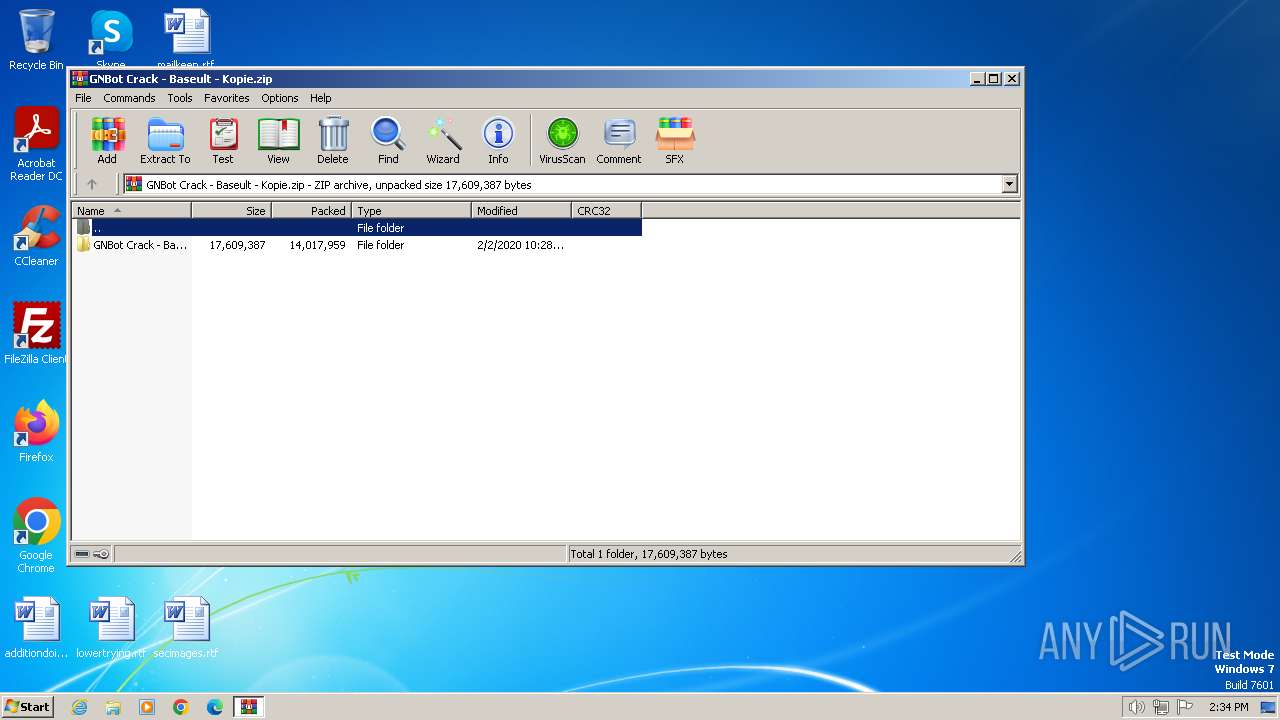
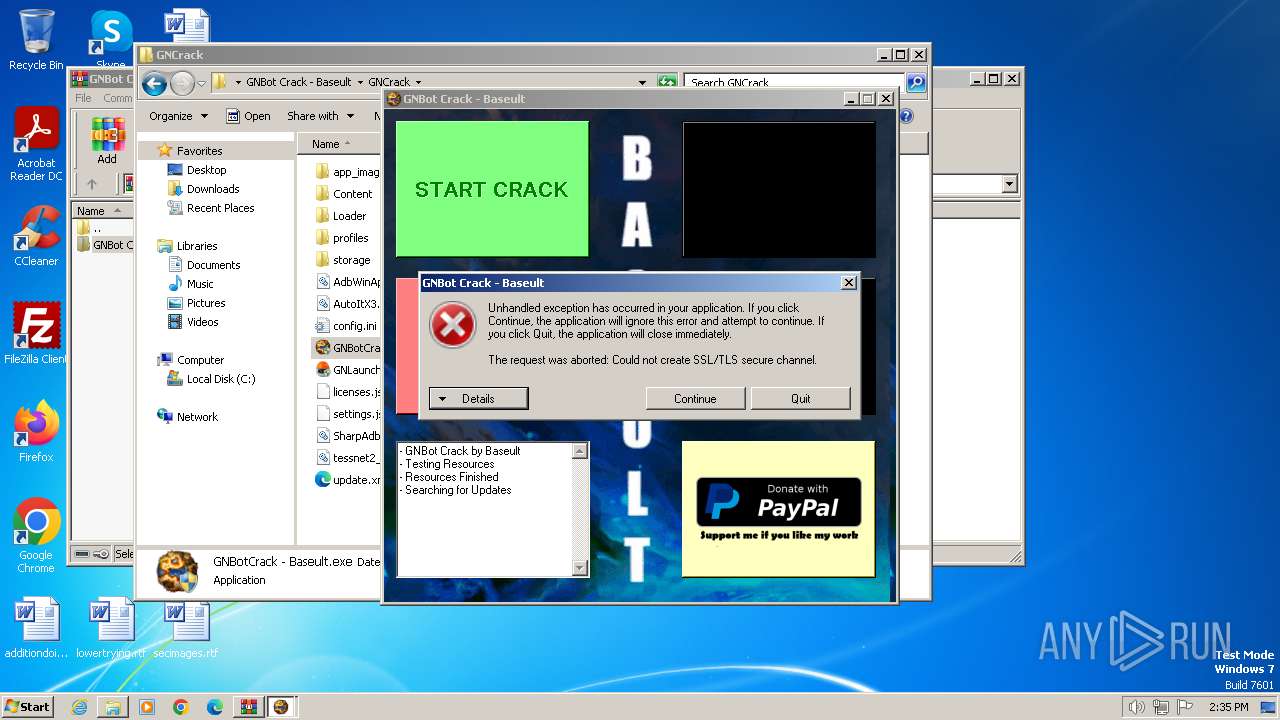
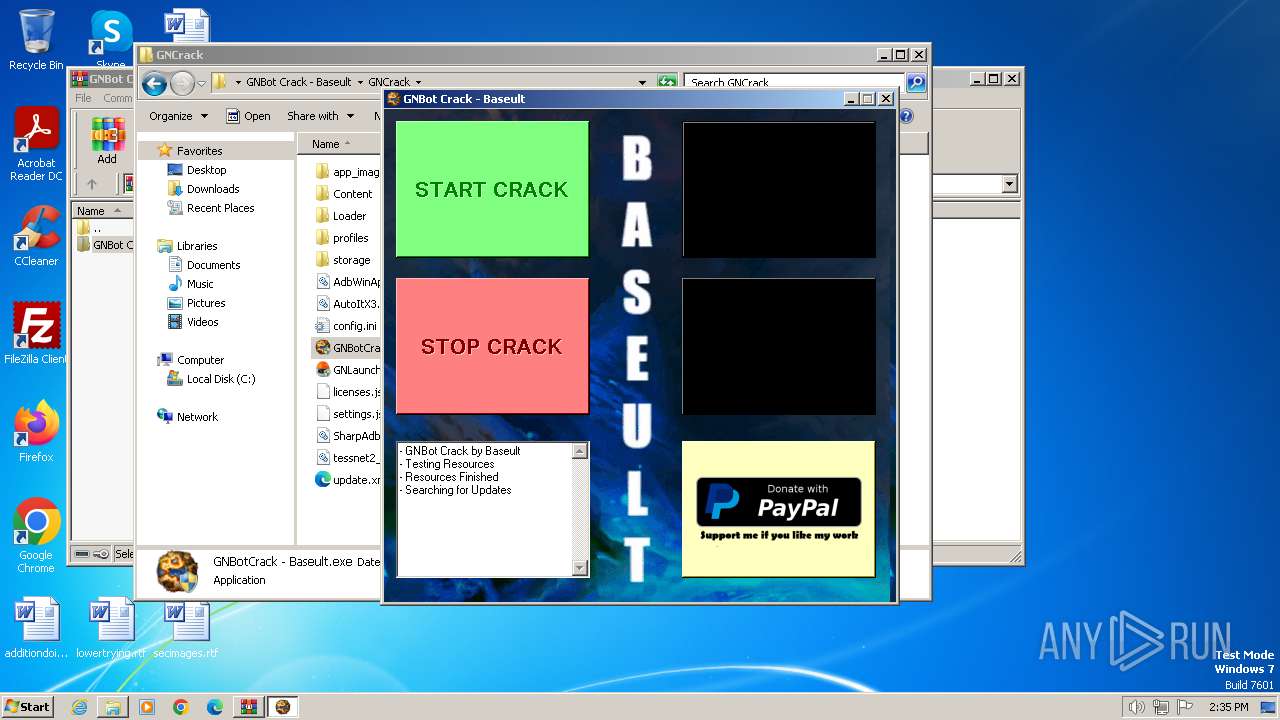
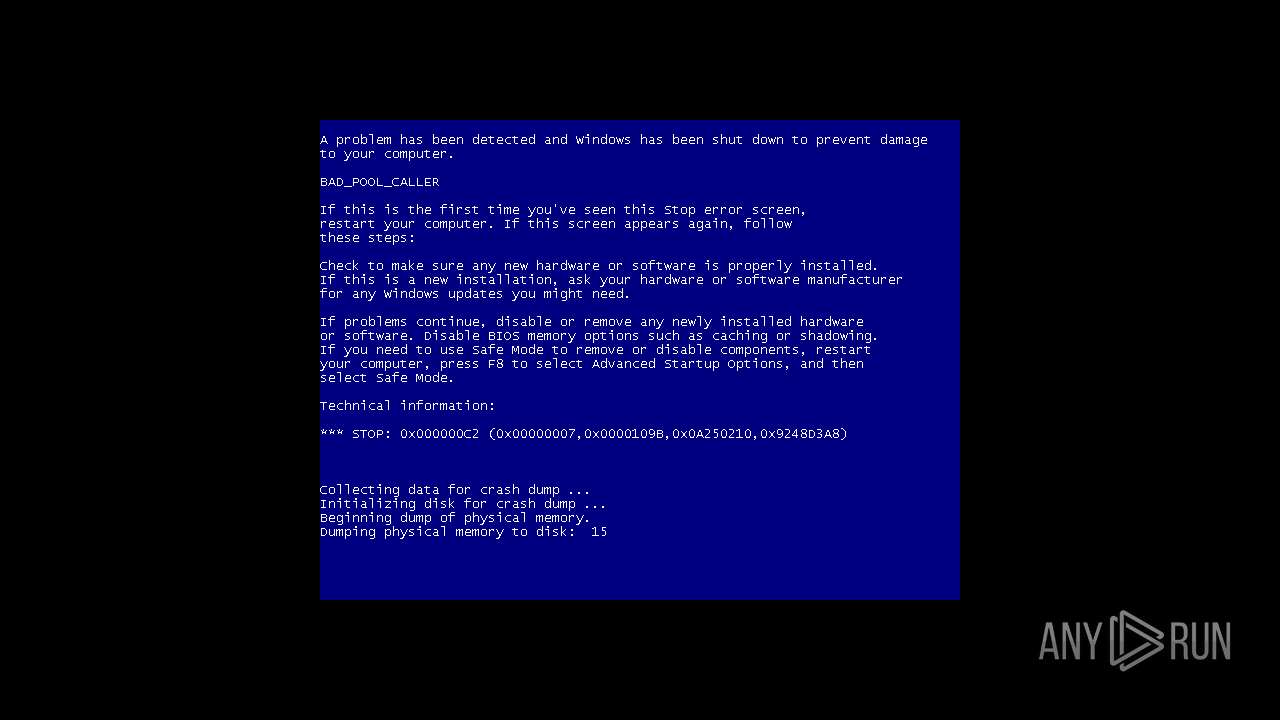
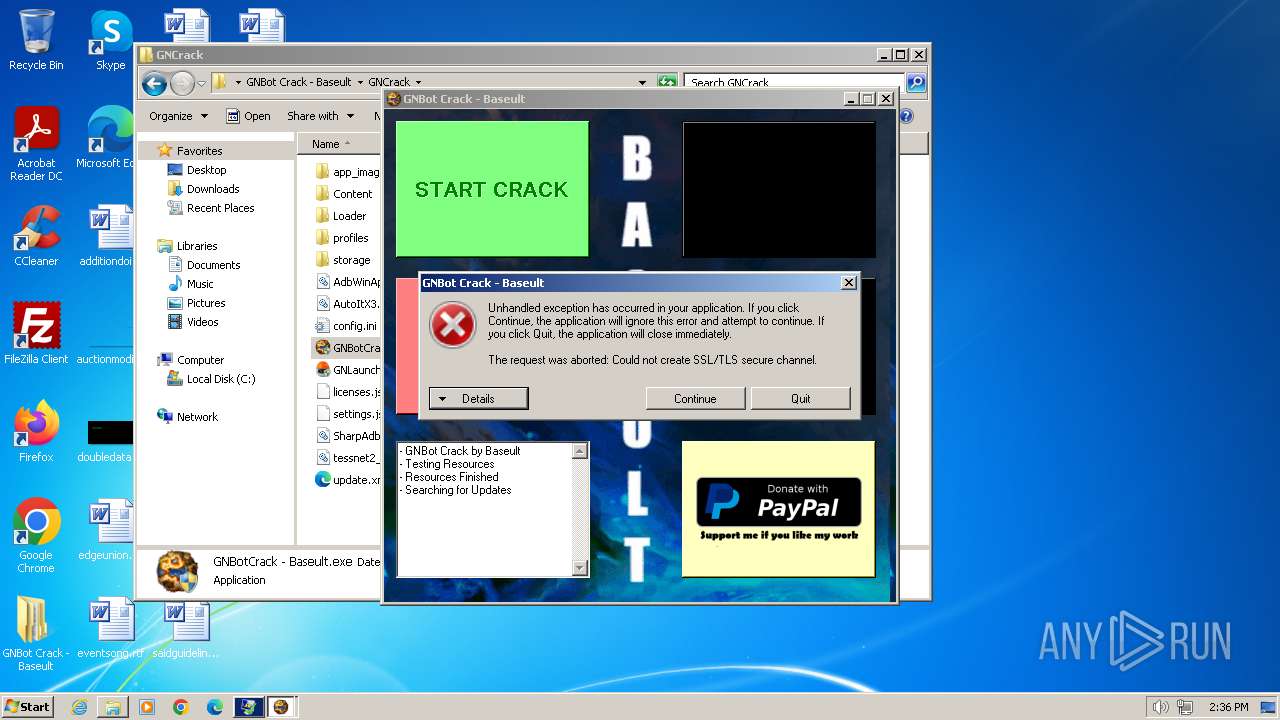
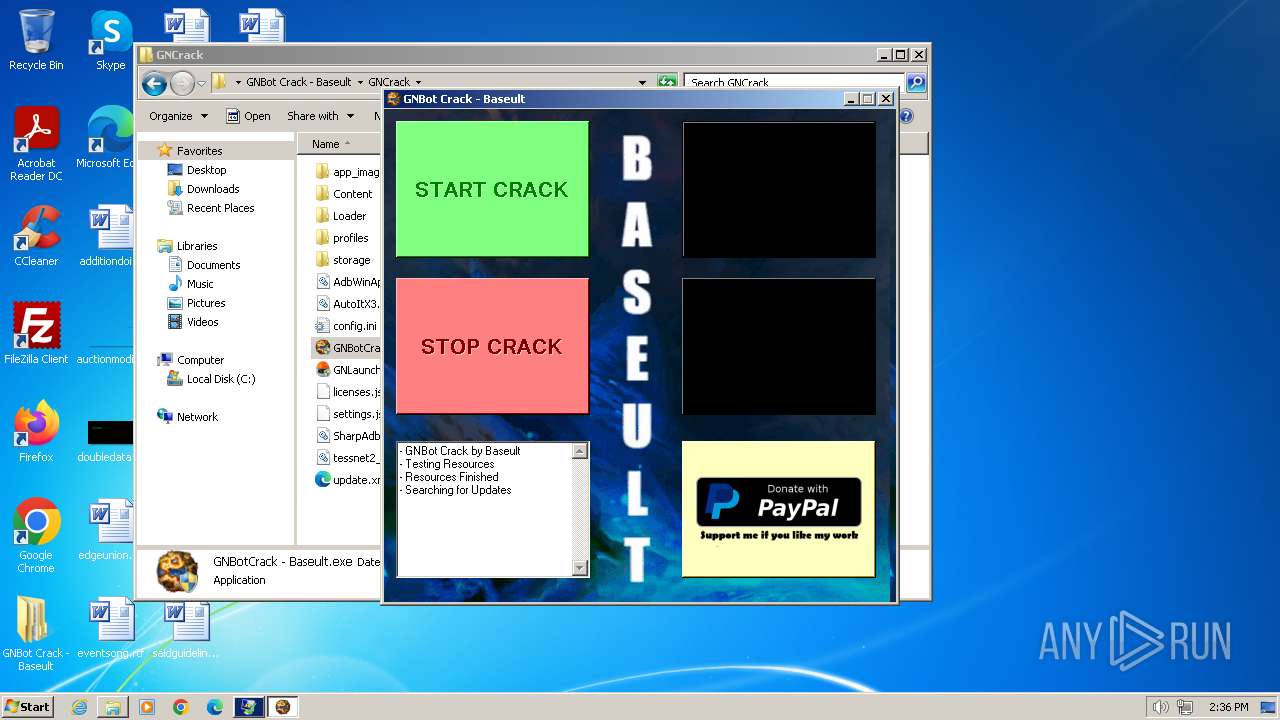
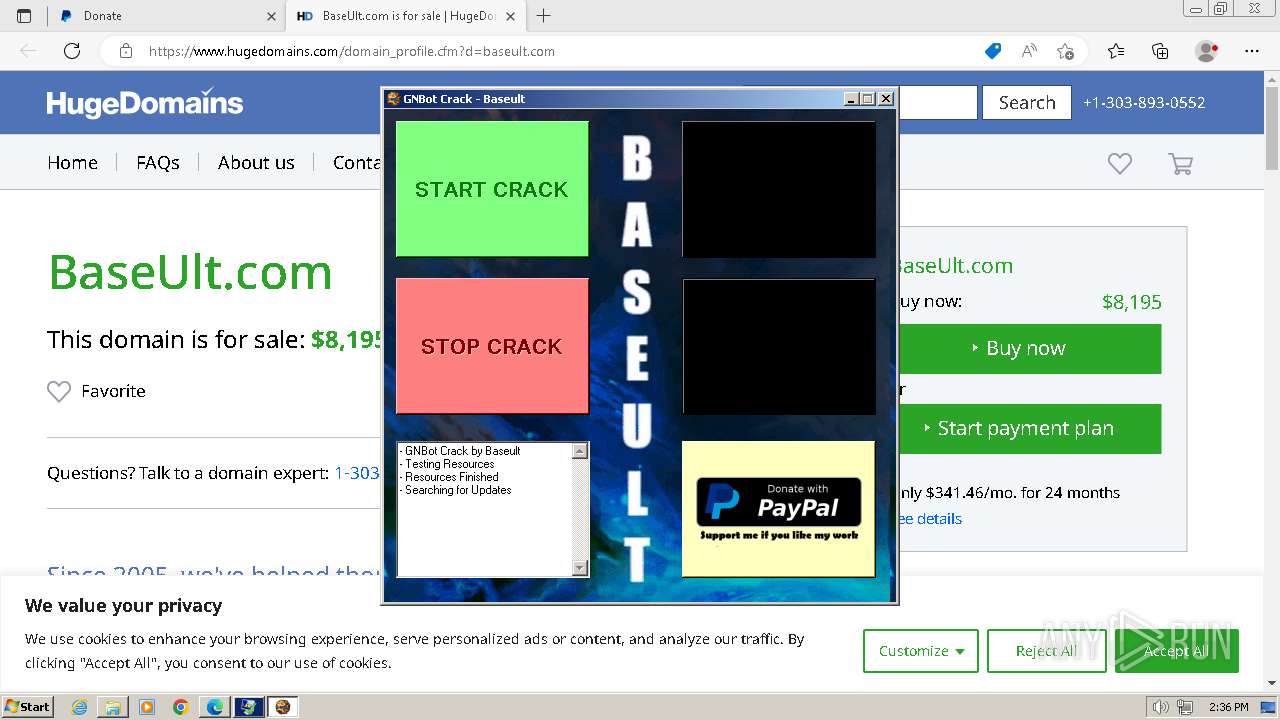
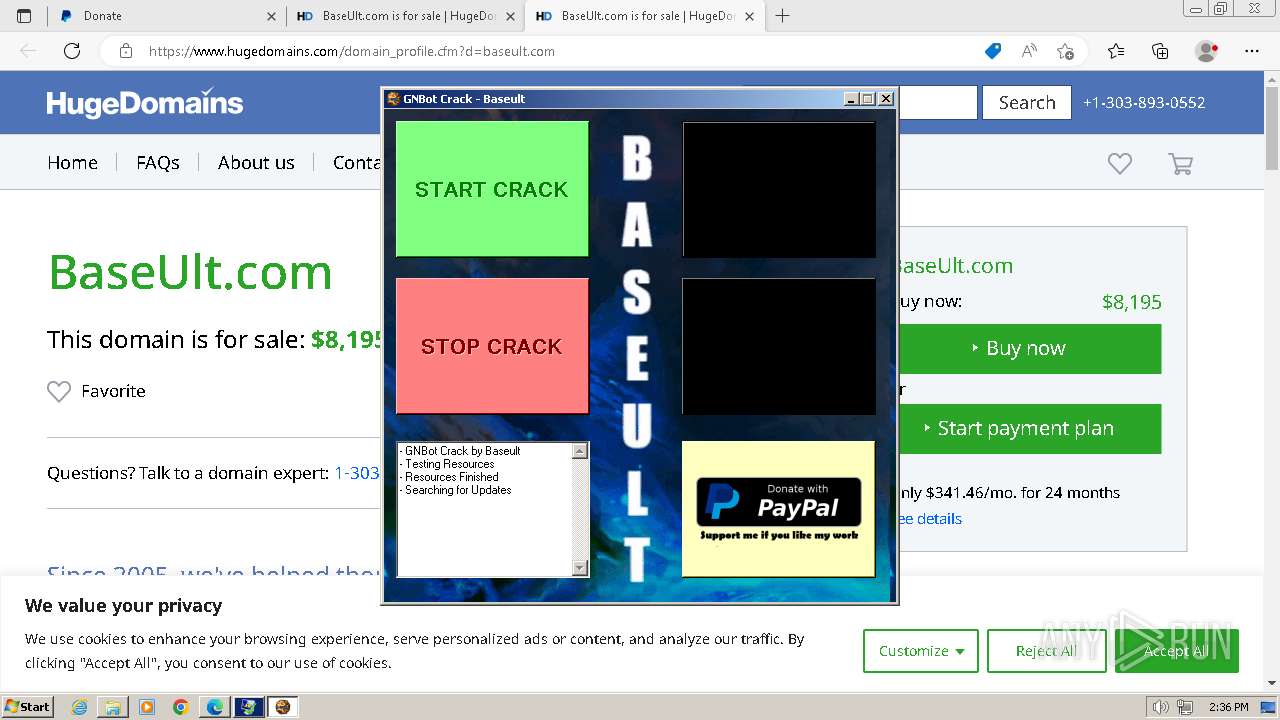
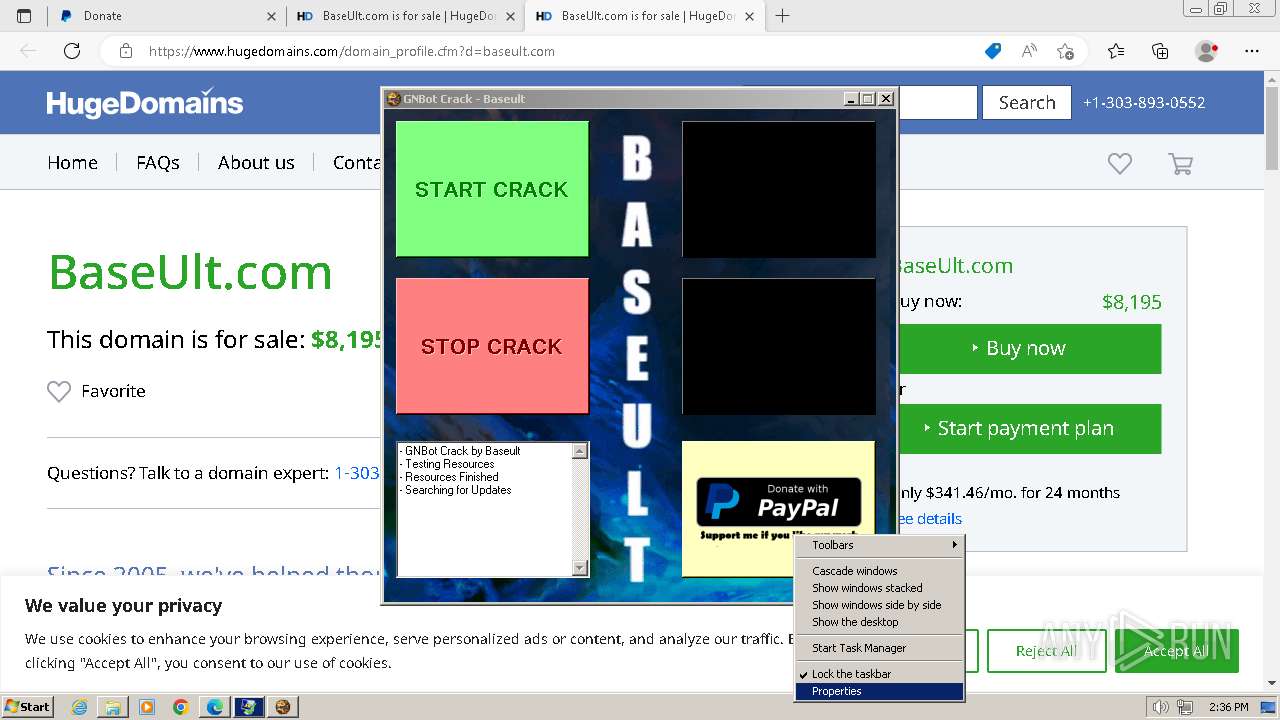
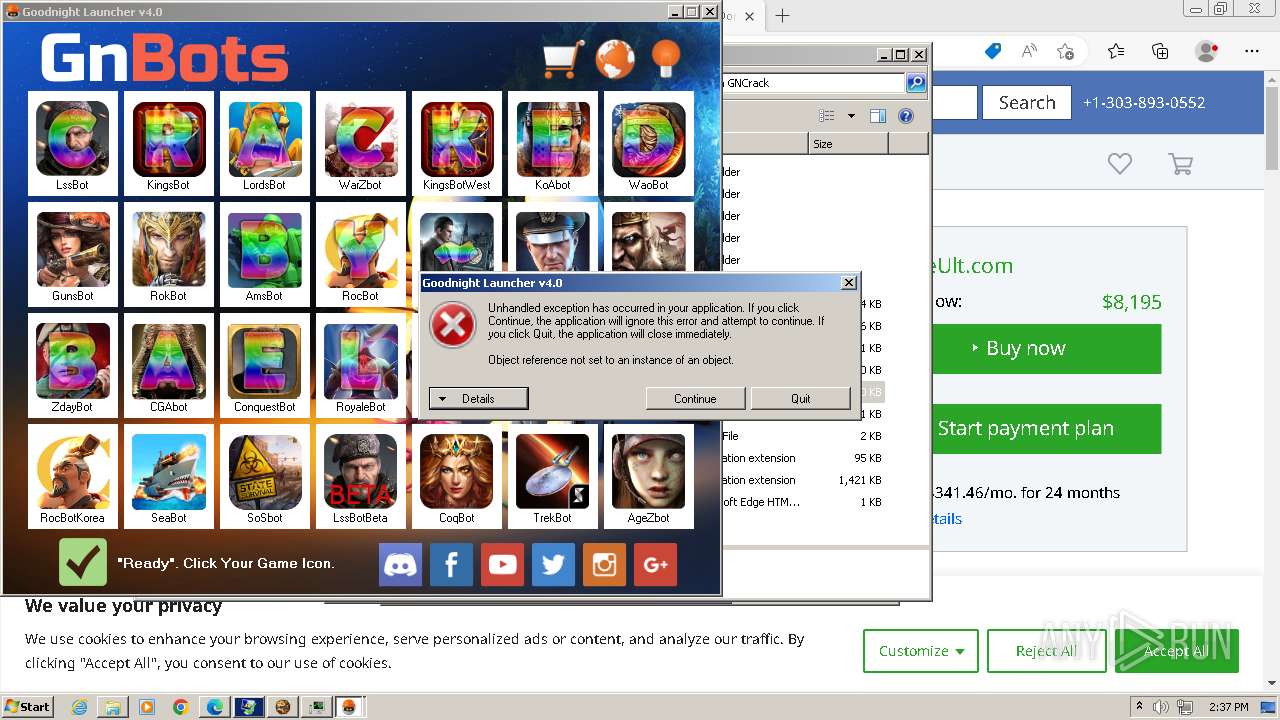
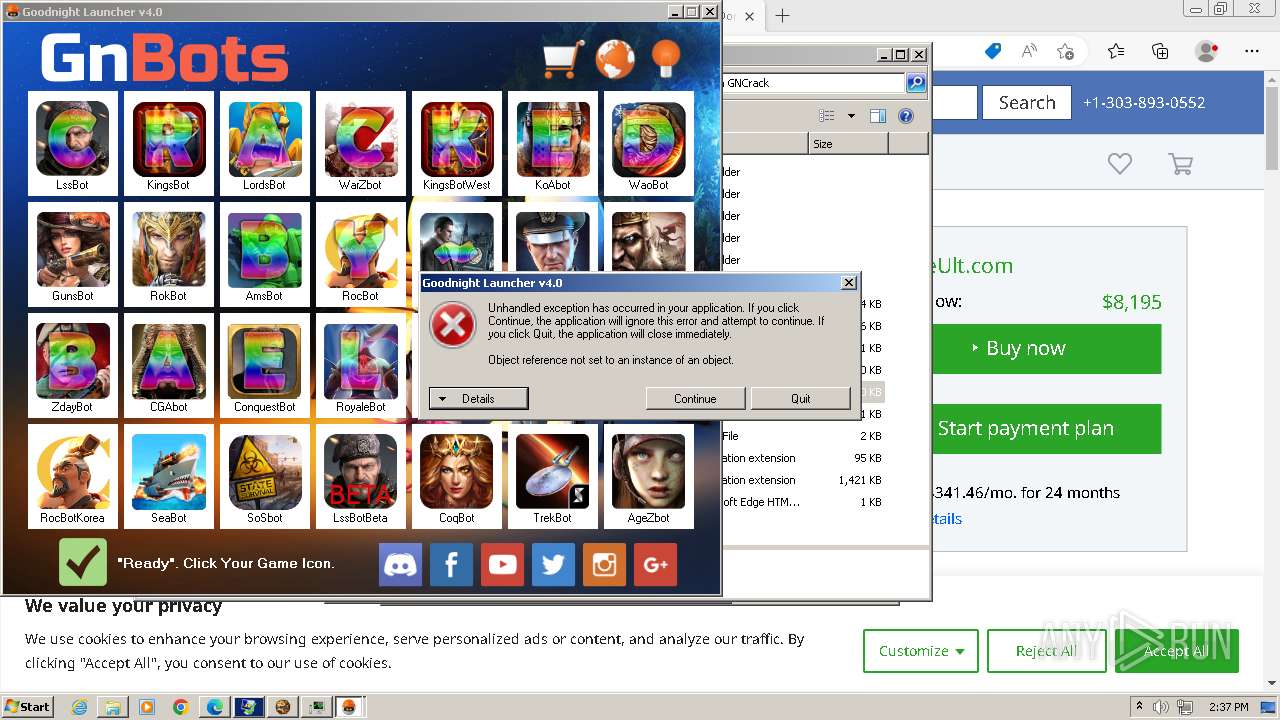
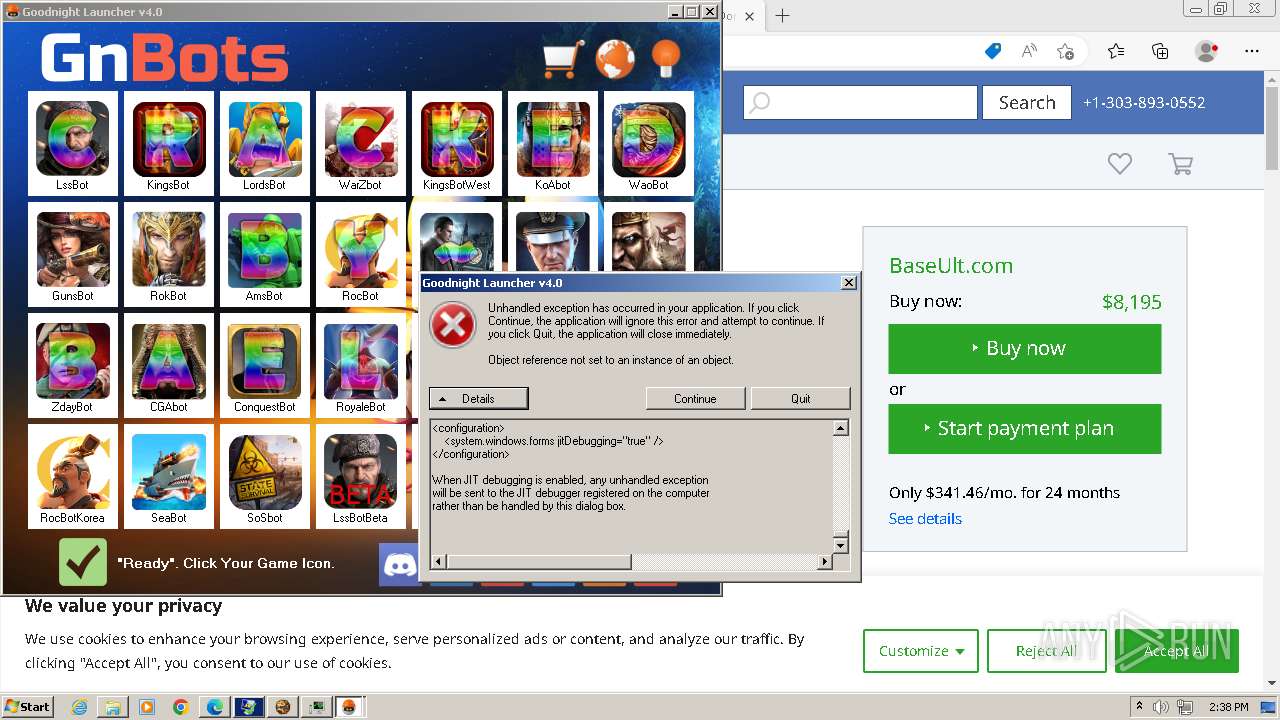
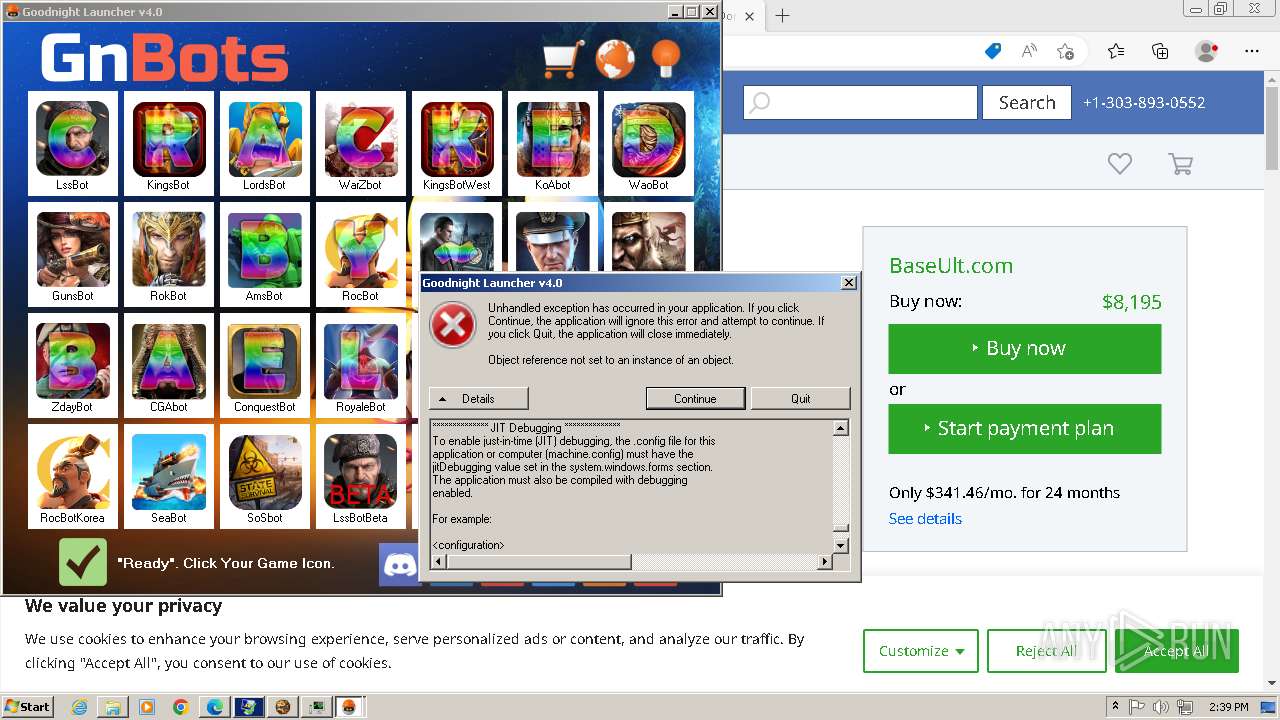
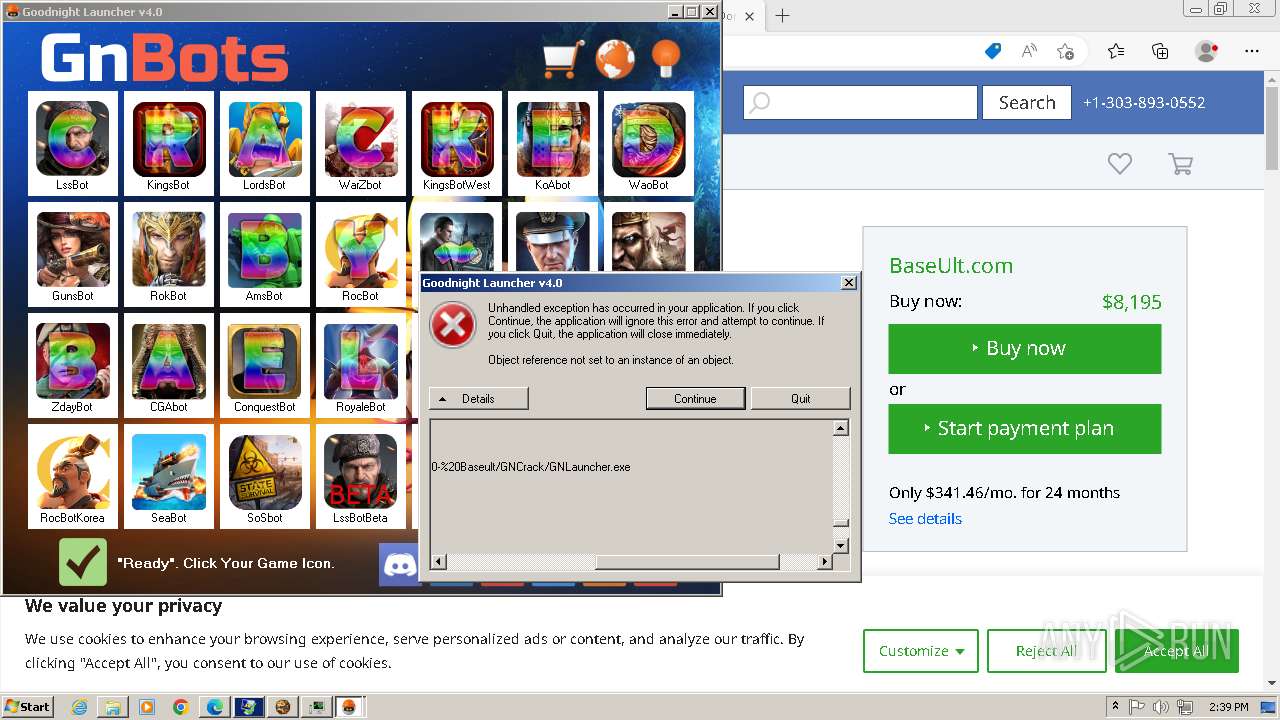
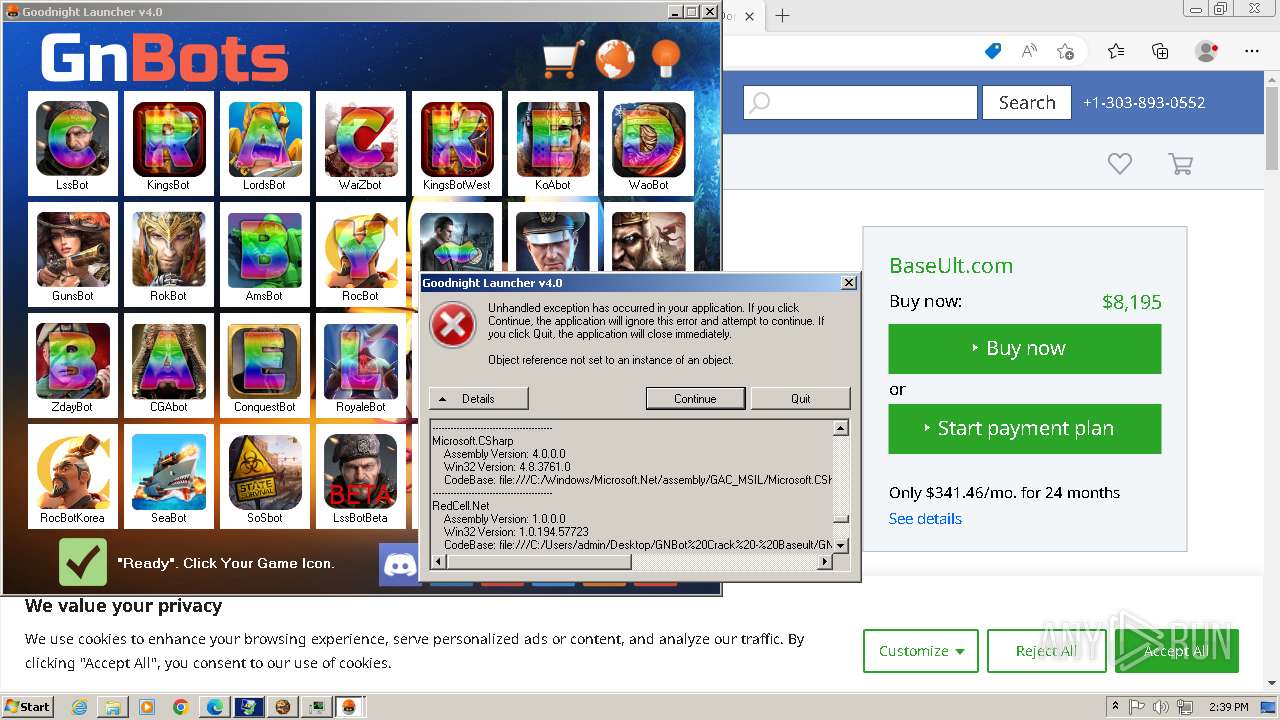
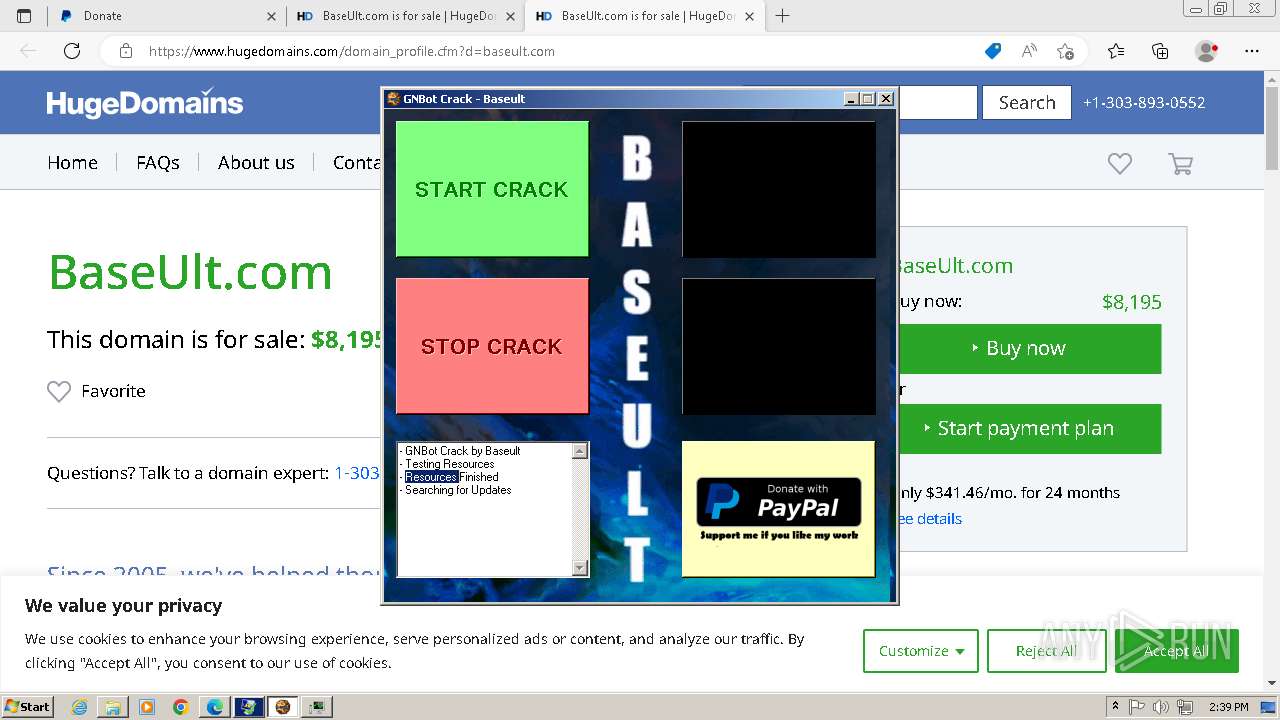
| File name: | GNBot Crack - Baseult - Kopie.zip |
| Full analysis: | https://app.any.run/tasks/530e929b-a4ec-475f-ba50-a9344f8dd71c |
| Verdict: | Malicious activity |
| Analysis date: | March 06, 2024, 14:34:23 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v1.0 to extract, compression method=store |
| MD5: | 32A9BC239201E46EB511799D103961AD |
| SHA1: | F6599CC36BA64C9FE5067E9AD98587682405322E |
| SHA256: | 8AFDC1B6143369A53236873DBFE4234F797BC900054AF1EDB29CFEF984466C53 |
| SSDEEP: | 393216:QixDDJ4zV16PaanzoAAjIa5pWRNtL0b19zkP:VDqzV1Kaahb3Yb194P |
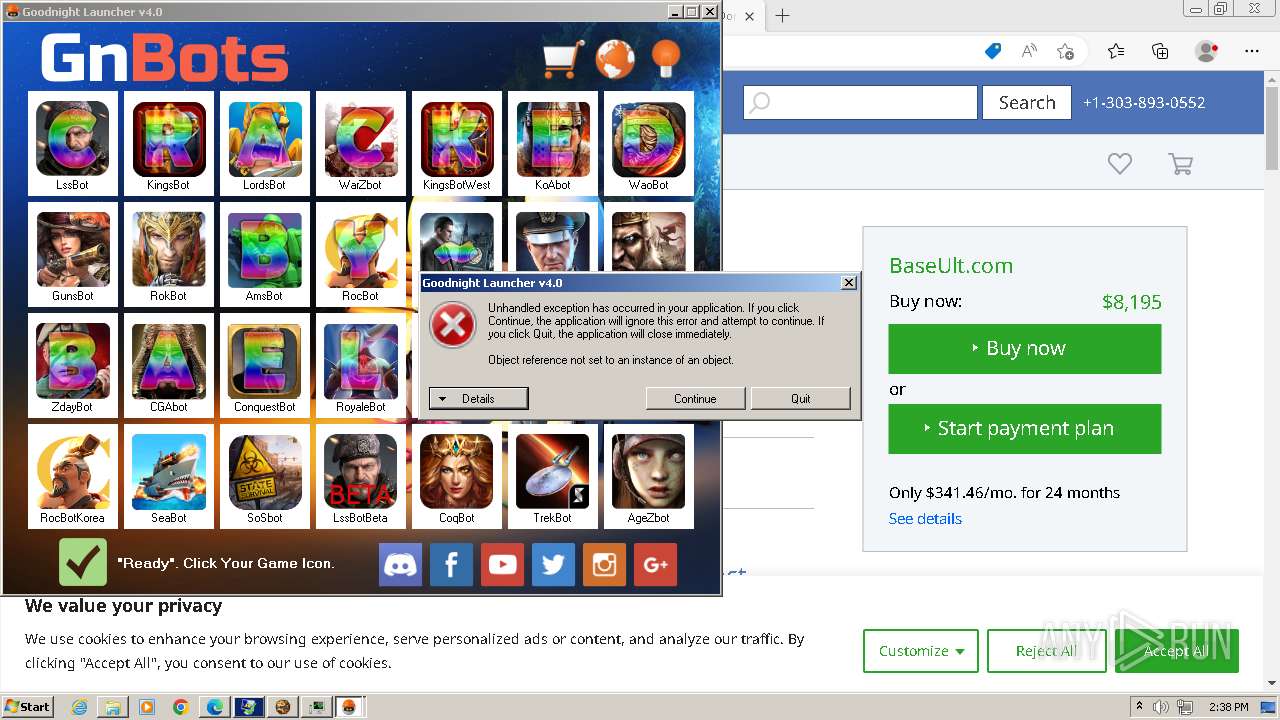
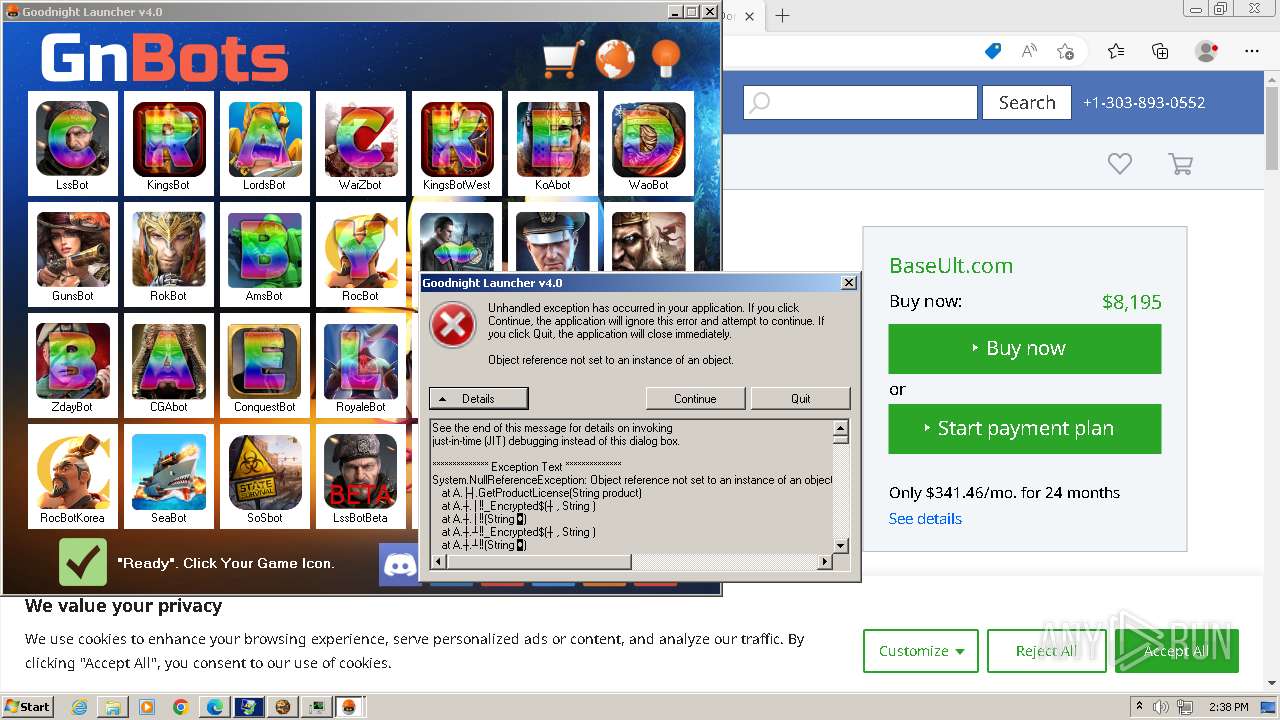
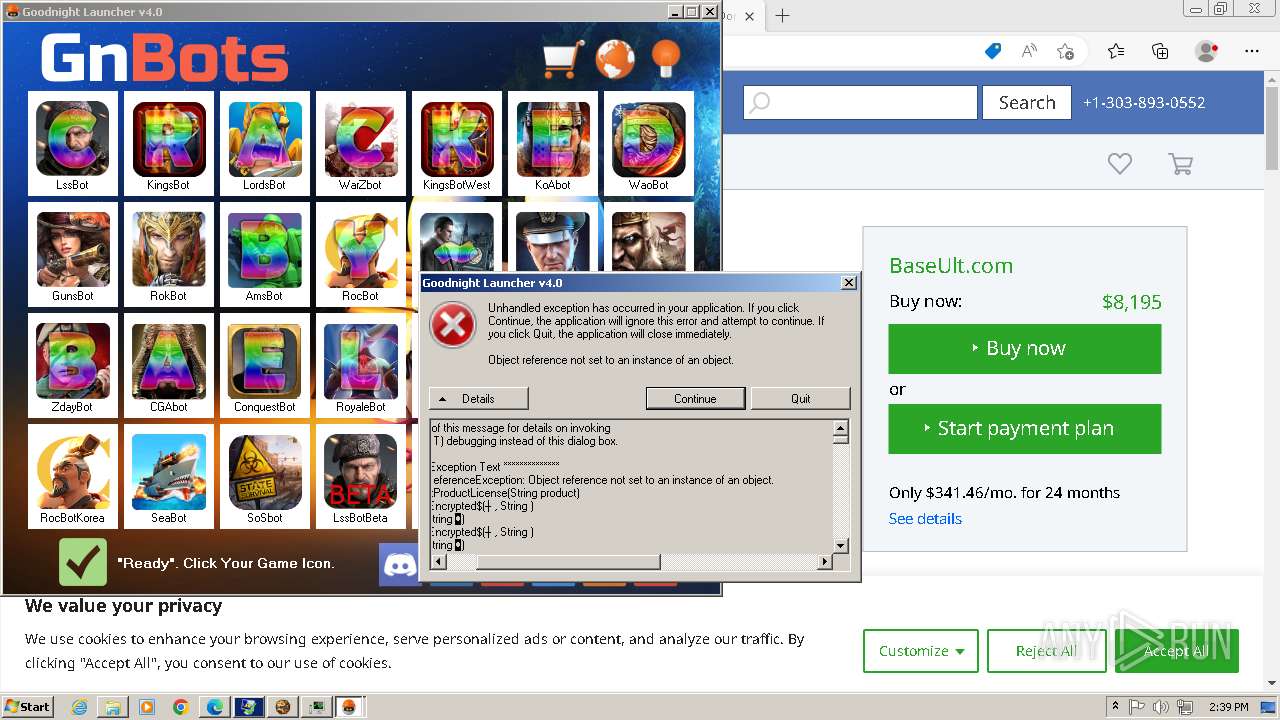
MALICIOUS
Drops the executable file immediately after the start
- WinRAR.exe (PID: 1432)
SUSPICIOUS
Reads the Internet Settings
- GNBotCrack - Baseult.exe (PID: 3276)
- sipnotify.exe (PID: 2040)
- runonce.exe (PID: 1140)
- GNLauncher.exe (PID: 1460)
- GNBotCrack - Baseult.exe (PID: 3020)
The process executes via Task Scheduler
- sipnotify.exe (PID: 2040)
- ctfmon.exe (PID: 284)
Application launched itself
- WerFault.exe (PID: 564)
Reads settings of System Certificates
- sipnotify.exe (PID: 2040)
INFO
Checks supported languages
- GNBotCrack - Baseult.exe (PID: 3276)
- IMEKLMG.EXE (PID: 2132)
- IMEKLMG.EXE (PID: 2144)
- wmpnscfg.exe (PID: 2460)
- GNBotCrack - Baseult.exe (PID: 3020)
- wmpnscfg.exe (PID: 2532)
- GNLauncher.exe (PID: 1460)
- wmpnscfg.exe (PID: 2096)
Reads the computer name
- GNBotCrack - Baseult.exe (PID: 3276)
- IMEKLMG.EXE (PID: 2132)
- IMEKLMG.EXE (PID: 2144)
- wmpnscfg.exe (PID: 2460)
- GNBotCrack - Baseult.exe (PID: 3020)
- wmpnscfg.exe (PID: 2532)
- GNLauncher.exe (PID: 1460)
- wmpnscfg.exe (PID: 2096)
Manual execution by a user
- GNBotCrack - Baseult.exe (PID: 2444)
- GNBotCrack - Baseult.exe (PID: 3276)
- runonce.exe (PID: 1140)
- wmpnscfg.exe (PID: 2532)
- IMEKLMG.EXE (PID: 2144)
- IMEKLMG.EXE (PID: 2132)
- wmpnscfg.exe (PID: 2460)
- GNBotCrack - Baseult.exe (PID: 3020)
- GNBotCrack - Baseult.exe (PID: 2916)
- wmpnscfg.exe (PID: 2096)
- msedge.exe (PID: 3344)
- taskmgr.exe (PID: 3884)
- GNLauncher.exe (PID: 1460)
- GNLauncher.exe (PID: 2212)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 1432)
Reads the machine GUID from the registry
- GNBotCrack - Baseult.exe (PID: 3276)
- GNLauncher.exe (PID: 1460)
- GNBotCrack - Baseult.exe (PID: 3020)
Reads Environment values
- GNBotCrack - Baseult.exe (PID: 3276)
- GNLauncher.exe (PID: 1460)
- GNBotCrack - Baseult.exe (PID: 3020)
Application launched itself
- msedge.exe (PID: 1348)
- msedge.exe (PID: 848)
- msedge.exe (PID: 1828)
- msedge.exe (PID: 3152)
- msedge.exe (PID: 892)
- msedge.exe (PID: 3108)
- msedge.exe (PID: 3344)
Reads security settings of Internet Explorer
- sipnotify.exe (PID: 2040)
- runonce.exe (PID: 1140)
Reads the software policy settings
- sipnotify.exe (PID: 2040)
Reads the time zone
- runonce.exe (PID: 1140)
Create files in a temporary directory
- WerFault.exe (PID: 2052)
Process checks whether UAC notifications are on
- IMEKLMG.EXE (PID: 2132)
- IMEKLMG.EXE (PID: 2144)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 10 |
|---|---|
| ZipBitFlag: | - |
| ZipCompression: | None |
| ZipModifyDate: | 2020:02:02 11:28:08 |
| ZipCRC: | 0x00000000 |
| ZipCompressedSize: | - |
| ZipUncompressedSize: | - |
| ZipFileName: | GNBot Crack - Baseult/ |
Total processes
161
Monitored processes
66
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
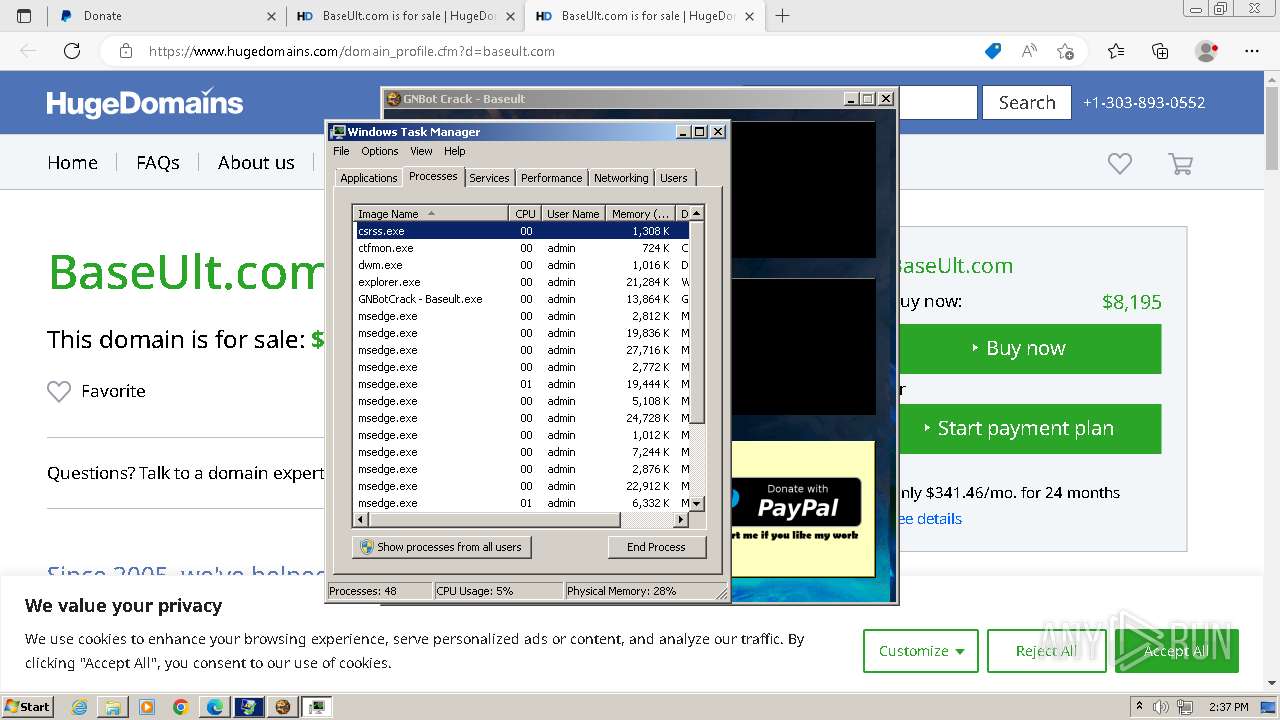
| 284 | C:\Windows\System32\ctfmon.exe | C:\Windows\System32\ctfmon.exe | — | taskeng.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: CTF Loader Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 308 | "C:\Program Files\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=data_decoder.mojom.DataDecoderService --lang=en-US --service-sandbox-type=service --mojo-platform-channel-handle=4052 --field-trial-handle=1264,i,7695952166897864188,7760900752832671003,131072 /prefetch:8 | C:\Program Files\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 109.0.1518.115 Modules
| |||||||||||||||
| 356 | "C:\Program Files\Microsoft\Edge\Application\msedge.exe" --type=crashpad-handler "--user-data-dir=C:\Users\admin\AppData\Local\Microsoft\Edge\User Data" /prefetch:7 --monitor-self-annotation=ptype=crashpad-handler "--database=C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Crashpad" "--metrics-dir=C:\Users\admin\AppData\Local\Microsoft\Edge\User Data" --annotation=IsOfficialBuild=1 --annotation=channel= --annotation=chromium-version=109.0.5414.149 "--annotation=exe=C:\Program Files\Microsoft\Edge\Application\msedge.exe" --annotation=plat=Win32 "--annotation=prod=Microsoft Edge" --annotation=ver=109.0.1518.115 --initial-client-data=0x138,0x13c,0x140,0x10c,0x148,0x681df598,0x681df5a8,0x681df5b4 | C:\Program Files\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Microsoft Edge Exit code: 0 Version: 109.0.1518.115 | |||||||||||||||
| 564 | "C:\Windows\System32\WerFault.exe" -k -rq | C:\Windows\System32\WerFault.exe | — | runonce.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Problem Reporting Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 568 | "C:\Program Files\Microsoft\Edge\Application\msedge.exe" --type=gpu-process --gpu-preferences=UAAAAAAAAADgAAAYAAAAAAAAAAAAAAAAAABgAAAAAAAwAAAAAAAAAAAAAAAQAAAAAAAAAAAAAAAAAAAAAAAAAEgAAAAAAAAASAAAAAAAAAAYAAAAAgAAABAAAAAAAAAAGAAAAAAAAAAQAAAAAAAAAAAAAAAOAAAAEAAAAAAAAAABAAAADgAAAAgAAAAAAAAACAAAAAAAAAA= --mojo-platform-channel-handle=1240 --field-trial-handle=1372,i,18314594967817289339,15858270348292758897,131072 /prefetch:2 | C:\Program Files\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 109.0.1518.115 Modules
| |||||||||||||||
| 848 | "C:\Program Files\Microsoft\Edge\Application\msedge.exe" --single-argument http://baseult.com/new/red.php | C:\Program Files\Microsoft\Edge\Application\msedge.exe | — | GNBotCrack - Baseult.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Microsoft Edge Exit code: 0 Version: 109.0.1518.115 Modules
| |||||||||||||||
| 892 | "C:\Program Files\Microsoft\Edge\Application\msedge.exe" --single-argument http://baseult.com/ | C:\Program Files\Microsoft\Edge\Application\msedge.exe | — | GNBotCrack - Baseult.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Microsoft Edge Exit code: 0 Version: 109.0.1518.115 Modules
| |||||||||||||||
| 944 | "C:\Program Files\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=data_decoder.mojom.DataDecoderService --lang=en-US --service-sandbox-type=service --mojo-platform-channel-handle=4052 --field-trial-handle=1264,i,7695952166897864188,7760900752832671003,131072 /prefetch:8 | C:\Program Files\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 109.0.1518.115 Modules
| |||||||||||||||
| 1140 | runonce.exe /Explorer | C:\Windows\System32\runonce.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Run Once Wrapper Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1208 | "C:\Program Files\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=asset_store.mojom.AssetStoreService --lang=en-US --service-sandbox-type=asset_store_service --mojo-platform-channel-handle=3820 --field-trial-handle=1264,i,7695952166897864188,7760900752832671003,131072 /prefetch:8 | C:\Program Files\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 109.0.1518.115 Modules
| |||||||||||||||
Total events
22 890
Read events
22 694
Write events
171
Delete events
25
Modification events
| (PID) Process: | (1432) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (1432) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (1432) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\182\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (1432) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\phacker.zip | |||
| (PID) Process: | (1432) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\Win7-KB3191566-x86.zip | |||
| (PID) Process: | (1432) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\curl-8.5.0_1-win32-mingw.zip | |||
| (PID) Process: | (1432) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\GNBot Crack - Baseult - Kopie.zip | |||
| (PID) Process: | (1432) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (1432) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (1432) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
Executable files
8
Suspicious files
102
Text files
122
Unknown types
56
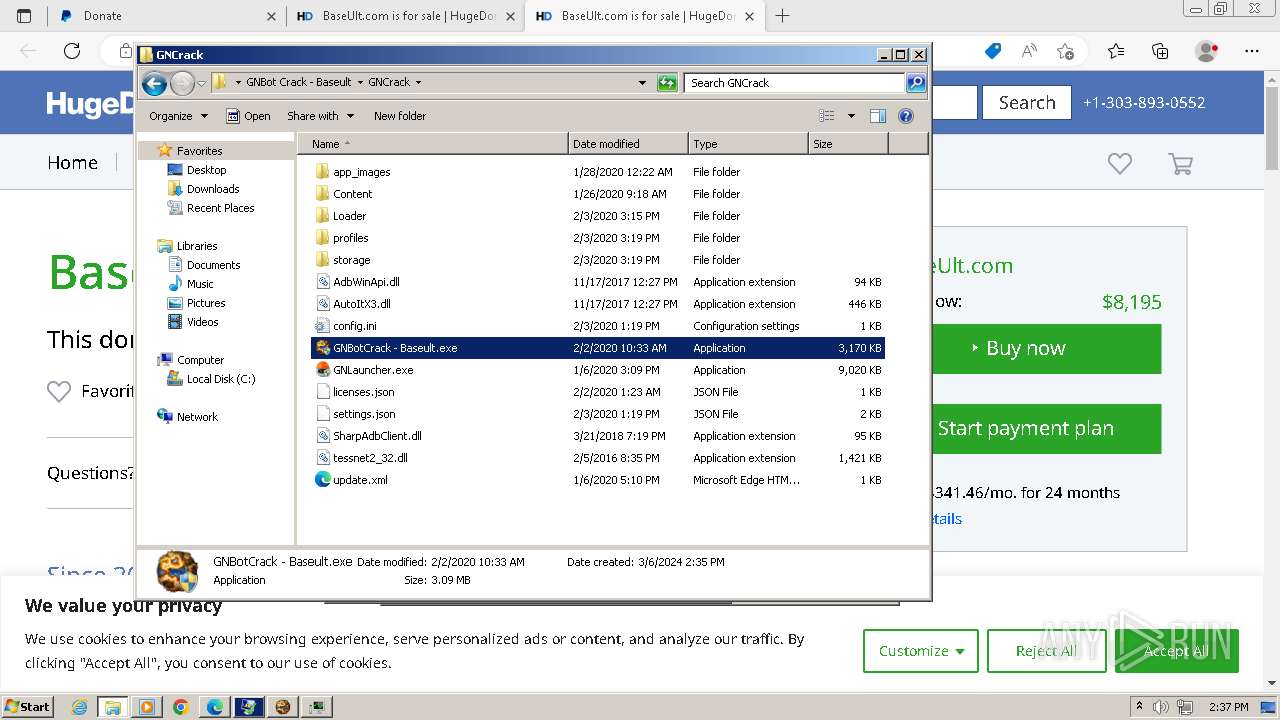
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 1432 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa1432.18155\GNBot Crack - Baseult\GNCrack\app_images\CGAbot.png | image | |
MD5:4509BD49050E9BBDE60CD8920AADF740 | SHA256:11488D987634829FA2C79C9FB24C378092F248159AC3FACB824A2AC6062A684C | |||
| 1432 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa1432.18155\GNBot Crack - Baseult\GNCrack\app_images\ConquestBot.png | image | |
MD5:A2F15088444A857BB7EEA07C93F412C5 | SHA256:4669A0C0A01938963F77C901DCBFBB21DD052FAE14E091588B705A2F5F99670A | |||
| 1432 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa1432.18155\GNBot Crack - Baseult\GNCrack\app_images\DunesBot.png | image | |
MD5:D05F1CFA89449D42D88E73C961ABE034 | SHA256:FC1D3FA2935A6CFC76F2FA9B4008394F30058DB6D156603EF8DCB1BD82EA4895 | |||
| 1432 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa1432.18155\GNBot Crack - Baseult\GNCrack\app_images\BWbot.png | image | |
MD5:8284379E400B9F7E159CFD22C040C79B | SHA256:95308A909F3B46540606FC5E96B9123E53C5DF8BEBF0B6E1D23AE75D4F9D2F9E | |||
| 1432 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa1432.18155\GNBot Crack - Baseult\GNCrack\app_images\GunsBot.png | image | |
MD5:54222EA8E62DD97F506636F54587721D | SHA256:DA9B6B46E302ACD3F9698E8CF0393928F92FF0CDD742E6FFD5EB741CFC3F4D87 | |||
| 1432 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa1432.18155\GNBot Crack - Baseult\GNCrack\app_images\KoAbot.png | image | |
MD5:C1085A3EB34FEAA420369524B9610E89 | SHA256:BB1E60DB32E0892A050B08319045C6E942CCBFBB7936C5AB317C3832668DEFCE | |||
| 1432 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa1432.18155\GNBot Crack - Baseult\GNCrack\app_images\LordsBot.png | image | |
MD5:228FC194C12C26DC5EDF965CA7497591 | SHA256:F3E92AF376A52C9F106B2E88ECF939405EFDD3408B52EE0899A67EDCBF2D57C5 | |||
| 1432 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa1432.18155\GNBot Crack - Baseult\GNCrack\app_images\KingsBotWest.png | image | |
MD5:B83E04674157A6191571C1314430D401 | SHA256:3E3C89DAEAB95EB88F20ED20A9D6CCBB9DF019B7ACD1CDC0166D029B0D299F90 | |||
| 1432 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa1432.18155\GNBot Crack - Baseult\GNCrack\app_images\MafiaBot.png | image | |
MD5:002E9EDC42015EB7DAD3263D835F0F7A | SHA256:F54E5ED84AC18702EBB47915C5A13ADF0CA6173278DA5284FD8C2FB193BC4BB6 | |||
| 1432 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa1432.18155\GNBot Crack - Baseult\GNCrack\app_images\KingsBot.png | image | |
MD5:1DCBE140A2BA20A6CC3C2D4048746A26 | SHA256:173EF014D0245ED281CD6188CBF336FD1119B7FB3CA21EC0E854ED3D98CE550C | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
17
TCP/UDP connections
116
DNS requests
115
Threats
7
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
3276 | GNBotCrack - Baseult.exe | GET | 302 | 54.209.32.212:80 | http://baseult.com/updates/version.txt | unknown | — | — | unknown |
2040 | sipnotify.exe | HEAD | 200 | 23.197.138.118:80 | http://query.prod.cms.rt.microsoft.com/cms/api/am/binary/RE2JgkA?v=133542093509060000 | unknown | — | — | unknown |
3552 | msedge.exe | GET | 302 | 54.209.32.212:80 | http://baseult.com/ | unknown | — | — | unknown |
3552 | msedge.exe | GET | — | 54.209.32.212:80 | http://baseult.com/new/red.php | unknown | — | — | unknown |
3552 | msedge.exe | GET | 302 | 54.209.32.212:80 | http://baseult.com/new/red.php | unknown | — | — | unknown |
1460 | GNLauncher.exe | POST | 200 | 92.205.10.59:80 | http://www.goodnightbot.net/gn/services/settings.php?seid=mkc | unknown | text | 172 b | unknown |
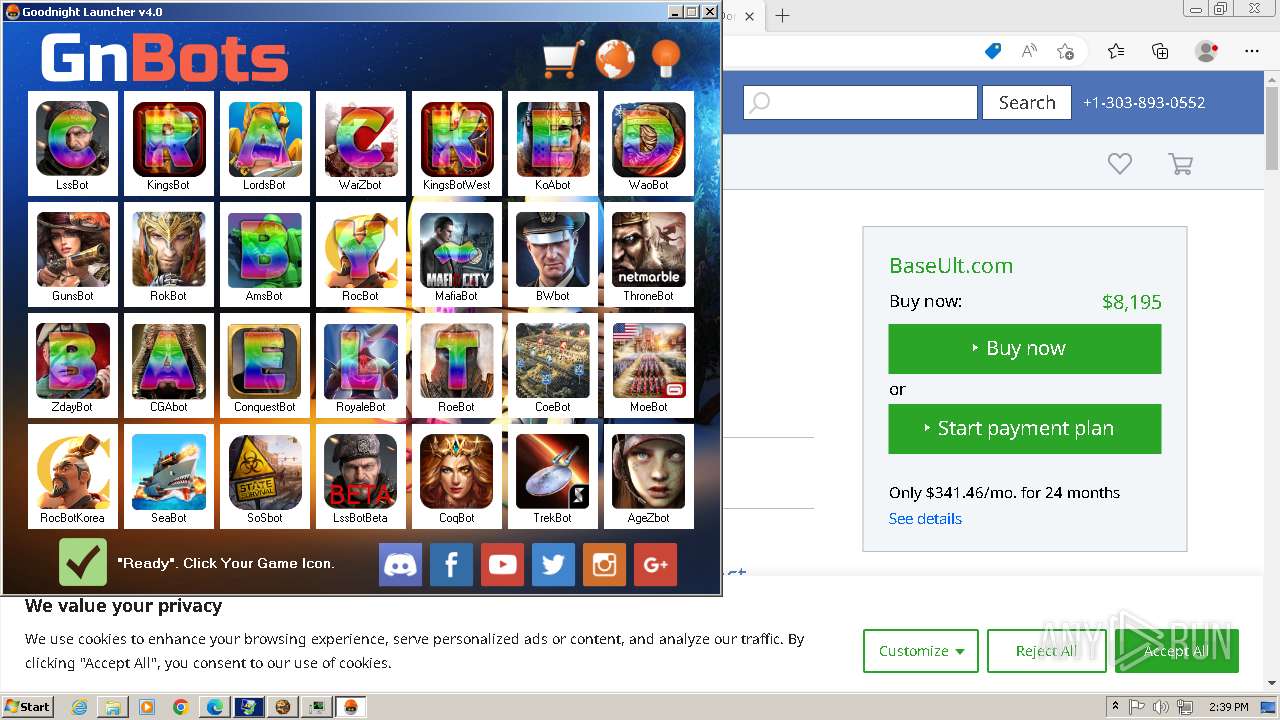
1460 | GNLauncher.exe | GET | 200 | 92.205.10.59:80 | http://goodnightbot.net/gn/gnbot/db/m/images/LssBotBeta.png | unknown | image | 45.1 Kb | unknown |
1460 | GNLauncher.exe | GET | 200 | 92.205.10.59:80 | http://goodnightbot.net/gn/gnbot/db/m/images/CoqBot.png | unknown | image | 38.9 Kb | unknown |
1460 | GNLauncher.exe | GET | 200 | 92.205.10.59:80 | http://goodnightbot.net/gn/gnbot/db/m/images/TrekBot.png | unknown | image | 29.5 Kb | unknown |
1460 | GNLauncher.exe | POST | 200 | 92.205.10.59:80 | http://www.goodnightbot.net/gn/services/settings.php?seid=config | unknown | text | 1.96 Kb | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | unknown |
— | — | 224.0.0.252:5355 | — | — | — | unknown |
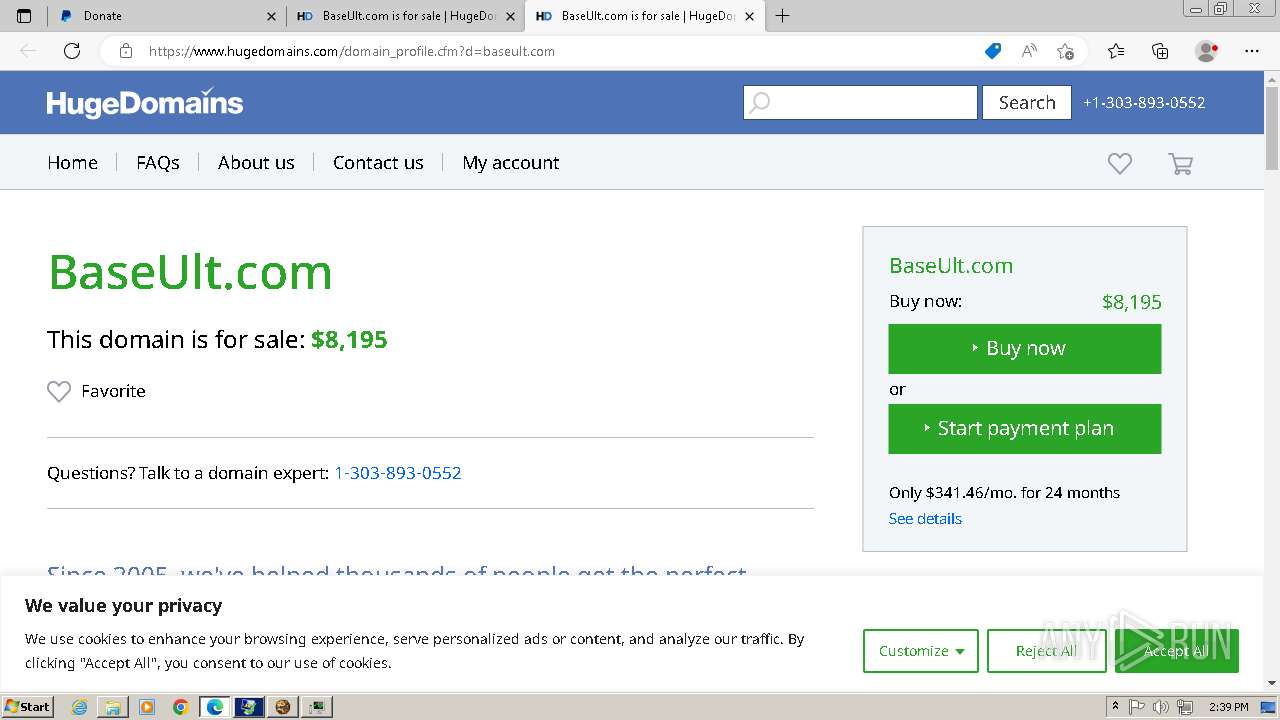
3276 | GNBotCrack - Baseult.exe | 54.209.32.212:80 | baseult.com | AMAZON-AES | US | unknown |
3276 | GNBotCrack - Baseult.exe | 172.67.70.191:443 | www.hugedomains.com | CLOUDFLARENET | US | unknown |
1108 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |
2040 | sipnotify.exe | 23.197.138.118:80 | query.prod.cms.rt.microsoft.com | Akamai International B.V. | US | unknown |
3020 | GNBotCrack - Baseult.exe | 52.71.57.184:80 | baseult.com | AMAZON-AES | US | unknown |
3020 | GNBotCrack - Baseult.exe | 104.26.7.37:443 | www.hugedomains.com | CLOUDFLARENET | US | shared |
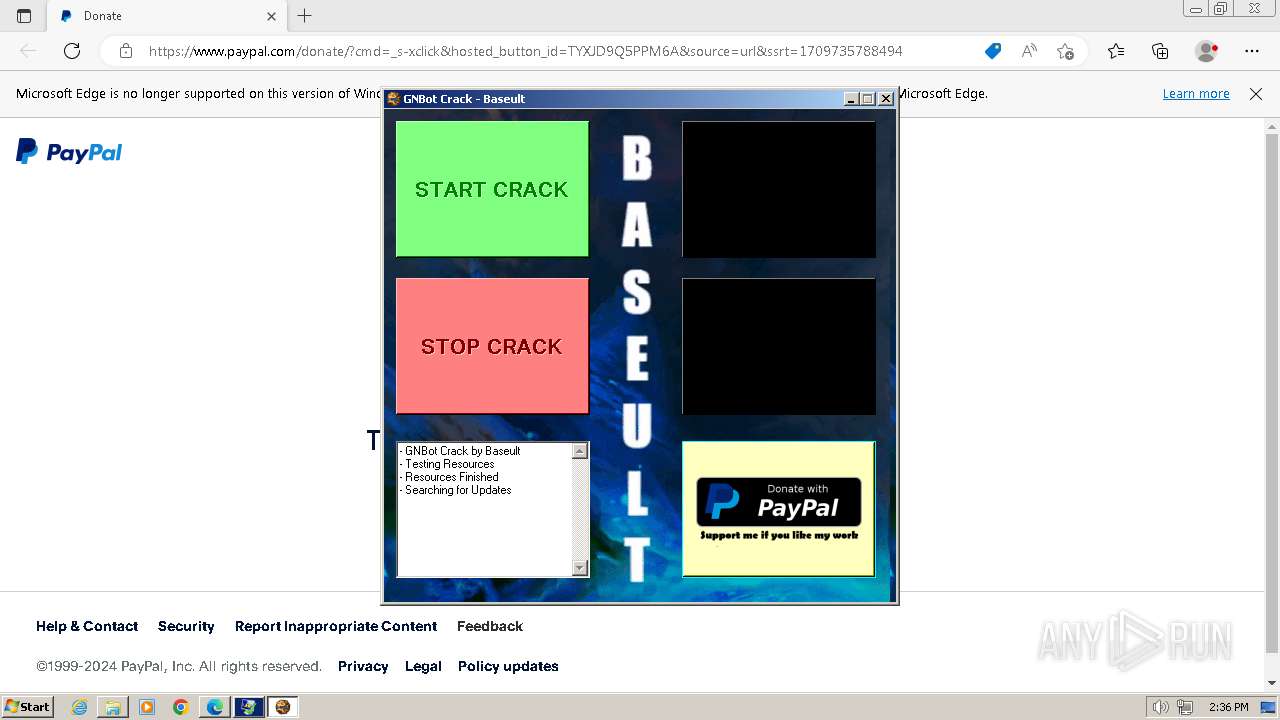
3552 | msedge.exe | 151.101.1.21:80 | www.paypal.com | FASTLY | US | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
baseult.com |
| unknown |
www.hugedomains.com |
| whitelisted |
query.prod.cms.rt.microsoft.com |
| whitelisted |
www.paypal.com |
| whitelisted |
config.edge.skype.com |
| whitelisted |
edge.microsoft.com |
| whitelisted |
www.paypalobjects.com |
| whitelisted |
t.paypal.com |
| whitelisted |
www.bing.com |
| whitelisted |
zn1ynnliufrct75cb-paypalxm.siteintercept.qualtrics.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
3552 | msedge.exe | Not Suspicious Traffic | INFO [ANY.RUN] A free CDN for open source projects (jsdelivr .net) |
1460 | GNLauncher.exe | Potential Corporate Privacy Violation | AV POLICY Empty HTTP Authentication Header |
1460 | GNLauncher.exe | Potential Corporate Privacy Violation | AV POLICY Empty HTTP Authentication Header |
1460 | GNLauncher.exe | Potential Corporate Privacy Violation | AV POLICY Empty HTTP Authentication Header |
3552 | msedge.exe | Not Suspicious Traffic | INFO [ANY.RUN] Cloudflare Network Error Logging (NEL) |
2 ETPRO signatures available at the full report