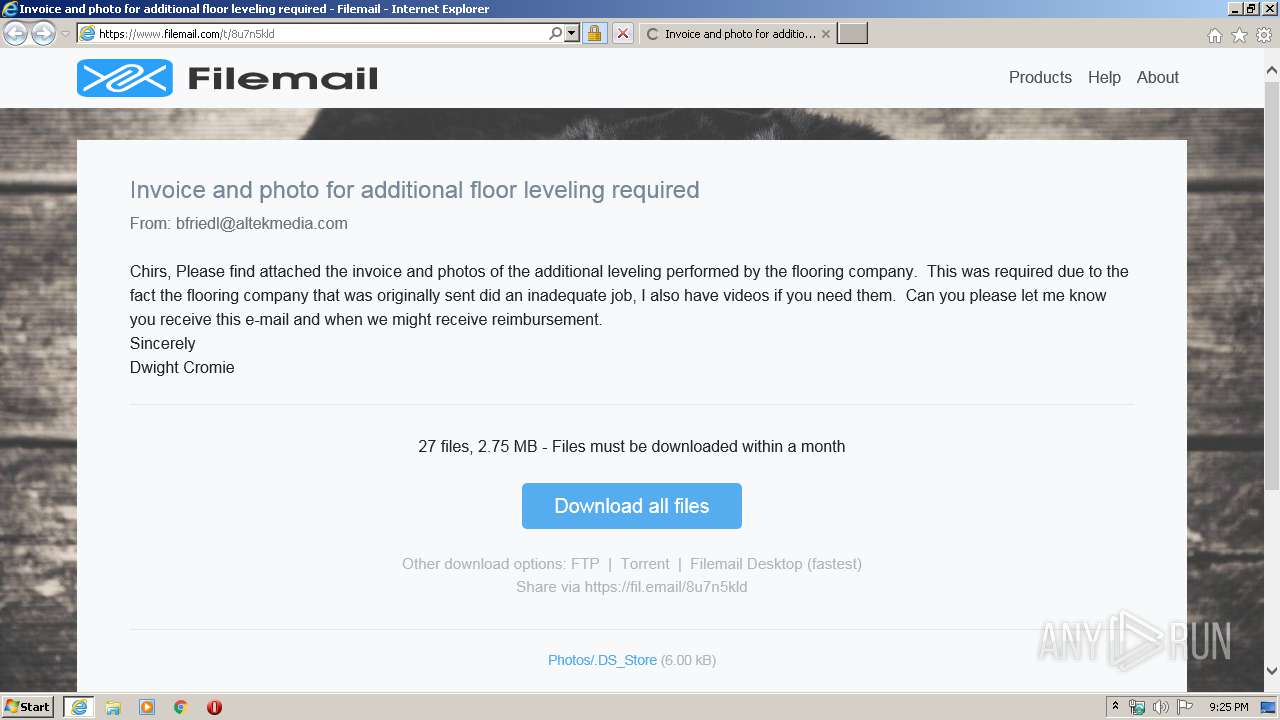
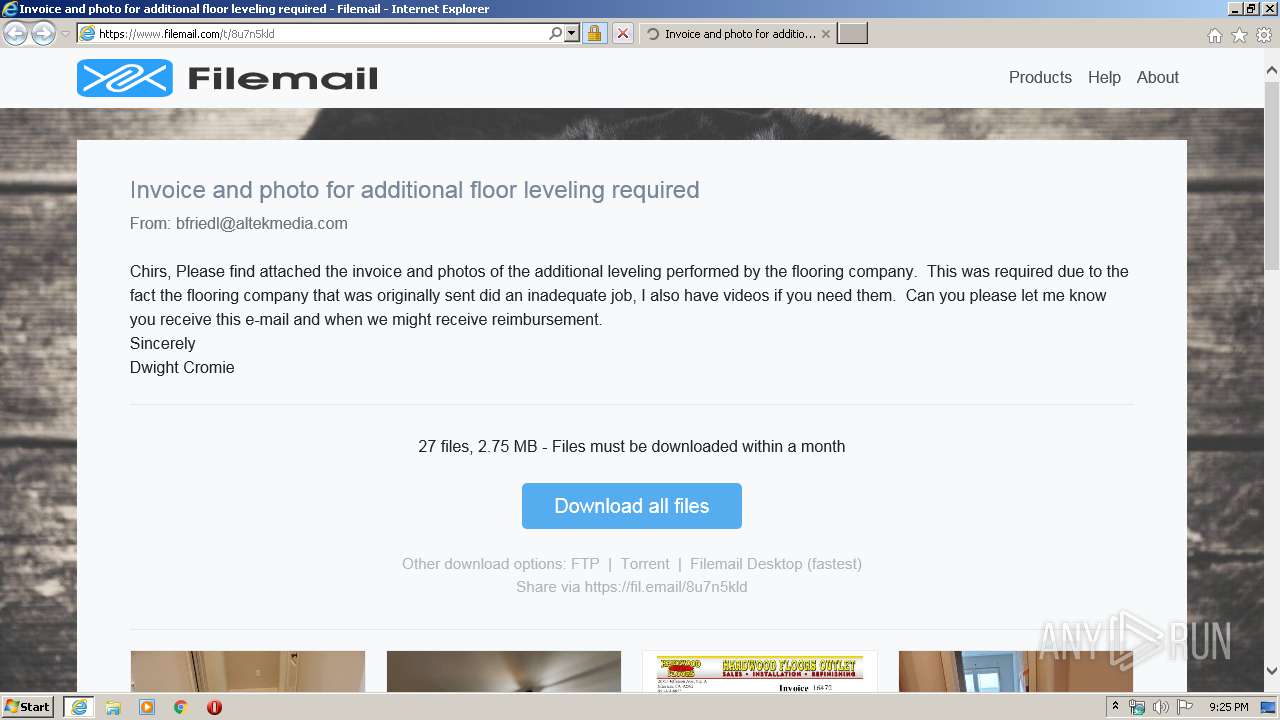
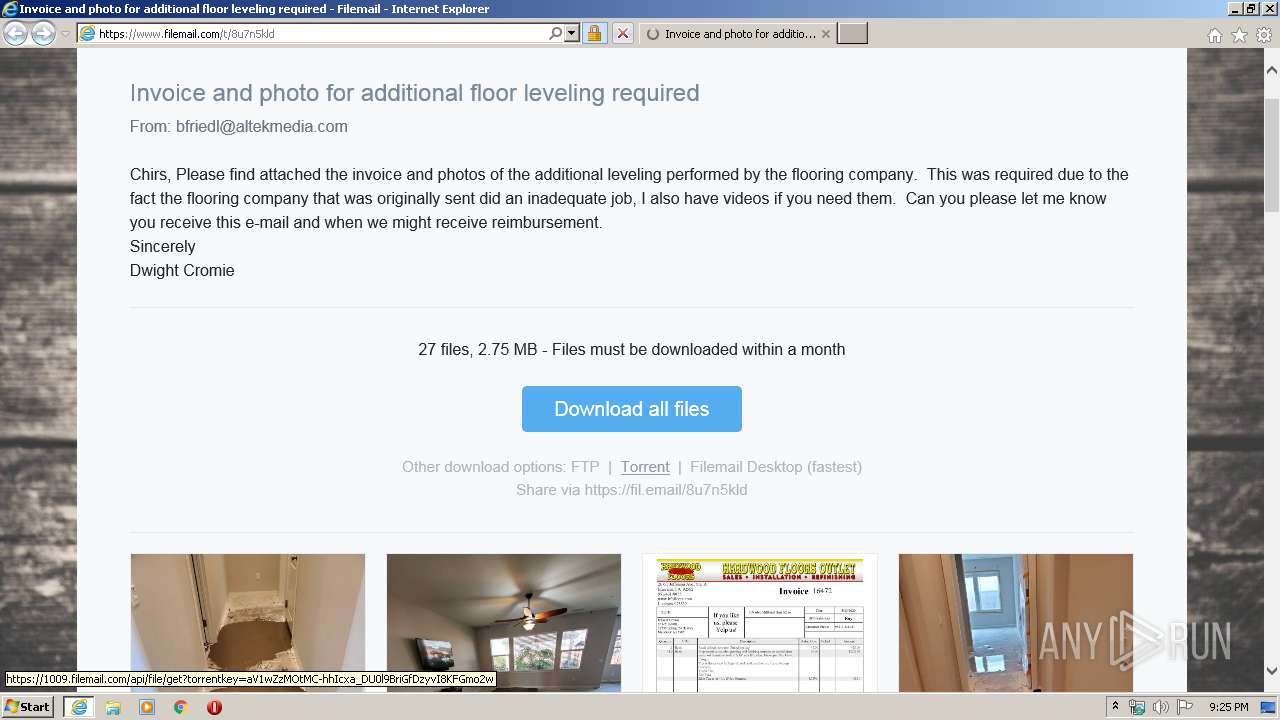
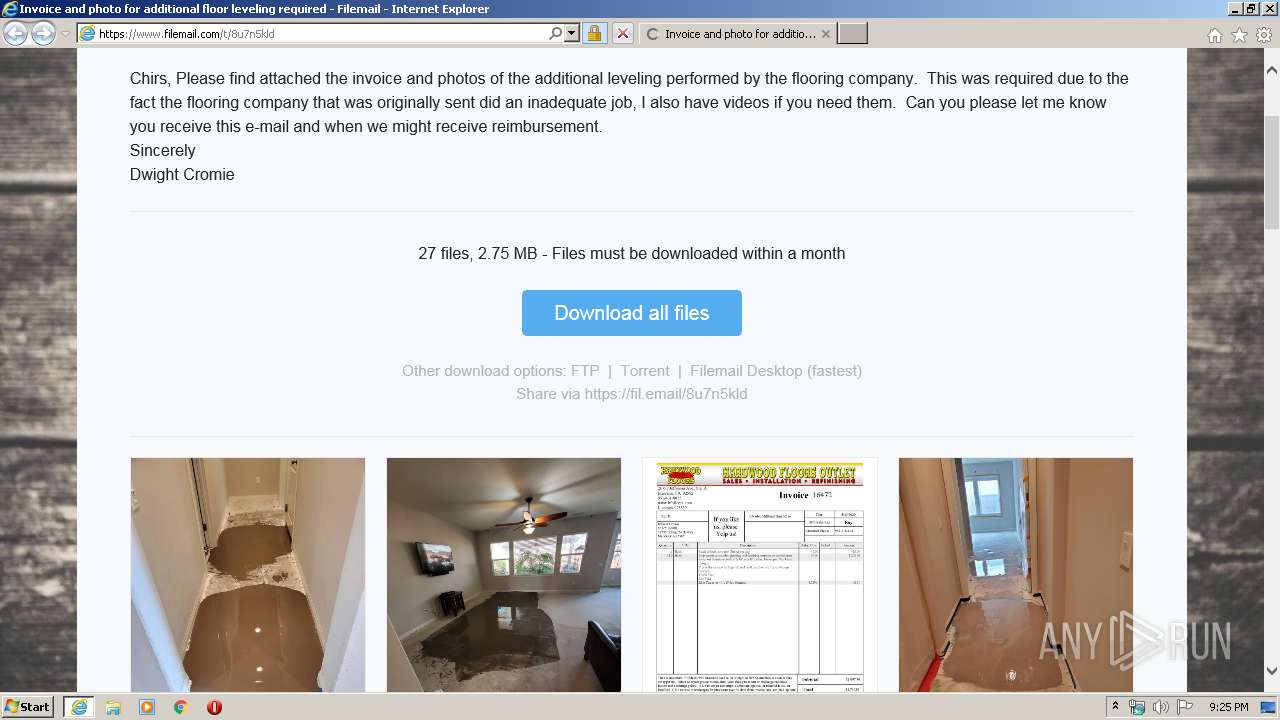
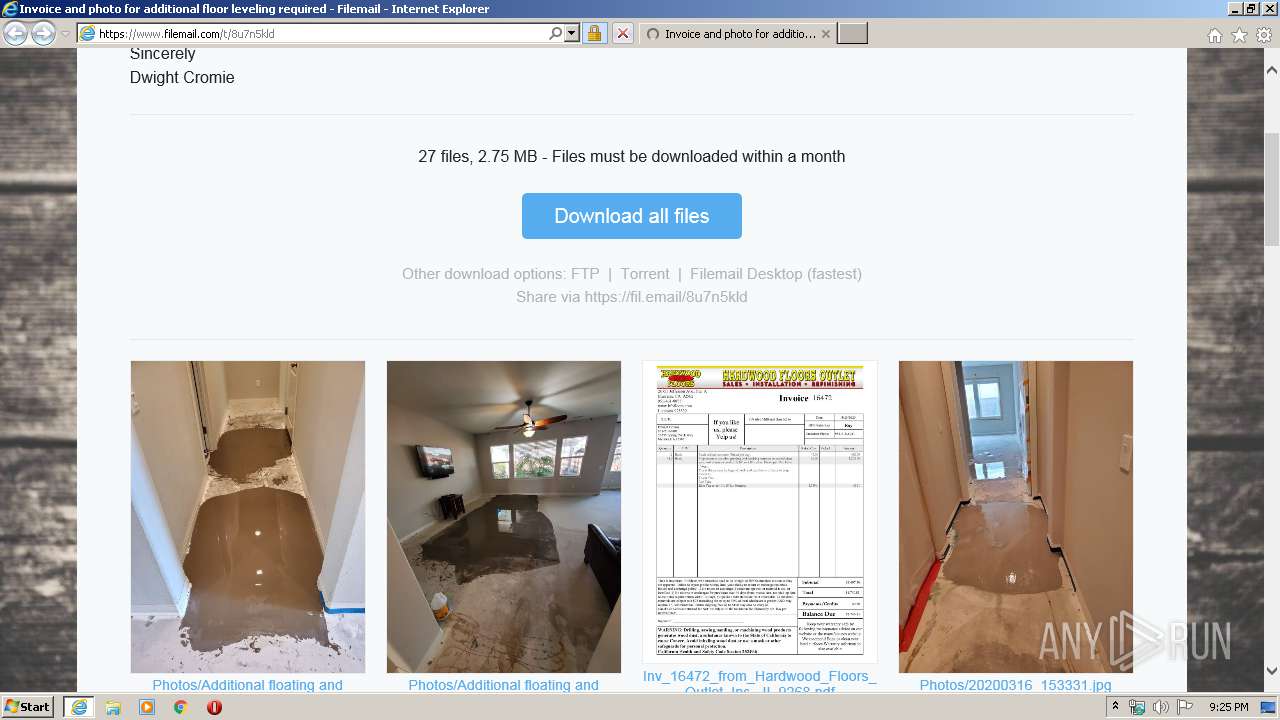
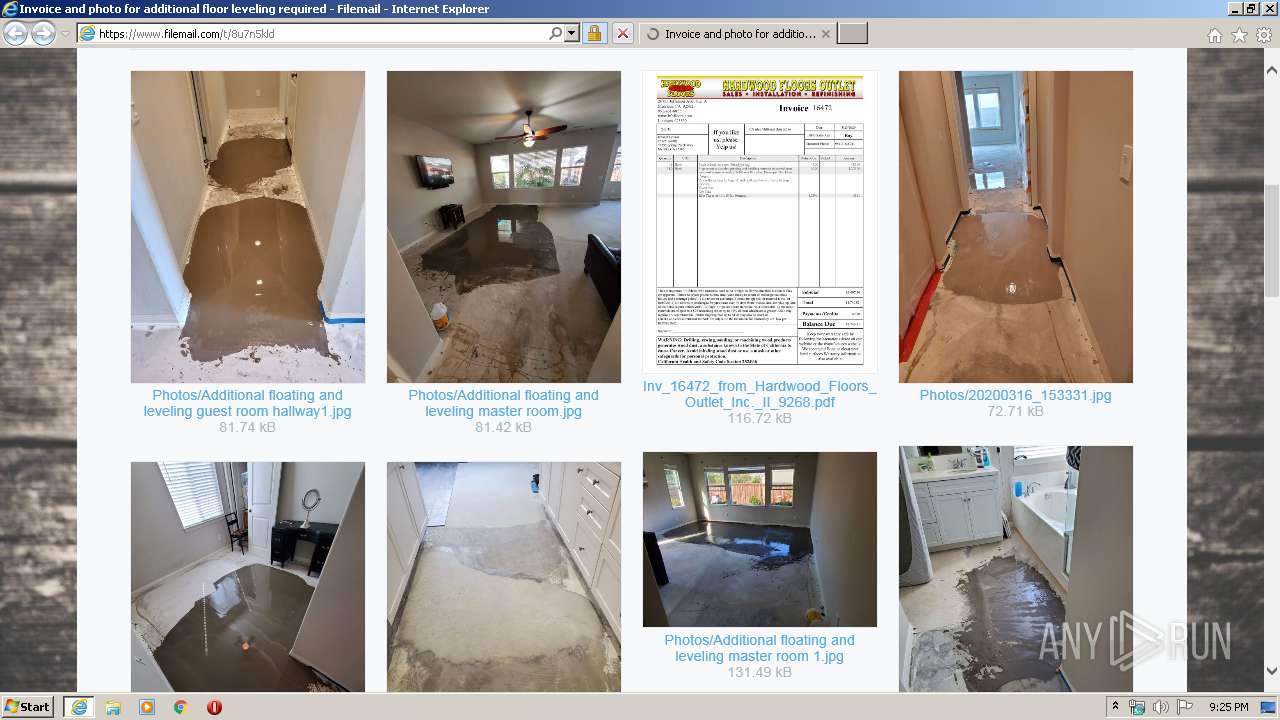
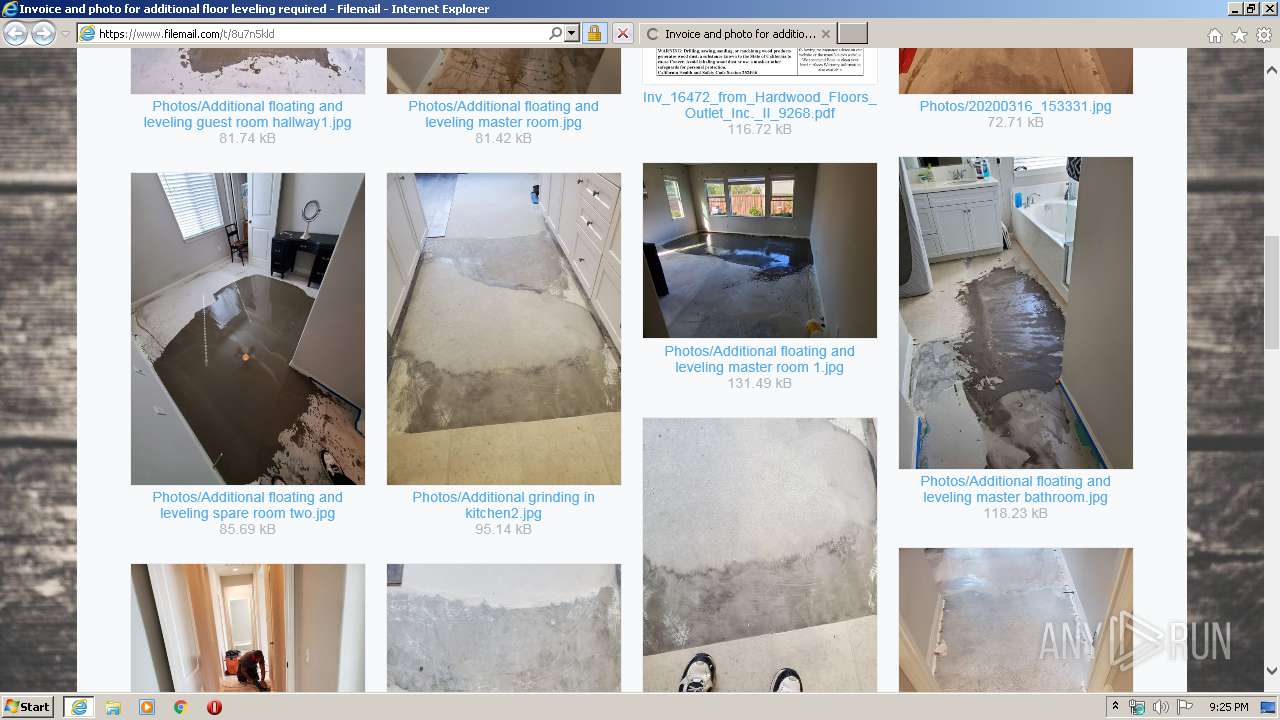
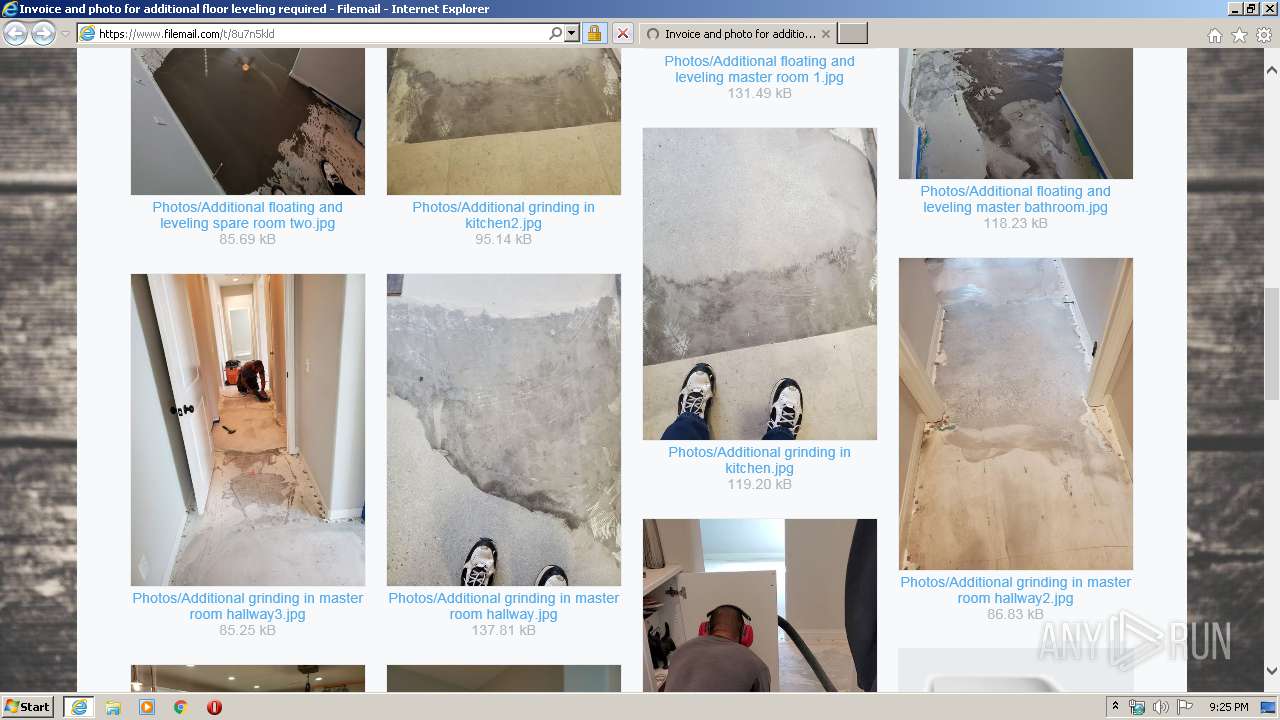
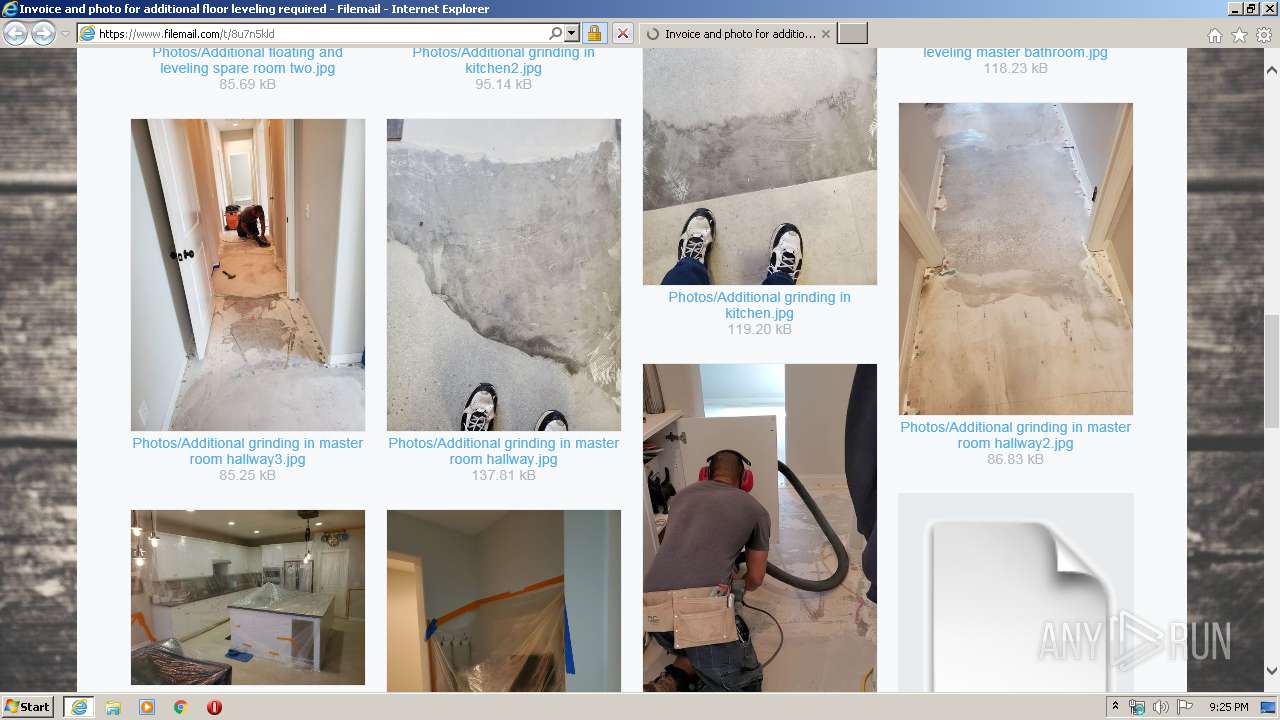
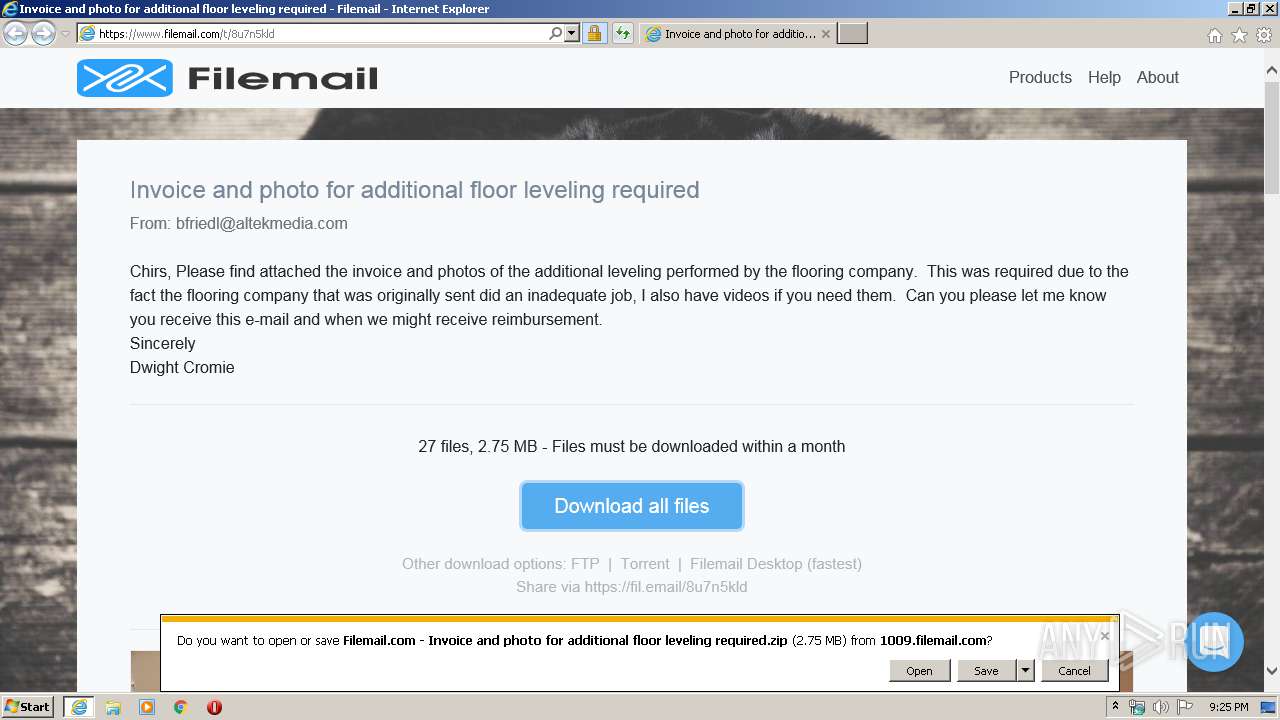
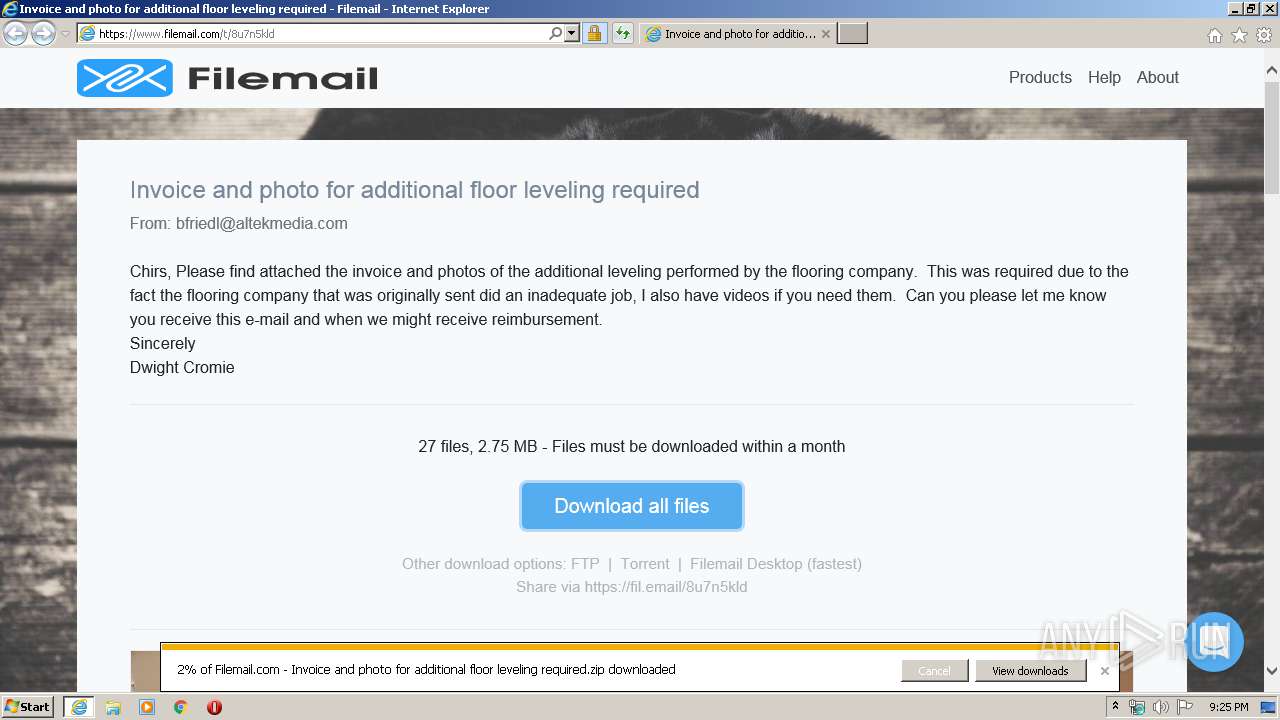
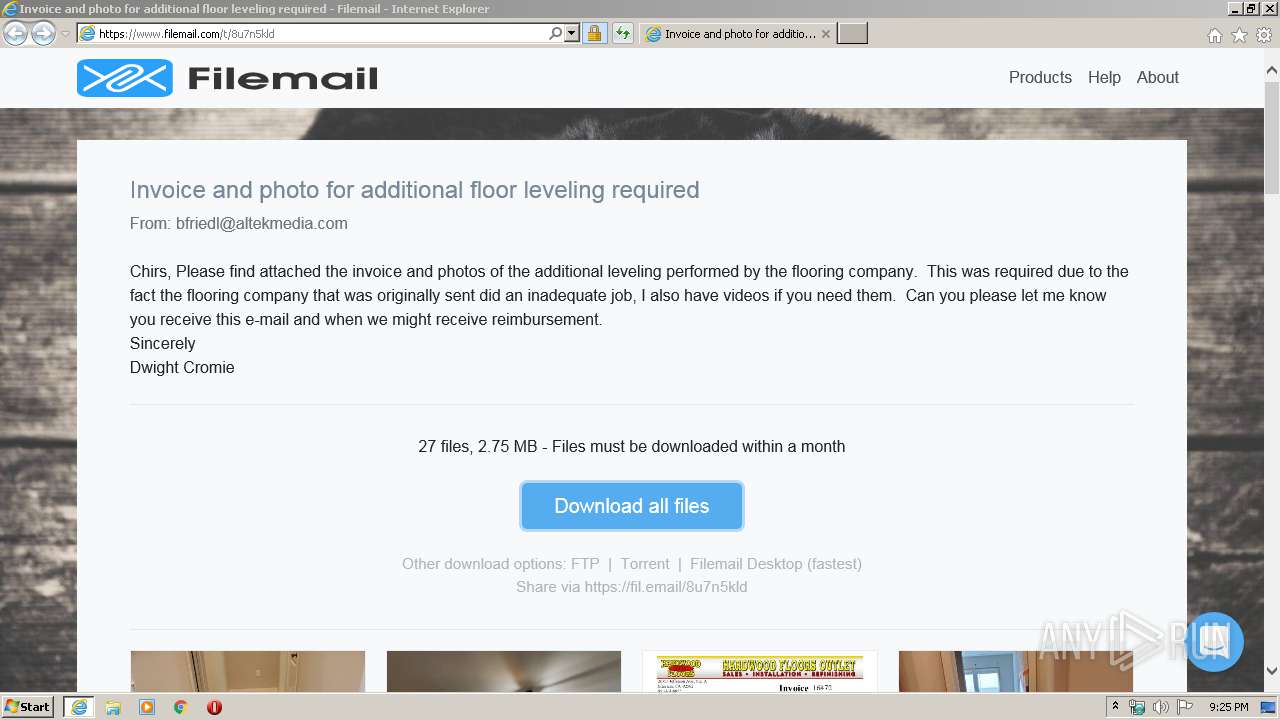
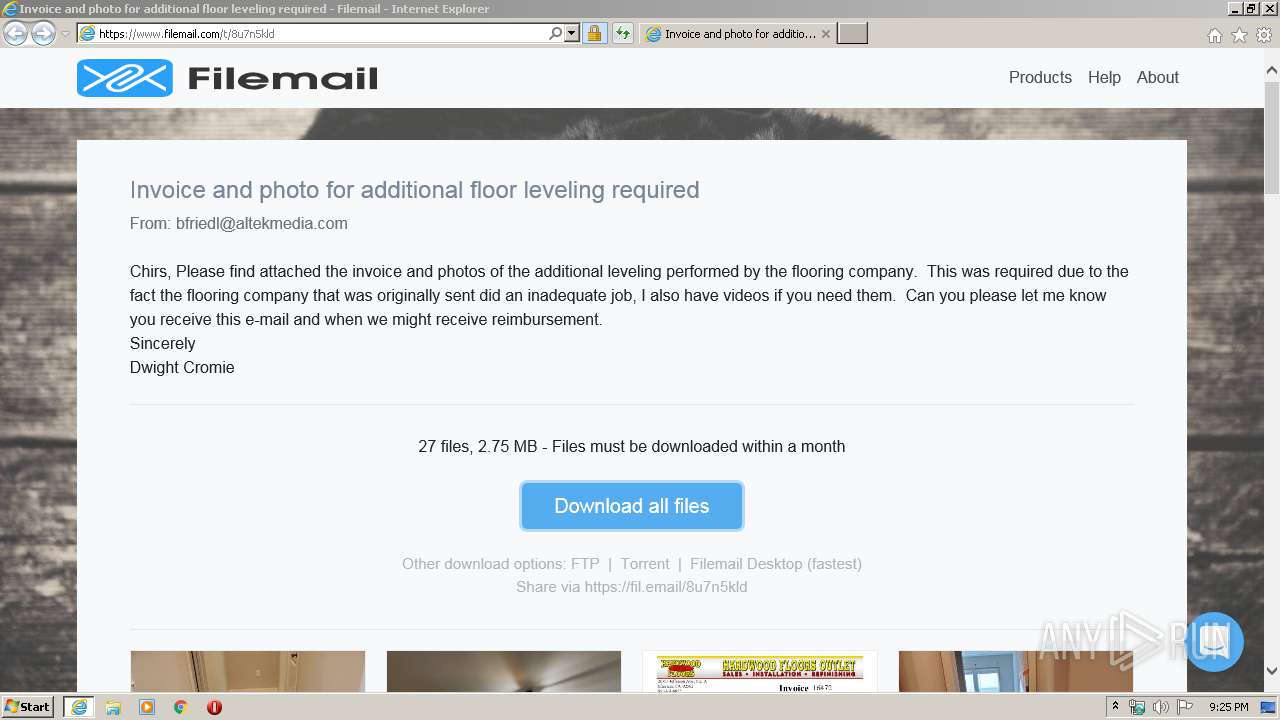
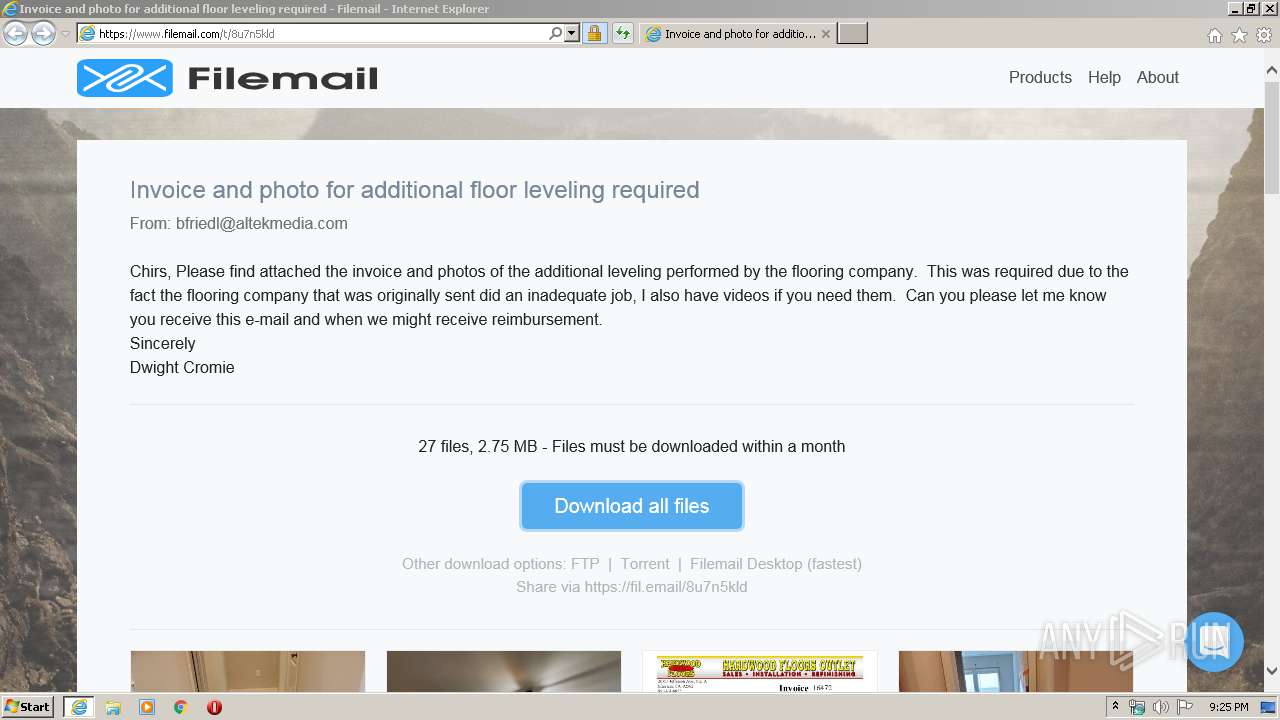
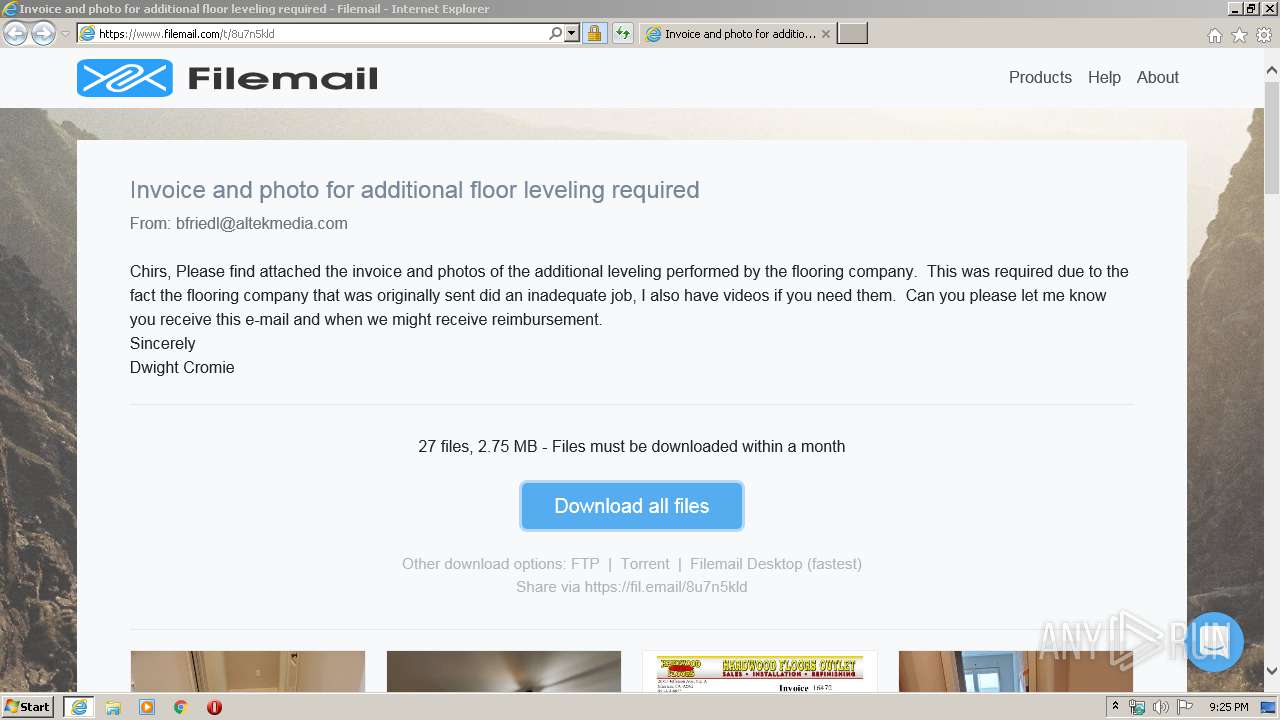
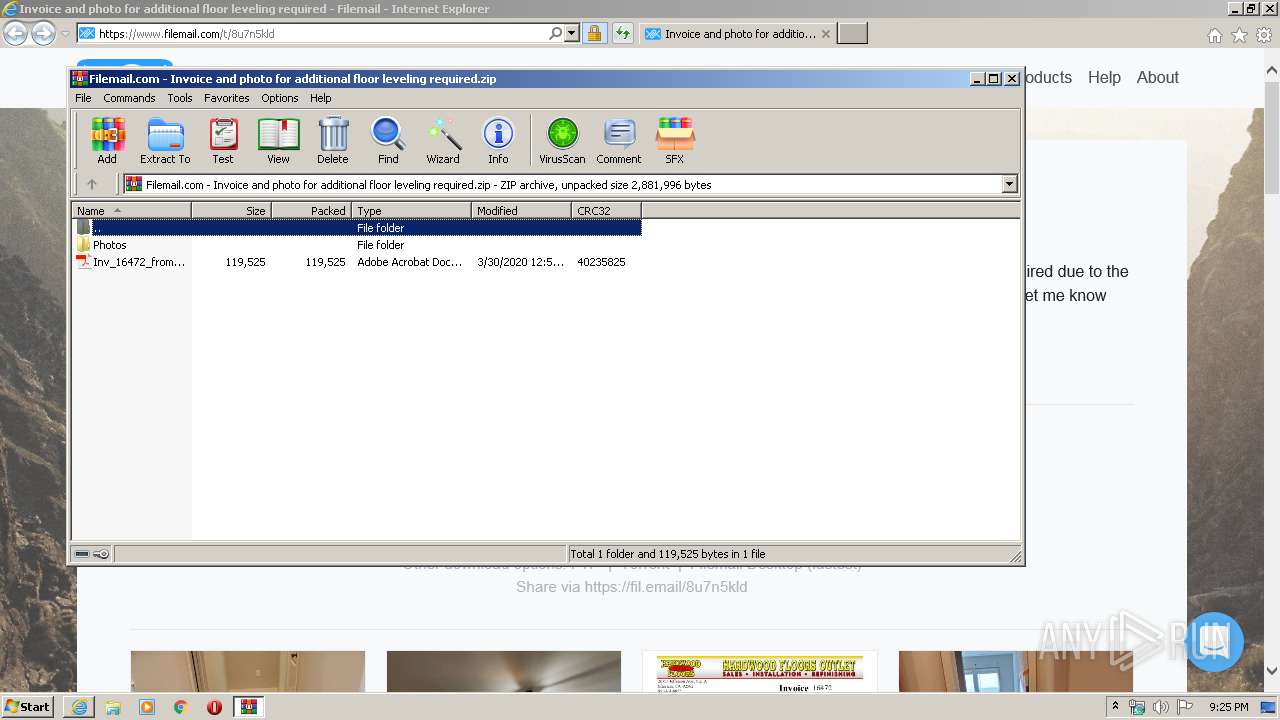
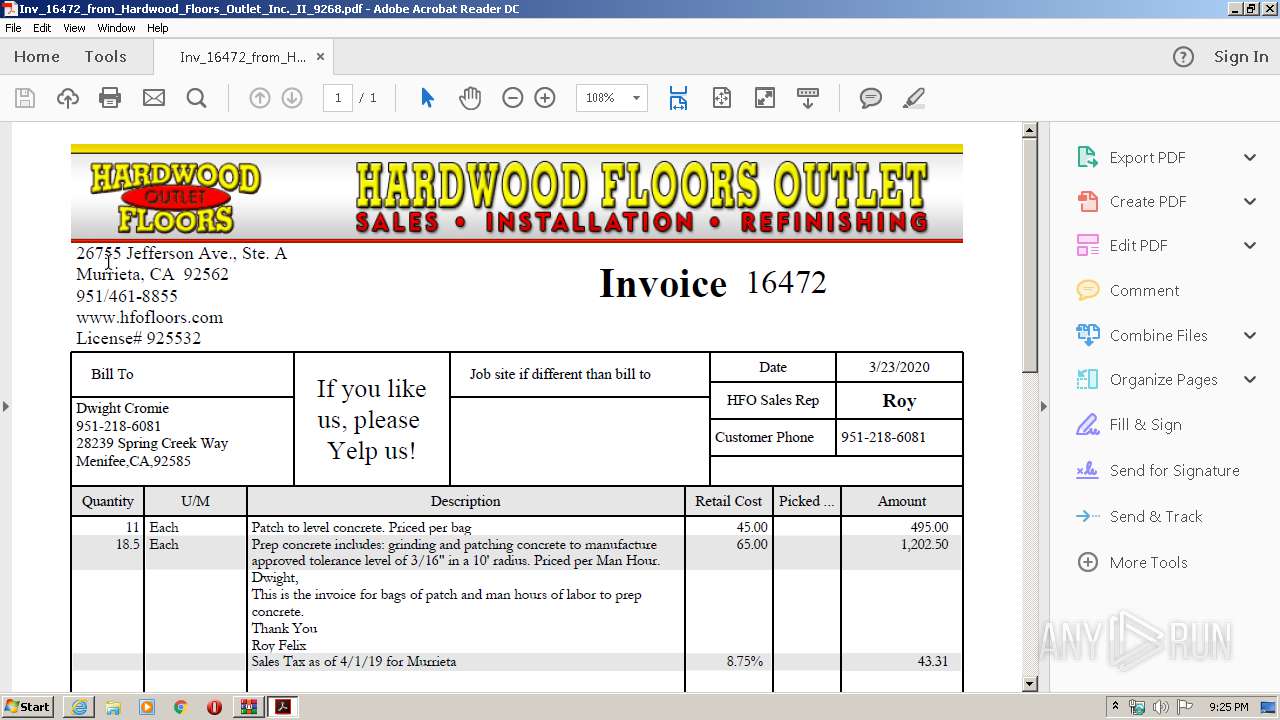
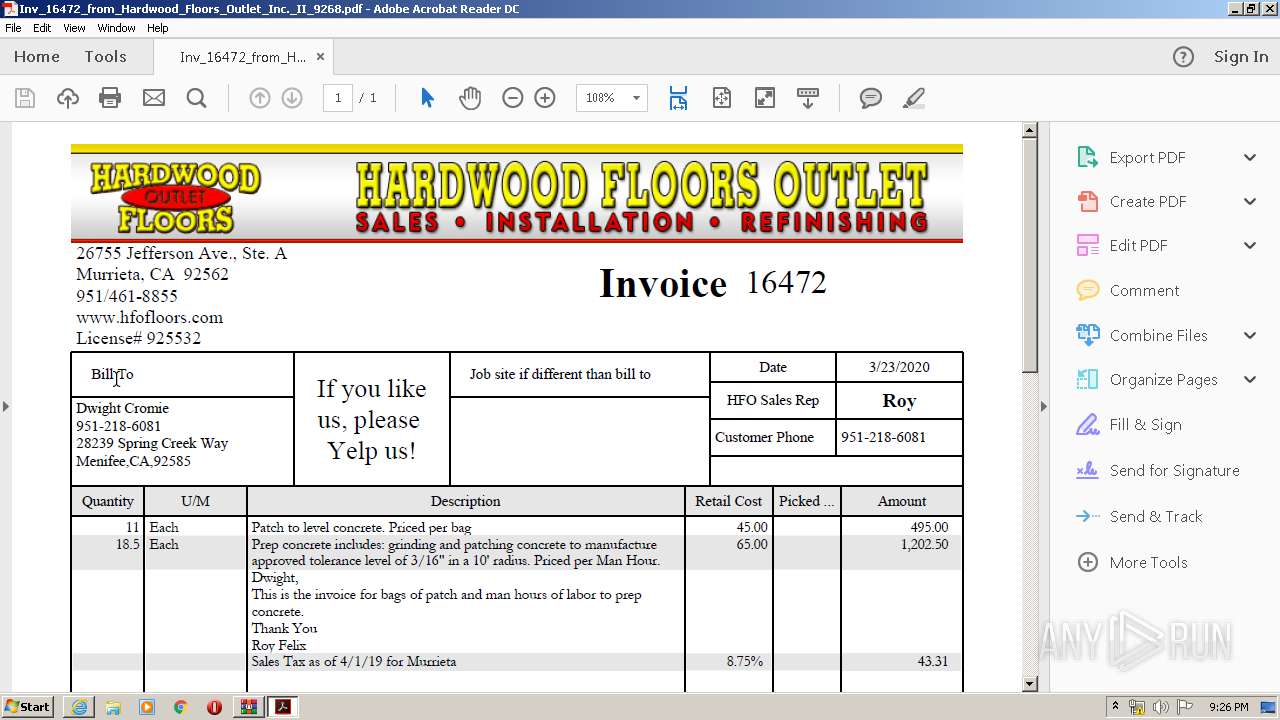
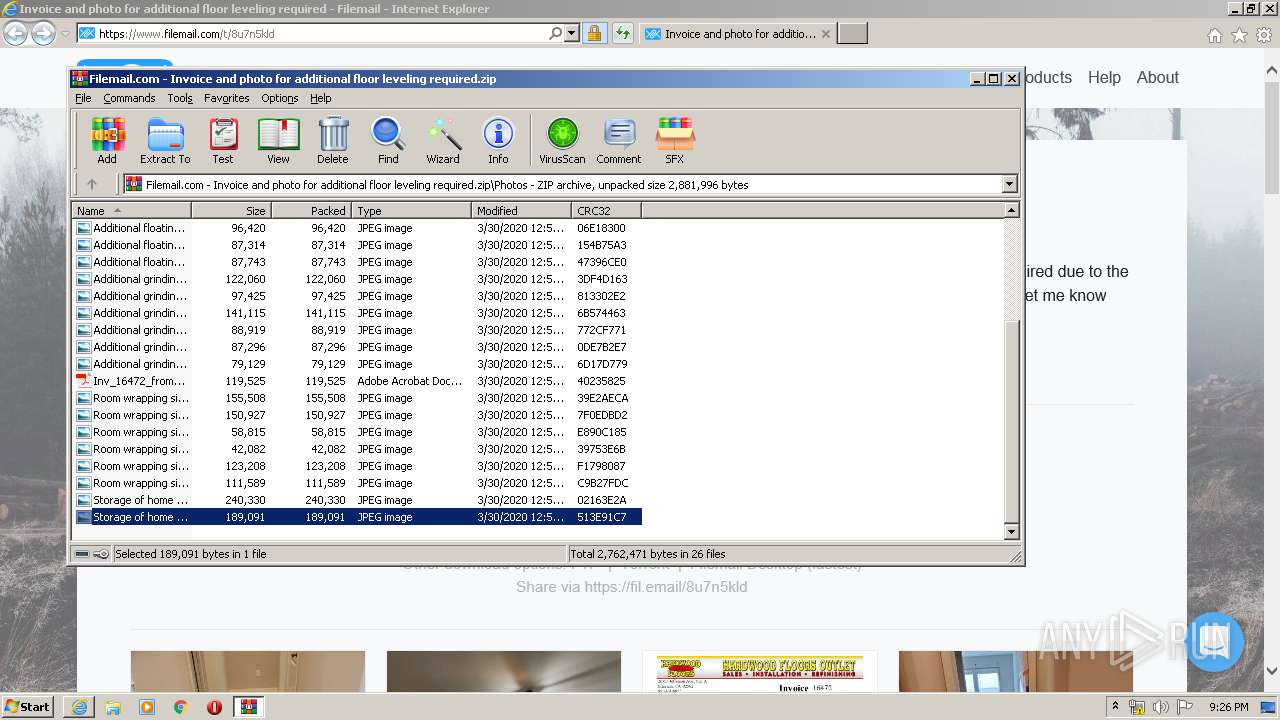
| URL: | https://fil.email/8u7n5kld |
| Full analysis: | https://app.any.run/tasks/c1b9dd03-d207-4d24-8376-b0faa2fb1994 |
| Verdict: | Malicious activity |
| Analysis date: | March 30, 2020, 20:24:48 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MD5: | 275ABD2FD6DD3AE0A4F29007BB276CBC |
| SHA1: | D9C7E3ACCEED871C3F789B7491994FFF152761FB |
| SHA256: | 8BF0F02FD0805DA4B51C31D37461B68B80284118BEC286CDDD2B0CC19D0C532A |
| SSDEEP: | 3:N8hIl0Hvn:2hS0P |
MALICIOUS
No malicious indicators.SUSPICIOUS
Changes IE settings (feature browser emulation)
- AcroRd32.exe (PID: 2652)
Executed via COM
- DllHost.exe (PID: 952)
- DllHost.exe (PID: 1872)
INFO
Changes internet zones settings
- iexplore.exe (PID: 2804)
Reads Internet Cache Settings
- iexplore.exe (PID: 2436)
- iexplore.exe (PID: 2804)
Application launched itself
- iexplore.exe (PID: 2804)
- AcroRd32.exe (PID: 2652)
- RdrCEF.exe (PID: 2192)
Reads settings of System Certificates
- iexplore.exe (PID: 2436)
- iexplore.exe (PID: 2804)
Modifies the phishing filter of IE
- iexplore.exe (PID: 2804)
Reads internet explorer settings
- iexplore.exe (PID: 2436)
Creates files in the user directory
- iexplore.exe (PID: 2804)
- iexplore.exe (PID: 2436)
Reads the hosts file
- RdrCEF.exe (PID: 2192)
Changes settings of System certificates
- iexplore.exe (PID: 2804)
Adds / modifies Windows certificates
- iexplore.exe (PID: 2804)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
45
Monitored processes
12
Malicious processes
0
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 952 | C:\Windows\system32\DllHost.exe /Processid:{76D0CB12-7604-4048-B83C-1005C7DDC503} | C:\Windows\system32\DllHost.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: COM Surrogate Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1872 | C:\Windows\system32\DllHost.exe /Processid:{76D0CB12-7604-4048-B83C-1005C7DDC503} | C:\Windows\system32\DllHost.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: COM Surrogate Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1888 | "C:\Program Files\Adobe\Acrobat Reader DC\Reader\AcroCEF\RdrCEF.exe" --type=renderer --disable-3d-apis --disable-databases --disable-direct-npapi-requests --disable-file-system --disable-notifications --disable-shared-workers --disable-direct-write --lang=en-US --lang=en-US --log-severity=disable --product-version="ReaderServices/15.23.20053 Chrome/45.0.2454.85" --device-scale-factor=1 --enable-delegated-renderer --num-raster-threads=2 --gpu-rasterization-msaa-sample-count=8 --content-image-texture-target=3553 --video-image-texture-target=3553 --disable-accelerated-video-decode --disable-webrtc-hw-encoding --disable-gpu-compositing --channel="2192.0.367363977\974776538" --allow-no-sandbox-job /prefetch:673131151 | C:\Program Files\Adobe\Acrobat Reader DC\Reader\AcroCEF\RdrCEF.exe | — | RdrCEF.exe | |||||||||||
User: admin Company: Adobe Systems Incorporated Integrity Level: LOW Description: Adobe RdrCEF Exit code: 0 Version: 15.23.20053.211670 Modules
| |||||||||||||||
| 2192 | "C:\Program Files\Adobe\Acrobat Reader DC\Reader\AcroCEF\RdrCEF.exe" --backgroundcolor=16448250 | C:\Program Files\Adobe\Acrobat Reader DC\Reader\AcroCEF\RdrCEF.exe | — | AcroRd32.exe | |||||||||||
User: admin Company: Adobe Systems Incorporated Integrity Level: MEDIUM Description: Adobe RdrCEF Exit code: 3221225547 Version: 15.23.20053.211670 Modules
| |||||||||||||||
| 2436 | "C:\Program Files\Internet Explorer\iexplore.exe" SCODEF:2804 CREDAT:267521 /prefetch:2 | C:\Program Files\Internet Explorer\iexplore.exe | iexplore.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Internet Explorer Exit code: 0 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
| 2528 | "C:\Program Files\Adobe\Acrobat Reader DC\Reader\AcroCEF\RdrCEF.exe" --type=renderer --disable-3d-apis --disable-databases --disable-direct-npapi-requests --disable-file-system --disable-notifications --disable-shared-workers --disable-direct-write --lang=en-US --lang=en-US --log-severity=disable --product-version="ReaderServices/15.23.20053 Chrome/45.0.2454.85" --device-scale-factor=1 --enable-delegated-renderer --num-raster-threads=2 --gpu-rasterization-msaa-sample-count=8 --content-image-texture-target=3553 --video-image-texture-target=3553 --disable-accelerated-video-decode --disable-webrtc-hw-encoding --disable-gpu-compositing --channel="2192.1.1061140875\331760380" --allow-no-sandbox-job /prefetch:673131151 | C:\Program Files\Adobe\Acrobat Reader DC\Reader\AcroCEF\RdrCEF.exe | — | RdrCEF.exe | |||||||||||
User: admin Company: Adobe Systems Incorporated Integrity Level: LOW Description: Adobe RdrCEF Exit code: 0 Version: 15.23.20053.211670 Modules
| |||||||||||||||
| 2652 | "C:\Program Files\Adobe\Acrobat Reader DC\Reader\AcroRd32.exe" "C:\Users\admin\AppData\Local\Temp\Rar$DIa3696.28134\Inv_16472_from_Hardwood_Floors_Outlet_Inc._II_9268.pdf" | C:\Program Files\Adobe\Acrobat Reader DC\Reader\AcroRd32.exe | — | WinRAR.exe | |||||||||||
User: admin Company: Adobe Systems Incorporated Integrity Level: MEDIUM Description: Adobe Acrobat Reader DC Exit code: 1 Version: 15.23.20070.215641 Modules
| |||||||||||||||
| 2804 | "C:\Program Files\Internet Explorer\iexplore.exe" https://fil.email/8u7n5kld | C:\Program Files\Internet Explorer\iexplore.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Internet Explorer Exit code: 0 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
| 2908 | "C:\Program Files\Adobe\Acrobat Reader DC\Reader\AcroRd32.exe" --type=renderer "C:\Users\admin\AppData\Local\Temp\Rar$DIa3696.30422\Inv_16472_from_Hardwood_Floors_Outlet_Inc._II_9268.pdf" | C:\Program Files\Adobe\Acrobat Reader DC\Reader\AcroRd32.exe | — | AcroRd32.exe | |||||||||||
User: admin Company: Adobe Systems Incorporated Integrity Level: LOW Description: Adobe Acrobat Reader DC Exit code: 1 Version: 15.23.20070.215641 Modules
| |||||||||||||||
| 3384 | "C:\Program Files\Adobe\Acrobat Reader DC\Reader\AcroRd32.exe" --type=renderer "C:\Users\admin\AppData\Local\Temp\Rar$DIa3696.28134\Inv_16472_from_Hardwood_Floors_Outlet_Inc._II_9268.pdf" | C:\Program Files\Adobe\Acrobat Reader DC\Reader\AcroRd32.exe | — | AcroRd32.exe | |||||||||||
User: admin Company: Adobe Systems Incorporated Integrity Level: LOW Description: Adobe Acrobat Reader DC Exit code: 1 Version: 15.23.20070.215641 Modules
| |||||||||||||||
Total events
7 240
Read events
1 802
Write events
3 720
Delete events
1 718
Modification events
| (PID) Process: | (2804) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\UrlBlockManager |
| Operation: | write | Name: | NextCheckForUpdateLowDateTime |
Value: 1574461410 | |||
| (PID) Process: | (2804) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\UrlBlockManager |
| Operation: | write | Name: | NextCheckForUpdateHighDateTime |
Value: 30803665 | |||
| (PID) Process: | (2804) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Content |
| Operation: | write | Name: | CachePrefix |
Value: | |||
| (PID) Process: | (2804) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (2804) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
| (PID) Process: | (2804) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\Main |
| Operation: | write | Name: | CompatibilityFlags |
Value: 0 | |||
| (PID) Process: | (2804) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings |
| Operation: | write | Name: | ProxyEnable |
Value: 0 | |||
| (PID) Process: | (2804) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\Connections |
| Operation: | write | Name: | SavedLegacySettings |
Value: 46000000A1000000010000000000000000000000000000000000000000000000C0E333BBEAB1D301000000000000000000000000020000001700000000000000FE800000000000007D6CB050D9C573F70B000000000000006D00330032005C004D00530049004D004700330032002E0064006C000100000004AA400014AA4000040000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000002000000C0A8016400000000000000000000000000000000000000000800000000000000805D3F00983740000008000002000000000000600000002060040000B8A94000020000008802000060040000B8A9400004000000F8010000B284000088B64000B84B400043003A000000000000000000000000000000000000000000 | |||
| (PID) Process: | (2804) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 0 | |||
| (PID) Process: | (2804) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 1 | |||
Executable files
0
Suspicious files
58
Text files
95
Unknown types
39
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2436 | iexplore.exe | C:\Users\admin\AppData\Local\Temp\Low\Cab717F.tmp | — | |
MD5:— | SHA256:— | |||
| 2436 | iexplore.exe | C:\Users\admin\AppData\Local\Temp\Low\Tar7180.tmp | — | |
MD5:— | SHA256:— | |||
| 2804 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\Internet Explorer\Services\search_{0633EE93-D776-472f-A0FF-E1416B8B2E3A}.ico | — | |
MD5:— | SHA256:— | |||
| 2436 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\1BB09BEEC155258835C193A7AA85AA5B_3FF795DBF505EC432A7895C84CFB04D5 | der | |
MD5:— | SHA256:— | |||
| 2436 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\5080DC7A65DB6A5960ECD874088F3328_6CBA2C06D5985DD95AE59AF8FC7C6220 | binary | |
MD5:— | SHA256:— | |||
| 2436 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\5457A8CE4B2A7499F8299A013B6E1C7C_CE50F893881D43DC0C815E4D80FAF2B4 | der | |
MD5:— | SHA256:— | |||
| 2436 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\5457A8CE4B2A7499F8299A013B6E1C7C_CE50F893881D43DC0C815E4D80FAF2B4 | binary | |
MD5:— | SHA256:— | |||
| 2436 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\DY534W2X\logo-horiz[1].svg | image | |
MD5:— | SHA256:— | |||
| 2436 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\MFAQUS6V\8u7n5kld[1].htm | html | |
MD5:— | SHA256:— | |||
| 2436 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\YTOWV792\logo[1].svg | image | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
24
TCP/UDP connections
91
DNS requests
31
Threats
3
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
2436 | iexplore.exe | GET | 200 | 13.35.254.57:80 | http://ocsp.rootca1.amazontrust.com/MFQwUjBQME4wTDAJBgUrDgMCGgUABBRPWaOUU8%2B5VZ5%2Fa9jFTaU9pkK3FAQUhBjMhTTsvAyUlC4IWZzHshBOCggCEwZ%2FlFeFh%2Bisd96yUzJbvJmLVg0%3D | US | der | 1.39 Kb | shared |
2436 | iexplore.exe | GET | 200 | 143.204.208.165:80 | http://o.ss2.us//MEowSDBGMEQwQjAJBgUrDgMCGgUABBSLwZ6EW5gdYc9UaSEaaLjjETNtkAQUv1%2B30c7dH4b0W1Ws3NcQwg6piOcCCQCnDkpMNIK3fw%3D%3D | US | der | 1.70 Kb | whitelisted |
2436 | iexplore.exe | GET | 200 | 151.139.128.14:80 | http://ocsp.comodoca.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBReAhtobFzTvhaRmVeJ38QUchY9AwQUu69%2BAj36pvE8hI6t7jiY7NkyMtQCECsuburZdTZsFIpu26N8jAc%3D | US | der | 727 b | whitelisted |
2436 | iexplore.exe | GET | 200 | 13.35.254.57:80 | http://ocsp.rootg2.amazontrust.com/MFQwUjBQME4wTDAJBgUrDgMCGgUABBSIfaREXmfqfJR3TkMYnD7O5MhzEgQUnF8A36oB1zArOIiiuG1KnPIRkYMCEwZ%2FlEoqJ83z%2BsKuKwH5CO65xMY%3D | US | der | 1.51 Kb | whitelisted |
2436 | iexplore.exe | GET | 200 | 151.139.128.14:80 | http://ocsp.usertrust.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBR8sWZUnKvbRO5iJhat9GV793rVlAQUrb2YejS0Jvf6xCZU7wO94CTLVBoCECdm7lbrSfOOq9dwovyE3iI%3D | US | der | 471 b | whitelisted |
2436 | iexplore.exe | GET | 200 | 172.217.16.131:80 | http://crl.pki.goog/gsr2/gsr2.crl | US | der | 950 b | whitelisted |
2436 | iexplore.exe | GET | 200 | 151.139.128.14:80 | http://ocsp.comodoca.com/MFIwUDBOMEwwSjAJBgUrDgMCGgUABBR64T7ooMQqLLQoy%2BemBUYZQOKh6QQUkK9qOpRaC9iQ6hJWc99DtDoo2ucCEQDDQHQviyD1bZds7moI6tz3 | US | der | 472 b | whitelisted |
2436 | iexplore.exe | GET | 200 | 172.217.16.131:80 | http://crl.pki.goog/gsr2/gsr2.crl | US | der | 950 b | whitelisted |
2436 | iexplore.exe | GET | 200 | 172.217.16.131:80 | http://ocsp.pki.goog/gts1o1/MFEwTzBNMEswSTAJBgUrDgMCGgUABBRCRjDCJxnb3nDwj%2Fxz5aZfZjgXvAQUmNH4bhDrz5vsYJ8YkBug630J%2FSsCEFeh1L3VO0beCAAAAAAyCgc%3D | US | der | 471 b | whitelisted |
2436 | iexplore.exe | GET | 200 | 172.217.16.131:80 | http://crl.pki.goog/gsr2/gsr2.crl | US | der | 950 b | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
2436 | iexplore.exe | 5.178.64.4:443 | fil.email | Serverius Holding B.V. | NL | unknown |
2436 | iexplore.exe | 5.178.64.6:443 | fil.email | Serverius Holding B.V. | NL | suspicious |
2804 | iexplore.exe | 204.79.197.200:80 | www.bing.com | Microsoft Corporation | US | whitelisted |
2436 | iexplore.exe | 172.217.16.164:443 | www.google.com | Google Inc. | US | whitelisted |
2436 | iexplore.exe | 172.217.16.131:80 | ocsp.pki.goog | Google Inc. | US | whitelisted |
2436 | iexplore.exe | 23.237.188.42:443 | 1009.filemail.com | Cogent Communications | US | unknown |
2436 | iexplore.exe | 157.240.20.19:443 | connect.facebook.net | Facebook, Inc. | US | whitelisted |
2436 | iexplore.exe | 216.58.206.14:443 | www.google-analytics.com | Google Inc. | US | whitelisted |
2804 | iexplore.exe | 5.178.64.6:443 | fil.email | Serverius Holding B.V. | NL | suspicious |
2436 | iexplore.exe | 93.184.220.29:80 | ocsp.digicert.com | MCI Communications Services, Inc. d/b/a Verizon Business | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
fil.email |
| whitelisted |
ocsp.comodoca.com |
| whitelisted |
www.filemail.com |
| unknown |
api.bing.com |
| whitelisted |
www.bing.com |
| whitelisted |
ocsp.usertrust.com |
| whitelisted |
www.googletagmanager.com |
| whitelisted |
www.google.com |
| malicious |
ocsp.pki.goog |
| whitelisted |
1009.filemail.com |
| unknown |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2436 | iexplore.exe | Potentially Bad Traffic | ET INFO TLS Handshake Failure |
2436 | iexplore.exe | Potentially Bad Traffic | ET INFO TLS Handshake Failure |
2436 | iexplore.exe | Potentially Bad Traffic | ET INFO TLS Handshake Failure |