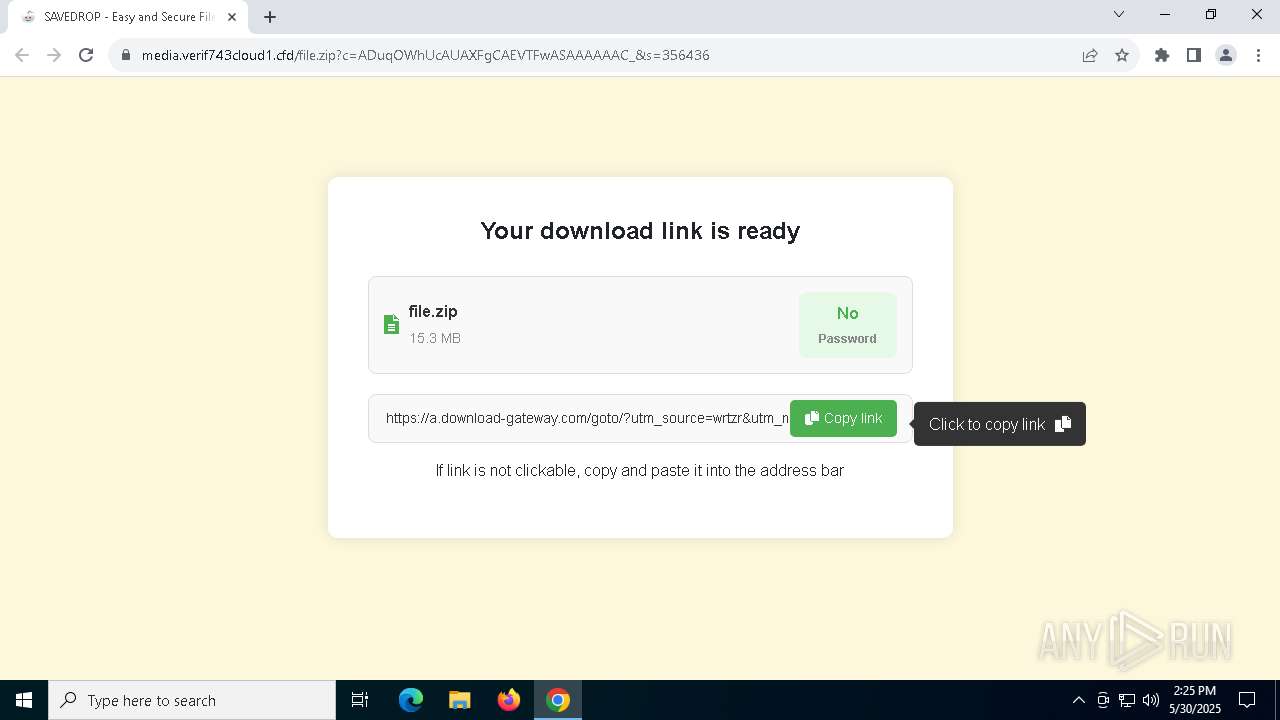
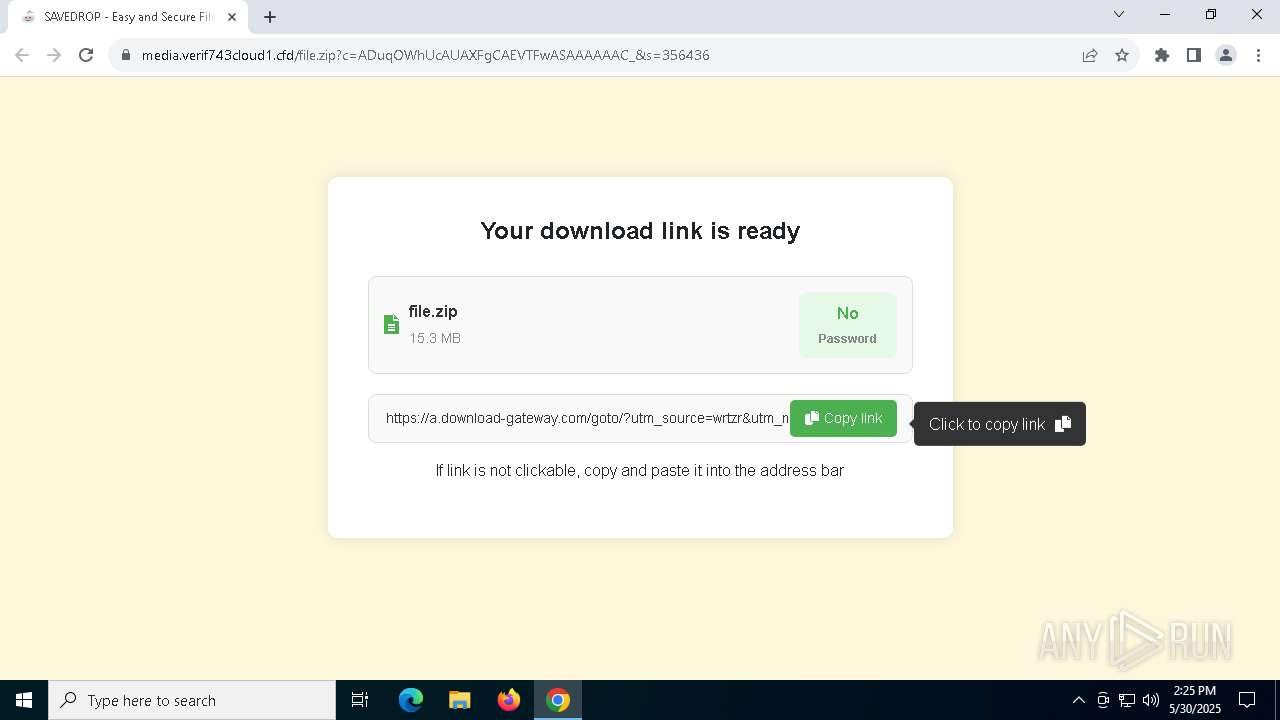
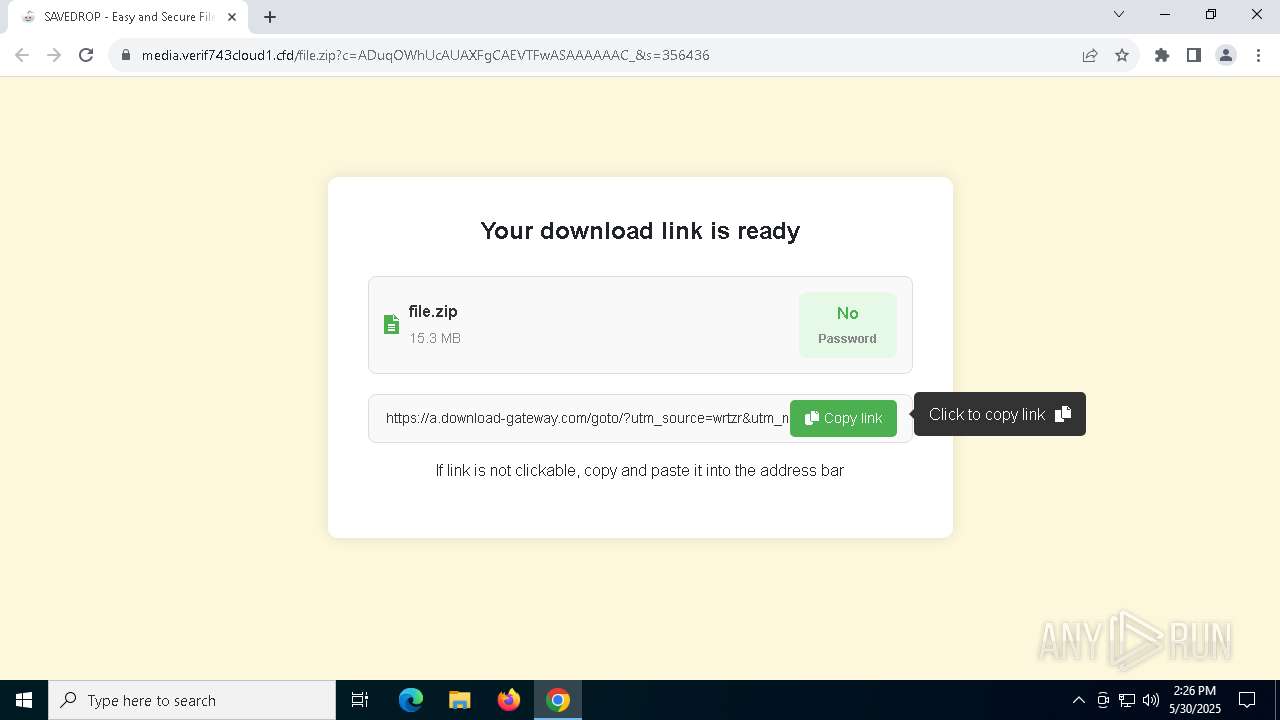
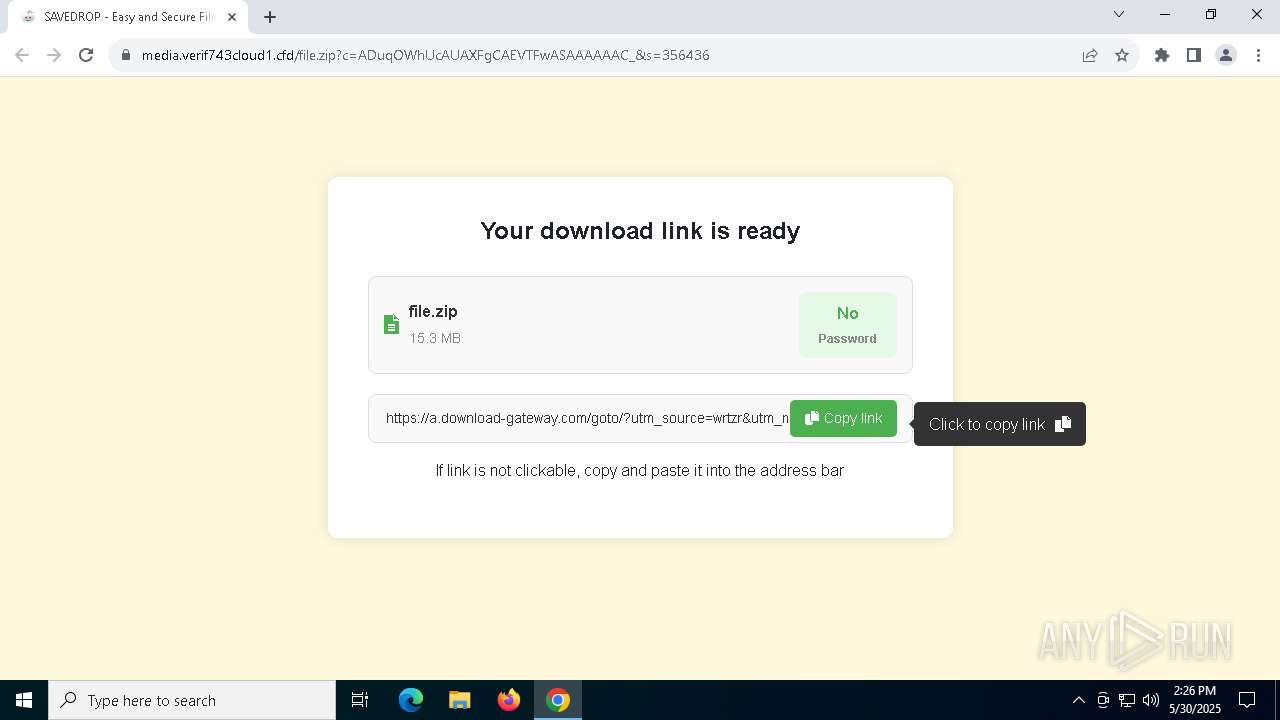
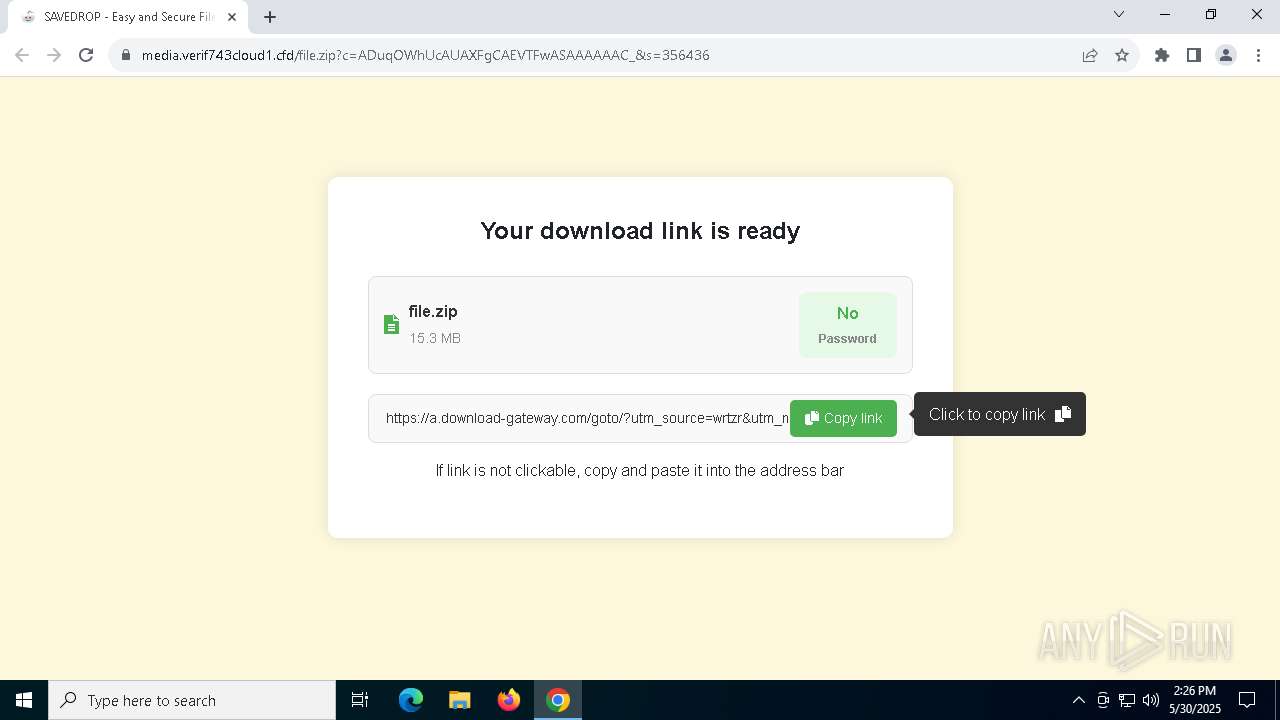
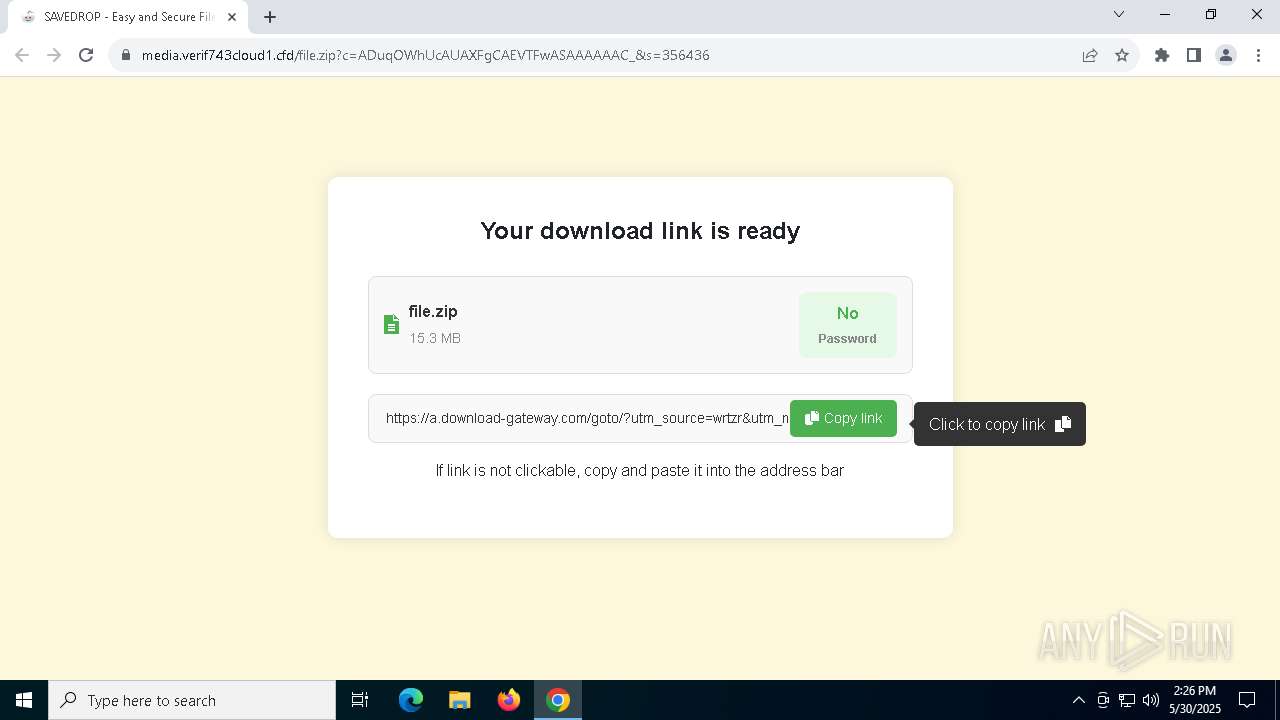
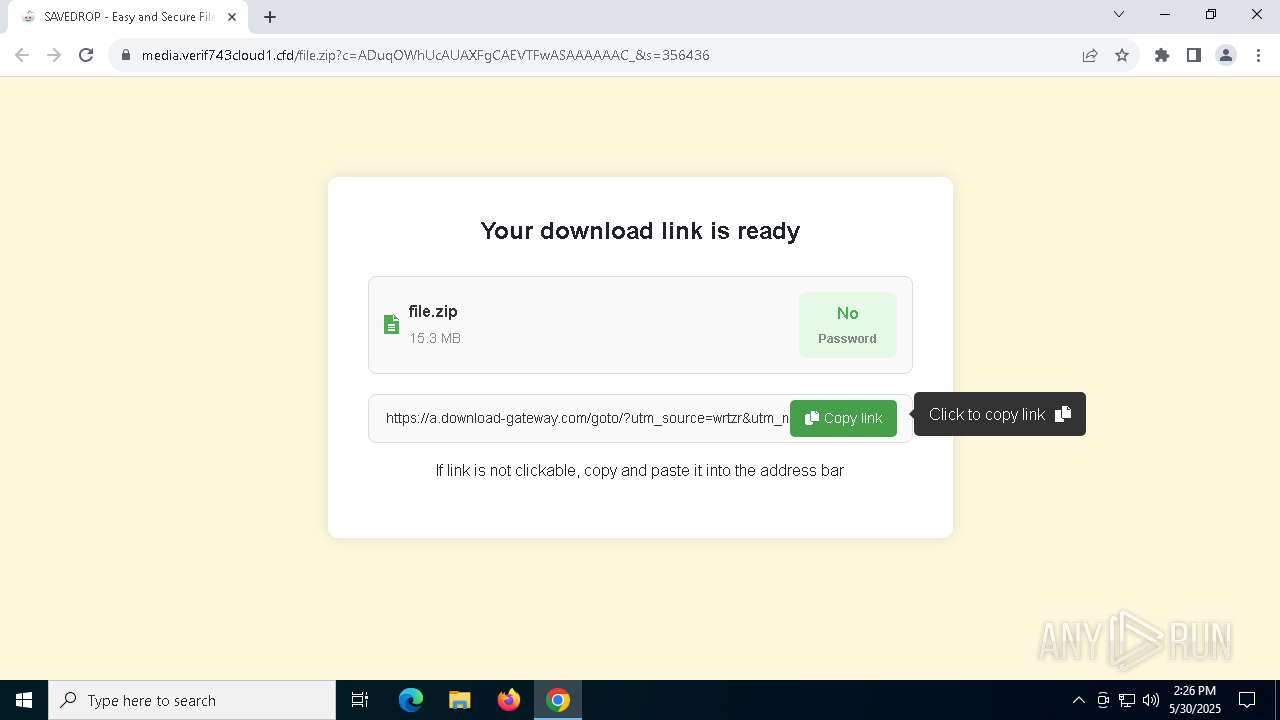
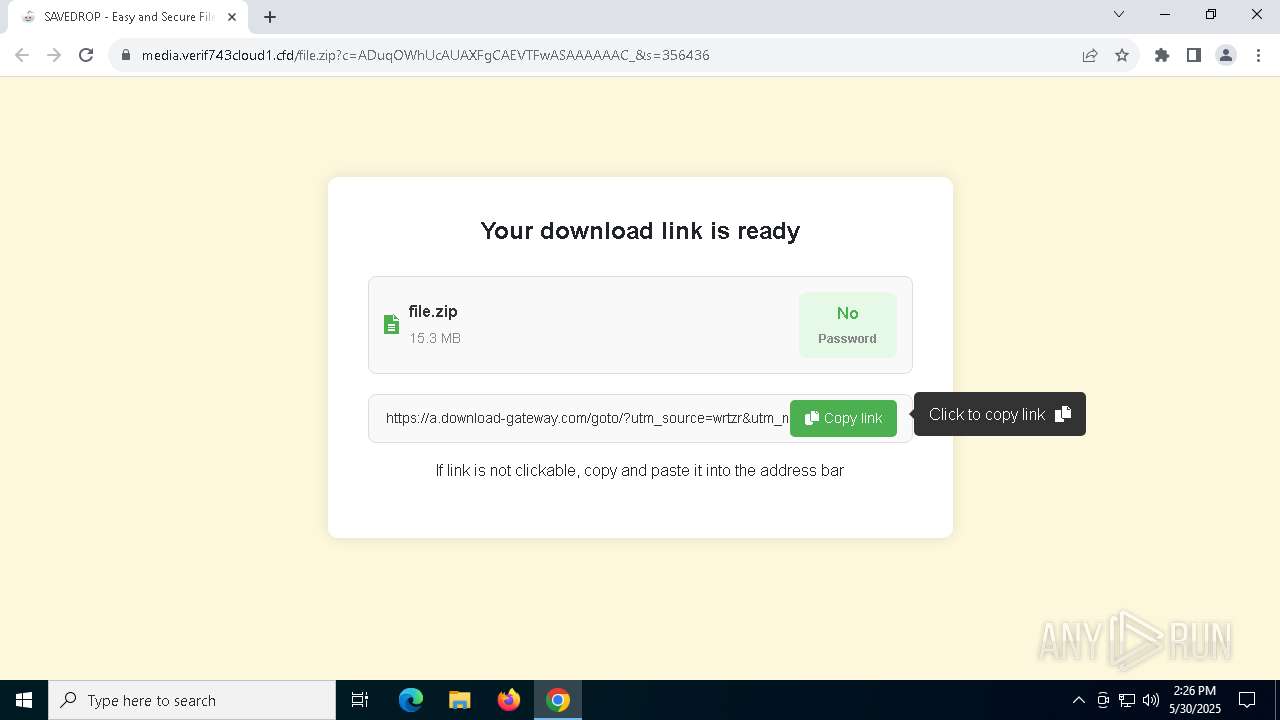
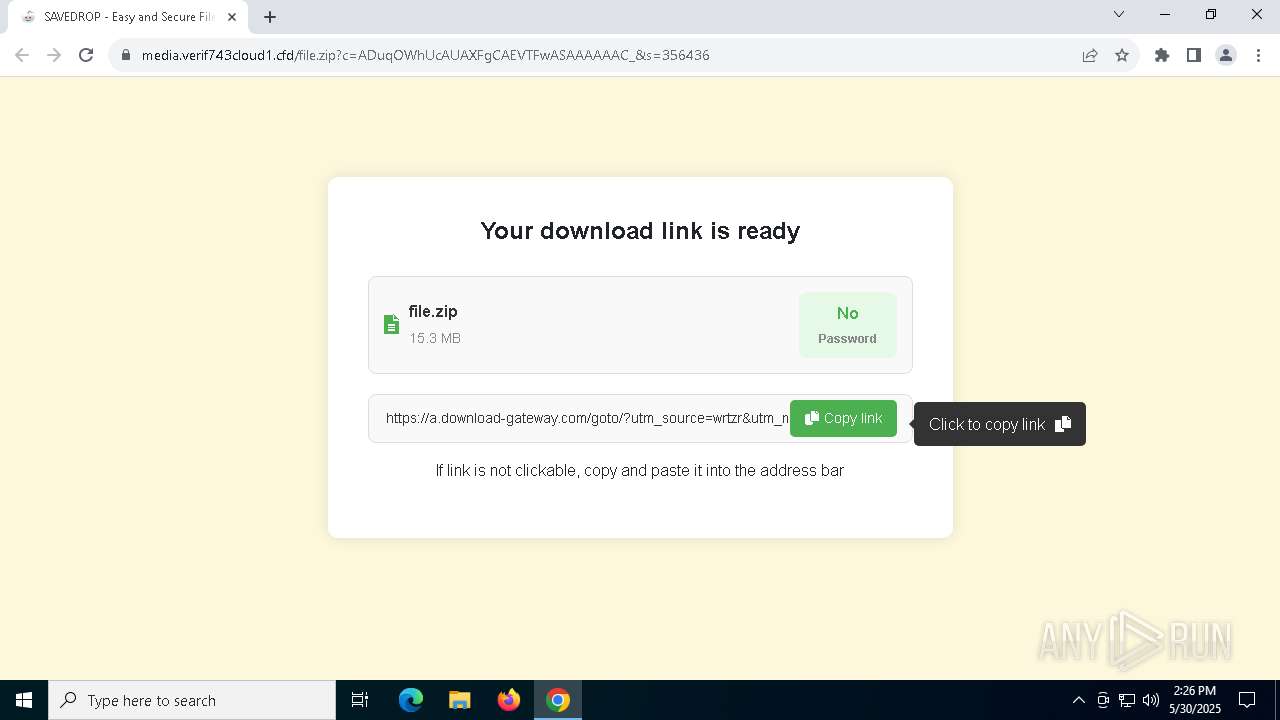
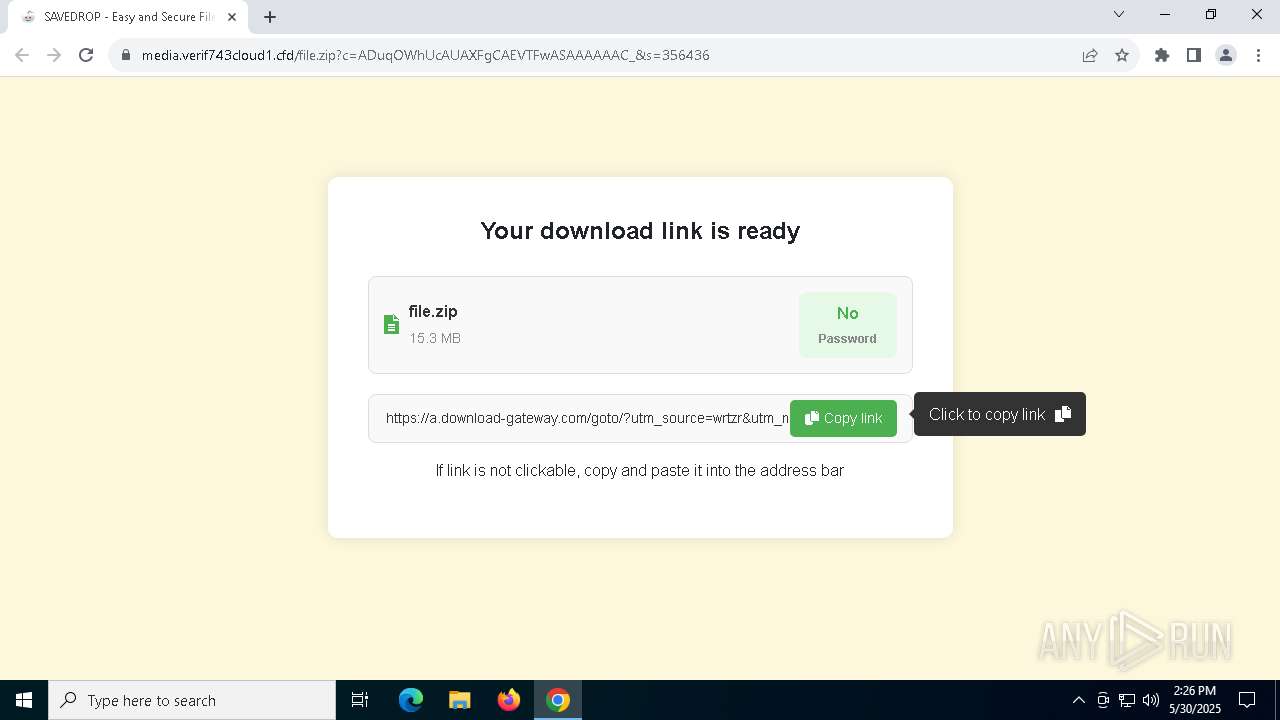
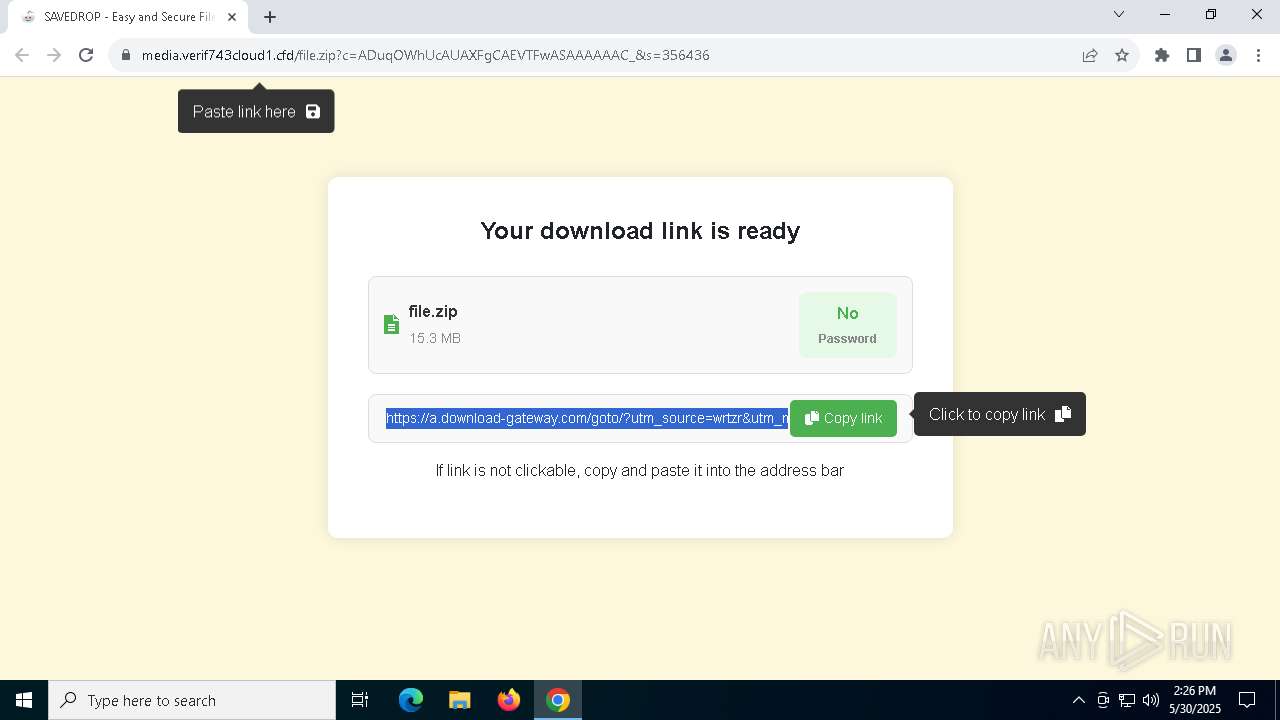
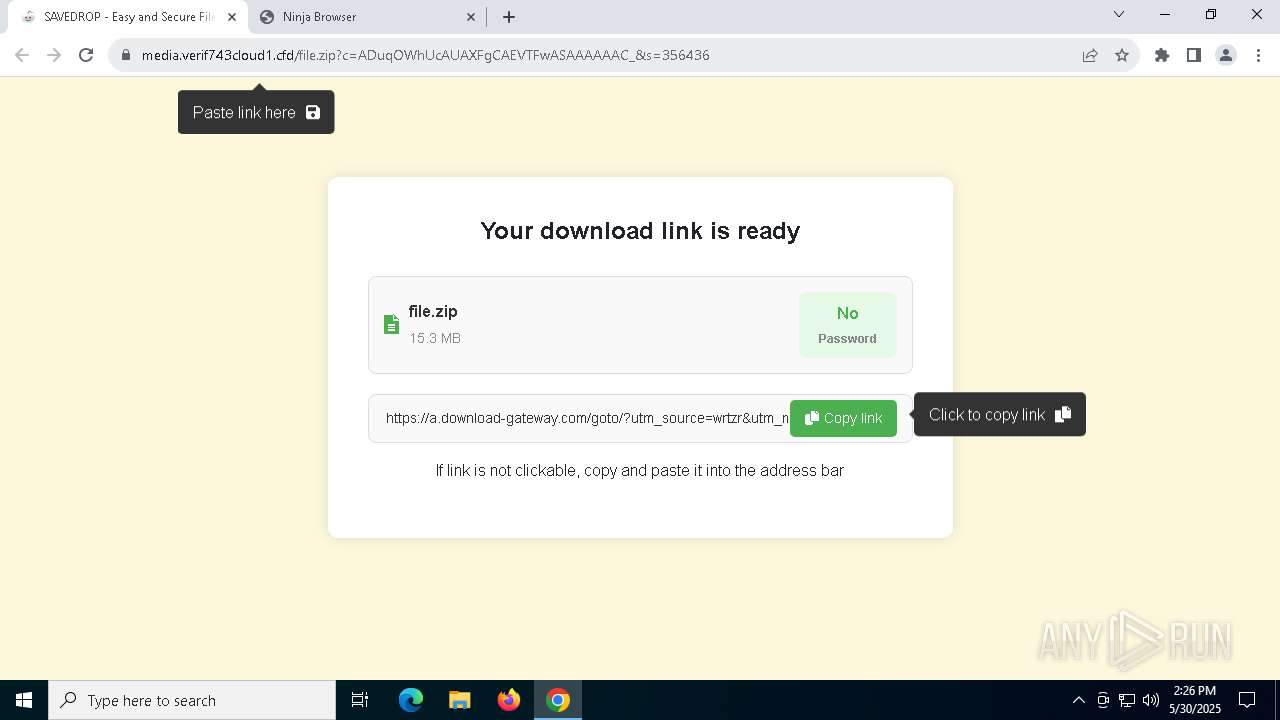
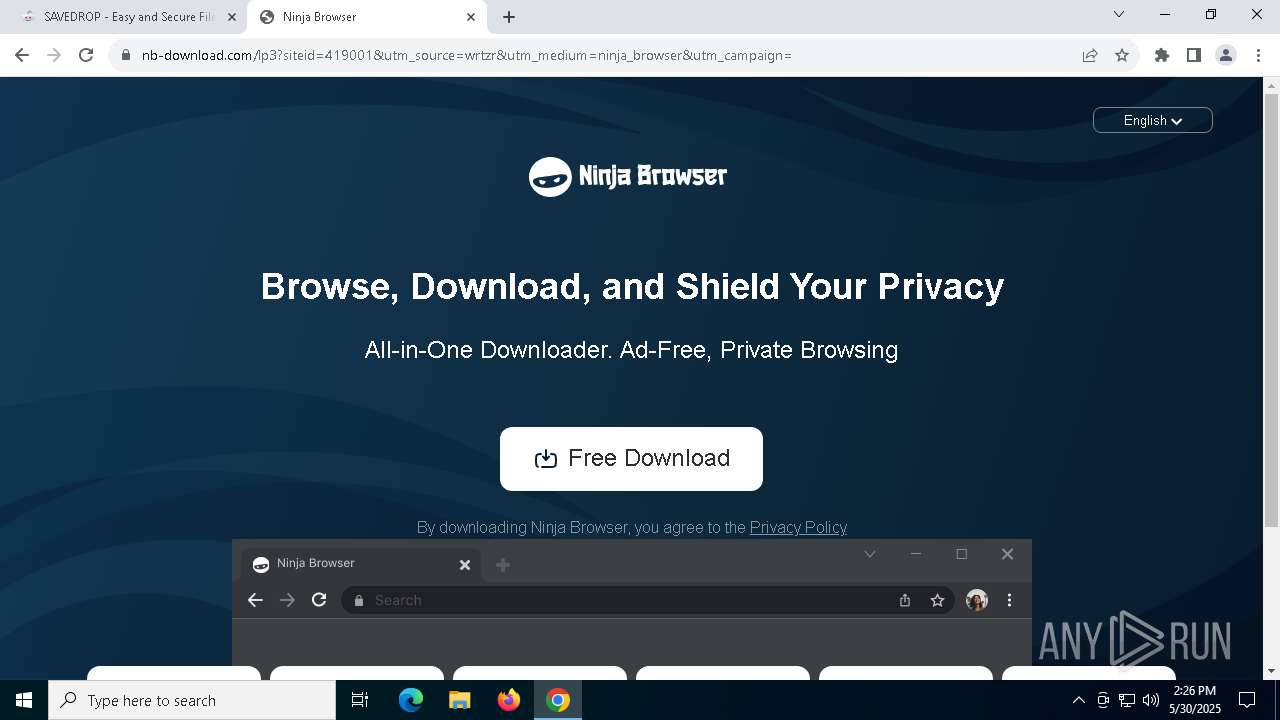
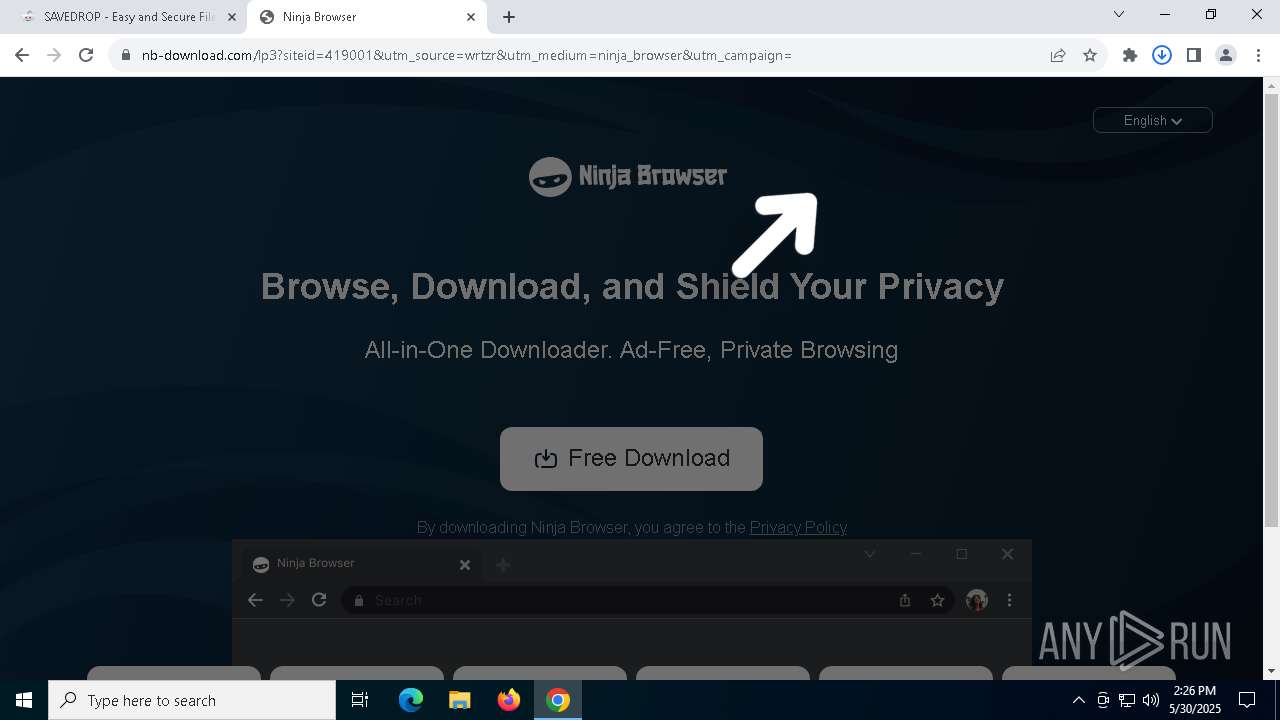
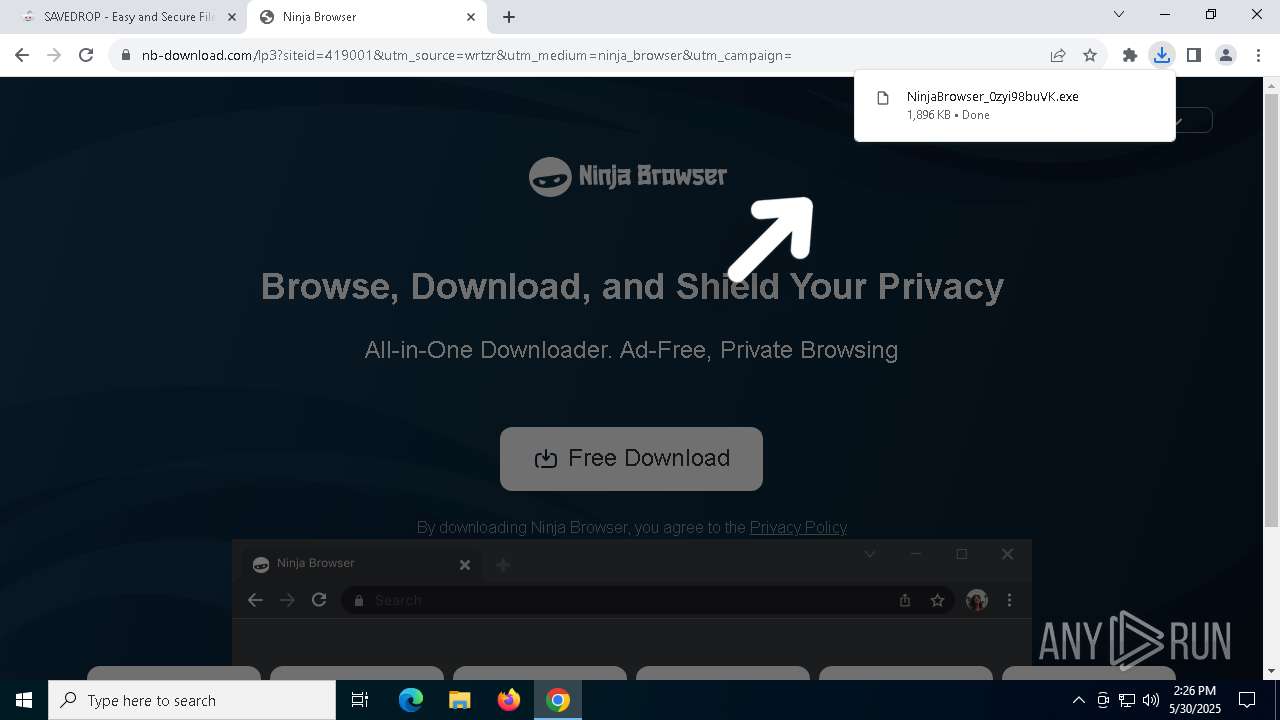
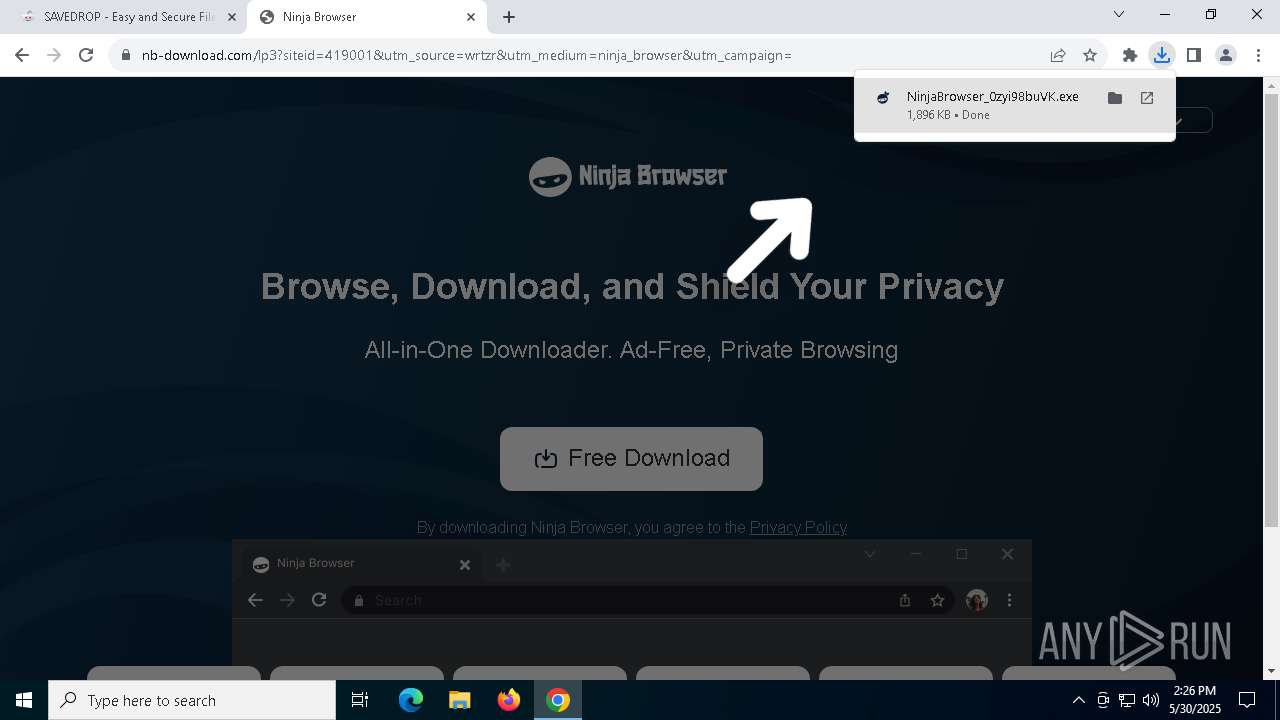
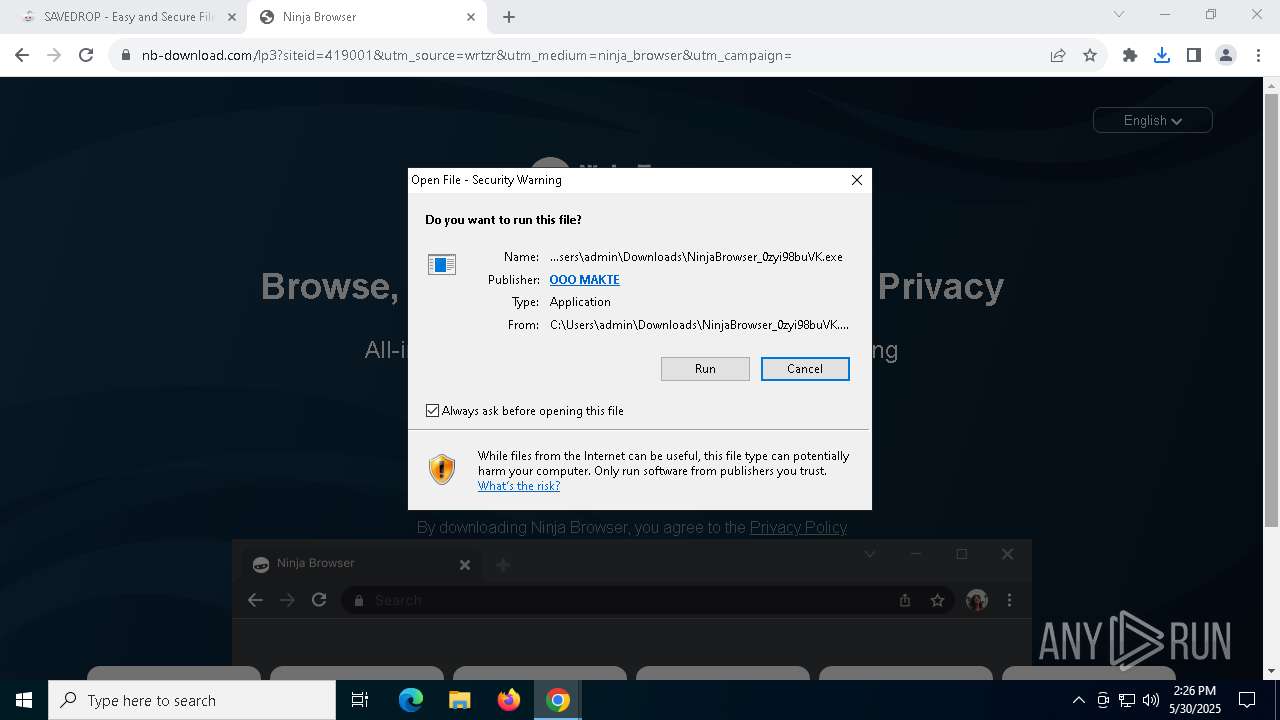
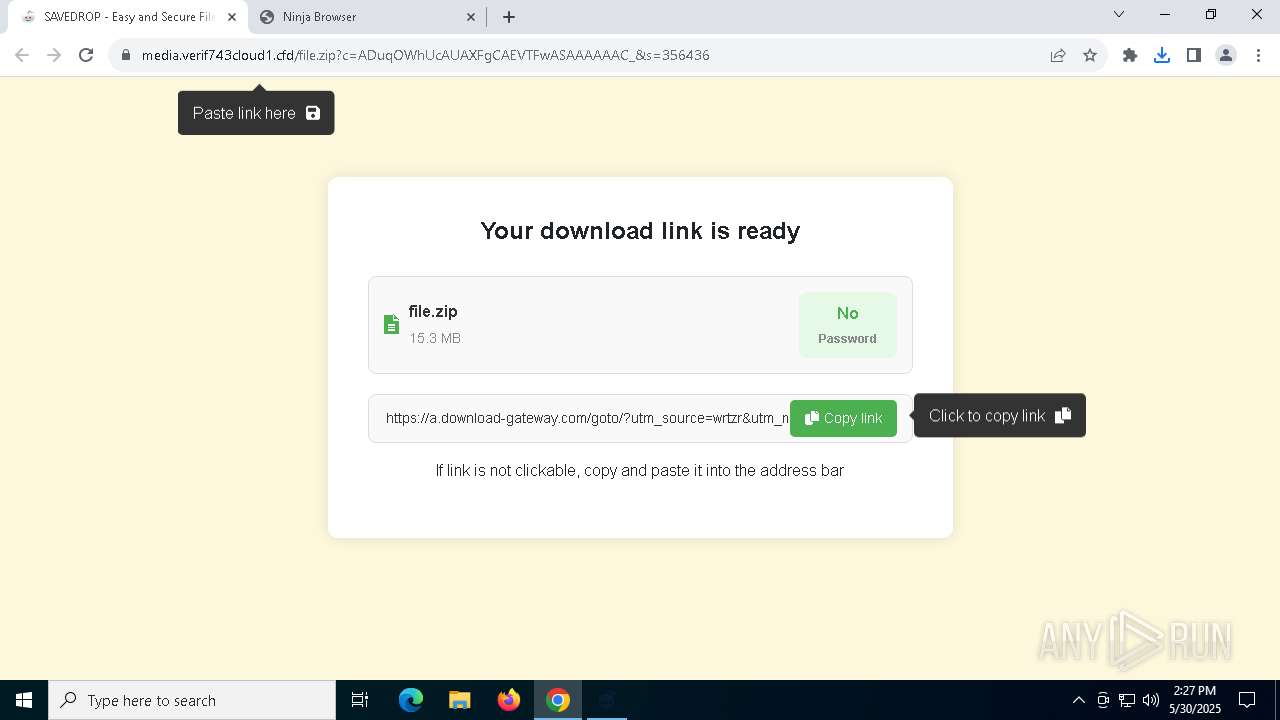
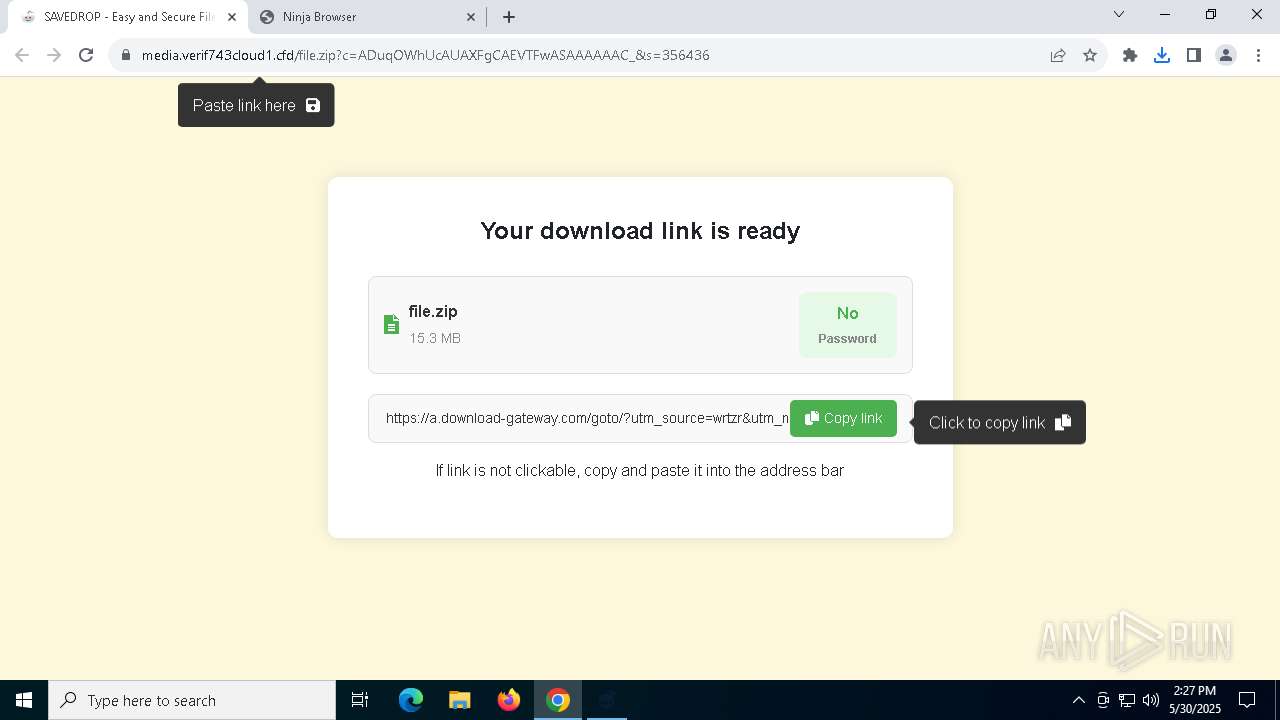
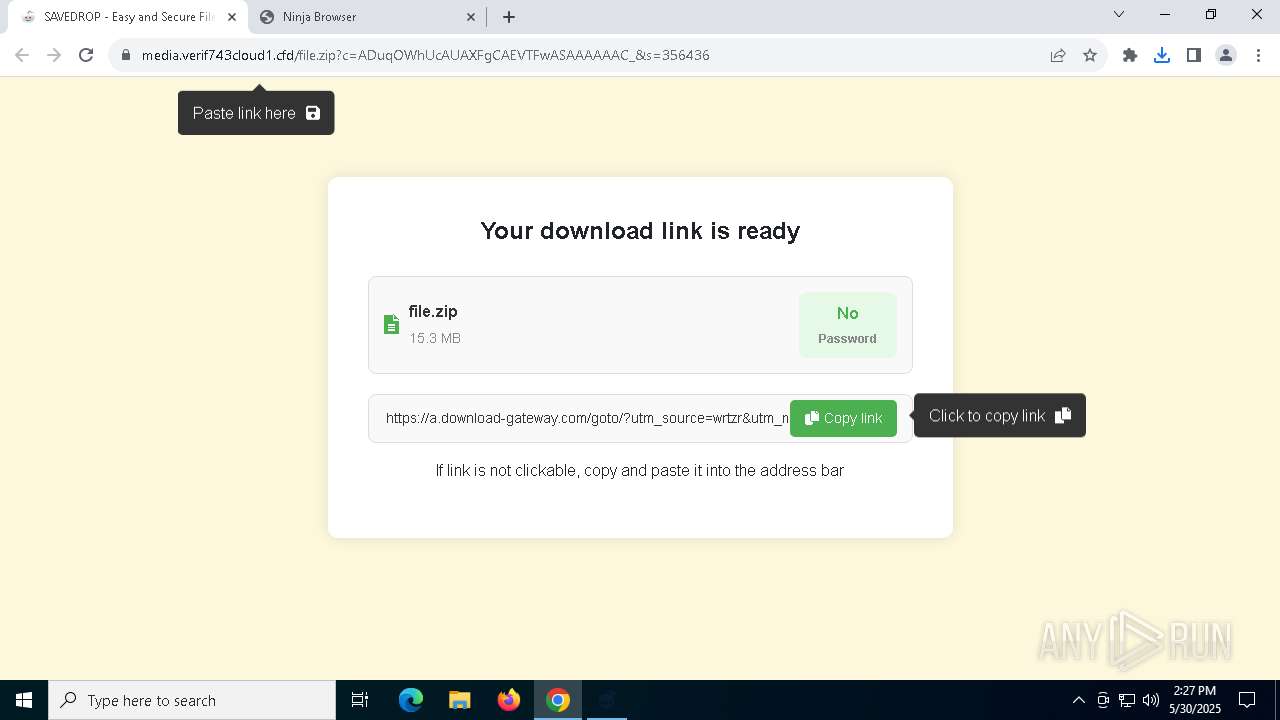
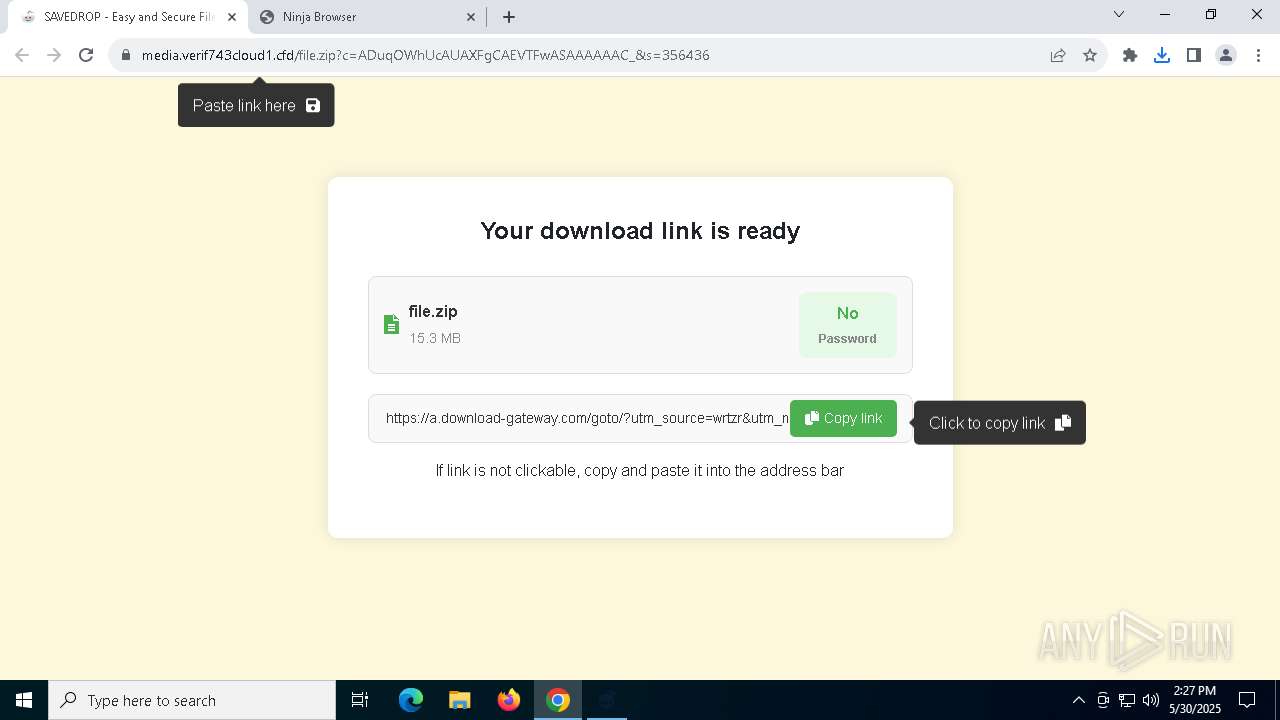
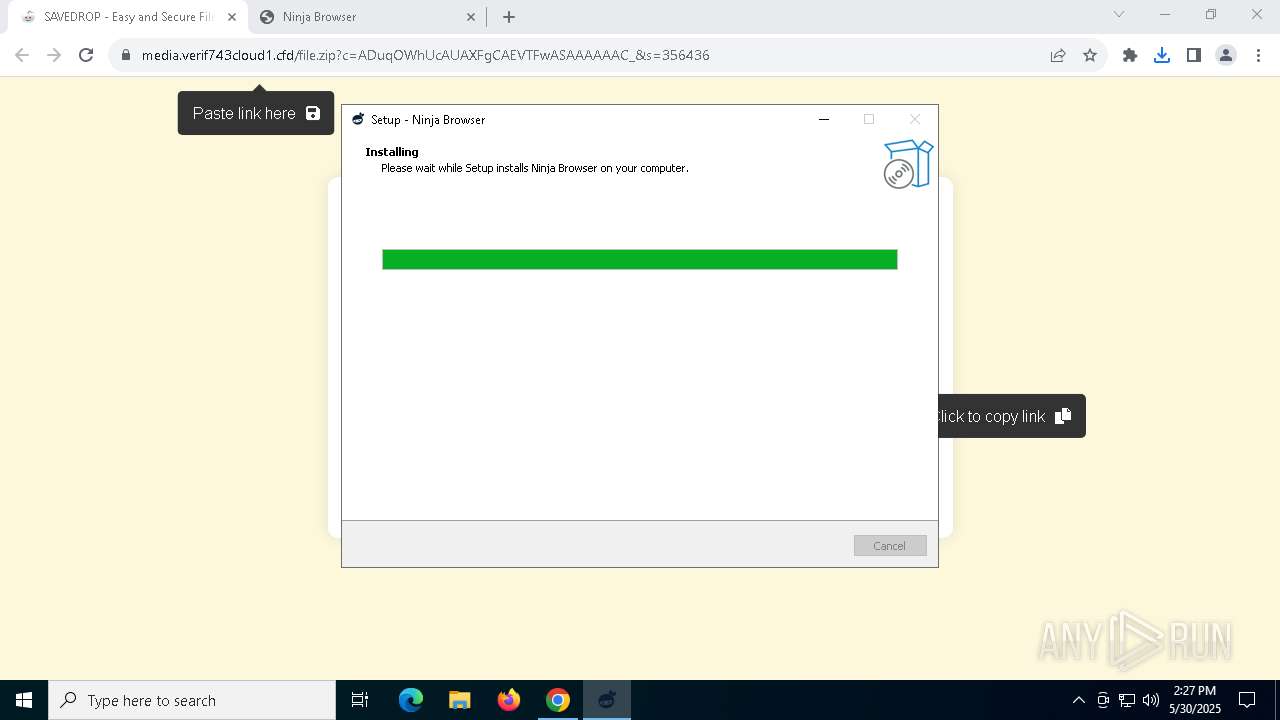
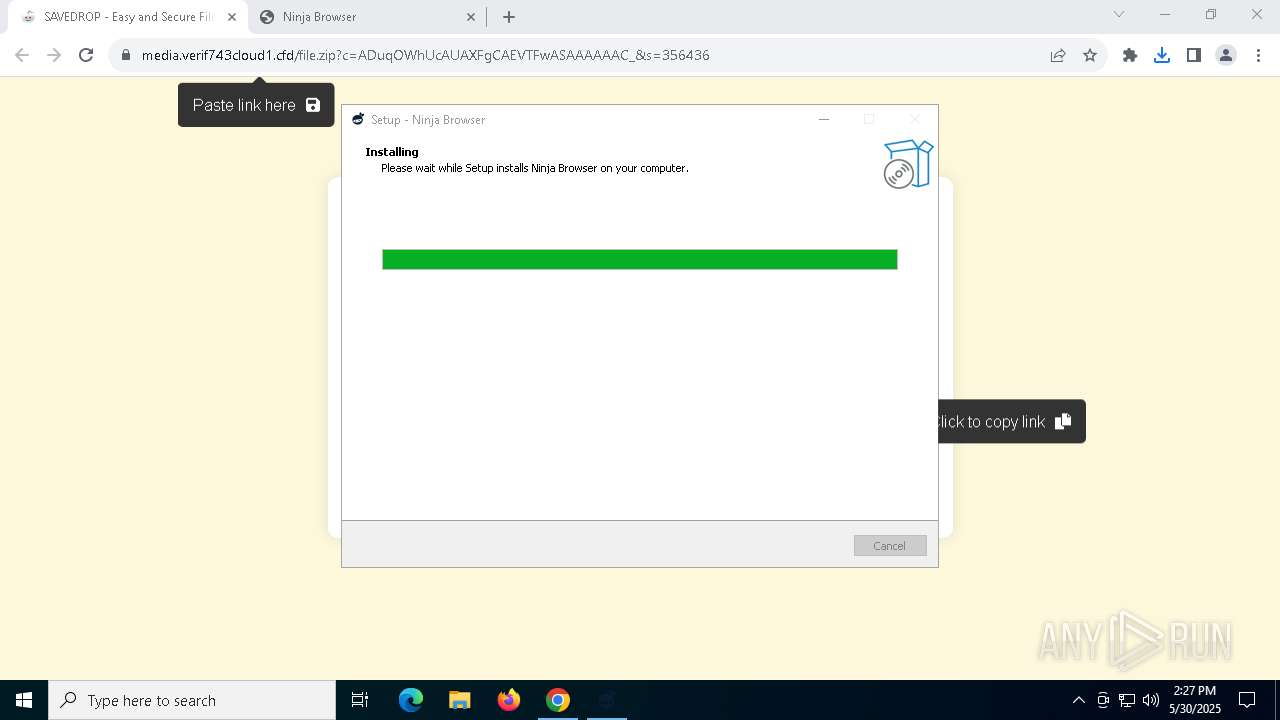
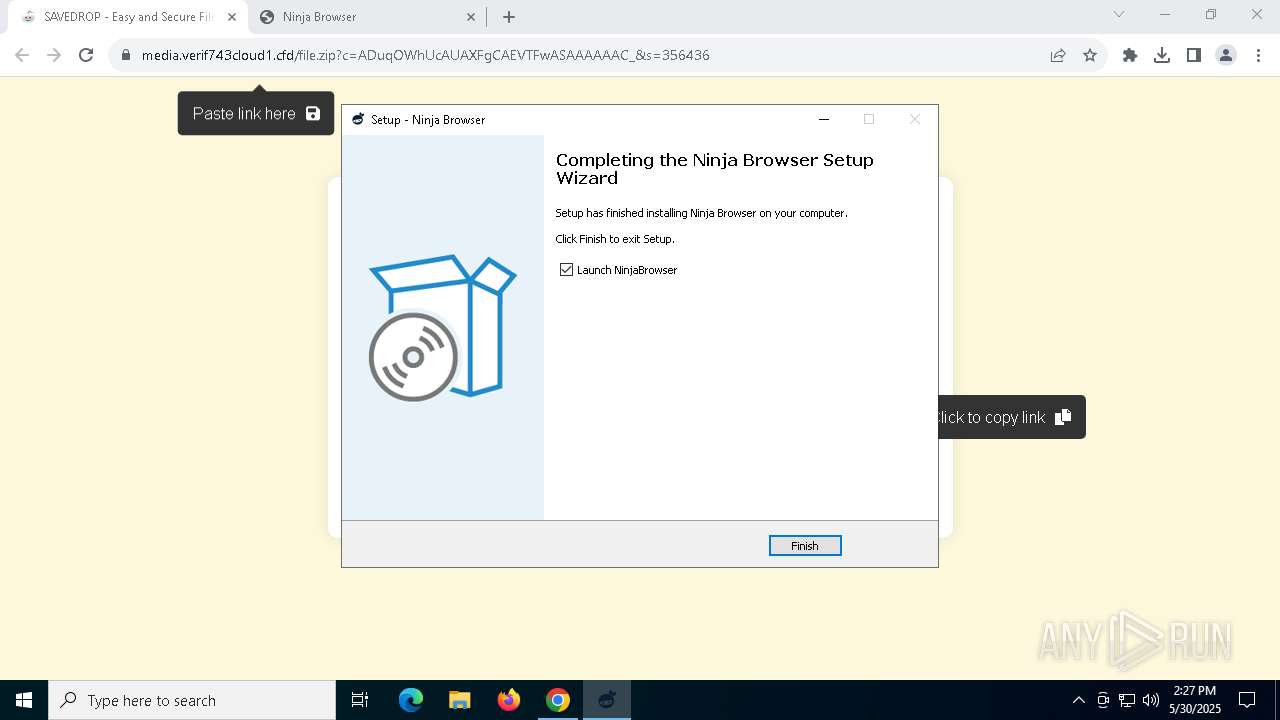
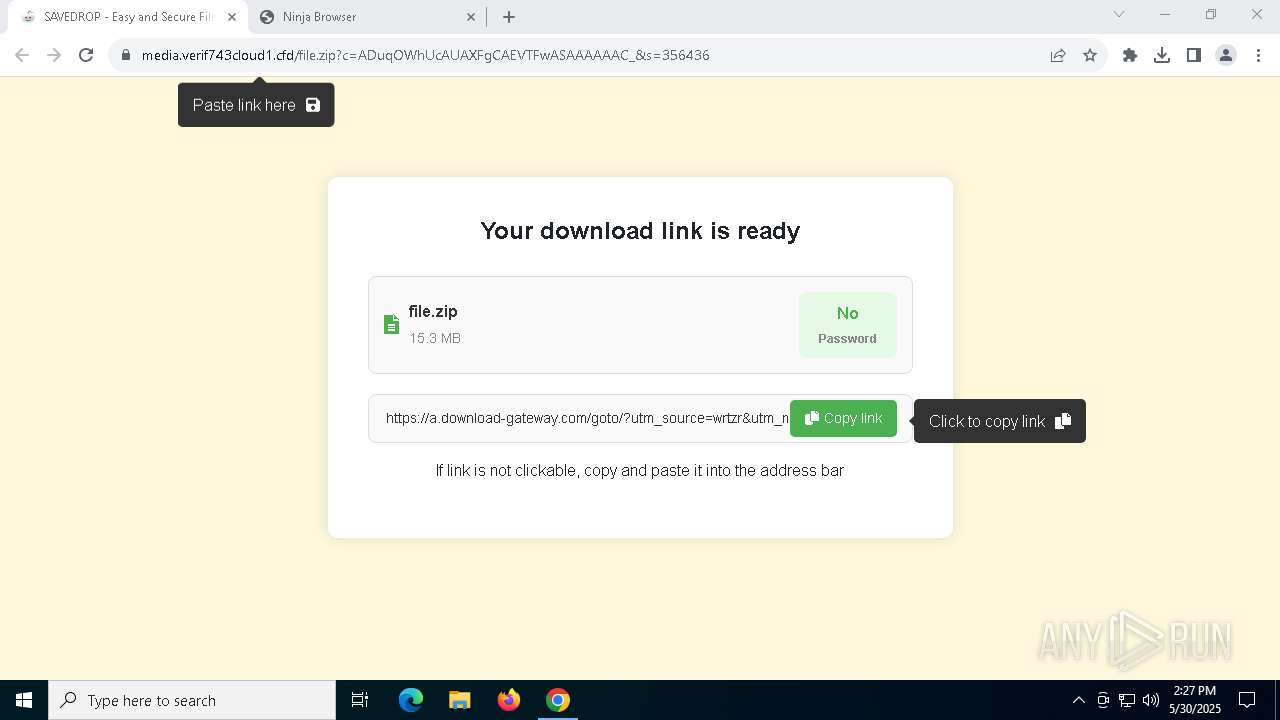
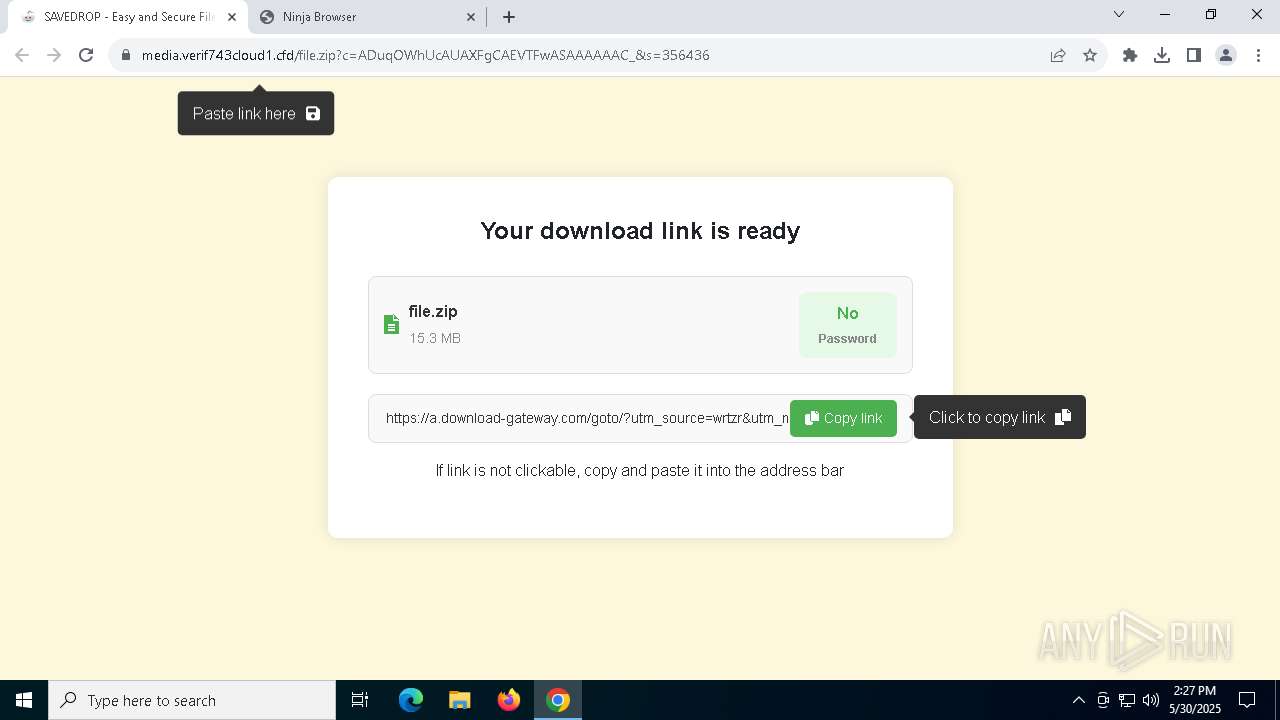
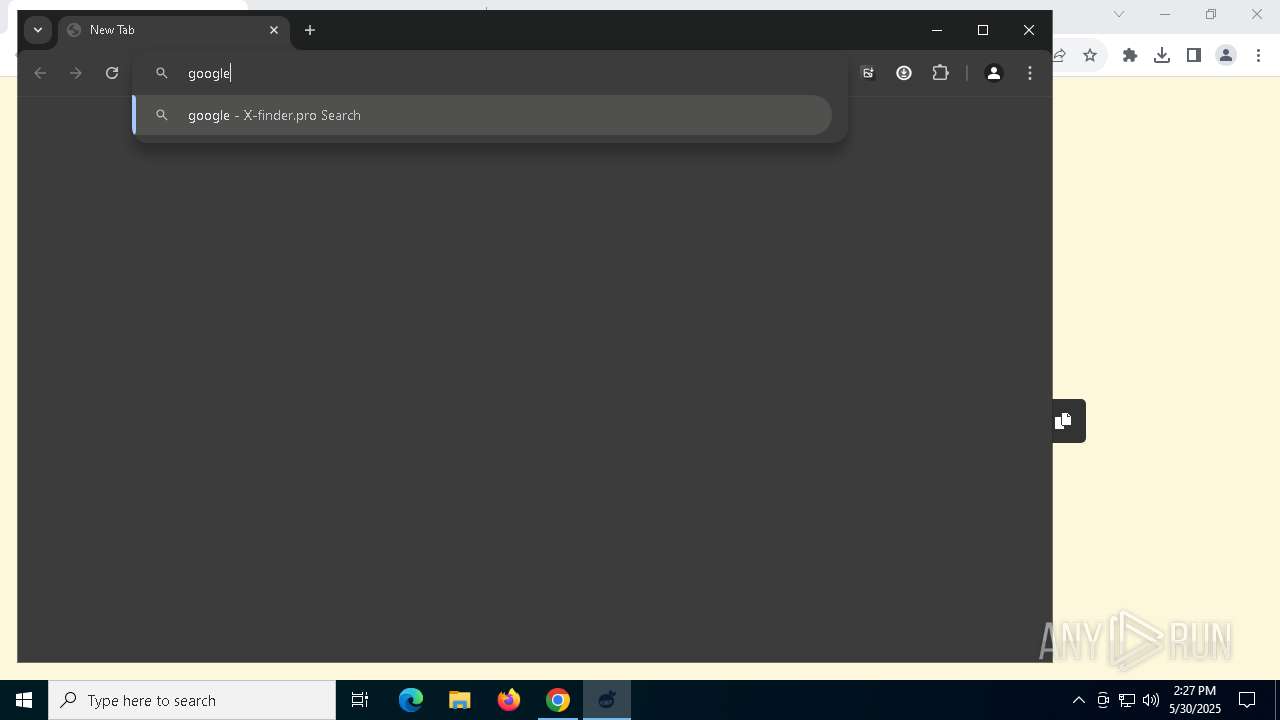
| URL: | media.verif743cloud1.cfd/file.zip?c=ADuqOWhUcAUAXFgCAEVTFwASAAAAAAC_&s=356436 |
| Full analysis: | https://app.any.run/tasks/a27c9f2a-ff68-4b69-96ab-e3013cbb4b2f |
| Verdict: | Malicious activity |
| Analysis date: | May 30, 2025, 14:25:46 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MD5: | E30D8BA45C7EE70D73624F5B0C2F1966 |
| SHA1: | 770ED1FF23A61CDE6297AAED3A5F0AB783F47402 |
| SHA256: | 8BE134E1C98BDCA7914136B1845F0FEBEB62DC4FE8936023DFDF2CBE3AC98DD2 |
| SSDEEP: | 3:9fyyQoGnwcqkUofWQdUn:9Qzl+l |
MALICIOUS
GENERIC has been found (auto)
- chrome.exe (PID: 6564)
- NinjaBrowser_0zyi98buVK.tmp (PID: 1348)
PHISHING has been detected (SURICATA)
- svchost.exe (PID: 2196)
Changes the autorun value in the registry
- setup.exe (PID: 7400)
Uses Task Scheduler to run other applications
- NinjaBrowser_0zyi98buVK.tmp (PID: 1348)
Uses Task Scheduler to autorun other applications
- NinjaBrowser_0zyi98buVK.tmp (PID: 1348)
Creates a new registry key or changes the value of an existing one (SCRIPT)
- mshta.exe (PID: 8048)
- mshta.exe (PID: 7980)
- mshta.exe (PID: 3804)
SUSPICIOUS
Reads the Windows owner or organization settings
- NinjaBrowser_0zyi98buVK.tmp (PID: 1348)
Executable content was dropped or overwritten
- NinjaBrowser_0zyi98buVK.exe (PID: 6988)
- NinjaBrowser_0zyi98buVK.tmp (PID: 1348)
- NinjaBrowser_0zyi98buVK.exe (PID: 8028)
- setup.exe (PID: 7400)
- chromium.exe (PID: 7604)
- chromium.exe (PID: 3240)
- setup.exe (PID: 4152)
Reads security settings of Internet Explorer
- NinjaBrowser_0zyi98buVK.tmp (PID: 8036)
Creates a software uninstall entry
- setup.exe (PID: 7400)
Application launched itself
- setup.exe (PID: 7400)
- NinjaBrowser.exe (PID: 8056)
Searches for installed software
- setup.exe (PID: 7400)
- setup.exe (PID: 7392)
- setup.exe (PID: 4152)
INFO
Reads the computer name
- NinjaBrowser_0zyi98buVK.tmp (PID: 1348)
- NinjaBrowser_0zyi98buVK.exe (PID: 6988)
- NinjaBrowser_0zyi98buVK.tmp (PID: 8036)
- chromium.exe (PID: 7604)
- setup.exe (PID: 7392)
- setup.exe (PID: 7400)
- chromium.exe (PID: 3240)
- def.exe (PID: 7740)
- def.exe (PID: 4188)
- def.exe (PID: 7536)
- NinjaBrowser.exe (PID: 6972)
- NinjaBrowser.exe (PID: 2908)
- def.exe (PID: 7416)
Executable content was dropped or overwritten
- chrome.exe (PID: 6564)
Create files in a temporary directory
- NinjaBrowser_0zyi98buVK.exe (PID: 8028)
- NinjaBrowser_0zyi98buVK.tmp (PID: 1348)
- NinjaBrowser_0zyi98buVK.exe (PID: 6988)
- chromium.exe (PID: 7604)
- chromium.exe (PID: 3240)
- def.exe (PID: 7740)
- def.exe (PID: 4188)
- def.exe (PID: 6184)
Checks supported languages
- NinjaBrowser_0zyi98buVK.exe (PID: 8028)
- NinjaBrowser_0zyi98buVK.tmp (PID: 8036)
- NinjaBrowser_0zyi98buVK.tmp (PID: 1348)
- NinjaBrowser_0zyi98buVK.exe (PID: 6988)
- setup.exe (PID: 7400)
- chromium.exe (PID: 7604)
- setup.exe (PID: 7392)
- setup.exe (PID: 4152)
- chromium.exe (PID: 3240)
- def.exe (PID: 7740)
- def.exe (PID: 4188)
- def.exe (PID: 6184)
- def.exe (PID: 7536)
- NinjaBrowser.exe (PID: 8056)
- NinjaBrowser.exe (PID: 2908)
- NinjaBrowser.exe (PID: 6972)
Launch of the file from Downloads directory
- chrome.exe (PID: 6564)
Application launched itself
- chrome.exe (PID: 6564)
Process checks computer location settings
- NinjaBrowser_0zyi98buVK.tmp (PID: 8036)
Reads the software policy settings
- NinjaBrowser_0zyi98buVK.tmp (PID: 1348)
- slui.exe (PID: 7760)
Checks proxy server information
- NinjaBrowser_0zyi98buVK.tmp (PID: 1348)
- NinjaBrowser.exe (PID: 8056)
Compiled with Borland Delphi (YARA)
- NinjaBrowser_0zyi98buVK.exe (PID: 8028)
- NinjaBrowser_0zyi98buVK.tmp (PID: 8036)
- NinjaBrowser_0zyi98buVK.exe (PID: 6988)
- NinjaBrowser_0zyi98buVK.tmp (PID: 1348)
Detects InnoSetup installer (YARA)
- NinjaBrowser_0zyi98buVK.exe (PID: 6988)
- NinjaBrowser_0zyi98buVK.exe (PID: 8028)
- NinjaBrowser_0zyi98buVK.tmp (PID: 1348)
- NinjaBrowser_0zyi98buVK.tmp (PID: 8036)
Creates files in the program directory
- NinjaBrowser_0zyi98buVK.tmp (PID: 1348)
- setup.exe (PID: 7400)
- setup.exe (PID: 7392)
- setup.exe (PID: 4152)
The sample compiled with english language support
- NinjaBrowser_0zyi98buVK.tmp (PID: 1348)
- setup.exe (PID: 7400)
- chromium.exe (PID: 3240)
- setup.exe (PID: 4152)
- chromium.exe (PID: 7604)
Launch of the file from Registry key
- setup.exe (PID: 7400)
Creates files or folders in the user directory
- setup.exe (PID: 7392)
- NinjaBrowser.exe (PID: 8056)
Launch of the file from Task Scheduler
- NinjaBrowser_0zyi98buVK.tmp (PID: 1348)
Reads Internet Explorer settings
- mshta.exe (PID: 7980)
- mshta.exe (PID: 2064)
- mshta.exe (PID: 7948)
- mshta.exe (PID: 8048)
- mshta.exe (PID: 3804)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
263
Monitored processes
126
Malicious processes
12
Suspicious processes
4
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 208 | "C:\Program Files (x86)\NinjaBrowser\NinjaBrowser\Application\NinjaBrowser.exe" --type=utility --utility-sub-type=unzip.mojom.Unzipper --lang=en-US --service-sandbox-type=service --field-trial-handle=4384,i,12236869155553310733,7889022294954743855,262144 --variations-seed-version --mojo-platform-channel-handle=4436 /prefetch:8 | C:\Program Files (x86)\NinjaBrowser\NinjaBrowser\Application\NinjaBrowser.exe | — | NinjaBrowser.exe | |||||||||||
User: admin Company: The Ninja Browser Authors Integrity Level: LOW Description: Ninja Browser Exit code: 0 Version: 135.0.6613.124 Modules
| |||||||||||||||
| 736 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | def.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 736 | "C:\Program Files (x86)\NinjaBrowser\NinjaBrowser\Application\135.0.6613.124\Installer\chrmstp.exe" --configure-user-settings --verbose-logging --system-level --force-configure-user-settings | C:\Program Files (x86)\NinjaBrowser\NinjaBrowser\Application\135.0.6613.124\Installer\chrmstp.exe | — | NinjaBrowser.exe | |||||||||||
User: admin Company: The Ninja Browser Authors Integrity Level: MEDIUM Description: Ninja Browser Installer Exit code: 0 Version: 135.0.6613.124 | |||||||||||||||
| 872 | "C:\Program Files (x86)\NinjaBrowser\NinjaBrowser\Application\NinjaBrowser.exe" --type=utility --utility-sub-type=unzip.mojom.Unzipper --lang=en-US --service-sandbox-type=service --field-trial-handle=3236,i,12236869155553310733,7889022294954743855,262144 --variations-seed-version --mojo-platform-channel-handle=4084 /prefetch:8 | C:\Program Files (x86)\NinjaBrowser\NinjaBrowser\Application\NinjaBrowser.exe | — | NinjaBrowser.exe | |||||||||||
User: admin Company: The Ninja Browser Authors Integrity Level: LOW Description: Ninja Browser Exit code: 0 Version: 135.0.6613.124 Modules
| |||||||||||||||
| 920 | "C:\Program Files (x86)\NinjaBrowser\NinjaBrowser\Application\NinjaBrowser.exe" --type=utility --utility-sub-type=unzip.mojom.Unzipper --lang=en-US --service-sandbox-type=service --field-trial-handle=8824,i,12236869155553310733,7889022294954743855,262144 --variations-seed-version --mojo-platform-channel-handle=8836 /prefetch:8 | C:\Program Files (x86)\NinjaBrowser\NinjaBrowser\Application\NinjaBrowser.exe | — | NinjaBrowser.exe | |||||||||||
User: admin Company: The Ninja Browser Authors Integrity Level: LOW Description: Ninja Browser Exit code: 0 Version: 135.0.6613.124 Modules
| |||||||||||||||
| 924 | "C:\Program Files (x86)\NinjaBrowser\NinjaBrowser\Application\NinjaBrowser.exe" --type=utility --utility-sub-type=unzip.mojom.Unzipper --lang=en-US --service-sandbox-type=service --field-trial-handle=4344,i,12236869155553310733,7889022294954743855,262144 --variations-seed-version --mojo-platform-channel-handle=4396 /prefetch:8 | C:\Program Files (x86)\NinjaBrowser\NinjaBrowser\Application\NinjaBrowser.exe | — | NinjaBrowser.exe | |||||||||||
User: admin Company: The Ninja Browser Authors Integrity Level: LOW Description: Ninja Browser Exit code: 0 Version: 135.0.6613.124 Modules
| |||||||||||||||
| 1012 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=quarantine.mojom.Quarantine --lang=en-US --service-sandbox-type=none --disable-quic --no-appcompat-clear --mojo-platform-channel-handle=5832 --field-trial-handle=1820,i,11692411891425489034,7466216937818266214,262144 --disable-features=OptimizationGuideModelDownloading,OptimizationHints,OptimizationHintsFetching,OptimizationTargetPrediction --variations-seed-version /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 122.0.6261.70 Modules
| |||||||||||||||
| 1072 | "C:\Program Files (x86)\NinjaBrowser\NinjaBrowser\Application\NinjaBrowser.exe" --type=utility --utility-sub-type=data_decoder.mojom.DataDecoderService --lang=en-US --service-sandbox-type=service --field-trial-handle=6436,i,12236869155553310733,7889022294954743855,262144 --variations-seed-version --mojo-platform-channel-handle=8212 /prefetch:8 | C:\Program Files (x86)\NinjaBrowser\NinjaBrowser\Application\NinjaBrowser.exe | — | NinjaBrowser.exe | |||||||||||
User: admin Company: The Ninja Browser Authors Integrity Level: LOW Description: Ninja Browser Exit code: 0 Version: 135.0.6613.124 Modules
| |||||||||||||||
| 1128 | "C:\Program Files (x86)\NinjaBrowser\NinjaBrowser\Application\NinjaBrowser.exe" --type=utility --utility-sub-type=unzip.mojom.Unzipper --lang=en-US --service-sandbox-type=service --field-trial-handle=4720,i,12236869155553310733,7889022294954743855,262144 --variations-seed-version --mojo-platform-channel-handle=4748 /prefetch:8 | C:\Program Files (x86)\NinjaBrowser\NinjaBrowser\Application\NinjaBrowser.exe | — | NinjaBrowser.exe | |||||||||||
User: admin Company: The Ninja Browser Authors Integrity Level: LOW Description: Ninja Browser Exit code: 0 Version: 135.0.6613.124 Modules
| |||||||||||||||
| 1348 | "C:\Users\admin\AppData\Local\Temp\is-6GQIG.tmp\NinjaBrowser_0zyi98buVK.tmp" /SL5="$60348,932127,896512,C:\Users\admin\Downloads\NinjaBrowser_0zyi98buVK.exe" /SPAWNWND=$5034A /NOTIFYWND=$E0352 | C:\Users\admin\AppData\Local\Temp\is-6GQIG.tmp\NinjaBrowser_0zyi98buVK.tmp | NinjaBrowser_0zyi98buVK.exe | ||||||||||||
User: admin Company: Ninja Browser Integrity Level: HIGH Description: Setup/Uninstall Exit code: 0 Version: 51.1052.0.0 Modules
| |||||||||||||||
Total events
14 439
Read events
14 265
Write events
163
Delete events
11
Modification events
| (PID) Process: | (6564) chrome.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Google\Chrome\BLBeacon |
| Operation: | write | Name: | failed_count |
Value: 0 | |||
| (PID) Process: | (6564) chrome.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Google\Chrome\BLBeacon |
| Operation: | write | Name: | state |
Value: 2 | |||
| (PID) Process: | (6564) chrome.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Google\Chrome\BLBeacon |
| Operation: | write | Name: | state |
Value: 1 | |||
| (PID) Process: | (6564) chrome.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Google\Chrome\StabilityMetrics |
| Operation: | write | Name: | user_experience_metrics.stability.exited_cleanly |
Value: 0 | |||
| (PID) Process: | (6564) chrome.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Google\Update\ClientStateMedium\{8A69D345-D564-463C-AFF1-A69D9E530F96} |
| Operation: | write | Name: | usagestats |
Value: 0 | |||
| (PID) Process: | (6564) chrome.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Google\Common\Rlz\Events\C |
| Operation: | write | Name: | C1F |
Value: 1 | |||
| (PID) Process: | (1012) chrome.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Shell Extensions\Cached |
| Operation: | write | Name: | {2781761E-28E0-4109-99FE-B9D127C57AFE} {56FFCC30-D398-11D0-B2AE-00A0C908FA49} 0xFFFF |
Value: 010000000000000069872ADB6ED1DB01 | |||
| (PID) Process: | (7400) setup.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\NinjaBrowser |
| Operation: | write | Name: | InstallerProgress |
Value: 19 | |||
| (PID) Process: | (7400) setup.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\NinjaBrowser |
| Operation: | write | Name: | InstallerProgress |
Value: 25 | |||
| (PID) Process: | (6564) chrome.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Google\Common\Rlz\RLZs |
| Operation: | write | Name: | C1 |
Value: 1C1GCEB_enGB1164GB1164 | |||
Executable files
21
Suspicious files
539
Text files
932
Unknown types
147
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 6564 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\coupon_db\LOG.old~RF10c8b1.TMP | — | |
MD5:— | SHA256:— | |||
| 6564 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\commerce_subscription_db\LOG.old~RF10c8b1.TMP | — | |
MD5:— | SHA256:— | |||
| 6564 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\coupon_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 6564 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\PersistentOriginTrials\LOG.old~RF10c8b1.TMP | — | |
MD5:— | SHA256:— | |||
| 6564 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\PersistentOriginTrials\LOG.old | — | |
MD5:— | SHA256:— | |||
| 6564 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\discounts_db\LOG.old~RF10c8b1.TMP | — | |
MD5:— | SHA256:— | |||
| 6564 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\discounts_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 6564 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\commerce_subscription_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 6564 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\parcel_tracking_db\LOG.old~RF10c8c0.TMP | — | |
MD5:— | SHA256:— | |||
| 6564 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\chrome_cart_db\LOG.old~RF10c8c0.TMP | — | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
14
TCP/UDP connections
69
DNS requests
99
Threats
28
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
5496 | MoUsoCoreWorker.exe | GET | 200 | 2.16.168.114:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
2104 | svchost.exe | GET | 200 | 2.16.168.114:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
5496 | MoUsoCoreWorker.exe | GET | 200 | 2.23.246.101:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
6544 | svchost.exe | GET | 200 | 184.30.131.245:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
8104 | SIHClient.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
2104 | svchost.exe | GET | 200 | 2.23.246.101:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
8104 | SIHClient.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
3896 | svchost.exe | GET | 206 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/chromewebstore/L2Nocm9tZV9leHRlbnNpb24vYmxvYnMvYjhkYWYwZDctOTExOS00MGQ5LTgyNjAtN2FlY2ZjMDg0NmNj/1.0.0.17_llkgjffcdpffmhiakmfcdcblohccpfmo.crx | unknown | — | — | whitelisted |
6564 | chrome.exe | GET | 200 | 151.101.194.133:80 | http://ocsp.globalsign.com/codesigningrootr45/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQVFZP5vqhCrtRN5SWf40Rn6NM1IAQUHwC%2FRoAK%2FHg5t6W0Q9lWULvOljsCEHe9DgW3WQu2HUdhUx4%2Fde0%3D | unknown | — | — | whitelisted |
6564 | chrome.exe | GET | 200 | 151.101.194.133:80 | http://ocsp.globalsign.com/gsgccr45evcodesignca2020/ME0wSzBJMEcwRTAJBgUrDgMCGgUABBQaCbVYh07WONuW4e63Ydlu4AlbDAQUJZ3Q%2FFkJhmPF7POxEztXHAOSNhECDB4WVKmt8yfHHrQPdw%3D%3D | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
— | — | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
5496 | MoUsoCoreWorker.exe | 2.16.168.114:80 | crl.microsoft.com | Akamai International B.V. | RU | whitelisted |
2104 | svchost.exe | 2.16.168.114:80 | crl.microsoft.com | Akamai International B.V. | RU | whitelisted |
5496 | MoUsoCoreWorker.exe | 2.23.246.101:80 | www.microsoft.com | Ooredoo Q.S.C. | QA | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
2104 | svchost.exe | 2.23.246.101:80 | www.microsoft.com | Ooredoo Q.S.C. | QA | whitelisted |
3216 | svchost.exe | 172.211.123.248:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | FR | whitelisted |
6564 | chrome.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
7220 | chrome.exe | 104.21.48.1:443 | media.verif743cloud1.cfd | CLOUDFLARENET | — | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
google.com |
| whitelisted |
settings-win.data.microsoft.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
media.verif743cloud1.cfd |
| unknown |
accounts.google.com |
| whitelisted |
cdn.jsdelivr.net |
| whitelisted |
cdnjs.cloudflare.com |
| whitelisted |
content-autofill.googleapis.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
7220 | chrome.exe | Not Suspicious Traffic | INFO [ANY.RUN] Requests to a free CDN for open source projects (jsdelivr .net) |
7220 | chrome.exe | Not Suspicious Traffic | INFO [ANY.RUN] Cloudflare content delivery network (cdnjs .cloudflare .com) |
7220 | chrome.exe | Not Suspicious Traffic | INFO [ANY.RUN] Requests to a free CDN for open source projects (jsdelivr .net) |
7220 | chrome.exe | Not Suspicious Traffic | INFO [ANY.RUN] Cloudflare content delivery network (cdnjs .cloudflare .com) |
7220 | chrome.exe | Potentially Bad Traffic | SUSPICIOUS [ANY.RUN] Suspected Malicious domain by CrossDomain (nb-download .com) |
7220 | chrome.exe | Potentially Bad Traffic | SUSPICIOUS [ANY.RUN] Suspected Malicious domain by CrossDomain (nb-download .com) |
7220 | chrome.exe | Potentially Bad Traffic | SUSPICIOUS [ANY.RUN] Suspected Malicious domain by CrossDomain (nb-download .com) |
7220 | chrome.exe | Potentially Bad Traffic | SUSPICIOUS [ANY.RUN] Suspected Malicious domain by CrossDomain (nb-download .com) |
2196 | svchost.exe | Possible Social Engineering Attempted | PHISHING [ANY.RUN] Suspected Phishing domain by CrossDomain ( .ninja-browser .com) |
— | — | Generic Protocol Command Decode | SURICATA QUIC failed decrypt |