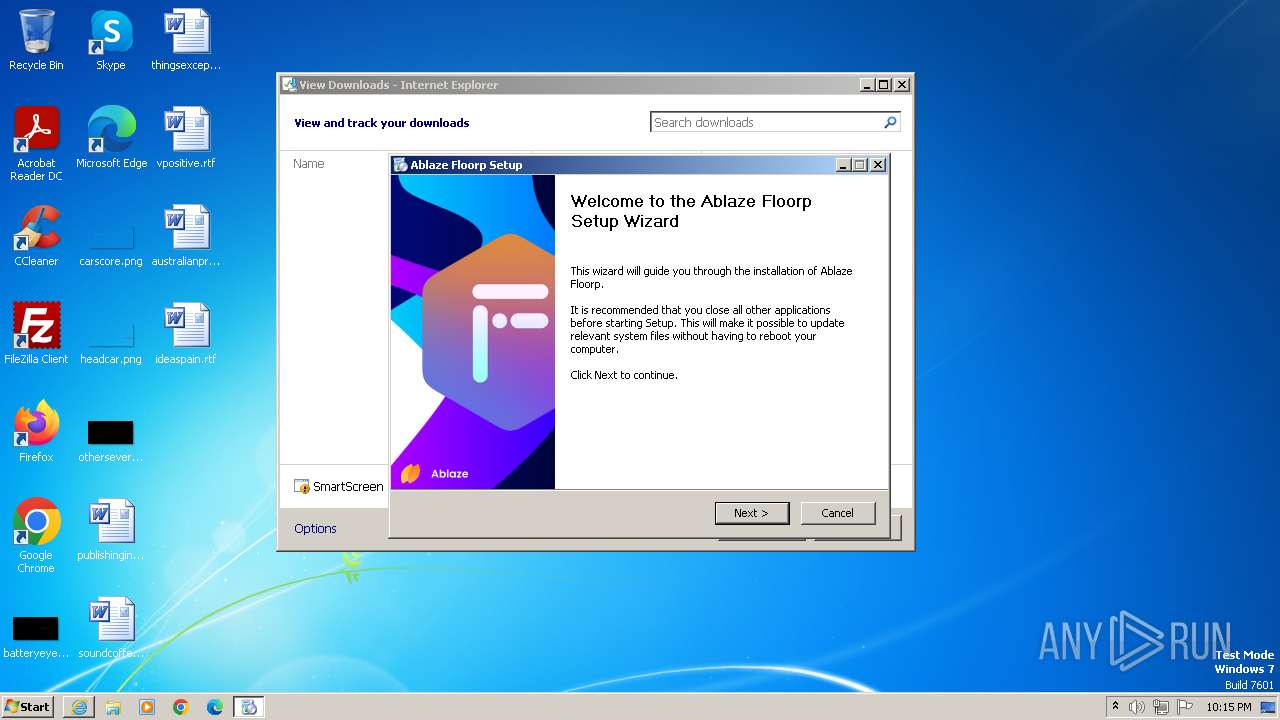
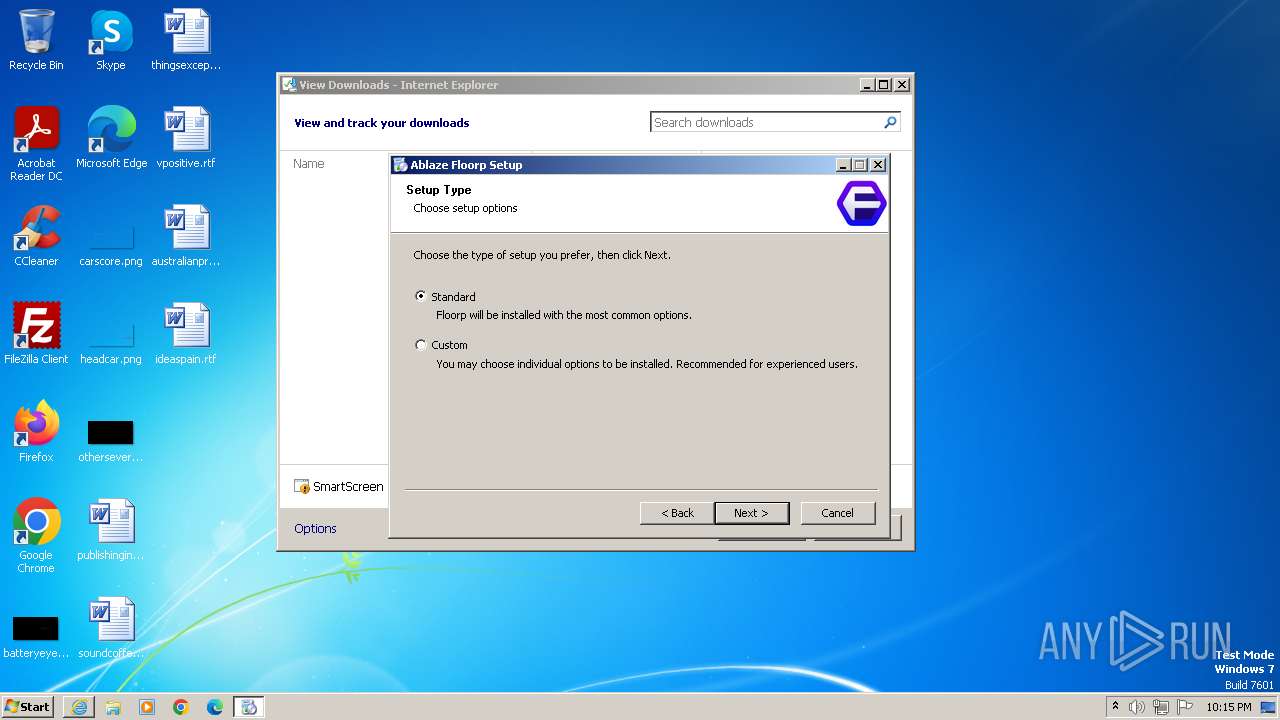
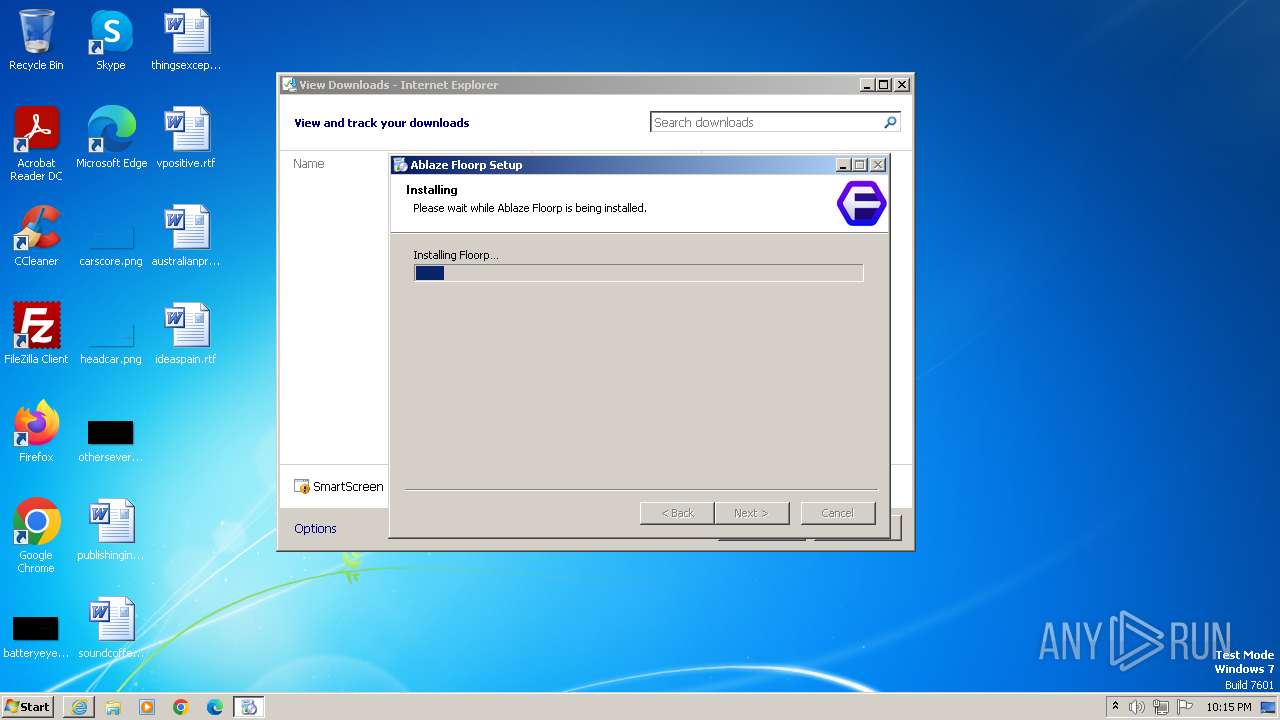
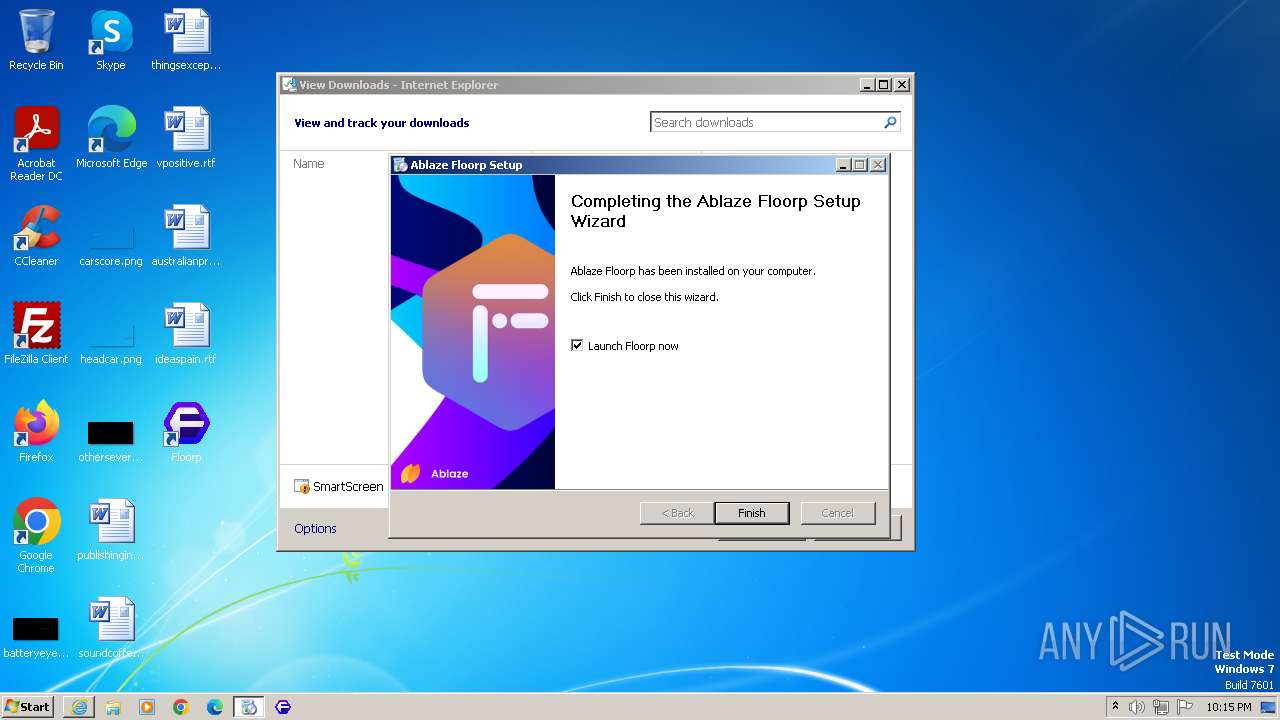
| URL: | https://github.com/Floorp-Projects/Floorp/releases/download/v11.6.1/floorp-win32.installer.exe |
| Full analysis: | https://app.any.run/tasks/43a42545-ffdf-429e-a31c-13b6abfb9e6a |
| Verdict: | Malicious activity |
| Analysis date: | November 21, 2023, 22:13:42 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| SHA1: | 7627C4504F663E59C6C6D452456FAF20B063676A |
| SHA256: | 8B65A8AC240FC8D07036CC9C850197144D0DAE7D9B84D77FBABBF05A6B6677EA |
| SSDEEP: | 3:N8tEdFE1py8XhE2kC5YSGDgXLNn:2ukrnGDgXLN |
MALICIOUS
Drops the executable file immediately after the start
- setup.exe (PID: 3724)
- setup.exe (PID: 3532)
- floorp-win32.installer.exe (PID: 3912)
- floorp.exe (PID: 1612)
SUSPICIOUS
The process drops C-runtime libraries
- floorp-win32.installer.exe (PID: 3912)
- setup.exe (PID: 3532)
Process drops legitimate windows executable
- floorp-win32.installer.exe (PID: 3912)
- setup.exe (PID: 3532)
The process creates files with name similar to system file names
- setup.exe (PID: 3724)
- setup.exe (PID: 3532)
Malware-specific behavior (creating "System.dll" in Temp)
- setup.exe (PID: 3724)
- setup.exe (PID: 3532)
Application launched itself
- setup.exe (PID: 3724)
- floorp.exe (PID: 916)
- floorp.exe (PID: 1880)
- floorp.exe (PID: 1612)
Reads the Internet Settings
- setup.exe (PID: 3532)
- floorp.exe (PID: 1612)
Creates/Modifies COM task schedule object
- setup.exe (PID: 3532)
Searches for installed software
- setup.exe (PID: 3532)
Checks Windows Trust Settings
- setup.exe (PID: 3532)
Reads settings of System Certificates
- setup.exe (PID: 3532)
Reads security settings of Internet Explorer
- setup.exe (PID: 3532)
INFO
Drops the executable file immediately after the start
- iexplore.exe (PID: 3220)
Checks supported languages
- wmpnscfg.exe (PID: 3444)
- floorp-win32.installer.exe (PID: 3912)
- setup.exe (PID: 3724)
- setup.exe (PID: 3532)
- wmpnscfg.exe (PID: 3884)
- default-browser-agent.exe (PID: 3820)
- floorp.exe (PID: 916)
- floorp.exe (PID: 1880)
- floorp.exe (PID: 2060)
- floorp.exe (PID: 1612)
- floorp.exe (PID: 2780)
- floorp.exe (PID: 1848)
- floorp.exe (PID: 2112)
- floorp.exe (PID: 3280)
- floorp.exe (PID: 968)
- floorp.exe (PID: 3380)
- floorp.exe (PID: 3680)
- floorp.exe (PID: 3972)
- floorp.exe (PID: 2064)
- floorp.exe (PID: 3864)
- floorp.exe (PID: 4076)
- floorp.exe (PID: 2428)
- floorp.exe (PID: 2452)
- floorp.exe (PID: 2860)
- floorp.exe (PID: 3748)
- floorp.exe (PID: 3152)
- floorp.exe (PID: 3240)
- floorp.exe (PID: 3484)
Application launched itself
- iexplore.exe (PID: 3128)
Manual execution by a user
- wmpnscfg.exe (PID: 3444)
- wmpnscfg.exe (PID: 3884)
Reads the computer name
- wmpnscfg.exe (PID: 3444)
- wmpnscfg.exe (PID: 3884)
- setup.exe (PID: 3724)
- setup.exe (PID: 3532)
- default-browser-agent.exe (PID: 3820)
- floorp.exe (PID: 2060)
- floorp.exe (PID: 1612)
- floorp.exe (PID: 2780)
- floorp.exe (PID: 1848)
- floorp.exe (PID: 2112)
- floorp.exe (PID: 3280)
- floorp.exe (PID: 968)
- floorp.exe (PID: 3484)
- floorp.exe (PID: 3864)
- floorp.exe (PID: 3680)
- floorp.exe (PID: 3380)
- floorp.exe (PID: 3972)
- floorp.exe (PID: 2064)
- floorp.exe (PID: 4076)
- floorp.exe (PID: 2428)
- floorp.exe (PID: 2860)
- floorp.exe (PID: 2452)
- floorp.exe (PID: 3748)
- floorp.exe (PID: 3152)
- floorp.exe (PID: 3240)
Reads the machine GUID from the registry
- wmpnscfg.exe (PID: 3444)
- wmpnscfg.exe (PID: 3884)
- setup.exe (PID: 3532)
- floorp.exe (PID: 2060)
- setup.exe (PID: 3724)
- floorp.exe (PID: 1612)
The process uses the downloaded file
- iexplore.exe (PID: 3128)
Create files in a temporary directory
- floorp-win32.installer.exe (PID: 3912)
- setup.exe (PID: 3724)
- setup.exe (PID: 3532)
- floorp.exe (PID: 2060)
- floorp.exe (PID: 1612)
Process checks are UAC notifies on
- setup.exe (PID: 3724)
- floorp.exe (PID: 2060)
Creates files in the program directory
- setup.exe (PID: 3532)
- floorp.exe (PID: 2060)
- floorp.exe (PID: 1612)
Reads CPU info
- floorp.exe (PID: 2060)
- floorp.exe (PID: 1612)
Creates files or folders in the user directory
- setup.exe (PID: 3724)
- floorp.exe (PID: 1612)
- setup.exe (PID: 3532)
Checks proxy server information
- setup.exe (PID: 3532)
- floorp.exe (PID: 1612)
Process checks computer location settings
- floorp.exe (PID: 1612)
- floorp.exe (PID: 3972)
- floorp.exe (PID: 2428)
- floorp.exe (PID: 2064)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
71
Monitored processes
30
Malicious processes
6
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 916 | "C:\Program Files\Ablaze Floorp\floorp.exe" --backgroundtask install | C:\Program Files\Ablaze Floorp\floorp.exe | — | setup.exe | |||||||||||
User: admin Company: Ablaze MIRAI Integrity Level: HIGH Description: Floorp Exit code: 0 Version: 115.6.0 Modules
| |||||||||||||||
| 968 | "C:\Program Files\Ablaze Floorp\floorp.exe" -contentproc --channel="1612.4.100074534\529472163" -childID 3 -isForBrowser -prefsHandle 2804 -prefMapHandle 2808 -prefsLen 22279 -prefMapSize 247554 -jsInitHandle 780 -jsInitLen 240916 -parentBuildID 20231121024253 -appDir "C:\Program Files\Ablaze Floorp\browser" - {cd89ff5b-5dc7-4998-87e9-fcaf51318eb7} 1612 tab | C:\Program Files\Ablaze Floorp\floorp.exe | — | floorp.exe | |||||||||||
User: admin Company: Ablaze MIRAI Integrity Level: LOW Description: Floorp Exit code: 0 Version: 115.6.0 Modules
| |||||||||||||||
| 1612 | "C:\Program Files\Ablaze Floorp\floorp.exe" -first-startup | C:\Program Files\Ablaze Floorp\floorp.exe | floorp.exe | ||||||||||||
User: admin Company: Ablaze MIRAI Integrity Level: MEDIUM Description: Floorp Exit code: 0 Version: 115.6.0 Modules
| |||||||||||||||
| 1848 | "C:\Program Files\Ablaze Floorp\floorp.exe" -contentproc --channel="1612.1.312197303\1203249411" -parentBuildID 20231121024253 -prefsHandle 1596 -prefMapHandle 1592 -prefsLen 20179 -prefMapSize 247554 -appDir "C:\Program Files\Ablaze Floorp\browser" - {b2aa6037-8e67-45a6-abe3-45233a303956} 1612 socket | C:\Program Files\Ablaze Floorp\floorp.exe | — | floorp.exe | |||||||||||
User: admin Company: Ablaze MIRAI Integrity Level: LOW Description: Floorp Exit code: 0 Version: 115.6.0 Modules
| |||||||||||||||
| 1880 | "C:\Program Files\Ablaze Floorp\floorp.exe" -first-startup | C:\Program Files\Ablaze Floorp\floorp.exe | — | setup.exe | |||||||||||
User: admin Company: Ablaze MIRAI Integrity Level: MEDIUM Description: Floorp Exit code: 0 Version: 115.6.0 Modules
| |||||||||||||||
| 2060 | "C:\Program Files\Ablaze Floorp\floorp.exe" --backgroundtask install | C:\Program Files\Ablaze Floorp\floorp.exe | — | floorp.exe | |||||||||||
User: admin Company: Ablaze MIRAI Integrity Level: MEDIUM Description: Floorp Exit code: 0 Version: 115.6.0 Modules
| |||||||||||||||
| 2064 | "C:\Program Files\Ablaze Floorp\floorp.exe" -contentproc --channel="1612.10.1007991053\1600182349" -childID 8 -isForBrowser -prefsHandle 8148 -prefMapHandle 8152 -prefsLen 28382 -prefMapSize 247554 -jsInitHandle 780 -jsInitLen 240916 -parentBuildID 20231121024253 -appDir "C:\Program Files\Ablaze Floorp\browser" - {7cb3296e-9fd9-455a-86fb-1ae047166d03} 1612 tab | C:\Program Files\Ablaze Floorp\floorp.exe | — | floorp.exe | |||||||||||
User: admin Company: Ablaze MIRAI Integrity Level: LOW Description: Floorp Exit code: 0 Version: 115.6.0 Modules
| |||||||||||||||
| 2112 | "C:\Program Files\Ablaze Floorp\floorp.exe" -contentproc --channel="1612.2.2034560281\964209039" -childID 1 -isForBrowser -prefsHandle 2248 -prefMapHandle 2244 -prefsLen 20792 -prefMapSize 247554 -jsInitHandle 780 -jsInitLen 240916 -parentBuildID 20231121024253 -appDir "C:\Program Files\Ablaze Floorp\browser" - {c4380bde-2976-4fdb-8f8c-81583b81debd} 1612 tab | C:\Program Files\Ablaze Floorp\floorp.exe | — | floorp.exe | |||||||||||
User: admin Company: Ablaze MIRAI Integrity Level: LOW Description: Floorp Exit code: 0 Version: 115.6.0 Modules
| |||||||||||||||
| 2428 | "C:\Program Files\Ablaze Floorp\floorp.exe" -contentproc --channel="1612.12.850245047\1728498920" -childID 10 -isForBrowser -prefsHandle 3700 -prefMapHandle 7652 -prefsLen 28652 -prefMapSize 247554 -jsInitHandle 780 -jsInitLen 240916 -parentBuildID 20231121024253 -appDir "C:\Program Files\Ablaze Floorp\browser" - {636ec161-7bcc-4ce0-a5c5-31c388fdb590} 1612 tab | C:\Program Files\Ablaze Floorp\floorp.exe | — | floorp.exe | |||||||||||
User: admin Company: Ablaze MIRAI Integrity Level: LOW Description: Floorp Exit code: 0 Version: 115.6.0 Modules
| |||||||||||||||
| 2452 | "C:\Program Files\Ablaze Floorp\floorp.exe" -contentproc --channel="1612.14.1968995139\472632574" -childID 11 -isForBrowser -prefsHandle 2788 -prefMapHandle 4060 -prefsLen 28652 -prefMapSize 247554 -jsInitHandle 780 -jsInitLen 240916 -parentBuildID 20231121024253 -appDir "C:\Program Files\Ablaze Floorp\browser" - {68d4f5c9-09f8-4885-9af9-1033c1f42b8c} 1612 tab | C:\Program Files\Ablaze Floorp\floorp.exe | — | floorp.exe | |||||||||||
User: admin Company: Ablaze MIRAI Integrity Level: LOW Description: Floorp Exit code: 0 Version: 115.6.0 Modules
| |||||||||||||||
Total events
43 445
Read events
43 269
Write events
155
Delete events
21
Modification events
| (PID) Process: | (3128) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPDaysSinceLastAutoMigration |
Value: 0 | |||
| (PID) Process: | (3128) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPLastLaunchHighDateTime |
Value: 30847387 | |||
| (PID) Process: | (3128) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\UrlBlockManager |
| Operation: | write | Name: | NextCheckForUpdateHighDateTime |
Value: 30847437 | |||
| (PID) Process: | (3128) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (3128) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
| (PID) Process: | (3128) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\Main |
| Operation: | write | Name: | CompatibilityFlags |
Value: 0 | |||
| (PID) Process: | (3128) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings |
| Operation: | write | Name: | ProxyEnable |
Value: 0 | |||
| (PID) Process: | (3128) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\Connections |
| Operation: | write | Name: | SavedLegacySettings |
Value: 4600000059010000090000000000000000000000000000000400000000000000C0E333BBEAB1D3010000000000000000000000000100000002000000C0A8016B000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (3128) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (3128) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
Executable files
127
Suspicious files
476
Text files
218
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3220 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\B6QGX7LP\floorp-win32.installer.exe.apilw7r.partial | — | |
MD5:— | SHA256:— | |||
| 3128 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\B6QGX7LP\floorp-win32.installer.exe | — | |
MD5:— | SHA256:— | |||
| 3220 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\57C8EDB95DF3F0AD4EE2DC2B8CFD4157 | binary | |
MD5:36CCBA2489459DDFF3C501F3575C823E | SHA256:EC901FE76C2BDE35C3DA7598AE41B1438C049794ACADB9C0C57F7D807D8D62E8 | |||
| 3128 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\B6QGX7LP\urlblockindex[1].bin | binary | |
MD5:FA518E3DFAE8CA3A0E495460FD60C791 | SHA256:775853600060162C4B4E5F883F9FD5A278E61C471B3EE1826396B6D129499AA7 | |||
| 3128 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Internet Explorer\VersionManager\verE709.tmp | xml | |
MD5:CBD0581678FA40F0EDCBC7C59E0CAD10 | SHA256:159BD4343F344A08F6AF3B716B6FA679859C1BD1D7030D26FF5EF0255B86E1D9 | |||
| 3220 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\57C8EDB95DF3F0AD4EE2DC2B8CFD4157 | compressed | |
MD5:1BFE591A4FE3D91B03CDF26EAACD8F89 | SHA256:9CF94355051BF0F4A45724CA20D1CC02F76371B963AB7D1E38BD8997737B13D8 | |||
| 3220 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\MFAQUS6V\floorp-win32.installer[1].exe | executable | |
MD5:798F7AED4107363D6495C52BE57EE4C9 | SHA256:105CC925EFD0630ED57039C63EED2E2E199A58737C94A065F94D0639AE22CB84 | |||
| 3220 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\B398B80134F72209547439DB21AB308D_A4CF52CCA82D7458083F7280801A3A04 | binary | |
MD5:0CDEC41FE02B65887B8ECABB92D5A170 | SHA256:5442E197979ECC472AA8C49EDDEC77C2B04FC0F7470A52F5DE5C7750C0304F2B | |||
| 3220 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\B398B80134F72209547439DB21AB308D_ADE4E4D3A3BCBCA5C39C54D362D88565 | binary | |
MD5:05F9AAE5112D22499BE955F3847E283D | SHA256:29A1C4F0D497AEB2295FA7E6D8B6CDBD5912CB1732F2865B12432B747BADA7FC | |||
| 3128 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\B6QGX7LP\floorp-win32.installer.exe.apilw7r.partial:Zone.Identifier | text | |
MD5:FBCCF14D504B7B2DBCB5A5BDA75BD93B | SHA256:EACD09517CE90D34BA562171D15AC40D302F0E691B439F91BE1B6406E25F5913 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
43
TCP/UDP connections
142
DNS requests
240
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
3220 | iexplore.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQrHR6YzPN2BNbByL0VoiTIBBMAOAQUCrwIKReMpTlteg7OM8cus%2B37w3oCEAzQqL7GMs%2FmReygqbCE%2Bxw%3D | unknown | binary | 312 b | unknown |
3128 | iexplore.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | binary | 471 b | unknown |
3128 | iexplore.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAqvpsXKY8RRQeo74ffHUxc%3D | unknown | binary | 471 b | unknown |
3220 | iexplore.exe | GET | 200 | 178.79.242.128:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?127045ce466871b6 | unknown | compressed | 4.66 Kb | unknown |
3128 | iexplore.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEA177el9ggmWelJjG4vdGL0%3D | unknown | binary | 471 b | unknown |
3532 | setup.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAo1CNVcKSsBffitZcAP9%2BQ%3D | unknown | binary | 471 b | unknown |
1612 | floorp.exe | GET | 200 | 34.107.221.82:80 | http://detectportal.firefox.com/success.txt?ipv4 | unknown | text | 8 b | unknown |
3220 | iexplore.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAfy81yHqHeveu%2FpR5k1Jb0%3D | unknown | binary | 471 b | unknown |
3128 | iexplore.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | binary | 471 b | unknown |
3220 | iexplore.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAbY2QTVWENG9oovp1QifsQ%3D | unknown | binary | 471 b | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
3220 | iexplore.exe | 140.82.121.4:443 | github.com | GITHUB | US | unknown |
3220 | iexplore.exe | 178.79.242.128:80 | ctldl.windowsupdate.com | LLNW | DE | unknown |
2588 | svchost.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
3220 | iexplore.exe | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
3220 | iexplore.exe | 185.199.108.133:443 | objects.githubusercontent.com | FASTLY | US | unknown |
1080 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |
3128 | iexplore.exe | 152.199.19.161:443 | r20swj13mr.microsoft.com | EDGECAST | US | whitelisted |
3128 | iexplore.exe | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
github.com |
| shared |
ctldl.windowsupdate.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
objects.githubusercontent.com |
| shared |
r20swj13mr.microsoft.com |
| whitelisted |
iecvlist.microsoft.com |
| whitelisted |
ieonline.microsoft.com |
| whitelisted |
go.microsoft.com |
| whitelisted |
www.msn.com |
| whitelisted |
incoming.telemetry.mozilla.org |
| whitelisted |