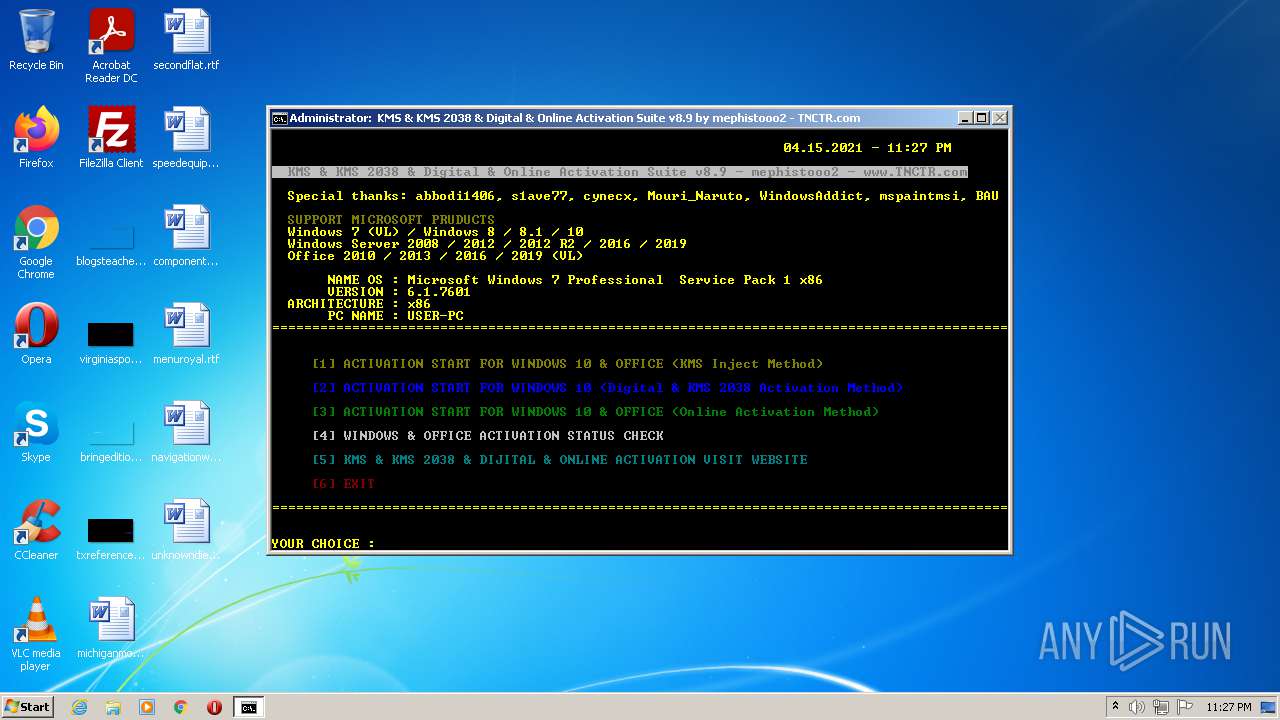
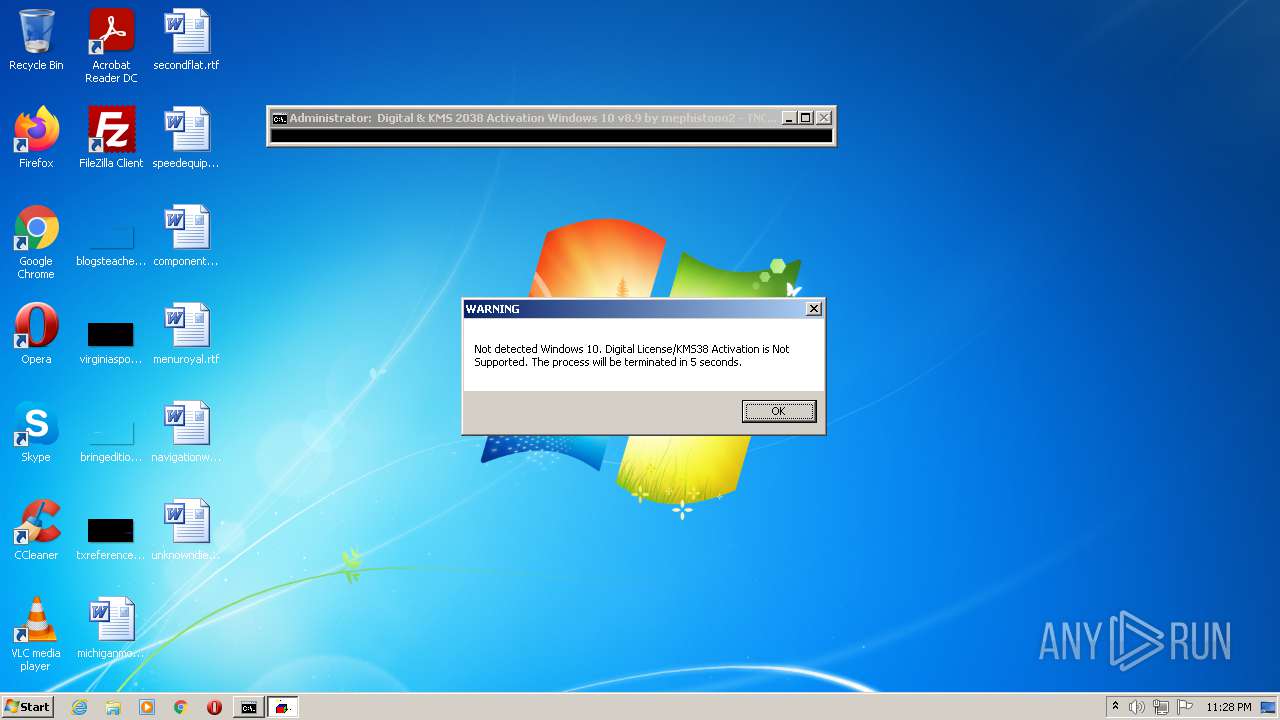
| File name: | KMS_Suite.v8.9.EN.cmd |
| Full analysis: | https://app.any.run/tasks/5f8a8eb6-3217-47d0-aebf-dfc12dede4be |
| Verdict: | Malicious activity |
| Analysis date: | April 15, 2021, 22:26:59 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | text/x-msdos-batch |
| File info: | DOS batch file, ASCII text, with very long lines, with CRLF line terminators |
| MD5: | 167A50507AF92AE8DD9906405E9F2962 |
| SHA1: | A6B8000433D72B13213E698F7DB4252448225667 |
| SHA256: | 8B8C5D5FFC3CDACCCA76BCE8D68C70347CB6D8A476A1251195C92BEF206DADBC |
| SSDEEP: | 6144:6ycETPZcQgKwsjcuhn/gUAlpLPcDXOEn2tcJadfBE7:xBxyKSutsb4DXOEn8c0s7 |
MALICIOUS
Executes PowerShell scripts
- cmd.exe (PID: 2488)
- cmd.exe (PID: 2064)
- cmd.exe (PID: 1448)
Starts Visual C# compiler
- powershell.exe (PID: 2768)
Drops executable file immediately after starts
- expand.exe (PID: 2324)
- xcopy.exe (PID: 3164)
Application was dropped or rewritten from another process
- DisableX.exe (PID: 2604)
- center.exe (PID: 2956)
SUSPICIOUS
Checks supported languages
- cmd.exe (PID: 2488)
- powershell.exe (PID: 896)
- cmd.exe (PID: 2064)
- mode.com (PID: 328)
- powershell.exe (PID: 2768)
- csc.exe (PID: 2728)
- cvtres.exe (PID: 2804)
- cmd.exe (PID: 1448)
- powershell.exe (PID: 2296)
- WScript.exe (PID: 2748)
- DisableX.exe (PID: 2604)
- cmd.exe (PID: 2856)
- mode.com (PID: 1656)
- mode.com (PID: 2960)
- cmd.exe (PID: 3136)
- WMIC.exe (PID: 3168)
- cmd.exe (PID: 2968)
- WMIC.exe (PID: 1224)
- cmd.exe (PID: 3204)
- WMIC.exe (PID: 4044)
- mode.com (PID: 2152)
- cmd.exe (PID: 2636)
- cmd.exe (PID: 2320)
- mode.com (PID: 3532)
- cmd.exe (PID: 1196)
- WMIC.exe (PID: 2120)
- WScript.exe (PID: 2772)
- center.exe (PID: 2956)
Uses REG.EXE to modify Windows registry
- cmd.exe (PID: 2488)
- cmd.exe (PID: 1448)
Reads the date of Windows installation
- powershell.exe (PID: 896)
- powershell.exe (PID: 2768)
- powershell.exe (PID: 2296)
Reads the computer name
- powershell.exe (PID: 896)
- powershell.exe (PID: 2768)
- powershell.exe (PID: 2296)
- cmd.exe (PID: 1448)
- WScript.exe (PID: 2748)
- WMIC.exe (PID: 3168)
- WMIC.exe (PID: 1224)
- WMIC.exe (PID: 4044)
- WMIC.exe (PID: 2120)
- WScript.exe (PID: 2772)
Starts CMD.EXE for commands execution
- powershell.exe (PID: 896)
- cmd.exe (PID: 2064)
- cmd.exe (PID: 1448)
Creates files in the user directory
- powershell.exe (PID: 896)
- powershell.exe (PID: 2768)
- powershell.exe (PID: 2296)
Executable content was dropped or overwritten
- csc.exe (PID: 2728)
- expand.exe (PID: 2324)
- xcopy.exe (PID: 3164)
Drops a file with a compile date too recent
- csc.exe (PID: 2728)
Drops a file that was compiled in debug mode
- csc.exe (PID: 2728)
- expand.exe (PID: 2324)
- xcopy.exe (PID: 3164)
Drops a file with too old compile date
- expand.exe (PID: 2324)
- xcopy.exe (PID: 3164)
Application launched itself
- cmd.exe (PID: 2064)
- cmd.exe (PID: 1448)
Executes scripts
- cmd.exe (PID: 1448)
Uses WMIC.EXE to obtain a system information
- cmd.exe (PID: 3136)
- cmd.exe (PID: 2968)
- cmd.exe (PID: 3204)
- cmd.exe (PID: 1196)
Reads Windows Product ID
- reg.exe (PID: 2992)
Starts CHOICE.EXE (used to create a delay)
- cmd.exe (PID: 1448)
Removes files from Windows directory
- cmd.exe (PID: 1448)
INFO
Checks supported languages
- reg.exe (PID: 2804)
- expand.exe (PID: 2324)
- xcopy.exe (PID: 3164)
- findstr.exe (PID: 2984)
- reg.exe (PID: 1624)
- findstr.exe (PID: 2752)
- findstr.exe (PID: 860)
- findstr.exe (PID: 3664)
- findstr.exe (PID: 2312)
- findstr.exe (PID: 2096)
- findstr.exe (PID: 2716)
- findstr.exe (PID: 3232)
- findstr.exe (PID: 604)
- choice.exe (PID: 2244)
- reg.exe (PID: 2532)
- reg.exe (PID: 2992)
Dropped object may contain Bitcoin addresses
- expand.exe (PID: 2324)
Checks Windows Trust Settings
- WScript.exe (PID: 2748)
- WScript.exe (PID: 2772)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
82
Monitored processes
44
Malicious processes
7
Suspicious processes
2
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 328 | mode con cols=78 lines=3 | C:\Windows\system32\mode.com | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: DOS Device MODE Utility Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 604 | findstr /v /a:4 /R "^f7f81a39-5f63-5b42-9efd-1f13b5431005quot; " [6] EXIT" nul | C:\Windows\system32\findstr.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Find String (QGREP) Utility Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 860 | findstr /v /a:6 /R "^f7f81a39-5f63-5b42-9efd-1f13b5431005quot; " SUPPORT MICROSOFT PRUDUCTS" nul | C:\Windows\system32\findstr.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Find String (QGREP) Utility Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 896 | powershell -NoProfile Start-Process -FilePath 'C:\Windows\system32\cmd.exe' -ArgumentList '/c """"""C:\Users\admin\AppData\Local\Temp\KMS_Suite.v8.9.EN.cmd""" 49127c4b-02dc-482e-ac4f-ec4d659b7547"""' -Verb RunAs | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1196 | C:\Windows\system32\cmd.exe /c wmic path Win32_OperatingSystem get BuildNumber /value | C:\Windows\system32\cmd.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 1224 | wmic Path Win32_OperatingSystem Get CSDVersion /format:LIST | C:\Windows\System32\Wbem\WMIC.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: WMI Commandline Utility Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1448 | cmd.exe /c KMS_Suite.cmd | C:\Windows\system32\cmd.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 1624 | REG QUERY HKU\S-1-5-19\Environment | C:\Windows\system32\reg.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Registry Console Tool Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1656 | mode con: cols=90 lines=40 | C:\Windows\system32\mode.com | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: DOS Device MODE Utility Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2064 | "C:\Windows\system32\cmd.exe" /c ""C:\Users\admin\AppData\Local\Temp\KMS_Suite.v8.9.EN.cmd" 49127c4b-02dc-482e-ac4f-ec4d659b7547" | C:\Windows\system32\cmd.exe | powershell.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 1 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
Total events
6 149
Read events
5 955
Write events
194
Delete events
0
Modification events
| (PID) Process: | (896) powershell.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\16B\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (896) powershell.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (896) powershell.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
| (PID) Process: | (896) powershell.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 1 | |||
| (PID) Process: | (896) powershell.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 0 | |||
| (PID) Process: | (2768) powershell.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\16B\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (2296) powershell.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\16B\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (1448) cmd.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (1448) cmd.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
| (PID) Process: | (1448) cmd.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 1 | |||
Executable files
25
Suspicious files
10
Text files
46
Unknown types
3
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2768 | powershell.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\PS5HD3VVMJ82T5E3K5BM.temp | binary | |
MD5:— | SHA256:— | |||
| 896 | powershell.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\d93f411851d7c929.customDestinations-ms~RF109184.TMP | binary | |
MD5:— | SHA256:— | |||
| 896 | powershell.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\V3OCK066LCW5SHOB94O2.temp | binary | |
MD5:— | SHA256:— | |||
| 896 | powershell.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\d93f411851d7c929.customDestinations-ms | binary | |
MD5:— | SHA256:— | |||
| 2768 | powershell.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\d93f411851d7c929.customDestinations-ms~RF10951e.TMP | binary | |
MD5:— | SHA256:— | |||
| 2768 | powershell.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\d93f411851d7c929.customDestinations-ms | binary | |
MD5:— | SHA256:— | |||
| 2768 | powershell.exe | C:\Users\admin\AppData\Local\Temp\m02yqvdu.cmdline | text | |
MD5:— | SHA256:— | |||
| 2728 | csc.exe | C:\Users\admin\AppData\Local\Temp\m02yqvdu.pdb | pdb | |
MD5:— | SHA256:— | |||
| 2728 | csc.exe | C:\Users\admin\AppData\Local\Temp\m02yqvdu.out | text | |
MD5:— | SHA256:— | |||
| 2728 | csc.exe | C:\Users\admin\AppData\Local\Temp\m02yqvdu.dll | executable | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
0
DNS requests
0
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
DNS requests
Threats
Process | Message |
|---|---|
csc.exe |
*** HR originated: -2147024774
*** Source File: d:\iso_whid\x86fre\base\isolation\com\copyout.cpp, line 1302
|
csc.exe |
*** HR propagated: -2147024774
*** Source File: d:\iso_whid\x86fre\base\isolation\com\enumidentityattribute.cpp, line 144
|
csc.exe |
*** HR originated: -2147024774
*** Source File: d:\iso_whid\x86fre\base\isolation\com\copyout.cpp, line 1302
|
csc.exe |
*** HR propagated: -2147024774
*** Source File: d:\iso_whid\x86fre\base\isolation\com\enumidentityattribute.cpp, line 144
|
csc.exe |
*** HR originated: -2147024774
*** Source File: d:\iso_whid\x86fre\base\isolation\com\copyout.cpp, line 1302
|
csc.exe |
*** HR propagated: -2147024774
*** Source File: d:\iso_whid\x86fre\base\isolation\com\enumidentityattribute.cpp, line 144
|
csc.exe |
*** HR originated: -2147024774
*** Source File: d:\iso_whid\x86fre\base\isolation\com\copyout.cpp, line 1302
|
csc.exe |
*** HR propagated: -2147024774
*** Source File: d:\iso_whid\x86fre\base\isolation\com\enumidentityattribute.cpp, line 144
|
csc.exe |
*** HR originated: -2147024774
*** Source File: d:\iso_whid\x86fre\base\isolation\com\copyout.cpp, line 1302
|
csc.exe |
*** HR propagated: -2147024774
*** Source File: d:\iso_whid\x86fre\base\isolation\com\enumidentityattribute.cpp, line 144
|