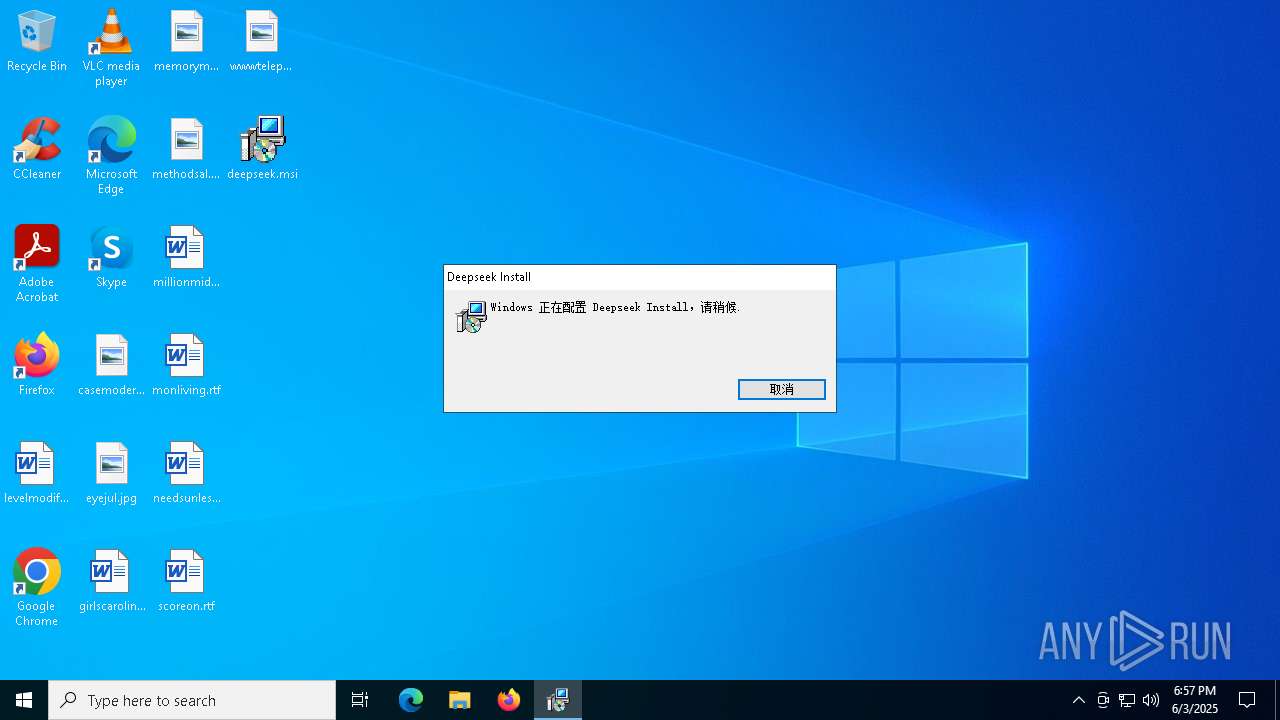
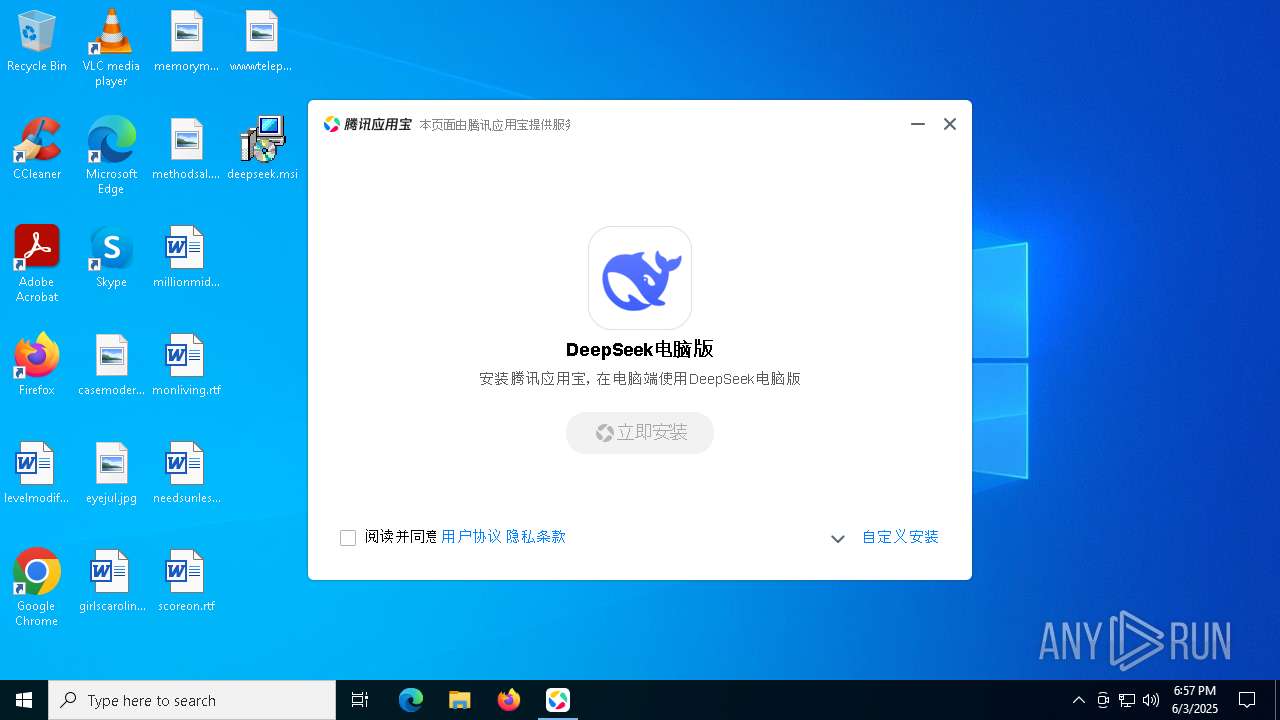
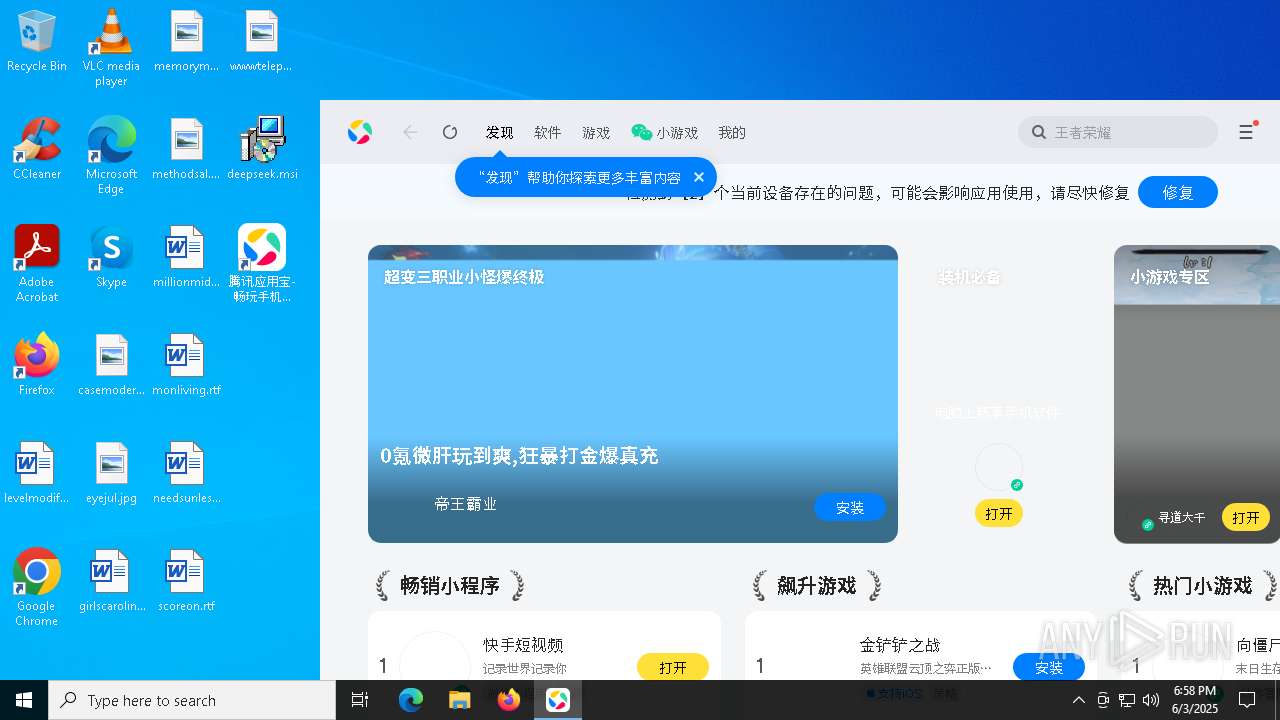
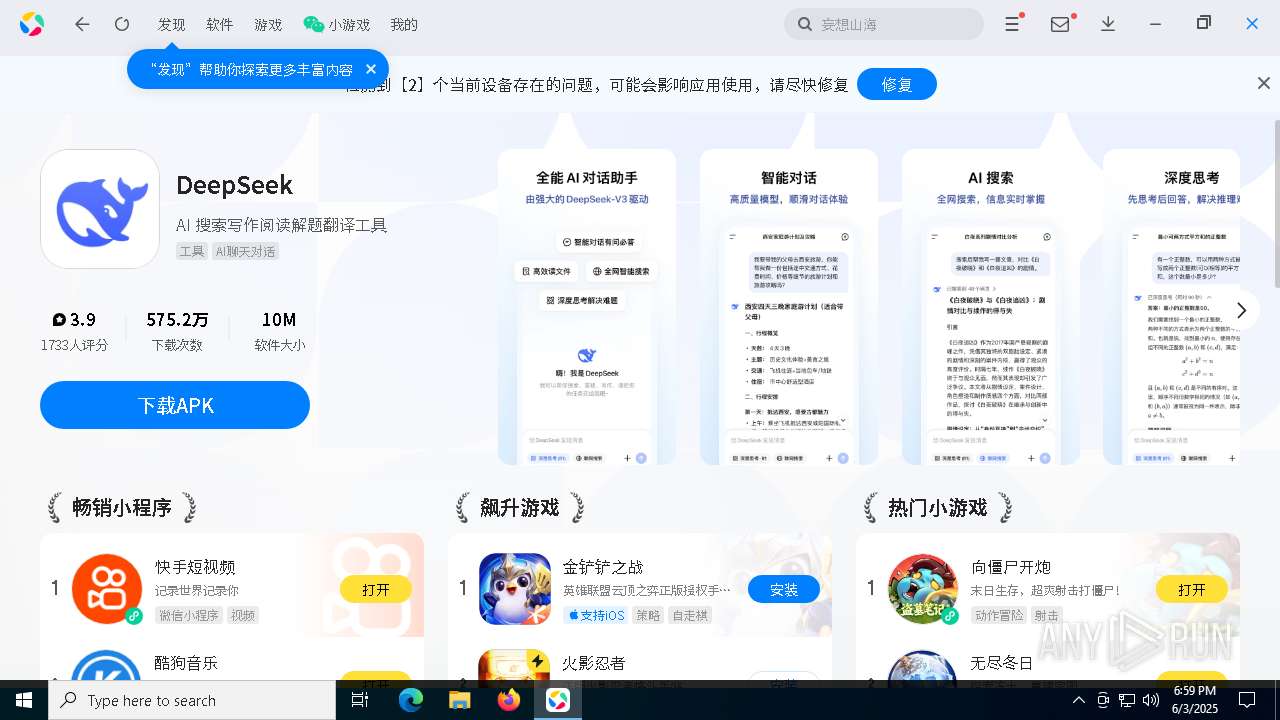
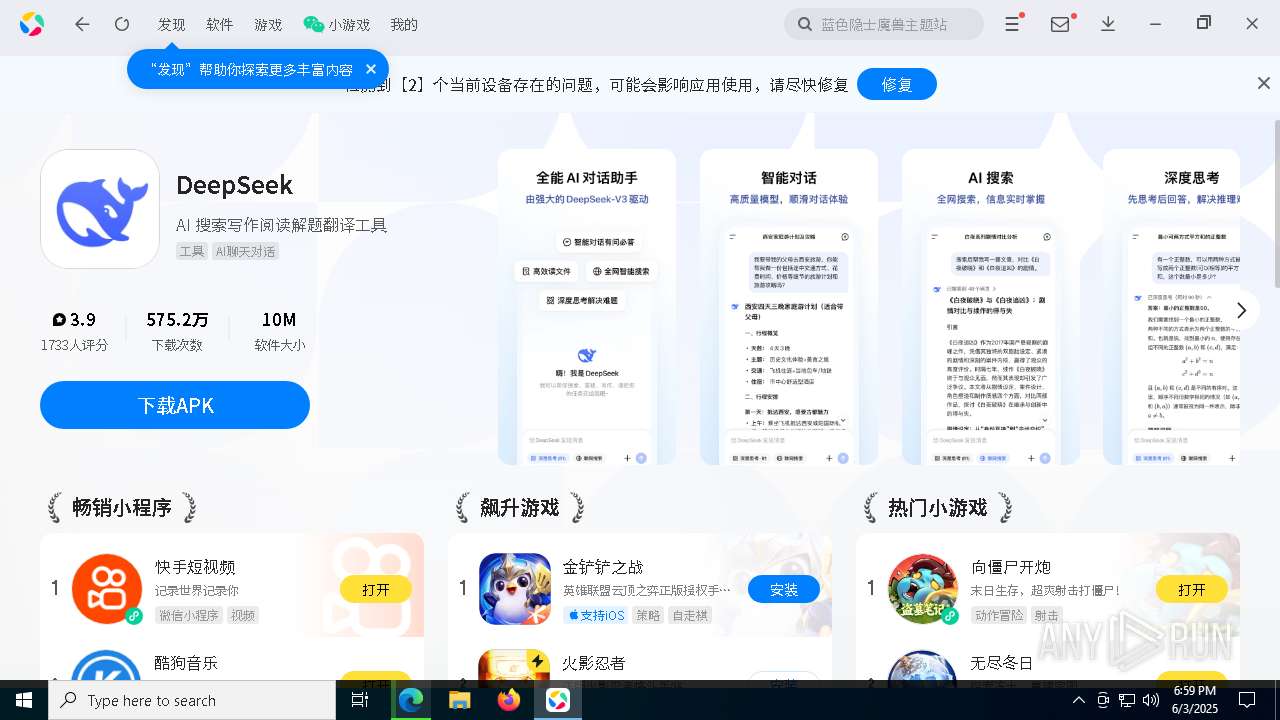
| File name: | deepseek.msi |
| Full analysis: | https://app.any.run/tasks/13095975-8545-47cb-ab4a-59da37827ccf |
| Verdict: | Malicious activity |
| Analysis date: | June 03, 2025, 18:57:16 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-msi |
| File info: | Composite Document File V2 Document, Little Endian, Os: Windows, Version 10.0, MSI Installer, Last Printed: Fri Dec 11 11:47:44 2009, Last Saved Time/Date: Fri Sep 18 14:06:51 2020, Security: 0, Code page: 936, Revision Number: {C83CA984-C147-47F4-A90F-1E62FCFE96ED}, Number of Words: 10, Subject: Deepseek Install, Author: Deepseek, Name of Creating Application: Deepseek Install, Template: ;2052, Comments: Installer Deepseek Install , Title: Installation Database, Keywords: Installer, MSI, Database, Create Time/Date: Wed May 28 12:23:30 2025, Number of Pages: 200 |
| MD5: | 8C6DF59659D4407FA4A07CC094F46DD5 |
| SHA1: | 57D2EFA9BF2DA0985B9D3E9637369558BC34F4F3 |
| SHA256: | 8BE316E9308A263FB890D2847D46B9DB59A42E76997DFBC7C7C91A46B0520FC9 |
| SSDEEP: | 98304:X9I6oIlkrvS252692pD1Rh4UJe521gNR/mFMPBYhZ2MUpQXeceLMebxMZqy6QqzF:bl/jpDuFNAKUEK |
MALICIOUS
Executing a file with an untrusted certificate
- Shine.exe (PID: 1188)
Changes the autorun value in the registry
- Shine.exe (PID: 1188)
Registers / Runs the DLL via REGSVR32.EXE
- Setup.exe (PID: 4452)
SUSPICIOUS
Reads the Windows owner or organization settings
- msiexec.exe (PID: 1696)
Reads security settings of Internet Explorer
- MSIFC93.tmp (PID: 7492)
- MSIFCD3.tmp (PID: 4380)
- Shine.exe (PID: 1188)
- pcyyb_com.deepseek.chat_installer.exe (PID: 1128)
- Setup.exe (PID: 4452)
- AndrowsSvr.exe (PID: 2140)
- AndrowsStore.exe (PID: 7920)
- AndrowsLauncher.exe (PID: 1120)
The process verifies whether the antivirus software is installed
- pcyyb_com.deepseek.chat_installer.exe (PID: 1128)
- AndrowsAssistant.exe (PID: 8136)
- Setup.exe (PID: 4452)
- regsvr32.exe (PID: 7404)
- AndrowsSvr.exe (PID: 2140)
- crashpad_handler.exe (PID: 5360)
- regsvr32.exe (PID: 6808)
- regsvr32.exe (PID: 7152)
- crashpad_handler.exe (PID: 8188)
- AndrowsDlSvr.exe (PID: 1268)
- AndrowsStore.exe (PID: 7920)
- opengl_checker.exe (PID: 776)
- AndrowsAssistant.exe (PID: 7376)
- CefRendererProcess.exe (PID: 7828)
- CefRendererProcess.exe (PID: 7836)
- AndrowsAssistant.exe (PID: 4272)
- WMIC.exe (PID: 7204)
- conhost.exe (PID: 7472)
- AndrowsAssistant.exe (PID: 7424)
- CefRendererProcess.exe (PID: 7888)
- AndrowsLauncher.exe (PID: 1120)
- crashpad_handler.exe (PID: 5232)
- AndrowsAssistant.exe (PID: 8088)
- AndrowsAssistant.exe (PID: 7592)
- AndrowsAssistant.exe (PID: 7724)
- AndrowsAssistant.exe (PID: 6828)
- AndrowsAssistant.exe (PID: 4272)
- AndrowsAssistant.exe (PID: 3332)
- AndrowsAssistant.exe (PID: 2984)
Uses WMIC.EXE to obtain data on the base board management (motherboard or system board)
- pcyyb_com.deepseek.chat_installer.exe (PID: 1128)
- AndrowsStore.exe (PID: 7920)
Connects to unusual port
- Shine.exe (PID: 1188)
Drops 7-zip archiver for unpacking
- pcyyb_com.deepseek.chat_installer.exe (PID: 1128)
- Setup.exe (PID: 4452)
Executable content was dropped or overwritten
- pcyyb_com.deepseek.chat_installer.exe (PID: 1128)
- Setup.exe (PID: 4452)
- AndrowsStore.exe (PID: 7920)
- Setup.exe (PID: 7724)
Process drops legitimate windows executable
- pcyyb_com.deepseek.chat_installer.exe (PID: 1128)
- Setup.exe (PID: 4452)
- AndrowsStore.exe (PID: 7920)
- Setup.exe (PID: 7724)
Found regular expressions for crypto-addresses (YARA)
- Shine.exe (PID: 1188)
The process drops C-runtime libraries
- pcyyb_com.deepseek.chat_installer.exe (PID: 1128)
- Setup.exe (PID: 4452)
- AndrowsStore.exe (PID: 7920)
There is functionality for taking screenshot (YARA)
- Shine.exe (PID: 1188)
- pcyyb_com.deepseek.chat_installer.exe (PID: 1128)
- Setup.exe (PID: 4452)
- AndrowsSvr.exe (PID: 2140)
Creates file in the systems drive root
- Setup.exe (PID: 4452)
- AndrowsSvr.exe (PID: 2140)
Reads the BIOS version
- Setup.exe (PID: 4452)
Reads the date of Windows installation
- Setup.exe (PID: 4452)
- AndrowsSvr.exe (PID: 2140)
- pcyyb_com.deepseek.chat_installer.exe (PID: 1128)
- AndrowsStore.exe (PID: 7920)
- AndrowsLauncher.exe (PID: 1120)
Drops a system driver (possible attempt to evade defenses)
- Setup.exe (PID: 4452)
- pcyyb_com.deepseek.chat_installer.exe (PID: 1128)
The process checks if it is being run in the virtual environment
- Setup.exe (PID: 4452)
- AndrowsSvr.exe (PID: 2140)
- AndrowsStore.exe (PID: 7920)
Executes as Windows Service
- AndrowsSvr.exe (PID: 2140)
Creates or modifies Windows services
- Setup.exe (PID: 4452)
Creates/Modifies COM task schedule object
- regsvr32.exe (PID: 7152)
- regsvr32.exe (PID: 6808)
Starts CMD.EXE for commands execution
- Setup.exe (PID: 4452)
- AndrowsAssistant.exe (PID: 7352)
Creates a software uninstall entry
- pcyyb_com.deepseek.chat_installer.exe (PID: 1128)
Starts SC.EXE for service management
- cmd.exe (PID: 3872)
Windows service management via SC.EXE
- sc.exe (PID: 7788)
INFO
The sample compiled with chinese language support
- msiexec.exe (PID: 1696)
- pcyyb_com.deepseek.chat_installer.exe (PID: 1128)
- Setup.exe (PID: 4452)
- AndrowsStore.exe (PID: 7920)
- Setup.exe (PID: 7724)
Checks supported languages
- msiexec.exe (PID: 1696)
- MSIFC93.tmp (PID: 7492)
- MSIFCD3.tmp (PID: 4380)
- Shine.exe (PID: 1188)
- pcyyb_com.deepseek.chat_installer.exe (PID: 1128)
- msiexec.exe (PID: 2980)
- crashpad_handler.exe (PID: 7572)
- AndrowsAssistant.exe (PID: 8136)
- AndrowsAssistant.exe (PID: 7996)
- AndrowsAssistant.exe (PID: 5772)
- AndrowsSvr.exe (PID: 2140)
- Setup.exe (PID: 4452)
- dokanctl.exe (PID: 1312)
- crashpad_handler.exe (PID: 5360)
- crashpad_handler.exe (PID: 8188)
- AndrowsAssistant.exe (PID: 4272)
- AndrowsDlSvr.exe (PID: 1268)
- opengl_checker.exe (PID: 776)
- AndrowsAssistant.exe (PID: 7376)
- AndrowsStore.exe (PID: 7920)
- AndrowsAssistant.exe (PID: 7424)
- CefRendererProcess.exe (PID: 7828)
- CefRendererProcess.exe (PID: 7836)
- CefRendererProcess.exe (PID: 7888)
- AndrowsLauncher.exe (PID: 1120)
- crashpad_handler.exe (PID: 5232)
- AndrowsAssistant.exe (PID: 8088)
- AndrowsAssistant.exe (PID: 3332)
- AndrowsAssistant.exe (PID: 7592)
- AndrowsAssistant.exe (PID: 7724)
- AndrowsAssistant.exe (PID: 2984)
Reads Environment values
- msiexec.exe (PID: 2980)
- Setup.exe (PID: 4452)
- AndrowsSvr.exe (PID: 2140)
- AndrowsStore.exe (PID: 7920)
Starts application with an unusual extension
- msiexec.exe (PID: 1696)
Create files in a temporary directory
- msiexec.exe (PID: 1696)
- pcyyb_com.deepseek.chat_installer.exe (PID: 1128)
- crashpad_handler.exe (PID: 7572)
- AndrowsAssistant.exe (PID: 4272)
- AndrowsStore.exe (PID: 7920)
- AndrowsLauncher.exe (PID: 1120)
The sample compiled with english language support
- msiexec.exe (PID: 1696)
- pcyyb_com.deepseek.chat_installer.exe (PID: 1128)
- Setup.exe (PID: 4452)
- AndrowsStore.exe (PID: 7920)
- Setup.exe (PID: 7724)
Reads the computer name
- MSIFCD3.tmp (PID: 4380)
- MSIFC93.tmp (PID: 7492)
- Shine.exe (PID: 1188)
- pcyyb_com.deepseek.chat_installer.exe (PID: 1128)
- msiexec.exe (PID: 2980)
- msiexec.exe (PID: 1696)
- Setup.exe (PID: 4452)
- crashpad_handler.exe (PID: 7572)
- AndrowsAssistant.exe (PID: 8136)
- AndrowsAssistant.exe (PID: 7996)
- AndrowsAssistant.exe (PID: 5772)
- AndrowsSvr.exe (PID: 2140)
- crashpad_handler.exe (PID: 5360)
- dokanctl.exe (PID: 1312)
- crashpad_handler.exe (PID: 8188)
- AndrowsAssistant.exe (PID: 4272)
- AndrowsAssistant.exe (PID: 7376)
- AndrowsAssistant.exe (PID: 7424)
- CefRendererProcess.exe (PID: 7836)
- AndrowsLauncher.exe (PID: 1120)
- crashpad_handler.exe (PID: 5232)
- AndrowsAssistant.exe (PID: 8088)
- AndrowsAssistant.exe (PID: 3332)
- AndrowsAssistant.exe (PID: 7592)
- AndrowsAssistant.exe (PID: 2984)
- AndrowsAssistant.exe (PID: 7724)
- AndrowsDlSvr.exe (PID: 1268)
- opengl_checker.exe (PID: 776)
Executable content was dropped or overwritten
- msiexec.exe (PID: 1696)
Process checks computer location settings
- MSIFCD3.tmp (PID: 4380)
- pcyyb_com.deepseek.chat_installer.exe (PID: 1128)
- MSIFC93.tmp (PID: 7492)
- Setup.exe (PID: 4452)
- AndrowsStore.exe (PID: 7920)
- CefRendererProcess.exe (PID: 7828)
- CefRendererProcess.exe (PID: 7888)
- AndrowsLauncher.exe (PID: 1120)
Launching a file from a Registry key
- Shine.exe (PID: 1188)
Reads CPU info
- Shine.exe (PID: 1188)
Creates files or folders in the user directory
- pcyyb_com.deepseek.chat_installer.exe (PID: 1128)
- Setup.exe (PID: 4452)
- AndrowsSvr.exe (PID: 2140)
- AndrowsStore.exe (PID: 7920)
- CefRendererProcess.exe (PID: 7836)
Checks proxy server information
- Shine.exe (PID: 1188)
- Setup.exe (PID: 4452)
- AndrowsSvr.exe (PID: 2140)
- AndrowsStore.exe (PID: 7920)
- AndrowsAssistant.exe (PID: 8088)
Reads the machine GUID from the registry
- pcyyb_com.deepseek.chat_installer.exe (PID: 1128)
- Setup.exe (PID: 4452)
- crashpad_handler.exe (PID: 7572)
- AndrowsAssistant.exe (PID: 8136)
- AndrowsSvr.exe (PID: 2140)
- crashpad_handler.exe (PID: 5360)
- crashpad_handler.exe (PID: 8188)
- AndrowsDlSvr.exe (PID: 1268)
- AndrowsStore.exe (PID: 7920)
- AndrowsAssistant.exe (PID: 7424)
- crashpad_handler.exe (PID: 5232)
- AndrowsAssistant.exe (PID: 8088)
Reads security settings of Internet Explorer
- WMIC.exe (PID: 5056)
- WMIC.exe (PID: 7204)
Reads Windows Product ID
- Setup.exe (PID: 4452)
Reads product name
- Setup.exe (PID: 4452)
- AndrowsSvr.exe (PID: 2140)
- AndrowsStore.exe (PID: 7920)
Creates files in the program directory
- Setup.exe (PID: 4452)
- AndrowsSvr.exe (PID: 2140)
- pcyyb_com.deepseek.chat_installer.exe (PID: 1128)
- AndrowsStore.exe (PID: 7920)
- AndrowsDlSvr.exe (PID: 1268)
Reads the software policy settings
- crashpad_handler.exe (PID: 7572)
- Setup.exe (PID: 4452)
- slui.exe (PID: 1672)
- crashpad_handler.exe (PID: 5360)
- crashpad_handler.exe (PID: 8188)
- AndrowsStore.exe (PID: 7920)
- crashpad_handler.exe (PID: 5232)
- AndrowsSvr.exe (PID: 2140)
TeamViewer related mutex has been found
- Setup.exe (PID: 4452)
- AndrowsStore.exe (PID: 7920)
- AndrowsSvr.exe (PID: 2140)
Application launched itself
- msedge.exe (PID: 5228)
- msedge.exe (PID: 1128)
Manual execution by a user
- msedge.exe (PID: 1128)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .msi | | | Microsoft Windows Installer (81.9) |
|---|---|---|
| .mst | | | Windows SDK Setup Transform Script (9.2) |
| .msp | | | Windows Installer Patch (7.6) |
| .msi | | | Microsoft Installer (100) |
EXIF
FlashPix
| LastPrinted: | 2009:12:11 11:47:44 |
|---|---|
| ModifyDate: | 2020:09:18 14:06:51 |
| Security: | None |
| CodePage: | Windows Simplified Chinese (PRC, Singapore) |
| RevisionNumber: | {C83CA984-C147-47F4-A90F-1E62FCFE96ED} |
| Words: | 10 |
| Subject: | Deepseek Install |
| Author: | Deepseek |
| LastModifiedBy: | - |
| Software: | Deepseek Install |
| Template: | ;2052 |
| Comments: | ?? Installer ???ݿ??????˰?װ Deepseek Install ?????????????ݡ? |
| Title: | Installation Database |
| Keywords: | Installer, MSI, Database |
| CreateDate: | 2025:05:28 12:23:30 |
| Pages: | 200 |
Total processes
236
Monitored processes
103
Malicious processes
29
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 776 | "C:\Program Files\Tencent\Androws\Application\3.0.9500.2291\opengl_checker.exe" | C:\Program Files\Tencent\Androws\Application\3.0.9500.2291\opengl_checker.exe | — | AndrowsStore.exe | |||||||||||
User: admin Integrity Level: HIGH Exit code: 1 Modules
| |||||||||||||||
| 960 | "C:\Program Files\Tencent\Androws\Application\3.0.9500.2291\AndrowsAssistant.exe" --check-opengl-process "AndrowsStore.exe" | C:\Program Files\Tencent\Androws\Application\3.0.9500.2291\AndrowsAssistant.exe | — | AndrowsStore.exe | |||||||||||
User: admin Company: Tencent Integrity Level: HIGH Description: 腾讯应用宝 Exit code: 1000 Version: 3.0.9500.2291 Modules
| |||||||||||||||
| 1120 | "C:\Program Files\Tencent\Androws\Application\AndrowsLauncher.exe" --launch-proc-name "AndrowsAssistant.exe" --monitor-main_window-handle "262952" --monitor-process-id "7920" --monitor-process-name "AndrowsStore.exe" | C:\Program Files\Tencent\Androws\Application\AndrowsLauncher.exe | — | AndrowsStore.exe | |||||||||||
User: admin Company: Tencent Integrity Level: HIGH Description: 腾讯应用宝 Exit code: 0 Version: 3.0.9500.2291 Modules
| |||||||||||||||
| 1128 | "C:\Users\admin\AppData\Local\Temp\pcyyb_com.deepseek.chat_installer.exe" | C:\Users\admin\AppData\Local\Temp\pcyyb_com.deepseek.chat_installer.exe | MSIFC93.tmp | ||||||||||||
User: admin Company: Tencent Integrity Level: HIGH Description: 腾讯应用宝 Exit code: 0 Version: 1.0.0.72868 Modules
| |||||||||||||||
| 1128 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --flag-switches-begin --disable-quic --flag-switches-end --do-not-de-elevate --single-argument https://sj.qq.com/appdetail/com.deepseek.chat?landing_type=yybclient | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Edge Version: 122.0.2365.59 Modules
| |||||||||||||||
| 1188 | "C:\ProgramData\Deepseek\Shine.exe" | C:\ProgramData\Deepseek\Shine.exe | MSIFCD3.tmp | ||||||||||||
User: admin Integrity Level: MEDIUM Modules
| |||||||||||||||
| 1268 | "C:\Program Files\Tencent\Androws\Application\3.0.9500.2291\AndrowsDlSvr.exe" --daemon --allow-overwrite=true --conf-path="C:\Program Files\Tencent\Androws\Application\3.0.9500.2291\androws_dl_svr.cfg" --log="C:\Program Files\Tencent\Androws\Application\3.0.9500.2291\logs\androws_dl_svr.log" --rpc-listen-port=49877 --rpc-secret=androws_660322669764e600f72a9d39b7a77924 --stop-with-process=7920 | C:\Program Files\Tencent\Androws\Application\3.0.9500.2291\AndrowsDlSvr.exe | AndrowsStore.exe | ||||||||||||
User: admin Integrity Level: HIGH Modules
| |||||||||||||||
| 1312 | "C:\Program Files\Tencent\Androws\Application\3.0.9500.2291\dokanctl.exe" /i d "C:\Program Files\Tencent\Androws\Application\3.0.9500.2291\Driver\dokan2t.sys" | C:\Program Files\Tencent\Androws\Application\3.0.9500.2291\dokanctl.exe | — | Setup.exe | |||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
| 1472 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1540 | "C:\Program Files\Tencent\Androws\Application\3.0.9500.2291\AndrowsAssistant.exe" --check-opengl-process "AndrowsStore.exe" | C:\Program Files\Tencent\Androws\Application\3.0.9500.2291\AndrowsAssistant.exe | — | AndrowsStore.exe | |||||||||||
User: admin Company: Tencent Integrity Level: HIGH Description: 腾讯应用宝 Exit code: 1000 Version: 3.0.9500.2291 Modules
| |||||||||||||||
Total events
38 912
Read events
38 346
Write events
521
Delete events
45
Modification events
| (PID) Process: | (1696) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Installer\Folders |
| Operation: | write | Name: | C:\Users\admin\AppData\Roaming\Microsoft\Installer\ |
Value: | |||
| (PID) Process: | (1696) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Installer\UserData\S-1-5-21-1693682860-607145093-2874071422-1001\Components\E8FA58832985772469EC723F4FFA2A3D |
| Operation: | write | Name: | EED9875B7204F0045B1B515E51A36DD6 |
Value: C:\Users\admin\AppData\Local\Temp\ | |||
| (PID) Process: | (1696) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Installer\UserData\S-1-5-21-1693682860-607145093-2874071422-1001\Components\654A6C3C1DE7561489692C71E8CC021C |
| Operation: | write | Name: | EED9875B7204F0045B1B515E51A36DD6 |
Value: C:\ProgramData\Deepseek\libcef.dll | |||
| (PID) Process: | (1696) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Installer\UserData\S-1-5-21-1693682860-607145093-2874071422-1001\Components\1D76AE40A756DC84998F1A4EFF364C87 |
| Operation: | write | Name: | EED9875B7204F0045B1B515E51A36DD6 |
Value: C:\ProgramData\Deepseek\Shine.exe | |||
| (PID) Process: | (1696) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Installer\UserData\S-1-5-21-1693682860-607145093-2874071422-1001\Components\EDEBC47D9F05CCB4982D5F7011FCFBA0 |
| Operation: | write | Name: | EED9875B7204F0045B1B515E51A36DD6 |
Value: C:\Users\admin\AppData\Local\Temp\pcyyb_com.deepseek.chat_installer.exe | |||
| (PID) Process: | (1696) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Installer\UserData\S-1-5-21-1693682860-607145093-2874071422-1001\Components\2A8488285E9829149ADACB91A73095DC |
| Operation: | write | Name: | EED9875B7204F0045B1B515E51A36DD6 |
Value: C:\ProgramData\Deepseek\1.txt | |||
| (PID) Process: | (1696) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Installer\Folders |
| Operation: | write | Name: | C:\ProgramData\Deepseek\ |
Value: | |||
| (PID) Process: | (1696) msiexec.exe | Key: | HKEY_USERS\S-1-5-21-1693682860-607145093-2874071422-1001\SOFTWARE\Microsoft\RestartManager\Session0000 |
| Operation: | write | Name: | Owner |
Value: A006000051106756B9D4DB01 | |||
| (PID) Process: | (1696) msiexec.exe | Key: | HKEY_USERS\S-1-5-21-1693682860-607145093-2874071422-1001\SOFTWARE\Microsoft\RestartManager\Session0000 |
| Operation: | write | Name: | SessionHash |
Value: 40E3AC870EAC505E7E129EA539C57779236FAD68144C8719720F40BBA826E1DA | |||
| (PID) Process: | (1696) msiexec.exe | Key: | HKEY_USERS\S-1-5-21-1693682860-607145093-2874071422-1001\SOFTWARE\Microsoft\RestartManager\Session0000 |
| Operation: | write | Name: | Sequence |
Value: 1 | |||
Executable files
548
Suspicious files
604
Text files
453
Unknown types
256
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 1696 | msiexec.exe | C:\Windows\Installer\11f7ca.msi | — | |
MD5:— | SHA256:— | |||
| 1696 | msiexec.exe | C:\Windows\Installer\MSIF9A0.tmp | executable | |
MD5:C7FBD5EE98E32A77EDF1156DB3FCA622 | SHA256:E140990B509DD6884A5742BDE64F2CDAA10012D472B0B32DE43EBECBC83242B6 | |||
| 1696 | msiexec.exe | C:\Windows\Installer\MSIFA10.tmp | executable | |
MD5:C7FBD5EE98E32A77EDF1156DB3FCA622 | SHA256:E140990B509DD6884A5742BDE64F2CDAA10012D472B0B32DE43EBECBC83242B6 | |||
| 1696 | msiexec.exe | C:\Windows\Temp\~DF69BC49D266806A97.TMP | binary | |
MD5:841B3AF1514FE9B6A8CC8B76EBF59CA4 | SHA256:B196B17192D5199968E4B4C8D51FEA43FA9BE34BD25643E883E15BE09241924B | |||
| 1696 | msiexec.exe | C:\Windows\Temp\~DF6EA3662B6419AB64.TMP | gmc | |
MD5:BF619EAC0CDF3F68D496EA9344137E8B | SHA256:076A27C79E5ACE2A3D47F9DD2E83E4FF6EA8872B3C2218F66C92B89B55F36560 | |||
| 1696 | msiexec.exe | C:\Windows\Installer\MSIF8B5.tmp | executable | |
MD5:C7FBD5EE98E32A77EDF1156DB3FCA622 | SHA256:E140990B509DD6884A5742BDE64F2CDAA10012D472B0B32DE43EBECBC83242B6 | |||
| 1696 | msiexec.exe | C:\Windows\Installer\inprogressinstallinfo.ipi | binary | |
MD5:841B3AF1514FE9B6A8CC8B76EBF59CA4 | SHA256:B196B17192D5199968E4B4C8D51FEA43FA9BE34BD25643E883E15BE09241924B | |||
| 1696 | msiexec.exe | C:\ProgramData\Deepseek\libcef.dll | executable | |
MD5:966310F10069F8443FE4D8ADF4A7BD80 | SHA256:3971AF2729D2BE9287D84FC0A187F8C08BE89ACC90BCC1E39623E3BA49FB199E | |||
| 1696 | msiexec.exe | C:\Windows\Installer\MSIFB2B.tmp | binary | |
MD5:A4FC08D7FE180C10509AD657CA437267 | SHA256:02E131749727050D85AAA282730D90DA8E91F1911CF64342E51B8A5FEA8F49E5 | |||
| 1696 | msiexec.exe | C:\Windows\Temp\~DFA63BD9D01010B99C.TMP | binary | |
MD5:841B3AF1514FE9B6A8CC8B76EBF59CA4 | SHA256:B196B17192D5199968E4B4C8D51FEA43FA9BE34BD25643E883E15BE09241924B | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
14
TCP/UDP connections
314
DNS requests
148
Threats
15
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
5496 | MoUsoCoreWorker.exe | GET | 200 | 23.219.150.101:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
6544 | svchost.exe | GET | 200 | 2.23.77.188:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
5496 | MoUsoCoreWorker.exe | GET | 200 | 2.16.168.114:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
6668 | SIHClient.exe | GET | 200 | 23.219.150.101:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
6668 | SIHClient.exe | GET | 200 | 23.219.150.101:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
4452 | Setup.exe | GET | 200 | 163.181.92.201:80 | http://ocsp.digicert.cn/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEA%2FgMquETQMxBsUMjhPIsGg%3D | unknown | — | — | whitelisted |
4452 | Setup.exe | GET | 200 | 163.181.92.201:80 | http://ocsp.digicert.cn/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEATBuWAZH8q%2B3NqTAabNeMM%3D | unknown | — | — | whitelisted |
2140 | AndrowsSvr.exe | GET | 200 | 163.181.92.201:80 | http://ocsp.digicert.cn/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEATBuWAZH8q%2B3NqTAabNeMM%3D | unknown | — | — | whitelisted |
2140 | AndrowsSvr.exe | GET | 200 | 163.181.92.201:80 | http://ocsp.digicert.cn/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEA%2FgMquETQMxBsUMjhPIsGg%3D | unknown | — | — | whitelisted |
2140 | AndrowsSvr.exe | GET | 200 | 163.181.92.201:80 | http://ocsp.digicert.cn/MFEwTzBNMEswSTAJBgUrDgMCGgUABBRdfbJlK8FvT8EKTy%2FQWk9HlJQmegQUKyMWgRtHiYqQeuzoMtRsjnL5ziUCEAtfHw4uO3jgnc1uenuzUtk%3D | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
7276 | RUXIMICS.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
— | — | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
5496 | MoUsoCoreWorker.exe | 2.16.168.114:80 | crl.microsoft.com | Akamai International B.V. | RU | whitelisted |
5496 | MoUsoCoreWorker.exe | 23.219.150.101:80 | www.microsoft.com | AKAMAI-AS | CL | whitelisted |
7784 | svchost.exe | 23.219.150.101:80 | www.microsoft.com | AKAMAI-AS | CL | whitelisted |
7784 | svchost.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
1188 | Shine.exe | 206.119.124.126:1804 | — | STARCLOUD GLOBAL PTE., LTD. | US | unknown |
1128 | pcyyb_com.deepseek.chat_installer.exe | 129.226.102.75:443 | yybadaccess.3g.qq.com | Tencent Building, Kejizhongyi Avenue | HK | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
yybadaccess.3g.qq.com |
| whitelisted |
oth.eve.mdt.qq.com |
| whitelisted |
conf.syzs.qq.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
7836 | CefRendererProcess.exe | Generic Protocol Command Decode | SURICATA QUIC failed decrypt |
7836 | CefRendererProcess.exe | Generic Protocol Command Decode | SURICATA QUIC failed decrypt |
7836 | CefRendererProcess.exe | Misc activity | ET INFO Tencent Cloud Storage Domain in DNS Lookup (myqcloud .com) |
7836 | CefRendererProcess.exe | Misc activity | ET INFO Tencent Cloud Storage Domain in DNS Lookup (myqcloud .com) |
7836 | CefRendererProcess.exe | Misc activity | ET INFO Observed Tencent Cloud Storage Domain (myqcloud .com in TLS SNI) |
7836 | CefRendererProcess.exe | Misc activity | ET INFO Observed Tencent Cloud Storage Domain (myqcloud .com in TLS SNI) |
7836 | CefRendererProcess.exe | Misc activity | ET INFO Observed Tencent Cloud Storage Domain (myqcloud .com in TLS SNI) |
7836 | CefRendererProcess.exe | Misc activity | ET INFO Observed Tencent Cloud Storage Domain (myqcloud .com in TLS SNI) |
7836 | CefRendererProcess.exe | Misc activity | ET INFO Observed Tencent Cloud Storage Domain (myqcloud .com in TLS SNI) |
7836 | CefRendererProcess.exe | Generic Protocol Command Decode | SURICATA QUIC failed decrypt |
Process | Message |
|---|---|
AndrowsSvr.exe | 06-03 18:58:28.613 [2140.2320](info)[app.androwsservice] [WaitForExploreReady] (uac_start.cc:234) [Msg]: Waiting for explore... |
AndrowsSvr.exe | 06-03 18:58:28.613 [2140.5236](info)[app.androwsservice] [service::ServiceMain] (androws_service.cpp:139) [Msg]: [Enter][argc]: 1 |
AndrowsSvr.exe | 06-03 18:58:28.613 [2140.5236](info)[app.androwsservice] [service::ServiceMain] (androws_service.cpp:167) [Msg]: Service Starting... |
AndrowsSvr.exe | 06-03 18:58:28.613 [2140.6992](info)[app.androwsservice] [service::Initialize::::operator()] (androws_service.cpp:191) [Msg]: Starting ServiceMain... |
AndrowsSvr.exe | 06-03 18:58:28.613 [2140.2320](info)[app.launch] [boot::Initialize] (initialize.cpp:103) [Msg]: "C:\Program Files\Tencent\Androws\Application\3.0.9500.2291\AndrowsSvr.exe" |
AndrowsSvr.exe | 06-03 18:58:28.613 [2140.2320](info)[app.androwsservice] [WaitForExploreReady] (uac_start.cc:244) [Msg]: Waiting for explore done. |
crashpad_handler.exe | [5360:7968:20250603,185828.675:ERROR filesystem_win.cc:130] GetFileAttributes C:\AndrowsData\BTrace\7ebaf51295\Trace: The system cannot find the file specified. (2)
|
crashpad_handler.exe | [5360:6920:20250603,185828.691:INFO bugly_trace_report.cc:322] [Trace] checkReportCacheFile num:0
|
crashpad_handler.exe | Bugly: [statistices] find statistices file count:0 |
crashpad_handler.exe | [Trace] checkReportCacheFile num:0 |