| File name: | output.ps1 |
| Full analysis: | https://app.any.run/tasks/8f39aac2-07cd-4fd9-9d5a-af3ca0fbbd17 |
| Verdict: | Malicious activity |
| Threats: | XWorm is a remote access trojan (RAT) sold as a malware-as-a-service. It possesses an extensive hacking toolset and is capable of gathering private information and files from the infected computer, hijacking MetaMask and Telegram accounts, and tracking user activity. XWorm is typically delivered to victims' computers through multi-stage attacks that start with phishing emails. |
| Analysis date: | February 21, 2024, 13:15:38 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | text/plain |
| File info: | ASCII text, with very long lines (41009), with CRLF line terminators |
| MD5: | 4B7E38F1CE53AF19B83D3886E57A7622 |
| SHA1: | 501093A9F45CD9CE75F5C65BEC0C5129E5F5DCDE |
| SHA256: | 8B51C049CCFF081F5C28687F9943D8D2BC359DEC5C0A1D2FF82C0B76FBAF4761 |
| SSDEEP: | 1536:o6vnNBMPcaT9hWGLEGFWsN5tf1yQRhjTU:omBQTTJwGFlNjEsQ |
MALICIOUS
May hide the program window using WMI (SCRIPT)
- wscript.exe (PID: 3308)
- wscript.exe (PID: 1792)
Bypass execution policy to execute commands
- powershell.exe (PID: 2744)
- powershell.exe (PID: 1596)
Connects to the CnC server
- powershell.exe (PID: 2744)
XWORM has been detected (SURICATA)
- powershell.exe (PID: 2744)
SUSPICIOUS
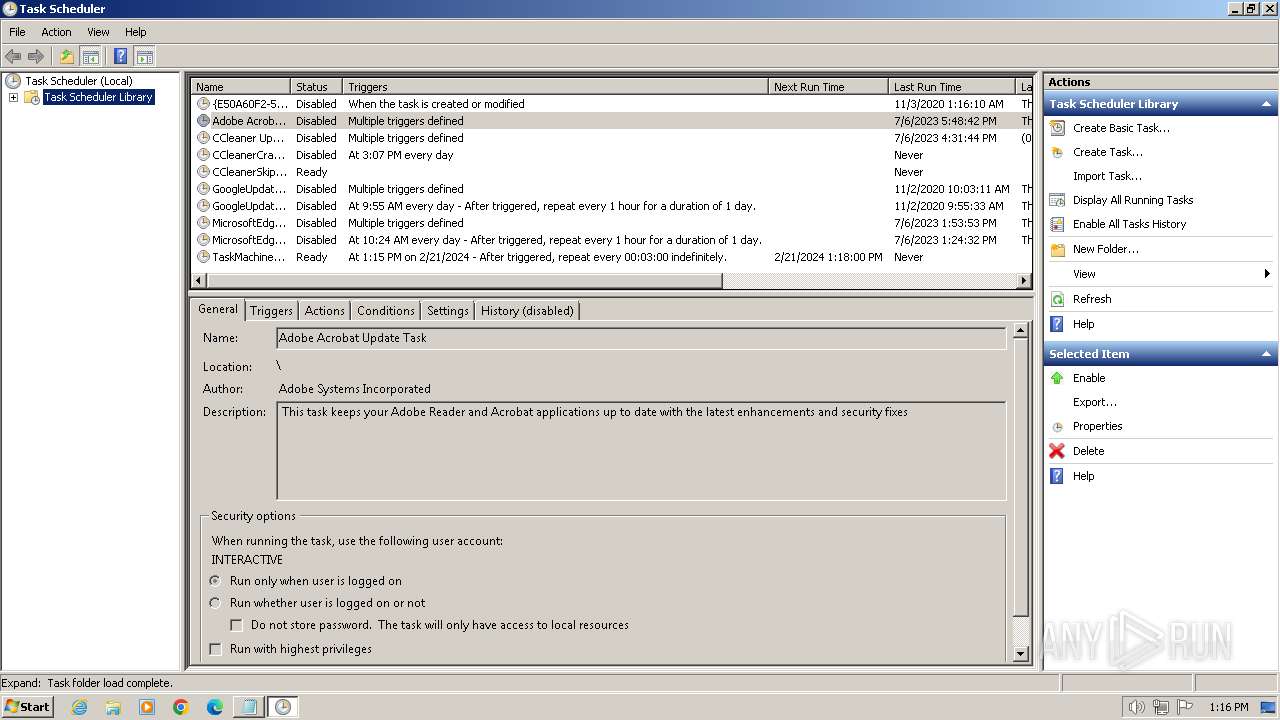
The process executes via Task Scheduler
- wscript.exe (PID: 3308)
- wscript.exe (PID: 1792)
Unusual connection from system programs
- powershell.exe (PID: 2160)
- powershell.exe (PID: 2744)
The Powershell connects to the Internet
- powershell.exe (PID: 2160)
- powershell.exe (PID: 2744)
Reads the Internet Settings
- powershell.exe (PID: 2160)
- powershell.exe (PID: 2744)
Accesses WMI object, sets custom ImpersonationLevel (SCRIPT)
- wscript.exe (PID: 3308)
- wscript.exe (PID: 1792)
Executed via WMI
- powershell.exe (PID: 2744)
- powershell.exe (PID: 1596)
Creates an object to access WMI (SCRIPT)
- wscript.exe (PID: 3308)
- wscript.exe (PID: 1792)
Connects to unusual port
- powershell.exe (PID: 2744)
INFO
Manual execution by a user
- mmc.exe (PID: 796)
- mmc.exe (PID: 2892)
- wmpnscfg.exe (PID: 664)
Creates files in the program directory
- powershell.exe (PID: 2160)
Reads the computer name
- wmpnscfg.exe (PID: 664)
Checks supported languages
- wmpnscfg.exe (PID: 664)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
53
Monitored processes
11
Malicious processes
3
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 664 | "C:\Program Files\Windows Media Player\wmpnscfg.exe" | C:\Program Files\Windows Media Player\wmpnscfg.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Media Player Network Sharing Service Configuration Application Exit code: 0 Version: 12.0.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 796 | "C:\Windows\system32\mmc.exe" "C:\Windows\system32\taskschd.msc" /s | C:\Windows\System32\mmc.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Microsoft Management Console Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1596 | powershell.exe -NoProfile -executionPolicy Bypass -Command C:/ProgramData/Local/Microsoft/PackagedEventProviders/LfSvc/IdentityCRL/365360DD-2683-46DB-B389-6FF680AC4EA4.ps1 | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | — | WmiPrvSE.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Exit code: 0 Version: 10.0.14409.1005 (rs1_srvoob.161208-1155) Modules
| |||||||||||||||
| 1792 | C:\Windows\System32\WScript.exe "C:\ProgramData\Local\Microsoft\PackagedEventProviders\LfSvc\365360DD-2683-46DB-B389-6FF680AC4EA4.vbs" | C:\Windows\System32\wscript.exe | — | taskeng.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft ® Windows Based Script Host Exit code: 0 Version: 5.8.7600.16385 Modules
| |||||||||||||||
| 2160 | "C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe" "-file" "C:\Users\admin\AppData\Local\Temp\output.ps1" | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Exit code: 0 Version: 10.0.14409.1005 (rs1_srvoob.161208-1155) Modules
| |||||||||||||||
| 2328 | C:\Windows\system32\DllHost.exe /Processid:{76D0CB12-7604-4048-B83C-1005C7DDC503} | C:\Windows\System32\dllhost.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: COM Surrogate Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2744 | powershell.exe -NoProfile -executionPolicy Bypass -Command C:/ProgramData/Local/Microsoft/PackagedEventProviders/LfSvc/IdentityCRL/365360DD-2683-46DB-B389-6FF680AC4EA4.ps1 | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | WmiPrvSE.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Exit code: 0 Version: 10.0.14409.1005 (rs1_srvoob.161208-1155) Modules
| |||||||||||||||
| 2892 | "C:\Windows\system32\mmc.exe" "C:\Windows\system32\taskschd.msc" /s | C:\Windows\System32\mmc.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Management Console Exit code: 3221226540 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3308 | C:\Windows\System32\WScript.exe "C:\ProgramData\Local\Microsoft\PackagedEventProviders\LfSvc\365360DD-2683-46DB-B389-6FF680AC4EA4.vbs" | C:\Windows\System32\wscript.exe | — | taskeng.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft ® Windows Based Script Host Exit code: 0 Version: 5.8.7600.16385 Modules
| |||||||||||||||
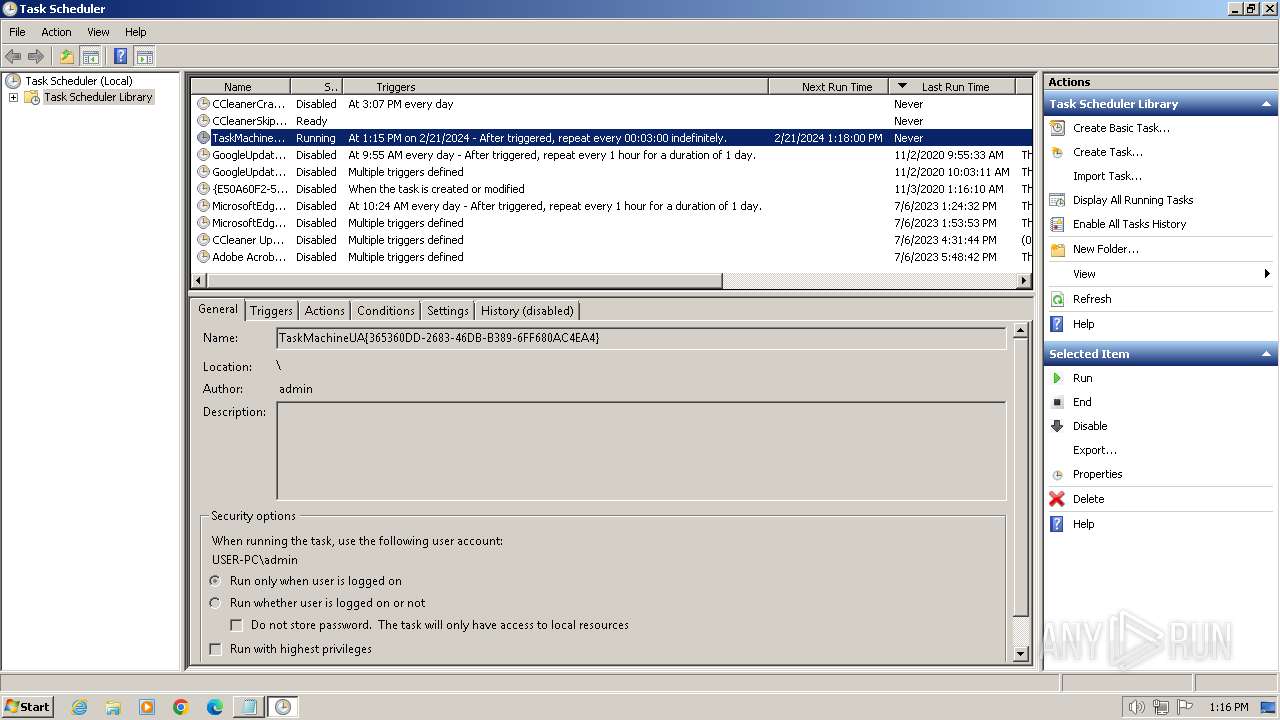
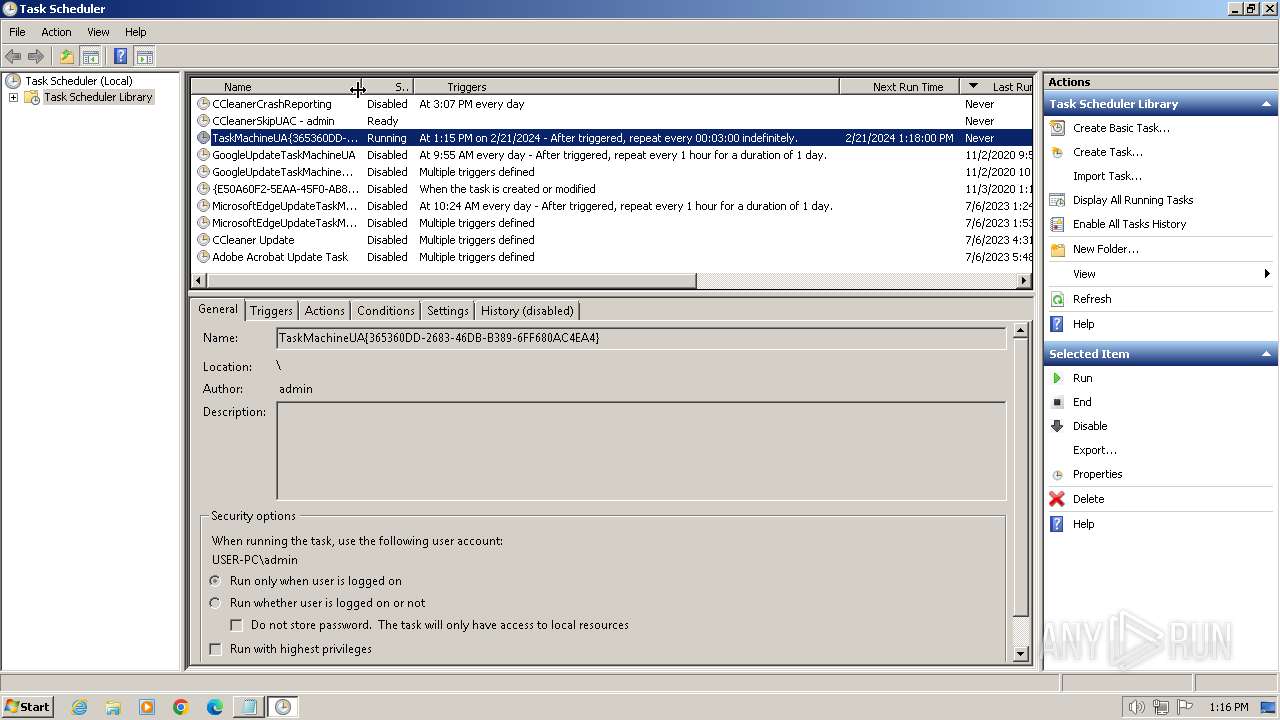
| 3464 | "C:\Windows\system32\schtasks.exe" /create /tn TaskMachineUA{365360DD-2683-46DB-B389-6FF680AC4EA4} /tr C:\ProgramData\Local\Microsoft\PackagedEventProviders\LfSvc\365360DD-2683-46DB-B389-6FF680AC4EA4.vbs /sc minute /mo 3 | C:\Windows\System32\schtasks.exe | — | powershell.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Manages scheduled tasks Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
Total events
14 657
Read events
14 572
Write events
84
Delete events
1
Modification events
| (PID) Process: | (2160) powershell.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\182\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (2160) powershell.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (2160) powershell.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
| (PID) Process: | (2160) powershell.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 1 | |||
| (PID) Process: | (2160) powershell.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 0 | |||
| (PID) Process: | (2328) dllhost.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Direct3D\MostRecentApplication |
| Operation: | write | Name: | Name |
Value: DllHost.exe | |||
| (PID) Process: | (2328) dllhost.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows Photo Viewer\Viewer |
| Operation: | write | Name: | MainWndPos |
Value: 6000000034000000A00400008002000000000000 | |||
| (PID) Process: | (796) mmc.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\MMC\SnapIns\FX:{c7b8fb06-bfe1-4c2e-9217-7a69a95bbac4} |
| Operation: | write | Name: | HelpTopic |
Value: C:\Windows\Help\taskscheduler.chm | |||
| (PID) Process: | (796) mmc.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\MMC\SnapIns\FX:{c7b8fb06-bfe1-4c2e-9217-7a69a95bbac4} |
| Operation: | write | Name: | LinkedHelpTopics |
Value: C:\Windows\Help\taskscheduler.chm | |||
| (PID) Process: | (796) mmc.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Microsoft Management Console\Recent File List |
| Operation: | delete key | Name: | (default) |
Value: | |||
Executable files
0
Suspicious files
5
Text files
4
Unknown types
6
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2160 | powershell.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\4B81KPH27NNL9BR124RT.temp | binary | |
MD5:42E3956892291F5EE35E1B989213EF05 | SHA256:D4E6947871B5FD00AD32F8707479DD6EC92AB65D8C6D157B1C0C3D99D575E468 | |||
| 2160 | powershell.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\d93f411851d7c929.customDestinations-ms~RF17f695.TMP | binary | |
MD5:0268C3470C936E6FBAC2945B9E1C2099 | SHA256:DF2AF58E8879B48826D8A418ED3B02CC8D484BCFC231C5B7A11BD153ED3998E9 | |||
| 2160 | powershell.exe | C:\Users\admin\AppData\Local\Temp\nunexqmh.1fv.psm1 | binary | |
MD5:C4CA4238A0B923820DCC509A6F75849B | SHA256:— | |||
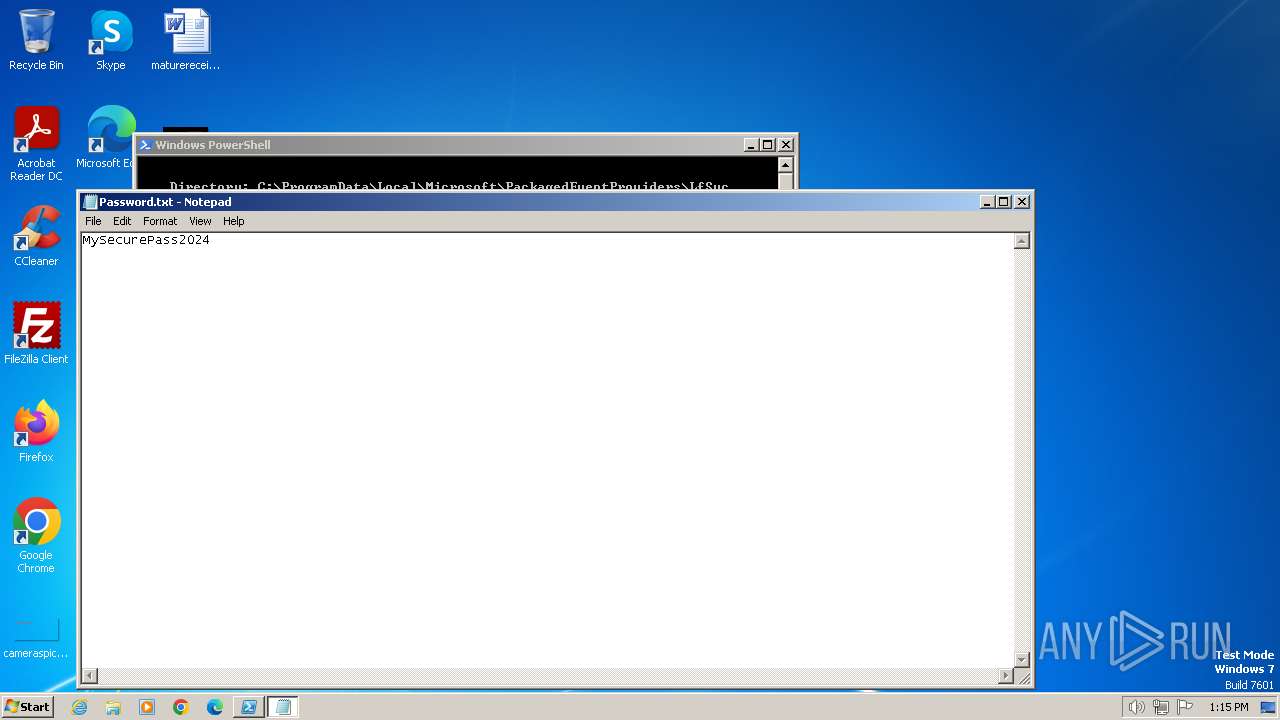
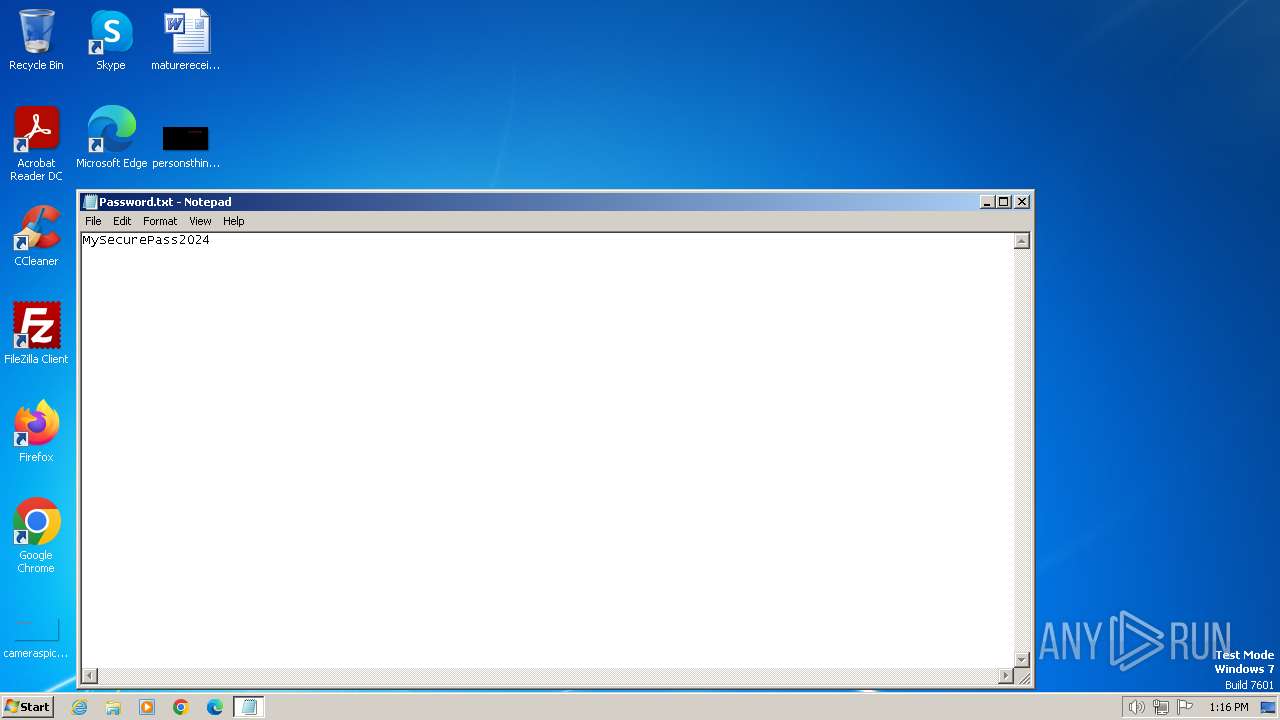
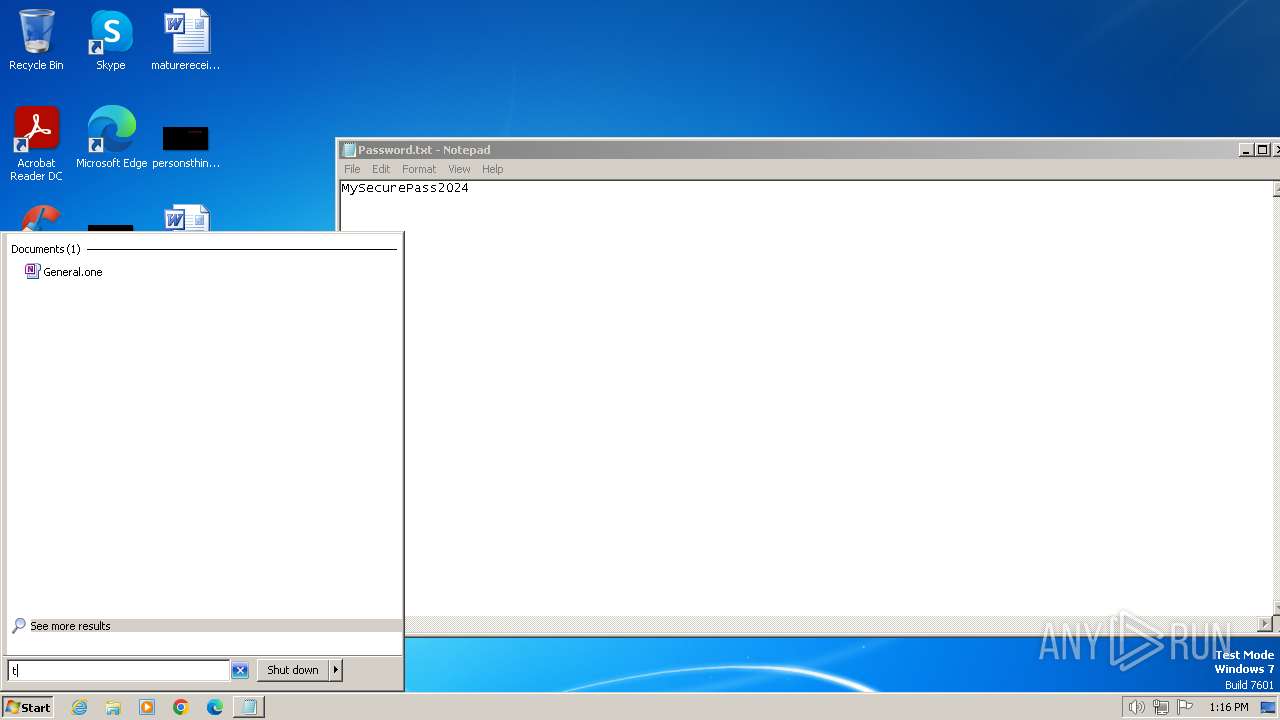
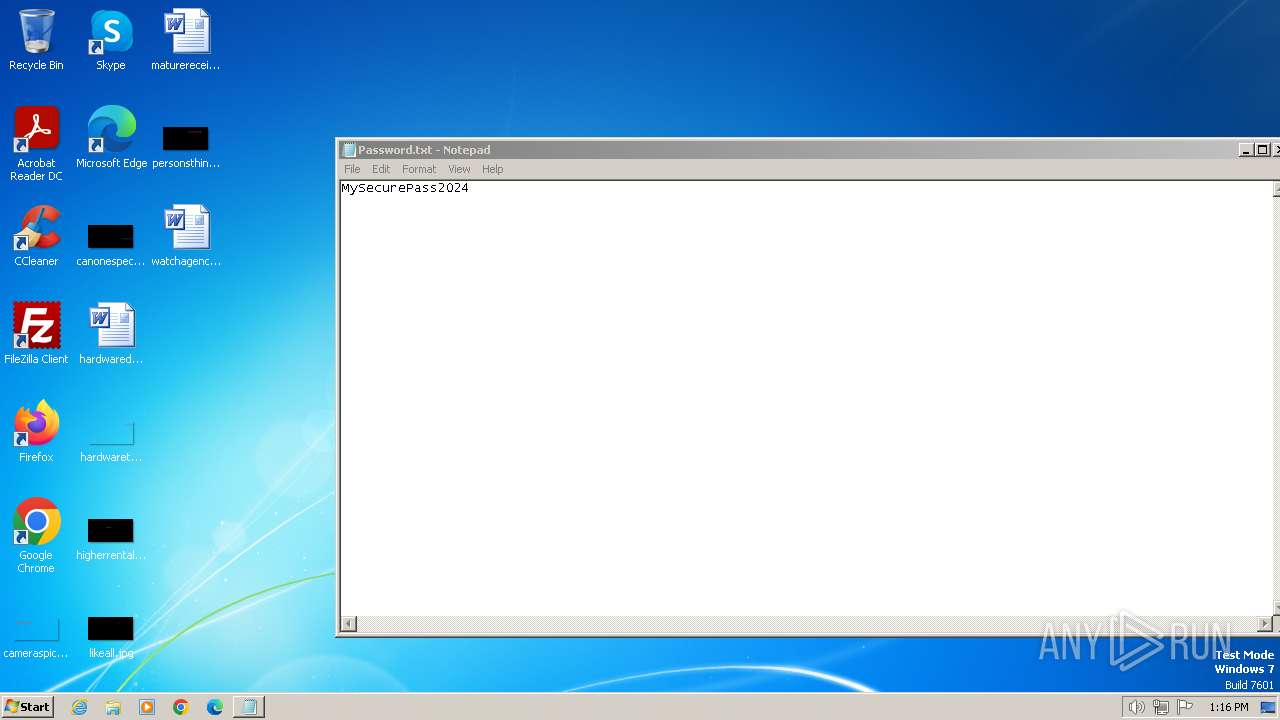
| 2160 | powershell.exe | C:\Users\admin\AppData\Local\Temp\Password.txt | text | |
MD5:85229641BC4CB53CAB2FB5B7880CB05D | SHA256:3123597AEF47EE6E7E567682F9D5BEB4E3BF1148AF5671A9DC0A588DCE44D7D6 | |||
| 2160 | powershell.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\PowerShell\StartupProfileData-NonInteractive | dbf | |
MD5:446DD1CF97EABA21CF14D03AEBC79F27 | SHA256:A7DE5177C68A64BD48B36D49E2853799F4EBCFA8E4761F7CC472F333DC5F65CF | |||
| 2160 | powershell.exe | C:\ProgramData\Local\Microsoft\PackagedEventProviders\LfSvc\365360DD-2683-46DB-B389-6FF680AC4EA4.vbs | text | |
MD5:3FA121AC5483D7DD18C26B1AD953F5DF | SHA256:3436CEB0317E95732D80EE61A1CB6ADD072C55DBD398CF0FA44BFE2143CCAB45 | |||
| 2744 | powershell.exe | C:\Users\admin\AppData\Local\Temp\0hzku4z1.skg.ps1 | binary | |
MD5:C4CA4238A0B923820DCC509A6F75849B | SHA256:— | |||
| 2744 | powershell.exe | C:\Users\admin\AppData\Local\Temp\kk34qy13.syp.psm1 | binary | |
MD5:C4CA4238A0B923820DCC509A6F75849B | SHA256:— | |||
| 2160 | powershell.exe | C:\Users\admin\AppData\Local\Temp\edrj0cal.ceb.ps1 | binary | |
MD5:C4CA4238A0B923820DCC509A6F75849B | SHA256:— | |||
| 2160 | powershell.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\d93f411851d7c929.customDestinations-ms | binary | |
MD5:42E3956892291F5EE35E1B989213EF05 | SHA256:D4E6947871B5FD00AD32F8707479DD6EC92AB65D8C6D157B1C0C3D99D575E468 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
1
TCP/UDP connections
7
DNS requests
3
Threats
12
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
2160 | powershell.exe | GET | 200 | 54.87.207.250:80 | http://54.87.207.250/FKAWMCIQISOOSNOEMTS/Password.txt | unknown | text | 16 b | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
1080 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |
2160 | powershell.exe | 54.87.207.250:80 | — | AMAZON-AES | US | unknown |
2744 | powershell.exe | 188.114.96.3:443 | paste.ee | CLOUDFLARENET | NL | unknown |
2744 | powershell.exe | 91.92.245.113:7000 | showtime24.store | Natskovi & Sie Ltd. | BG | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
paste.ee |
| shared |
showtime24.store |
| unknown |
dns.msftncsi.com |
| shared |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2160 | powershell.exe | Not Suspicious Traffic | ET INFO Windows Powershell User-Agent Usage |
2744 | powershell.exe | Potential Corporate Privacy Violation | ET POLICY Pastebin-style Service (paste .ee) in TLS SNI |
2744 | powershell.exe | Misc Attack | ET DROP Spamhaus DROP Listed Traffic Inbound group 7 |
2744 | powershell.exe | Malware Command and Control Activity Detected | REMOTE [ANY.RUN] Xworm Network Packet |
8 ETPRO signatures available at the full report
Process | Message |
|---|---|
mmc.exe | Constructor: Microsoft.TaskScheduler.SnapIn.TaskSchedulerSnapIn
|
mmc.exe | OnInitialize: Microsoft.TaskScheduler.SnapIn.TaskSchedulerSnapIn
|
mmc.exe | AddIcons: Microsoft.TaskScheduler.SnapIn.TaskSchedulerSnapIn
|
mmc.exe | ProcessCommandLineArguments: Microsoft.TaskScheduler.SnapIn.TaskSchedulerSnapIn
|