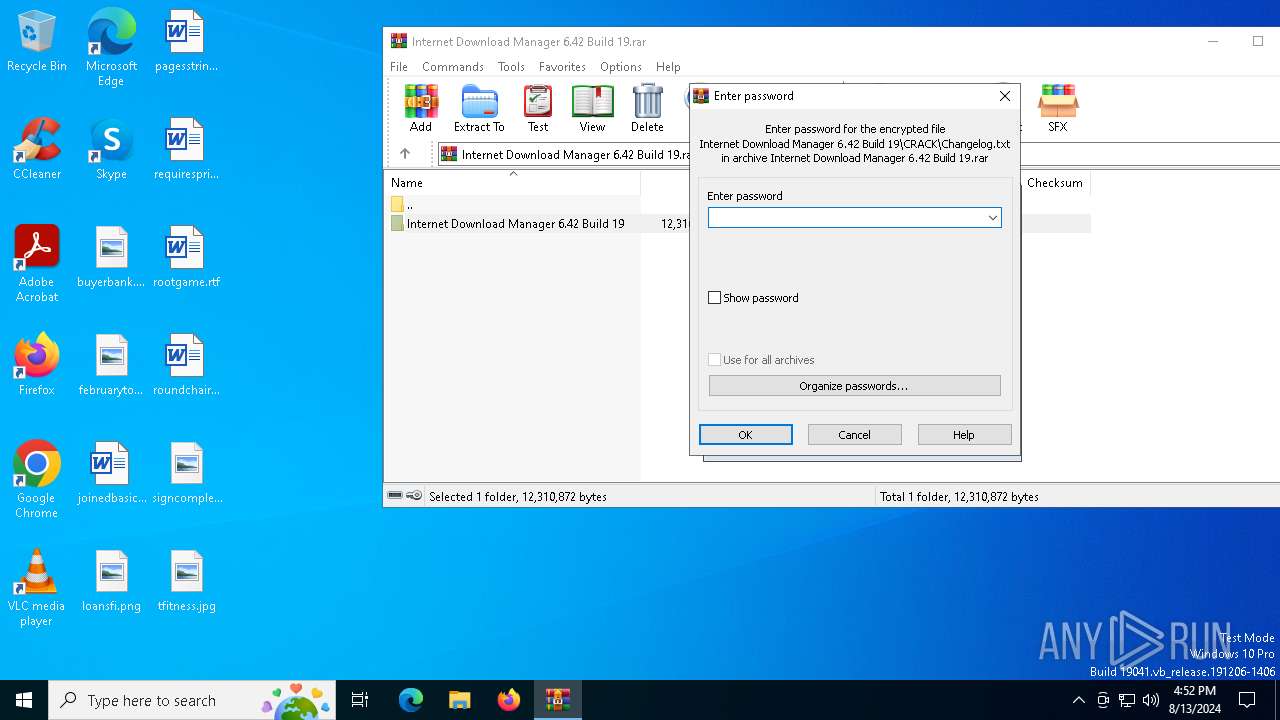
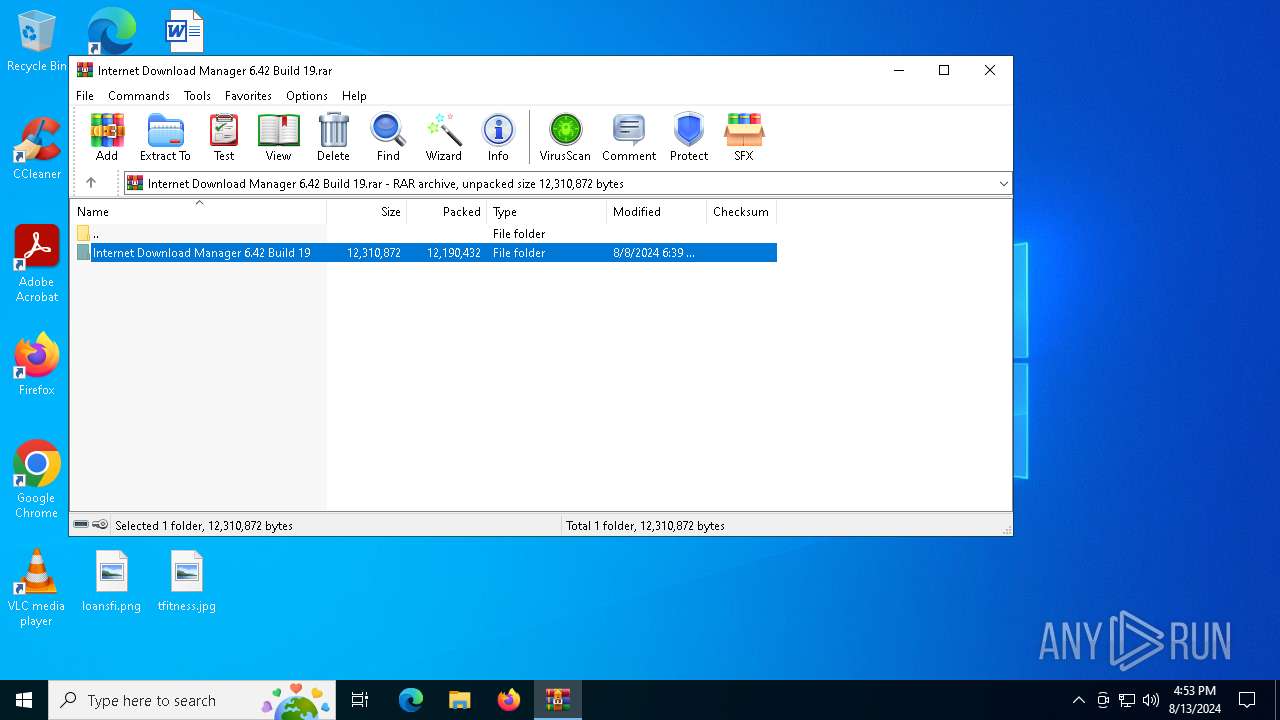
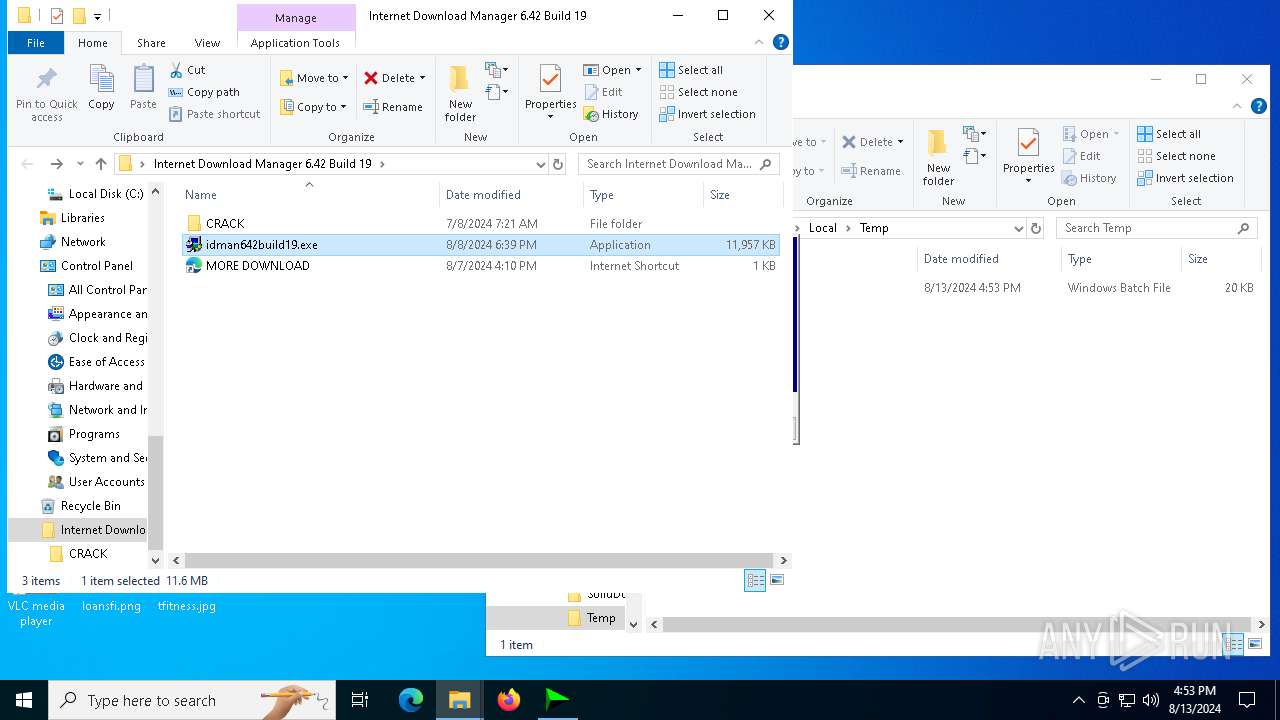
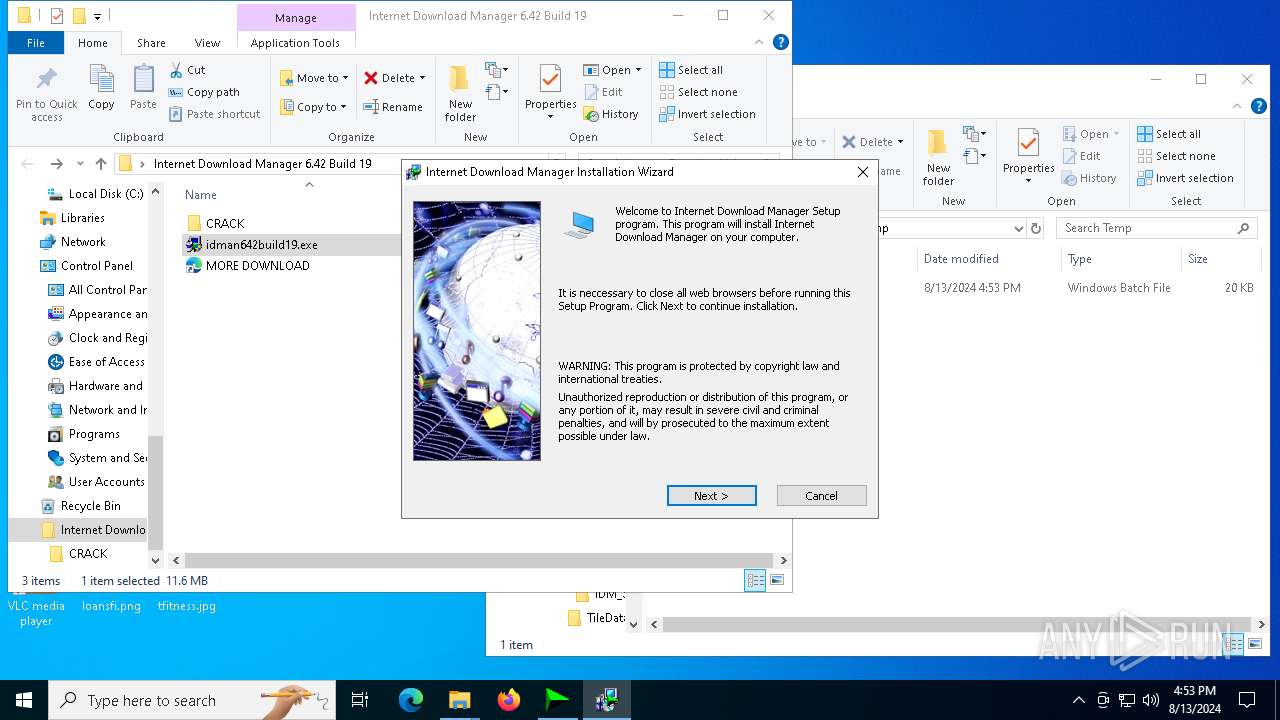
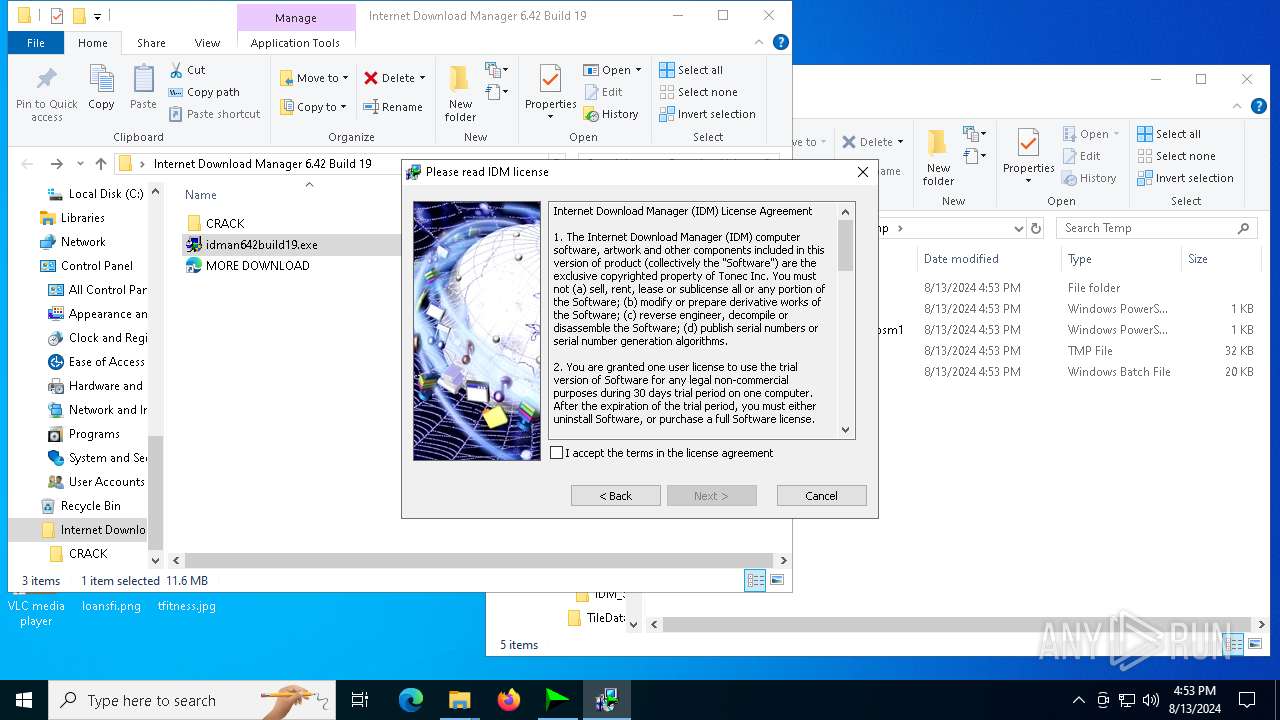
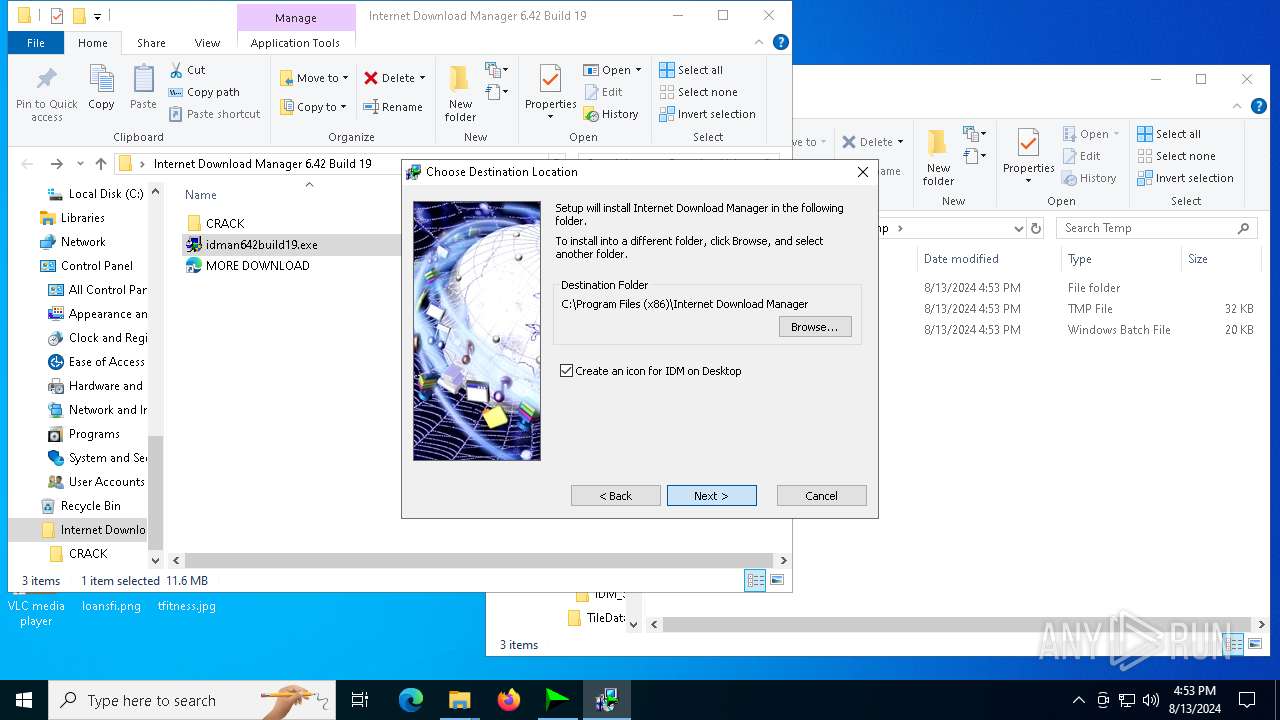
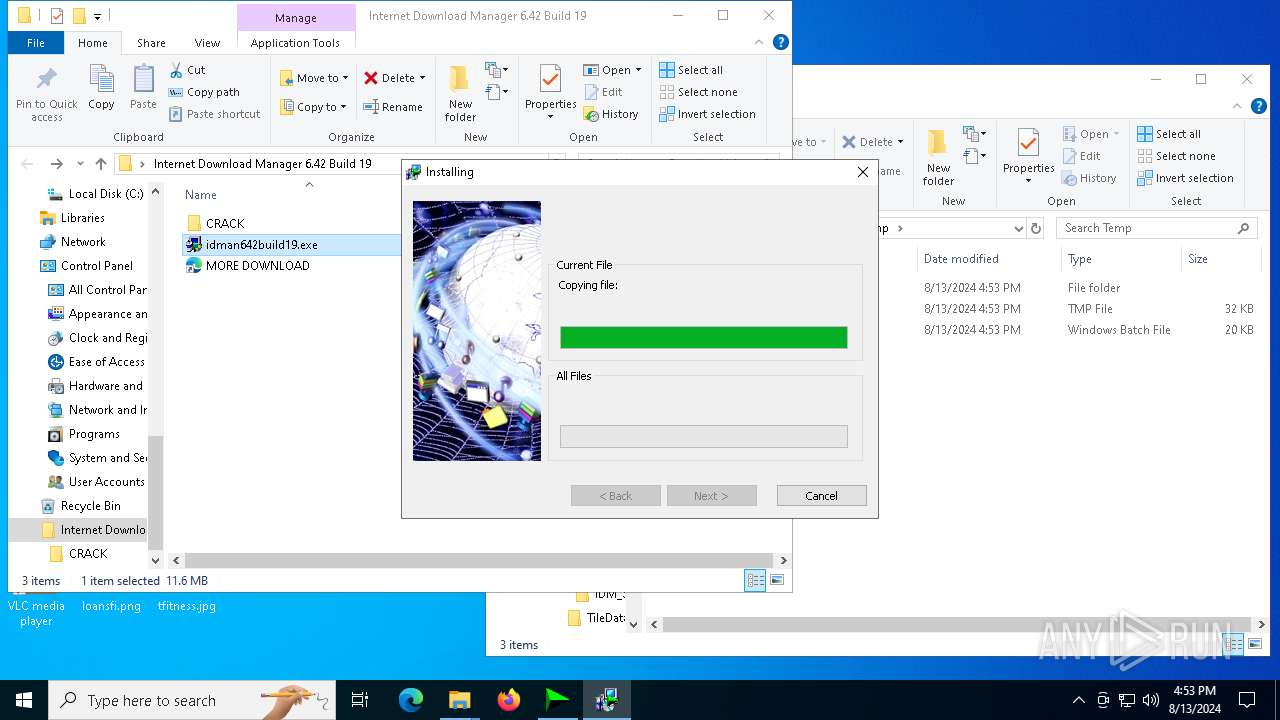
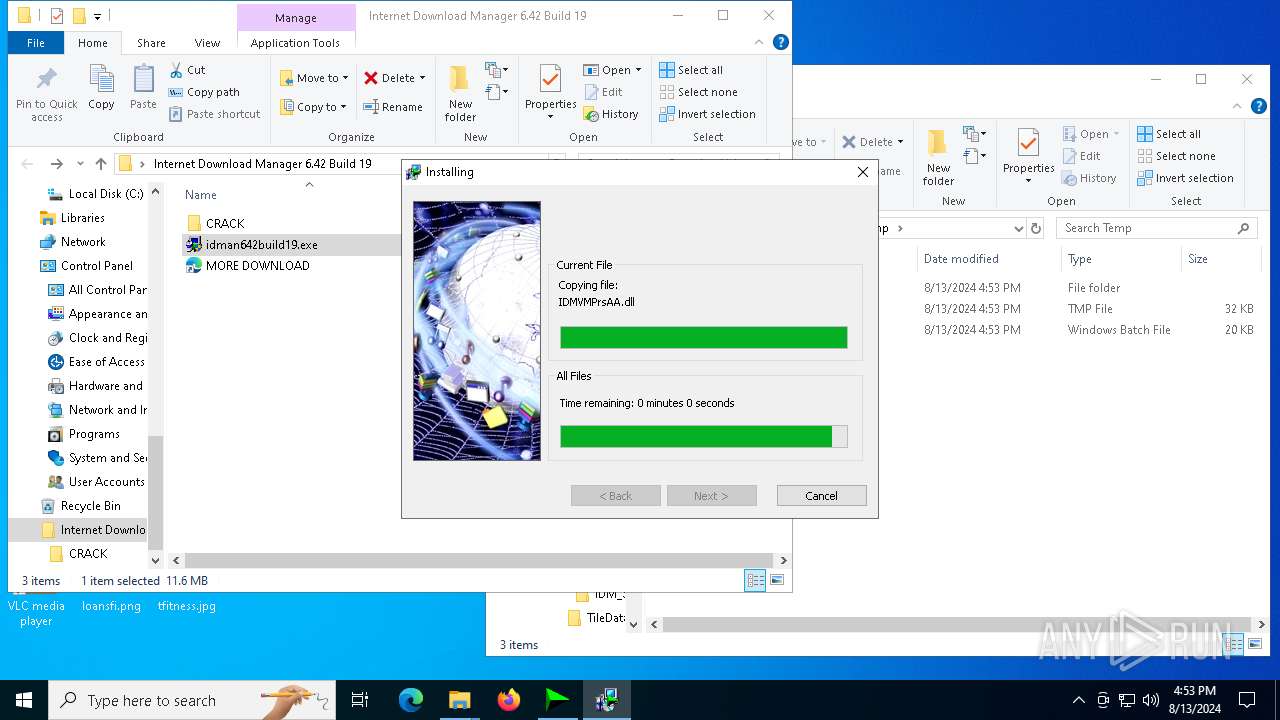
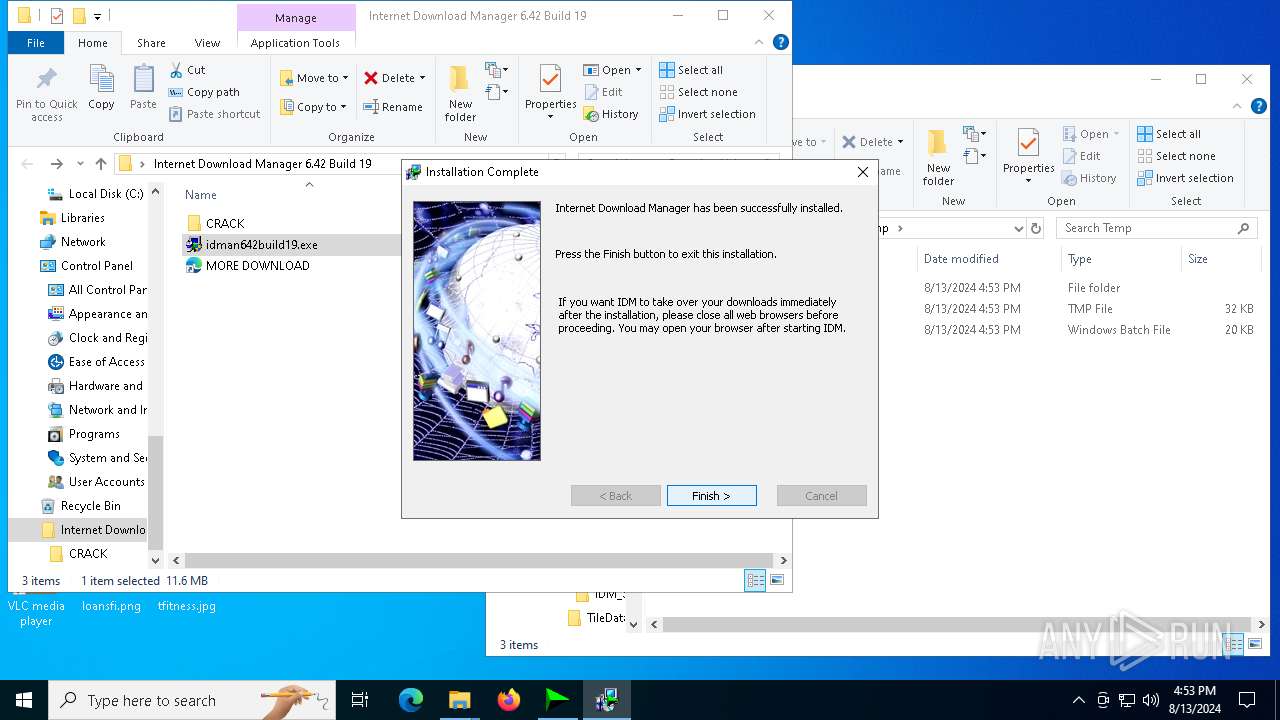
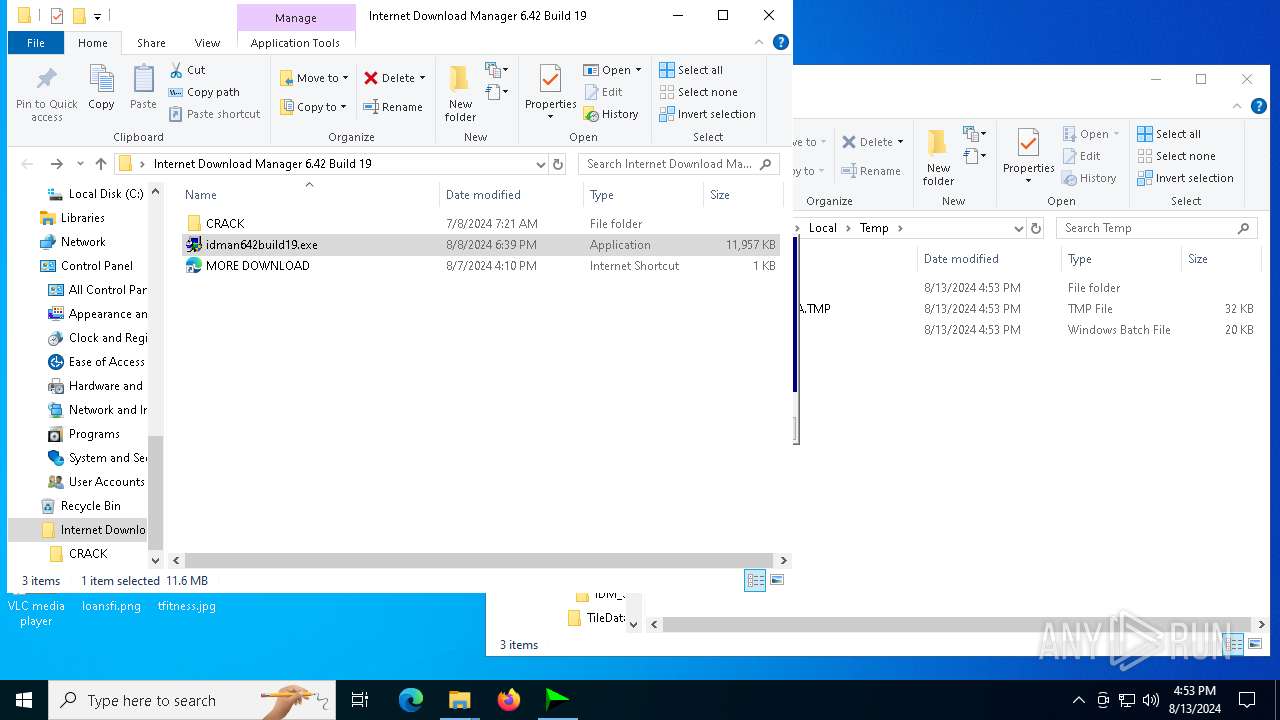
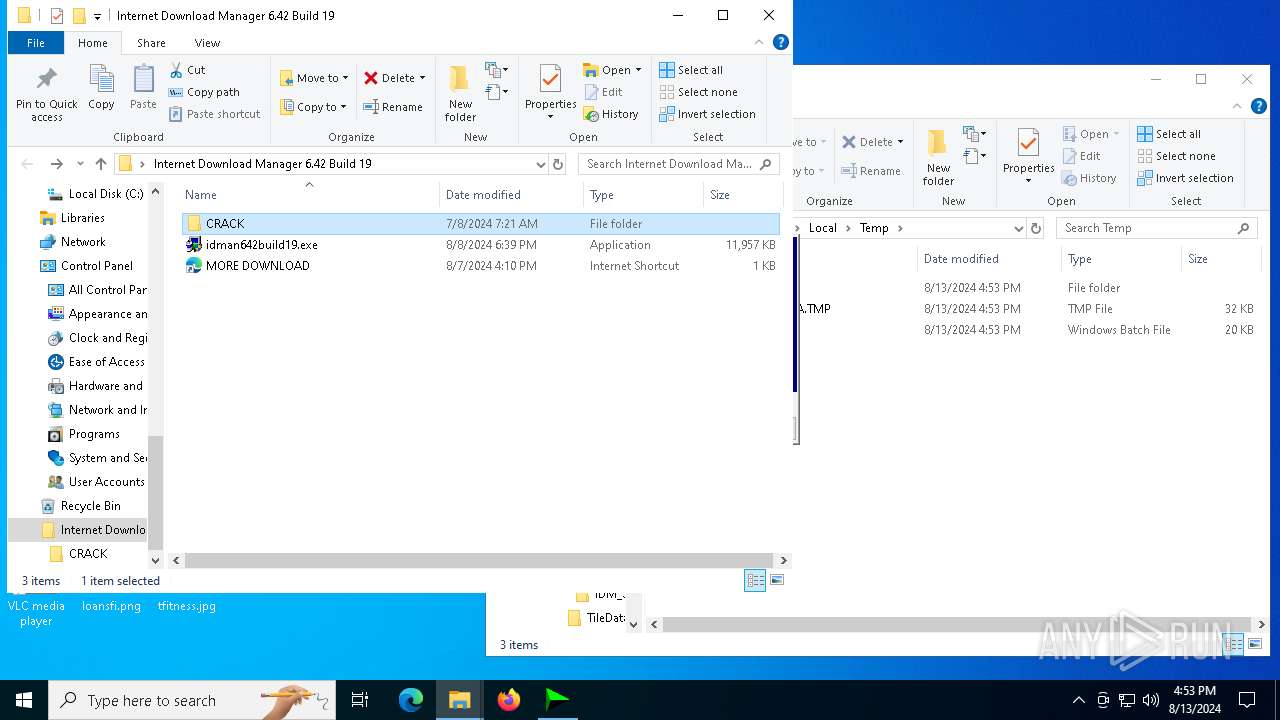
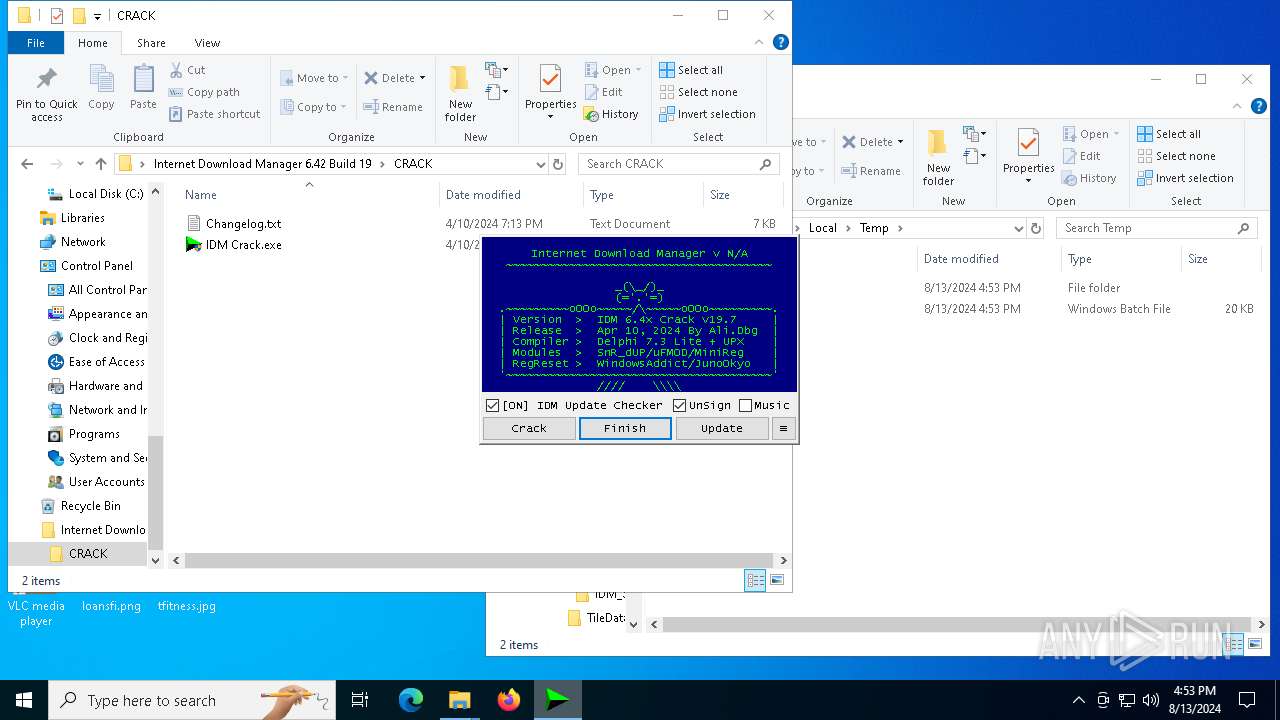
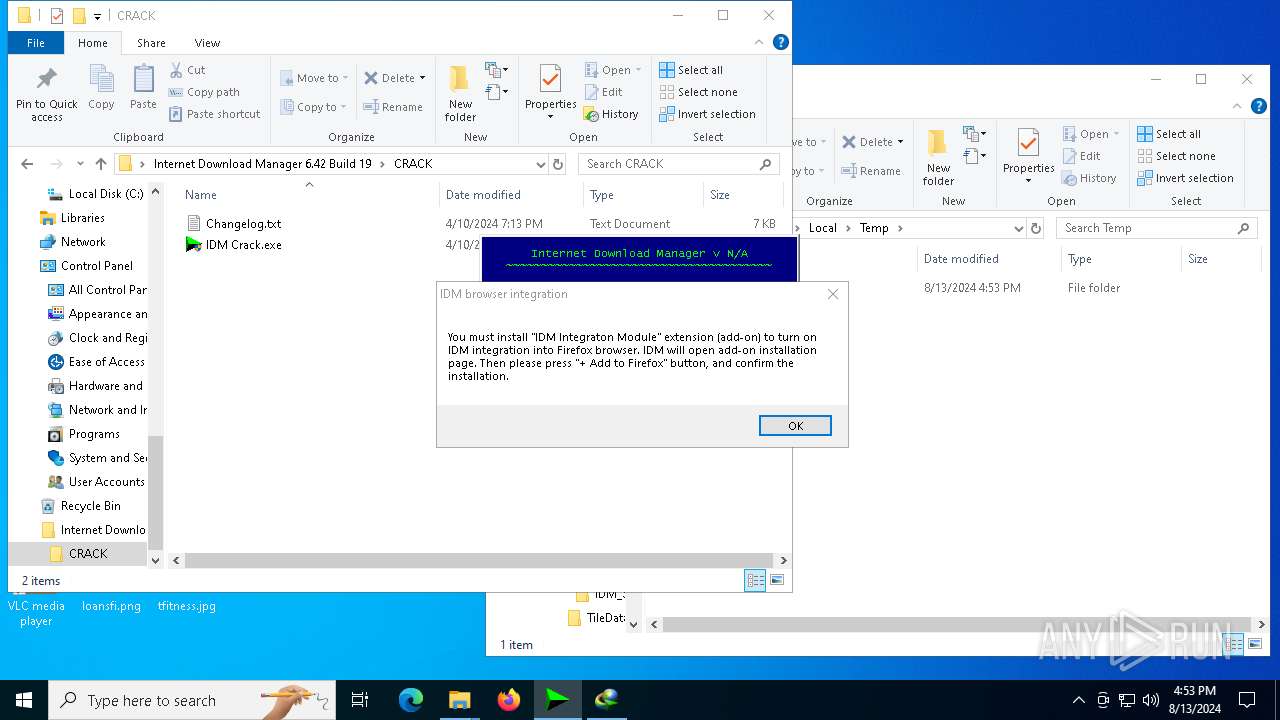
| File name: | Internet Download Manager 6.42 Build 19.rar |
| Full analysis: | https://app.any.run/tasks/20bcca2b-9298-45e0-8f41-647825867fc7 |
| Verdict: | Malicious activity |
| Analysis date: | August 13, 2024, 16:52:39 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Indicators: | |
| MIME: | application/x-rar |
| File info: | RAR archive data, v5 |
| MD5: | 8D38A6F851BE90311A7DE520F023C197 |
| SHA1: | 6811FFFDE1E692DEC6FA8938011599F5A531B654 |
| SHA256: | 8B45D354CE43E173BAC841E4A0A05FB641D1D17519BFEC657E1FEF6558B3DB27 |
| SSDEEP: | 98304:p6foyATjd9P6QHiFJs4iYBfp3uNPw5y5zi9GpKHuo4FdyXLS7lnoBBwFhgFnE2us:7xlOcIhpvjpUJquFrsb |
MALICIOUS
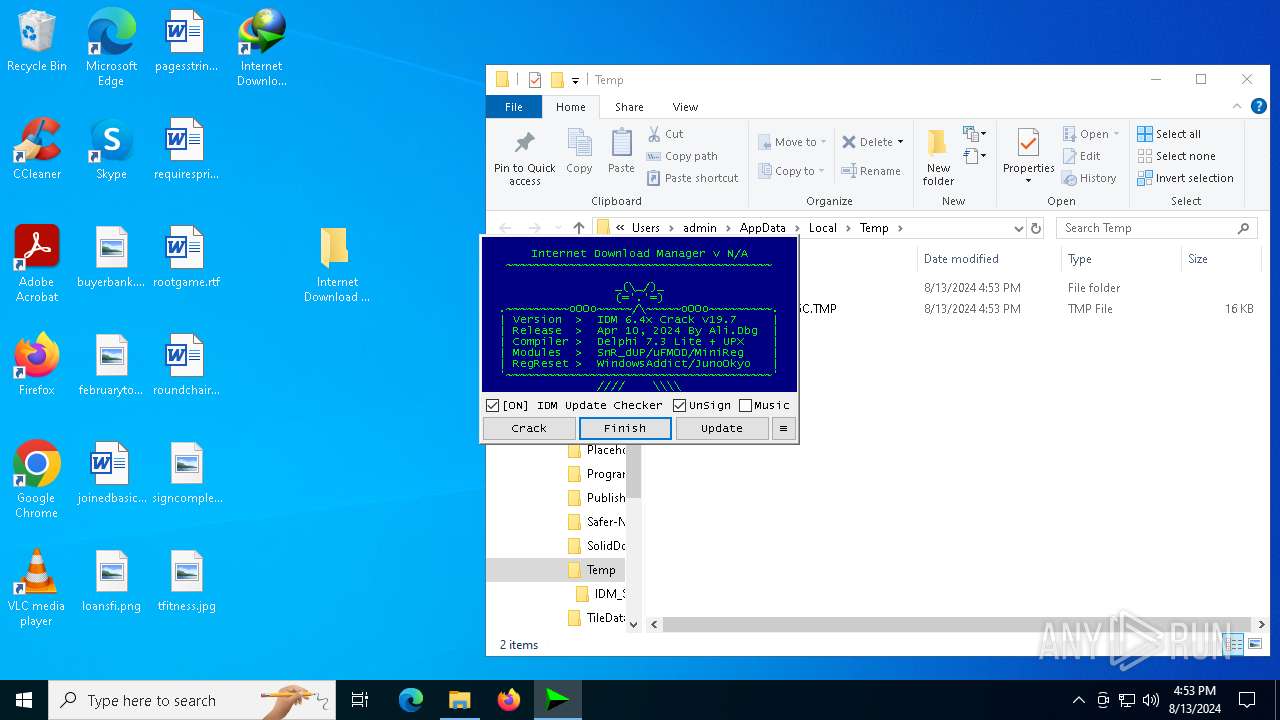
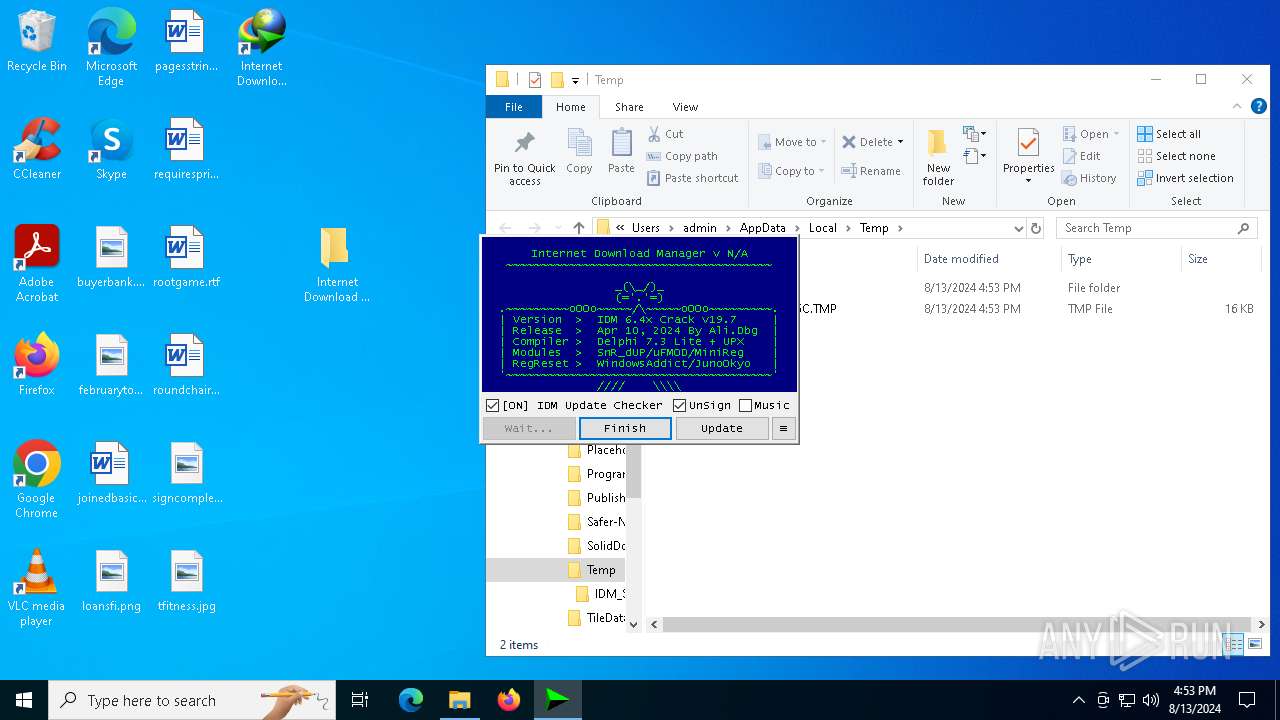
Registers / Runs the DLL via REGSVR32.EXE
- IDM1.tmp (PID: 300)
- IDMan.exe (PID: 6676)
- Uninstall.exe (PID: 6720)
- IDMan.exe (PID: 8496)
Starts NET.EXE for service management
- Uninstall.exe (PID: 6720)
- net.exe (PID: 7400)
SUSPICIOUS
Uses REG/REGEDIT.EXE to modify registry
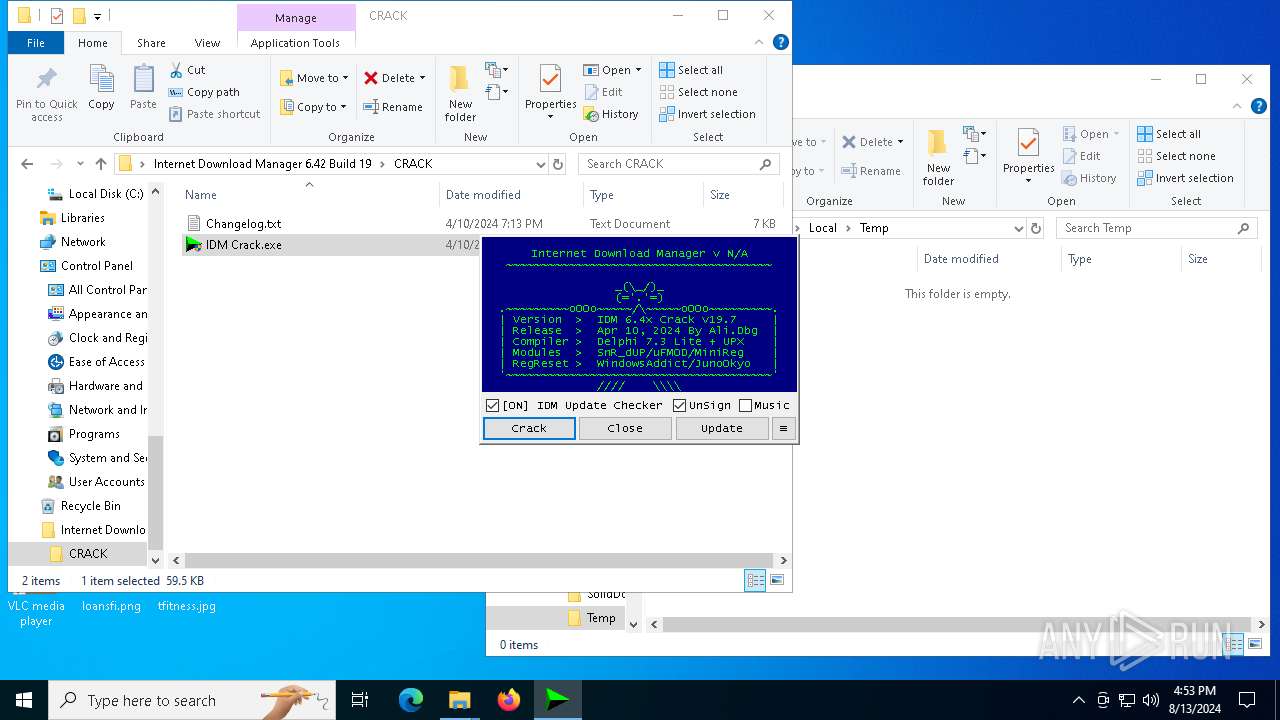
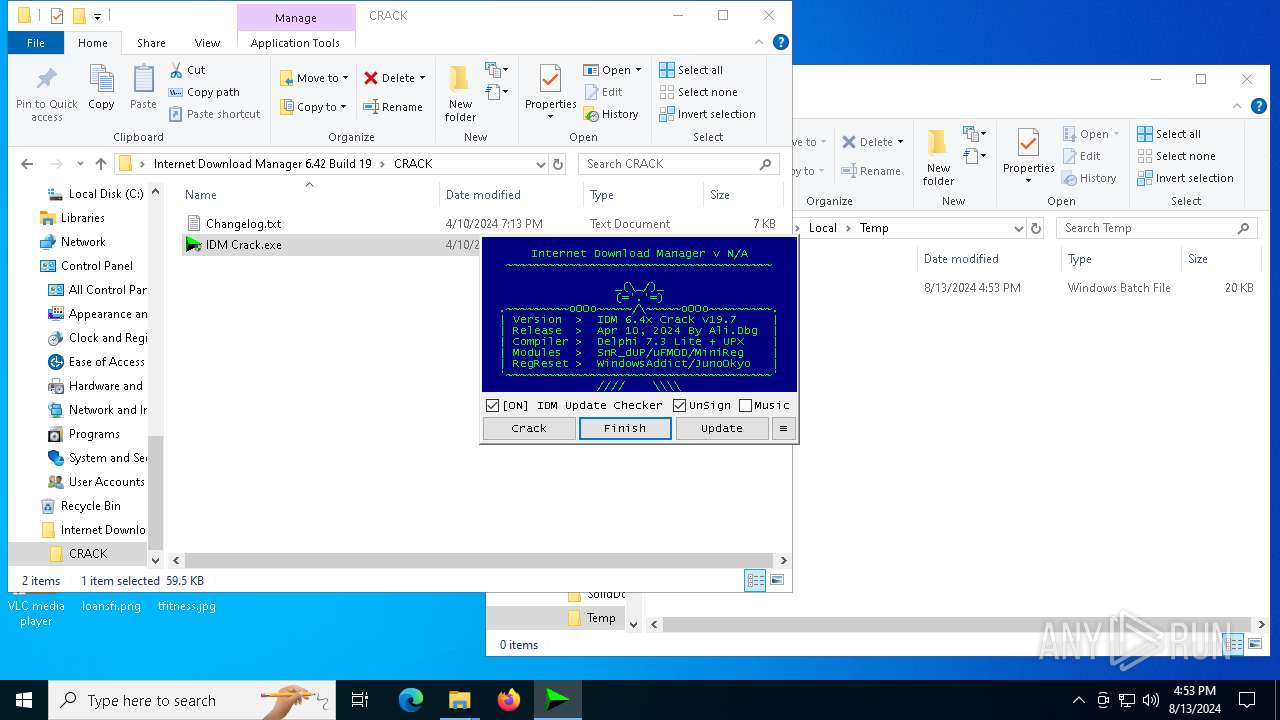
- IDM Crack.exe (PID: 5068)
- cmd.exe (PID: 5052)
- cmd.exe (PID: 2092)
Starts CMD.EXE for commands execution
- IDM Crack.exe (PID: 5068)
- cmd.exe (PID: 5588)
- cmd.exe (PID: 5052)
- cmd.exe (PID: 8856)
- cmd.exe (PID: 8980)
Executing commands from a ".bat" file
- IDM Crack.exe (PID: 5068)
- cmd.exe (PID: 5052)
- cmd.exe (PID: 8856)
Application launched itself
- cmd.exe (PID: 5052)
- cmd.exe (PID: 5588)
- cmd.exe (PID: 8856)
- cmd.exe (PID: 8980)
Starts POWERSHELL.EXE for commands execution
- cmd.exe (PID: 5052)
- cmd.exe (PID: 6620)
- cmd.exe (PID: 1608)
- cmd.exe (PID: 8856)
Probably obfuscated PowerShell command line is found
- cmd.exe (PID: 5052)
- cmd.exe (PID: 8856)
Possibly malicious use of IEX has been detected
- cmd.exe (PID: 5052)
- cmd.exe (PID: 8856)
Starts application with an unusual extension
- idman642build19.exe (PID: 4088)
- cmd.exe (PID: 5052)
Hides command output
- cmd.exe (PID: 6620)
- cmd.exe (PID: 2092)
The process creates files with name similar to system file names
- IDM1.tmp (PID: 300)
Creates a software uninstall entry
- IDM1.tmp (PID: 300)
Creates/Modifies COM task schedule object
- IDM1.tmp (PID: 300)
- regsvr32.exe (PID: 1108)
- regsvr32.exe (PID: 6236)
- regsvr32.exe (PID: 7056)
- regsvr32.exe (PID: 4168)
- regsvr32.exe (PID: 300)
- regsvr32.exe (PID: 1184)
- regsvr32.exe (PID: 6260)
- IDMan.exe (PID: 6676)
Reads the date of Windows installation
- IDM1.tmp (PID: 300)
- IDMan.exe (PID: 6676)
- Uninstall.exe (PID: 6720)
Reads security settings of Internet Explorer
- IDMan.exe (PID: 6676)
- IDM1.tmp (PID: 300)
- Uninstall.exe (PID: 6720)
Checks Windows Trust Settings
- IDMan.exe (PID: 6676)
Executable content was dropped or overwritten
- IDMan.exe (PID: 6676)
- rundll32.exe (PID: 6448)
- drvinst.exe (PID: 7272)
- IDM Crack.exe (PID: 5068)
Drops the executable file immediately after the start
- IDMan.exe (PID: 6676)
- drvinst.exe (PID: 7272)
- IDM Crack.exe (PID: 5068)
Uses RUNDLL32.EXE to load library
- Uninstall.exe (PID: 6720)
Drops a system driver (possible attempt to evade defenses)
- rundll32.exe (PID: 6448)
- drvinst.exe (PID: 7272)
Creates files in the driver directory
- drvinst.exe (PID: 7272)
INFO
Checks supported languages
- TextInputHost.exe (PID: 6452)
- IDM Crack.exe (PID: 5068)
- idman642build19.exe (PID: 4088)
- IDM1.tmp (PID: 300)
- IDMan.exe (PID: 6676)
- idmBroker.exe (PID: 6736)
- chcp.com (PID: 4080)
- drvinst.exe (PID: 7272)
- Uninstall.exe (PID: 6720)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 6492)
Manual execution by a user
- IDM Crack.exe (PID: 5068)
- IDM Crack.exe (PID: 4604)
- idman642build19.exe (PID: 4132)
- idman642build19.exe (PID: 4088)
- firefox.exe (PID: 6788)
Create files in a temporary directory
- IDM Crack.exe (PID: 5068)
- idman642build19.exe (PID: 4088)
- IDM1.tmp (PID: 300)
- reg.exe (PID: 6716)
- IDMan.exe (PID: 6676)
- rundll32.exe (PID: 6448)
Reads the computer name
- TextInputHost.exe (PID: 6452)
- IDM Crack.exe (PID: 5068)
- idman642build19.exe (PID: 4088)
- IDM1.tmp (PID: 300)
- idmBroker.exe (PID: 6736)
- IDMan.exe (PID: 6676)
- Uninstall.exe (PID: 6720)
Checks operating system version
- cmd.exe (PID: 5052)
- cmd.exe (PID: 8856)
Checks whether the specified file exists (POWERSHELL)
- powershell.exe (PID: 4920)
- powershell.exe (PID: 6448)
Creates files in the program directory
- IDM1.tmp (PID: 300)
- IDMan.exe (PID: 6676)
Process checks computer location settings
- IDM1.tmp (PID: 300)
- IDMan.exe (PID: 6676)
- Uninstall.exe (PID: 6720)
Changes the display of characters in the console
- chcp.com (PID: 4080)
Reads the machine GUID from the registry
- IDMan.exe (PID: 6676)
Creates files or folders in the user directory
- IDM1.tmp (PID: 300)
- IDMan.exe (PID: 6676)
Reads the software policy settings
- IDMan.exe (PID: 6676)
Disables trace logs
- IDMan.exe (PID: 6676)
Checks proxy server information
- IDMan.exe (PID: 6676)
Reads Microsoft Office registry keys
- IDMan.exe (PID: 6676)
Application launched itself
- firefox.exe (PID: 6788)
- firefox.exe (PID: 4232)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .rar | | | RAR compressed archive (v5.0) (61.5) |
|---|---|---|
| .rar | | | RAR compressed archive (gen) (38.4) |
Total processes
269
Monitored processes
132
Malicious processes
8
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 300 | "C:\Users\admin\AppData\Local\Temp\IDM_Setup_Temp\IDM1.tmp" -d "C:\Users\admin\AppData\Local\Temp\IDM_Setup_Temp\" | C:\Users\admin\AppData\Local\Temp\IDM_Setup_Temp\IDM1.tmp | — | idman642build19.exe | |||||||||||
User: admin Company: Tonec Inc. Integrity Level: HIGH Description: Internet Download Manager installer Exit code: 0 Version: 6, 42, 7, 1 Modules
| |||||||||||||||
| 300 | /s "C:\Program Files (x86)\Internet Download Manager\IDMIECC64.dll" | C:\Windows\System32\regsvr32.exe | — | regsvr32.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Microsoft(C) Register Server Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 532 | reg query "HKCU\Console" /v ForceV2 | C:\Windows\System32\reg.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Registry Console Tool Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 644 | cmd | C:\Windows\System32\cmd.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1108 | /s "C:\Program Files (x86)\Internet Download Manager\IDMIECC64.dll" | C:\Windows\System32\regsvr32.exe | — | regsvr32.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Microsoft(C) Register Server Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1132 | "C:\Windows\System32\regsvr32.exe" /s "C:\Program Files (x86)\Internet Download Manager\IDMIECC64.dll" | C:\Windows\SysWOW64\regsvr32.exe | — | IDM1.tmp | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Microsoft(C) Register Server Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1184 | reg delete HKU\S-1-5-21-1693682860-607145093-2874071422-1001\IAS_TEST /f | C:\Windows\System32\reg.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Registry Console Tool Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1184 | /s "C:\Program Files (x86)\Internet Download Manager\IDMGetAll64.dll" | C:\Windows\System32\regsvr32.exe | — | regsvr32.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Microsoft(C) Register Server Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1608 | C:\WINDOWS\system32\cmd.exe /c powershell.exe "(Get-Date).ToString('yyyyMMdd-HHmmssfff')" | C:\Windows\SysWOW64\cmd.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2092 | C:\WINDOWS\system32\cmd.exe /c reg query "HKU\S-1-5-21-1693682860-607145093-2874071422-1001\Software\DownloadManager" /v ExePath 2>nul | C:\Windows\SysWOW64\cmd.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 1 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
46 040
Read events
45 622
Write events
291
Delete events
127
Modification events
| (PID) Process: | (6492) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (6492) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (6492) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\GoogleChromeEnterpriseBundle64.zip | |||
| (PID) Process: | (6492) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Downloads\Internet Download Manager 6.42 Build 19.rar | |||
| (PID) Process: | (6492) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (6492) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (6492) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (6492) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (6492) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface |
| Operation: | write | Name: | ShowPassword |
Value: 0 | |||
| (PID) Process: | (6492) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface\MainWin |
| Operation: | write | Name: | Placement |
Value: 2C0000000000000001000000FFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFF3D00000037000000FD03000020020000 | |||
Executable files
17
Suspicious files
62
Text files
39
Unknown types
37
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 6492 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRb6492.28582\Internet Download Manager 6.42 Build 19\idman642build19.exe | executable | |
MD5:192103BACEF3A33B70CECB80A1460ACF | SHA256:25095F71F564F688BBBCEDAD14A192A7AD47CC4D8B14B3734423C0A955B5E8D7 | |||
| 4920 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_d4q55iyg.vqt.ps1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 5600 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_ztyjpyjx.m2q.ps1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 6492 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRb6492.28582\Internet Download Manager 6.42 Build 19\CRACK\IDM Crack.exe | executable | |
MD5:27016937B5781C4F84B6B3432170F4D0 | SHA256:FC1A02B509B8F351AC45BD45EFD4E7296B365545A48FFD6A14E8E07BC7189155 | |||
| 4920 | powershell.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\PowerShell\StartupProfileData-NonInteractive | binary | |
MD5:62E4122AC5FC4A0D8F22DC50747637A1 | SHA256:2F601EA34C8476F8188B7683CF9AF2F2EBFC1B6B87BA2EAD7BF29211CCD83BA6 | |||
| 3036 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_vmx4ex1w.eag.psm1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 5068 | IDM Crack.exe | C:\Users\admin\AppData\Local\Temp\BATCLEN.bat | text | |
MD5:9FE22C4AD624881F8F0977CC7614346F | SHA256:12B47C1949CC555C2F68F9FD4677ED5266F25C4DA4630BEC36E303629B133225 | |||
| 3036 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_oyiazijg.lao.ps1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 6492 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRb6492.28582\Internet Download Manager 6.42 Build 19\MORE DOWNLOAD.url | url | |
MD5:63C65B6A41E742752A7E38E12477307E | SHA256:E9A1102EF465ADC321DD44D72A85EAECF01CBCEC9846B382D0C22377FC1F26CA | |||
| 5600 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_qnz43f1d.dql.psm1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
20
TCP/UDP connections
51
DNS requests
88
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
5336 | SearchApp.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
1948 | svchost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
1948 | svchost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
6864 | backgroundTaskHost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | whitelisted |
6900 | backgroundTaskHost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | whitelisted |
5336 | SearchApp.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | whitelisted |
— | — | GET | 200 | 34.107.221.82:80 | http://detectportal.firefox.com/canonical.html | unknown | — | — | whitelisted |
— | — | GET | 200 | 34.107.221.82:80 | http://detectportal.firefox.com/success.txt?ipv4 | unknown | — | — | whitelisted |
— | — | POST | 200 | 142.250.186.67:80 | http://o.pki.goog/wr2 | unknown | — | — | unknown |
— | — | POST | 200 | 184.24.77.54:80 | http://r11.o.lencr.org/ | unknown | — | — | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4760 | RUXIMICS.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
3888 | svchost.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
2120 | MoUsoCoreWorker.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
2680 | svchost.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
— | — | 192.168.100.255:138 | — | — | — | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
5336 | SearchApp.exe | 184.86.251.21:443 | www.bing.com | Akamai International B.V. | DE | unknown |
5336 | SearchApp.exe | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
1948 | svchost.exe | 20.190.159.75:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
1948 | svchost.exe | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
google.com |
| whitelisted |
settings-win.data.microsoft.com |
| whitelisted |
www.bing.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
login.live.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
th.bing.com |
| whitelisted |
fd.api.iris.microsoft.com |
| whitelisted |
r.bing.com |
| whitelisted |
arc.msn.com |
| whitelisted |