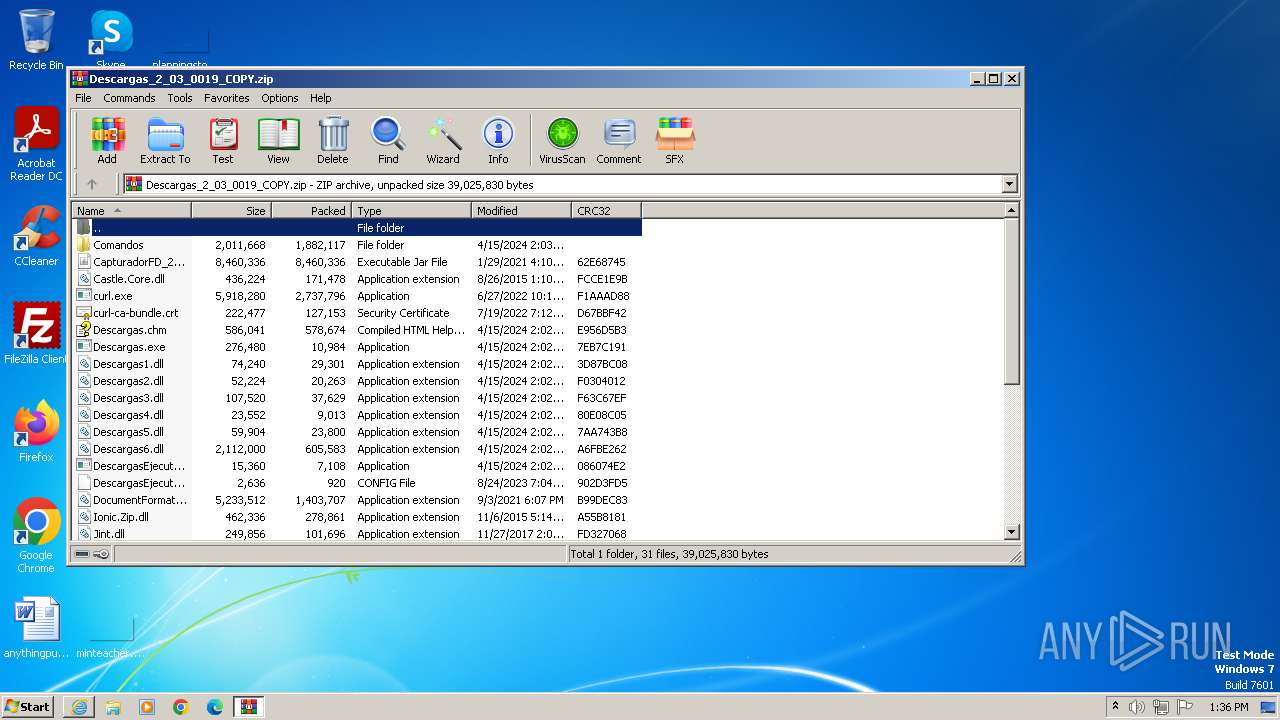
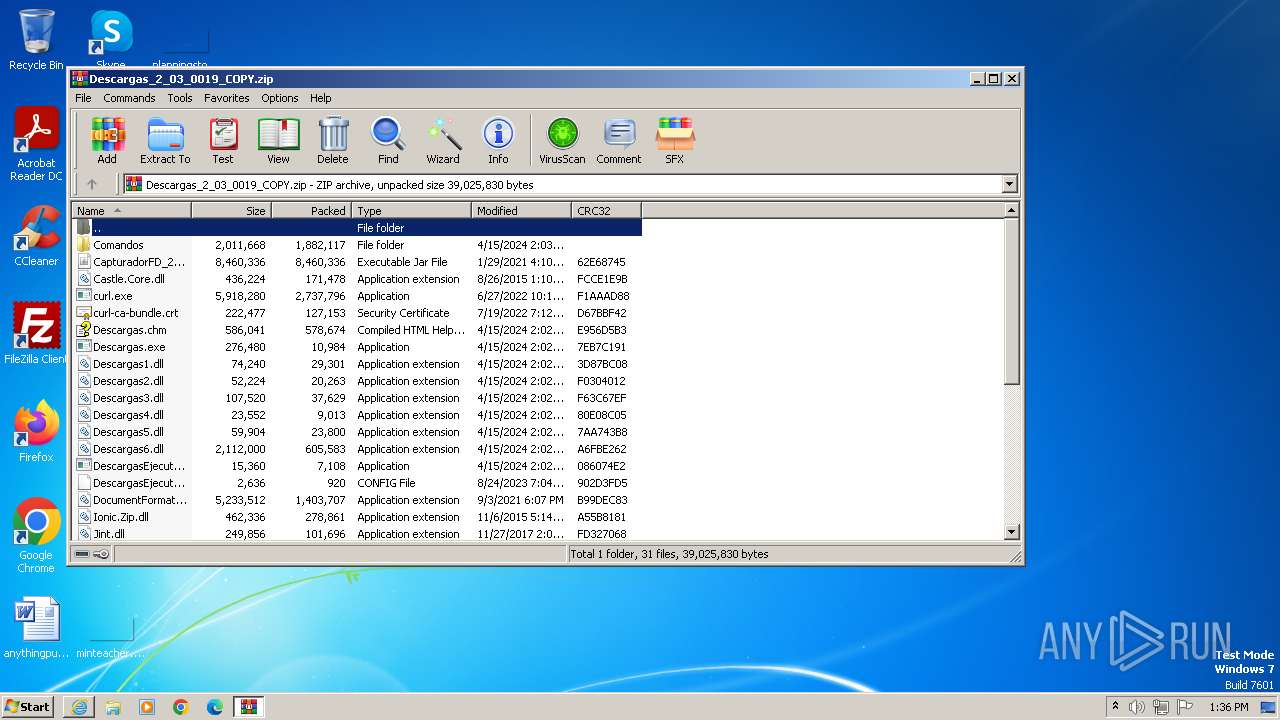
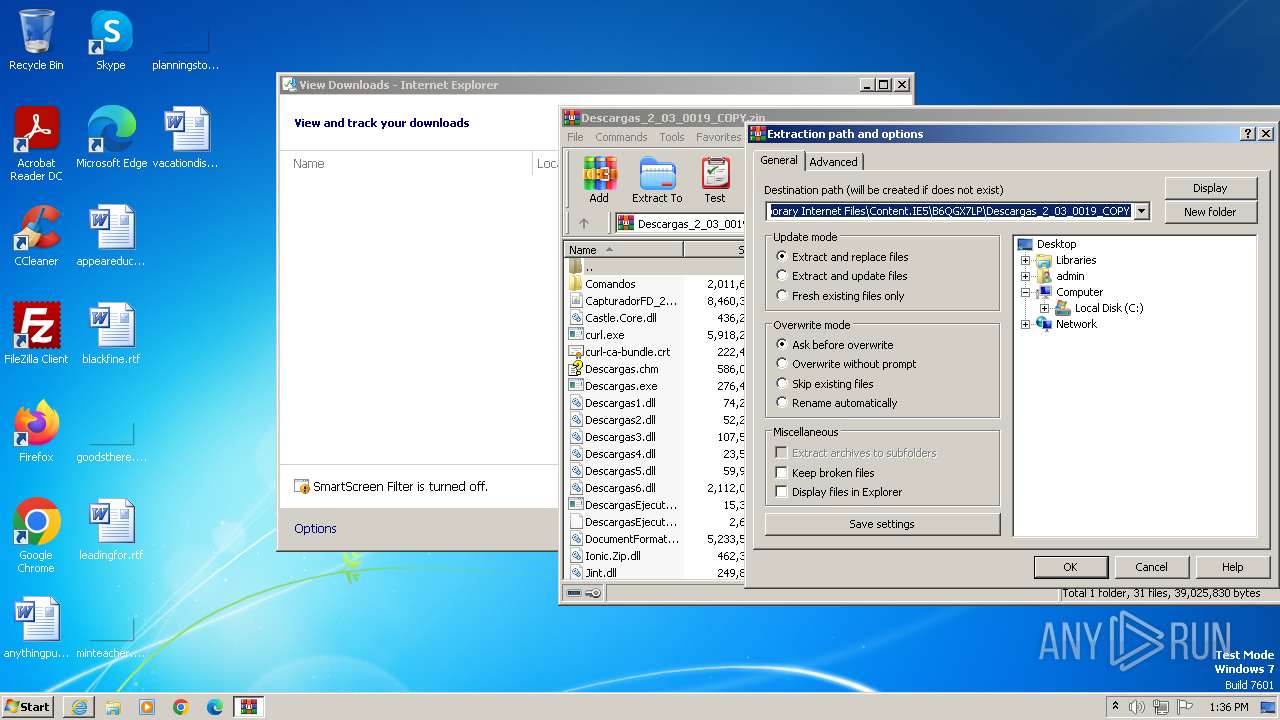
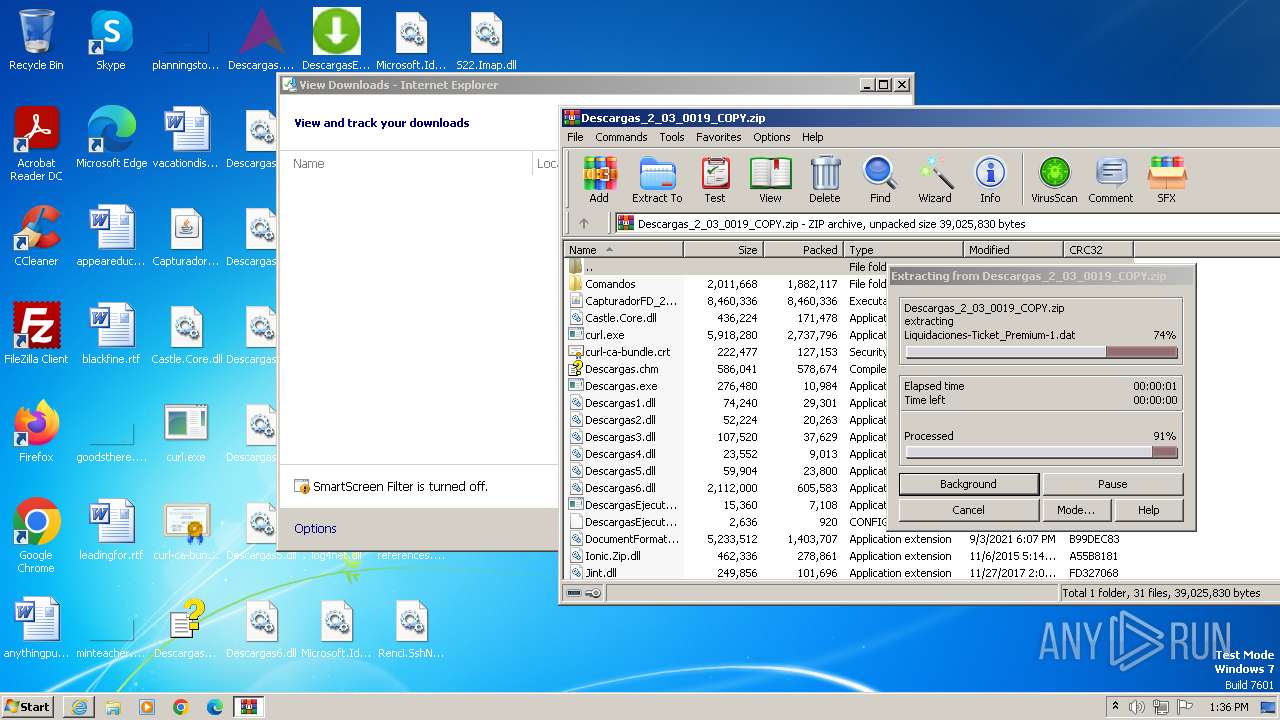
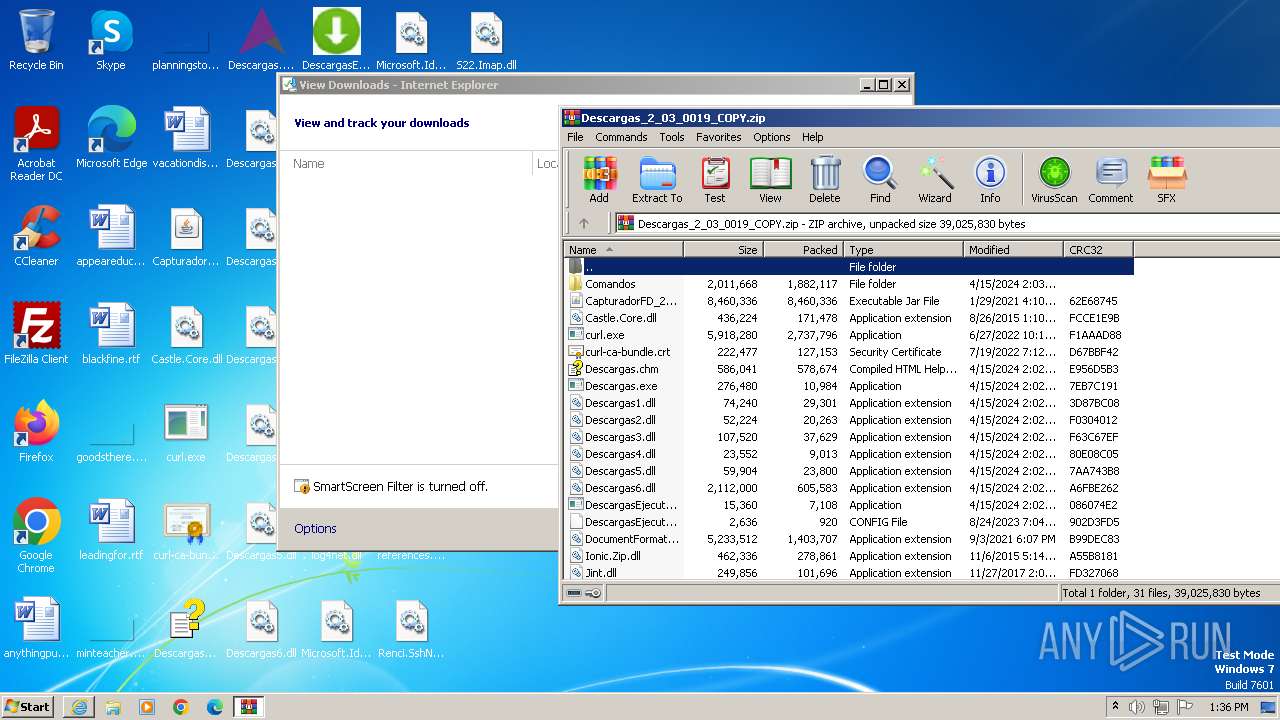
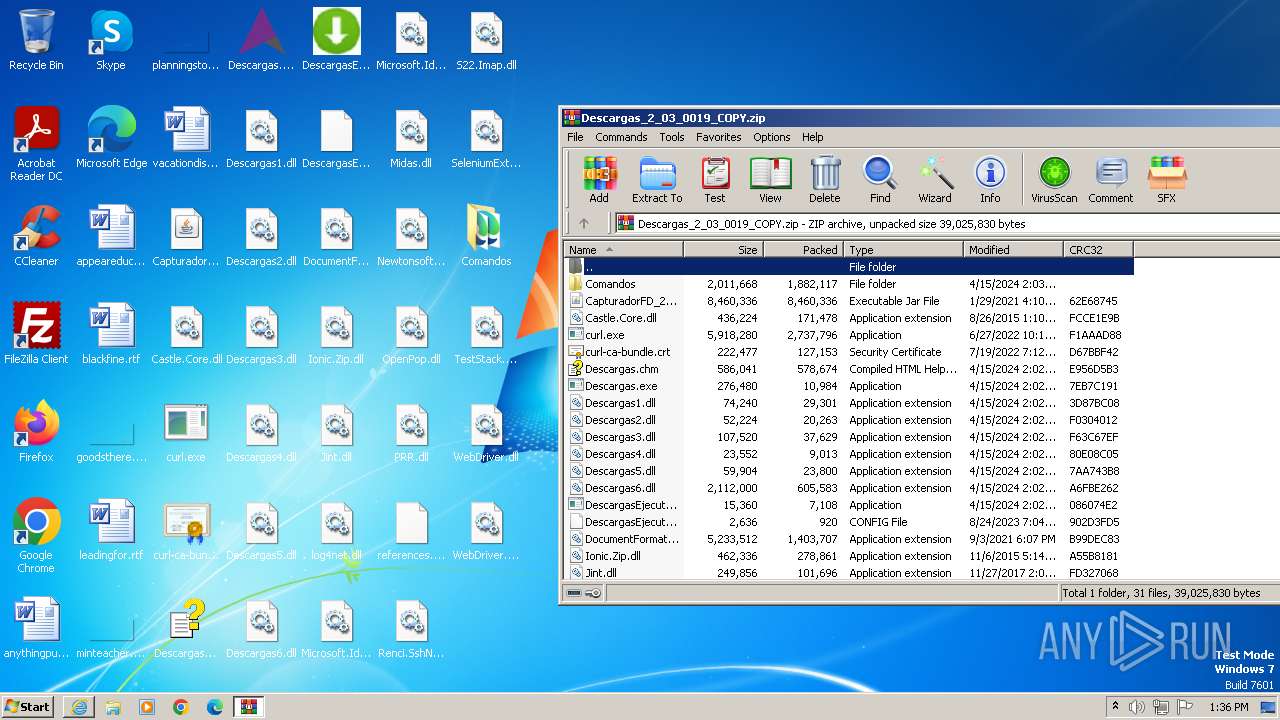
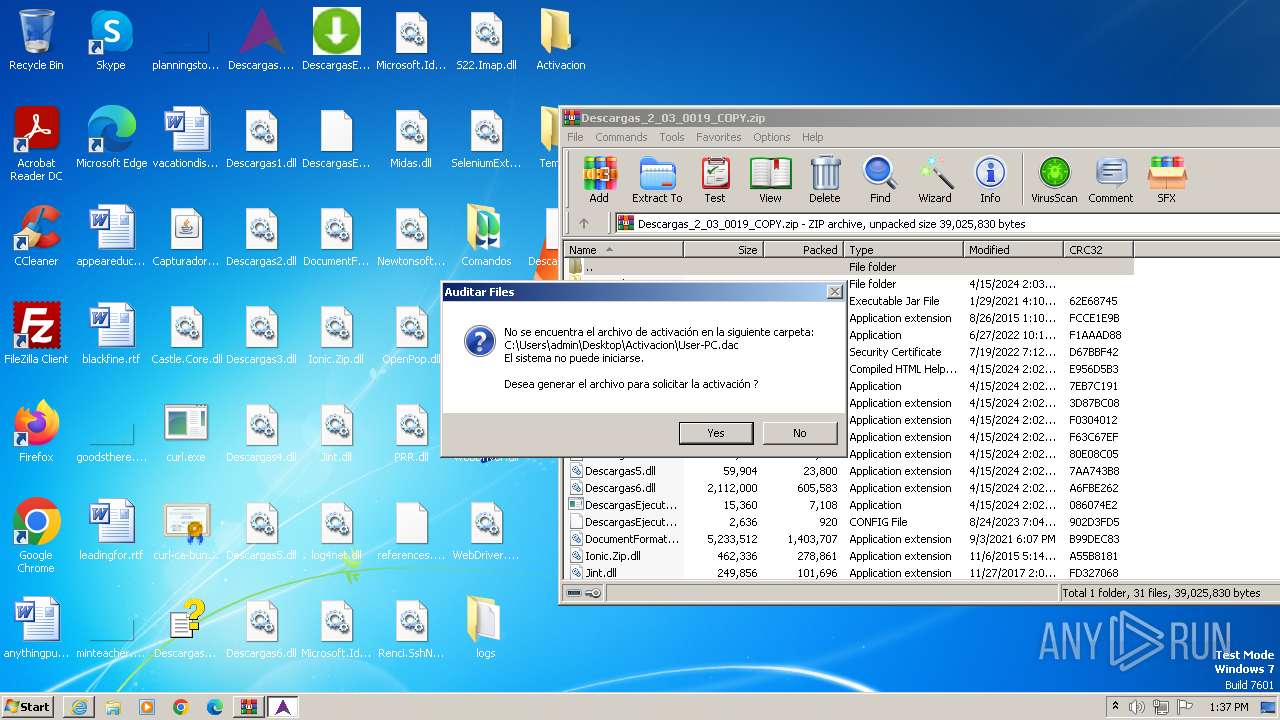
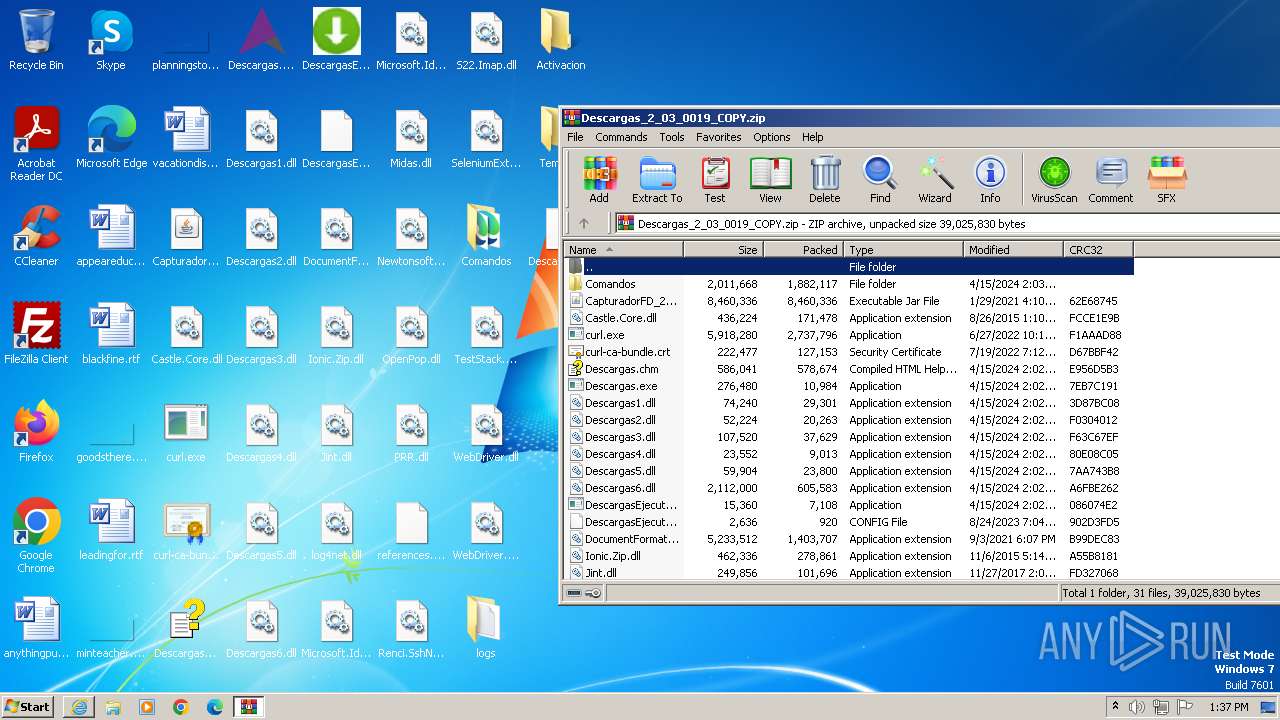
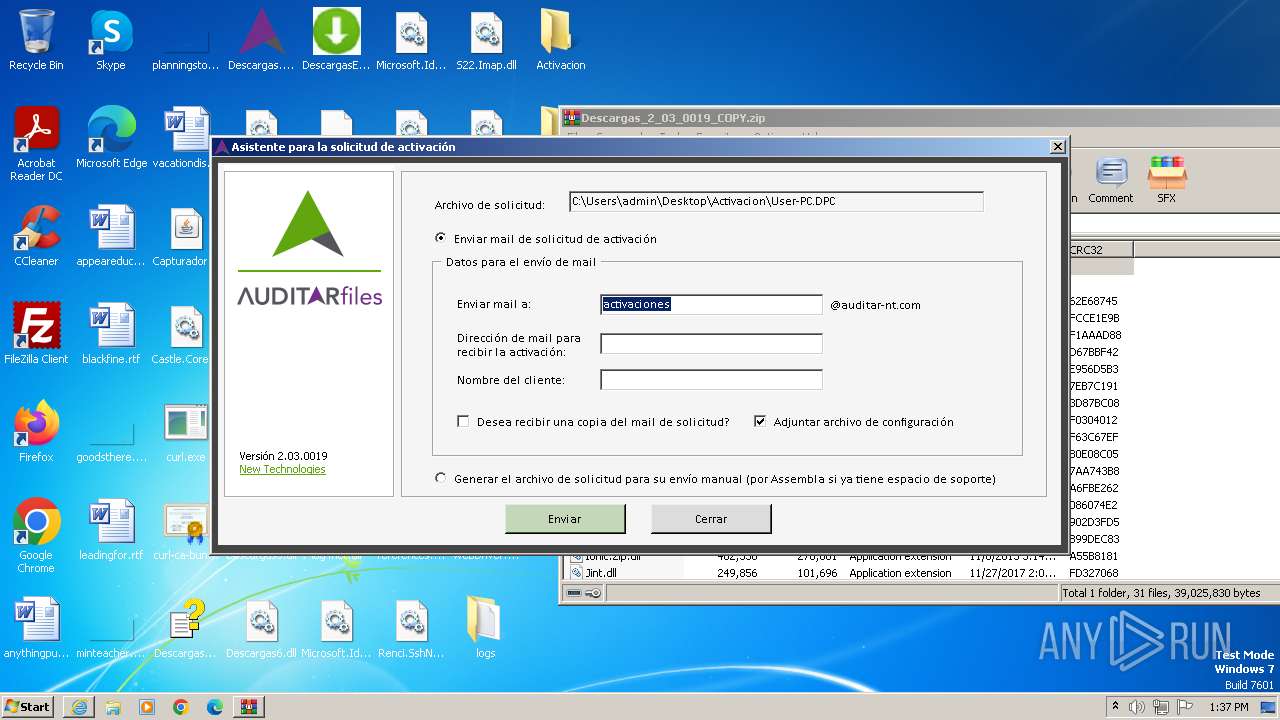
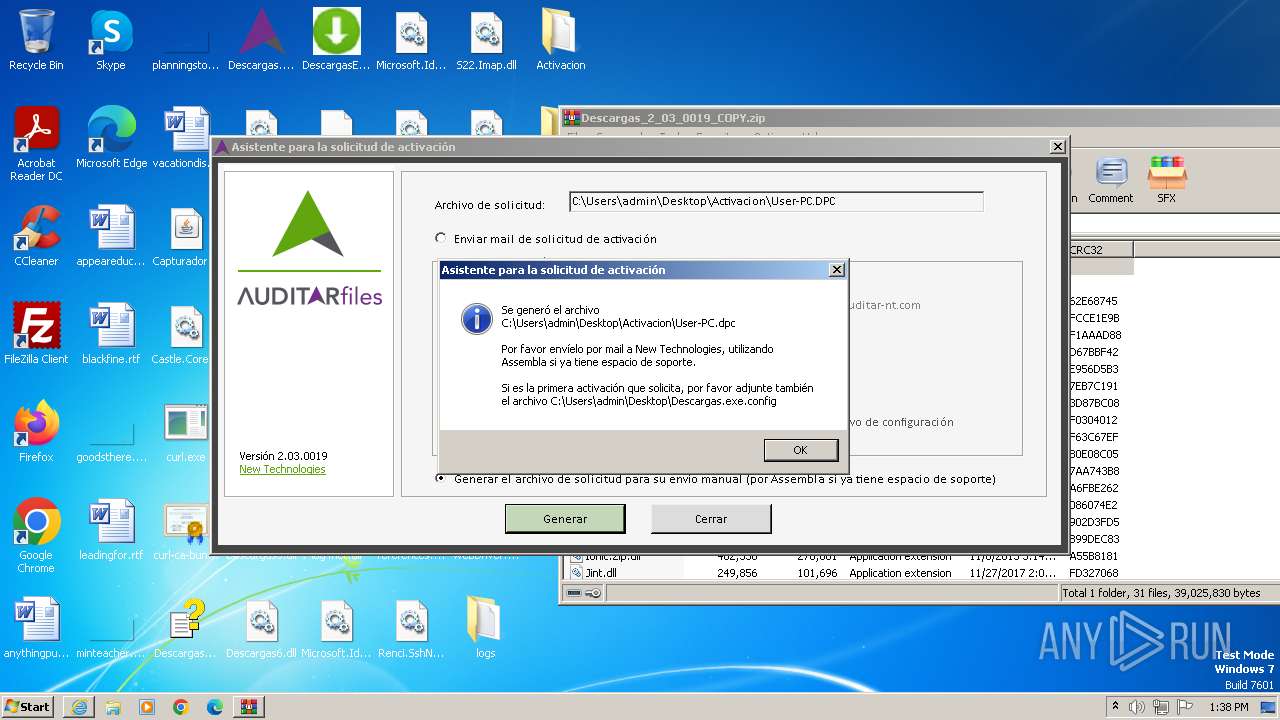
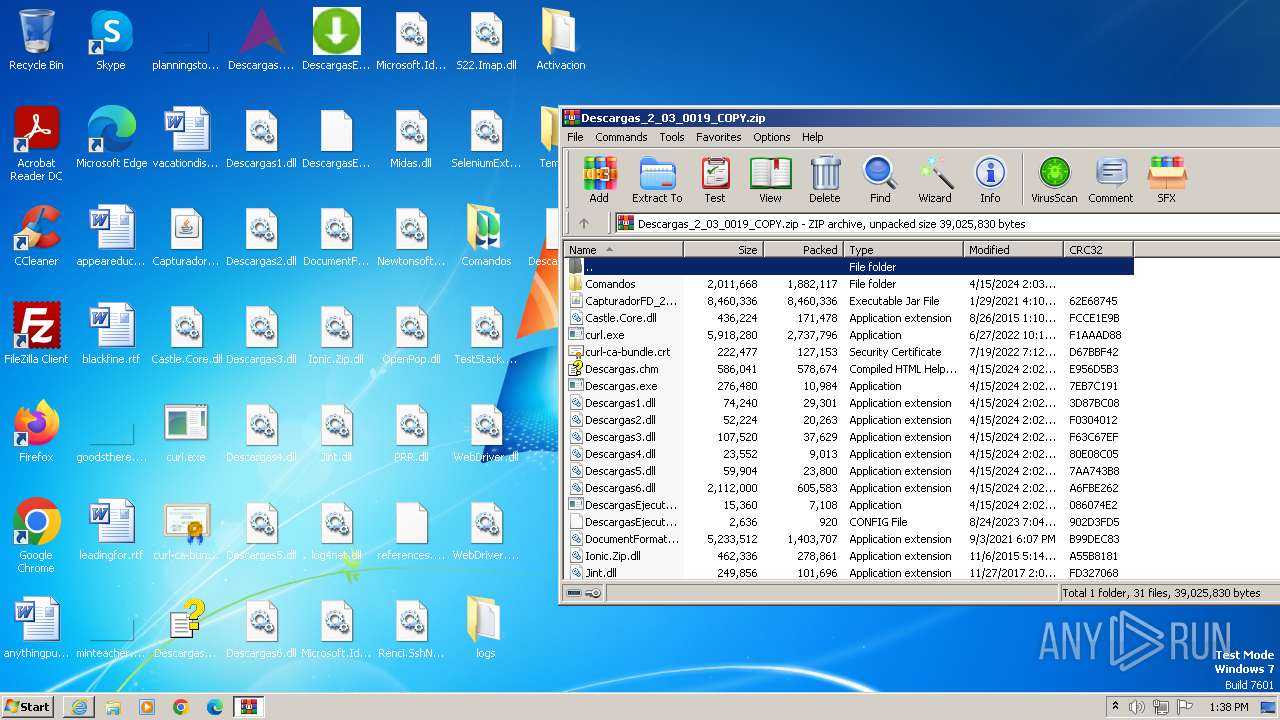
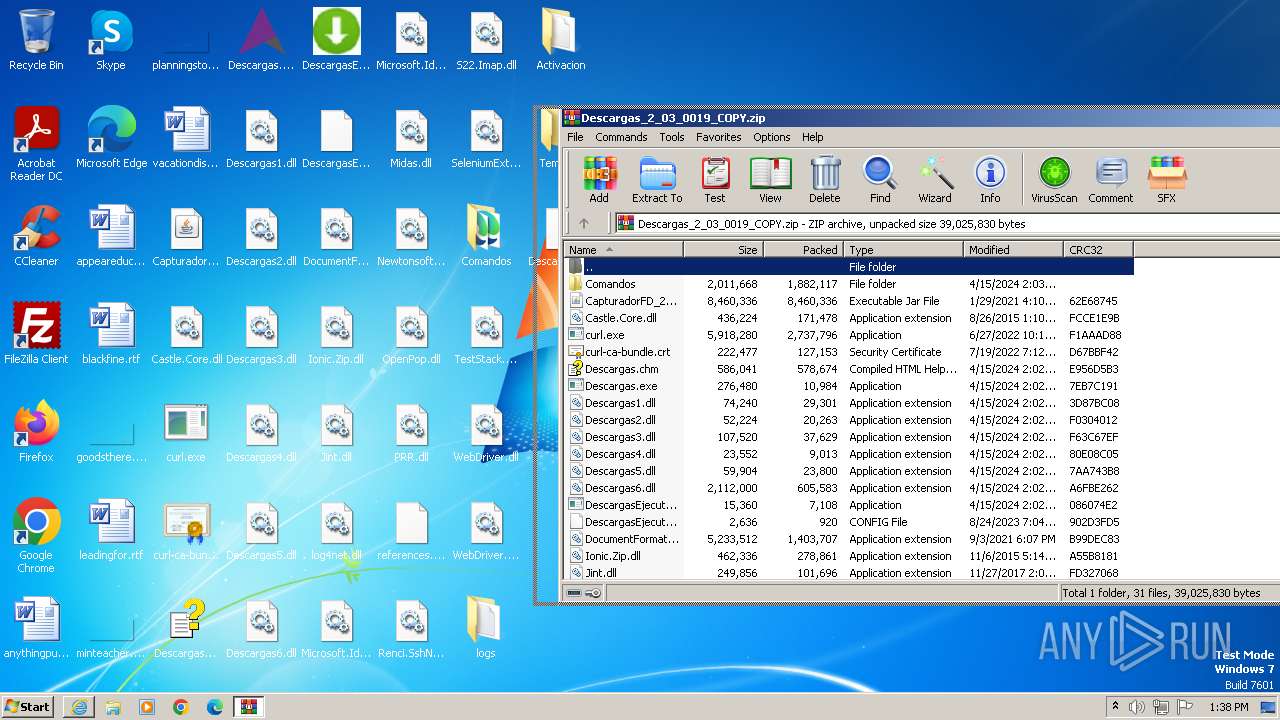
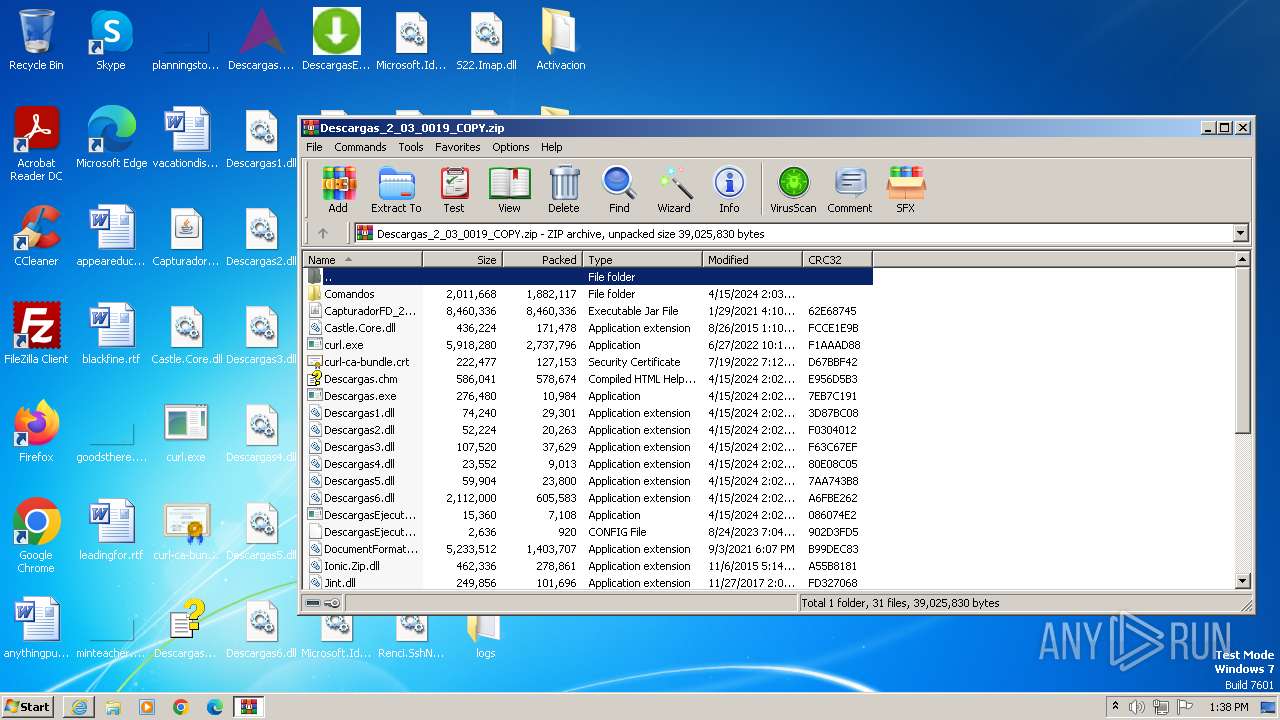
| URL: | http://www.newtechnologiesweb.com/downloads/Descargas_2_03_0019_COPY.zip |
| Full analysis: | https://app.any.run/tasks/c3aac70f-33b7-4ea1-91c7-6706e5ff008a |
| Verdict: | Malicious activity |
| Analysis date: | May 17, 2024, 12:33:41 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MD5: | 2BCD3D52FF51957F7B2BFE8B79DEB0A3 |
| SHA1: | 4B45F03223A21C0800CB1E97CCA30E0D999BD661 |
| SHA256: | 8B017EF805F1C32CAD661C5E54E1B86ED78001D807B650D56176E5CFDA32F98B |
| SSDEEP: | 3:N1KJS40iAaeqHzKXKgEwOc41/:Cc40qmagXz41/ |
MALICIOUS
No malicious indicators.SUSPICIOUS
Process drops legitimate windows executable
- WinRAR.exe (PID: 764)
Reads the Internet Settings
- DescargasEjecutor.exe (PID: 2256)
- DescargasEjecutor.exe (PID: 2516)
- Descargas.exe (PID: 1980)
- Descargas.exe (PID: 1888)
Reads security settings of Internet Explorer
- DescargasEjecutor.exe (PID: 2256)
- Descargas.exe (PID: 1980)
- Descargas.exe (PID: 1888)
- DescargasEjecutor.exe (PID: 2516)
INFO
Modifies the phishing filter of IE
- iexplore.exe (PID: 3968)
Manual execution by a user
- wmpnscfg.exe (PID: 2032)
- DescargasEjecutor.exe (PID: 2256)
- DescargasEjecutor.exe (PID: 2516)
- Descargas.exe (PID: 1980)
- Descargas.exe (PID: 1888)
Application launched itself
- iexplore.exe (PID: 3968)
Checks supported languages
- wmpnscfg.exe (PID: 2032)
- DescargasEjecutor.exe (PID: 2256)
- DescargasEjecutor.exe (PID: 2516)
- Descargas.exe (PID: 1980)
- Descargas.exe (PID: 1888)
Reads the computer name
- wmpnscfg.exe (PID: 2032)
- DescargasEjecutor.exe (PID: 2256)
- DescargasEjecutor.exe (PID: 2516)
- Descargas.exe (PID: 1980)
- Descargas.exe (PID: 1888)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 764)
The process uses the downloaded file
- iexplore.exe (PID: 3968)
- WinRAR.exe (PID: 764)
Reads the machine GUID from the registry
- DescargasEjecutor.exe (PID: 2256)
- DescargasEjecutor.exe (PID: 2516)
- Descargas.exe (PID: 1980)
- Descargas.exe (PID: 1888)
Drops the executable file immediately after the start
- WinRAR.exe (PID: 764)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
53
Monitored processes
8
Malicious processes
0
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 764 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\B6QGX7LP\Descargas_2_03_0019_COPY.zip" | C:\Program Files\WinRAR\WinRAR.exe | iexplore.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Version: 5.91.0 Modules
| |||||||||||||||
| 1888 | "C:\Users\admin\Desktop\Descargas.exe" | C:\Users\admin\Desktop\Descargas.exe | — | explorer.exe | |||||||||||
User: admin Company: New Technologies Integrity Level: MEDIUM Description: Descargas Exit code: 2 Version: 1.0.0.0 Modules
| |||||||||||||||
| 1980 | "C:\Users\admin\Desktop\Descargas.exe" | C:\Users\admin\Desktop\Descargas.exe | — | explorer.exe | |||||||||||
User: admin Company: New Technologies Integrity Level: MEDIUM Description: Descargas Exit code: 0 Version: 1.0.0.0 Modules
| |||||||||||||||
| 2032 | "C:\Program Files\Windows Media Player\wmpnscfg.exe" | C:\Program Files\Windows Media Player\wmpnscfg.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Media Player Network Sharing Service Configuration Application Exit code: 0 Version: 12.0.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2256 | "C:\Users\admin\Desktop\DescargasEjecutor.exe" | C:\Users\admin\Desktop\DescargasEjecutor.exe | explorer.exe | ||||||||||||
User: admin Company: New Technologies Integrity Level: MEDIUM Description: Descargas Exit code: 1 Version: 1.0.0.0 Modules
| |||||||||||||||
| 2516 | "C:\Users\admin\Desktop\DescargasEjecutor.exe" | C:\Users\admin\Desktop\DescargasEjecutor.exe | explorer.exe | ||||||||||||
User: admin Company: New Technologies Integrity Level: MEDIUM Description: Descargas Exit code: 1 Version: 1.0.0.0 Modules
| |||||||||||||||
| 3968 | "C:\Program Files\Internet Explorer\iexplore.exe" "http://www.newtechnologiesweb.com/downloads/Descargas_2_03_0019_COPY.zip" | C:\Program Files\Internet Explorer\iexplore.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Internet Explorer Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
| 4028 | "C:\Program Files\Internet Explorer\iexplore.exe" SCODEF:3968 CREDAT:267521 /prefetch:2 | C:\Program Files\Internet Explorer\iexplore.exe | iexplore.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Internet Explorer Exit code: 0 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
Total events
23 034
Read events
22 838
Write events
153
Delete events
43
Modification events
| (PID) Process: | (3968) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPDaysSinceLastAutoMigration |
Value: 1 | |||
| (PID) Process: | (3968) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPLastLaunchLowDateTime |
Value: | |||
| (PID) Process: | (3968) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPLastLaunchHighDateTime |
Value: 31107158 | |||
| (PID) Process: | (3968) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\UrlBlockManager |
| Operation: | write | Name: | NextCheckForUpdateLowDateTime |
Value: | |||
| (PID) Process: | (3968) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\UrlBlockManager |
| Operation: | write | Name: | NextCheckForUpdateHighDateTime |
Value: 31107158 | |||
| (PID) Process: | (3968) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Content |
| Operation: | write | Name: | CachePrefix |
Value: | |||
| (PID) Process: | (3968) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (3968) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
| (PID) Process: | (3968) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\Main |
| Operation: | write | Name: | CompatibilityFlags |
Value: 0 | |||
| (PID) Process: | (3968) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
Executable files
55
Suspicious files
185
Text files
110
Unknown types
1
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3968 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\B6QGX7LP\urlblockindex[1].bin | binary | |
MD5:FA518E3DFAE8CA3A0E495460FD60C791 | SHA256:775853600060162C4B4E5F883F9FD5A278E61C471B3EE1826396B6D129499AA7 | |||
| 4028 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\B6QGX7LP\Descargas_2_03_0019_COPY.zip.h4f34w3.partial | compressed | |
MD5:9FDE69F997E15BADD5D0ECD03A9D54A9 | SHA256:39570DF9BB616D2D184FBD9555FC7CFDAFD47F2500EDEF329072377206518306 | |||
| 3968 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Internet Explorer\VersionManager\versionlist.xml | xml | |
MD5:CBD0581678FA40F0EDCBC7C59E0CAD10 | SHA256:159BD4343F344A08F6AF3B716B6FA679859C1BD1D7030D26FF5EF0255B86E1D9 | |||
| 3968 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\7423F88C7F265F0DEFC08EA88C3BDE45_AA1E8580D4EBC816148CE81268683776 | binary | |
MD5:2C0220CEB016B27477538660EB0234FB | SHA256:77A531C9A5E789DE9EB42ED4F5F87A33B7D6A5224AAA61CFD6282F0CB3899B43 | |||
| 3968 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Internet Explorer\VersionManager\verCE00.tmp | xml | |
MD5:CBD0581678FA40F0EDCBC7C59E0CAD10 | SHA256:159BD4343F344A08F6AF3B716B6FA679859C1BD1D7030D26FF5EF0255B86E1D9 | |||
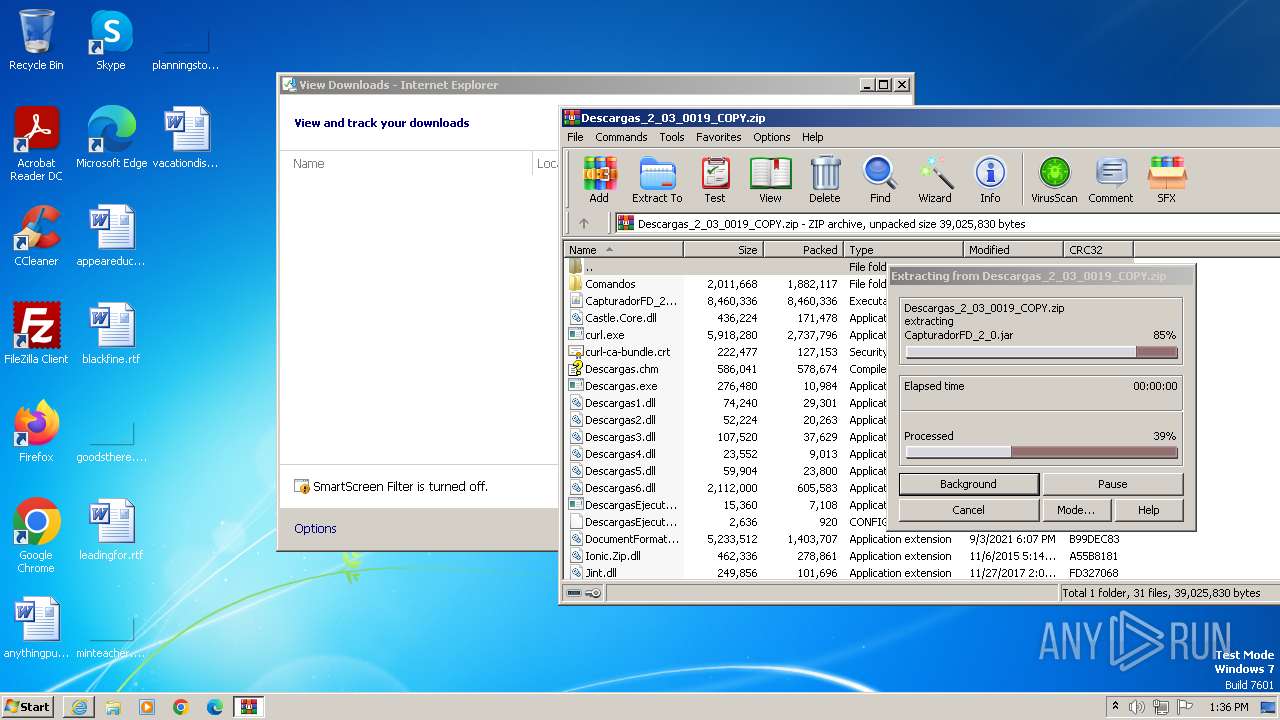
| 764 | WinRAR.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\B6QGX7LP\Descargas_2_03_0019_COPY\CapturadorFD_2_0.jar | compressed | |
MD5:605C9CE5349142D10EE8CD229D0F6429 | SHA256:F468C12F79C058EF94C9E6B5FE1448795113751A06C86B2769386C2E93C01D7D | |||
| 3968 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\B6QGX7LP\Descargas_2_03_0019_COPY.zip | compressed | |
MD5:1A49A6BEEBB7EE72ABE3207ACC29C636 | SHA256:18FDF19FB06D8B731D69B589C6DEA6A4F5D97A33534C987255E48673E3CB50BD | |||
| 3968 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Internet Explorer\Recovery\Active\{B620BB45-1449-11EF-9E36-12A9866C77DE}.dat | binary | |
MD5:A7507BA799477280E50690A58008082F | SHA256:540258A1984D66CBDA6029D09B9182C1472490D2ABE0836045396E7FD92BA3AB | |||
| 764 | WinRAR.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\B6QGX7LP\Descargas_2_03_0019_COPY\curl-ca-bundle.crt | text | |
MD5:CBA7B319792B372675225B57279BE08E | SHA256:6ED95025FBA2AEF0CE7B647607225745624497F876D74EF6EC22B26E73E9DE77 | |||
| 3968 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\57C8EDB95DF3F0AD4EE2DC2B8CFD4157 | binary | |
MD5:4BB3C3F1734E9FB2A30A07590075DBB6 | SHA256:F6B094F29B463F62AA4879CF54AE9AD884178727C9341CAFDBB8619C669DB2E2 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
10
TCP/UDP connections
21
DNS requests
11
Threats
1
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
4028 | iexplore.exe | GET | — | 209.59.169.153:80 | http://www.newtechnologiesweb.com/downloads/Descargas_2_03_0019_COPY.zip | unknown | — | — | unknown |
3968 | iexplore.exe | GET | 304 | 199.232.210.172:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?c21588876f974d24 | unknown | — | — | unknown |
3968 | iexplore.exe | GET | 304 | 199.232.210.172:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?7d495c908dca8b32 | unknown | — | — | unknown |
3968 | iexplore.exe | GET | 304 | 199.232.214.172:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?375896791b56e52b | unknown | — | — | unknown |
1088 | svchost.exe | GET | 304 | 199.232.214.172:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?4f7497503626c948 | unknown | — | — | unknown |
3968 | iexplore.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | unknown |
4028 | iexplore.exe | GET | 206 | 209.59.169.153:80 | http://www.newtechnologiesweb.com/downloads/Descargas_2_03_0019_COPY.zip | unknown | — | — | unknown |
3968 | iexplore.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | unknown |
3968 | iexplore.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAxq6XzO1ZmDhpCgCp6lMhQ%3D | unknown | — | — | unknown |
3968 | iexplore.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEA177el9ggmWelJjG4vdGL0%3D | unknown | — | — | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4028 | iexplore.exe | 209.59.169.153:80 | www.newtechnologiesweb.com | LIQUIDWEB | US | unknown |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
3968 | iexplore.exe | 152.199.19.161:443 | r20swj13mr.microsoft.com | EDGECAST | US | whitelisted |
3968 | iexplore.exe | 199.232.210.172:80 | ctldl.windowsupdate.com | FASTLY | US | unknown |
3968 | iexplore.exe | 199.232.214.172:80 | ctldl.windowsupdate.com | FASTLY | US | unknown |
3968 | iexplore.exe | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
1088 | svchost.exe | 199.232.214.172:80 | ctldl.windowsupdate.com | FASTLY | US | unknown |
3968 | iexplore.exe | 204.79.197.200:443 | ieonline.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
3968 | iexplore.exe | 23.35.238.131:443 | go.microsoft.com | AKAMAI-AS | DE | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
www.newtechnologiesweb.com |
| unknown |
r20swj13mr.microsoft.com |
| whitelisted |
iecvlist.microsoft.com |
| whitelisted |
ctldl.windowsupdate.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
ieonline.microsoft.com |
| whitelisted |
go.microsoft.com |
| whitelisted |
www.msn.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
— | — | Attempted Administrator Privilege Gain | AV EXPLOIT Potential ZIP file exploiting CVE-2023-36413 |
Process | Message |
|---|---|
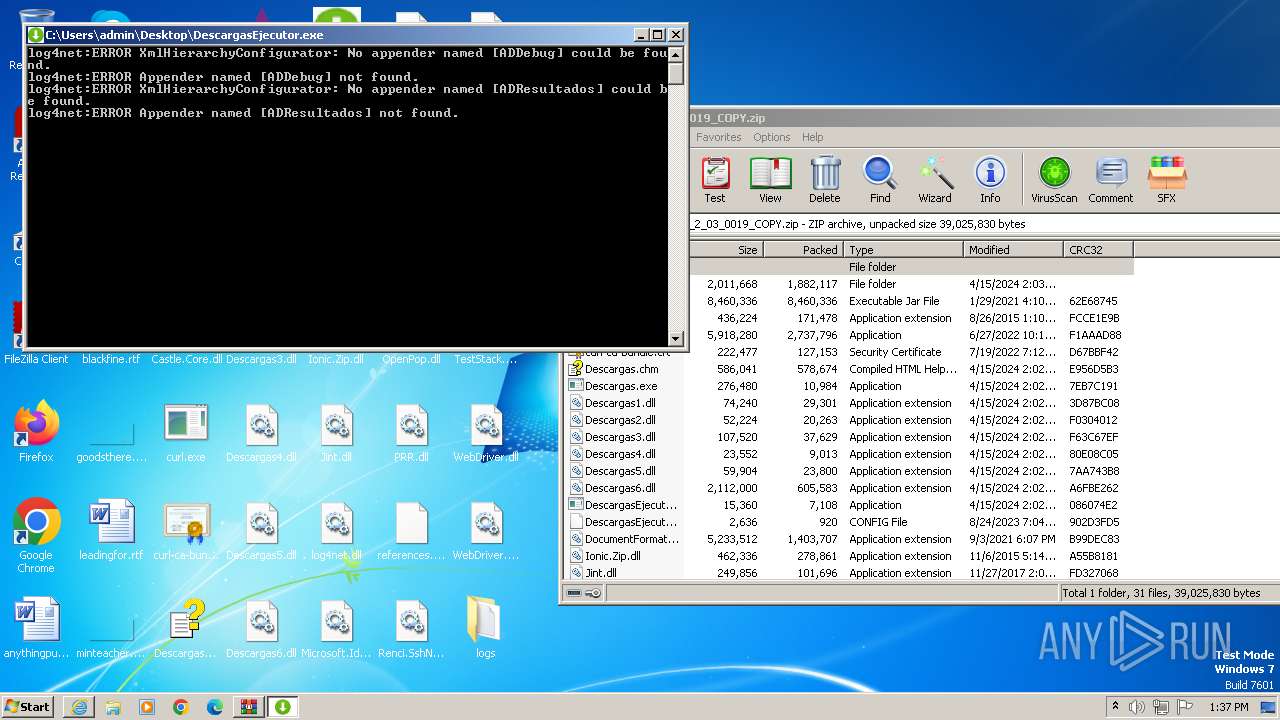
DescargasEjecutor.exe | log4net:ERROR Appender named [ADDebug] not found.
|
DescargasEjecutor.exe | log4net:ERROR XmlHierarchyConfigurator: No appender named [ADDebug] could be found.
|
DescargasEjecutor.exe | log4net:ERROR XmlHierarchyConfigurator: No appender named [ADResultados] could be found.
|
DescargasEjecutor.exe | log4net:ERROR Appender named [ADResultados] not found.
|
DescargasEjecutor.exe | log4net:ERROR Appender named [ADResultados] not found.
|
DescargasEjecutor.exe | log4net:ERROR XmlHierarchyConfigurator: No appender named [ADDebug] could be found.
|
DescargasEjecutor.exe | log4net:ERROR Appender named [ADDebug] not found.
|
DescargasEjecutor.exe | log4net:ERROR XmlHierarchyConfigurator: No appender named [ADResultados] could be found.
|