| File name: | sqlite3.dll |
| Full analysis: | https://app.any.run/tasks/e4c54c9d-12fd-477f-8cbb-a20f8fb98912 |
| Verdict: | Malicious activity |
| Analysis date: | November 28, 2023, 08:27:29 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (DLL) (console) Intel 80386, for MS Windows |
| MD5: | 2BA363CB9C8ECA112DAA44CFB567E91E |
| SHA1: | 37AF542FE44A189FB7EFB1702D567E516ABDFFFB |
| SHA256: | 8BE3304FEC9D41D44012213DDBB28980D2570EDEEF3523B909AF2F97768A8D85 |
| SSDEEP: | 24576:ytXHPNHm9np5saIFYNDhDuLBEXiDcU/c4VTPXcjhYeUvubmbzjLY63:IXHPNHm9np5saIFYNDhDuLBEXiDcU/cC |
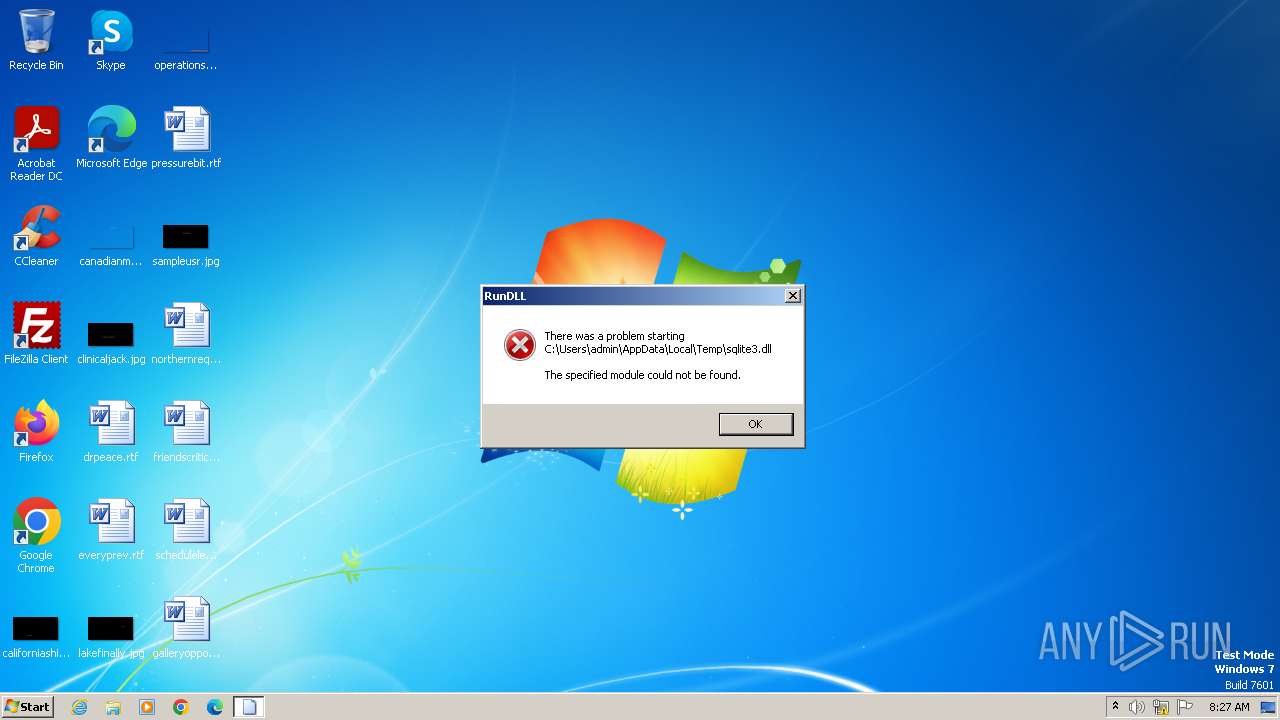
MALICIOUS
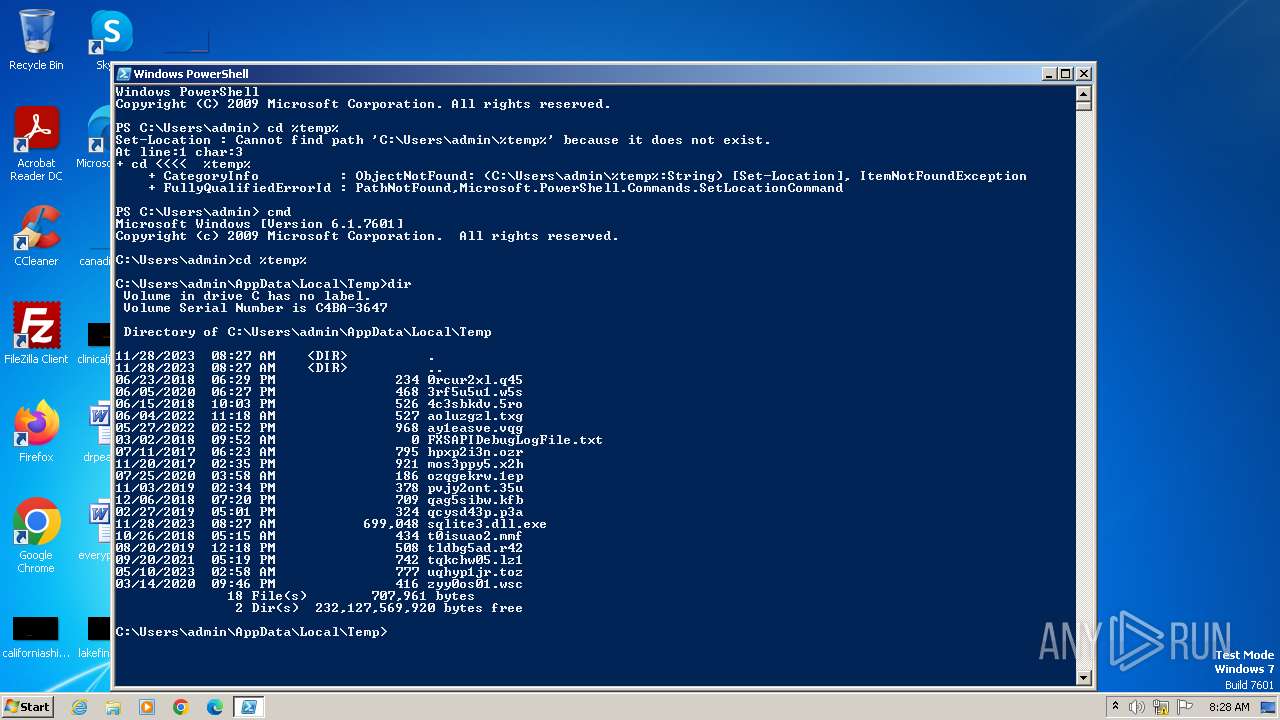
Drops the executable file immediately after the start
- cmd.exe (PID: 1668)
SUSPICIOUS
Powershell version downgrade attack
- powershell.exe (PID: 2168)
Starts CMD.EXE for commands execution
- powershell.exe (PID: 2168)
Process drops SQLite DLL files
- cmd.exe (PID: 1668)
INFO
Manual execution by a user
- powershell.exe (PID: 2168)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win64 Executable (generic) (64.6) |
|---|---|---|
| .dll | | | Win32 Dynamic Link Library (generic) (15.3) |
| .exe | | | Win32 Executable (generic) (10.5) |
| .exe | | | Generic Win/DOS Executable (4.6) |
| .exe | | | DOS Executable Generic (4.6) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2015:07:29 22:08:18+02:00 |
| ImageFileCharacteristics: | Executable, No line numbers, 32-bit, DLL |
| PEType: | PE32 |
| LinkerVersion: | 2.21 |
| CodeSize: | 473088 |
| InitializedDataSize: | 549376 |
| UninitializedDataSize: | 1536 |
| EntryPoint: | 0x1058 |
| OSVersion: | 4 |
| ImageVersion: | 1 |
| SubsystemVersion: | 4 |
| Subsystem: | Windows command line |
| FileVersionNumber: | 3.8.11.1 |
| ProductVersionNumber: | 3.8.11.1 |
| FileFlagsMask: | 0x003f |
| FileFlags: | (none) |
| FileOS: | Win32 |
| ObjectFileType: | Dynamic link library |
| FileSubtype: | - |
| LanguageCode: | English (U.S.) |
| CharacterSet: | Unicode |
| CompanyName: | SQLite Development Team |
| FileDescription: | SQLite is a software library that implements a self-contained, serverless, zero-configuration, transactional SQL database engine. |
| FileVersion: | 3.8.11.1 |
| InternalName: | sqlite3 |
| LegalCopyright: | http://www.sqlite.org/copyright.html |
| ProductName: | SQLite |
| ProductVersion: | 3.8.11.1 |
| SourceId: | 2015-07-29 20:00:57 cf538e2783e468bbc25e7cb2a9ee64d3e0e80b2f |
Total processes
39
Monitored processes
3
Malicious processes
2
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1668 | "C:\Windows\system32\cmd.exe" | C:\Windows\System32\cmd.exe | — | powershell.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 2168 | "C:\WINDOWS\system32\WindowsPowerShell\v1.0\powershell.exe" | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2876 | "C:\Windows\System32\rundll32.exe" C:\Users\admin\AppData\Local\Temp\sqlite3.dll,sqlite3_aggregate_context | C:\Windows\System32\rundll32.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows host process (Rundll32) Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
Total events
768
Read events
715
Write events
53
Delete events
0
Modification events
| (PID) Process: | (2168) powershell.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\17F\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
Executable files
1
Suspicious files
3
Text files
0
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2168 | powershell.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\d93f411851d7c929.customDestinations-ms | binary | |
MD5:3C9EA70BE0EB9C07AB7B929F19966EB2 | SHA256:9AD86CBABCCCD9B21DD789AA354DF25F0ECE29BAF284F5C81DE6A19A634E756F | |||
| 1668 | cmd.exe | C:\Users\admin\AppData\Local\Temp\sqlite3.dll | executable | |
MD5:2BA363CB9C8ECA112DAA44CFB567E91E | SHA256:8BE3304FEC9D41D44012213DDBB28980D2570EDEEF3523B909AF2F97768A8D85 | |||
| 2168 | powershell.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\B11MPXG3CTDA0LD87IVU.temp | binary | |
MD5:3C9EA70BE0EB9C07AB7B929F19966EB2 | SHA256:9AD86CBABCCCD9B21DD789AA354DF25F0ECE29BAF284F5C81DE6A19A634E756F | |||
| 2168 | powershell.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\d93f411851d7c929.customDestinations-ms~RF1c1a17.TMP | binary | |
MD5:16F6D260068B85896C0EBB2E1B2A60D1 | SHA256:6E3B1EF1FB4736A9BF18FADF8E42935CC5053478B6F403A38EFBA8500E819984 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
4
DNS requests
0
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
1080 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
2588 | svchost.exe | 239.255.255.250:1900 | — | — | — | whitelisted |