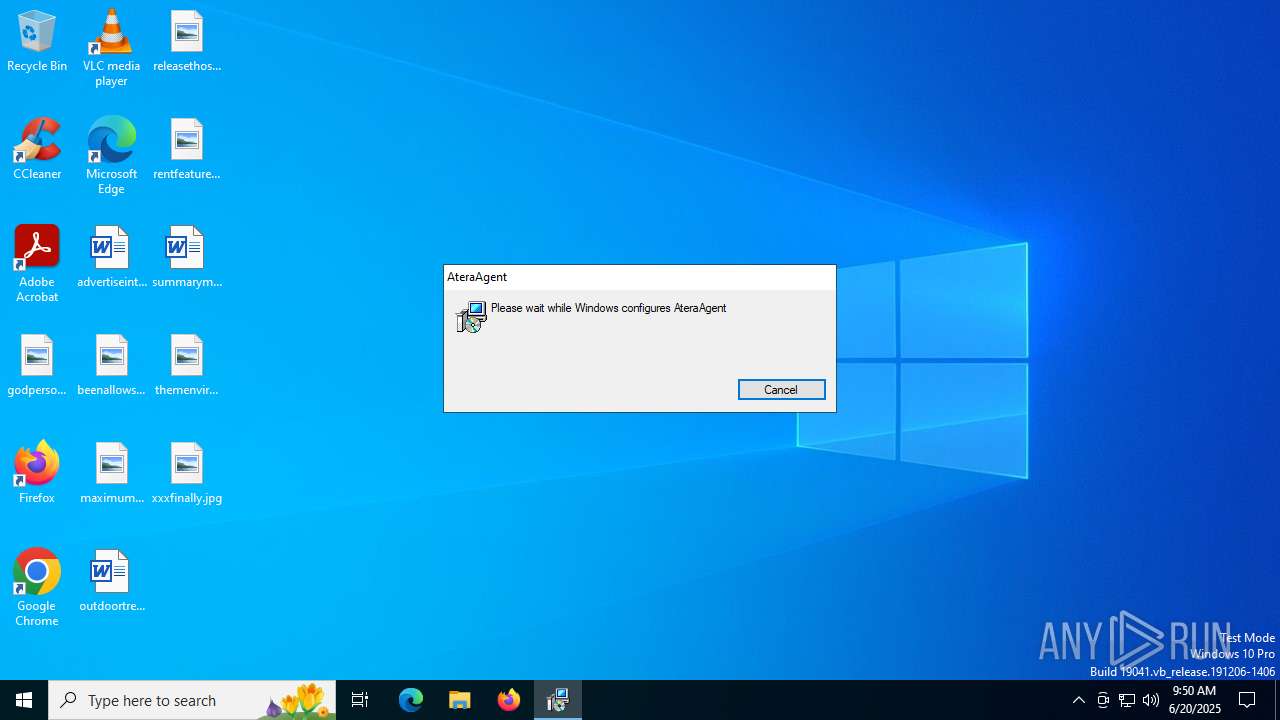
| File name: | Factura.msi |
| Full analysis: | https://app.any.run/tasks/9447c13b-0aa8-41c6-a6b1-5b7436ff7b55 |
| Verdict: | Malicious activity |
| Analysis date: | June 20, 2025, 09:50:29 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-msi |
| File info: | Composite Document File V2 Document, Little Endian, Os: Windows, Version 10.0, MSI Installer, Code page: 1252, Title: Installation Database, Subject: AteraAgent, Author: Atera networks, Keywords: Installer, Comments: This installer database contains the logic and data required to install AteraAgent., Template: Intel;1033, Revision Number: {721AD955-79FD-4019-BBF5-9DCC4C1175BB}, Create Time/Date: Wed Feb 28 10:52:02 2024, Last Saved Time/Date: Wed Feb 28 10:52:02 2024, Number of Pages: 200, Number of Words: 6, Name of Creating Application: Windows Installer XML Toolset (3.11.2.4516), Security: 2 |
| MD5: | CD5E8FB7FC885887F0DC0814E6B0DAB6 |
| SHA1: | FC7CE66344278620477077CF5D0702CB7A6ABF64 |
| SHA256: | 8BF8D0DCE138B5E3761D947746CAAF6C2E48122A844B8AB959A94E9D6A733148 |
| SSDEEP: | 98304:wIZTffzvns6eLKLdpRwznfsJb+7J7ERXndiWaKzPtSjXmbABY/lT8vjkZBvrePVv:F3XP9No |
MALICIOUS
Starts NET.EXE for service management
- msiexec.exe (PID: 1336)
- net.exe (PID: 3956)
- msiexec.exe (PID: 4528)
- net.exe (PID: 5468)
- net.exe (PID: 3956)
Bypass execution policy to execute commands
- powershell.exe (PID: 1512)
- powershell.exe (PID: 7728)
- powershell.exe (PID: 6540)
Changes powershell execution policy (Bypass)
- AgentPackageAgentInformation.exe (PID: 2232)
- AgentPackageAgentInformation.exe (PID: 8108)
- AgentPackageAgentInformation.exe (PID: 2320)
Executing a file with an untrusted certificate
- SRSelfSignCertUtil.exe (PID: 7260)
ATERA mutex has been found
- AgentPackageInternalPoller.exe (PID: 3480)
- AgentPackageMonitoring.exe (PID: 7772)
- AgentPackageInternalPoller.exe (PID: 7084)
- AgentPackageMonitoring.exe (PID: 3652)
Changes the autorun value in the registry
- dotnet-runtime-8.0.11-win-x64.exe (PID: 2160)
SUSPICIOUS
Process drops legitimate windows executable
- msiexec.exe (PID: 1324)
- AteraAgent.exe (PID: 6320)
- msiexec.exe (PID: 6828)
- AteraAgent.exe (PID: 2680)
- AgentPackageUpgradeAgent.exe (PID: 7344)
- 8-0-11.exe (PID: 5908)
- AgentPackageRuntimeInstaller.exe (PID: 7900)
- dotnet-runtime-8.0.11-win-x64.exe (PID: 2160)
- 8-0-11.exe (PID: 7152)
- AteraAgent.exe (PID: 7956)
- Agent.Package.Availability.exe (PID: 7072)
- AgentPackageUpgradeAgent.exe (PID: 5896)
- AgentPackageUpgradeAgent.exe (PID: 2524)
Executes as Windows Service
- VSSVC.exe (PID: 6140)
- AteraAgent.exe (PID: 6320)
- AteraAgent.exe (PID: 2680)
- SRService.exe (PID: 4916)
- AteraAgent.exe (PID: 7956)
Executable content was dropped or overwritten
- rundll32.exe (PID: 2192)
- rundll32.exe (PID: 3588)
- rundll32.exe (PID: 856)
- rundll32.exe (PID: 2032)
- AteraAgent.exe (PID: 6320)
- SplashtopStreamer.exe (PID: 7364)
- PreVerCheck.exe (PID: 7412)
- csc.exe (PID: 7520)
- SetupUtil.exe (PID: 7240)
- AteraAgent.exe (PID: 2680)
- AgentPackageTicketing.exe (PID: 7368)
- AgentPackageUpgradeAgent.exe (PID: 7344)
- rundll32.exe (PID: 5444)
- rundll32.exe (PID: 2368)
- 8-0-11.exe (PID: 5908)
- rundll32.exe (PID: 6956)
- 8-0-11.exe (PID: 7152)
- AgentPackageRuntimeInstaller.exe (PID: 7900)
- dotnet-runtime-8.0.11-win-x64.exe (PID: 2160)
- csc.exe (PID: 6208)
- rundll32.exe (PID: 7364)
- AteraAgent.exe (PID: 7956)
- AgentPackageTicketing.exe (PID: 7412)
- Agent.Package.Availability.exe (PID: 7072)
- csc.exe (PID: 6684)
- Agent.Package.Availability.exe (PID: 4648)
- AgentPackageUpgradeAgent.exe (PID: 2524)
- AgentPackageUpgradeAgent.exe (PID: 5896)
Reads the Windows owner or organization settings
- msiexec.exe (PID: 6828)
Uses TASKKILL.EXE to kill process
- msiexec.exe (PID: 1336)
- cmd.exe (PID: 6764)
- cmd.exe (PID: 8144)
- cmd.exe (PID: 7232)
- cmd.exe (PID: 6780)
- cmd.exe (PID: 7340)
- cmd.exe (PID: 7772)
- cmd.exe (PID: 7888)
- cmd.exe (PID: 8128)
- cmd.exe (PID: 8012)
- cmd.exe (PID: 7520)
- msiexec.exe (PID: 4528)
Potential Corporate Privacy Violation
- rundll32.exe (PID: 3588)
- rundll32.exe (PID: 2032)
- AteraAgent.exe (PID: 6320)
- AgentPackageAgentInformation.exe (PID: 6532)
- AgentPackageAgentInformation.exe (PID: 3624)
- AgentPackageMonitoring.exe (PID: 3620)
- AgentPackageAgentInformation.exe (PID: 2232)
- AgentPackageInternalPoller.exe (PID: 3480)
- AteraAgent.exe (PID: 2680)
- AgentPackageMarketplace.exe (PID: 7804)
- AgentPackageTicketing.exe (PID: 7368)
- rundll32.exe (PID: 2368)
- AgentPackageAgentInformation.exe (PID: 8108)
- AgentPackageMonitoring.exe (PID: 7772)
- AteraAgent.exe (PID: 7956)
- rundll32.exe (PID: 7364)
- AgentPackageInternalPoller.exe (PID: 7084)
- AgentPackageMonitoring.exe (PID: 3652)
- AgentPackageAgentInformation.exe (PID: 2320)
- AgentPackageUpgradeAgent.exe (PID: 7344)
Reads security settings of Internet Explorer
- AteraAgent.exe (PID: 5720)
- AteraAgent.exe (PID: 6320)
- AteraAgent.exe (PID: 2680)
- SplashtopStreamer.exe (PID: 7364)
- AgentPackageAgentInformation.exe (PID: 2232)
- SetupUtil.exe (PID: 7240)
- 8-0-11.exe (PID: 7152)
- AgentPackageAgentInformation.exe (PID: 8108)
- AteraAgent.exe (PID: 6232)
- AteraAgent.exe (PID: 7956)
- AgentPackageAgentInformation.exe (PID: 2320)
ATERAAGENT has been detected
- AteraAgent.exe (PID: 5720)
- AteraAgent.exe (PID: 6320)
- AteraAgent.exe (PID: 2680)
- AteraAgent.exe (PID: 7692)
- AteraAgent.exe (PID: 6232)
- AteraAgent.exe (PID: 7956)
Restarts service on failure
- sc.exe (PID: 6228)
- sc.exe (PID: 1136)
- sc.exe (PID: 7912)
Starts SC.EXE for service management
- AteraAgent.exe (PID: 6320)
- AteraAgent.exe (PID: 2680)
- AteraAgent.exe (PID: 7956)
Reads the date of Windows installation
- AteraAgent.exe (PID: 6320)
- AteraAgent.exe (PID: 2680)
- AteraAgent.exe (PID: 7956)
Starts POWERSHELL.EXE for commands execution
- AgentPackageAgentInformation.exe (PID: 2232)
- AgentPackageAgentInformation.exe (PID: 8108)
- AgentPackageAgentInformation.exe (PID: 2320)
The process hides Powershell's copyright startup banner
- AgentPackageAgentInformation.exe (PID: 2232)
- AgentPackageAgentInformation.exe (PID: 8108)
- AgentPackageAgentInformation.exe (PID: 2320)
The process bypasses the loading of PowerShell profile settings
- AgentPackageAgentInformation.exe (PID: 2232)
- AgentPackageAgentInformation.exe (PID: 8108)
- AgentPackageAgentInformation.exe (PID: 2320)
The process executes Powershell scripts
- AgentPackageAgentInformation.exe (PID: 2232)
- AgentPackageAgentInformation.exe (PID: 8108)
- AgentPackageAgentInformation.exe (PID: 2320)
CSC.EXE is used to compile C# code
- csc.exe (PID: 7520)
- csc.exe (PID: 6208)
- csc.exe (PID: 6684)
Starts CMD.EXE for commands execution
- AgentPackageAgentInformation.exe (PID: 2232)
- msiexec.exe (PID: 7484)
- SetupUtil.exe (PID: 7240)
- AgentPackageRuntimeInstaller.exe (PID: 7900)
- AgentPackageAgentInformation.exe (PID: 8108)
- AgentPackageRuntimeInstaller.exe (PID: 7672)
- AgentPackageAgentInformation.exe (PID: 2320)
The process executes VB scripts
- cmd.exe (PID: 7600)
- cmd.exe (PID: 4512)
- cmd.exe (PID: 3980)
Creates FileSystem object to access computer's file system (SCRIPT)
- cscript.exe (PID: 7668)
- cscript.exe (PID: 6956)
- cscript.exe (PID: 7236)
Checks whether a specific file exists (SCRIPT)
- cscript.exe (PID: 7668)
- cscript.exe (PID: 6956)
- cscript.exe (PID: 7236)
Gets full path of the running script (SCRIPT)
- cscript.exe (PID: 7668)
- cscript.exe (PID: 6956)
- cscript.exe (PID: 7236)
Gets a collection of all available drive names (SCRIPT)
- cscript.exe (PID: 7668)
- cscript.exe (PID: 6956)
- cscript.exe (PID: 7236)
Accesses computer name via WMI (SCRIPT)
- cscript.exe (PID: 7668)
- cscript.exe (PID: 6956)
- cscript.exe (PID: 7236)
Gets the drive type (SCRIPT)
- cscript.exe (PID: 7668)
- cscript.exe (PID: 6956)
- cscript.exe (PID: 7236)
Accesses WMI object, sets custom ImpersonationLevel (SCRIPT)
- cscript.exe (PID: 7668)
- cscript.exe (PID: 6956)
- cscript.exe (PID: 7236)
Accesses OperatingSystem(Win32_OperatingSystem) via WMI (SCRIPT)
- cscript.exe (PID: 7668)
- cscript.exe (PID: 6956)
- cscript.exe (PID: 7236)
Executes WMI query (SCRIPT)
- cscript.exe (PID: 7668)
- cscript.exe (PID: 6956)
- cscript.exe (PID: 7236)
Searches for installed software
- AgentPackageAgentInformation.exe (PID: 2232)
- 8-0-11.exe (PID: 7152)
- dotnet-runtime-8.0.11-win-x64.exe (PID: 2160)
- AgentPackageAgentInformation.exe (PID: 8108)
- Agent.Package.Software.exe (PID: 4308)
- AgentPackageAgentInformation.exe (PID: 2320)
The process creates files with name similar to system file names
- msiexec.exe (PID: 6828)
- AteraAgent.exe (PID: 2680)
Drops a system driver (possible attempt to evade defenses)
- msiexec.exe (PID: 6828)
Creates/Modifies COM task schedule object
- msiexec.exe (PID: 7484)
- SRService.exe (PID: 6180)
Starts a Microsoft application from unusual location
- 8-0-11.exe (PID: 7152)
- dotnet-runtime-8.0.11-win-x64.exe (PID: 2160)
Starts itself from another location
- 8-0-11.exe (PID: 7152)
- Agent.Package.Availability.exe (PID: 7072)
- AgentPackageUpgradeAgent.exe (PID: 5896)
Creates a software uninstall entry
- dotnet-runtime-8.0.11-win-x64.exe (PID: 2160)
Connects to unusual port
- Agent.Package.Availability.exe (PID: 7072)
- Agent.Package.Availability.exe (PID: 4648)
INFO
Reads security settings of Internet Explorer
- msiexec.exe (PID: 1324)
Reads the software policy settings
- msiexec.exe (PID: 1324)
- msiexec.exe (PID: 6828)
- rundll32.exe (PID: 3588)
- AteraAgent.exe (PID: 5720)
- rundll32.exe (PID: 2032)
- AteraAgent.exe (PID: 6320)
- AgentPackageAgentInformation.exe (PID: 6532)
- AgentPackageAgentInformation.exe (PID: 3624)
- AteraAgent.exe (PID: 2680)
- AgentPackageSTRemote.exe (PID: 6732)
- AgentPackageMonitoring.exe (PID: 3620)
- msiexec.exe (PID: 7484)
- cscript.exe (PID: 7668)
- AgentPackageAgentInformation.exe (PID: 2232)
- SRManager.exe (PID: 2212)
- AgentPackageInternalPoller.exe (PID: 3480)
- AgentPackageSTRemote.exe (PID: 7316)
- AgentPackageHeartbeat.exe (PID: 6232)
- AgentPackageMarketplace.exe (PID: 7804)
- AgentPackageRuntimeInstaller.exe (PID: 7900)
- AgentPackageTicketing.exe (PID: 7368)
- AgentPackageUpgradeAgent.exe (PID: 7344)
- rundll32.exe (PID: 2368)
- cscript.exe (PID: 6956)
- AgentPackageAgentInformation.exe (PID: 8108)
- AgentPackageMonitoring.exe (PID: 7772)
- rundll32.exe (PID: 7364)
- AteraAgent.exe (PID: 6232)
- AteraAgent.exe (PID: 7956)
- AgentPackageHeartbeat.exe (PID: 7288)
- AgentPackageInternalPoller.exe (PID: 7084)
- Agent.Package.Software.exe (PID: 4308)
- Agent.Package.Availability.exe (PID: 7072)
- AgentPackageMarketplace.exe (PID: 2804)
- AgentPackageRuntimeInstaller.exe (PID: 7672)
- AgentPackageTicketing.exe (PID: 7412)
- Agent.Package.Availability.exe (PID: 4648)
- slui.exe (PID: 7172)
- cscript.exe (PID: 7236)
- AgentPackageMonitoring.exe (PID: 3652)
- AgentPackageAgentInformation.exe (PID: 2320)
- AgentPackageHeartbeat.exe (PID: 3676)
- AgentPackageHeartbeat.exe (PID: 7196)
Checks proxy server information
- msiexec.exe (PID: 1324)
- rundll32.exe (PID: 3588)
- rundll32.exe (PID: 2032)
- slui.exe (PID: 7172)
Checks supported languages
- msiexec.exe (PID: 6828)
- msiexec.exe (PID: 1336)
- AteraAgent.exe (PID: 5720)
- msiexec.exe (PID: 4312)
- AgentPackageAgentInformation.exe (PID: 6532)
- AgentPackageAgentInformation.exe (PID: 3624)
- AgentPackageAgentInformation.exe (PID: 5744)
- AteraAgent.exe (PID: 2680)
- AgentPackageAgentInformation.exe (PID: 2232)
- AteraAgent.exe (PID: 6320)
- SplashtopStreamer.exe (PID: 7364)
- PreVerCheck.exe (PID: 7412)
- csc.exe (PID: 7520)
- cvtres.exe (PID: 7548)
- msiexec.exe (PID: 7484)
- _isE186.exe (PID: 7744)
- _isE186.exe (PID: 7828)
- _isE186.exe (PID: 7788)
- _isE186.exe (PID: 7872)
- _isE186.exe (PID: 7912)
- _isE186.exe (PID: 7988)
- _isE186.exe (PID: 8024)
- _isE186.exe (PID: 8064)
- _isE186.exe (PID: 8100)
- AgentPackageSTRemote.exe (PID: 6732)
- AgentPackageMonitoring.exe (PID: 3620)
- _isE186.exe (PID: 7956)
- _isEAED.exe (PID: 3620)
- _isEAED.exe (PID: 8152)
- _isEAED.exe (PID: 7216)
- _isEAED.exe (PID: 6236)
- _isEAED.exe (PID: 3748)
- _isEAED.exe (PID: 7392)
- _isEAED.exe (PID: 7320)
- _isEAED.exe (PID: 2628)
- _isEAED.exe (PID: 7736)
- _isEAED.exe (PID: 7544)
- _is174.exe (PID: 7916)
- _is174.exe (PID: 7928)
- _is174.exe (PID: 8048)
- _is174.exe (PID: 8068)
- _is174.exe (PID: 8104)
- _is174.exe (PID: 8160)
- _is174.exe (PID: 8116)
- _is174.exe (PID: 7784)
- _is174.exe (PID: 8180)
- SetupUtil.exe (PID: 7212)
- SetupUtil.exe (PID: 504)
- SetupUtil.exe (PID: 7240)
- _is174.exe (PID: 7676)
- SRSelfSignCertUtil.exe (PID: 7260)
- _is13F4.exe (PID: 7640)
- _is13F4.exe (PID: 7564)
- _is13F4.exe (PID: 2492)
- _is13F4.exe (PID: 2612)
- _is13F4.exe (PID: 7920)
- _is13F4.exe (PID: 7060)
- _is13F4.exe (PID: 7904)
- _is13F4.exe (PID: 8044)
- _is13F4.exe (PID: 8060)
- _is13F4.exe (PID: 8064)
- SRService.exe (PID: 6180)
- _is17BE.exe (PID: 7784)
- _is17BE.exe (PID: 7676)
- _is17BE.exe (PID: 7196)
- _is17BE.exe (PID: 7348)
- _is17BE.exe (PID: 6956)
- _is17BE.exe (PID: 1808)
- _is17BE.exe (PID: 5252)
- _is17BE.exe (PID: 3760)
- SRService.exe (PID: 7756)
- _is17BE.exe (PID: 8136)
- SRService.exe (PID: 4916)
- _is17BE.exe (PID: 3740)
- SRServer.exe (PID: 7880)
- SRAgent.exe (PID: 8092)
- SRAppPB.exe (PID: 8076)
- SRManager.exe (PID: 2212)
- SRUtility.exe (PID: 7976)
- AgentPackageAgentInformation.exe (PID: 8108)
- SRFeature.exe (PID: 8124)
- BdEpSDK.exe (PID: 3628)
- AgentPackageInternalPoller.exe (PID: 3480)
- AgentPackageSTRemote.exe (PID: 7316)
- AgentPackageHeartbeat.exe (PID: 6232)
- AgentPackageRuntimeInstaller.exe (PID: 7900)
- SRUtility.exe (PID: 7176)
- AgentPackageSystemTools.exe (PID: 7432)
- AgentPackageMonitoring.exe (PID: 7772)
- AgentPackageADRemote.exe (PID: 760)
- AgentPackageUpgradeAgent.exe (PID: 7344)
- AgentPackageTicketing.exe (PID: 7368)
- AgentPackageMarketplace.exe (PID: 7804)
- Agent.Package.Software.exe (PID: 4800)
- AgentPackageOsUpdates.exe (PID: 6664)
- Agent.Package.Watchdog.exe (PID: 4648)
- Agent.Package.Availability.exe (PID: 6900)
- msiexec.exe (PID: 4528)
- 8-0-11.exe (PID: 5908)
- 8-0-11.exe (PID: 7152)
- dotnet-runtime-8.0.11-win-x64.exe (PID: 2160)
- csc.exe (PID: 6208)
- cvtres.exe (PID: 7784)
- AteraAgent.exe (PID: 7692)
- AteraAgent.exe (PID: 6232)
- AteraAgent.exe (PID: 7956)
- msiexec.exe (PID: 6520)
- wifiNetwork.ext.exe (PID: 5924)
- lockscreen.ext.exe (PID: 8120)
- SRVirtualDisplay.exe (PID: 7396)
- osqueryi.exe (PID: 4648)
- msiexec.exe (PID: 7640)
- msiexec.exe (PID: 2524)
- dotnet.exe (PID: 2764)
- dotnet.exe (PID: 6980)
- AgentPackageHeartbeat.exe (PID: 7288)
- AgentPackageInternalPoller.exe (PID: 7084)
- AgentPackageAgentInformation.exe (PID: 2320)
- AgentPackageSTRemote.exe (PID: 5340)
- AgentPackageSystemTools.exe (PID: 7484)
- AgentPackageADRemote.exe (PID: 640)
- AgentPackageMarketplace.exe (PID: 2804)
- SRUtility.exe (PID: 6376)
- AgentPackageRuntimeInstaller.exe (PID: 7672)
- Agent.Package.Availability.exe (PID: 7072)
- AgentPackageMonitoring.exe (PID: 3652)
- Agent.Package.Software.exe (PID: 4308)
- AgentPackageTicketing.exe (PID: 7412)
- Agent.Package.Watchdog.exe (PID: 5528)
- dotnet.exe (PID: 3672)
- Agent.Package.Availability.exe (PID: 4648)
- cvtres.exe (PID: 7388)
- csc.exe (PID: 6684)
- AgentPackageHeartbeat.exe (PID: 3676)
- AgentPackageUpgradeAgent.exe (PID: 2524)
- AgentPackageUpgradeAgent.exe (PID: 5896)
- AgentPackageHeartbeat.exe (PID: 7196)
- AgentPackageTicketing.exe (PID: 3688)
Reads the computer name
- msiexec.exe (PID: 6828)
- msiexec.exe (PID: 4312)
- msiexec.exe (PID: 1336)
- AteraAgent.exe (PID: 5720)
- AgentPackageAgentInformation.exe (PID: 6532)
- AgentPackageAgentInformation.exe (PID: 3624)
- AgentPackageAgentInformation.exe (PID: 5744)
- AteraAgent.exe (PID: 2680)
- AgentPackageAgentInformation.exe (PID: 2232)
- AteraAgent.exe (PID: 6320)
- AgentPackageMonitoring.exe (PID: 3620)
- AgentPackageSTRemote.exe (PID: 6732)
- SplashtopStreamer.exe (PID: 7364)
- msiexec.exe (PID: 7484)
- _isE186.exe (PID: 7744)
- _isE186.exe (PID: 7788)
- _isE186.exe (PID: 7828)
- _isE186.exe (PID: 7956)
- _isE186.exe (PID: 7912)
- _isE186.exe (PID: 7872)
- _isE186.exe (PID: 7988)
- _isE186.exe (PID: 8100)
- _isE186.exe (PID: 8024)
- _isE186.exe (PID: 8064)
- _isEAED.exe (PID: 8152)
- _isEAED.exe (PID: 7216)
- _isEAED.exe (PID: 6236)
- _isEAED.exe (PID: 3620)
- _isEAED.exe (PID: 7320)
- _isEAED.exe (PID: 7544)
- _isEAED.exe (PID: 7392)
- _isEAED.exe (PID: 7736)
- _isEAED.exe (PID: 3748)
- _isEAED.exe (PID: 2628)
- _is174.exe (PID: 8068)
- _is174.exe (PID: 7928)
- _is174.exe (PID: 8048)
- _is174.exe (PID: 8104)
- _is174.exe (PID: 8160)
- _is174.exe (PID: 8116)
- _is174.exe (PID: 7784)
- _is174.exe (PID: 7916)
- _is174.exe (PID: 8180)
- SetupUtil.exe (PID: 7240)
- _is174.exe (PID: 7676)
- SRSelfSignCertUtil.exe (PID: 7260)
- _is13F4.exe (PID: 7640)
- _is13F4.exe (PID: 7564)
- _is13F4.exe (PID: 2492)
- _is13F4.exe (PID: 7060)
- _is13F4.exe (PID: 7904)
- _is13F4.exe (PID: 7920)
- _is13F4.exe (PID: 2612)
- _is13F4.exe (PID: 8060)
- _is13F4.exe (PID: 8064)
- _is13F4.exe (PID: 8044)
- _is17BE.exe (PID: 7348)
- _is17BE.exe (PID: 7784)
- _is17BE.exe (PID: 7676)
- _is17BE.exe (PID: 3760)
- SRService.exe (PID: 6180)
- _is17BE.exe (PID: 6956)
- _is17BE.exe (PID: 7196)
- _is17BE.exe (PID: 1808)
- _is17BE.exe (PID: 8136)
- _is17BE.exe (PID: 5252)
- SRService.exe (PID: 4916)
- _is17BE.exe (PID: 3740)
- SRService.exe (PID: 7756)
- SRManager.exe (PID: 2212)
- SRServer.exe (PID: 7880)
- SRAgent.exe (PID: 8092)
- SRAppPB.exe (PID: 8076)
- SRFeature.exe (PID: 8124)
- AgentPackageAgentInformation.exe (PID: 8108)
- AgentPackageInternalPoller.exe (PID: 3480)
- AgentPackageHeartbeat.exe (PID: 6232)
- AgentPackageSTRemote.exe (PID: 7316)
- AgentPackageSystemTools.exe (PID: 7432)
- AgentPackageMonitoring.exe (PID: 7772)
- AgentPackageRuntimeInstaller.exe (PID: 7900)
- AgentPackageTicketing.exe (PID: 7368)
- AgentPackageUpgradeAgent.exe (PID: 7344)
- AgentPackageADRemote.exe (PID: 760)
- AgentPackageMarketplace.exe (PID: 7804)
- Agent.Package.Availability.exe (PID: 6900)
- Agent.Package.Watchdog.exe (PID: 4648)
- Agent.Package.Software.exe (PID: 4800)
- AgentPackageOsUpdates.exe (PID: 6664)
- msiexec.exe (PID: 4528)
- 8-0-11.exe (PID: 5908)
- 8-0-11.exe (PID: 7152)
- dotnet-runtime-8.0.11-win-x64.exe (PID: 2160)
- AteraAgent.exe (PID: 7692)
- AteraAgent.exe (PID: 6232)
- AteraAgent.exe (PID: 7956)
- osqueryi.exe (PID: 4648)
- wifiNetwork.ext.exe (PID: 5924)
- lockscreen.ext.exe (PID: 8120)
- msiexec.exe (PID: 6520)
- msiexec.exe (PID: 7640)
- msiexec.exe (PID: 2524)
- AgentPackageHeartbeat.exe (PID: 7288)
- SRVirtualDisplay.exe (PID: 7396)
- AgentPackageInternalPoller.exe (PID: 7084)
- AgentPackageAgentInformation.exe (PID: 2320)
- AgentPackageSTRemote.exe (PID: 5340)
- AgentPackageADRemote.exe (PID: 640)
- AgentPackageSystemTools.exe (PID: 7484)
- AgentPackageRuntimeInstaller.exe (PID: 7672)
- AgentPackageMarketplace.exe (PID: 2804)
- AgentPackageTicketing.exe (PID: 7412)
- Agent.Package.Availability.exe (PID: 7072)
- Agent.Package.Watchdog.exe (PID: 5528)
- AgentPackageMonitoring.exe (PID: 3652)
- Agent.Package.Software.exe (PID: 4308)
- Agent.Package.Availability.exe (PID: 4648)
- AgentPackageHeartbeat.exe (PID: 3676)
- AgentPackageUpgradeAgent.exe (PID: 5896)
- AgentPackageUpgradeAgent.exe (PID: 2524)
- AgentPackageHeartbeat.exe (PID: 7196)
- AgentPackageTicketing.exe (PID: 3688)
Creates files or folders in the user directory
- msiexec.exe (PID: 1324)
Reads the machine GUID from the registry
- msiexec.exe (PID: 6828)
- AteraAgent.exe (PID: 5720)
- AteraAgent.exe (PID: 6320)
- AgentPackageAgentInformation.exe (PID: 6532)
- AgentPackageAgentInformation.exe (PID: 3624)
- AgentPackageAgentInformation.exe (PID: 5744)
- AteraAgent.exe (PID: 2680)
- AgentPackageAgentInformation.exe (PID: 2232)
- AgentPackageSTRemote.exe (PID: 6732)
- csc.exe (PID: 7520)
- msiexec.exe (PID: 7484)
- AgentPackageMonitoring.exe (PID: 3620)
- SRSelfSignCertUtil.exe (PID: 7260)
- SRManager.exe (PID: 2212)
- AgentPackageSTRemote.exe (PID: 7316)
- AgentPackageInternalPoller.exe (PID: 3480)
- AgentPackageAgentInformation.exe (PID: 8108)
- AgentPackageHeartbeat.exe (PID: 6232)
- AgentPackageSystemTools.exe (PID: 7432)
- AgentPackageMonitoring.exe (PID: 7772)
- AgentPackageRuntimeInstaller.exe (PID: 7900)
- AgentPackageTicketing.exe (PID: 7368)
- AgentPackageUpgradeAgent.exe (PID: 7344)
- AgentPackageMarketplace.exe (PID: 7804)
- AgentPackageADRemote.exe (PID: 760)
- AgentPackageOsUpdates.exe (PID: 6664)
- dotnet-runtime-8.0.11-win-x64.exe (PID: 2160)
- csc.exe (PID: 6208)
- AteraAgent.exe (PID: 7692)
- AteraAgent.exe (PID: 7956)
- AteraAgent.exe (PID: 6232)
- AgentPackageSystemTools.exe (PID: 7484)
- AgentPackageAgentInformation.exe (PID: 2320)
- AgentPackageHeartbeat.exe (PID: 7288)
- AgentPackageSTRemote.exe (PID: 5340)
- AgentPackageRuntimeInstaller.exe (PID: 7672)
- AgentPackageInternalPoller.exe (PID: 7084)
- AgentPackageADRemote.exe (PID: 640)
- AgentPackageMonitoring.exe (PID: 3652)
- AgentPackageMarketplace.exe (PID: 2804)
- Agent.Package.Availability.exe (PID: 7072)
- AgentPackageTicketing.exe (PID: 7412)
- Agent.Package.Availability.exe (PID: 4648)
- csc.exe (PID: 6684)
- AgentPackageHeartbeat.exe (PID: 3676)
- AgentPackageUpgradeAgent.exe (PID: 5896)
- AgentPackageUpgradeAgent.exe (PID: 2524)
- AgentPackageHeartbeat.exe (PID: 7196)
- AgentPackageTicketing.exe (PID: 3688)
The sample compiled with english language support
- rundll32.exe (PID: 2192)
- rundll32.exe (PID: 3588)
- rundll32.exe (PID: 856)
- rundll32.exe (PID: 2032)
- SplashtopStreamer.exe (PID: 7364)
- PreVerCheck.exe (PID: 7412)
- msiexec.exe (PID: 7484)
- AteraAgent.exe (PID: 6320)
- SetupUtil.exe (PID: 7240)
- msiexec.exe (PID: 6828)
- AteraAgent.exe (PID: 2680)
- rundll32.exe (PID: 5444)
- rundll32.exe (PID: 2368)
- 8-0-11.exe (PID: 7152)
- 8-0-11.exe (PID: 5908)
- rundll32.exe (PID: 6956)
- AgentPackageRuntimeInstaller.exe (PID: 7900)
- dotnet-runtime-8.0.11-win-x64.exe (PID: 2160)
- rundll32.exe (PID: 7364)
- AteraAgent.exe (PID: 7956)
- AgentPackageUpgradeAgent.exe (PID: 5896)
Create files in a temporary directory
- rundll32.exe (PID: 3588)
- rundll32.exe (PID: 856)
- rundll32.exe (PID: 2192)
- rundll32.exe (PID: 2032)
Disables trace logs
- rundll32.exe (PID: 3588)
- AteraAgent.exe (PID: 6320)
- rundll32.exe (PID: 2032)
- AgentPackageAgentInformation.exe (PID: 6532)
- AgentPackageAgentInformation.exe (PID: 3624)
- AteraAgent.exe (PID: 2680)
- AgentPackageMonitoring.exe (PID: 3620)
- AgentPackageSTRemote.exe (PID: 6732)
- AgentPackageAgentInformation.exe (PID: 2232)
- AgentPackageInternalPoller.exe (PID: 3480)
- AgentPackageHeartbeat.exe (PID: 6232)
- AgentPackageSTRemote.exe (PID: 7316)
- AgentPackageRuntimeInstaller.exe (PID: 7900)
- AgentPackageUpgradeAgent.exe (PID: 7344)
- AgentPackageMarketplace.exe (PID: 7804)
- AgentPackageTicketing.exe (PID: 7368)
- rundll32.exe (PID: 2368)
- AgentPackageAgentInformation.exe (PID: 8108)
- AgentPackageMonitoring.exe (PID: 7772)
- rundll32.exe (PID: 7364)
- AteraAgent.exe (PID: 7956)
- AgentPackageInternalPoller.exe (PID: 7084)
- AgentPackageHeartbeat.exe (PID: 7288)
- AgentPackageMarketplace.exe (PID: 2804)
- AgentPackageTicketing.exe (PID: 7412)
- AgentPackageRuntimeInstaller.exe (PID: 7672)
- AgentPackageMonitoring.exe (PID: 3652)
- AgentPackageAgentInformation.exe (PID: 2320)
- AgentPackageHeartbeat.exe (PID: 3676)
- AgentPackageHeartbeat.exe (PID: 7196)
Creates a software uninstall entry
- msiexec.exe (PID: 6828)
Reads Environment values
- AteraAgent.exe (PID: 5720)
- AteraAgent.exe (PID: 6320)
- AgentPackageAgentInformation.exe (PID: 6532)
- AgentPackageAgentInformation.exe (PID: 3624)
- AgentPackageAgentInformation.exe (PID: 5744)
- AteraAgent.exe (PID: 2680)
- AgentPackageMonitoring.exe (PID: 3620)
- AgentPackageAgentInformation.exe (PID: 2232)
- AgentPackageSTRemote.exe (PID: 6732)
- AgentPackageSTRemote.exe (PID: 7316)
- AgentPackageInternalPoller.exe (PID: 3480)
- AgentPackageAgentInformation.exe (PID: 8108)
- AgentPackageHeartbeat.exe (PID: 6232)
- AgentPackageSystemTools.exe (PID: 7432)
- AgentPackageMonitoring.exe (PID: 7772)
- AgentPackageRuntimeInstaller.exe (PID: 7900)
- AgentPackageTicketing.exe (PID: 7368)
- AgentPackageADRemote.exe (PID: 760)
- AgentPackageMarketplace.exe (PID: 7804)
- AgentPackageUpgradeAgent.exe (PID: 7344)
- AgentPackageOsUpdates.exe (PID: 6664)
- SRManager.exe (PID: 2212)
- AteraAgent.exe (PID: 7692)
- AteraAgent.exe (PID: 6232)
- AteraAgent.exe (PID: 7956)
- AgentPackageSTRemote.exe (PID: 5340)
- AgentPackageAgentInformation.exe (PID: 2320)
- AgentPackageADRemote.exe (PID: 640)
- AgentPackageHeartbeat.exe (PID: 7288)
- AgentPackageRuntimeInstaller.exe (PID: 7672)
- AgentPackageInternalPoller.exe (PID: 7084)
- AgentPackageMonitoring.exe (PID: 3652)
- AgentPackageSystemTools.exe (PID: 7484)
- AgentPackageTicketing.exe (PID: 7412)
- AgentPackageMarketplace.exe (PID: 2804)
- AgentPackageHeartbeat.exe (PID: 3676)
- AgentPackageUpgradeAgent.exe (PID: 2524)
- AgentPackageUpgradeAgent.exe (PID: 5896)
- AgentPackageTicketing.exe (PID: 3688)
- AgentPackageHeartbeat.exe (PID: 7196)
Creates files in the program directory
- AteraAgent.exe (PID: 5720)
- AteraAgent.exe (PID: 6320)
- AgentPackageSTRemote.exe (PID: 6732)
- AgentPackageMonitoring.exe (PID: 3620)
- AgentPackageAgentInformation.exe (PID: 2232)
- SetupUtil.exe (PID: 7240)
- SRSelfSignCertUtil.exe (PID: 7260)
- SRService.exe (PID: 6180)
- SRManager.exe (PID: 2212)
- AteraAgent.exe (PID: 2680)
- SRAgent.exe (PID: 8092)
- AgentPackageInternalPoller.exe (PID: 3480)
- AgentPackageSystemTools.exe (PID: 7432)
- AgentPackageUpgradeAgent.exe (PID: 7344)
- AgentPackageMonitoring.exe (PID: 7772)
- AgentPackageTicketing.exe (PID: 7368)
- AgentPackageRuntimeInstaller.exe (PID: 7900)
- dotnet-runtime-8.0.11-win-x64.exe (PID: 2160)
- AteraAgent.exe (PID: 6232)
- SRVirtualDisplay.exe (PID: 7396)
- AteraAgent.exe (PID: 7956)
- AgentPackageInternalPoller.exe (PID: 7084)
- Agent.Package.Watchdog.exe (PID: 5528)
- Agent.Package.Availability.exe (PID: 7072)
- Agent.Package.Software.exe (PID: 4308)
- AgentPackageMonitoring.exe (PID: 3652)
- AgentPackageRuntimeInstaller.exe (PID: 7672)
- AgentPackageTicketing.exe (PID: 7412)
- AgentPackageAgentInformation.exe (PID: 2320)
Executable content was dropped or overwritten
- msiexec.exe (PID: 6828)
- msiexec.exe (PID: 7484)
Manages system restore points
- SrTasks.exe (PID: 4012)
SPLASHTOP has been detected
- AgentPackageSTRemote.exe (PID: 6732)
- msiexec.exe (PID: 6828)
- msiexec.exe (PID: 7484)
- msiexec.exe (PID: 7484)
- SetupUtil.exe (PID: 504)
- SetupUtil.exe (PID: 7212)
- SetupUtil.exe (PID: 504)
- SetupUtil.exe (PID: 7212)
- SetupUtil.exe (PID: 7240)
- conhost.exe (PID: 6236)
- cmd.exe (PID: 7292)
- conhost.exe (PID: 7296)
- SRSelfSignCertUtil.exe (PID: 7260)
- cmd.exe (PID: 7280)
- SRService.exe (PID: 6180)
- conhost.exe (PID: 8104)
- conhost.exe (PID: 5824)
- SRService.exe (PID: 4916)
- SRService.exe (PID: 7756)
- SRService.exe (PID: 4916)
- SRManager.exe (PID: 2212)
- SRManager.exe (PID: 2212)
- PreVerCheck.exe (PID: 7412)
- SRServer.exe (PID: 7880)
- SRAgent.exe (PID: 8092)
- SRAgent.exe (PID: 8092)
- SRAppPB.exe (PID: 8076)
- SRServer.exe (PID: 7880)
- SRAppPB.exe (PID: 8076)
- SRFeature.exe (PID: 8124)
- SRFeature.exe (PID: 8124)
- conhost.exe (PID: 7672)
- SRUtility.exe (PID: 7976)
- conhost.exe (PID: 7584)
- SRUtility.exe (PID: 7976)
- AgentPackageSTRemote.exe (PID: 6732)
- BdEpSDK.exe (PID: 3628)
- AgentPackageSTRemote.exe (PID: 7316)
- SRUtility.exe (PID: 7176)
- conhost.exe (PID: 7452)
- AgentPackageSTRemote.exe (PID: 7316)
- SRUtility.exe (PID: 7176)
- AgentPackageAgentInformation.exe (PID: 8108)
- osqueryi.exe (PID: 4648)
- lockscreen.ext.exe (PID: 8120)
- wifiNetwork.ext.exe (PID: 5924)
- SRVirtualDisplay.exe (PID: 7396)
- conhost.exe (PID: 2288)
- SRVirtualDisplay.exe (PID: 7396)
- AgentPackageSTRemote.exe (PID: 5340)
- SRUtility.exe (PID: 6376)
- AgentPackageSTRemote.exe (PID: 5340)
- conhost.exe (PID: 7612)
- SRUtility.exe (PID: 6376)
- AgentPackageAgentInformation.exe (PID: 2320)
Script raised an exception (POWERSHELL)
- powershell.exe (PID: 1512)
- powershell.exe (PID: 7728)
- powershell.exe (PID: 6540)
The sample compiled with chinese language support
- msiexec.exe (PID: 6828)
Launching a file from a Registry key
- dotnet-runtime-8.0.11-win-x64.exe (PID: 2160)
Reads product name
- SRManager.exe (PID: 2212)
Process checks computer location settings
- Agent.Package.Watchdog.exe (PID: 5528)
- Agent.Package.Software.exe (PID: 4308)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .msi | | | Microsoft Windows Installer (98.5) |
|---|---|---|
| .msi | | | Microsoft Installer (100) |
EXIF
FlashPix
| CodePage: | Windows Latin 1 (Western European) |
|---|---|
| Title: | Installation Database |
| Subject: | AteraAgent |
| Author: | Atera networks |
| Keywords: | Installer |
| Comments: | This installer database contains the logic and data required to install AteraAgent. |
| Template: | Intel;1033 |
| RevisionNumber: | {721AD955-79FD-4019-BBF5-9DCC4C1175BB} |
| CreateDate: | 2024:02:28 10:52:02 |
| ModifyDate: | 2024:02:28 10:52:02 |
| Pages: | 200 |
| Words: | 6 |
| Software: | Windows Installer XML Toolset (3.11.2.4516) |
| Security: | Read-only recommended |
Total processes
424
Monitored processes
280
Malicious processes
21
Suspicious processes
15
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 504 | "C:\Program Files (x86)\Splashtop\Splashtop Remote\Server\Support\SetupUtil.exe" /P USERSESSIONID | C:\Program Files (x86)\Splashtop\Splashtop Remote\Server\Support\SetupUtil.exe | — | msiexec.exe | |||||||||||
User: SYSTEM Company: Splashtop Inc. Integrity Level: SYSTEM Description: Splashtop® Streamer Setup Utility Exit code: 0 Version: 1.0.4.1 Modules
| |||||||||||||||
| 504 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | taskkill.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 640 | "C:\Program Files\ATERA Networks\AteraAgent\Packages\AgentPackageADRemote\AgentPackageADRemote.exe" a2d4452d-ebcb-40ad-877a-ab1218cf124e "66b0bbd7-3e6d-4698-840f-77ee8f3b4aeb" agent-api.atera.com/Production 443 or8ixLi90Mf "eyJBZENvbW1hbmRUeXBlIjo1LCJJbnN0YWxsYXRpb25GaWxlVXJsIjoiaHR0cHM6Ly9wYWNrYWdlc3N0b3JlLmJsb2IuY29yZS53aW5kb3dzLm5ldC9pbnN0YWxsZXJzL0FueURlc2svV2luZG93cy9BZ2VudF9BbnlEZXNrX0N1c3RvbV9DbGllbnRfOS4wLjUubXNpIiwiRm9yY2VJbnN0YWxsIjpmYWxzZSwiVGFyZ2V0VmVyc2lvbiI6IjkuMC41In0=" 001Q300000Tr1TZIAZ | C:\Program Files\ATERA Networks\AteraAgent\Packages\AgentPackageADRemote\AgentPackageADRemote.exe | — | AteraAgent.exe | |||||||||||
User: SYSTEM Integrity Level: SYSTEM Description: AgentPackageADRemote Exit code: 0 Version: 6.0.0.0 Modules
| |||||||||||||||
| 760 | "C:\Program Files (x86)\ATERA Networks\AteraAgent\Packages\AgentPackageADRemote\AgentPackageADRemote.exe" a2d4452d-ebcb-40ad-877a-ab1218cf124e "739f01d1-0d71-4323-92b3-7dde21b04c67" agent-api.atera.com/Production 443 or8ixLi90Mf "eyJBZENvbW1hbmRUeXBlIjo1LCJJbnN0YWxsYXRpb25GaWxlVXJsIjoiaHR0cHM6Ly9wYWNrYWdlc3N0b3JlLmJsb2IuY29yZS53aW5kb3dzLm5ldC9pbnN0YWxsZXJzL0FueURlc2svV2luZG93cy9BZ2VudF9BbnlEZXNrX0N1c3RvbV9DbGllbnRfOS4wLjUubXNpIiwiRm9yY2VJbnN0YWxsIjpmYWxzZSwiVGFyZ2V0VmVyc2lvbiI6IjkuMC41In0=" 001Q300000Tr1TZIAZ | C:\Program Files (x86)\ATERA Networks\AteraAgent\Packages\AgentPackageADRemote\AgentPackageADRemote.exe | — | AteraAgent.exe | |||||||||||
User: SYSTEM Integrity Level: SYSTEM Description: AgentPackageADRemote Exit code: 0 Version: 6.0.0.0 Modules
| |||||||||||||||
| 856 | rundll32.exe "C:\WINDOWS\Installer\MSI98B7.tmp",zzzzInvokeManagedCustomActionOutOfProc SfxCA_1546484 10 AlphaControlAgentInstallation!AlphaControlAgentInstallation.CustomActions.ShouldContinueInstallation | C:\Windows\SysWOW64\rundll32.exe | msiexec.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows host process (Rundll32) Exit code: 0 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 856 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | AgentPackageHeartbeat.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 868 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 984 | C:\WINDOWS\system32\net1 STOP AteraAgent | C:\Windows\SysWOW64\net1.exe | — | net.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Net Command Exit code: 2 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1136 | "C:\Windows\System32\sc.exe" failure AteraAgent reset= 600 actions= restart/25000 | C:\Windows\System32\sc.exe | — | AteraAgent.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Service Control Manager Configuration Tool Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1148 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | AgentPackageTicketing.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
126 598
Read events
124 479
Write events
1 902
Delete events
217
Modification events
| (PID) Process: | (6140) VSSVC.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\COM+ REGDB Writer |
| Operation: | write | Name: | IDENTIFY (Leave) |
Value: 4800000000000000D9D0C9C5C8E1DB01FC1700000C170000E80300000000000001000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (6140) VSSVC.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\Registry Writer |
| Operation: | write | Name: | IDENTIFY (Leave) |
Value: 4800000000000000D9D0C9C5C8E1DB01FC170000C0070000E80300000000000001000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (6140) VSSVC.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\Shadow Copy Optimization Writer |
| Operation: | write | Name: | IDENTIFY (Leave) |
Value: 4800000000000000D9D0C9C5C8E1DB01FC1700001C080000E80300000000000001000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (6140) VSSVC.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\ASR Writer |
| Operation: | write | Name: | IDENTIFY (Leave) |
Value: 48000000000000004836CCC5C8E1DB01FC170000680A0000E80300000000000001000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (6828) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\SystemRestore |
| Operation: | write | Name: | SrCreateRp (Enter) |
Value: 4800000000000000909414C5C8E1DB01AC1A000030150000D50700000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (6828) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\SPP |
| Operation: | write | Name: | SppGetSnapshots (Enter) |
Value: 4800000000000000909414C5C8E1DB01AC1A000030150000D20700000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (6828) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\SPP |
| Operation: | write | Name: | SppGetSnapshots (Leave) |
Value: 48000000000000008E8C3FC5C8E1DB01AC1A000030150000D20700000100000000000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (6828) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\SPP |
| Operation: | write | Name: | SppEnumGroups (Enter) |
Value: 48000000000000008E8C3FC5C8E1DB01AC1A000030150000D10700000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (6828) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\SPP |
| Operation: | write | Name: | SppEnumGroups (Leave) |
Value: 4800000000000000F4DD41C5C8E1DB01AC1A000030150000D10700000100000000000000010000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (6828) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\SPP |
| Operation: | write | Name: | SppCreate (Enter) |
Value: 4800000000000000A64244C5C8E1DB01AC1A000030150000D00700000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
Executable files
1 270
Suspicious files
314
Text files
276
Unknown types
30
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 6828 | msiexec.exe | C:\System Volume Information\SPP\metadata-2 | — | |
MD5:— | SHA256:— | |||
| 1324 | msiexec.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\698460A0B6E60F2F602361424D832905_8BB23D43DE574E82F2BEE0DF0EC47EEB | binary | |
MD5:BFFBA61A92B1A2AD500615E8CC78E2EF | SHA256:9776EBA42C0FF3F863CE964E0353DE8F019CFCDA489FAFF745FD7F1C7B110CD5 | |||
| 1324 | msiexec.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\8EC9B1D0ABBD7F98B401D425828828CE_93E8F0A6DF0B1F1414474691911362FC | binary | |
MD5:36A66BD02EC83D5DA4FD34B7094991CB | SHA256:7A501AB294CE64AF0A95DBD414879E9AEE8AA3F90005C6508214E3CC5A52EECF | |||
| 1324 | msiexec.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\698460A0B6E60F2F602361424D832905_8BB23D43DE574E82F2BEE0DF0EC47EEB | der | |
MD5:653413033FA5D21D7CC91C51197EC1C0 | SHA256:1C84D61BB29FCE7C41249D162273565278A5A470F48B01977D613EF349868AB3 | |||
| 1324 | msiexec.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\8EC9B1D0ABBD7F98B401D425828828CE_93E8F0A6DF0B1F1414474691911362FC | der | |
MD5:47CDFD743BE7F61EABB54AD1FC592990 | SHA256:094BE78B821F4C3DBDB1ED052B7236ECF9D06DB821F1D58B7F5C04867092CA95 | |||
| 6828 | msiexec.exe | C:\Windows\Installer\MSI94A0.tmp | executable | |
MD5:88D29734F37BDCFFD202EAFCDD082F9D | SHA256:87C97269E2B68898BE87B884CD6A21880E6F15336B1194713E12A2DB45F1DCCF | |||
| 2192 | rundll32.exe | C:\Users\admin\AppData\Local\Temp\MSI920E.tmp-\Newtonsoft.Json.dll | executable | |
MD5:715A1FBEE4665E99E859EDA667FE8034 | SHA256:C5C83BBC1741BE6FF4C490C0AEE34C162945423EC577C646538B2D21CE13199E | |||
| 1324 | msiexec.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\C8E534EE129F27D55460CE17FD628216_1130D9B25898B0DB0D4F04DC5B93F141 | der | |
MD5:0F9272EA858E8F9AAC604C431F0BBDBB | SHA256:854DCDD86095C740EB1C4B1B5A0A87745AEA0BB0B1D98F7C9F0A70618F51DC05 | |||
| 3588 | rundll32.exe | C:\Users\admin\AppData\Local\Temp\MSI94A0.tmp-\AlphaControlAgentInstallation.dll | executable | |
MD5:AA1B9C5C685173FAD2DABEBEB3171F01 | SHA256:E44A6582CD3F84F4255D3C230E0A2C284E0CFFA0CA5E62E4D749E089555494C7 | |||
| 3588 | rundll32.exe | C:\Users\admin\AppData\Local\Temp\MSI94A0.tmp-\Microsoft.Deployment.WindowsInstaller.dll | executable | |
MD5:1A5CAEA6734FDD07CAA514C3F3FB75DA | SHA256:CF06D4ED4A8BAF88C82D6C9AE0EFC81C469DE6DA8788AB35F373B350A4B4CDCA | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
20
TCP/UDP connections
134
DNS requests
66
Threats
89
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
1324 | msiexec.exe | GET | 200 | 2.23.77.188:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBT3xL4LQLXDRDM9P665TW442vrsUQQUReuir%2FSSy4IxLVGLp6chnfNtyA8CEA6bGI750C3n79tQ4ghAGFo%3D | unknown | — | — | whitelisted |
1324 | msiexec.exe | GET | 200 | 2.23.77.188:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTfIs%2BLjDtGwQ09XEB1Yeq%2BtX%2BBgQQU7NfjgtJxXWRM3y5nP%2Be6mK4cD08CEAitQLJg0pxMn17Nqb2Trtk%3D | unknown | — | — | whitelisted |
2520 | svchost.exe | GET | 200 | 2.23.77.188:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
1324 | msiexec.exe | GET | 200 | 2.23.77.188:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSRXerF0eFeSWRripTgTkcJWMm7iQQUaDfg67Y7%2BF8Rhvv%2BYXsIiGX0TkICEAnTy%2FhDMohv9omwS69%2Fdow%3D | unknown | — | — | whitelisted |
4804 | SIHClient.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
5720 | AteraAgent.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTfIs%2BLjDtGwQ09XEB1Yeq%2BtX%2BBgQQU7NfjgtJxXWRM3y5nP%2Be6mK4cD08CEAitQLJg0pxMn17Nqb2Trtk%3D | unknown | — | — | whitelisted |
4804 | SIHClient.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
7072 | Agent.Package.Availability.exe | GET | 200 | 18.173.208.27:80 | http://ocsp.r2m01.amazontrust.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBShdVEFnSEQ0gG5CBtzM48cPMe9XwQUgbgOY4qJEhjl%2Bjs7UJWf5uWQE4UCEA4%2F%2F1d%2BlymNOgCTf4FzSko%3D | unknown | — | — | whitelisted |
7484 | msiexec.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTfIs%2BLjDtGwQ09XEB1Yeq%2BtX%2BBgQQU7NfjgtJxXWRM3y5nP%2Be6mK4cD08CEAitQLJg0pxMn17Nqb2Trtk%3D | unknown | — | — | whitelisted |
7668 | cscript.exe | GET | 200 | 2.16.241.19:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut_2010-06-23.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
5944 | MoUsoCoreWorker.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
1268 | svchost.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4544 | RUXIMICS.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
1324 | msiexec.exe | 2.23.77.188:80 | ocsp.digicert.com | AKAMAI-AS | DE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
2520 | svchost.exe | 20.190.160.128:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
2520 | svchost.exe | 2.23.77.188:80 | ocsp.digicert.com | AKAMAI-AS | DE | whitelisted |
2336 | svchost.exe | 172.211.123.249:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | FR | whitelisted |
1268 | svchost.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
login.live.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
go.microsoft.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
agent-api.atera.com |
| whitelisted |
nexusrules.officeapps.live.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
3588 | rundll32.exe | Potential Corporate Privacy Violation | POLICY [ANY.RUN] Possible Atera Remote Access Software Domain observed in TLS SNI (agent-api .atera .com) |
2032 | rundll32.exe | Potential Corporate Privacy Violation | POLICY [ANY.RUN] Possible Atera Remote Access Software Domain observed in TLS SNI (agent-api .atera .com) |
2032 | rundll32.exe | Potential Corporate Privacy Violation | POLICY [ANY.RUN] Possible Atera Remote Access Software Domain observed in TLS SNI (agent-api .atera .com) |
6320 | AteraAgent.exe | Potential Corporate Privacy Violation | POLICY [ANY.RUN] Possible Atera Remote Access Software Domain observed in TLS SNI (agent-api .atera .com) |
6320 | AteraAgent.exe | Potential Corporate Privacy Violation | POLICY [ANY.RUN] Possible Atera Remote Access Software Domain observed in TLS SNI (agent-api .atera .com) |
6532 | AgentPackageAgentInformation.exe | Potential Corporate Privacy Violation | POLICY [ANY.RUN] Possible Atera Remote Access Software Domain observed in TLS SNI (agent-api .atera .com) |
6532 | AgentPackageAgentInformation.exe | Potential Corporate Privacy Violation | POLICY [ANY.RUN] Possible Atera Remote Access Software Domain observed in TLS SNI (agent-api .atera .com) |
3624 | AgentPackageAgentInformation.exe | Potential Corporate Privacy Violation | POLICY [ANY.RUN] Possible Atera Remote Access Software Domain observed in TLS SNI (agent-api .atera .com) |
6320 | AteraAgent.exe | Potential Corporate Privacy Violation | POLICY [ANY.RUN] Possible Atera Remote Access Software Domain observed in TLS SNI (agent-api .atera .com) |
6320 | AteraAgent.exe | Potential Corporate Privacy Violation | POLICY [ANY.RUN] Possible Atera Remote Access Software Domain observed in TLS SNI (agent-api .atera .com) |
Process | Message |
|---|---|
AgentPackageMonitoring.exe | Native library pre-loader is trying to load native SQLite library "C:\Program Files (x86)\ATERA Networks\AteraAgent\Packages\AgentPackageMonitoring\x64\SQLite.Interop.dll"...
|
SplashtopStreamer.exe | [7364]2025-06-20 09:51:08 [CUtility::OSInfo] OS 10.0(19045) x64:1 (Last=0) |
SplashtopStreamer.exe | [7364]2025-06-20 09:51:08 [CUnPack::FindHeader] Name:C:\WINDOWS\TEMP\SplashtopStreamer.exe (Last=0) |
SplashtopStreamer.exe | [7364]2025-06-20 09:51:08 [CUnPack::FindHeader] Header offset:434176 (Last=183) |
SplashtopStreamer.exe | [7364]2025-06-20 09:51:08 [CUnPack::UnPackFiles] (1/5)UnPack file name:C:\WINDOWS\TEMP\unpack\setup.msi (63211520) (Last=0) |
SplashtopStreamer.exe | [7364]2025-06-20 09:51:08 [CUnPack::FindHeader] Sign Size:10440 (Last=0) |
SplashtopStreamer.exe | [7364]2025-06-20 09:51:08 [CUnPack::UnPackFiles] FreeSpace:232986484736 FileSize:63211520 (Last=0) |
SplashtopStreamer.exe | [7364]2025-06-20 09:51:08 [CUnPack::UnPackFiles] UnPack count:1 len:63211520 File:(null) (Last=0) |
SplashtopStreamer.exe | [7364]2025-06-20 09:51:08 [CUnPack::UnPackFiles] FreeSpace:232923254784 FileSize:1528 (Last=183) |
SplashtopStreamer.exe | [7364]2025-06-20 09:51:08 [CUnPack::UnPackFiles] FreeSpace:232923254784 FileSize:15 (Last=183) |