| URL: | http://deliverhq.org/a12 |
| Full analysis: | https://app.any.run/tasks/b4d6acc9-d598-4f2f-adc1-a7b00e5bec20 |
| Verdict: | Malicious activity |
| Analysis date: | November 25, 2023, 17:38:54 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| SHA1: | ADDC2388F695ADF5022B97623D4823F35E22F58E |
| SHA256: | 8B002EB1CF880408EA81E9845C6DD7C0927F917E76B302BEE64343DD1071133B |
| SSDEEP: | 3:N1KaAJSC/:CahS |
MALICIOUS
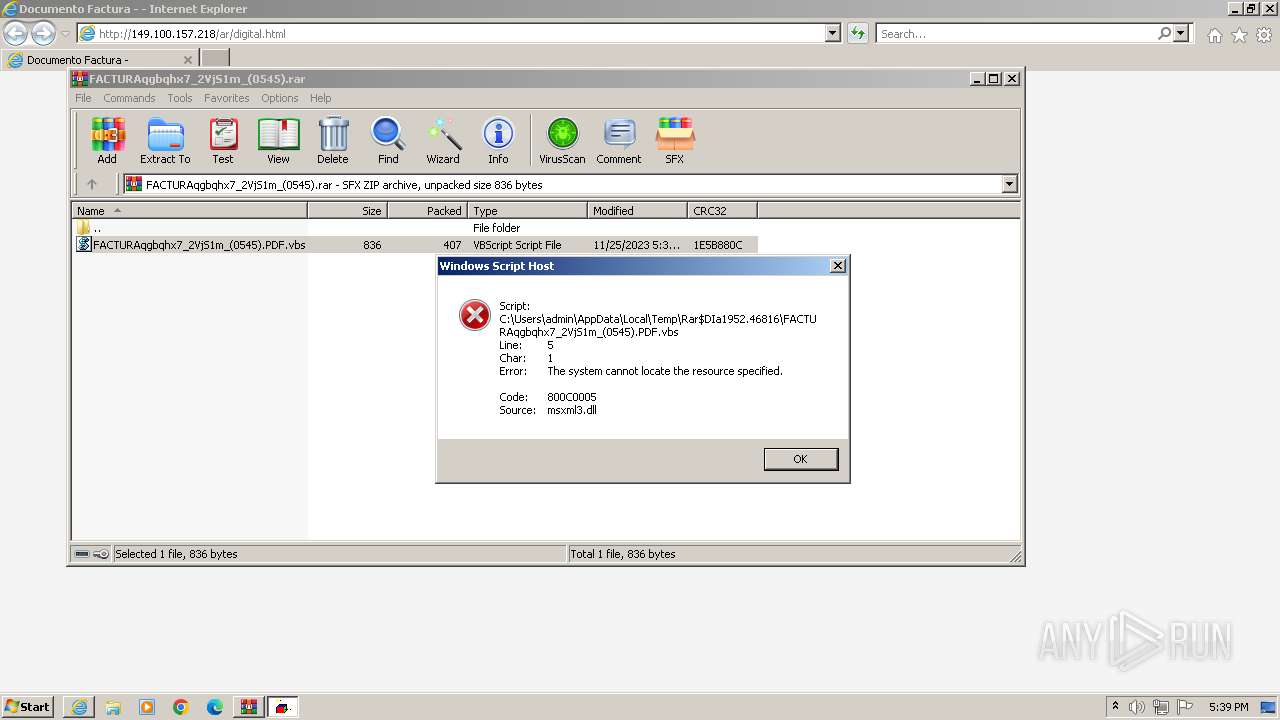
Creates internet connection object (SCRIPT)
- wscript.exe (PID: 2996)
Opens an HTTP connection (SCRIPT)
- wscript.exe (PID: 2996)
Sends HTTP request (SCRIPT)
- wscript.exe (PID: 2996)
SUSPICIOUS
Reads the Internet Settings
- wscript.exe (PID: 2996)
The process executes VB scripts
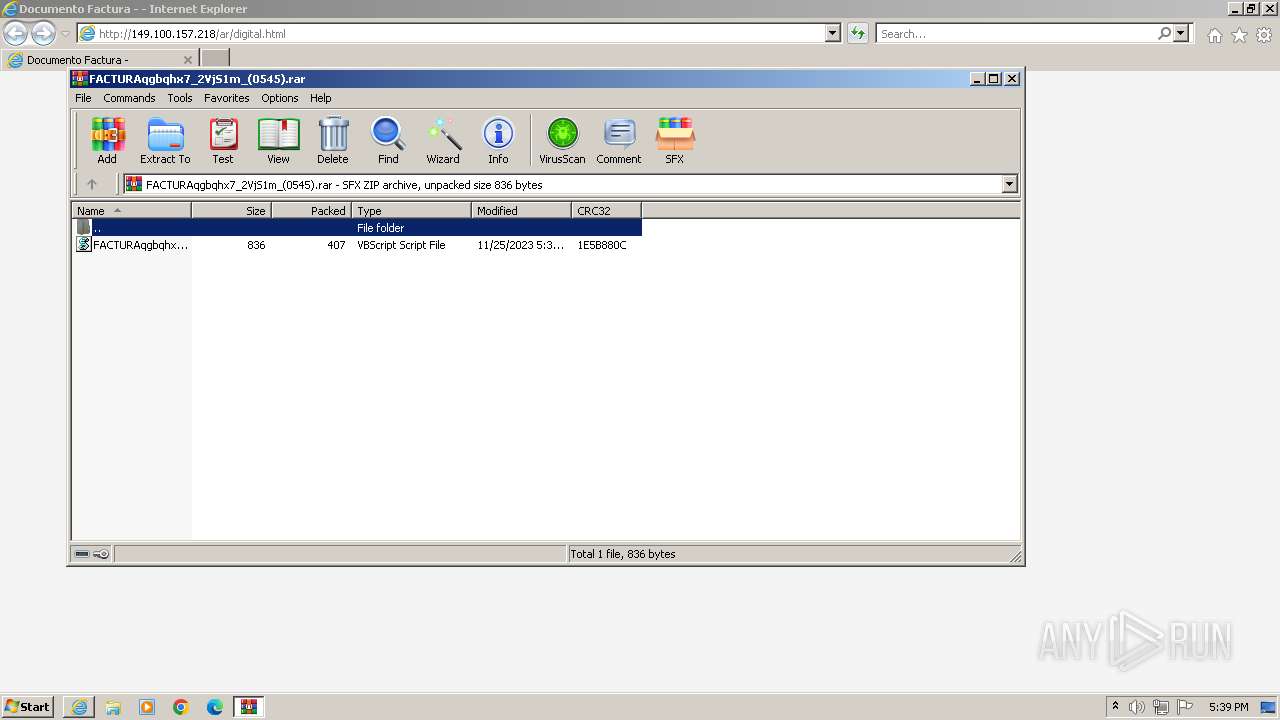
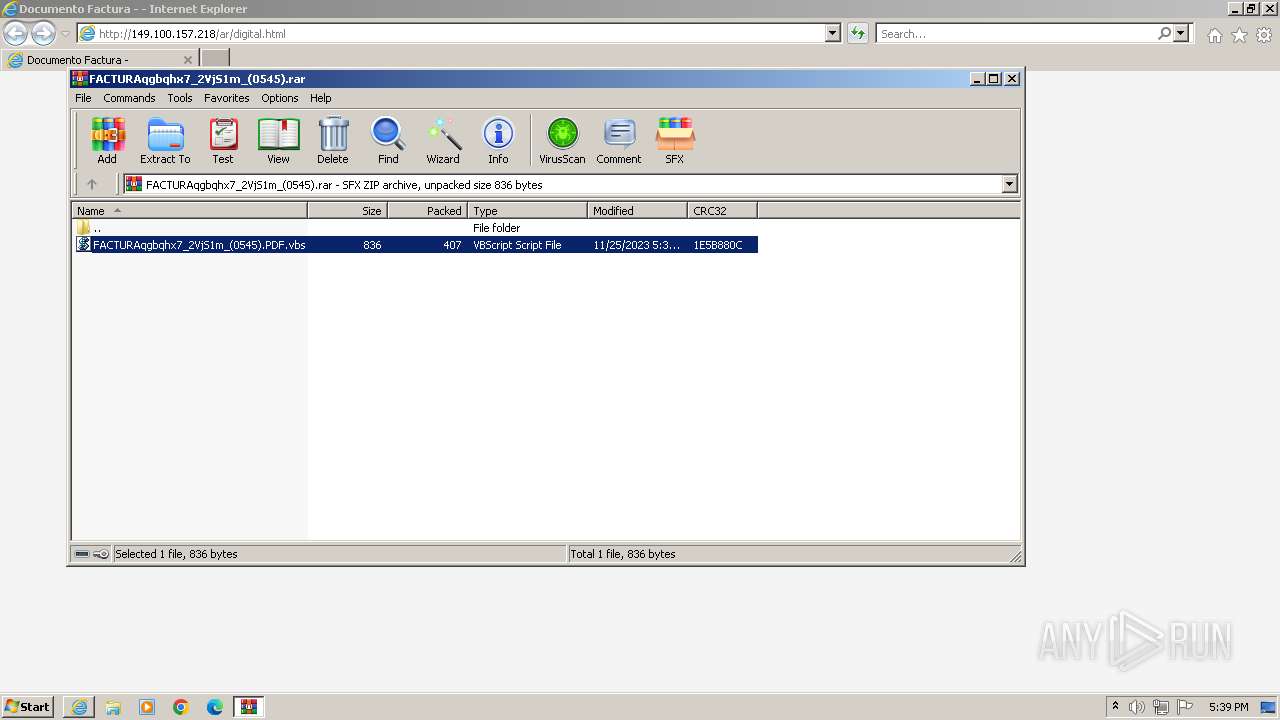
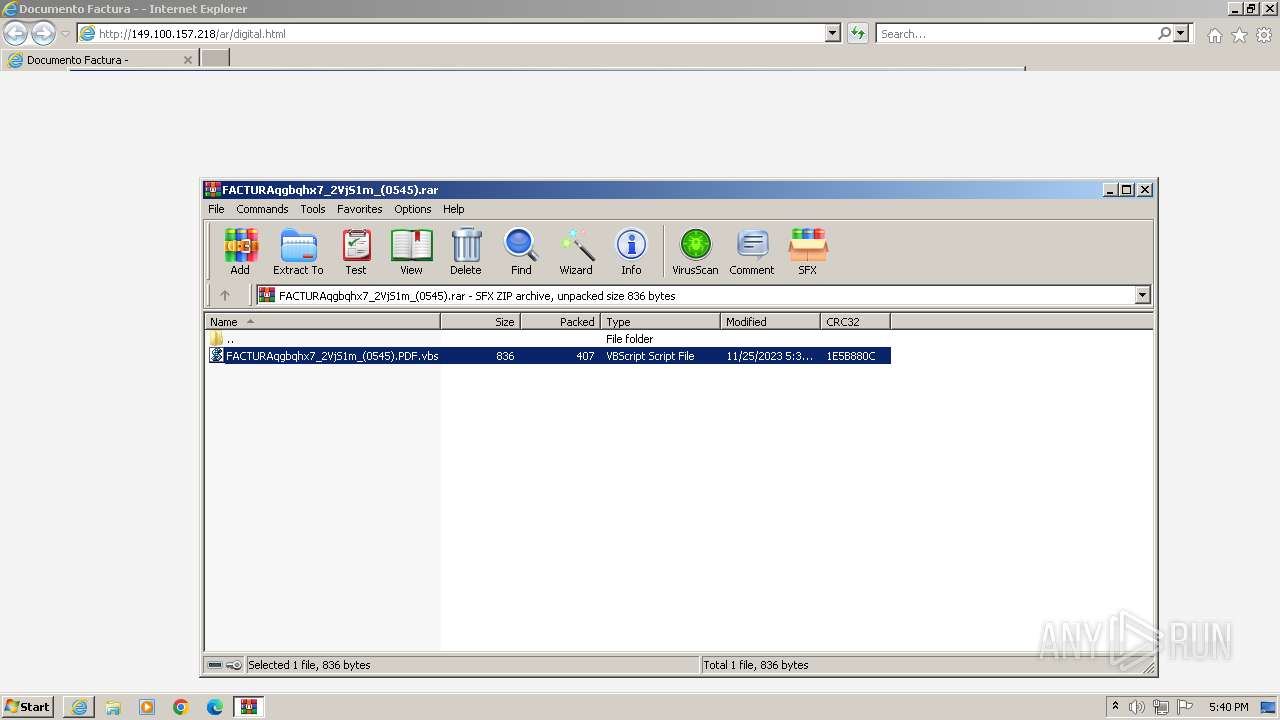
- WinRAR.exe (PID: 1952)
Adds, changes, or deletes HTTP request header (SCRIPT)
- wscript.exe (PID: 2996)
INFO
Reads the computer name
- wmpnscfg.exe (PID: 2400)
Application launched itself
- iexplore.exe (PID: 3004)
Checks supported languages
- wmpnscfg.exe (PID: 2400)
Checks proxy server information
- wscript.exe (PID: 2996)
Reads the machine GUID from the registry
- wmpnscfg.exe (PID: 2400)
Manual execution by a user
- wmpnscfg.exe (PID: 2400)
- explorer.exe (PID: 3152)
- WinRAR.exe (PID: 3424)
The process uses the downloaded file
- WinRAR.exe (PID: 1952)
- iexplore.exe (PID: 3004)
- WinRAR.exe (PID: 3424)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
51
Monitored processes
7
Malicious processes
2
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
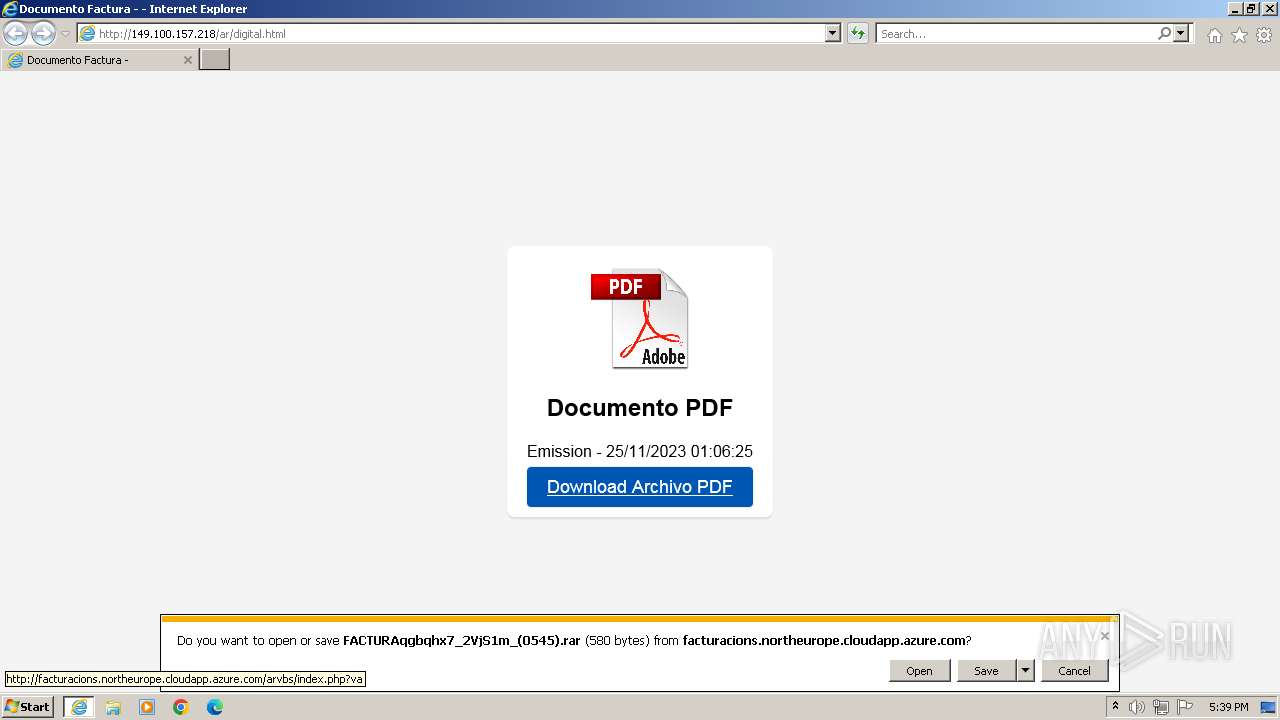
| 1952 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\B6QGX7LP\FACTURAqgbqhx7_2VjS1m_(0545).rar" | C:\Program Files\WinRAR\WinRAR.exe | — | iexplore.exe | |||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.91.0 Modules
| |||||||||||||||
| 2400 | "C:\Program Files\Windows Media Player\wmpnscfg.exe" | C:\Program Files\Windows Media Player\wmpnscfg.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Media Player Network Sharing Service Configuration Application Exit code: 0 Version: 12.0.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2996 | "C:\Windows\System32\WScript.exe" "C:\Users\admin\AppData\Local\Temp\Rar$DIa1952.46816\FACTURAqgbqhx7_2VjS1m_(0545).PDF.vbs" | C:\Windows\System32\wscript.exe | — | WinRAR.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft ® Windows Based Script Host Exit code: 0 Version: 5.8.7600.16385 Modules
| |||||||||||||||
| 3004 | "C:\Program Files\Internet Explorer\iexplore.exe" "http://deliverhq.org/a12" | C:\Program Files\Internet Explorer\iexplore.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Internet Explorer Exit code: 0 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
| 3024 | "C:\Program Files\Internet Explorer\iexplore.exe" SCODEF:3004 CREDAT:267521 /prefetch:2 | C:\Program Files\Internet Explorer\iexplore.exe | iexplore.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Internet Explorer Exit code: 0 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
| 3152 | "C:\Windows\explorer.exe" | C:\Windows\explorer.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Explorer Exit code: 1 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3424 | "C:\Program Files\WinRAR\WinRAR.exe" x -iext -ow -ver -- "C:\Users\admin\Downloads\FACTURAyfkQ_mJr09h(98).rar" C:\Users\admin\Downloads\FACTURAyfkQ_mJr09h(98)\ | C:\Program Files\WinRAR\WinRAR.exe | — | explorer.exe | |||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.91.0 Modules
| |||||||||||||||
Total events
15 000
Read events
14 871
Write events
126
Delete events
3
Modification events
| (PID) Process: | (3004) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPDaysSinceLastAutoMigration |
Value: 0 | |||
| (PID) Process: | (3004) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPLastLaunchHighDateTime |
Value: 30847387 | |||
| (PID) Process: | (3004) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\UrlBlockManager |
| Operation: | write | Name: | NextCheckForUpdateHighDateTime |
Value: 30847437 | |||
| (PID) Process: | (3004) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (3004) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
| (PID) Process: | (3004) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\Main |
| Operation: | write | Name: | CompatibilityFlags |
Value: 0 | |||
| (PID) Process: | (3004) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings |
| Operation: | write | Name: | ProxyEnable |
Value: 0 | |||
| (PID) Process: | (3004) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\Connections |
| Operation: | write | Name: | SavedLegacySettings |
Value: 4600000059010000090000000000000000000000000000000400000000000000C0E333BBEAB1D3010000000000000000000000000100000002000000C0A8016B000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (3004) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (3004) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
Executable files
0
Suspicious files
24
Text files
26
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3024 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\MFAQUS6V\a12[1].htm | html | |
MD5:E67EB918890D61941CCCF37C060E6BB1 | SHA256:003C18E426DA37B3CE5ACB60F40F2D4B9207DE68D0366B10381F07212ACE32ED | |||
| 3024 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\5IWPIAR9\pdf[1].png | image | |
MD5:E0E4E8434635E00627E2F868DF2500F9 | SHA256:ACFD78CB7C13332286CE42A942D6C48B640269059232035CB33DA9676CCDD574 | |||
| 3004 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\57C8EDB95DF3F0AD4EE2DC2B8CFD4157 | binary | |
MD5:551EA69439932E9EDF3EB98A3EA95BC9 | SHA256:959BF803CCD2D74BBEAE8EEA85F0195899B27822A1A81AE42CD6DF68F813DC46 | |||
| 3004 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\80237EE4964FC9C409AAF55BF996A292_C5130A0BDC8C859A2757D77746C10868 | binary | |
MD5:265FFD705374EB38CAF82242D43795D9 | SHA256:5C9B9DFAF8B02BFB69F530EC05EF4C2665ADA2740C84770485EDF75BDBE59574 | |||
| 3024 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\DY534W2X\a12[1].htm | html | |
MD5:FBEF015CDA2FC38ED11C10B0C61EB623 | SHA256:482142247FEDCBB782F8F92DAE9BF0A384A7A56AEAEE381959F128D44463C903 | |||
| 3004 | iexplore.exe | C:\Users\admin\AppData\Local\Temp\~DF87ADABC1FE893935.TMP | binary | |
MD5:024ECFB9A6976169431D1A358A7CCA23 | SHA256:BB8EA9CD6FC1BF0300CCAA6A98BDBD7EF178FEF7773B5A97BFC9F5FF4CF13C84 | |||
| 3004 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\78RFYB7Z\favicon[3].ico | image | |
MD5:DA597791BE3B6E732F0BC8B20E38EE62 | SHA256:5B2C34B3C4E8DD898B664DBA6C3786E2FF9869EFF55D673AA48361F11325ED07 | |||
| 3004 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\78RFYB7Z\favicon[2].ico | image | |
MD5:DA597791BE3B6E732F0BC8B20E38EE62 | SHA256:5B2C34B3C4E8DD898B664DBA6C3786E2FF9869EFF55D673AA48361F11325ED07 | |||
| 3004 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\80237EE4964FC9C409AAF55BF996A292_C5130A0BDC8C859A2757D77746C10868 | binary | |
MD5:4F5EA15BB427A646ABD987E7E005790F | SHA256:1DA1CF071B58FE063FC86F37AA3029964700CC3279BE005C8B5238375E34E29D | |||
| 3004 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Internet Explorer\Recovery\Active\{843203EC-8BB9-11EE-A826-12A9866C77DE}.dat | binary | |
MD5:104DD68D9573DF3C1E96B27A45CAB00B | SHA256:9C7952234C1021C4051BEBEB49096FDD9A3B5AF4F87C4C84225CBF8732C4C119 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
15
TCP/UDP connections
29
DNS requests
14
Threats
3
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
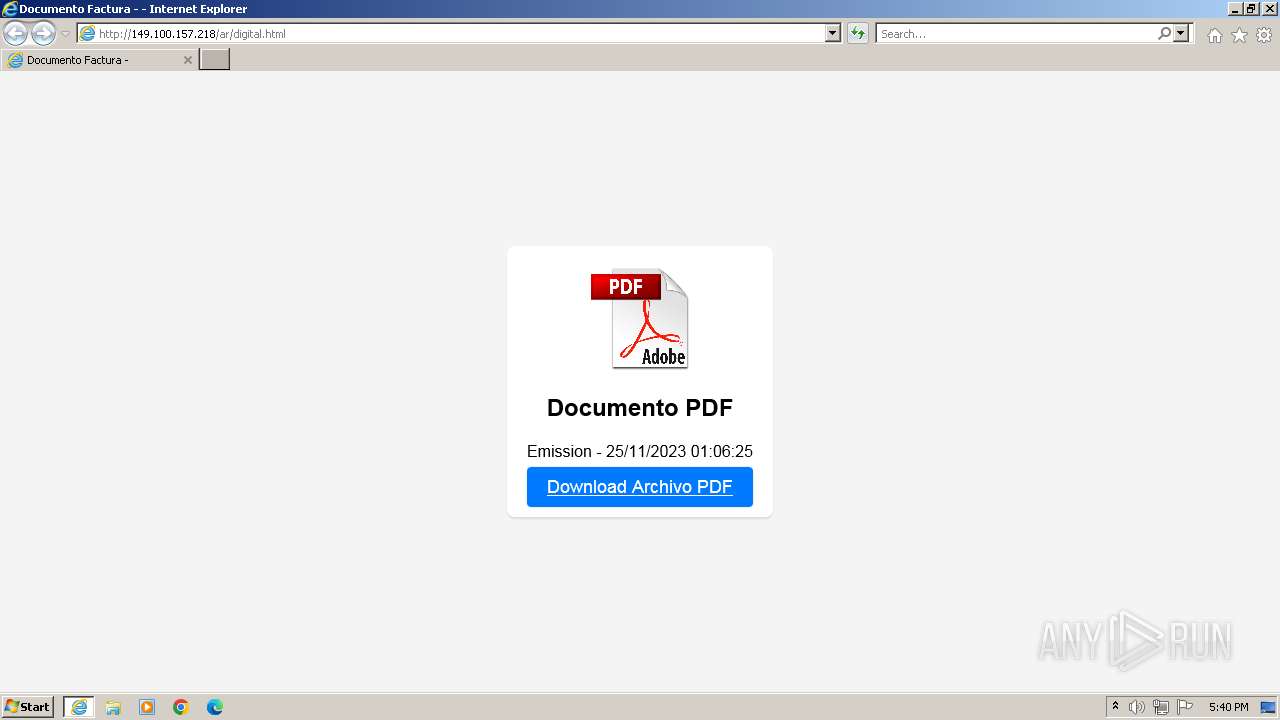
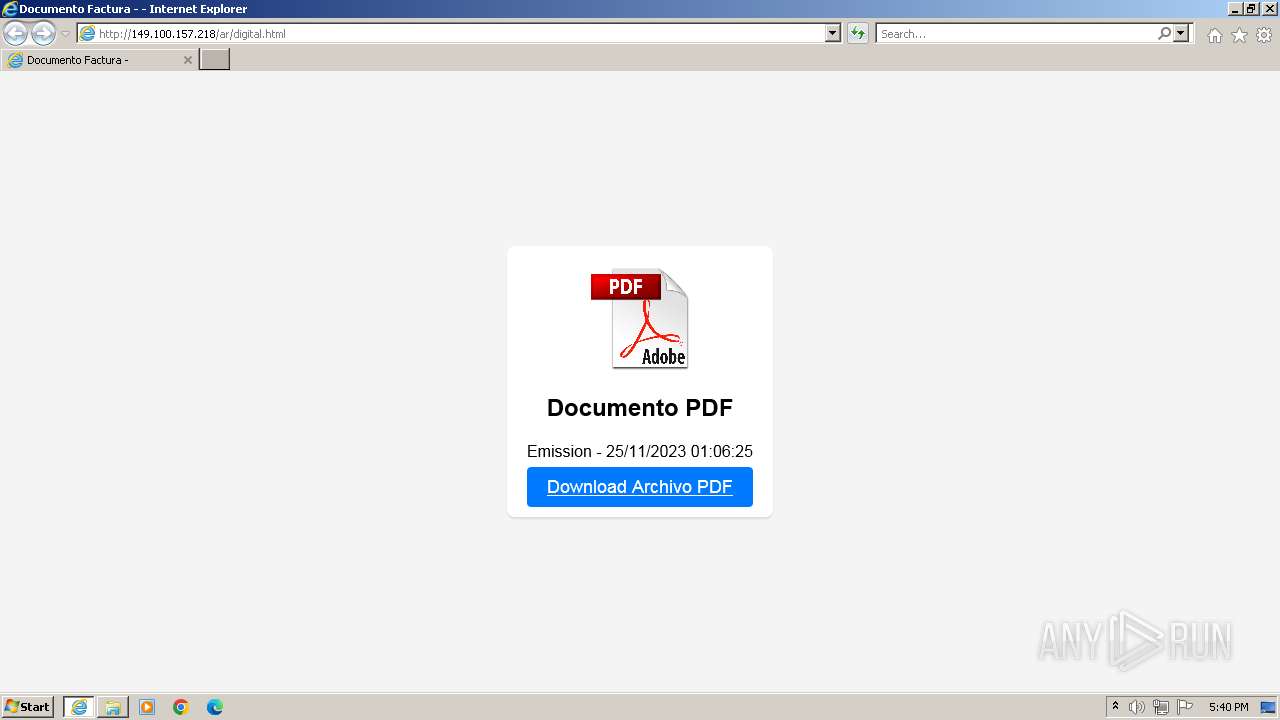
3024 | iexplore.exe | GET | 301 | 149.100.157.218:80 | http://deliverhq.org/a12 | unknown | html | 312 b | unknown |
3024 | iexplore.exe | GET | 200 | 149.100.157.218:80 | http://deliverhq.org/a12/ | unknown | html | 278 b | unknown |
3024 | iexplore.exe | GET | 200 | 149.100.157.218:80 | http://149.100.157.218/ar/digital.html | unknown | html | 760 b | unknown |
3024 | iexplore.exe | GET | 200 | 149.100.157.218:80 | http://149.100.157.218/ar/pdf.png | unknown | image | 160 Kb | unknown |
3004 | iexplore.exe | GET | 404 | 149.100.157.218:80 | http://149.100.157.218/favicon.ico | unknown | html | 277 b | unknown |
3004 | iexplore.exe | GET | 200 | 8.253.207.120:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?1baf01bbc5a6544d | unknown | compressed | 4.66 Kb | unknown |
3004 | iexplore.exe | GET | 200 | 8.253.207.120:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?32d41101e1be45bf | unknown | compressed | 4.66 Kb | unknown |
3004 | iexplore.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAqvpsXKY8RRQeo74ffHUxc%3D | unknown | binary | 471 b | unknown |
1080 | svchost.exe | GET | 304 | 8.253.207.120:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?049ef7e64aa6ea1a | unknown | — | — | unknown |
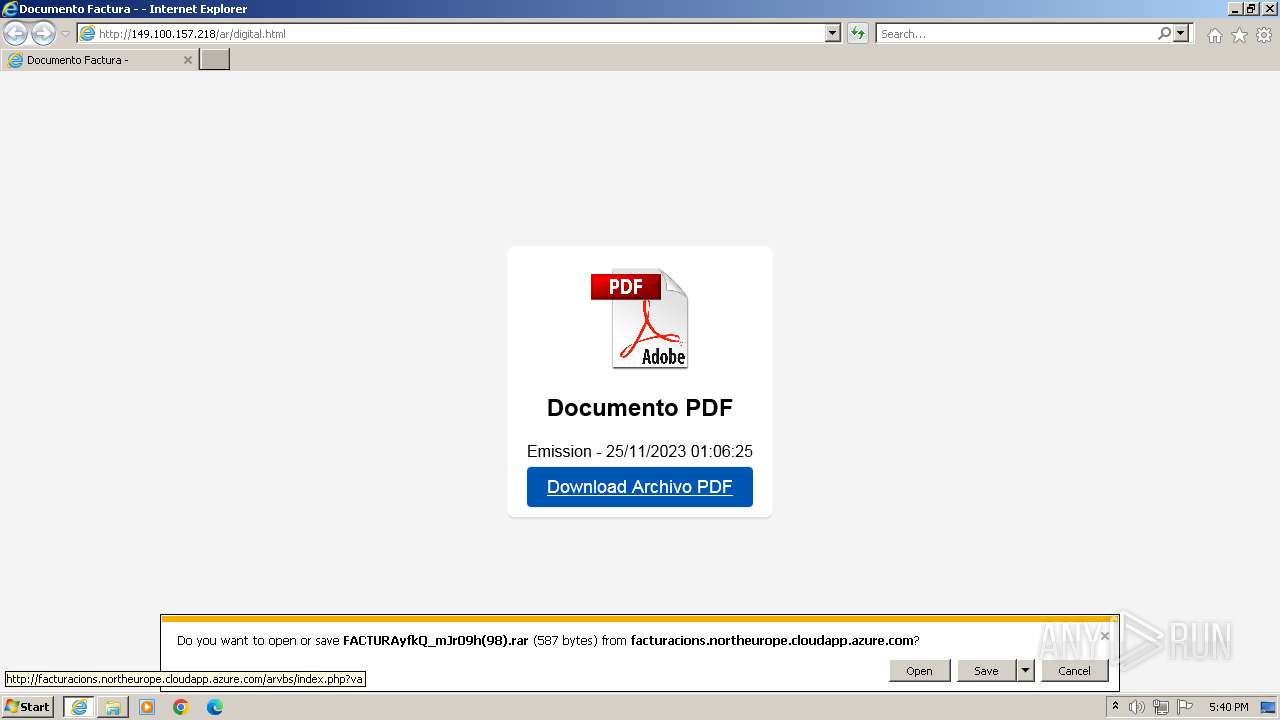
3024 | iexplore.exe | GET | 200 | 4.231.170.128:80 | http://facturacions.northeurope.cloudapp.azure.com/arvbs/index.php?va | unknown | binary | 580 b | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
3024 | iexplore.exe | 149.100.157.218:80 | deliverhq.org | COGENT-174 | US | unknown |
1080 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
3004 | iexplore.exe | 149.100.157.218:80 | deliverhq.org | COGENT-174 | US | unknown |
2588 | svchost.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
3004 | iexplore.exe | 204.79.197.200:443 | www.bing.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
3004 | iexplore.exe | 8.253.207.120:80 | ctldl.windowsupdate.com | LEVEL3 | US | unknown |
3004 | iexplore.exe | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
1080 | svchost.exe | 8.253.207.120:80 | ctldl.windowsupdate.com | LEVEL3 | US | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
deliverhq.org |
| unknown |
api.bing.com |
| whitelisted |
www.bing.com |
| whitelisted |
ctldl.windowsupdate.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
facturacions.northeurope.cloudapp.azure.com |
| unknown |
r20swj13mr.microsoft.com |
| whitelisted |
iecvlist.microsoft.com |
| whitelisted |
fabulasnats.ddnsking.com |
| unknown |
ieonline.microsoft.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
3024 | iexplore.exe | Potentially Bad Traffic | ET HUNTING Suspicious Possible Zip DL containing single VBS script |
1080 | svchost.exe | Potentially Bad Traffic | ET POLICY DNS Query to DynDNS Domain *.ddnsking .com |
3024 | iexplore.exe | Potentially Bad Traffic | ET HUNTING Suspicious Possible Zip DL containing single VBS script |