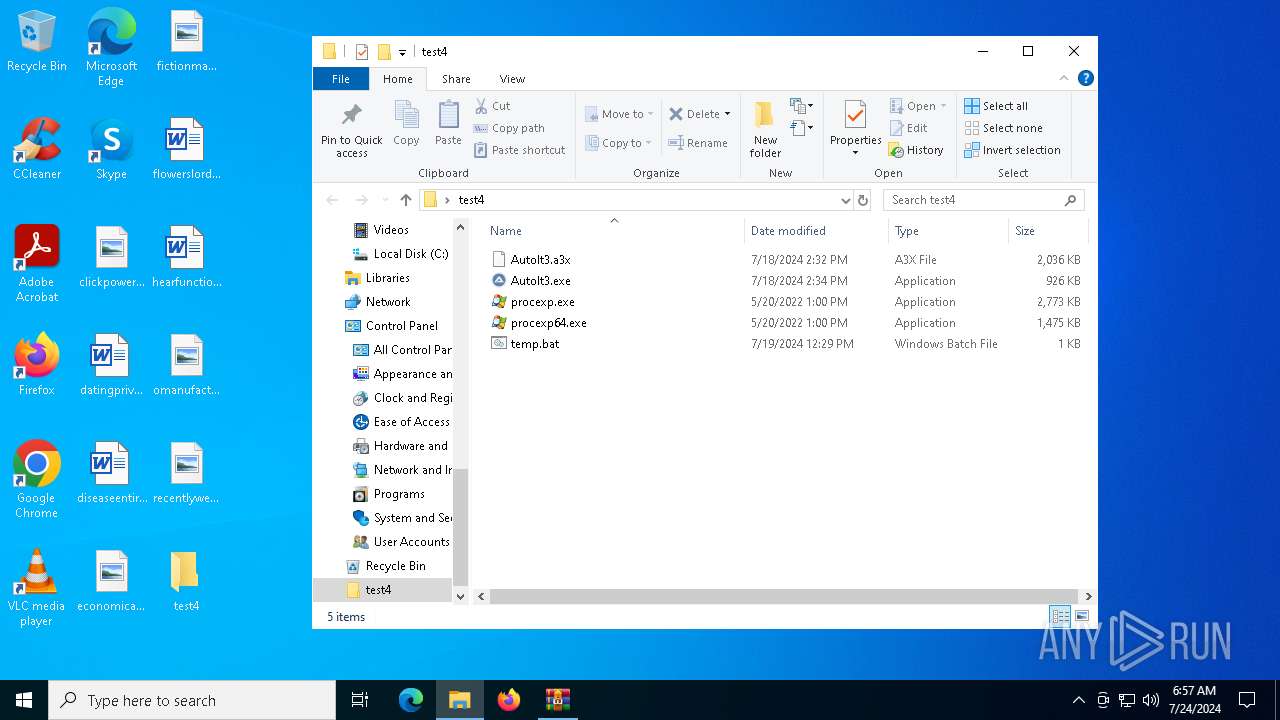
| File name: | test41.zip |
| Full analysis: | https://app.any.run/tasks/7c91cc9f-fa2e-4a28-8c80-99408ee6e281 |
| Verdict: | Malicious activity |
| Analysis date: | July 24, 2024, 06:56:56 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v2.0 to extract, compression method=store |
| MD5: | 8B4255B919E38CF1487EFC9DB01760D9 |
| SHA1: | 6367B5D73B3F312B3289561961A5110D9BD8C6E3 |
| SHA256: | 8C5E51F3B24F897D5CEA26D529C4FD40F706A1373D7756AA1B9CB529F68C2E7F |
| SSDEEP: | 98304:Ggzxtqff/GNOQcYWMp9VVnfpsI6yW5bEDwQKoqAnDdELs0qHlmZiHEK6Miv60B5W:n/irtVHs |
MALICIOUS
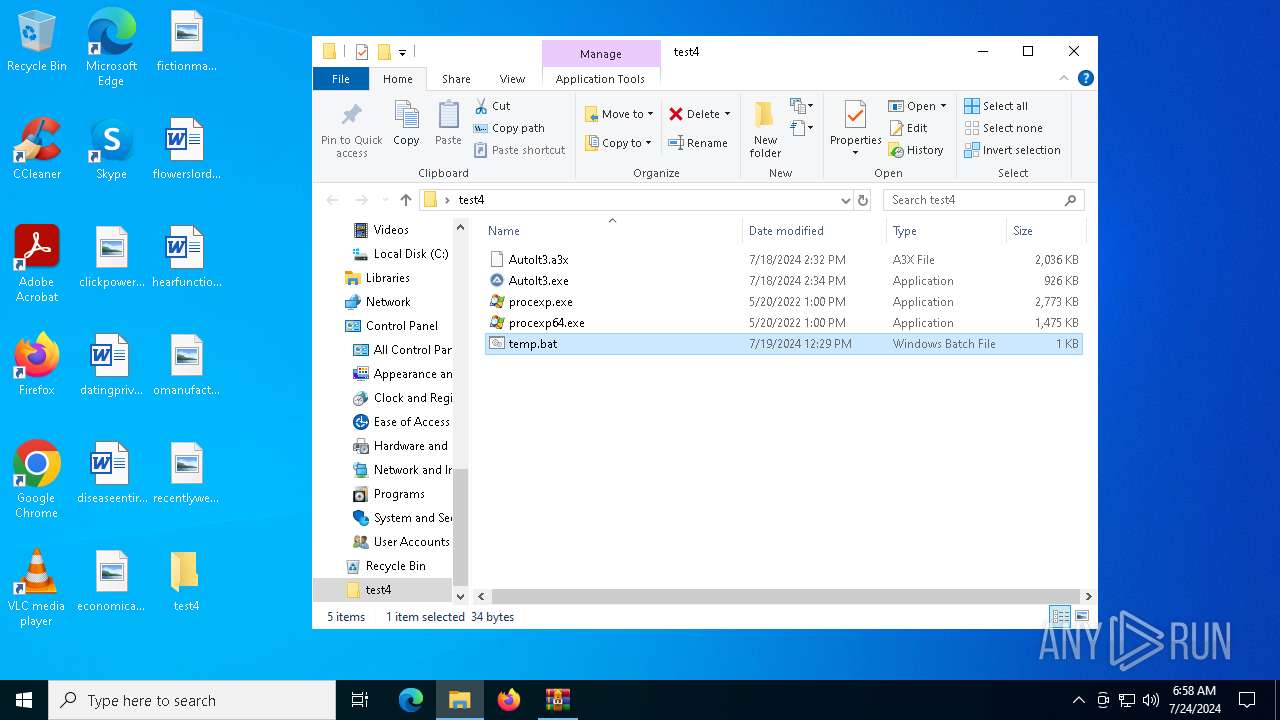
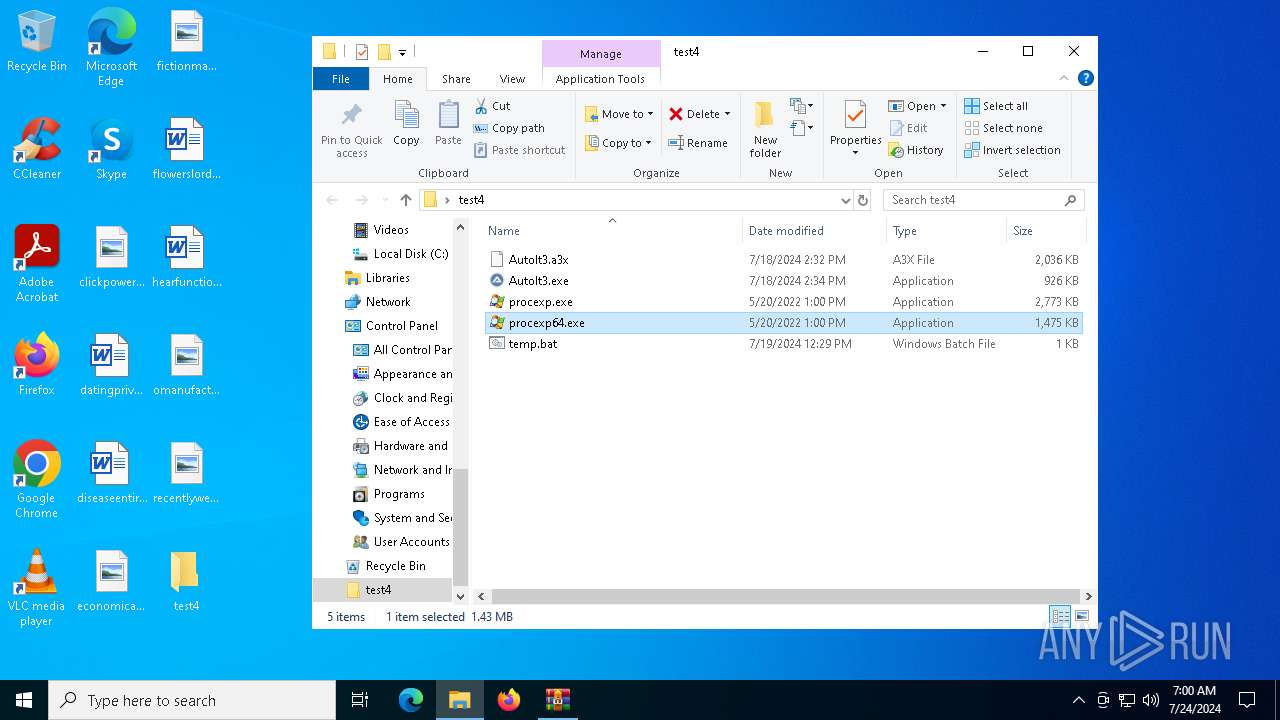
Drops the executable file immediately after the start
- WinRAR.exe (PID: 2884)
- procexp64.exe (PID: 6548)
SUSPICIOUS
Application launched itself
- cmd.exe (PID: 4328)
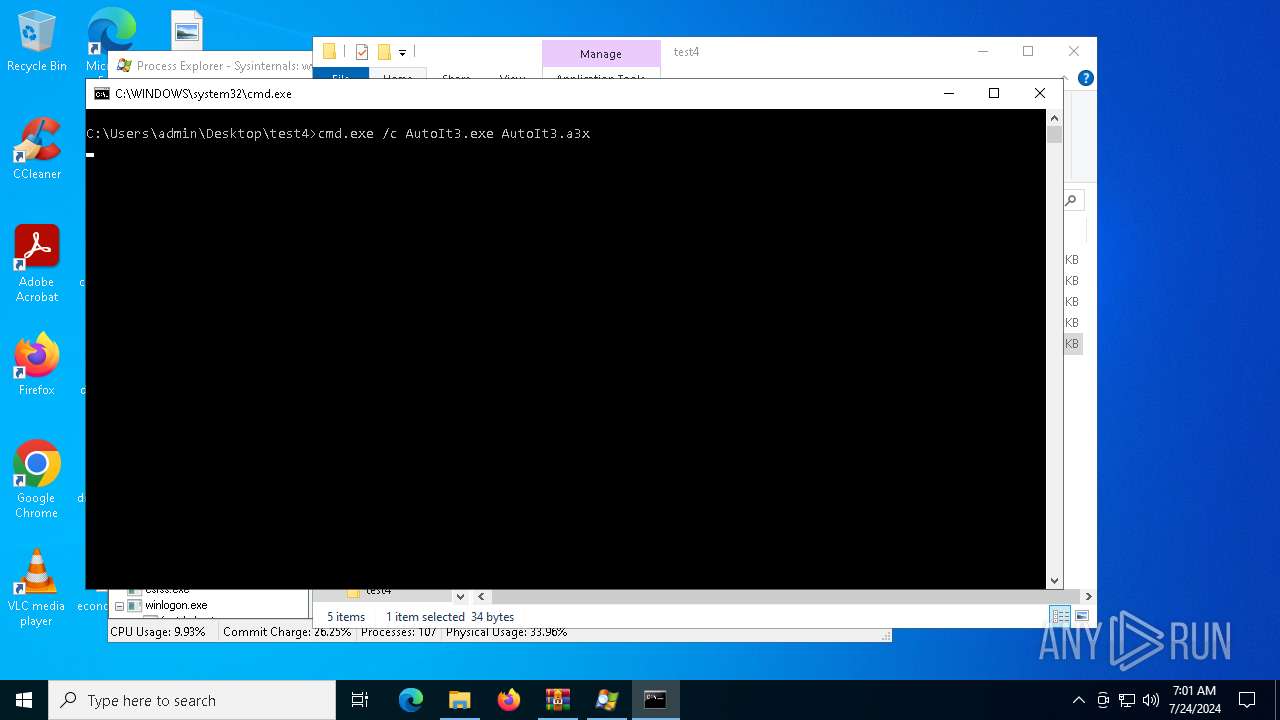
- AutoIt3.exe (PID: 6316)
- AutoIt3.exe (PID: 4040)
- cmd.exe (PID: 2100)
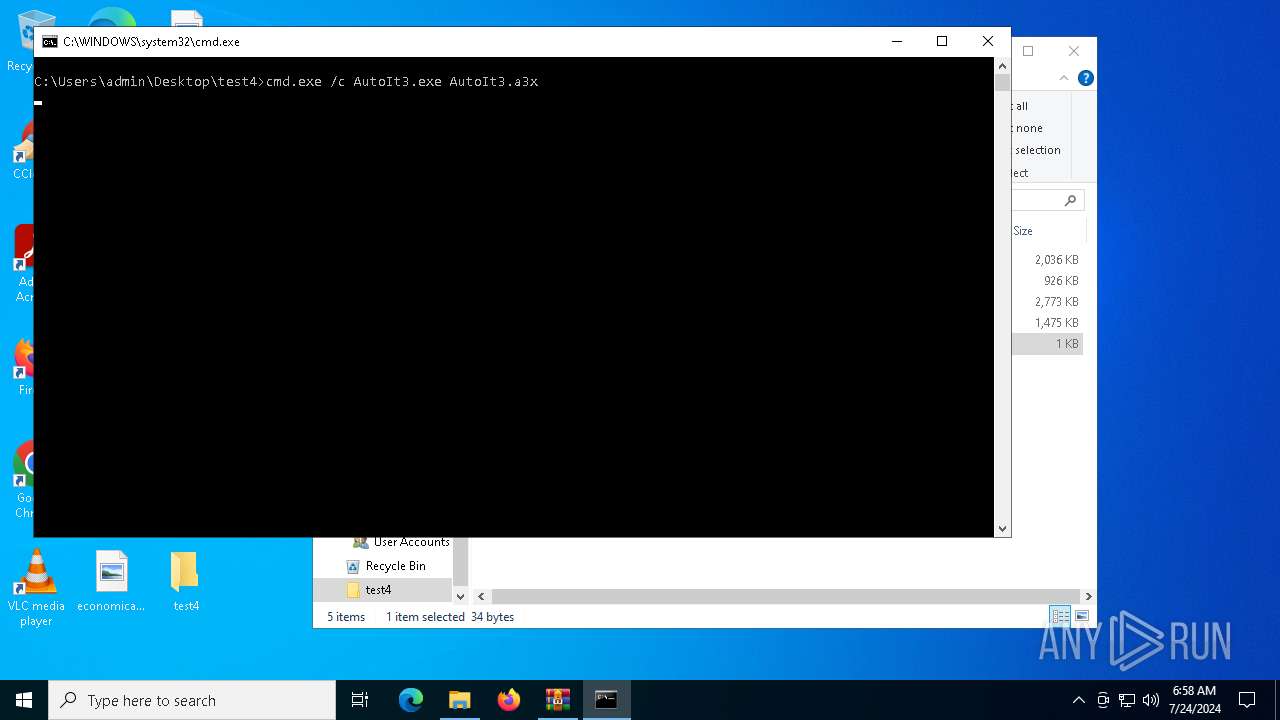
Starts CMD.EXE for commands execution
- cmd.exe (PID: 4328)
- cmd.exe (PID: 2100)
Executes application which crashes
- AutoIt3.exe (PID: 5552)
- AutoIt3.exe (PID: 2456)
The process checks if it is being run in the virtual environment
- procexp64.exe (PID: 6548)
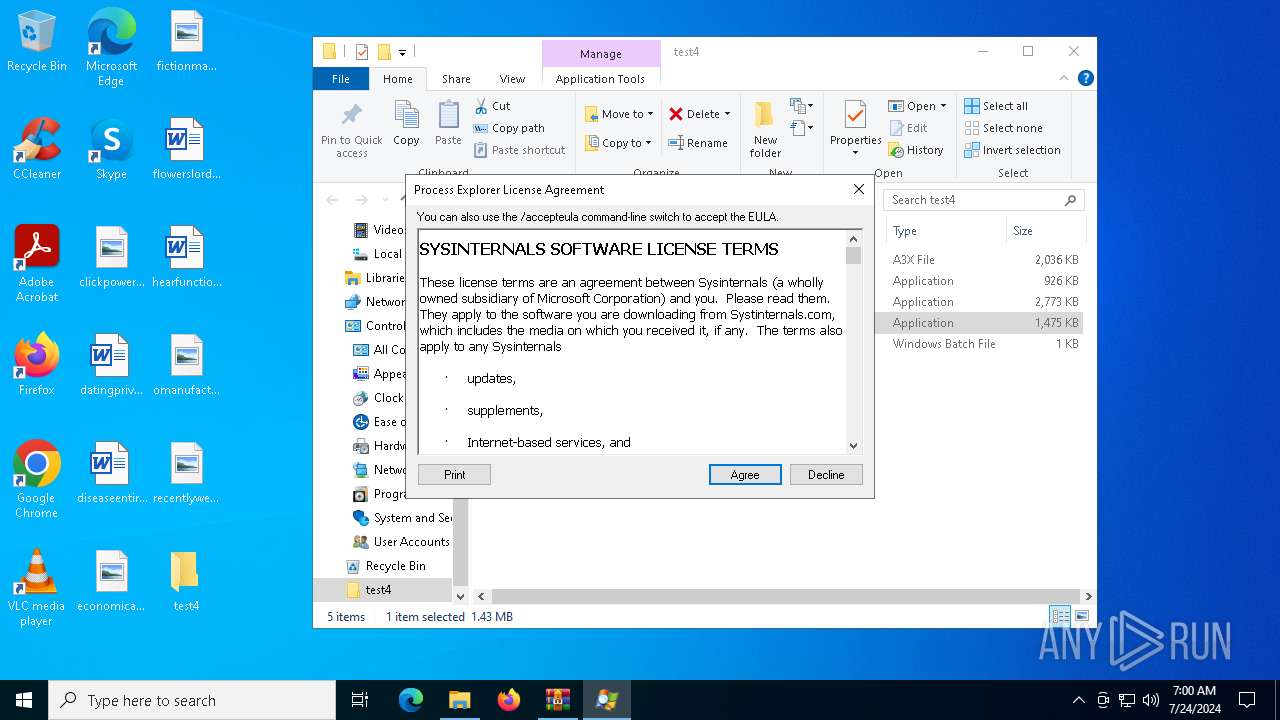
Drops a system driver (possible attempt to evade defenses)
- procexp64.exe (PID: 6548)
Executable content was dropped or overwritten
- procexp64.exe (PID: 6548)
Reads security settings of Internet Explorer
- procexp64.exe (PID: 6548)
Detected use of alternative data streams (AltDS)
- procexp64.exe (PID: 6548)
Read startup parameters
- procexp64.exe (PID: 6548)
Checks Windows Trust Settings
- procexp64.exe (PID: 6548)
INFO
Executable content was dropped or overwritten
- WinRAR.exe (PID: 2884)
Reads mouse settings
- AutoIt3.exe (PID: 6316)
- AutoIt3.exe (PID: 5552)
- AutoIt3.exe (PID: 2456)
- AutoIt3.exe (PID: 4040)
Reads the machine GUID from the registry
- AutoIt3.exe (PID: 6316)
- procexp64.exe (PID: 6548)
- AutoIt3.exe (PID: 4040)
Manual execution by a user
- cmd.exe (PID: 4328)
- procexp64.exe (PID: 6548)
- cmd.exe (PID: 2100)
Checks supported languages
- AutoIt3.exe (PID: 6316)
- AutoIt3.exe (PID: 5552)
- procexp64.exe (PID: 6548)
- AutoIt3.exe (PID: 2456)
- AutoIt3.exe (PID: 4040)
Checks proxy server information
- WerFault.exe (PID: 1256)
- procexp64.exe (PID: 6548)
- slui.exe (PID: 5032)
- WerFault.exe (PID: 3396)
Reads the software policy settings
- WerFault.exe (PID: 1256)
- WerFault.exe (PID: 3396)
- procexp64.exe (PID: 6548)
Creates files or folders in the user directory
- WerFault.exe (PID: 1256)
- procexp64.exe (PID: 6548)
- WerFault.exe (PID: 3396)
Reads product name
- procexp64.exe (PID: 6548)
Reads the computer name
- procexp64.exe (PID: 6548)
Reads Environment values
- procexp64.exe (PID: 6548)
Create files in a temporary directory
- procexp64.exe (PID: 6548)
Reads Microsoft Office registry keys
- procexp64.exe (PID: 6548)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 20 |
|---|---|
| ZipBitFlag: | - |
| ZipCompression: | None |
| ZipModifyDate: | 2024:07:24 07:49:48 |
| ZipCRC: | 0x00000000 |
| ZipCompressedSize: | - |
| ZipUncompressedSize: | - |
| ZipFileName: | test4/ |
Total processes
158
Monitored processes
17
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 504 | C:\WINDOWS\System32\slui.exe -Embedding | C:\Windows\System32\slui.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Activation Client Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1132 | C:\WINDOWS\System32\rundll32.exe C:\WINDOWS\System32\shell32.dll,SHCreateLocalServerRunDll {9aa46009-3ce0-458a-a354-715610a075e6} -Embedding | C:\Windows\System32\rundll32.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows host process (Rundll32) Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1256 | C:\WINDOWS\SysWOW64\WerFault.exe -u -p 5552 -s 632 | C:\Windows\SysWOW64\WerFault.exe | AutoIt3.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Problem Reporting Exit code: 0 Version: 10.0.19041.3996 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2096 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
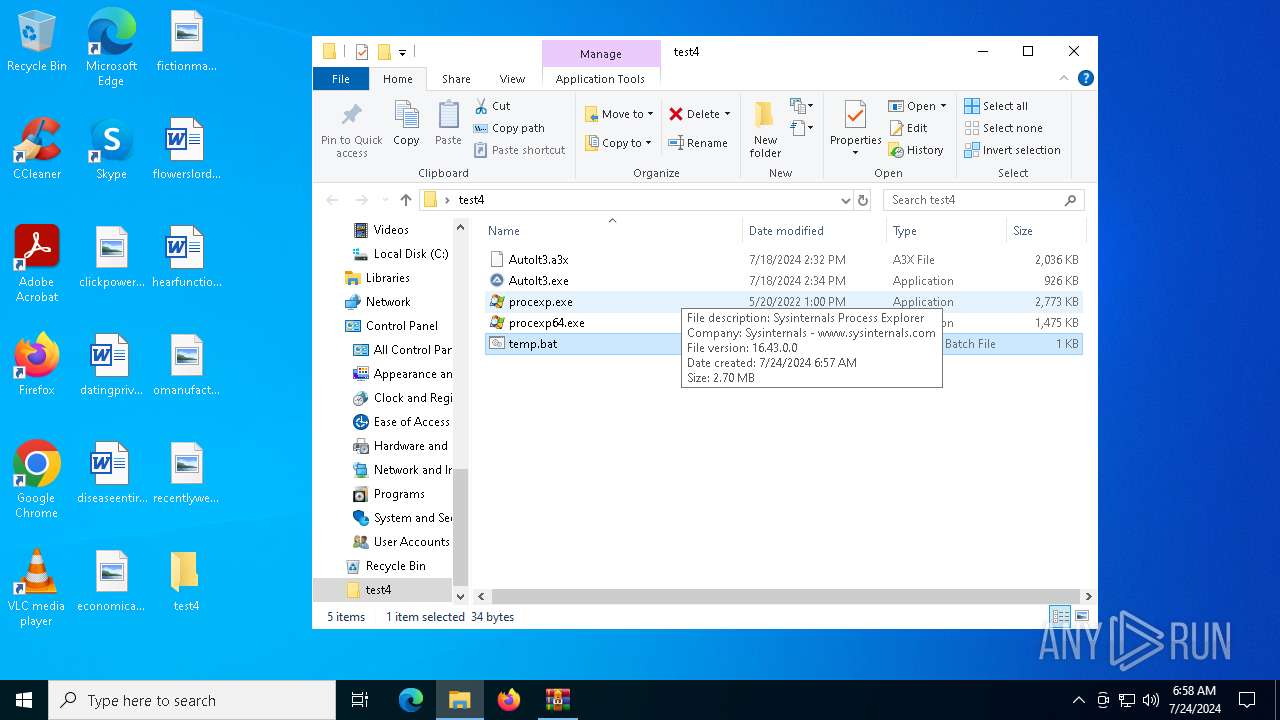
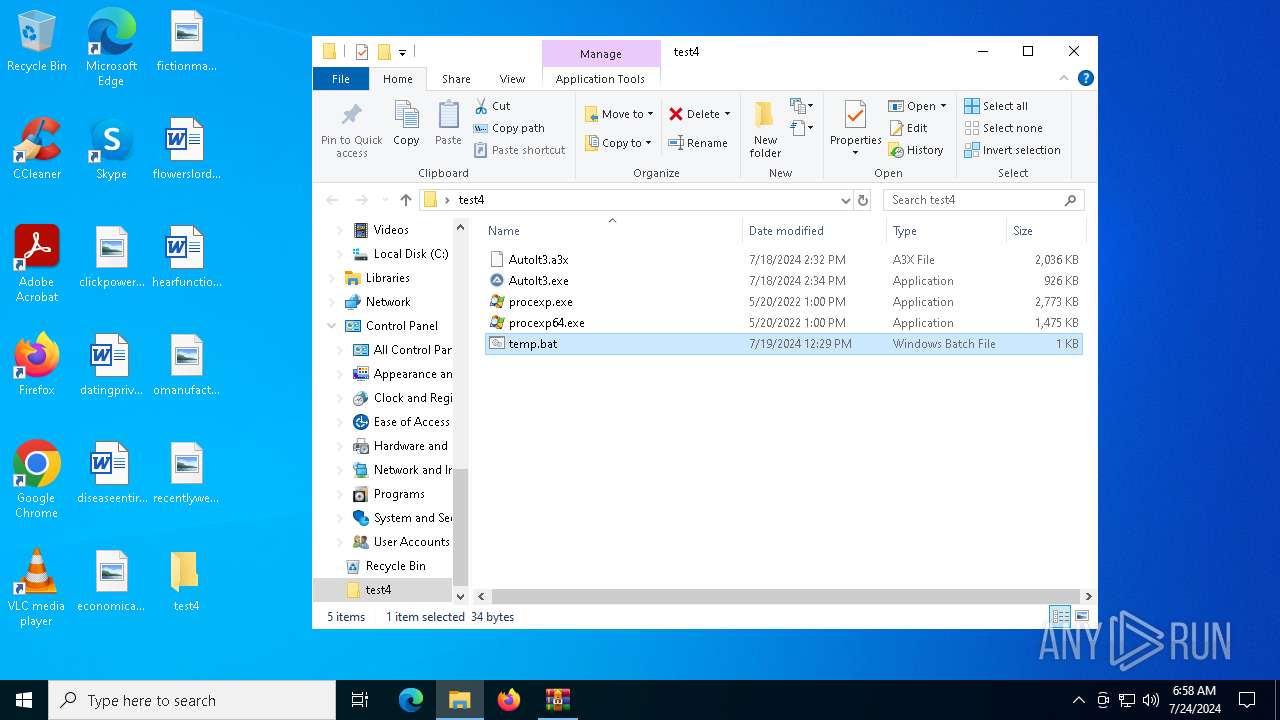
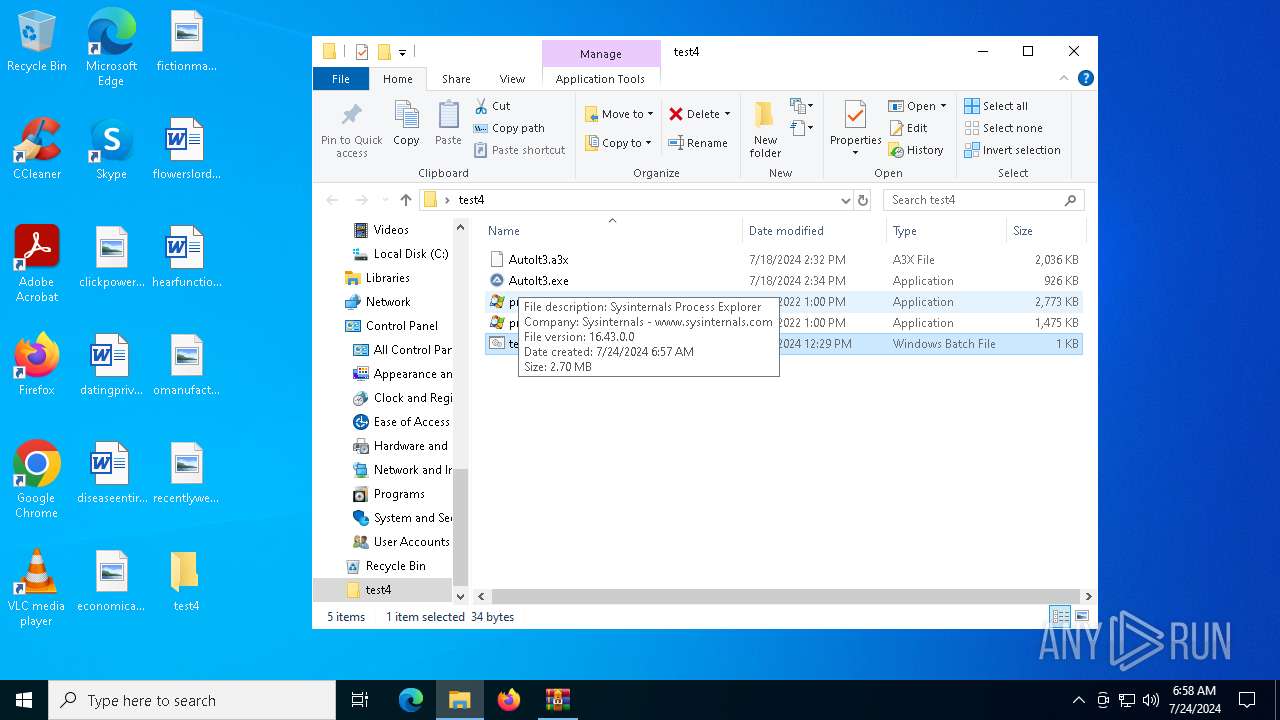
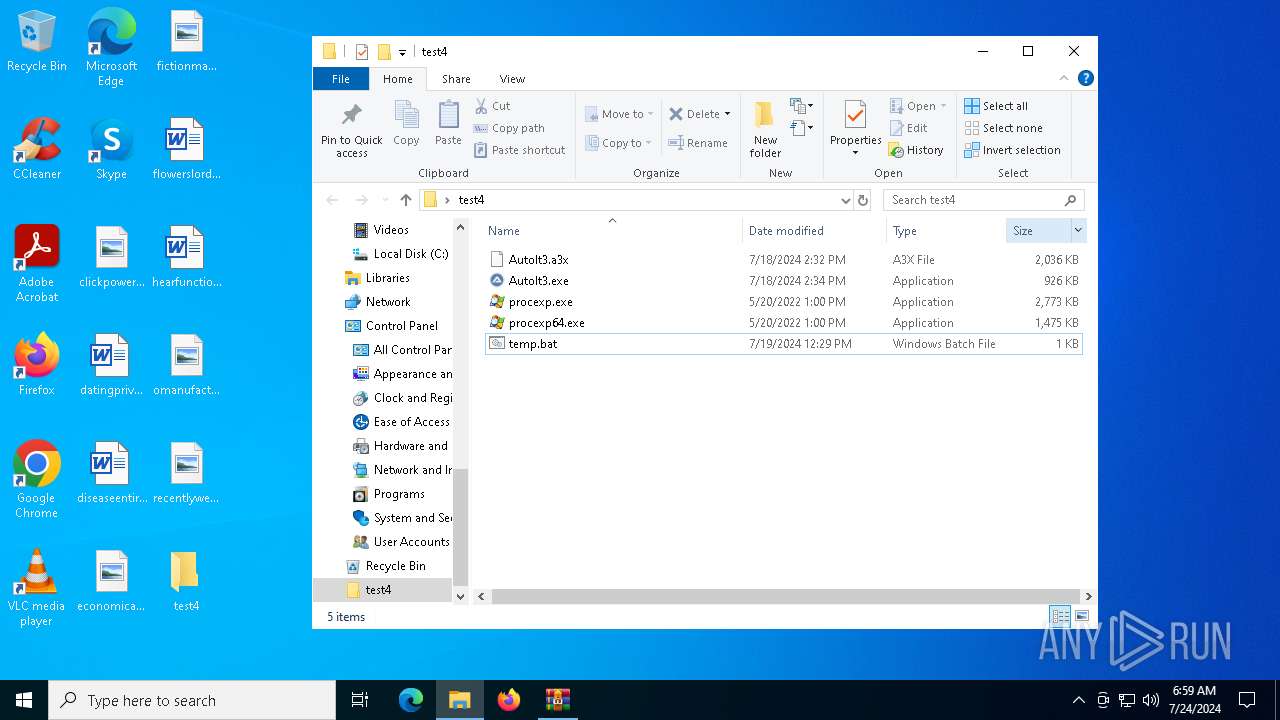
| 2100 | C:\WINDOWS\system32\cmd.exe /c ""C:\Users\admin\Desktop\test4\temp.bat" " | C:\Windows\System32\cmd.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2456 | "C:\Users\admin\Desktop\test4\AutoIt3.exe" | C:\Users\admin\Desktop\test4\AutoIt3.exe | AutoIt3.exe | ||||||||||||
User: admin Company: AutoIt Team Integrity Level: MEDIUM Description: AutoIt v3 Script Exit code: 3221225477 Version: 3, 3, 16, 1 Modules
| |||||||||||||||
| 2884 | "C:\Program Files\WinRAR\WinRAR.exe" C:\Users\admin\AppData\Local\Temp\test41.zip | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Version: 5.91.0 Modules
| |||||||||||||||
| 3396 | C:\WINDOWS\SysWOW64\WerFault.exe -u -p 2456 -s 616 | C:\Windows\SysWOW64\WerFault.exe | AutoIt3.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Problem Reporting Exit code: 0 Version: 10.0.19041.3996 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4040 | AutoIt3.exe AutoIt3.a3x | C:\Users\admin\Desktop\test4\AutoIt3.exe | — | cmd.exe | |||||||||||
User: admin Company: AutoIt Team Integrity Level: MEDIUM Description: AutoIt v3 Script Exit code: 0 Version: 3, 3, 16, 1 Modules
| |||||||||||||||
| 4328 | C:\WINDOWS\system32\cmd.exe /c ""C:\Users\admin\Desktop\test4\temp.bat" " | C:\Windows\System32\cmd.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
65 073
Read events
65 059
Write events
14
Delete events
0
Modification events
| (PID) Process: | (2884) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (2884) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (2884) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\GoogleChromeEnterpriseBundle64.zip | |||
| (PID) Process: | (2884) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\test41.zip | |||
| (PID) Process: | (2884) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (2884) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (2884) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (2884) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (2884) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\DialogEditHistory\ExtrPath |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Desktop | |||
| (PID) Process: | (1256) WerFault.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\IdentityCRL\Immersive\production\Property |
| Operation: | write | Name: | 00180010F429971D |
Value: 0100000001000000D08C9DDF0115D1118C7A00C04FC297EB0100000042CB6C300049C042863C8A748EF9A2B2000000000200000000001066000000010000200000006B2169286F19317B6ED27A11CA93F5A2610E22264976B7B9CC72528058C16D11000000000E80000000020000200000003F987F8C9549F2D2BC1684DF073A628D817FACDBD8905010DC5F675665BE78118000000093E3D572910197548E2042B1D480389A3E9D3EB541382D5B096B87A1828385B4026DF4F2D053FE9509938F827F1FDD8FFA61359F4FA8C4F3A81B811CE1DC6ECD13D2B56BAA933524B42AE73E63AC2E6DF157BD347040F0AAFDC05BC6627EB7EB0A5B93C23F52B5B8C93DE99C9C6A74BE469A4C26805021AB9BF64E56FEF62B074000000023E14BA8254B938730A4C4F0712720FF40AC640EF1649CF2455BE175E4A097108C96D219643B8CC44D81642457B08BB29CB201F8B5D8CFA505736D5408D38552 | |||
Executable files
4
Suspicious files
64
Text files
5
Unknown types
1
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 1256 | WerFault.exe | C:\ProgramData\Microsoft\Windows\WER\ReportArchive\AppCrash_AutoIt3.exe_367ab2494e7ebdd990c1283e68eb75327a23a_b05016a0_6c7f39e7-6452-485a-88c8-0dc90afa965a\Report.wer | — | |
MD5:— | SHA256:— | |||
| 2884 | WinRAR.exe | C:\Users\admin\Desktop\test4\AutoIt3.a3x | binary | |
MD5:4A1F2CBBA55A6FA758C0F0B1D043812E | SHA256:22EA25EC7A5F8047DB3494648205198F9E3C4EDF1710E784AA82BB47F7A3251D | |||
| 1256 | WerFault.exe | C:\ProgramData\Microsoft\Windows\WER\Temp\WER2B7B.tmp.dmp | binary | |
MD5:55D5724F729702C64FFAD93955764051 | SHA256:0715767B9ACCA649225FBE9BD70BD40E16FFF4D6B7288487AB150F9B8BC108D1 | |||
| 1256 | WerFault.exe | C:\ProgramData\Microsoft\Windows\WER\Temp\WER2D42.tmp.WERInternalMetadata.xml | xml | |
MD5:20CB97F0D785AF4D460A46954588782E | SHA256:C7C4229119B8E12265EECD515547BBC8CA2651B03317F700BE008718DCE09EC8 | |||
| 1256 | WerFault.exe | C:\ProgramData\Microsoft\Windows\WER\Temp\WER2D71.tmp.xml | xml | |
MD5:60E2DA00E7087503B915E689F390B58A | SHA256:6833A421AA01814C8F9DDAE9CFC1EF901E4D81073BFF019DAD3B87028EC7B8EE | |||
| 1256 | WerFault.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\21253908F3CB05D51B1C2DA8B681A785 | binary | |
MD5:82C30E45BF5F93A5DB1D5E47F913053B | SHA256:2C6BBFF9207065E8800C4AF0CB2748818ABB3CFFC0D6D518FE17F76A232F8967 | |||
| 6548 | procexp64.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\4C7F163ED126D5C3CB9457F68EC64E9E | binary | |
MD5:06EEA670780D7B3466A0BD38DC27C6BD | SHA256:95924B9397CFDB5110F5BB0BAE48C7C70E214A0BDD617DC4EE59CBDDE5E77CE9 | |||
| 6548 | procexp64.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\0B8A20E1F3F4D73D52A19929F922C892 | binary | |
MD5:0840F3C261E695105CD15C84EA85BEED | SHA256:F60632399A87485A7417DDF8B407DA66794C37347B3AA9E995EC389ECD091947 | |||
| 6548 | procexp64.exe | C:\Users\admin\AppData\Local\Temp\PROCEXP152.SYS | executable | |
MD5:97E3A44EC4AE58C8CC38EEFC613E950E | SHA256:440883CD9D6A76DB5E53517D0EC7FE13D5A50D2F6A7F91ECFC863BC3490E4F5C | |||
| 6548 | procexp64.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\45AE547469FB7137480E06153457A2DD | binary | |
MD5:647FDACFC3E6C5E01F51BCC03C1A7241 | SHA256:2452D95FBC94B05ABD449EFB967F1FC73E450B03F5D2F7253A48BFAD9E0999AC | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
41
TCP/UDP connections
76
DNS requests
59
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
6544 | backgroundTaskHost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | whitelisted |
6548 | procexp64.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/MicWinProPCA2011_2011-10-19.crl%20 | unknown | — | — | whitelisted |
5904 | backgroundTaskHost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | whitelisted |
3148 | OfficeClickToRun.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAUZZSZEml49Gjh0j13P68w%3D | unknown | — | — | whitelisted |
6548 | procexp64.exe | GET | 200 | 2.16.164.43:80 | http://crl.microsoft.com/pki/crl/products/MicCodSigPCA_2010-07-06.crl | unknown | — | — | whitelisted |
6548 | procexp64.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/MicCodSigPCA2011_2011-07-08.crl | unknown | — | — | whitelisted |
6548 | procexp64.exe | GET | 200 | 2.16.164.25:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut_2010-06-23.crl | unknown | — | — | whitelisted |
6548 | procexp64.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20Time-Stamp%20PCA%202010(1).crl | unknown | — | — | whitelisted |
6548 | procexp64.exe | GET | 200 | 2.16.164.51:80 | http://crl.microsoft.com/pki/crl/products/MicTimStaPCA_2010-07-01.crl | unknown | — | — | whitelisted |
6548 | procexp64.exe | GET | 404 | 172.64.149.23:80 | http://crl.trust-provider.com/AddTrustExternalCARoot.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4136 | RUXIMICS.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
6012 | MoUsoCoreWorker.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
3076 | svchost.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
— | — | 239.255.255.250:1900 | — | — | — | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
4204 | svchost.exe | 4.209.32.67:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | US | unknown |
3076 | svchost.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | unknown |
4012 | slui.exe | 20.83.72.98:443 | activation-v2.sls.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
5272 | svchost.exe | 20.190.159.4:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
activation-v2.sls.microsoft.com |
| whitelisted |
www.bing.com |
| whitelisted |
login.live.com |
| whitelisted |
go.microsoft.com |
| whitelisted |
arc.msn.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |