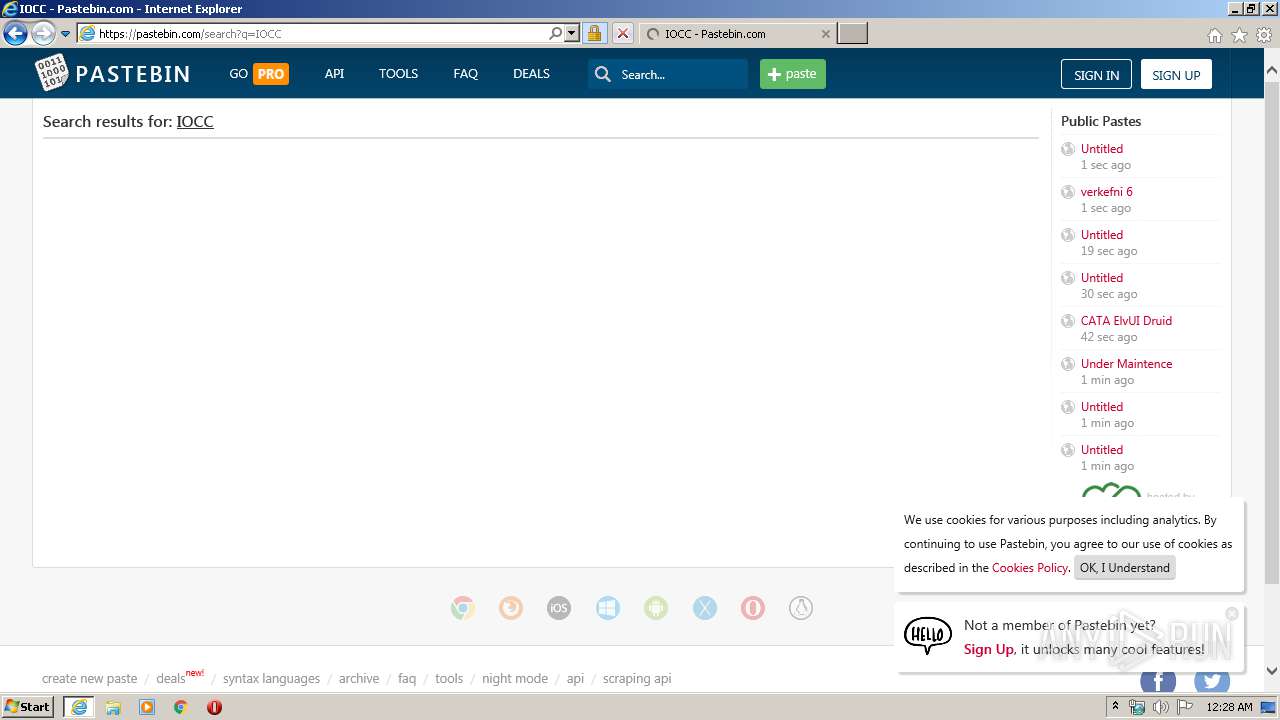
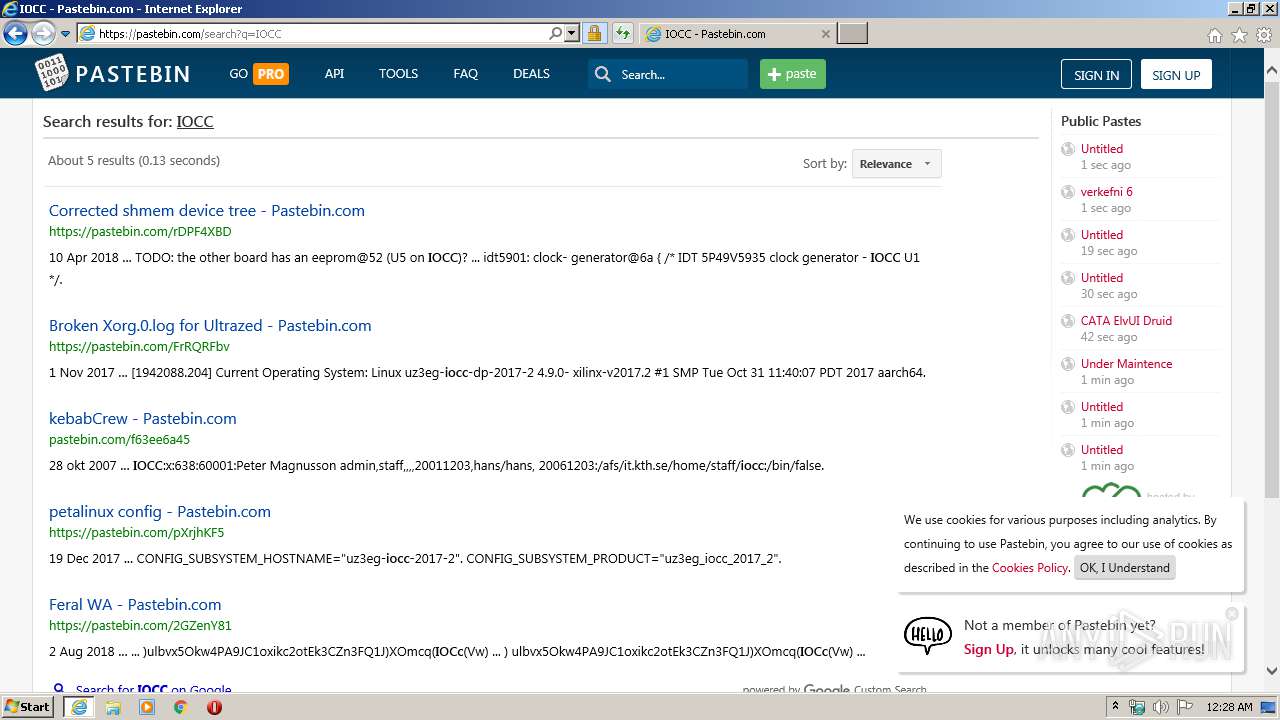
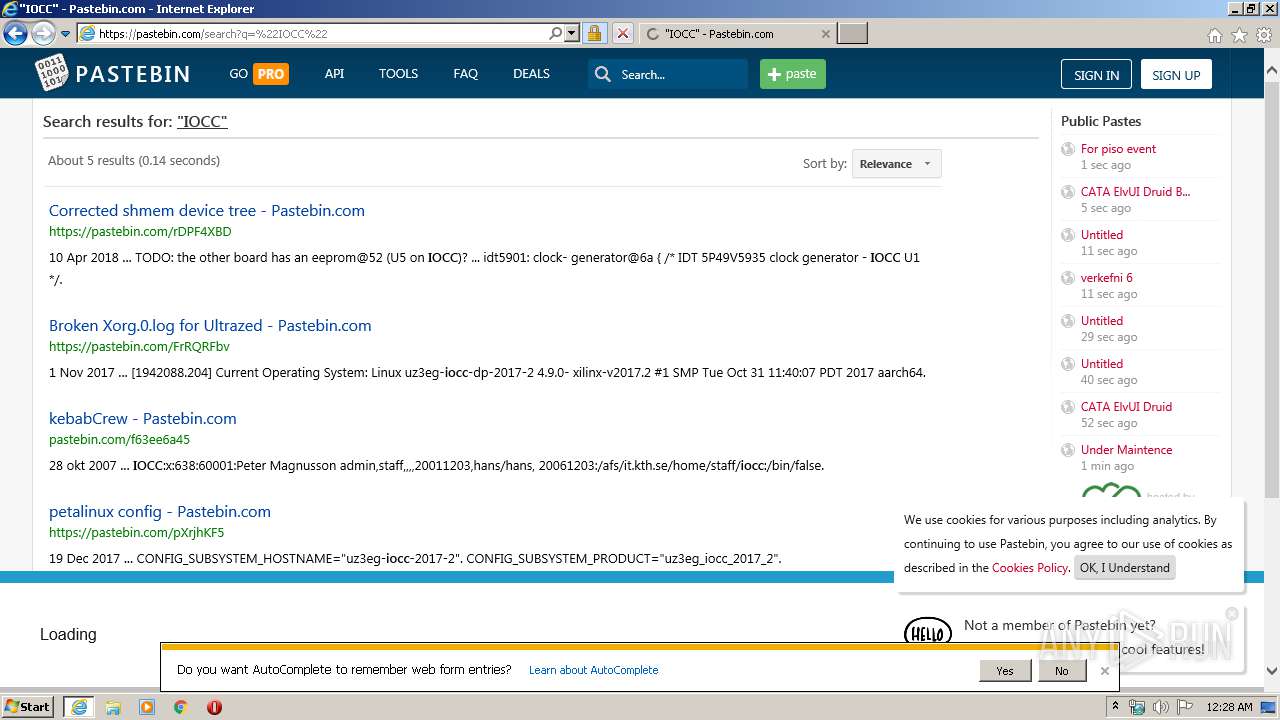
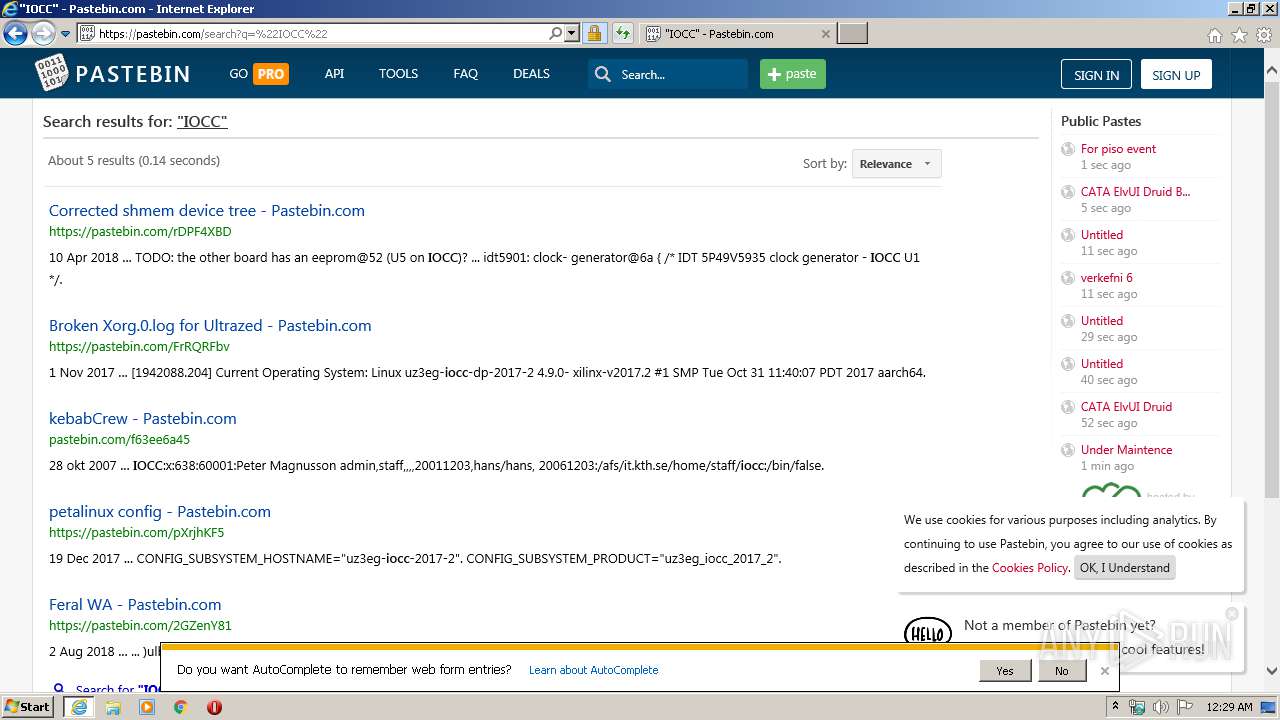
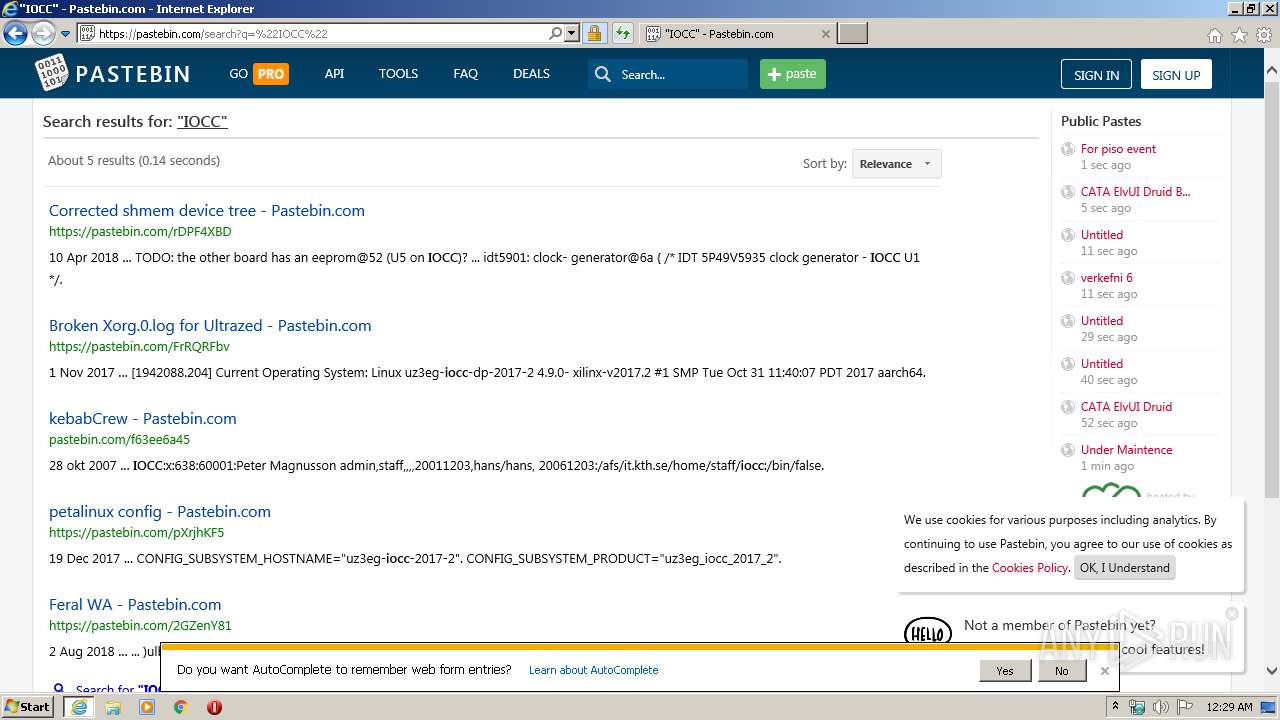
| URL: | http://pastebin.com |
| Full analysis: | https://app.any.run/tasks/f96bcc26-5078-4844-8a4a-01d6d487bf04 |
| Verdict: | Malicious activity |
| Analysis date: | February 22, 2020, 00:28:18 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MD5: | BFFB75A18F97A7C0E82BD3466FB4BCD9 |
| SHA1: | 5E0B147D42B45C592A4958CE9166535B70D8FB0D |
| SHA256: | 8B4E56B3A474A3071037C8CDC57BE4209238FDA6670C36384E92CBFE05407F77 |
| SSDEEP: | 3:N1KOEWRiMLZI:CO/V2 |
MALICIOUS
No malicious indicators.SUSPICIOUS
Disables Form Suggestion in IE
- iexplore.exe (PID: 1440)
INFO
Reads Internet Cache Settings
- iexplore.exe (PID: 1440)
- iexplore.exe (PID: 3592)
Changes internet zones settings
- iexplore.exe (PID: 1440)
Application launched itself
- iexplore.exe (PID: 1440)
Dropped object may contain Bitcoin addresses
- iexplore.exe (PID: 3592)
Reads internet explorer settings
- iexplore.exe (PID: 3592)
Creates files in the user directory
- iexplore.exe (PID: 1440)
- iexplore.exe (PID: 3592)
Reads settings of System Certificates
- iexplore.exe (PID: 1440)
Changes settings of System certificates
- iexplore.exe (PID: 1440)
Adds / modifies Windows certificates
- iexplore.exe (PID: 1440)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
36
Monitored processes
2
Malicious processes
0
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1440 | "C:\Program Files\Internet Explorer\iexplore.exe" "http://pastebin.com" | C:\Program Files\Internet Explorer\iexplore.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Internet Explorer Exit code: 0 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
| 3592 | "C:\Program Files\Internet Explorer\iexplore.exe" SCODEF:1440 CREDAT:267521 /prefetch:2 | C:\Program Files\Internet Explorer\iexplore.exe | iexplore.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Internet Explorer Exit code: 0 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
Total events
6 227
Read events
902
Write events
3 609
Delete events
1 716
Modification events
| (PID) Process: | (3592) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\LowCache\Content |
| Operation: | write | Name: | CachePrefix |
Value: | |||
| (PID) Process: | (3592) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\LowCache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (3592) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\LowCache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
| (PID) Process: | (1440) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\UrlBlockManager |
| Operation: | write | Name: | NextCheckForUpdateLowDateTime |
Value: 357961470 | |||
| (PID) Process: | (1440) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\UrlBlockManager |
| Operation: | write | Name: | NextCheckForUpdateHighDateTime |
Value: 30796055 | |||
| (PID) Process: | (1440) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Content |
| Operation: | write | Name: | CachePrefix |
Value: | |||
| (PID) Process: | (1440) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (1440) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
| (PID) Process: | (1440) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\Main |
| Operation: | write | Name: | CompatibilityFlags |
Value: 0 | |||
| (PID) Process: | (1440) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings |
| Operation: | write | Name: | ProxyEnable |
Value: 0 | |||
Executable files
0
Suspicious files
230
Text files
199
Unknown types
105
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3592 | iexplore.exe | C:\Users\admin\AppData\Local\Temp\Low\Cab6DF5.tmp | — | |
MD5:— | SHA256:— | |||
| 3592 | iexplore.exe | C:\Users\admin\AppData\Local\Temp\Low\Tar6DF6.tmp | — | |
MD5:— | SHA256:— | |||
| 3592 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\6BADA8974A10C4BD62CC921D13E43B18_74167E25E5476CCA2A5946AAA61BF9E1 | der | |
MD5:— | SHA256:— | |||
| 3592 | iexplore.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Cookies\Low\8QU1CQCK.txt | text | |
MD5:— | SHA256:— | |||
| 3592 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\MFAQUS6V\pastebin.min.v9[1].css | text | |
MD5:— | SHA256:— | |||
| 3592 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\6BADA8974A10C4BD62CC921D13E43B18_74167E25E5476CCA2A5946AAA61BF9E1 | binary | |
MD5:— | SHA256:— | |||
| 3592 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\YTOWV792\pastebin.min.v3[1].js | text | |
MD5:— | SHA256:— | |||
| 3592 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\5IWPIAR9\select2.min[1].css | text | |
MD5:— | SHA256:— | |||
| 3592 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\CFE86DBBE02D859DC92F1E17E0574EE8_46766FC45507C0B9E264E4C18BC7288B | binary | |
MD5:— | SHA256:— | |||
| 3592 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\DY534W2X\header_bg[1].png | image | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
119
TCP/UDP connections
240
DNS requests
99
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
3592 | iexplore.exe | GET | 301 | 104.23.98.190:80 | http://pastebin.com/ | US | — | — | malicious |
3592 | iexplore.exe | GET | 200 | 2.16.186.11:80 | http://ocsp.int-x3.letsencrypt.org/MFMwUTBPME0wSzAJBgUrDgMCGgUABBR%2B5mrncpqz%2FPiiIGRsFqEtYHEIXQQUqEpqYwR93brm0Tm3pkVl7%2FOo7KECEgTKD08ug1ewuLziNIDJxgY4sg%3D%3D | unknown | der | 527 b | whitelisted |
3592 | iexplore.exe | GET | 200 | 216.58.210.3:80 | http://ocsp.pki.goog/gsr2/ME4wTDBKMEgwRjAJBgUrDgMCGgUABBTgXIsxbvr2lBkPpoIEVRE6gHlCnAQUm%2BIHV2ccHsBqBt5ZtJot39wZhi4CDQHjtJqhjYqpgSVpULg%3D | US | der | 468 b | whitelisted |
3592 | iexplore.exe | GET | 200 | 93.184.220.29:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTBL0V27RVZ7LBduom%2FnYB45SPUEwQU5Z1ZMIJHWMys%2BghUNoZ7OrUETfACEA%2Fz5hY5qj0aEmX0H4s05bY%3D | US | der | 1.47 Kb | whitelisted |
3592 | iexplore.exe | GET | 200 | 2.16.186.11:80 | http://isrg.trustid.ocsp.identrust.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBRv9GhNQxLSSGKBnMArPUcsHYovpgQUxKexpHsscfrb4UuQdf%2FEFWCFiRACEAoBQUIAAAFThXNqC4Xspwg%3D | unknown | der | 1.37 Kb | whitelisted |
3592 | iexplore.exe | GET | 200 | 151.139.128.14:80 | http://ocsp.trust-provider.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBR8sWZUnKvbRO5iJhat9GV793rVlAQUrb2YejS0Jvf6xCZU7wO94CTLVBoCEENSAj%2F6qJAfE5%2Fj9OXBRE4%3D | US | der | 471 b | whitelisted |
3592 | iexplore.exe | GET | 200 | 93.184.220.29:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAH9o%2BtuynXIiEOLckvPvJE%3D | US | der | 471 b | whitelisted |
3592 | iexplore.exe | GET | 200 | 151.139.128.14:80 | http://ocsp.comodoca4.com/MFIwUDBOMEwwSjAJBgUrDgMCGgUABBTOpjOEf6LG1z52jqAxwDlTxoaOCgQUQAlhZ%2FC8g3FP3hIILG%2FU1Ct2PZYCEQDKl00c0RK6%2BBDF41XhwvTi | US | der | 281 b | whitelisted |
3592 | iexplore.exe | GET | 200 | 2.16.186.11:80 | http://ocsp.int-x3.letsencrypt.org/MFMwUTBPME0wSzAJBgUrDgMCGgUABBR%2B5mrncpqz%2FPiiIGRsFqEtYHEIXQQUqEpqYwR93brm0Tm3pkVl7%2FOo7KECEgTKD08ug1ewuLziNIDJxgY4sg%3D%3D | unknown | der | 527 b | whitelisted |
3592 | iexplore.exe | GET | 200 | 151.139.128.14:80 | http://ocsp.usertrust.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTNMNJMNDqCqx8FcBWK16EHdimS6QQUU3m%2FWqorSs9UgOHYm8Cd8rIDZssCEBN9U5yqfDGppDNwGWiEeo0%3D | US | der | 727 b | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
3592 | iexplore.exe | 104.23.98.190:80 | — | Cloudflare Inc | US | malicious |
3592 | iexplore.exe | 104.23.98.190:443 | — | Cloudflare Inc | US | malicious |
3592 | iexplore.exe | 93.184.220.29:80 | ocsp.digicert.com | MCI Communications Services, Inc. d/b/a Verizon Business | US | whitelisted |
3592 | iexplore.exe | 74.117.181.81:443 | aj2073.online | WZ Communications Inc. | US | unknown |
3592 | iexplore.exe | 216.58.210.3:80 | ocsp.pki.goog | Google Inc. | US | whitelisted |
3592 | iexplore.exe | 216.58.205.238:443 | www.google-analytics.com | Google Inc. | US | whitelisted |
3592 | iexplore.exe | 74.125.140.155:443 | stats.g.doubleclick.net | Google Inc. | US | whitelisted |
3592 | iexplore.exe | 2.16.186.35:80 | isrg.trustid.ocsp.identrust.com | Akamai International B.V. | — | whitelisted |
3592 | iexplore.exe | 2.16.186.11:80 | isrg.trustid.ocsp.identrust.com | Akamai International B.V. | — | whitelisted |
3592 | iexplore.exe | 104.26.14.238:443 | services.vlitag.com | Cloudflare Inc | US | suspicious |
DNS requests
Domain | IP | Reputation |
|---|---|---|
pastebin.com |
| malicious |
ocsp.digicert.com |
| whitelisted |
www.googletagmanager.com |
| whitelisted |
services.vlitag.com |
| shared |
aj2073.online |
| unknown |
ocsp.pki.goog |
| whitelisted |
tag.vlitag.com |
| whitelisted |
www.google-analytics.com |
| whitelisted |
isrg.trustid.ocsp.identrust.com |
| whitelisted |
ocsp.int-x3.letsencrypt.org |
| whitelisted |