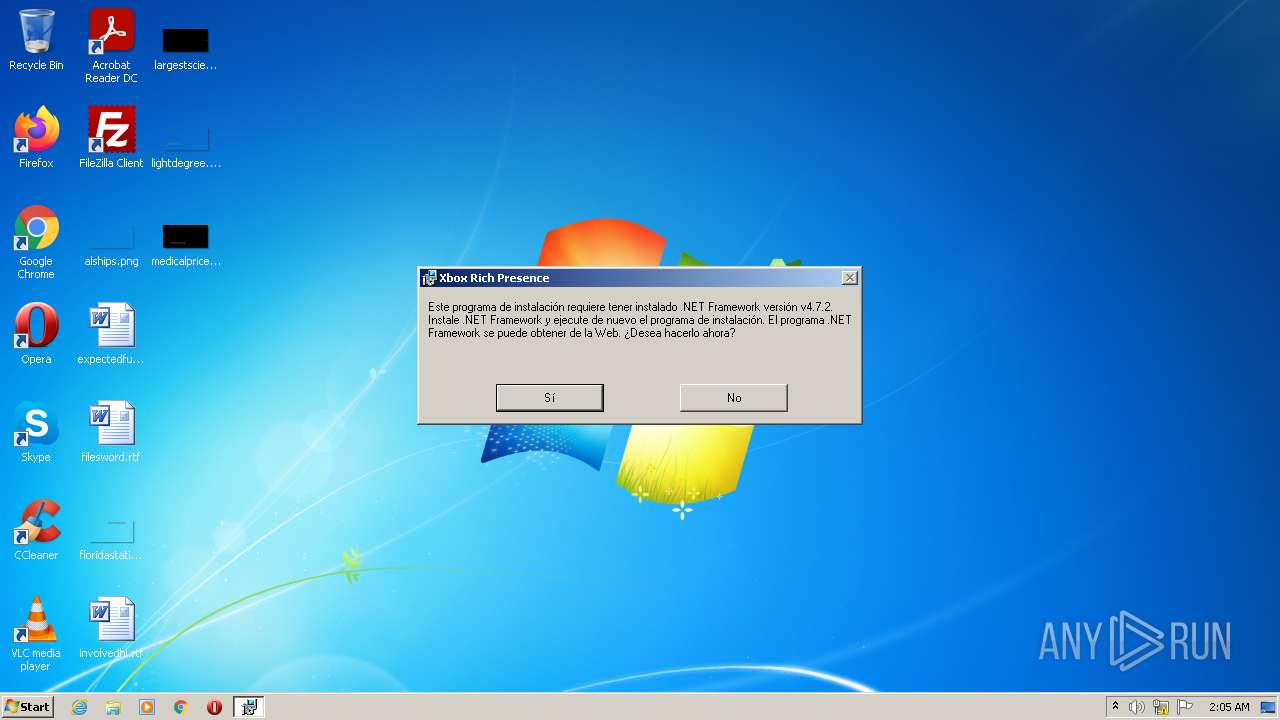
| File name: | XboxRichPresence_Setup.msi |
| Full analysis: | https://app.any.run/tasks/cc181e54-0634-43af-b088-38a6181baac9 |
| Verdict: | Malicious activity |
| Analysis date: | January 25, 2022, 02:05:21 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/x-msi |
| File info: | Composite Document File V2 Document, Little Endian, Os: Windows, Version 10.0, MSI Installer, Create Time/Date: Mon Jun 21 08:00:00 1999, Name of Creating Application: Windows Installer, Security: 1, Code page: 1252, Template: Intel;3082, Number of Pages: 200, Revision Number: {351E593E-2499-4600-BE61-0F514DF13C98}, Title: Setup, Author: MrCoolAndroid, Number of Words: 2, Last Saved Time/Date: Thu Jan 6 16:19:35 2022, Last Printed: Thu Jan 6 16:19:35 2022 |
| MD5: | 65B731BAD552E61AB2BD46274D7B52D2 |
| SHA1: | 63355B49F5B802F54A8012870D968AEA8CE5F53D |
| SHA256: | 8B5EC1767568FF2717250DA91259BC099DBB379E23A95EA8F69324CD2CD1D0C0 |
| SSDEEP: | 49152:sOBYicLXMfzBoQX8dSBNcebxhhVWKiQCIT6QrmXfNK9ZXk26knSN:zYicXMrXCSBZxliyxEO4S |
MALICIOUS
Drops executable file immediately after starts
- msiexec.exe (PID: 2256)
SUSPICIOUS
Executed as Windows Service
- msiexec.exe (PID: 3608)
Reads Windows owner or organization settings
- msiexec.exe (PID: 2256)
Reads the Windows organization settings
- msiexec.exe (PID: 2256)
Application launched itself
- msiexec.exe (PID: 3608)
Executable content was dropped or overwritten
- msiexec.exe (PID: 2256)
- iexplore.exe (PID: 1988)
Drops a file that was compiled in debug mode
- msiexec.exe (PID: 2256)
Starts Internet Explorer
- MsiExec.exe (PID: 744)
Reads Microsoft Outlook installation path
- iexplore.exe (PID: 1988)
INFO
Checks supported languages
- msiexec.exe (PID: 2256)
- msiexec.exe (PID: 3608)
- MsiExec.exe (PID: 744)
- iexplore.exe (PID: 3480)
- iexplore.exe (PID: 1988)
Reads the computer name
- msiexec.exe (PID: 2256)
- msiexec.exe (PID: 3608)
- MsiExec.exe (PID: 744)
- iexplore.exe (PID: 3480)
- iexplore.exe (PID: 1988)
Application launched itself
- iexplore.exe (PID: 3480)
Changes internet zones settings
- iexplore.exe (PID: 3480)
Checks Windows Trust Settings
- iexplore.exe (PID: 1988)
- iexplore.exe (PID: 3480)
Reads settings of System Certificates
- iexplore.exe (PID: 1988)
- iexplore.exe (PID: 3480)
Reads the date of Windows installation
- iexplore.exe (PID: 3480)
Modifies the phishing filter of IE
- iexplore.exe (PID: 3480)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .msi | | | Microsoft Windows Installer (90.2) |
|---|---|---|
| .msp | | | Windows Installer Patch (8.4) |
| .msi | | | Microsoft Installer (100) |
EXIF
FlashPix
| LastPrinted: | 2022:01:06 16:19:35 |
|---|---|
| ModifyDate: | 2022:01:06 16:19:35 |
| Words: | 2 |
| Comments: | - |
| Keywords: | - |
| Author: | MrCoolAndroid |
| Subject: | - |
| Title: | Setup |
| RevisionNumber: | {351E593E-2499-4600-BE61-0F514DF13C98} |
| Pages: | 200 |
| Template: | Intel;3082 |
| CodePage: | Windows Latin 1 (Western European) |
| Security: | Password protected |
| Software: | Windows Installer |
| CreateDate: | 1999:06:21 07:00:00 |
Total processes
39
Monitored processes
5
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 744 | C:\Windows\system32\MsiExec.exe -Embedding 431CDEFC81D75F00F3291B46B73417A7 C | C:\Windows\system32\MsiExec.exe | — | msiexec.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows� installer Exit code: 0 Version: 5.0.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1988 | "C:\Program Files\Internet Explorer\iexplore.exe" SCODEF:3480 CREDAT:267521 /prefetch:2 | C:\Program Files\Internet Explorer\iexplore.exe | iexplore.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Internet Explorer Exit code: 0 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
| 2256 | "C:\Windows\System32\msiexec.exe" /i "C:\Users\admin\AppData\Local\Temp\XboxRichPresence_Setup.msi" | C:\Windows\System32\msiexec.exe | Explorer.EXE | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows� installer Exit code: 1603 Version: 5.0.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
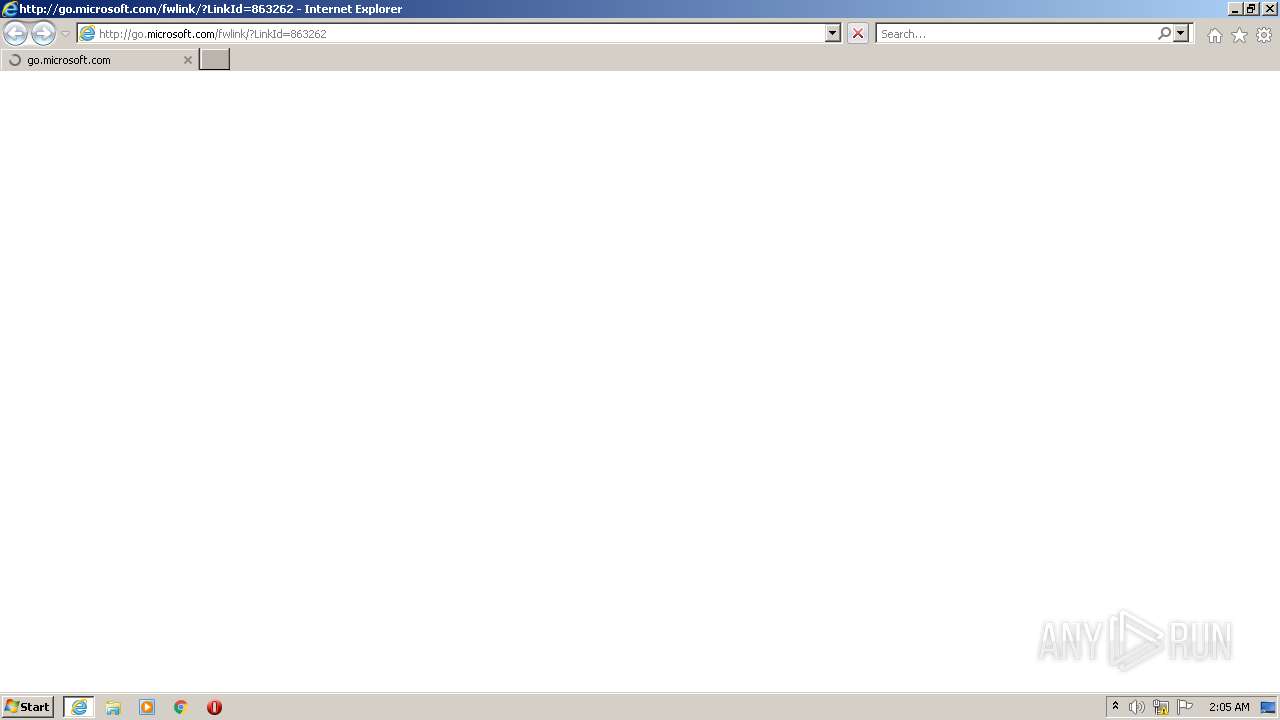
| 3480 | "C:\Program Files\Internet Explorer\iexplore.exe" http://go.microsoft.com/fwlink/?LinkId=863262 | C:\Program Files\Internet Explorer\iexplore.exe | MsiExec.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Internet Explorer Exit code: 0 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
| 3608 | C:\Windows\system32\msiexec.exe /V | C:\Windows\system32\msiexec.exe | — | services.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows� installer Exit code: 0 Version: 5.0.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
Total events
14 693
Read events
14 594
Write events
99
Delete events
0
Modification events
| (PID) Process: | (3480) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPDaysSinceLastAutoMigration |
Value: 1 | |||
| (PID) Process: | (3480) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPLastLaunchLowDateTime |
Value: 167527552 | |||
| (PID) Process: | (3480) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPLastLaunchHighDateTime |
Value: 30937488 | |||
| (PID) Process: | (3480) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\UrlBlockManager |
| Operation: | write | Name: | NextCheckForUpdateLowDateTime |
Value: 467532552 | |||
| (PID) Process: | (3480) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\UrlBlockManager |
| Operation: | write | Name: | NextCheckForUpdateHighDateTime |
Value: 30937488 | |||
| (PID) Process: | (3480) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Content |
| Operation: | write | Name: | CachePrefix |
Value: | |||
| (PID) Process: | (3480) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (3480) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
| (PID) Process: | (3480) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\Main |
| Operation: | write | Name: | CompatibilityFlags |
Value: 0 | |||
| (PID) Process: | (3480) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
Executable files
3
Suspicious files
5
Text files
5
Unknown types
2
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 1988 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\6BADA8974A10C4BD62CC921D13E43B18_711ED44619924BA6DC33E69F97E7FF63 | binary | |
MD5:— | SHA256:— | |||
| 1988 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\6BADA8974A10C4BD62CC921D13E43B18_711ED44619924BA6DC33E69F97E7FF63 | der | |
MD5:— | SHA256:— | |||
| 1988 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\57C8EDB95DF3F0AD4EE2DC2B8CFD4157 | compressed | |
MD5:F7DCB24540769805E5BB30D193944DCE | SHA256:6B88C6AC55BBD6FEA0EBE5A760D1AD2CFCE251C59D0151A1400701CB927E36EA | |||
| 1988 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\57C8EDB95DF3F0AD4EE2DC2B8CFD4157 | binary | |
MD5:— | SHA256:— | |||
| 1988 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\7423F88C7F265F0DEFC08EA88C3BDE45_AA1E8580D4EBC816148CE81268683776 | der | |
MD5:— | SHA256:— | |||
| 1988 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\7423F88C7F265F0DEFC08EA88C3BDE45_AA1E8580D4EBC816148CE81268683776 | binary | |
MD5:— | SHA256:— | |||
| 3480 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\B6QGX7LP\favicon[2].ico | image | |
MD5:DA597791BE3B6E732F0BC8B20E38EE62 | SHA256:5B2C34B3C4E8DD898B664DBA6C3786E2FF9869EFF55D673AA48361F11325ED07 | |||
| 2256 | msiexec.exe | C:\Users\admin\AppData\Local\Temp\MSIE880.tmp | executable | |
MD5:9945F10135A4C7214FA5605C21E5DE9B | SHA256:9F3B0F3AF4BFA061736935BAB1D50ED2581358DDC9A9C0DB22564ACED1A1807C | |||
| 2256 | msiexec.exe | C:\Users\admin\AppData\Local\Temp\MSIE831.tmp | executable | |
MD5:9945F10135A4C7214FA5605C21E5DE9B | SHA256:9F3B0F3AF4BFA061736935BAB1D50ED2581358DDC9A9C0DB22564ACED1A1807C | |||
| 3480 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Internet Explorer\VersionManager\versionlist.xml | xml | |
MD5:CBD0581678FA40F0EDCBC7C59E0CAD10 | SHA256:159BD4343F344A08F6AF3B716B6FA679859C1BD1D7030D26FF5EF0255B86E1D9 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
4
TCP/UDP connections
12
DNS requests
9
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
1988 | iexplore.exe | GET | 200 | 93.184.220.29:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTBL0V27RVZ7LBduom%2FnYB45SPUEwQU5Z1ZMIJHWMys%2BghUNoZ7OrUETfACEA8Ull8gIGmZT9XHrHiJQeI%3D | US | der | 1.47 Kb | whitelisted |
1988 | iexplore.exe | GET | 200 | 23.32.238.178:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?be1b941b0e4920f8 | US | compressed | 4.70 Kb | whitelisted |
1988 | iexplore.exe | GET | 200 | 23.32.238.178:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?6861b72b063ee58a | US | compressed | 4.70 Kb | whitelisted |
1988 | iexplore.exe | GET | 200 | 93.184.220.29:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | US | der | 471 b | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
1988 | iexplore.exe | 104.111.242.51:443 | go.microsoft.com | Akamai International B.V. | NL | unknown |
1988 | iexplore.exe | 23.32.238.178:80 | ctldl.windowsupdate.com | XO Communications | US | suspicious |
1988 | iexplore.exe | 93.184.220.29:80 | ocsp.digicert.com | MCI Communications Services, Inc. d/b/a Verizon Business | US | whitelisted |
3480 | iexplore.exe | 204.79.197.200:443 | www.bing.com | Microsoft Corporation | US | whitelisted |
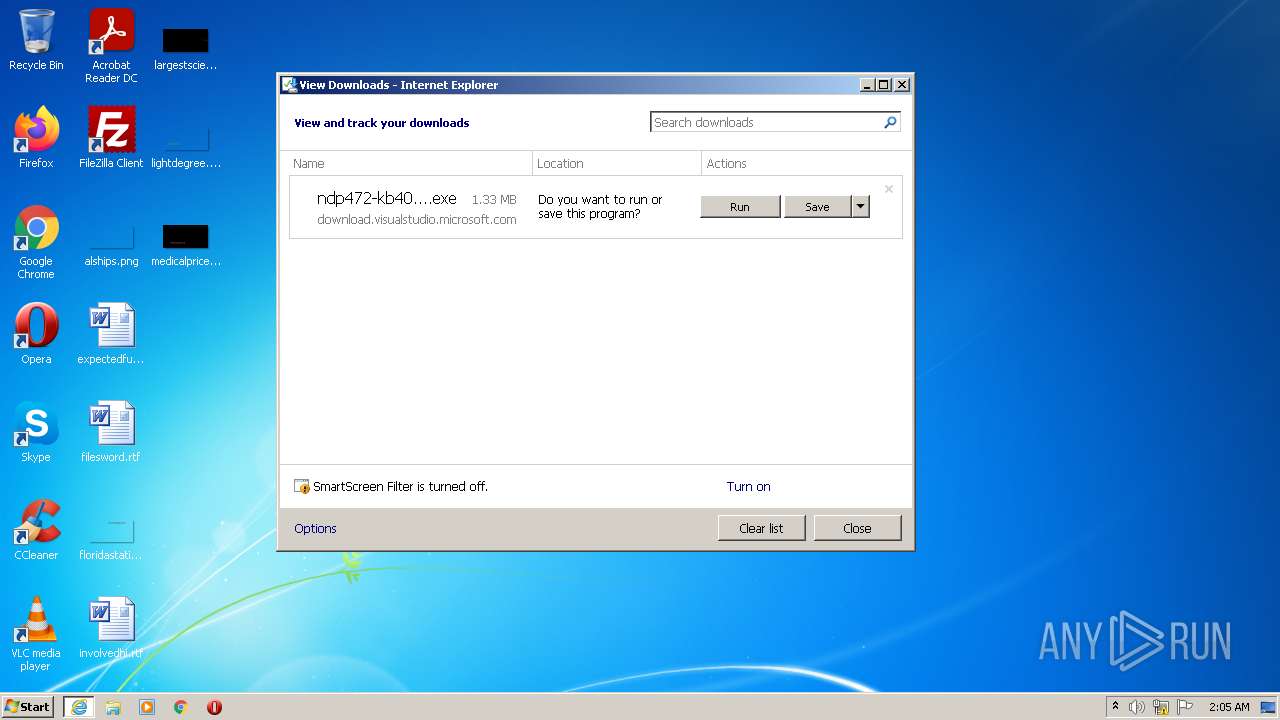
1988 | iexplore.exe | 68.232.34.200:443 | download.visualstudio.microsoft.com | MCI Communications Services, Inc. d/b/a Verizon Business | US | whitelisted |
3480 | iexplore.exe | 152.199.19.161:443 | r20swj13mr.microsoft.com | MCI Communications Services, Inc. d/b/a Verizon Business | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
go.microsoft.com |
| whitelisted |
ctldl.windowsupdate.com |
| whitelisted |
api.bing.com |
| whitelisted |
www.bing.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
download.visualstudio.microsoft.com |
| whitelisted |
r20swj13mr.microsoft.com |
| whitelisted |
iecvlist.microsoft.com |
| whitelisted |