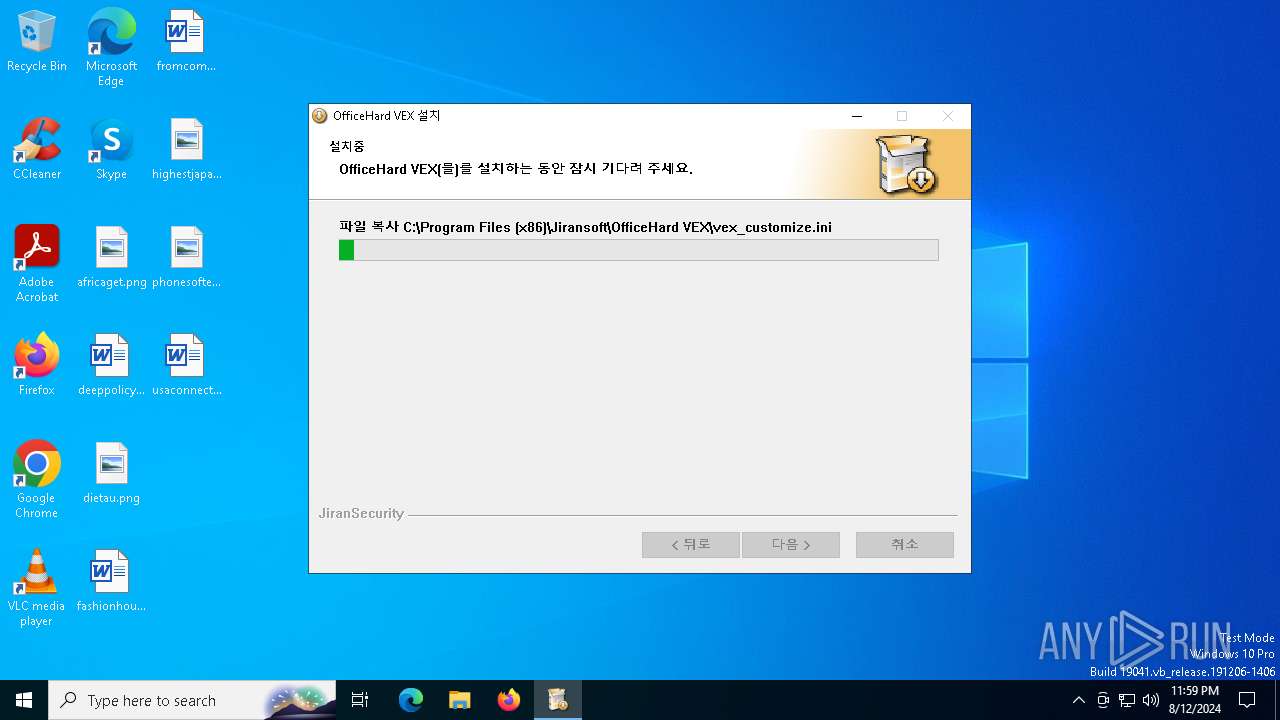
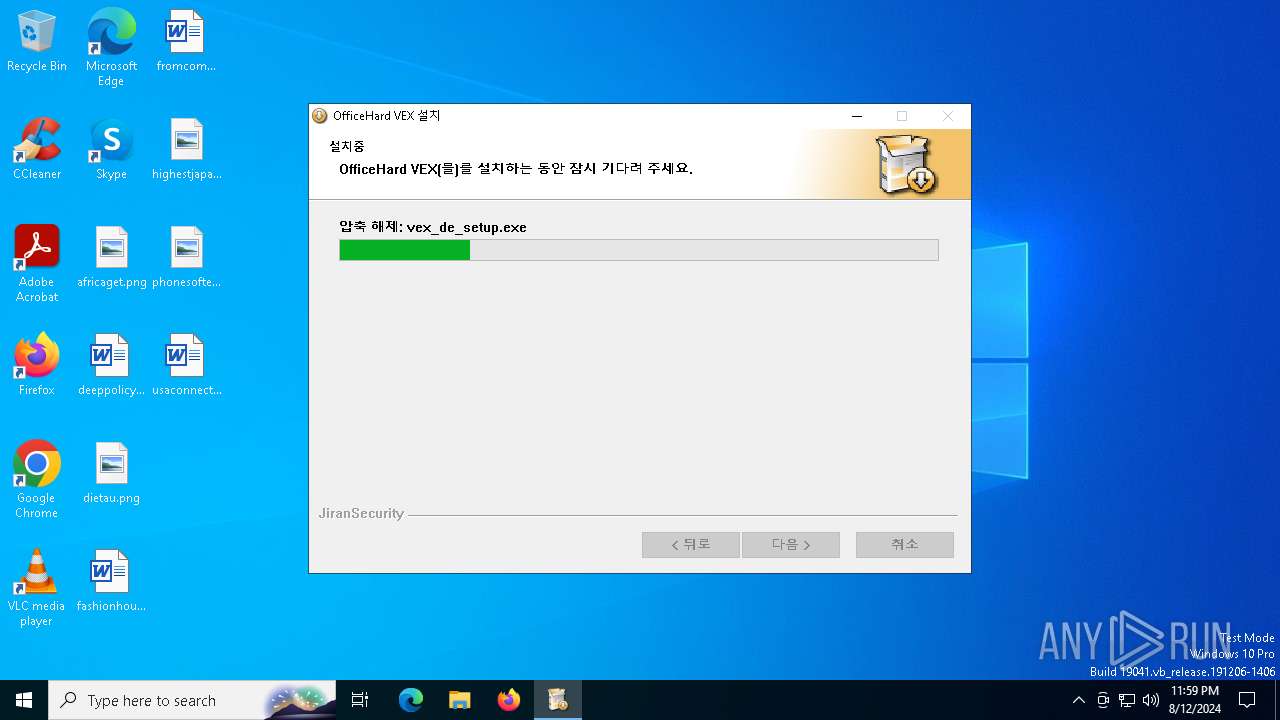
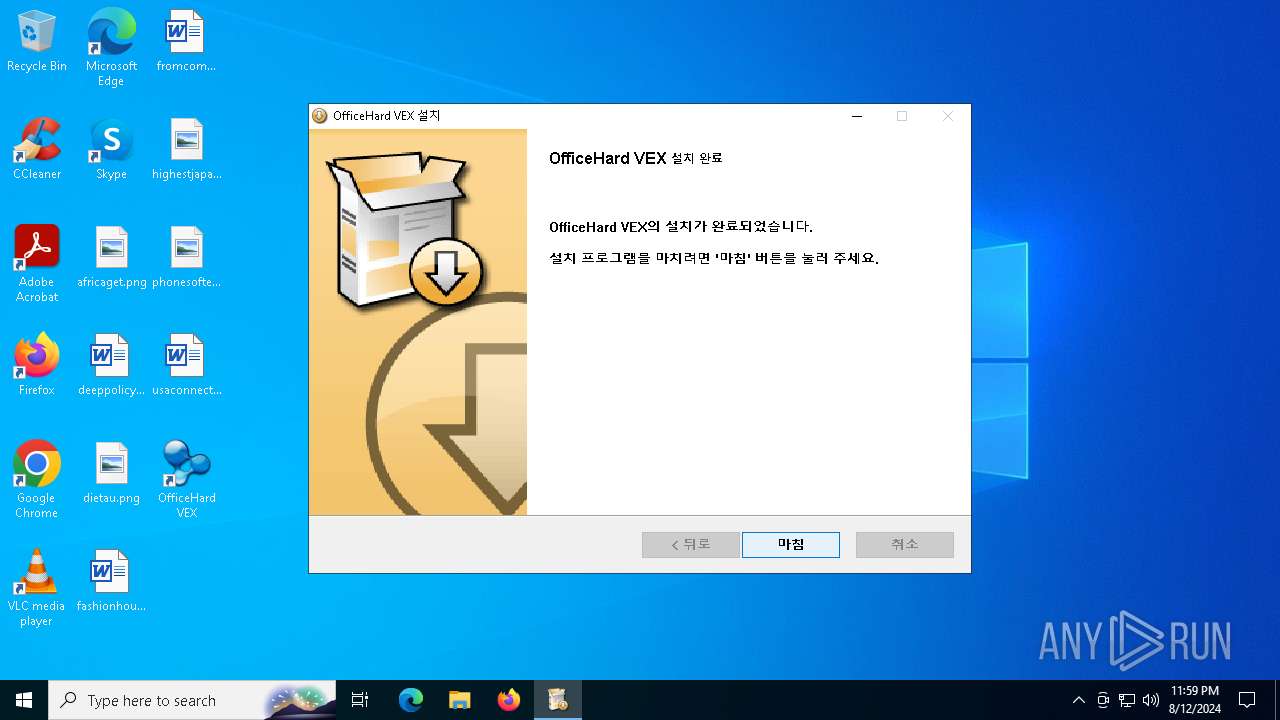
| File name: | vex_setup.exe |
| Full analysis: | https://app.any.run/tasks/fbc691b5-8f60-42e3-b4ae-487d038c9a32 |
| Verdict: | Malicious activity |
| Analysis date: | August 12, 2024, 23:58:47 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows |
| MD5: | 45178DFA0373B6E1DB3808782F806CFB |
| SHA1: | 2BEBE1830F534BB3070C8B5FDDAE716EECC7B344 |
| SHA256: | 8C2CA66937A5764AC13767888CE4E2F1963181B14F2CC1903FBD79972259D4BA |
| SSDEEP: | 98304:P6VnvKEDb22XJHyIz+DLYQELbsfHLx1gLm05Nqz+PDZ6DIXM56nsDJFnukp2iOoG:2Vsjkp9SxbotKlXdYszvgi8 |
MALICIOUS
No malicious indicators.SUSPICIOUS
Drops 7-zip archiver for unpacking
- vex_setup.exe (PID: 6312)
Drops the executable file immediately after the start
- vex_setup.exe (PID: 6312)
- vex_setup.exe (PID: 6372)
Executable content was dropped or overwritten
- vex_setup.exe (PID: 6312)
- vex_setup.exe (PID: 6372)
The process creates files with name similar to system file names
- vex_setup.exe (PID: 6372)
Malware-specific behavior (creating "System.dll" in Temp)
- vex_setup.exe (PID: 6372)
Reads security settings of Internet Explorer
- vex_setup.exe (PID: 6372)
- OfficeHardVEX.exe (PID: 5064)
Process drops legitimate windows executable
- vex_setup.exe (PID: 6372)
The process drops C-runtime libraries
- vex_setup.exe (PID: 6372)
Creates a software uninstall entry
- vex_setup.exe (PID: 6372)
Changes Internet Explorer settings (feature browser emulation)
- OfficeHardVEX.exe (PID: 5064)
INFO
Checks supported languages
- vex_setup.exe (PID: 6312)
- vex_setup.exe (PID: 6372)
- OfficeHardVEX.exe (PID: 1168)
- OfficeHardVEX.exe (PID: 5064)
Create files in a temporary directory
- vex_setup.exe (PID: 6312)
- vex_setup.exe (PID: 6372)
Reads the computer name
- vex_setup.exe (PID: 6312)
- vex_setup.exe (PID: 6372)
- OfficeHardVEX.exe (PID: 5064)
Creates files in the program directory
- vex_setup.exe (PID: 6372)
Manual execution by a user
- OfficeHardVEX.exe (PID: 1168)
- OfficeHardVEX.exe (PID: 5064)
Creates files or folders in the user directory
- OfficeHardVEX.exe (PID: 5064)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | InstallShield setup (36.8) |
|---|---|---|
| .exe | | | Win32 Executable MS Visual C++ (generic) (26.6) |
| .exe | | | Win64 Executable (generic) (23.6) |
| .dll | | | Win32 Dynamic Link Library (generic) (5.6) |
| .exe | | | Win32 Executable (generic) (3.8) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2011:04:18 18:54:06+00:00 |
| ImageFileCharacteristics: | No relocs, Executable, No line numbers, No symbols, Large address aware, 32-bit |
| PEType: | PE32 |
| LinkerVersion: | 6 |
| CodeSize: | 104448 |
| InitializedDataSize: | 45056 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x148d4 |
| OSVersion: | 4 |
| ImageVersion: | - |
| SubsystemVersion: | 4 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 9.22.0.0 |
| ProductVersionNumber: | 9.22.0.0 |
| FileFlagsMask: | 0x003f |
| FileFlags: | (none) |
| FileOS: | Windows NT 32-bit |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | English (U.S.) |
| CharacterSet: | Unicode |
| CompanyName: | Igor Pavlov |
| FileDescription: | 7z Setup SFX |
| FileVersion: | 9.22 beta |
| InternalName: | 7zS.sfx |
| LegalCopyright: | Copyright (c) 1999-2011 Igor Pavlov |
| OriginalFileName: | 7zS.sfx.exe |
| ProductName: | 7-Zip |
| ProductVersion: | 9.22 beta |
Total processes
141
Monitored processes
5
Malicious processes
2
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1168 | "C:\Program Files (x86)\Jiransoft\OfficeHard VEX\OfficeHardVEX.exe" | C:\Program Files (x86)\Jiransoft\OfficeHard VEX\OfficeHardVEX.exe | — | explorer.exe | |||||||||||
User: admin Company: JiranSecurity Co.,Ltd. Integrity Level: MEDIUM Description: Main application Exit code: 0 Version: 3, 0, 4, 167 Modules
| |||||||||||||||
| 5064 | "C:\Program Files (x86)\Jiransoft\OfficeHard VEX\OfficeHardVEX.exe" | C:\Program Files (x86)\Jiransoft\OfficeHard VEX\OfficeHardVEX.exe | — | explorer.exe | |||||||||||
User: admin Company: JiranSecurity Co.,Ltd. Integrity Level: MEDIUM Description: Main application Version: 3, 0, 4, 167 Modules
| |||||||||||||||
| 6264 | "C:\Users\admin\AppData\Local\Temp\vex_setup.exe" | C:\Users\admin\AppData\Local\Temp\vex_setup.exe | — | explorer.exe | |||||||||||
User: admin Company: Igor Pavlov Integrity Level: MEDIUM Description: 7z Setup SFX Exit code: 3221226540 Version: 9.22 beta Modules
| |||||||||||||||
| 6312 | "C:\Users\admin\AppData\Local\Temp\vex_setup.exe" | C:\Users\admin\AppData\Local\Temp\vex_setup.exe | explorer.exe | ||||||||||||
User: admin Company: Igor Pavlov Integrity Level: HIGH Description: 7z Setup SFX Exit code: 0 Version: 9.22 beta Modules
| |||||||||||||||
| 6372 | .\vex_setup.exe | C:\Users\admin\AppData\Local\Temp\7zS8A80C03E\vex_setup.exe | vex_setup.exe | ||||||||||||
User: admin Company: JiranSecurity Co.,Ltd. Integrity Level: HIGH Description: OfficeHard VEX Setup program Exit code: 0 Version: 3.0.4.167 Modules
| |||||||||||||||
Total events
4 773
Read events
4 747
Write events
26
Delete events
0
Modification events
| (PID) Process: | (6372) vex_setup.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Classes\WOW6432Node\Interface\{618736E0-3C3D-11CF-810C-00AA00389B71}\TypeLib |
| Operation: | write | Name: | Version |
Value: 1.1 | |||
| (PID) Process: | (6372) vex_setup.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Classes\Interface\{618736E0-3C3D-11CF-810C-00AA00389B71}\TypeLib |
| Operation: | write | Name: | Version |
Value: 1.1 | |||
| (PID) Process: | (6372) vex_setup.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Volatile\00\MACHINE\SOFTWARE\Classes\WOW6432Node\Interface\{03022430-ABC4-11D0-BDE2-00AA001A1953}\TypeLib |
| Operation: | write | Name: | Version |
Value: 1.1 | |||
| (PID) Process: | (6372) vex_setup.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Volatile\00\MACHINE\SOFTWARE\Classes\Interface\{03022430-ABC4-11D0-BDE2-00AA001A1953}\TypeLib |
| Operation: | write | Name: | Version |
Value: 1.1 | |||
| (PID) Process: | (6372) vex_setup.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Jiransoft\OfficeHDVEX |
| Operation: | write | Name: | LinkName |
Value: OfficeHard VEX | |||
| (PID) Process: | (6372) vex_setup.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Jiransoft\OfficeHDVEX |
| Operation: | write | Name: | CustomCode |
Value: | |||
| (PID) Process: | (6372) vex_setup.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Jiransoft\OfficeHDVEX |
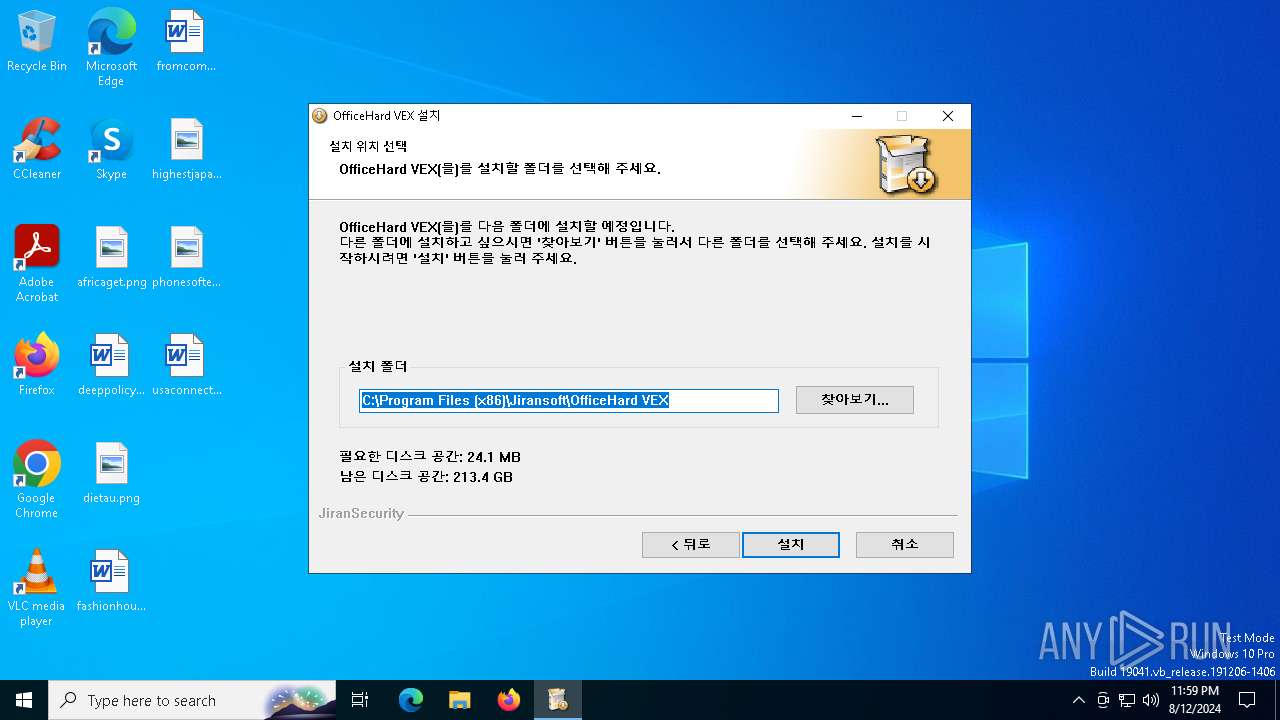
| Operation: | write | Name: | InstallDir |
Value: C:\Program Files (x86)\Jiransoft\OfficeHard VEX | |||
| (PID) Process: | (6372) vex_setup.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Jiransoft\OfficeHDVEX |
| Operation: | write | Name: | InstallDir |
Value: C:\Program Files (x86)\Jiransoft\OfficeHard VEX | |||
| (PID) Process: | (6372) vex_setup.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Jiransoft\OfficeHDVEX |
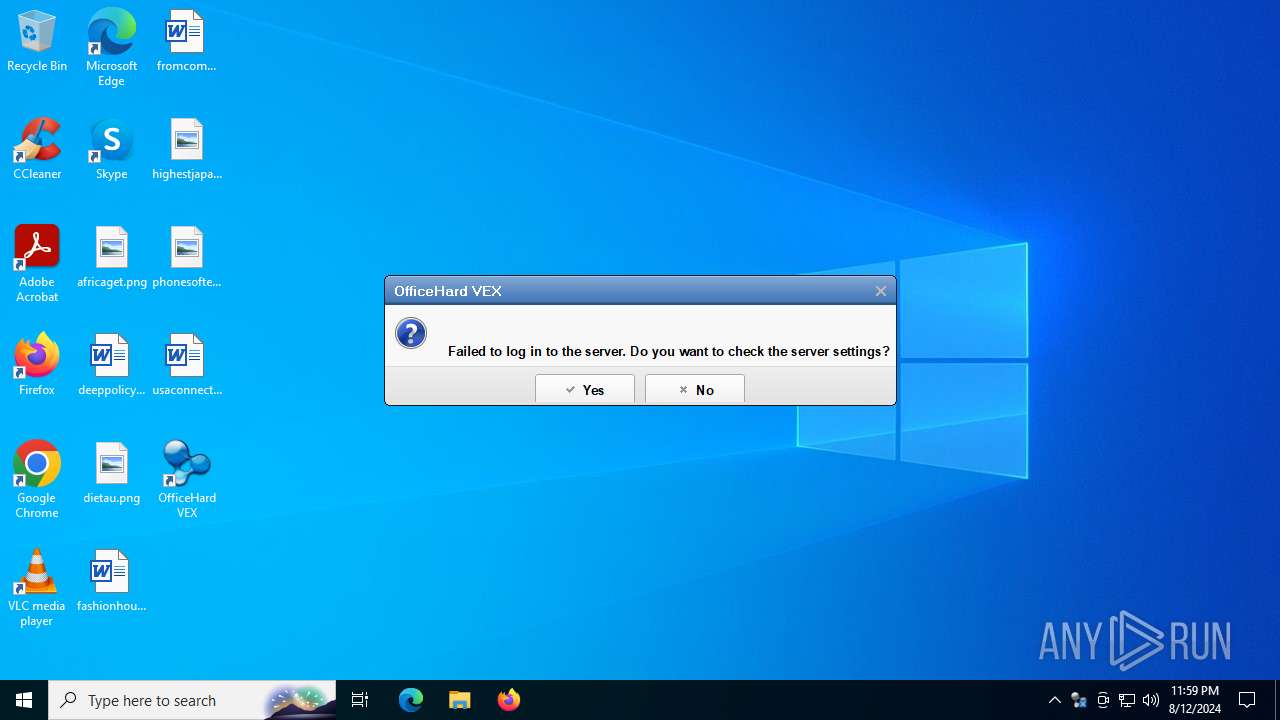
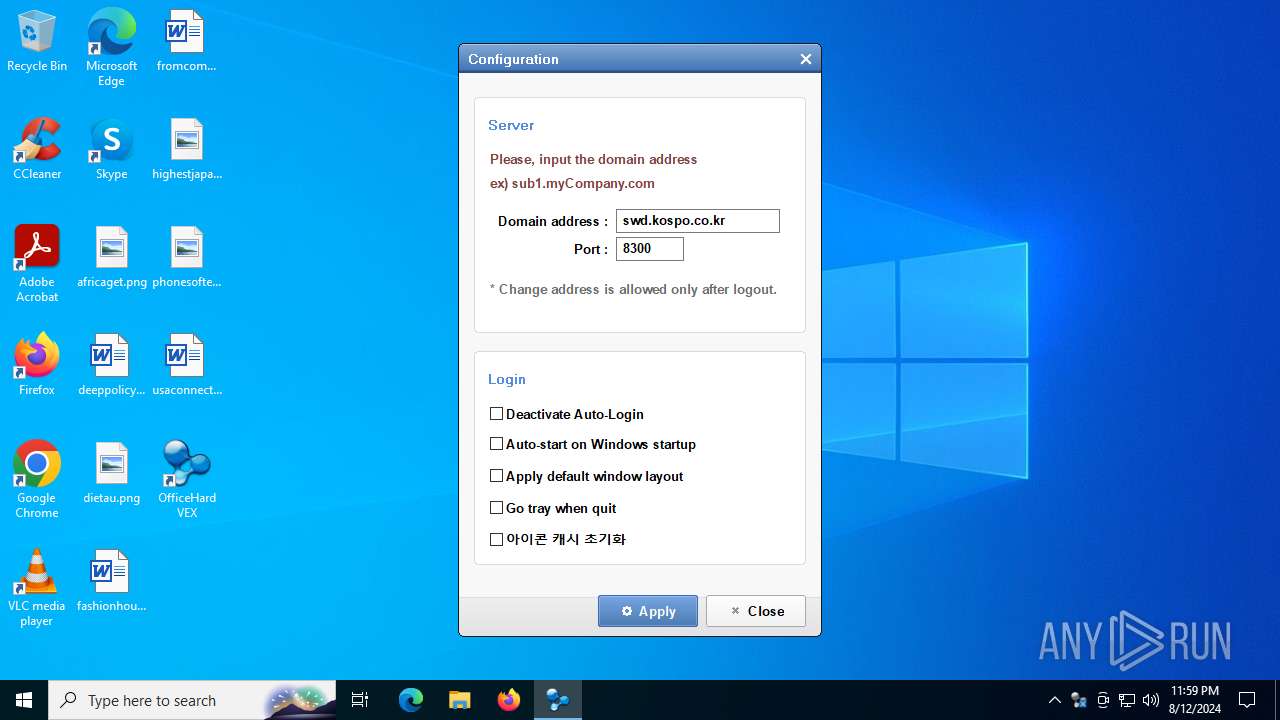
| Operation: | write | Name: | ServerIP |
Value: swd.kospo.co.kr | |||
| (PID) Process: | (6372) vex_setup.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Jiransoft\OfficeHDVEX |
| Operation: | write | Name: | ServerPort |
Value: 8300 | |||
Executable files
32
Suspicious files
5
Text files
12
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 6312 | vex_setup.exe | C:\Users\admin\AppData\Local\Temp\7zS8A80C03E\vex_setup.ini | text | |
MD5:C51138846E1B9D4072C0611CB134CF66 | SHA256:9776FB821BE7569414B9CCBB76E8E58D2DF76BEBE136CC0B80FA195495582CDA | |||
| 6372 | vex_setup.exe | C:\Program Files (x86)\Jiransoft\OfficeHard VEX\mfc80.dll | executable | |
MD5:1F5AFD468EB5E09E9ED75A087529EAB5 | SHA256:8204DBCC054C1E54B6065BACB78C55716681AD91759E25111B4E4797E51D0AA3 | |||
| 6372 | vex_setup.exe | C:\Users\admin\AppData\Local\Temp\nsa562B.tmp\System.dll | executable | |
MD5:192639861E3DC2DC5C08BB8F8C7260D5 | SHA256:23D618A0293C78CE00F7C6E6DD8B8923621DA7DD1F63A070163EF4C0EC3033D6 | |||
| 6312 | vex_setup.exe | C:\Users\admin\AppData\Local\Temp\7zS8A80C03E\vex_setup.exe | executable | |
MD5:E5E68701B6BF1029AAB53A6DE5BA6AEA | SHA256:FEA617F09E21CD97FE67B4BF0297253F49321F3FE59FDA2A3BF14D051DE9F89B | |||
| 6372 | vex_setup.exe | C:\Users\admin\AppData\Local\Temp\nsa562B.tmp\LangDLL.dll | executable | |
MD5:549EE11198143574F4D9953198A09FE8 | SHA256:131AA0DF90C08DCE2EECEE46CCE8759E9AFFF04BF15B7B0002C2A53AE5E92C36 | |||
| 6372 | vex_setup.exe | C:\Program Files (x86)\Jiransoft\OfficeHard VEX\vex_customize.ini | text | |
MD5:17F5C03B06FAE281BB03C5750E42B067 | SHA256:EE92206500ABF4C0D7C755256DB3D74E11B77127E7D4BE5C08A2A57F1E0C8245 | |||
| 6372 | vex_setup.exe | C:\Program Files (x86)\Jiransoft\OfficeHard VEX\gdiplus.dll | executable | |
MD5:188B5704E726026A4CC394386E5F5D45 | SHA256:05471ED008B10BD4B3978D5CBED4FC21C3C4CB6AC6B10FBF4B83EBEB56608A5C | |||
| 6372 | vex_setup.exe | C:\Users\admin\AppData\Local\Temp\nsa562B.tmp\modern-wizard.bmp | image | |
MD5:9E4CD80A60DB6947642677BF31A10906 | SHA256:A7B2F12E01CBEA88D4F645F797F2CA6107D76AE13CD1BE6DC532B759BFE0D925 | |||
| 6372 | vex_setup.exe | C:\Program Files (x86)\Jiransoft\OfficeHard VEX\mfcm80.dll | executable | |
MD5:83362EE950AD18ADB85B54409155C378 | SHA256:BE1FAA17B466E56DA8259CDC1F1B02EE0DEB4C5E022E6EB3B82643EF508C8BEA | |||
| 6372 | vex_setup.exe | C:\Program Files (x86)\Jiransoft\OfficeHard VEX\login.png | image | |
MD5:F97A6B622F6E26F8D832D6A92BCD4B94 | SHA256:A8F3B039A45D0D4697286ABFBDB35097734800DB0E7E3DDF1B174EE66D57D7C5 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
4
TCP/UDP connections
38
DNS requests
18
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
5336 | SearchApp.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
2248 | svchost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
6660 | backgroundTaskHost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | whitelisted |
6708 | backgroundTaskHost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
4056 | RUXIMICS.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | unknown |
2120 | MoUsoCoreWorker.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | unknown |
4080 | svchost.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | unknown |
3888 | svchost.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
5336 | SearchApp.exe | 184.86.251.19:443 | www.bing.com | Akamai International B.V. | DE | unknown |
5336 | SearchApp.exe | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
2248 | svchost.exe | 40.126.32.136:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | unknown |
2248 | svchost.exe | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
3260 | svchost.exe | 40.115.3.253:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
google.com |
| whitelisted |
settings-win.data.microsoft.com |
| whitelisted |
www.bing.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
login.live.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
th.bing.com |
| whitelisted |
fd.api.iris.microsoft.com |
| whitelisted |
arc.msn.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
Threats
Process | Message |
|---|---|
vex_setup.exe | ExecShellAsUser: got desktop |
vex_setup.exe | ExecShellAsUser: elevated process detected |
vex_setup.exe | ExecShellAsUser: thread finished |
vex_setup.exe | ExecShellAsUser: DLL_PROCESS_DETACH |