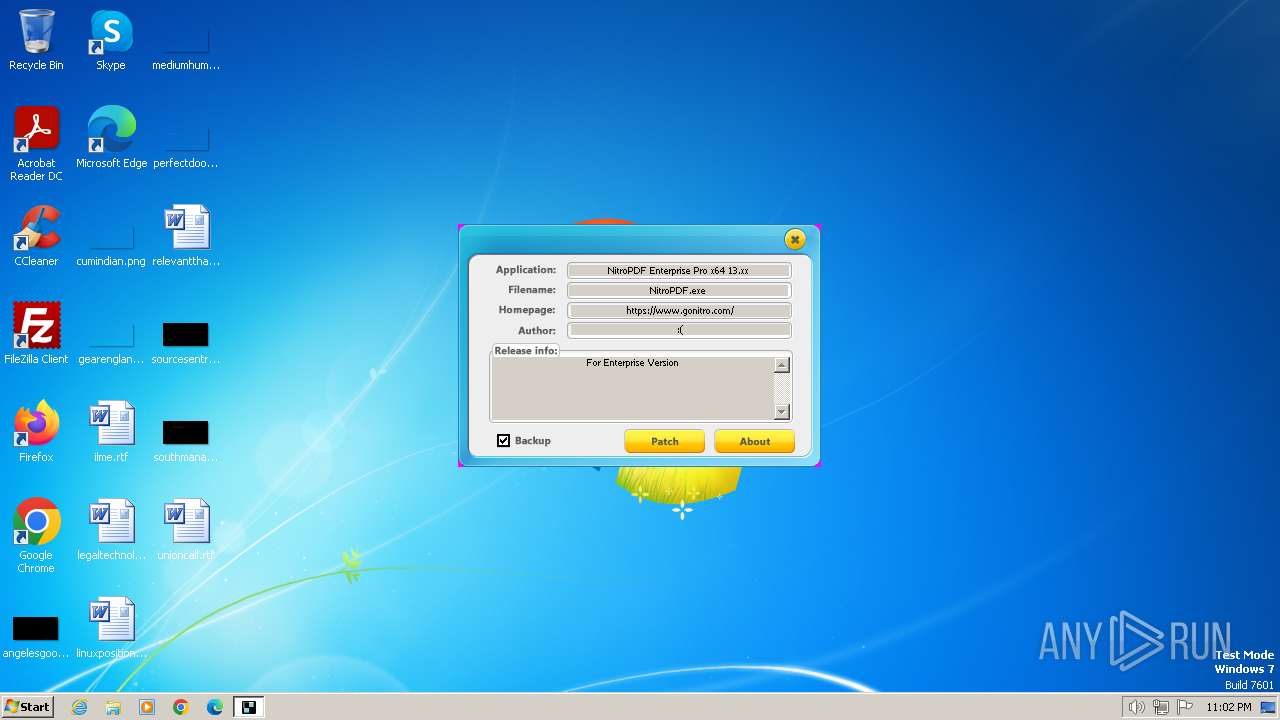
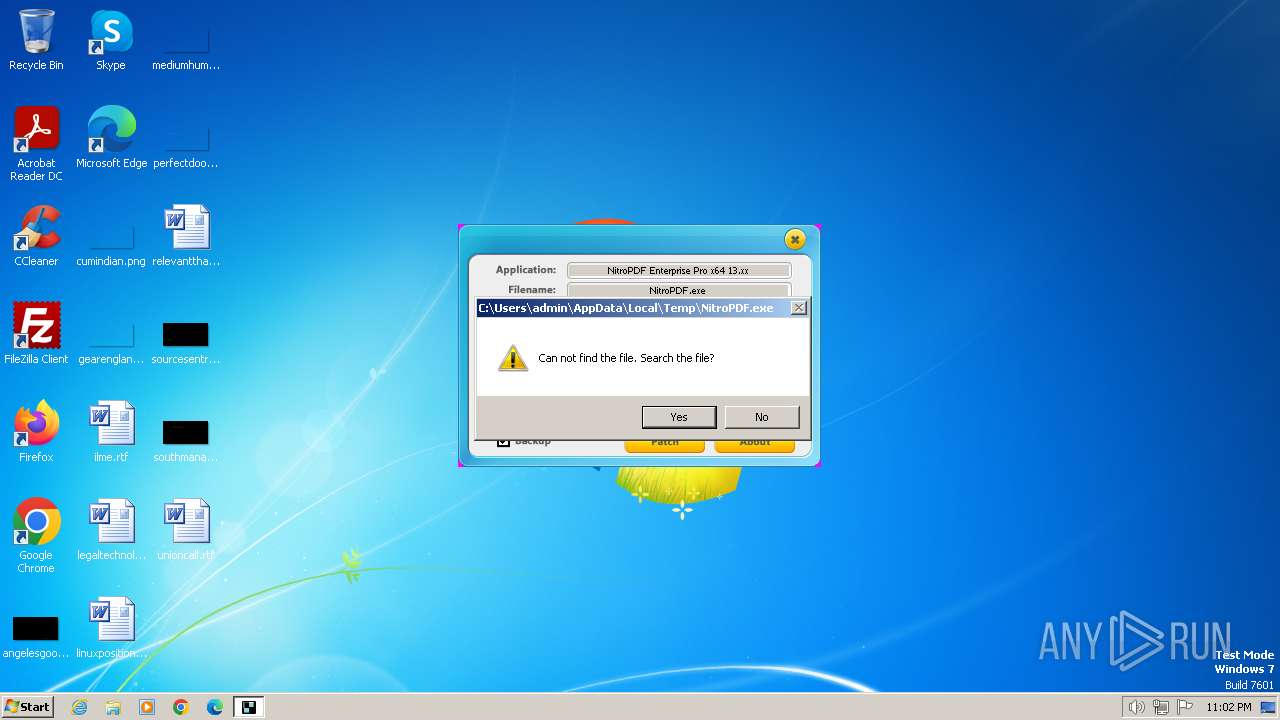
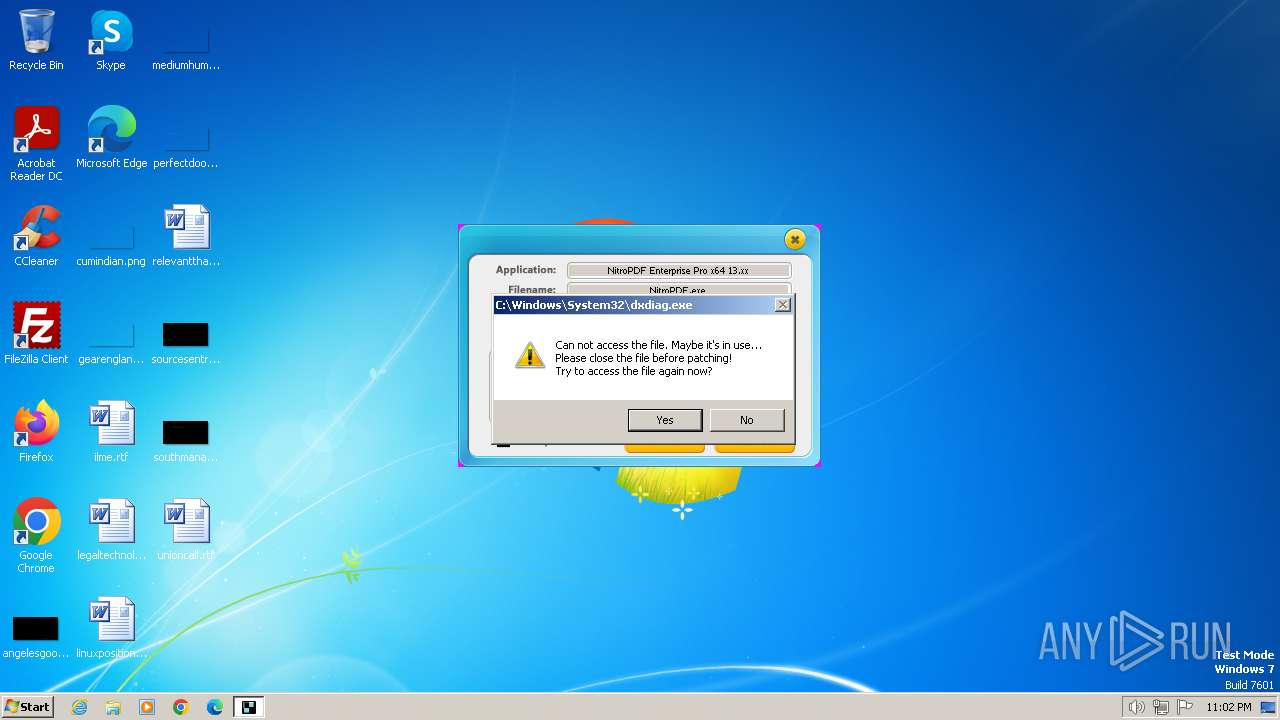
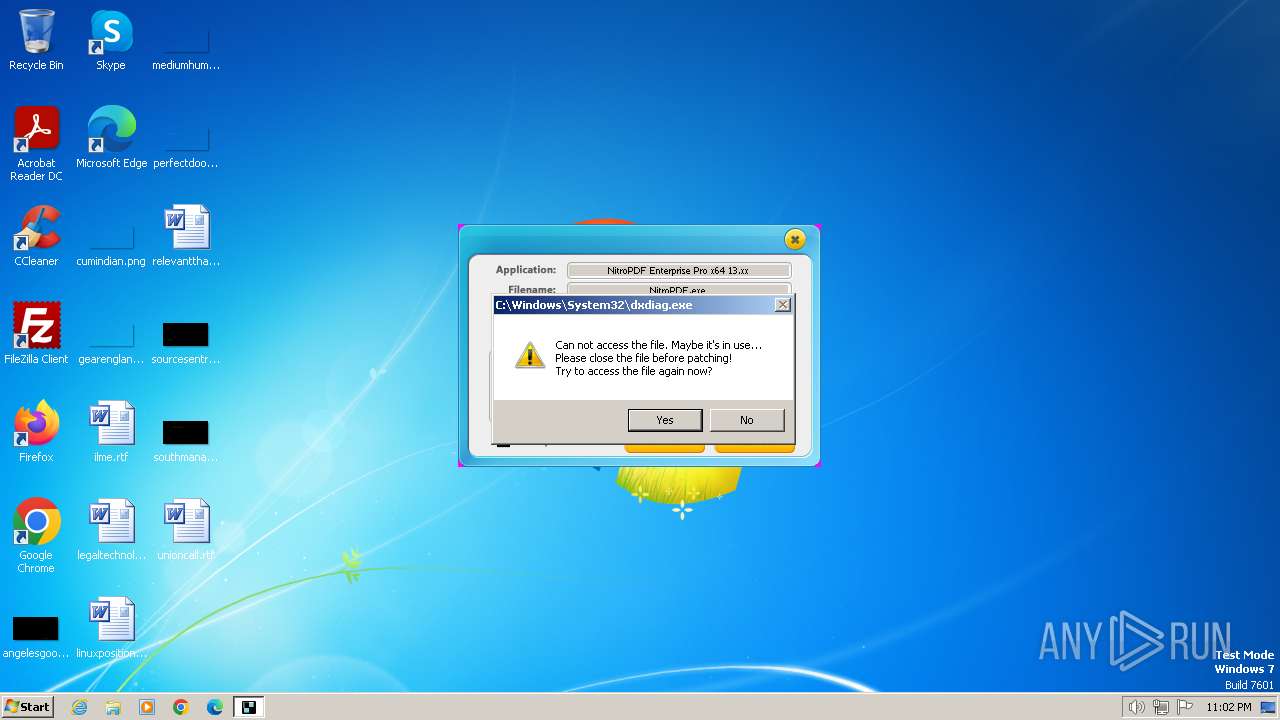
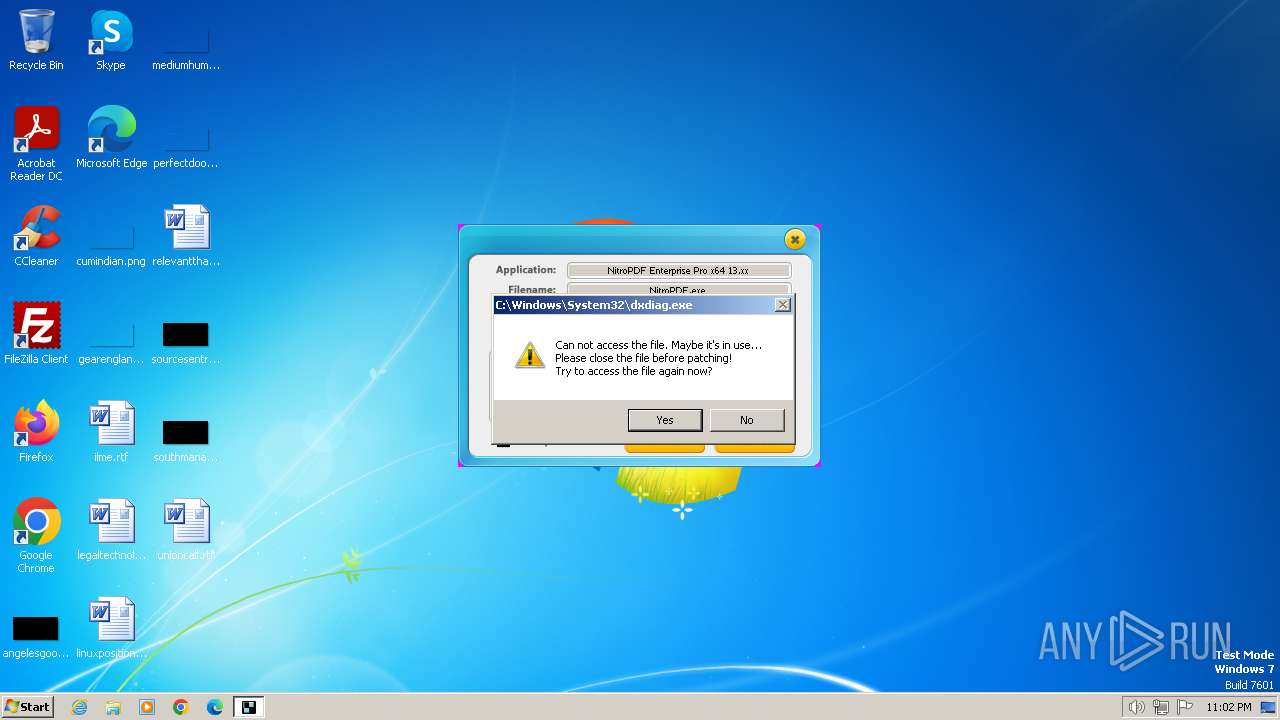
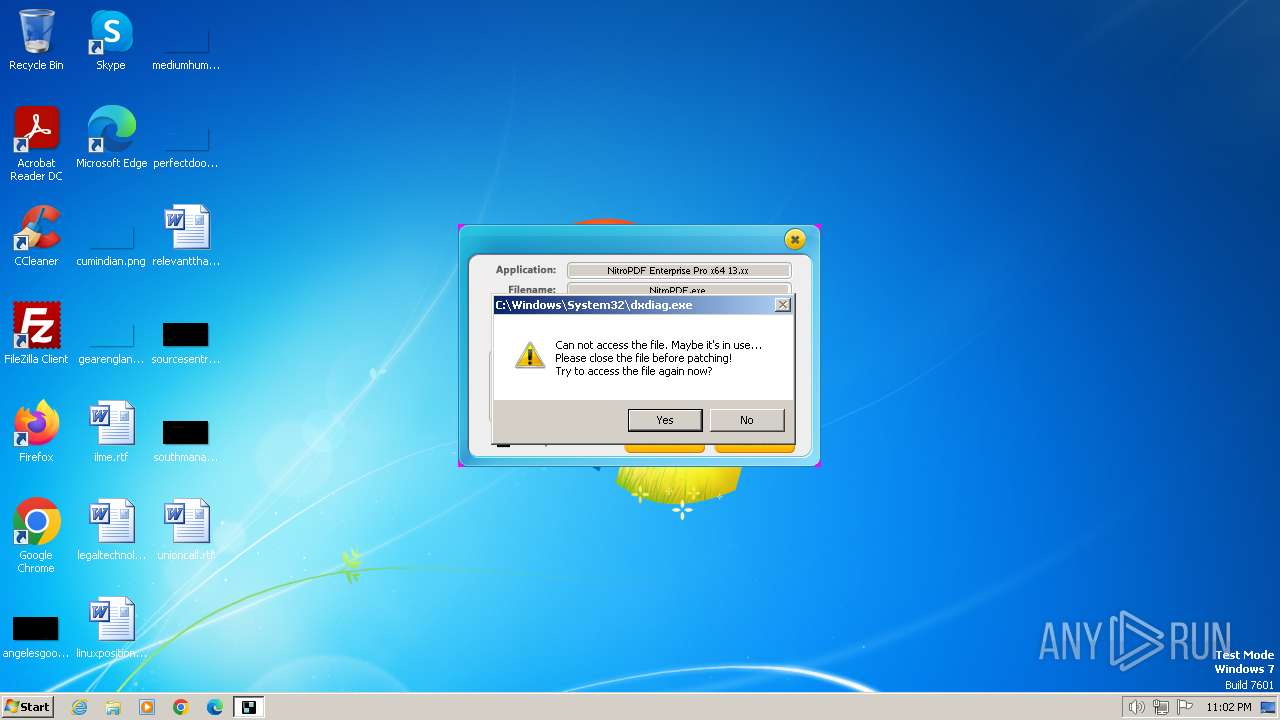
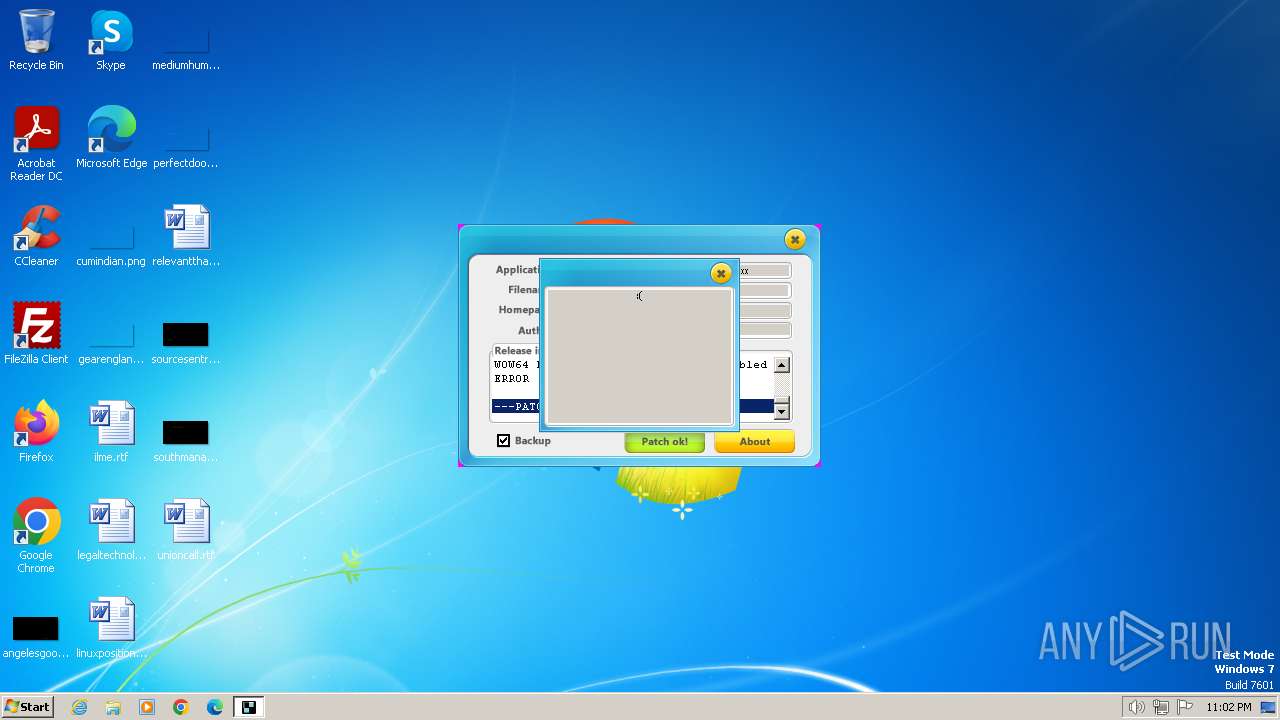
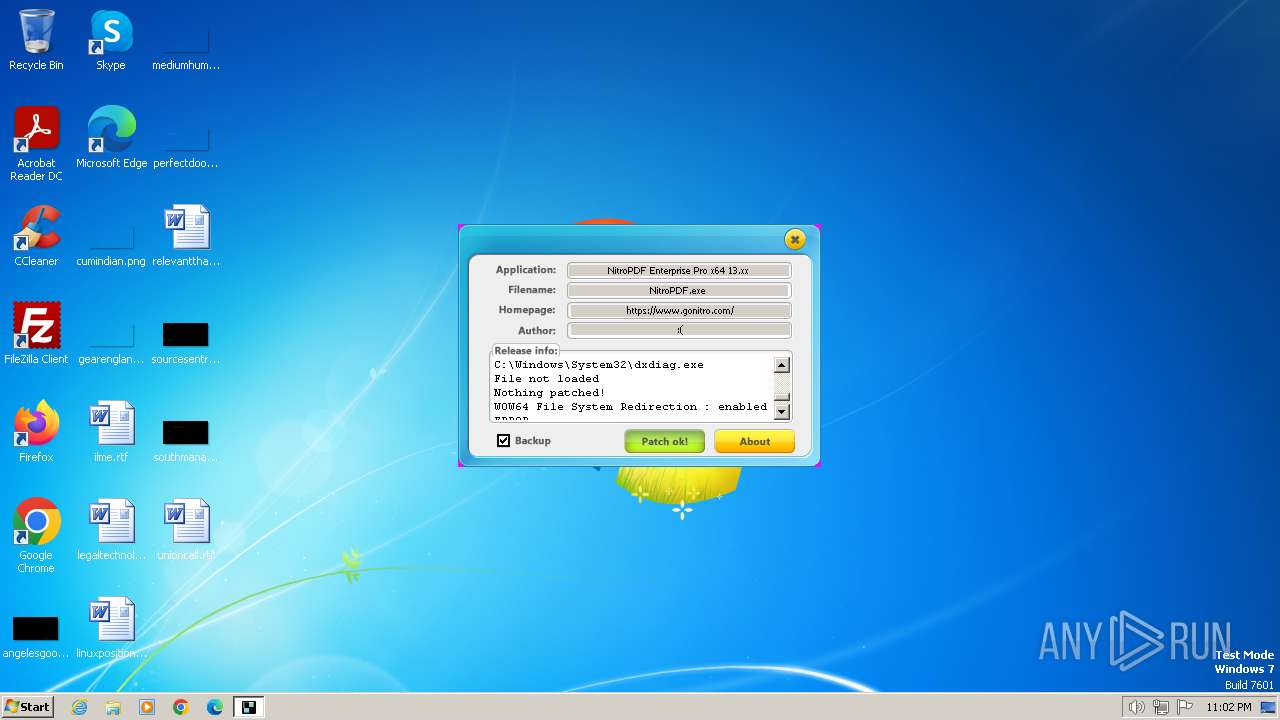
| File name: | nitropdf.enterprise.pro.x64.13.xx-patch.exe |
| Full analysis: | https://app.any.run/tasks/2654e2c8-feeb-41fb-a686-a5a9274f95d5 |
| Verdict: | Malicious activity |
| Analysis date: | March 07, 2024, 23:02:00 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows |
| MD5: | 646260E1F316DD6E518D4C7A9AC6B589 |
| SHA1: | 33EB1212FD842078B5B65D8720672582D8ACB7CA |
| SHA256: | 8B0A871839C2E9714684CDB00CD18484780E29EE762F004D300C1FE65BB08628 |
| SSDEEP: | 6144:Lc/v5aMDNj7duYP9JCBz1M/ka5uyJG/e+p3xO85tO:4/v5dJIY1JCvxa5uyJAeM3xTQ |
MALICIOUS
Drops the executable file immediately after the start
- nitropdf.enterprise.pro.x64.13.xx-patch.exe (PID: 3784)
Creates a writable file in the system directory
- nitropdf.enterprise.pro.x64.13.xx-patch.exe (PID: 3784)
SUSPICIOUS
Creates file in the systems drive root
- nitropdf.enterprise.pro.x64.13.xx-patch.exe (PID: 3784)
Process drops legitimate windows executable
- nitropdf.enterprise.pro.x64.13.xx-patch.exe (PID: 3784)
Executable content was dropped or overwritten
- nitropdf.enterprise.pro.x64.13.xx-patch.exe (PID: 3784)
INFO
Reads the computer name
- nitropdf.enterprise.pro.x64.13.xx-patch.exe (PID: 3784)
Checks supported languages
- nitropdf.enterprise.pro.x64.13.xx-patch.exe (PID: 3784)
Create files in a temporary directory
- nitropdf.enterprise.pro.x64.13.xx-patch.exe (PID: 3784)
Reads the machine GUID from the registry
- nitropdf.enterprise.pro.x64.13.xx-patch.exe (PID: 3784)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win64 Executable (generic) (64.6) |
|---|---|---|
| .dll | | | Win32 Dynamic Link Library (generic) (15.4) |
| .exe | | | Win32 Executable (generic) (10.5) |
| .exe | | | Generic Win/DOS Executable (4.6) |
| .exe | | | DOS Executable Generic (4.6) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2012:12:21 20:59:46+00:00 |
| ImageFileCharacteristics: | Executable, 32-bit |
| PEType: | PE32 |
| LinkerVersion: | 10 |
| CodeSize: | 512 |
| InitializedDataSize: | 244736 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x102b |
| OSVersion: | 5 |
| ImageVersion: | - |
| SubsystemVersion: | 5 |
| Subsystem: | Windows GUI |
Total processes
41
Monitored processes
2
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 3240 | "C:\Users\admin\AppData\Local\Temp\nitropdf.enterprise.pro.x64.13.xx-patch.exe" | C:\Users\admin\AppData\Local\Temp\nitropdf.enterprise.pro.x64.13.xx-patch.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 3221226540 Modules
| |||||||||||||||
| 3784 | "C:\Users\admin\AppData\Local\Temp\nitropdf.enterprise.pro.x64.13.xx-patch.exe" | C:\Users\admin\AppData\Local\Temp\nitropdf.enterprise.pro.x64.13.xx-patch.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
Total events
14 023
Read events
13 658
Write events
348
Delete events
17
Modification events
| (PID) Process: | (3784) nitropdf.enterprise.pro.x64.13.xx-patch.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Explorer\ComDlg32\FirstFolder |
| Operation: | delete value | Name: | MRUList |
Value: | |||
| (PID) Process: | (3784) nitropdf.enterprise.pro.x64.13.xx-patch.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Explorer\ComDlg32\FirstFolder |
| Operation: | write | Name: | 0 |
Value: 43003A005C00550073006500720073005C00610064006D0069006E005C0041007000700044006100740061005C004C006F00630061006C005C00540065006D0070005C006E006900740072006F007000640066002E0065006E00740065007200700072006900730065002E00700072006F002E007800360034002E00310033002E00780078002D00700061007400630068002E00650078006500000043003A005C00550073006500720073005C00610064006D0069006E005C0041007000700044006100740061005C004C006F00630061006C005C00540065006D0070000000 | |||
| (PID) Process: | (3784) nitropdf.enterprise.pro.x64.13.xx-patch.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Explorer\ComDlg32\FirstFolder |
| Operation: | write | Name: | MRUListEx |
Value: 00000000FFFFFFFF | |||
| (PID) Process: | (3784) nitropdf.enterprise.pro.x64.13.xx-patch.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\BagMRU |
| Operation: | write | Name: | NodeSlots |
Value: 0202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202 | |||
| (PID) Process: | (3784) nitropdf.enterprise.pro.x64.13.xx-patch.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\BagMRU |
| Operation: | write | Name: | MRUListEx |
Value: 07000000020000000100000006000000000000000B0000000C0000000D0000000A0000000900000008000000030000000500000004000000FFFFFFFF | |||
| (PID) Process: | (3784) nitropdf.enterprise.pro.x64.13.xx-patch.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\Bags\103\Shell |
| Operation: | write | Name: | SniffedFolderType |
Value: Generic | |||
| (PID) Process: | (3784) nitropdf.enterprise.pro.x64.13.xx-patch.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\182\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (3784) nitropdf.enterprise.pro.x64.13.xx-patch.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\BagMRU\7\1\0\1 |
| Operation: | write | Name: | MRUListEx |
Value: 010000000500000004000000030000000200000000000000FFFFFFFF | |||
| (PID) Process: | (3784) nitropdf.enterprise.pro.x64.13.xx-patch.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\Bags\103\ComDlg\{5C4F28B5-F869-4E84-8E60-F11DB97C5CC7} |
| Operation: | write | Name: | Mode |
Value: 4 | |||
| (PID) Process: | (3784) nitropdf.enterprise.pro.x64.13.xx-patch.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\Bags\103\ComDlg\{5C4F28B5-F869-4E84-8E60-F11DB97C5CC7} |
| Operation: | write | Name: | LogicalViewMode |
Value: 1 | |||
Executable files
2
Suspicious files
0
Text files
0
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3784 | nitropdf.enterprise.pro.x64.13.xx-patch.exe | C:\Users\admin\AppData\Local\Temp\dup2patcher.dll | executable | |
MD5:6F8B0021A206E48A50986333B87A5245 | SHA256:326CA48A87C1E82E1FCAF95ACD5B8C09D92F712591BA88928F48E093C485C40A | |||
| 3784 | nitropdf.enterprise.pro.x64.13.xx-patch.exe | C:\Windows\System32\dxdiag.exe.BAK | executable | |
MD5:42BD9F1FA0A5DAC38A5BE56C0E8BEA8B | SHA256:313E9B08704A8494AFA388B2689C95FAAAB60275ECF4EE74841971F67EA1BCDD | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
4
DNS requests
0
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
— | — | 224.0.0.252:5355 | — | — | — | unknown |
1080 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |