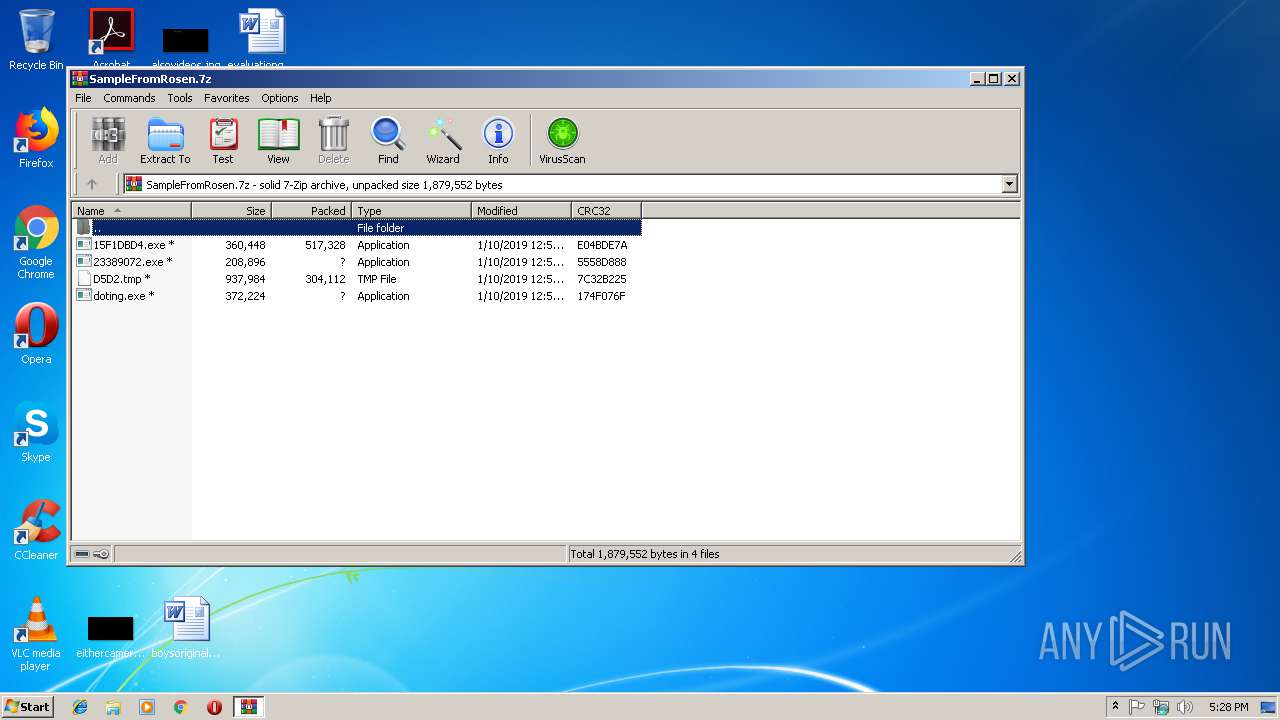
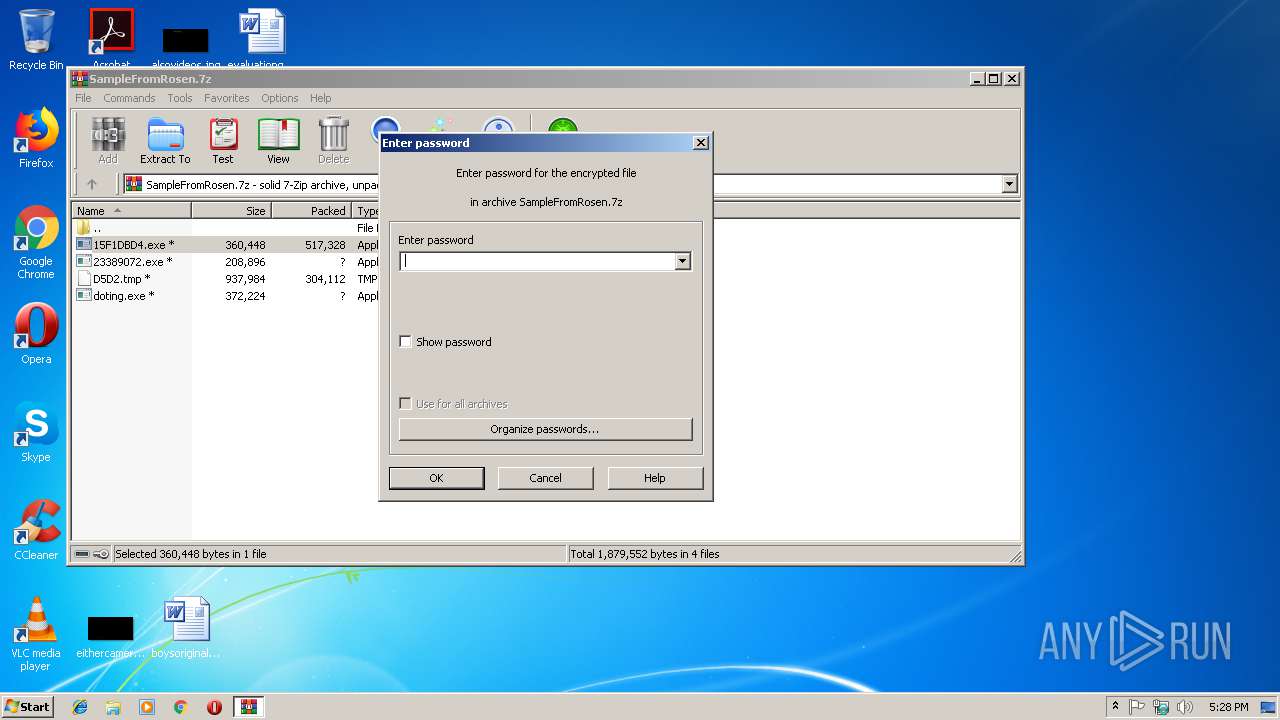
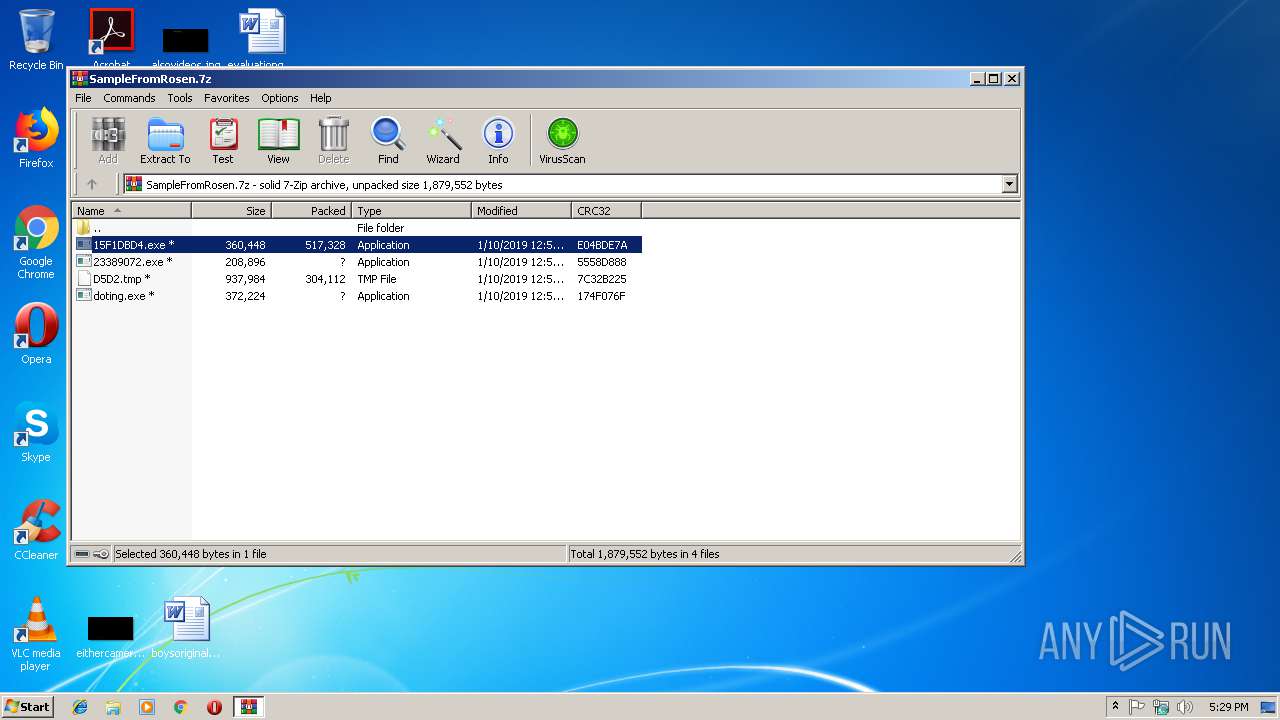
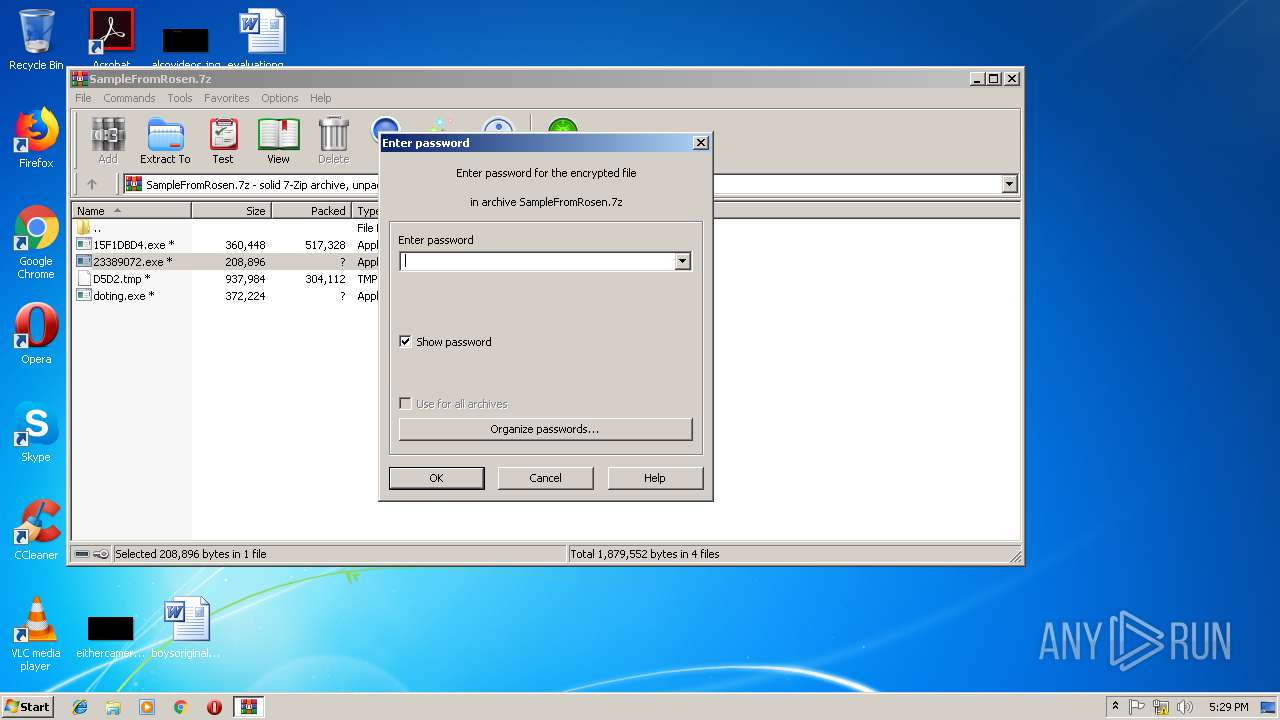
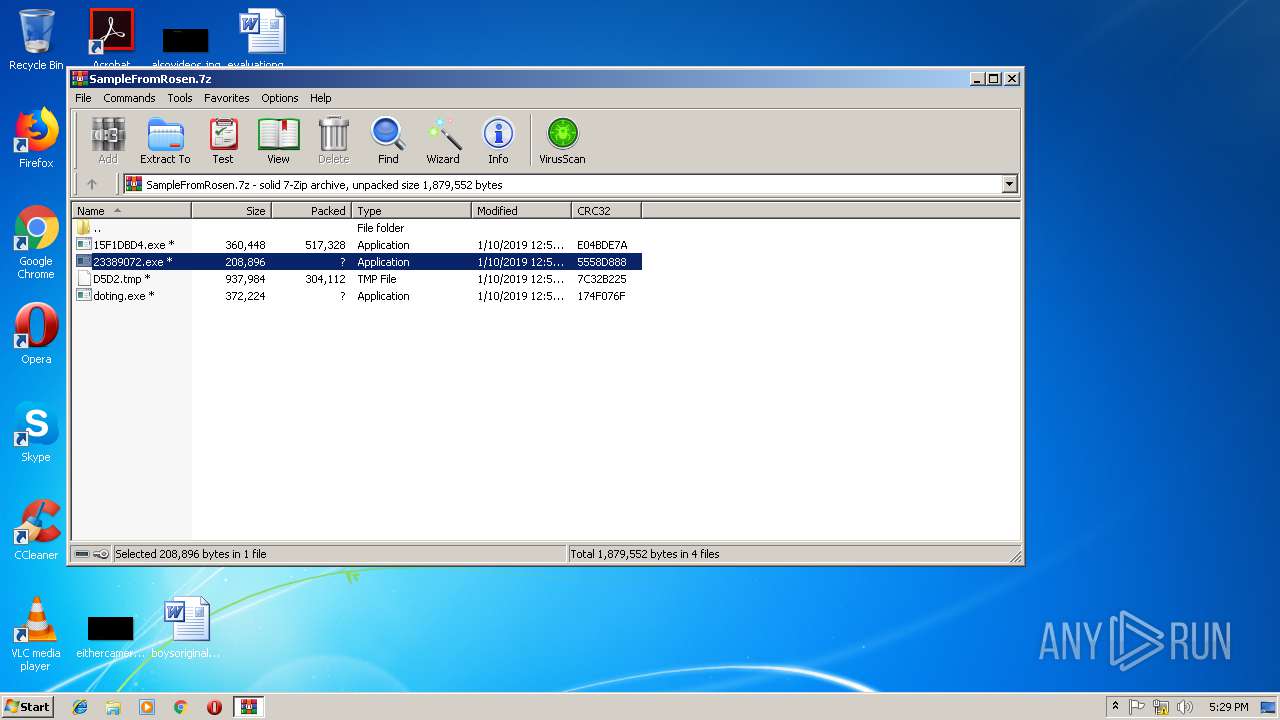
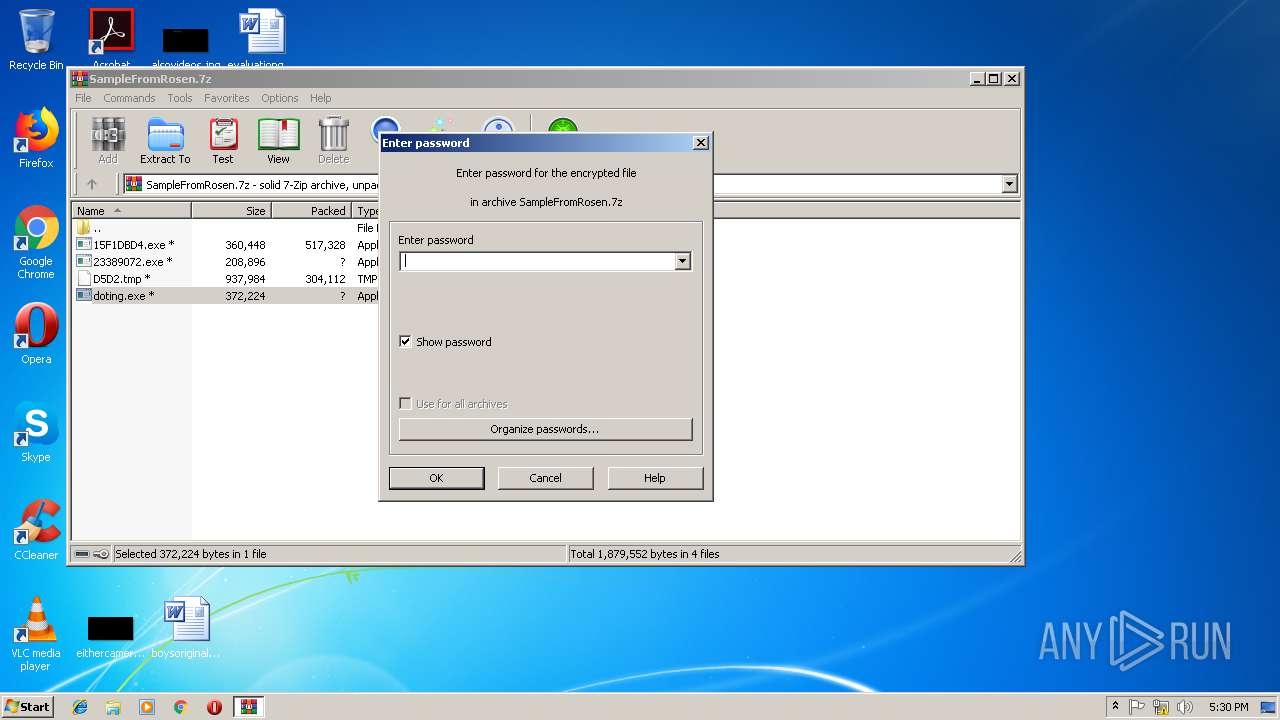
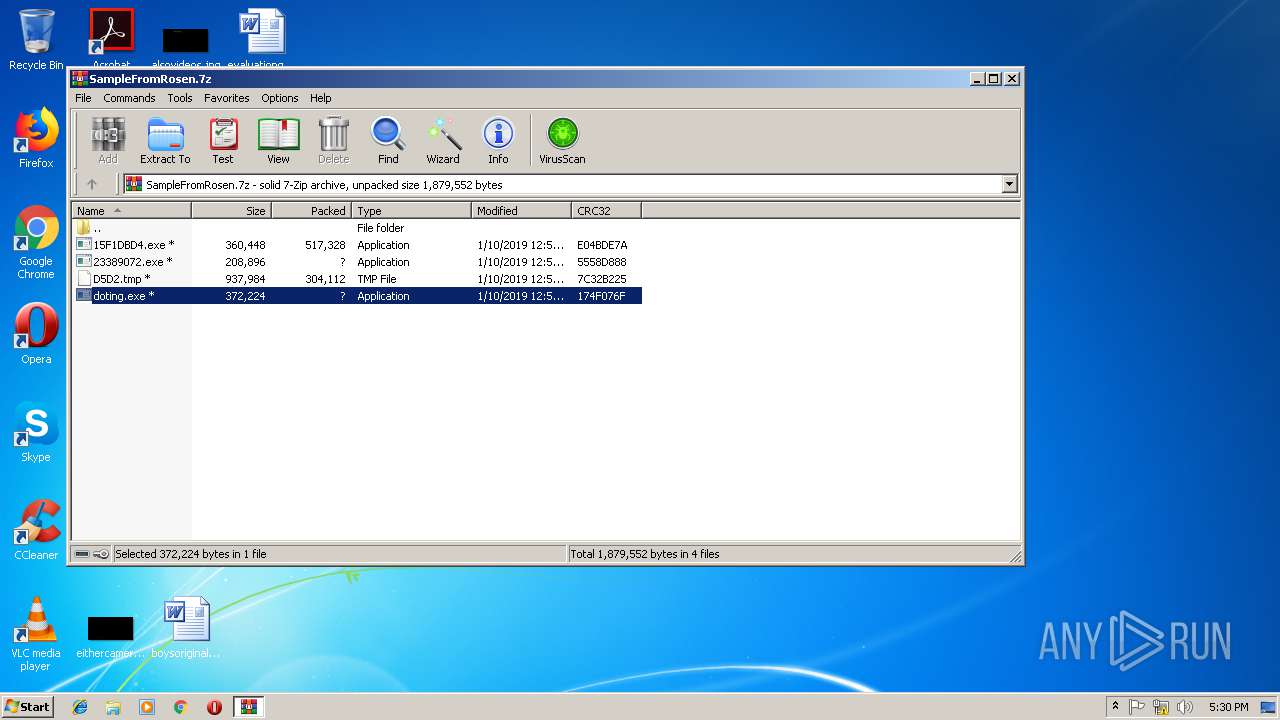
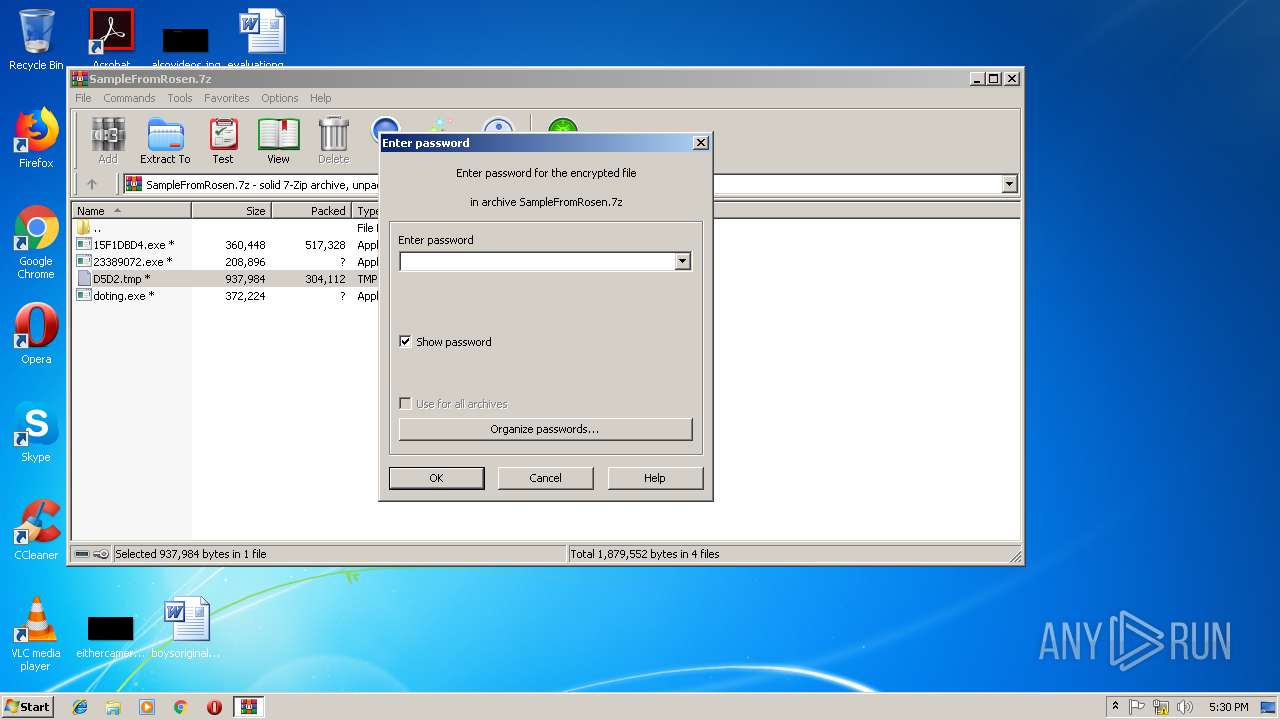
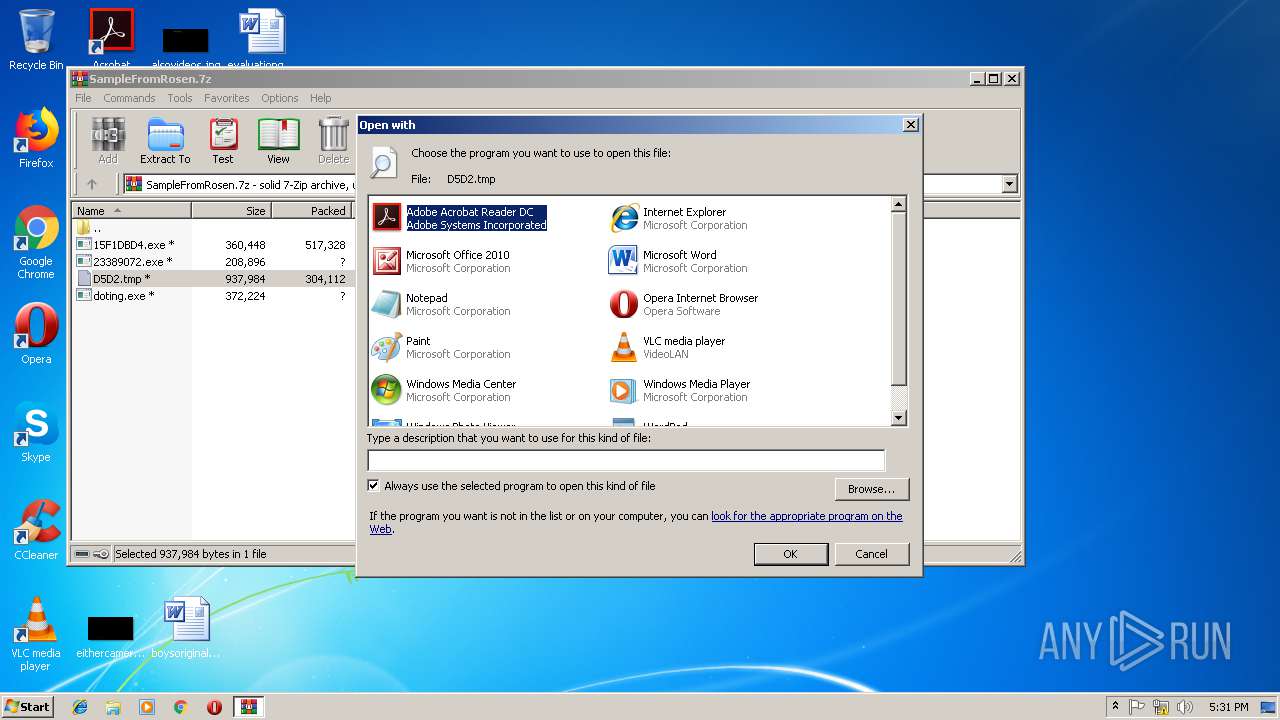
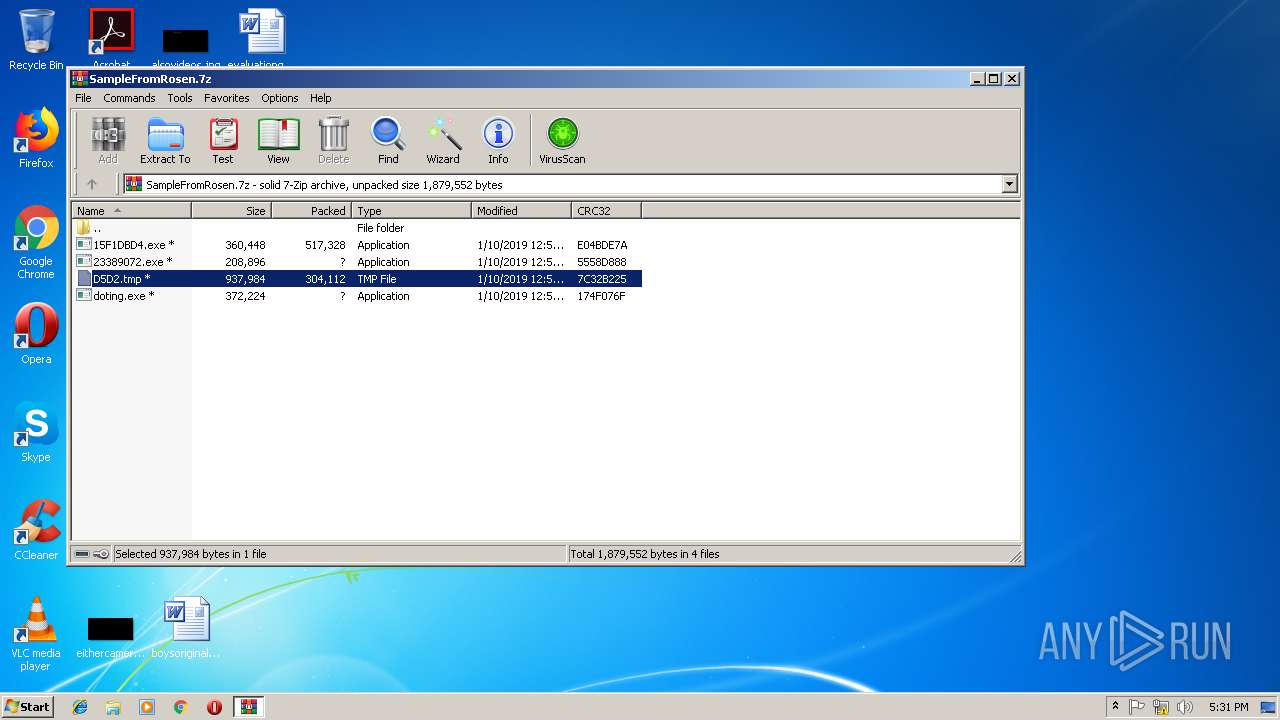
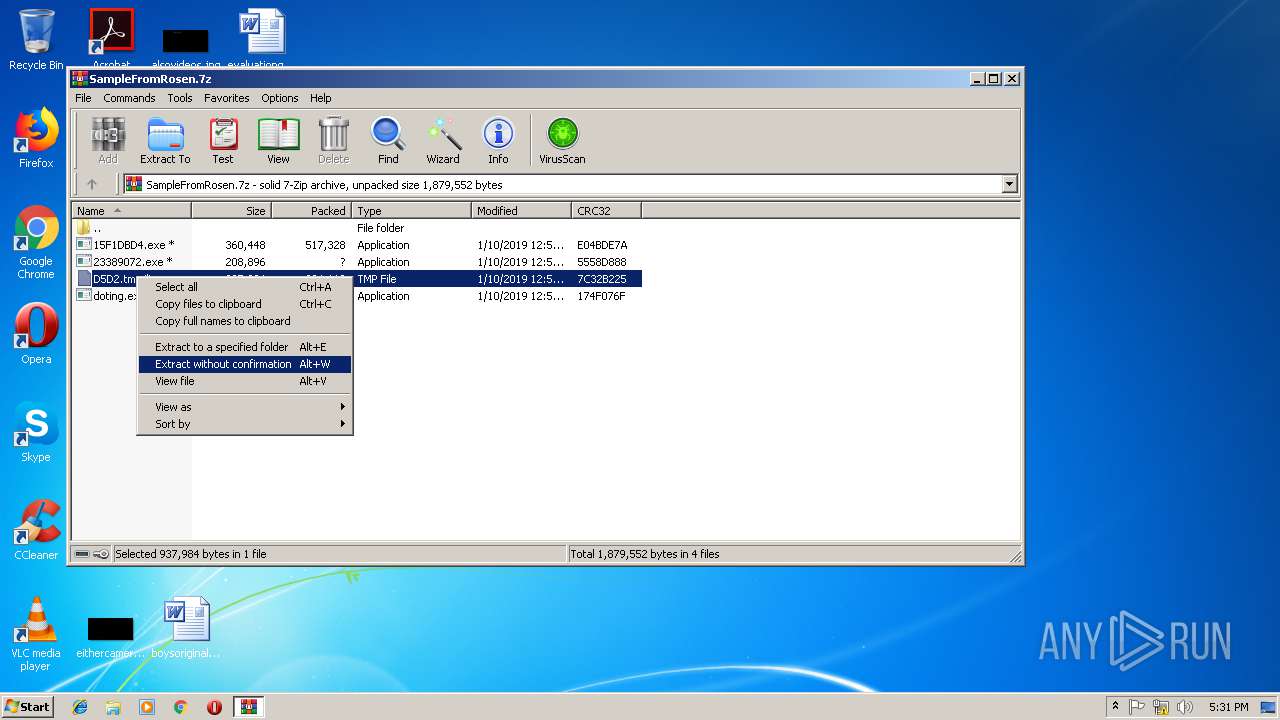
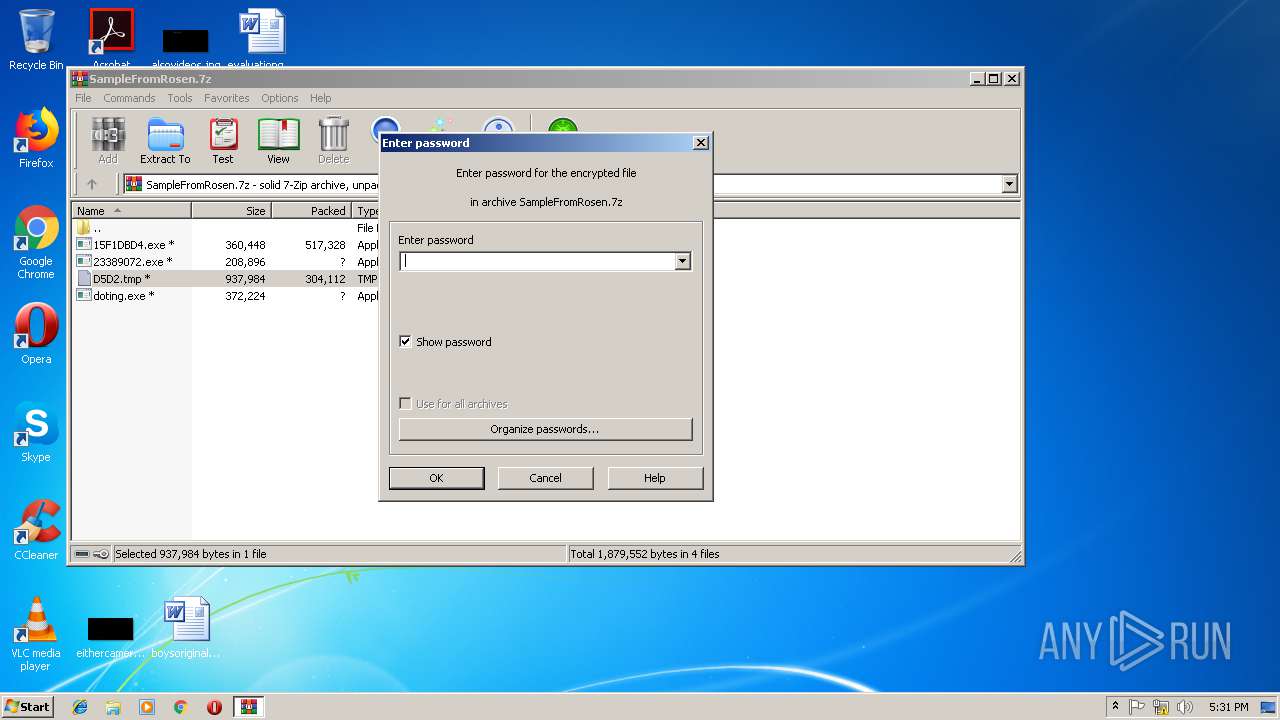
| File name: | SampleFromRosen.7z |
| Full analysis: | https://app.any.run/tasks/d82d1e18-b8cf-4bea-90c5-61253b43c7f6 |
| Verdict: | Malicious activity |
| Threats: | Emotet is one of the most dangerous trojans ever created. Over the course of its lifetime, it was upgraded to become a very destructive malware. It targets mostly corporate victims but even private users get infected in mass spam email campaigns. |
| Analysis date: | January 10, 2019, 17:28:09 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-7z-compressed |
| File info: | 7-zip archive data, version 0.4 |
| MD5: | 3E258E0BAABC15A0BDCA6CAA21D39881 |
| SHA1: | 2EAE303572A8611D5C40034035A95720E8ADF5F5 |
| SHA256: | 8C028C5279B41AE5AF45FDAA40FF99D5C7152072228C795D9034A8D28E164EDB |
| SSDEEP: | 12288:noAYPcFmqJhff3IxsGU6u6ySVixjQLBcyY850dZNw3h+jyYgNX3BMzF0QNOzF0:nB1p3xRUQjQNl2kh+OFBgvNj |
MALICIOUS
Emotet process was detected
- searchatsd.exe (PID: 884)
- searchatsd.exe (PID: 3648)
Application was dropped or rewritten from another process
- 23389072.exe (PID: 2984)
- 15F1DBD4.exe (PID: 2572)
- 15F1DBD4.exe (PID: 2996)
- searchatsd.exe (PID: 884)
- searchatsd.exe (PID: 3648)
- searchatsd.exe (PID: 2664)
- 23389072.exe (PID: 2628)
- searchatsd.exe (PID: 1504)
- doting.exe (PID: 3148)
- doting.exe (PID: 2560)
Connects to CnC server
- searchatsd.exe (PID: 2664)
- searchatsd.exe (PID: 1504)
EMOTET was detected
- searchatsd.exe (PID: 2664)
- searchatsd.exe (PID: 1504)
Detected GootKit
- doting.exe (PID: 3148)
Changes settings of System certificates
- doting.exe (PID: 2560)
GOOTKIT was detected
- doting.exe (PID: 2560)
Changes internet zones settings
- doting.exe (PID: 3148)
SUSPICIOUS
Application launched itself
- searchatsd.exe (PID: 884)
- searchatsd.exe (PID: 3648)
- doting.exe (PID: 3148)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 2724)
- 15F1DBD4.exe (PID: 2996)
- 23389072.exe (PID: 2984)
Starts itself from another location
- 15F1DBD4.exe (PID: 2996)
- 23389072.exe (PID: 2984)
Starts CMD.EXE for commands execution
- doting.exe (PID: 2560)
Uses WMIC.EXE to obtain a list of AntiViruses
- cmd.exe (PID: 2908)
Connects to unusual port
- searchatsd.exe (PID: 1504)
Creates files in the user directory
- doting.exe (PID: 2560)
Uses RUNDLL32.EXE to load library
- WinRAR.exe (PID: 2724)
Reads CPU info
- doting.exe (PID: 2560)
INFO
Modifies the open verb of a shell class
- rundll32.exe (PID: 3620)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .7z | | | 7-Zip compressed archive (v0.4) (57.1) |
|---|---|---|
| .7z | | | 7-Zip compressed archive (gen) (42.8) |
Total processes
45
Monitored processes
16
Malicious processes
11
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 884 | "C:\Users\admin\AppData\Local\Microsoft\Windows\searchatsd.exe" | C:\Users\admin\AppData\Local\Microsoft\Windows\searchatsd.exe | 15F1DBD4.exe | ||||||||||||
User: admin Company: Fatal Enterprice Integrity Level: MEDIUM Description: QllZad Exit code: 0 Version: 91.333.22.1 Modules
| |||||||||||||||
| 1328 | "C:\Windows\system32\NOTEPAD.EXE" C:\Users\admin\AppData\Local\Temp\Rar$DIb2724.45150\D5D2.tmp | C:\Windows\system32\NOTEPAD.EXE | — | rundll32.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Notepad Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1504 | "C:\Users\admin\AppData\Local\Microsoft\Windows\searchatsd.exe" | C:\Users\admin\AppData\Local\Microsoft\Windows\searchatsd.exe | searchatsd.exe | ||||||||||||
User: admin Company: Microsoft Corporatio Integrity Level: MEDIUM Description: Ru Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255 Modules
| |||||||||||||||
| 2560 | C:\Users\admin\AppData\Local\Temp\Rar$EXb2724.40955\doting.exe --vwxyz | C:\Users\admin\AppData\Local\Temp\Rar$EXb2724.40955\doting.exe | doting.exe | ||||||||||||
User: admin Company: Rally Software Development Against Integrity Level: MEDIUM Description: Veryran Exit code: 0 Version: 10.0.27.87 Modules
| |||||||||||||||
| 2572 | "C:\Users\admin\AppData\Local\Temp\Rar$EXb2724.33352\15F1DBD4.exe" | C:\Users\admin\AppData\Local\Temp\Rar$EXb2724.33352\15F1DBD4.exe | — | WinRAR.exe | |||||||||||
User: admin Company: Fatal Enterprice Integrity Level: MEDIUM Description: QllZad Exit code: 0 Version: 91.333.22.1 Modules
| |||||||||||||||
| 2628 | "C:\Users\admin\AppData\Local\Temp\Rar$EXb2724.37197\23389072.exe" | C:\Users\admin\AppData\Local\Temp\Rar$EXb2724.37197\23389072.exe | — | WinRAR.exe | |||||||||||
User: admin Company: Microsoft Corporatio Integrity Level: MEDIUM Description: Ru Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255 Modules
| |||||||||||||||
| 2664 | "C:\Users\admin\AppData\Local\Microsoft\Windows\searchatsd.exe" | C:\Users\admin\AppData\Local\Microsoft\Windows\searchatsd.exe | searchatsd.exe | ||||||||||||
User: admin Company: Fatal Enterprice Integrity Level: MEDIUM Description: QllZad Exit code: 0 Version: 91.333.22.1 Modules
| |||||||||||||||
| 2724 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\AppData\Local\Temp\SampleFromRosen.7z" | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.60.0 Modules
| |||||||||||||||
| 2908 | C:\Windows\system32\cmd.exe /c WMIC /Node:localhost /Namespace:\\root\SecurityCenter2 Path AntiVirusProduct Get displayName,productState /format:list | C:\Windows\system32\cmd.exe | — | doting.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 2984 | "C:\Users\admin\AppData\Local\Temp\Rar$EXb2724.37197\23389072.exe" | C:\Users\admin\AppData\Local\Temp\Rar$EXb2724.37197\23389072.exe | 23389072.exe | ||||||||||||
User: admin Company: Microsoft Corporatio Integrity Level: MEDIUM Description: Ru Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255 Modules
| |||||||||||||||
Total events
2 125
Read events
1 055
Write events
1 070
Delete events
0
Modification events
| (PID) Process: | (2724) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (2724) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (2724) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\5F\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (2724) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\SampleFromRosen.7z | |||
| (PID) Process: | (2724) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (2724) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (2724) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (2724) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (2724) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface |
| Operation: | write | Name: | ShowPassword |
Value: 1 | |||
| (PID) Process: | (2724) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 0 | |||
Executable files
16
Suspicious files
5
Text files
3
Unknown types
1
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2560 | doting.exe | C:\Users\admin\AppData\Local\Temp\Cab9027.tmp | — | |
MD5:— | SHA256:— | |||
| 2560 | doting.exe | C:\Users\admin\AppData\Local\Temp\Tar9028.tmp | — | |
MD5:— | SHA256:— | |||
| 2560 | doting.exe | C:\Users\admin\AppData\Local\Temp\Cab9048.tmp | — | |
MD5:— | SHA256:— | |||
| 2560 | doting.exe | C:\Users\admin\AppData\Local\Temp\Tar9049.tmp | — | |
MD5:— | SHA256:— | |||
| 2560 | doting.exe | C:\Users\admin\AppData\Local\Temp\Cab90C7.tmp | — | |
MD5:— | SHA256:— | |||
| 2560 | doting.exe | C:\Users\admin\AppData\Local\Temp\Tar90C8.tmp | — | |
MD5:— | SHA256:— | |||
| 2984 | 23389072.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\searchatsd.exe | executable | |
MD5:— | SHA256:— | |||
| 2724 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXb2724.37197\doting.exe | executable | |
MD5:— | SHA256:— | |||
| 2560 | doting.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\94308059B57B3142E455B38A6EB92015 | compressed | |
MD5:— | SHA256:— | |||
| 2996 | 15F1DBD4.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\searchatsd.exe | executable | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
10
TCP/UDP connections
15
DNS requests
2
Threats
31
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
2664 | searchatsd.exe | GET | — | 72.224.73.157:8080 | http://72.224.73.157:8080/ | US | — | — | malicious |
1504 | searchatsd.exe | GET | — | 216.21.168.27:80 | http://216.21.168.27/ | US | — | — | whitelisted |
1504 | searchatsd.exe | GET | — | 74.131.89.83:80 | http://74.131.89.83/ | US | — | — | malicious |
1504 | searchatsd.exe | GET | — | 173.61.22.150:443 | http://173.61.22.150:443/ | US | — | — | whitelisted |
1504 | searchatsd.exe | GET | — | 69.70.217.174:80 | http://69.70.217.174/ | CA | — | — | malicious |
2560 | doting.exe | GET | 200 | 93.184.221.240:80 | http://www.download.windowsupdate.com/msdownload/update/v3/static/trustedr/en/authrootstl.cab | US | compressed | 55.2 Kb | whitelisted |
1504 | searchatsd.exe | GET | — | 115.64.32.202:80 | http://115.64.32.202/ | AU | — | — | malicious |
1504 | searchatsd.exe | GET | — | 100.35.105.159:443 | http://100.35.105.159:443/ | US | — | — | whitelisted |
1504 | searchatsd.exe | GET | — | 109.69.52.112:8080 | http://109.69.52.112:8080/ | ES | — | — | malicious |
1504 | searchatsd.exe | GET | — | 117.232.118.18:443 | http://117.232.118.18:443/ | IN | — | — | malicious |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
1504 | searchatsd.exe | 74.131.89.83:80 | — | Time Warner Cable Internet LLC | US | malicious |
1504 | searchatsd.exe | 100.35.105.159:443 | — | MCI Communications Services, Inc. d/b/a Verizon Business | US | whitelisted |
1504 | searchatsd.exe | 173.61.22.150:443 | — | MCI Communications Services, Inc. d/b/a Verizon Business | US | whitelisted |
1504 | searchatsd.exe | 69.70.217.174:80 | — | Videotron Telecom Ltee | CA | malicious |
1504 | searchatsd.exe | 109.69.52.112:8080 | — | Soluciones Corporativas IP, SL | ES | malicious |
1504 | searchatsd.exe | 117.232.118.18:443 | — | National Internet Backbone | IN | malicious |
1504 | searchatsd.exe | 95.5.225.35:50000 | — | Turk Telekom | TR | malicious |
1504 | searchatsd.exe | 216.21.168.27:80 | — | Google Fiber Inc. | US | whitelisted |
2560 | doting.exe | 14.1.28.165:443 | fault.limpiezaapresion.com | US Dedicated | US | malicious |
1504 | searchatsd.exe | 115.64.32.202:80 | — | TPG Telecom Limited | AU | malicious |
DNS requests
Domain | IP | Reputation |
|---|---|---|
fault.limpiezaapresion.com |
| malicious |
www.download.windowsupdate.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2664 | searchatsd.exe | A Network Trojan was detected | SC SPYWARE Spyware Emotet Win32 |
2664 | searchatsd.exe | A Network Trojan was detected | MALWARE [PTsecurity] Feodo HTTP request |
2560 | doting.exe | A Network Trojan was detected | MALWARE [PTsecurity] JA3 GootKit Connection |
2560 | doting.exe | A Network Trojan was detected | MALWARE [PTsecurity] JA3 GootKit Connection |
1504 | searchatsd.exe | A Network Trojan was detected | SC SPYWARE Trojan-Banker.Win32.Emotet |
1504 | searchatsd.exe | A Network Trojan was detected | SC SPYWARE Spyware Emotet Win32 |
1504 | searchatsd.exe | A Network Trojan was detected | MALWARE [PTsecurity] Feodo HTTP request |
1504 | searchatsd.exe | A Network Trojan was detected | SC SPYWARE Spyware Emotet Win32 |
1504 | searchatsd.exe | A Network Trojan was detected | MALWARE [PTsecurity] Feodo HTTP request |
1504 | searchatsd.exe | A Network Trojan was detected | SC SPYWARE Trojan-Banker.Win32.Emotet |
10 ETPRO signatures available at the full report
Process | Message |
|---|---|
doting.exe | MP3 file corrupted |
doting.exe | WMA 0 |
doting.exe | WMA 3 |
doting.exe | 2560:C:\Users\admin\AppData\Local\Temp\Rar$EXb2724.40955\doting.exe --vwxyz Ignition....
|
doting.exe | JS : RUN : doting.exe, ver : 27.12.18.1308
|
doting.exe | JS : WDE3:: GetAV processing...
|
doting.exe | JS : WDE3:: GetAV records: NOAV
|
doting.exe | OGG 0 |