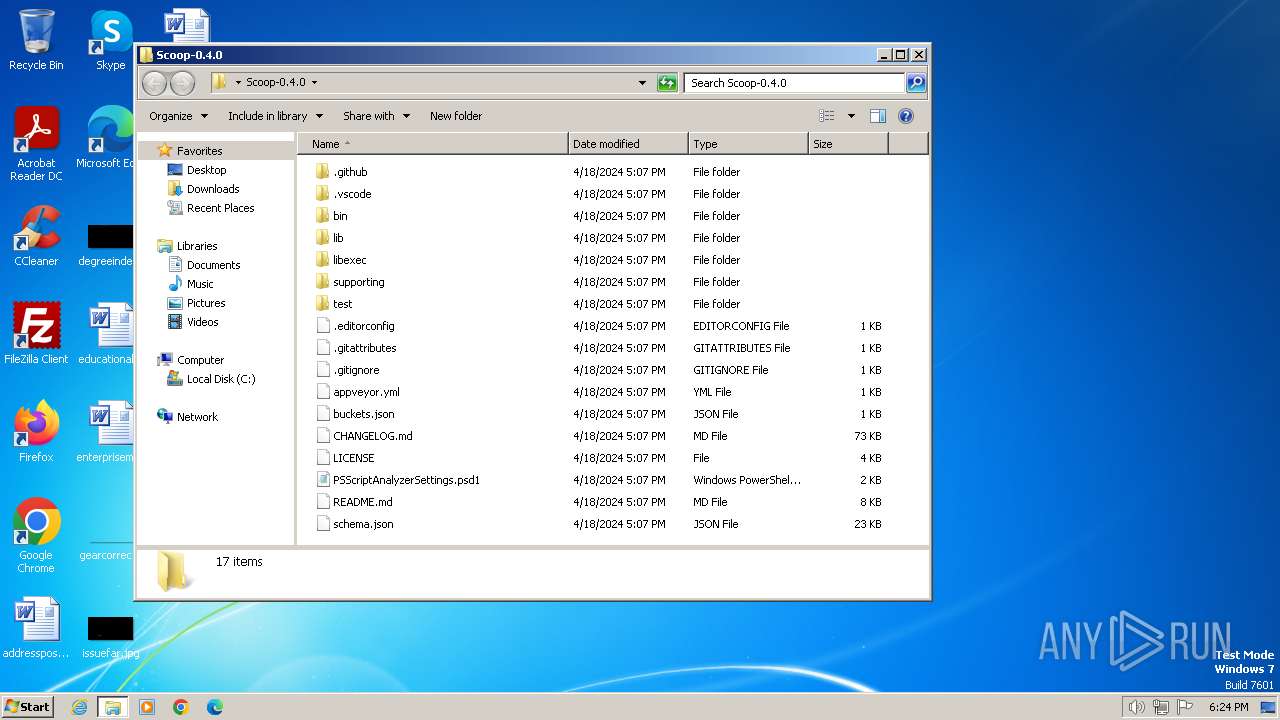
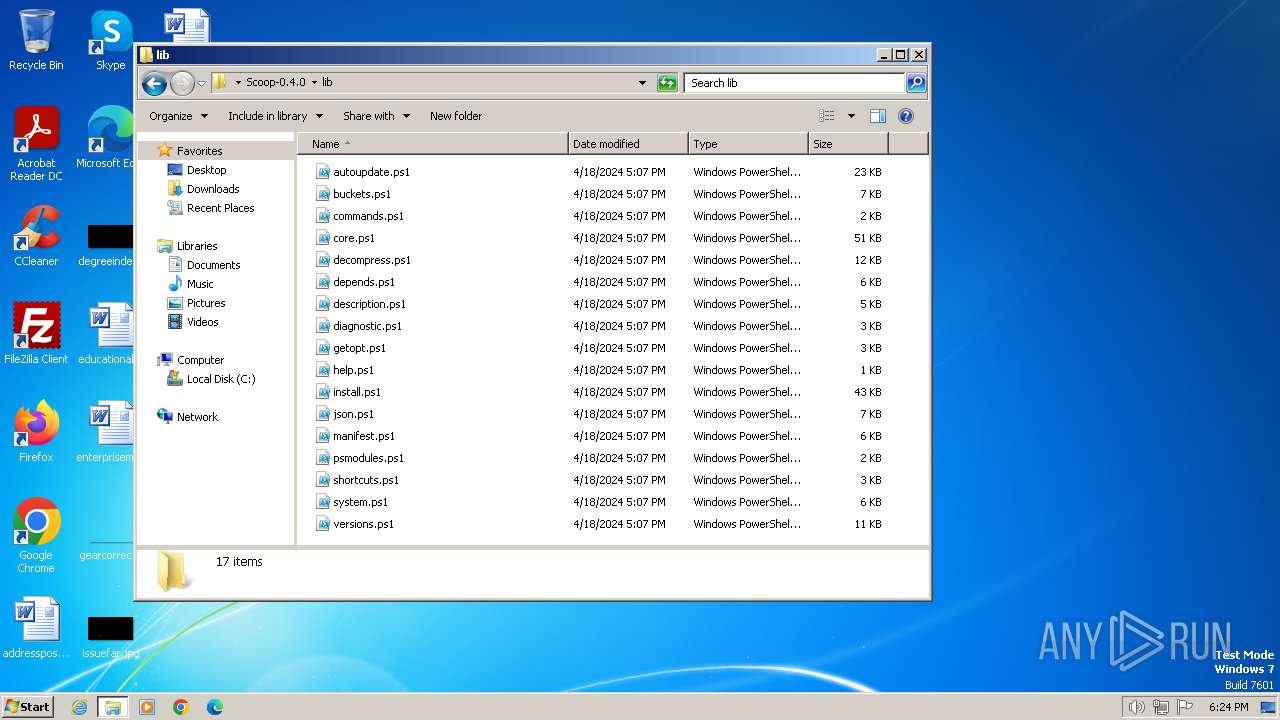
| File name: | Scoop-0.4.0.zip |
| Full analysis: | https://app.any.run/tasks/f9592ea4-4b5b-4842-a114-3b7887a13f5a |
| Verdict: | Malicious activity |
| Analysis date: | April 19, 2024, 17:24:05 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v1.0 to extract, compression method=store |
| MD5: | BE132AC9135EE95AEA614D73DBE35042 |
| SHA1: | B163DD4F88CC370490FCA609FCBBFBD2E9FB85ED |
| SHA256: | 8BB03E707B3578166193BEA37095F7AC88BCE54A765F840B83B931C9272D898C |
| SSDEEP: | 49152:2X6EHB5Da+VVgsTzc02fTMX3nJxHocKVK90fSKz1WzKcDcsXXnSMVPbVKe33wL6m:5EHB5zSs4QX3flB2bz14VnSOZKLLB9W8 |
MALICIOUS
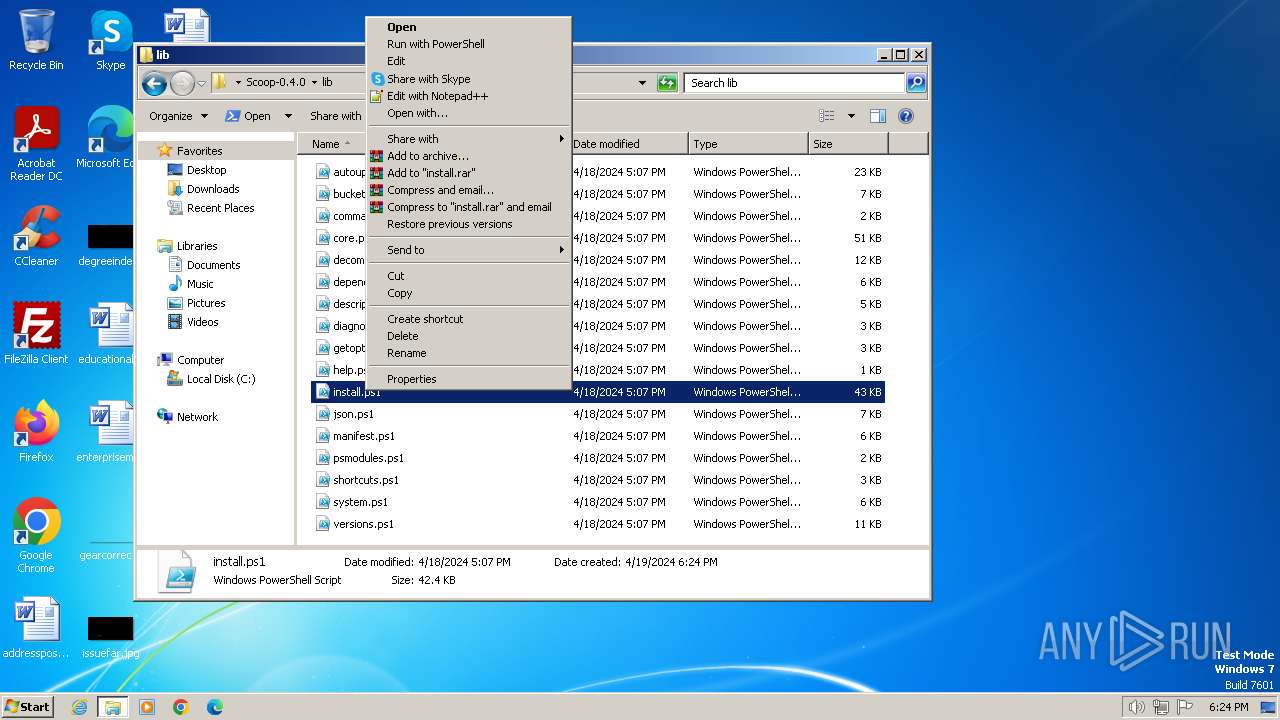
Bypass execution policy to execute commands
- powershell.exe (PID: 1376)
- powershell.exe (PID: 3692)
Drops the executable file immediately after the start
- powershell.exe (PID: 3692)
- csc.exe (PID: 1844)
Starts Visual C# compiler
- powershell.exe (PID: 3692)
SUSPICIOUS
Reads the Internet Settings
- powershell.exe (PID: 1376)
- powershell.exe (PID: 3692)
The Powershell connects to the Internet
- powershell.exe (PID: 3692)
Gets or sets the security protocol (POWERSHELL)
- powershell.exe (PID: 3692)
Using PowerShell to operate with local accounts
- powershell.exe (PID: 3692)
Gets file extension (POWERSHELL)
- powershell.exe (PID: 3692)
Unusual connection from system programs
- powershell.exe (PID: 3692)
Executable content was dropped or overwritten
- powershell.exe (PID: 3692)
- csc.exe (PID: 1844)
Writes data into a file (POWERSHELL)
- powershell.exe (PID: 3692)
Uses .NET C# to load dll
- powershell.exe (PID: 3692)
INFO
Executable content was dropped or overwritten
- WinRAR.exe (PID: 668)
Drops the executable file immediately after the start
- WinRAR.exe (PID: 668)
Manual execution by a user
- powershell.exe (PID: 3692)
- powershell.exe (PID: 1376)
Checks whether the specified file exists (POWERSHELL)
- powershell.exe (PID: 3692)
- powershell.exe (PID: 3692)
The dropped object may contain a URL to Tor Browser
- powershell.exe (PID: 3692)
Reads the machine GUID from the registry
- csc.exe (PID: 1844)
- cvtres.exe (PID: 3116)
Checks supported languages
- csc.exe (PID: 1844)
- cvtres.exe (PID: 3116)
Create files in a temporary directory
- csc.exe (PID: 1844)
- cvtres.exe (PID: 3116)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .xpi | | | Mozilla Firefox browser extension (66.6) |
|---|---|---|
| .zip | | | ZIP compressed archive (33.3) |
EXIF
ZIP
| ZipRequiredVersion: | 10 |
|---|---|
| ZipBitFlag: | - |
| ZipCompression: | None |
| ZipModifyDate: | 2024:04:18 09:07:58 |
| ZipCRC: | 0x00000000 |
| ZipCompressedSize: | - |
| ZipUncompressedSize: | - |
| ZipFileName: | Scoop-0.4.0/ |
Total processes
45
Monitored processes
5
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 668 | "C:\Program Files\WinRAR\WinRAR.exe" C:\Users\admin\AppData\Local\Temp\Scoop-0.4.0.zip | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.91.0 Modules
| |||||||||||||||
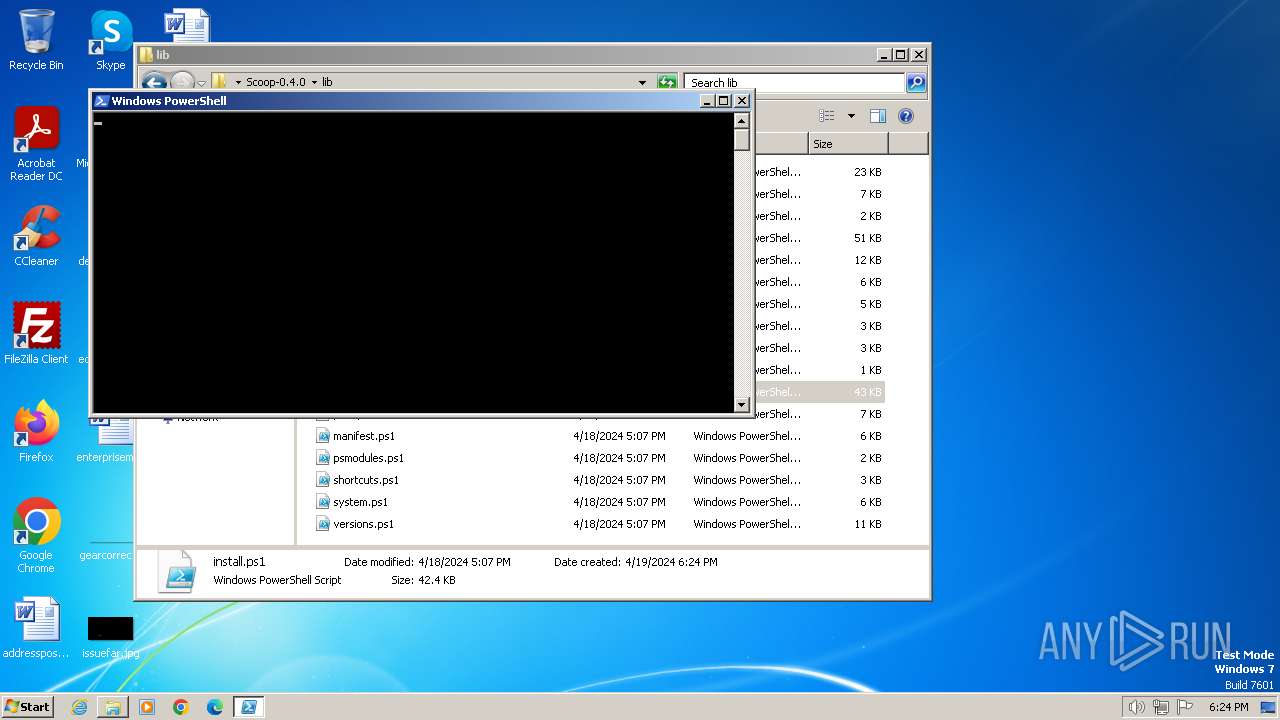
| 1376 | "C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe" "-file" "C:\Users\admin\Desktop\Scoop-0.4.0\lib\install.ps1" "-Command" "if((Get-ExecutionPolicy ) -ne AllSigned) { Set-ExecutionPolicy -Scope Process Bypass }" | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Exit code: 0 Version: 10.0.14409.1005 (rs1_srvoob.161208-1155) Modules
| |||||||||||||||
| 1844 | "C:\Windows\Microsoft.NET\Framework\v4.0.30319\csc.exe" /noconfig /fullpaths @"C:\Users\admin\AppData\Local\Temp\r5ctewat.cmdline" | C:\Windows\Microsoft.NET\Framework\v4.0.30319\csc.exe | powershell.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Visual C# Command Line Compiler Exit code: 0 Version: 4.8.3761.0 built by: NET48REL1 Modules
| |||||||||||||||
| 3116 | C:\Windows\Microsoft.NET\Framework\v4.0.30319\cvtres.exe /NOLOGO /READONLY /MACHINE:IX86 "/OUT:C:\Users\admin\AppData\Local\Temp\RES47D.tmp" "c:\Users\admin\AppData\Local\Temp\CSCD491D8A394504F1EBD95321EFE915C7.TMP" | C:\Windows\Microsoft.NET\Framework\v4.0.30319\cvtres.exe | — | csc.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft® Resource File To COFF Object Conversion Utility Exit code: 0 Version: 14.10.25028.0 built by: VCTOOLSD15RTM Modules
| |||||||||||||||
| 3692 | "C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe" "-file" "C:\Users\admin\Desktop\Scoop-0.4.0\bin\install.ps1" "-Command" "if((Get-ExecutionPolicy ) -ne AllSigned) { Set-ExecutionPolicy -Scope Process Bypass }" | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Exit code: 0 Version: 10.0.14409.1005 (rs1_srvoob.161208-1155) Modules
| |||||||||||||||
Total events
16 153
Read events
15 989
Write events
164
Delete events
0
Modification events
| (PID) Process: | (668) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (668) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (668) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\182\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (668) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\phacker.zip | |||
| (PID) Process: | (668) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\Win7-KB3191566-x86.zip | |||
| (PID) Process: | (668) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\curl-8.5.0_1-win32-mingw.zip | |||
| (PID) Process: | (668) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\Scoop-0.4.0.zip | |||
| (PID) Process: | (668) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (668) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (668) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
Executable files
22
Suspicious files
2 136
Text files
445
Unknown types
605
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 668 | WinRAR.exe | C:\Users\admin\Desktop\Scoop-0.4.0\.github\dependabot.yml | text | |
MD5:FEA828476F4EA031B9F7E53F6025F493 | SHA256:2663AD7216ABC03A048155D068E5A2D14558E50F8E596C200561872A70A1E90F | |||
| 668 | WinRAR.exe | C:\Users\admin\Desktop\Scoop-0.4.0\.github\ISSUE_TEMPLATE\Feature_request.md | text | |
MD5:8B3D5907515257610D30EA4698A39676 | SHA256:EB0251E60D6E46843363740C13AB6902BFECDD1D8478C8DBE3DABC7CA01F647E | |||
| 668 | WinRAR.exe | C:\Users\admin\Desktop\Scoop-0.4.0\.gitattributes | text | |
MD5:6CDE7FF8D395B49FA66F34AEA51CD292 | SHA256:D489E08E5A640328E377071E6620A0D84D2A391A175182060CD8CCC143A88470 | |||
| 668 | WinRAR.exe | C:\Users\admin\Desktop\Scoop-0.4.0\.editorconfig | text | |
MD5:84DD997A84FAB54A9C94126DBEA09F2B | SHA256:33E753B9DC4B0C1F3DEF03F5E53BEC1E50565943901180369B862DF910186BC3 | |||
| 668 | WinRAR.exe | C:\Users\admin\Desktop\Scoop-0.4.0\.github\workflows\ci.yml | text | |
MD5:736263E97938C1C8B10D1BE2DBAACE5B | SHA256:00230BC788E69E27990B2D5D7867FA3DCACEBF35AD27B07A15CD45C758B087CB | |||
| 668 | WinRAR.exe | C:\Users\admin\Desktop\Scoop-0.4.0\.vscode\settings.json | text | |
MD5:0BBADEE4B23CCA648D8E70F35CF43163 | SHA256:726A03218E0F11B95AE68FA85FB97B4C2F2EB42E498BF734442B7B9AD9C51703 | |||
| 668 | WinRAR.exe | C:\Users\admin\Desktop\Scoop-0.4.0\README.md | html | |
MD5:39118C0A087F34890C2DF69E0E950B60 | SHA256:B4611C60CEB1778E4737915F8F9C5633CAEEEF9F984EC2FEE5FA823C00729258 | |||
| 668 | WinRAR.exe | C:\Users\admin\Desktop\Scoop-0.4.0\CHANGELOG.md | text | |
MD5:EBF6BDA2C72C5B2DA16434DA4736184B | SHA256:180C3994E0F8C87773DD2990C064AB90A9BF9704814A4B8622150D9B6EC89CA1 | |||
| 668 | WinRAR.exe | C:\Users\admin\Desktop\Scoop-0.4.0\PSScriptAnalyzerSettings.psd1 | text | |
MD5:8DB1F93B7197C80B038C582211C0C6BF | SHA256:6CF60B166B862E393F4491678088140C78549E162AE92CDF6E67FDAA41E17231 | |||
| 668 | WinRAR.exe | C:\Users\admin\Desktop\Scoop-0.4.0\appveyor.yml | text | |
MD5:EC1B29716E385319A4AD5CDC713D34E4 | SHA256:3688B4CA11214F42F6F8E93EFA8C3BBCCC464BBD2CCEA314998DF92E7EE644A9 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
8
DNS requests
4
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
1080 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |
3692 | powershell.exe | 18.66.102.91:443 | get.scoop.sh | — | US | unknown |
3692 | powershell.exe | 185.199.108.133:443 | raw.githubusercontent.com | FASTLY | US | unknown |
3692 | powershell.exe | 140.82.121.3:443 | github.com | GITHUB | US | unknown |
3692 | powershell.exe | 140.82.121.10:443 | codeload.github.com | GITHUB | US | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
get.scoop.sh |
| whitelisted |
raw.githubusercontent.com |
| shared |
github.com |
| shared |
codeload.github.com |
| whitelisted |