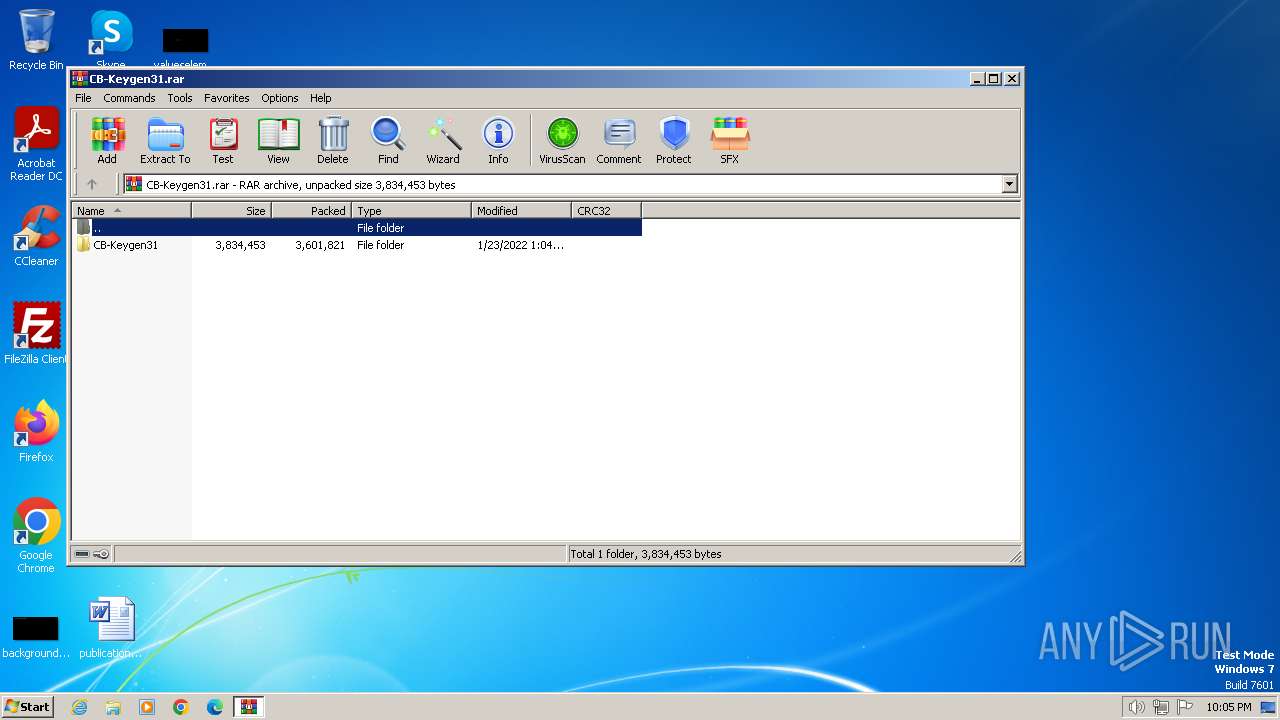
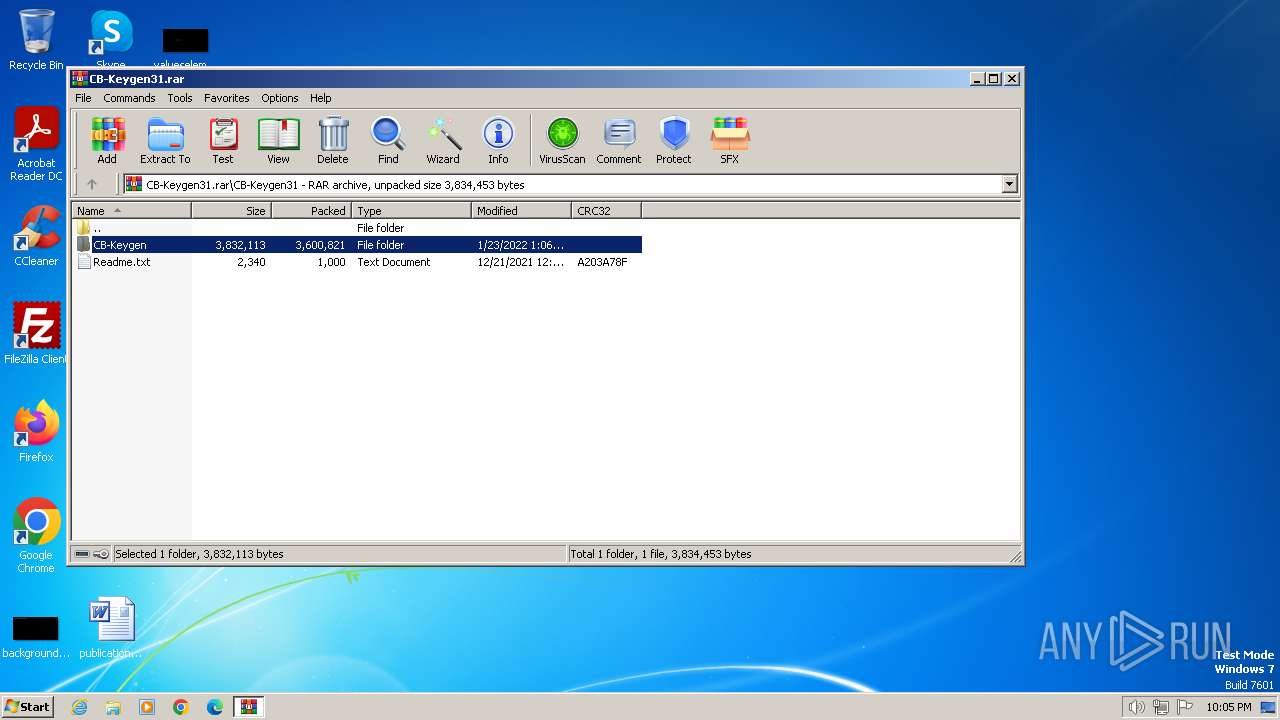
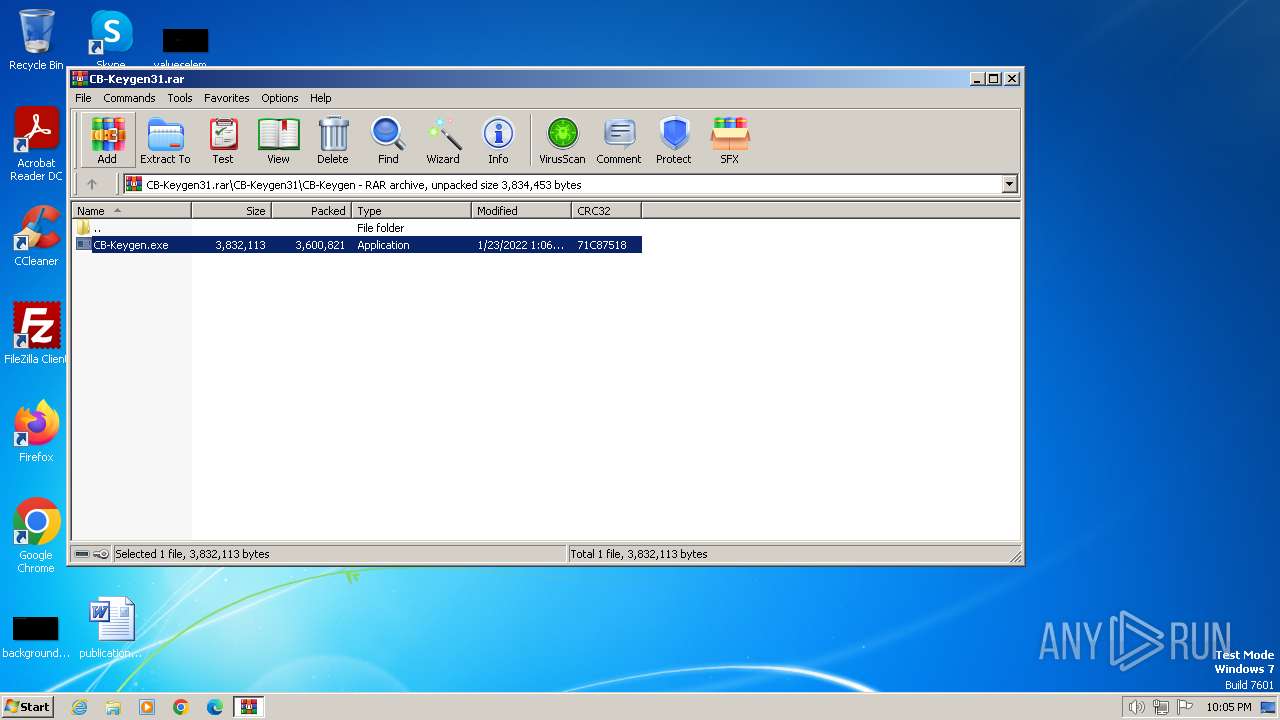
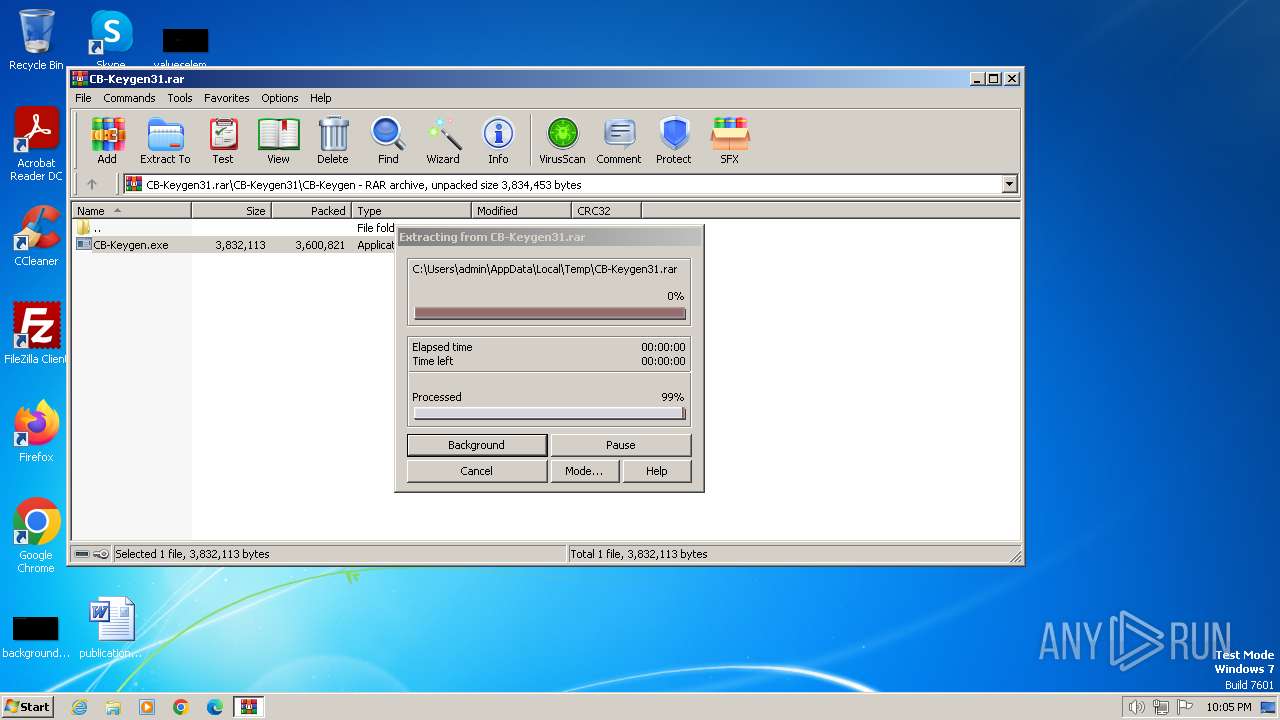
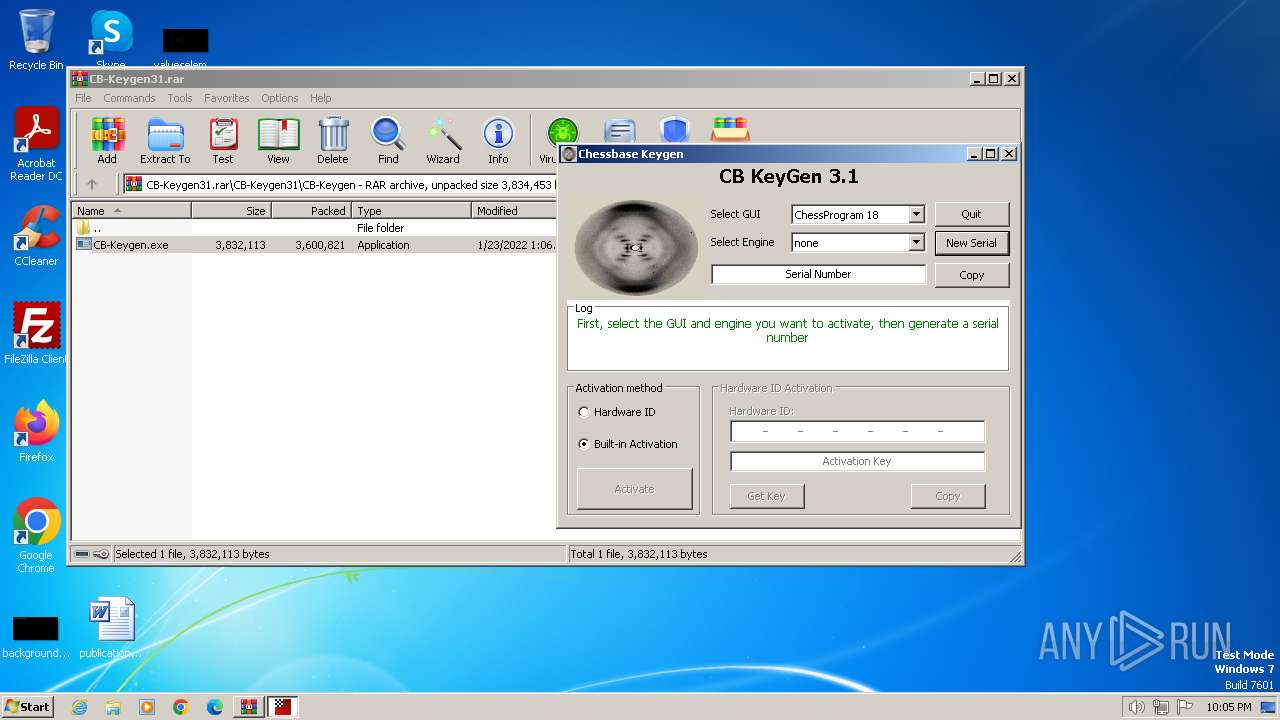
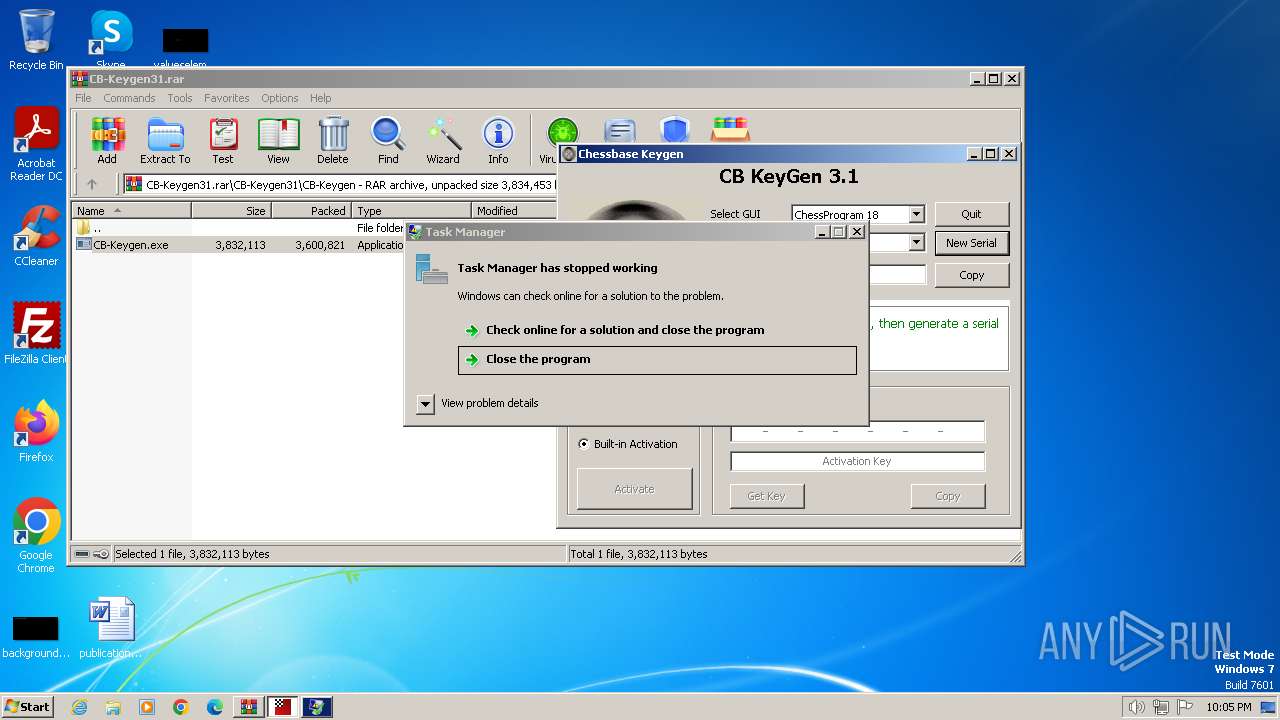
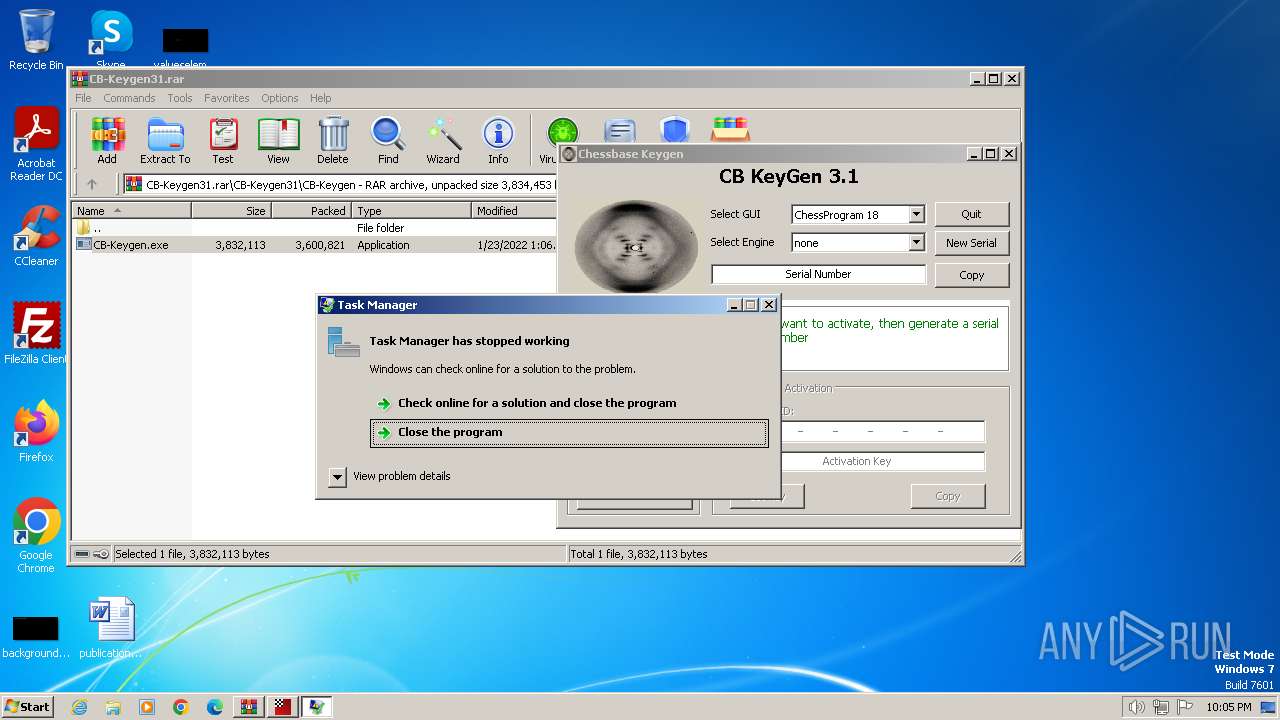
| File name: | CB-Keygen31.rar |
| Full analysis: | https://app.any.run/tasks/20a0cdf8-c41e-4e5c-9605-62dabcbbfd5b |
| Verdict: | Malicious activity |
| Analysis date: | July 14, 2024, 21:04:54 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/x-rar |
| File info: | RAR archive data, v5 |
| MD5: | 85BEC0369134CBA764A518636695054B |
| SHA1: | B82942ECC68BC1D8864A0263E7989D6B04D28652 |
| SHA256: | 8BB5D275C7CB2115514788C4545C4062FA8CC9A9B477649928BA305C7879EC34 |
| SSDEEP: | 98304:T+1a9KkbaValpZLTNIdZM9rTijpqo9r/zaV8HRmVZxeaRspcCES2MkoVM9kvpqqo:1rHIhitX |
MALICIOUS
Drops the executable file immediately after the start
- WinRAR.exe (PID: 3400)
- CB-Keygen.exe (PID: 3308)
SUSPICIOUS
Reads security settings of Internet Explorer
- WinRAR.exe (PID: 3400)
- CB-Keygen.exe (PID: 3308)
- TaskShell.exe (PID: 3100)
The process creates files with name similar to system file names
- CB-Keygen.exe (PID: 3308)
Process drops legitimate windows executable
- CB-Keygen.exe (PID: 3308)
Executable content was dropped or overwritten
- CB-Keygen.exe (PID: 3308)
The process drops C-runtime libraries
- CB-Keygen.exe (PID: 3308)
The process executes VB scripts
- CB-Keygen.exe (PID: 3308)
Reads the Internet Settings
- CB-Keygen.exe (PID: 3308)
- wscript.exe (PID: 3208)
- TaskShell.exe (PID: 3100)
Runs shell command (SCRIPT)
- wscript.exe (PID: 3208)
Starts a Microsoft application from unusual location
- TaskShell.exe (PID: 3100)
Starts POWERSHELL.EXE for commands execution
- TaskShell.exe (PID: 3100)
INFO
Executable content was dropped or overwritten
- WinRAR.exe (PID: 3400)
Checks supported languages
- CB-Keygen.exe (PID: 3308)
- CB_KG.exe (PID: 2936)
- TaskShell.exe (PID: 3100)
Reads the computer name
- CB-Keygen.exe (PID: 3308)
- TaskShell.exe (PID: 3100)
Create files in a temporary directory
- CB-Keygen.exe (PID: 3308)
Reads the machine GUID from the registry
- TaskShell.exe (PID: 3100)
Reads Environment values
- TaskShell.exe (PID: 3100)
Script raised an exception (POWERSHELL)
- powershell.exe (PID: 2940)
Disables trace logs
- TaskShell.exe (PID: 3100)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .rar | | | RAR compressed archive (v5.0) (61.5) |
|---|---|---|
| .rar | | | RAR compressed archive (gen) (38.4) |
Total processes
46
Monitored processes
6
Malicious processes
2
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 2936 | "C:\Users\admin\AppData\Local\Temp\RarSFX0\CB_KG.exe" | C:\Users\admin\AppData\Local\Temp\RarSFX0\CB_KG.exe | — | wscript.exe | |||||||||||
User: admin Integrity Level: MEDIUM Modules
| |||||||||||||||
| 2940 | "C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe" Test-Connection google.com; Test-Connection yahoo.com; Test-Connection youtube.com; Test-Connection google.com | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | — | TaskShell.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Exit code: 0 Version: 10.0.14409.1005 (rs1_srvoob.161208-1155) Modules
| |||||||||||||||
| 3100 | "C:\Users\admin\AppData\Local\Temp\RarSFX0\TaskShell.exe" | C:\Users\admin\AppData\Local\Temp\RarSFX0\TaskShell.exe | wscript.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Task Manager Version: 10.0.22000.65 Modules
| |||||||||||||||
| 3208 | "C:\Windows\System32\WScript.exe" "C:\Users\admin\AppData\Local\Temp\RarSFX0\sfdgdgfghdsertrgdfsfwrrerggr.vbs" | C:\Windows\System32\wscript.exe | — | CB-Keygen.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft ® Windows Based Script Host Exit code: 0 Version: 5.8.7600.16385 Modules
| |||||||||||||||
| 3308 | "C:\Users\admin\AppData\Local\Temp\Rar$EXa3400.41737\CB-Keygen31\CB-Keygen\CB-Keygen.exe" | C:\Users\admin\AppData\Local\Temp\Rar$EXa3400.41737\CB-Keygen31\CB-Keygen\CB-Keygen.exe | WinRAR.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 3400 | "C:\Program Files\WinRAR\WinRAR.exe" C:\Users\admin\AppData\Local\Temp\CB-Keygen31.rar | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Version: 5.91.0 Modules
| |||||||||||||||
Total events
12 828
Read events
12 772
Write events
56
Delete events
0
Modification events
| (PID) Process: | (3400) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (3400) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (3400) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\182\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (3400) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\phacker.zip | |||
| (PID) Process: | (3400) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\Win7-KB3191566-x86.zip | |||
| (PID) Process: | (3400) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\curl-8.5.0_1-win32-mingw.zip | |||
| (PID) Process: | (3400) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\CB-Keygen31.rar | |||
| (PID) Process: | (3400) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (3400) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (3400) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
Executable files
7
Suspicious files
3
Text files
8
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3400 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa3400.41737\CB-Keygen31\CB-Keygen\CB-Keygen.exe | executable | |
MD5:6175B9A4A2C670119F76D4486DD30BBA | SHA256:56838CABFFCDD560C02804CBCF3BC4B04892FC055BDB969B85CD8387E4C8F357 | |||
| 3308 | CB-Keygen.exe | C:\Users\admin\AppData\Local\Temp\RarSFX0\SView3.dll | executable | |
MD5:42C88D91B51436BB0D3D5B2F35FA73DE | SHA256:F8399BCD60601667B3A23BC6893F9D3E6B1683C53C8A3D39E92271F557F84E0A | |||
| 3308 | CB-Keygen.exe | C:\Users\admin\AppData\Local\Temp\RarSFX0\TaskShell.exe | executable | |
MD5:064CA8586ECF62D9AE4C6BCB60EAC31A | SHA256:541D22E662F0B557B2EFEA53F3558F8C93E930D9E0347682983D80BB749166C3 | |||
| 3308 | CB-Keygen.exe | C:\Users\admin\AppData\Local\Temp\RarSFX0\Messages\Deutsch\Frame.strings | text | |
MD5:73FBE3F89DC743B87138026CE5FF3C0F | SHA256:4B0BC1FA9E43E7CE547FF1450C03EBBEF2F8FA1651876DBC0A26875B88AD2D71 | |||
| 3308 | CB-Keygen.exe | C:\Users\admin\AppData\Local\Temp\RarSFX0\CB_KG.exe | executable | |
MD5:C643FFD35FA59C679967E72AC18076C1 | SHA256:99BD21DE291DFF07762463787A7D511DAA3B80A97FDBC7791038CBF48E1EC919 | |||
| 3308 | CB-Keygen.exe | C:\Users\admin\AppData\Local\Temp\RarSFX0\msvcp140.dll | executable | |
MD5:C092885EA11BD80D35CB55C7D488F1E2 | SHA256:885A0A146A83B0D5A19B88C4EB6372B648CFAED817BD31D8CD3FB91313DEA13D | |||
| 3308 | CB-Keygen.exe | C:\Users\admin\AppData\Local\Temp\RarSFX0\vcruntime140.dll | executable | |
MD5:31CE620CB32AC950D31E019E67EFC638 | SHA256:1E0F8F7F13502F5CEE17232E9BEBCA7B44DD6EC29F1842BB61033044C65B2BBF | |||
| 3308 | CB-Keygen.exe | C:\Users\admin\AppData\Local\Temp\RarSFX0\Messages\Countries.inc | text | |
MD5:200710201C95F4E8A612299B132289DA | SHA256:A1FF5302B95A293433F77DB64B40F04A2BD6706521CF0A8702991D88378B015C | |||
| 3308 | CB-Keygen.exe | C:\Users\admin\AppData\Local\Temp\RarSFX0\mfc140.dll | executable | |
MD5:C594917D6C51B6696CAA3C707BC435BF | SHA256:6E668ACF6F4FC3FBED14C89CFA80AE38E49B09AC9035DF698C191A217C6D0BC0 | |||
| 3308 | CB-Keygen.exe | C:\Users\admin\AppData\Local\Temp\RarSFX0\Messages\Deutsch\Countries.strings | text | |
MD5:E831412DB1A96BBA8BEFA223EF2849D6 | SHA256:637829E1E9198E5ED1C6B6B2AB2D8E8FF7E9B0BD02005272FD56E6C48C093555 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
4
TCP/UDP connections
13
DNS requests
10
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
1372 | svchost.exe | GET | 304 | 93.184.221.240:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?33775f6043c93e33 | unknown | — | — | whitelisted |
1372 | svchost.exe | GET | 200 | 23.48.23.164:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
1372 | svchost.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
1060 | svchost.exe | GET | 304 | 199.232.214.172:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?67a3611ec3c0260d | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
— | — | 224.0.0.252:5355 | — | — | — | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
1372 | svchost.exe | 51.104.136.2:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
1060 | svchost.exe | 224.0.0.252:5355 | — | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
2564 | svchost.exe | 239.255.255.250:3702 | — | — | — | whitelisted |
1372 | svchost.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
1372 | svchost.exe | 93.184.221.240:80 | ctldl.windowsupdate.com | EDGECAST | GB | whitelisted |
1372 | svchost.exe | 23.48.23.164:80 | crl.microsoft.com | Akamai International B.V. | DE | unknown |
1372 | svchost.exe | 184.30.21.171:80 | www.microsoft.com | AKAMAI-AS | DE | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
google.com |
| whitelisted |
yahoo.com |
| whitelisted |
settings-win.data.microsoft.com |
| whitelisted |
ctldl.windowsupdate.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
youtube.com |
| whitelisted |
taskmgrdev.com |
| unknown |