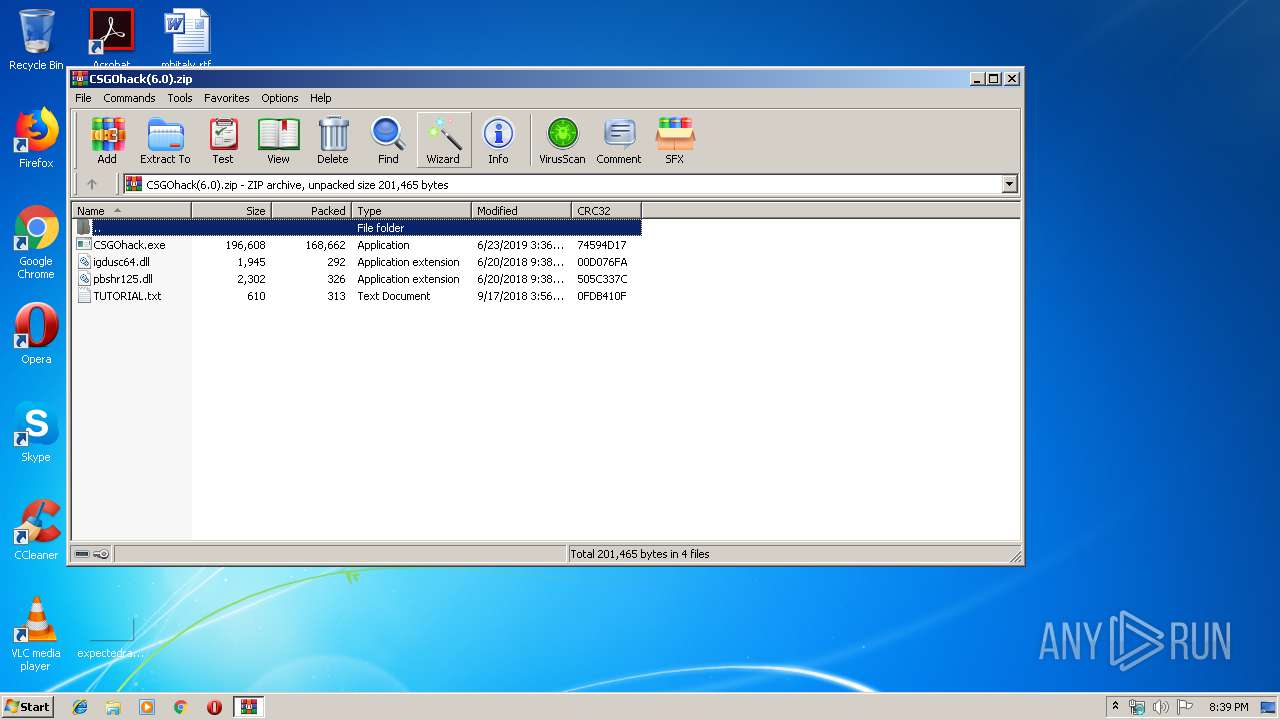
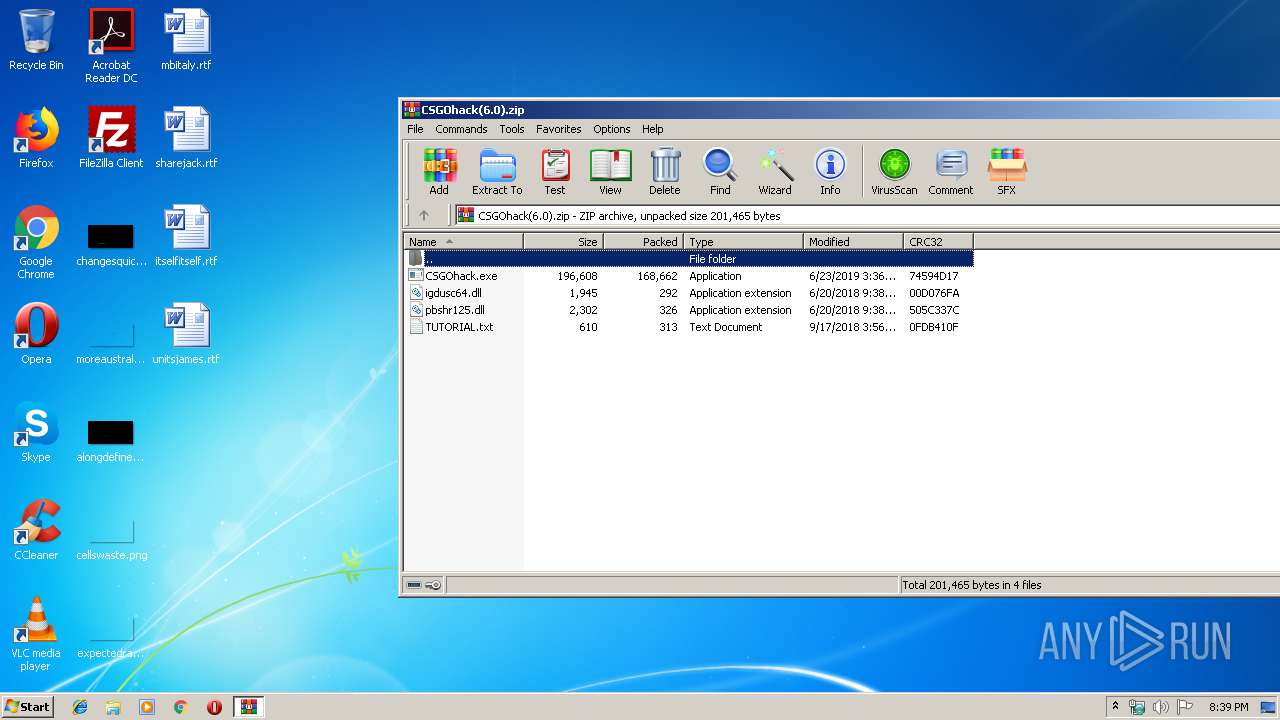
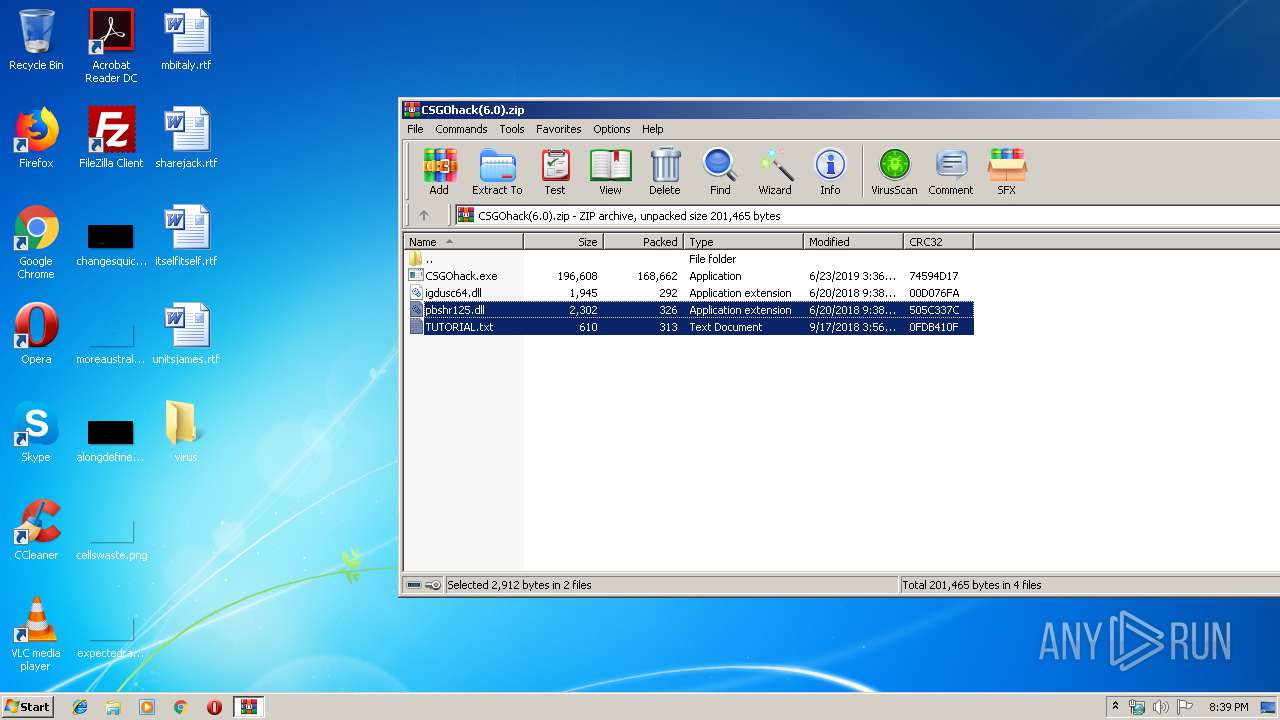
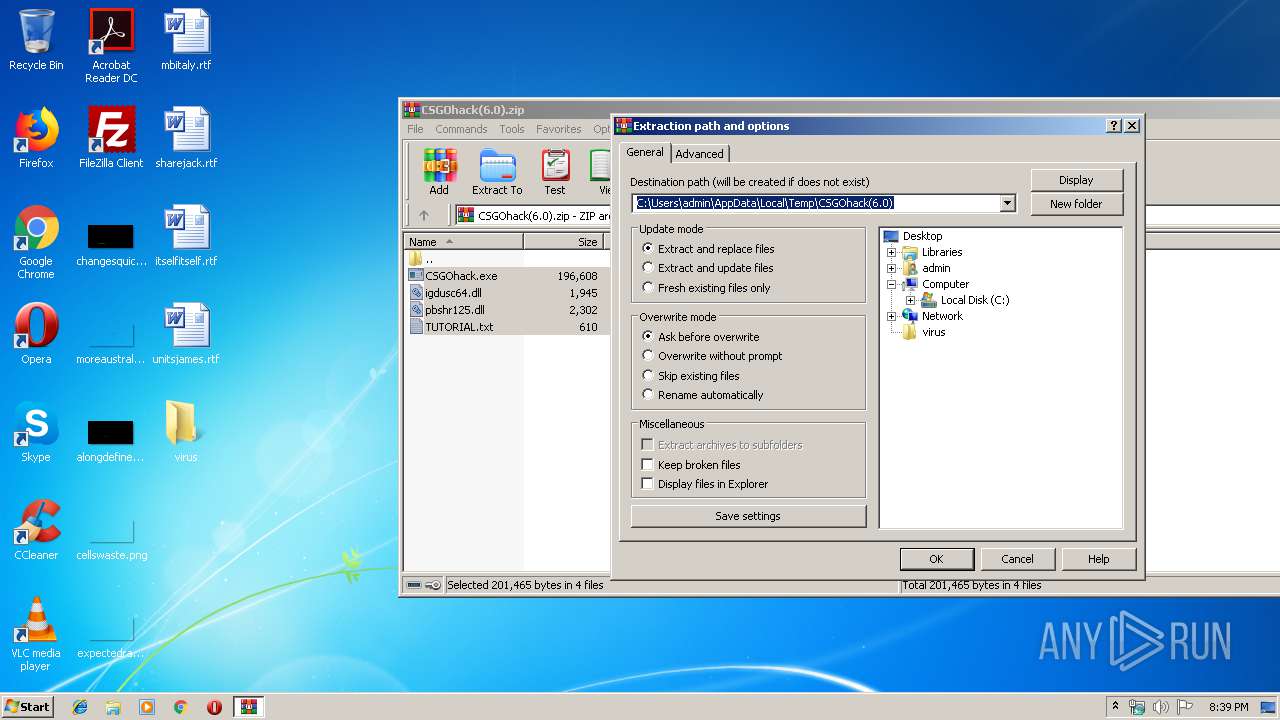
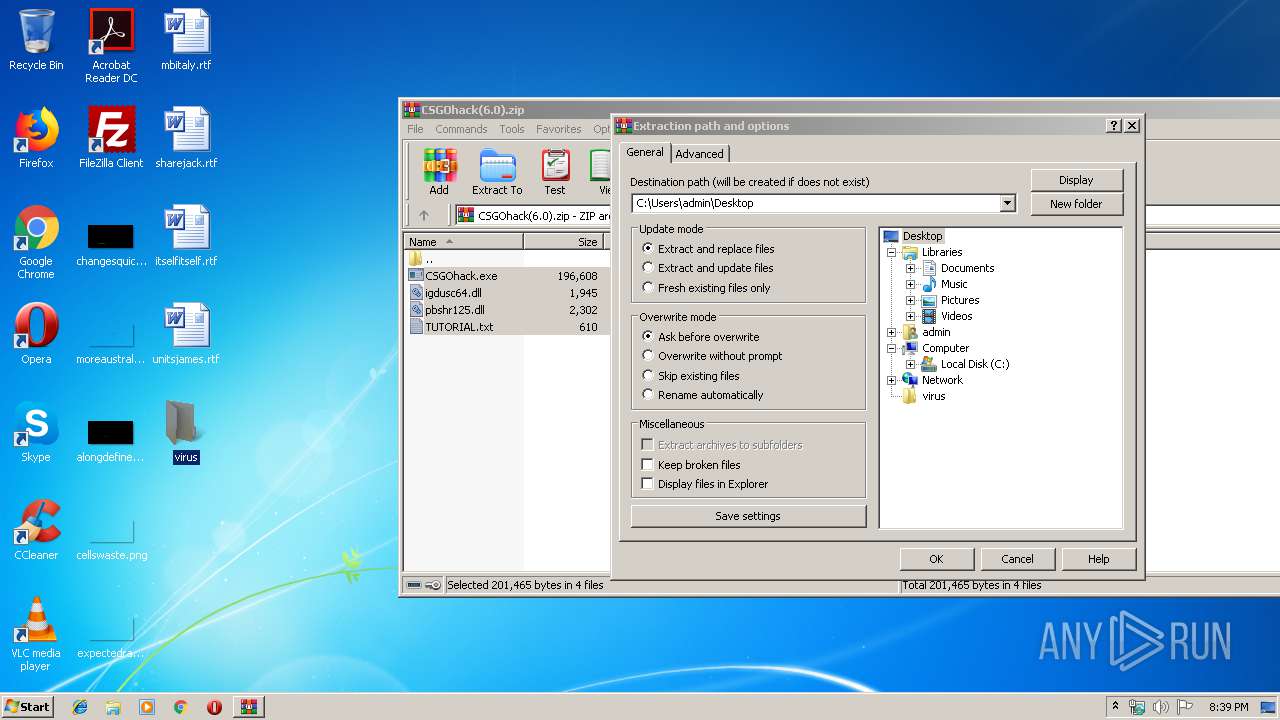
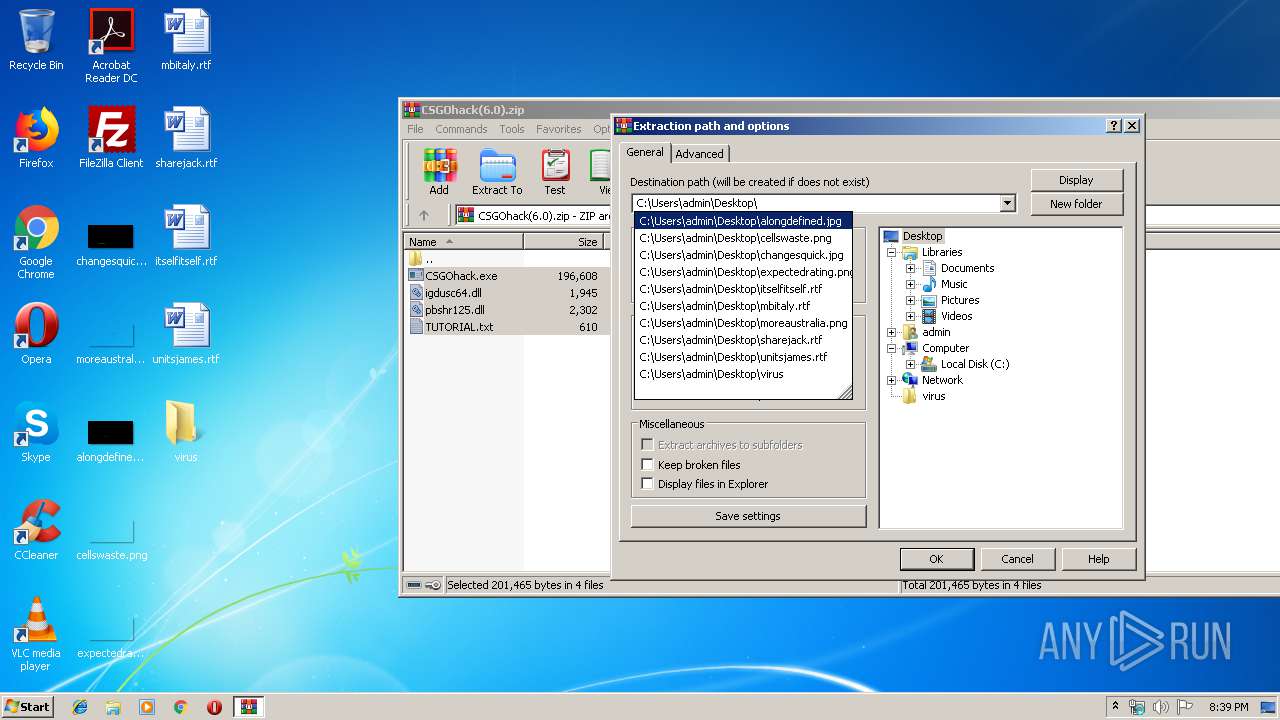
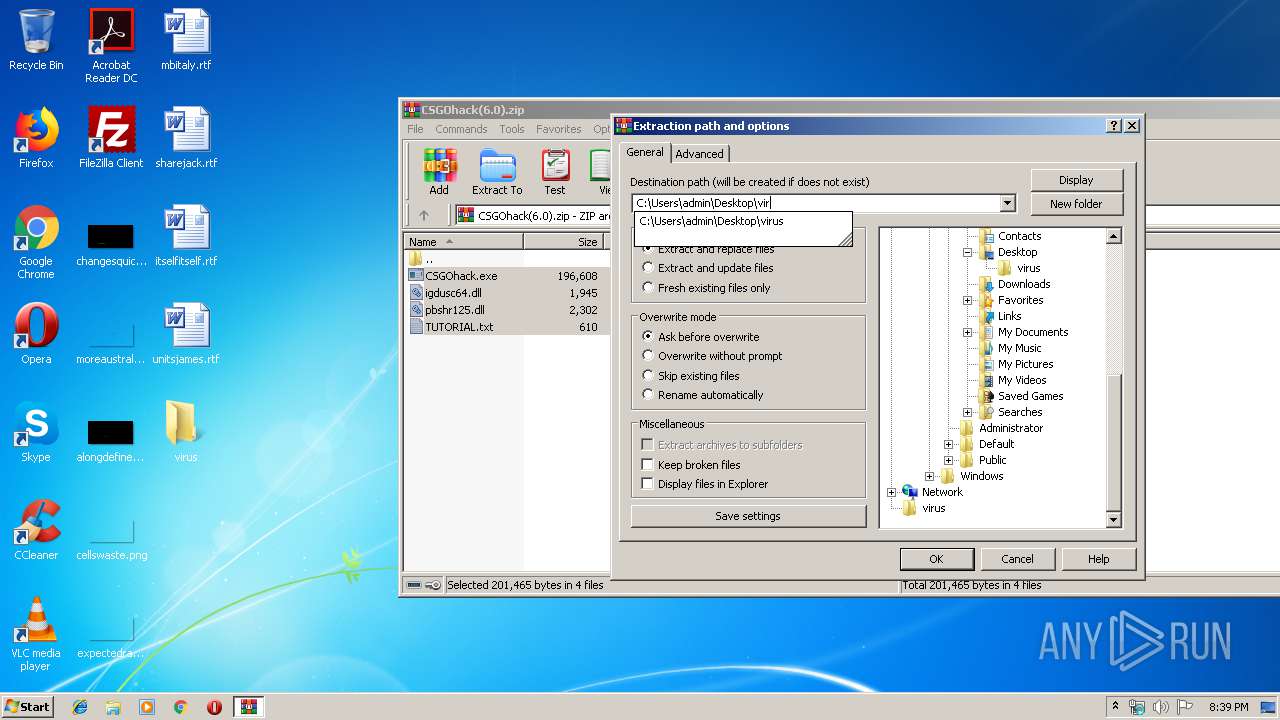
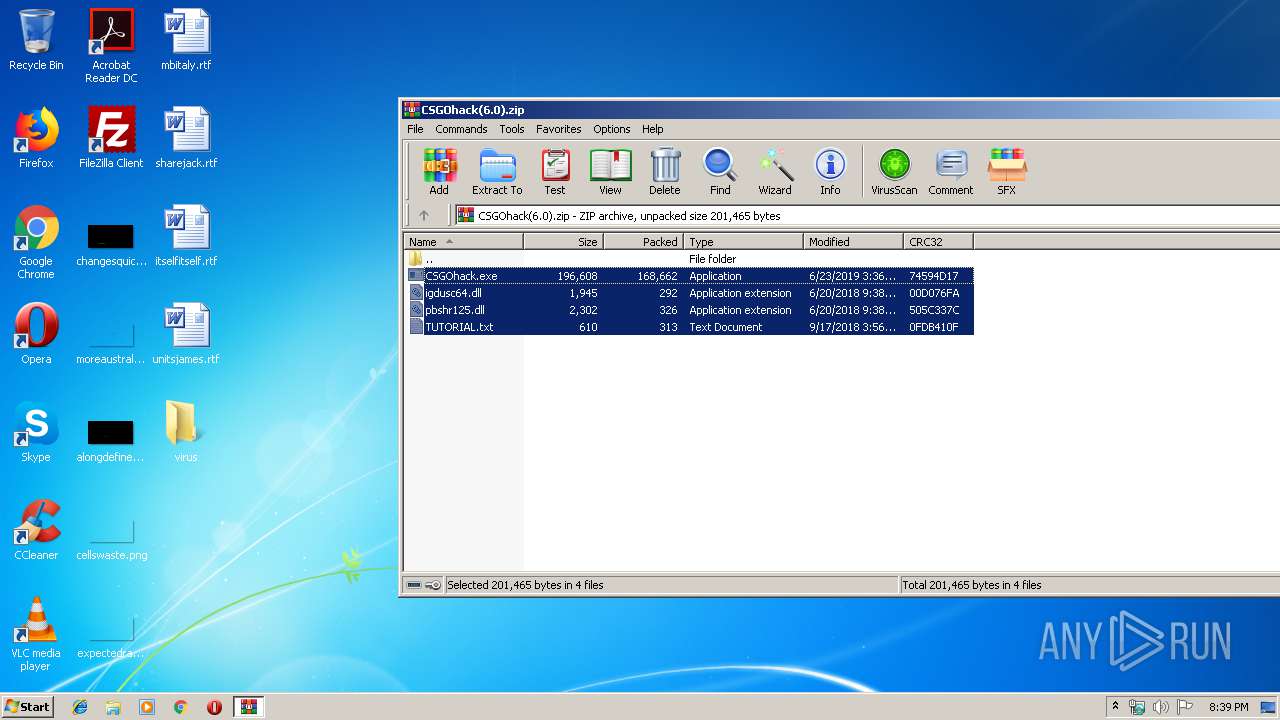
| File name: | CSGOhack(6.0).zip |
| Full analysis: | https://app.any.run/tasks/db93acce-44fe-4055-867f-f005c470f510 |
| Verdict: | Malicious activity |
| Analysis date: | July 11, 2019, 19:38:36 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v2.0 to extract |
| MD5: | 627F430280E40799C2025344A205B806 |
| SHA1: | 4C61888622C330E60696102875D6B9DEEB5CC94A |
| SHA256: | 8AFB7BCBF2090756C3CE59592FE19DD565C7E90B7B3244AD12B15A35D98B18C4 |
| SSDEEP: | 3072:zOuOQ0Q2AVZnOZ1DnP7NH+EX5ePWlouzT9ciMlpQDc1T+Oyl2iakm:s7iurT9duaT9v4pdKVlDHm |
MALICIOUS
Application was dropped or rewritten from another process
- CSGOhack.exe (PID: 3968)
- svhost.exe (PID: 588)
Runs app for hidden code execution
- CSGOhack.exe (PID: 3968)
Changes the autorun value in the registry
- reg.exe (PID: 4008)
SUSPICIOUS
Starts CMD.EXE for commands execution
- CSGOhack.exe (PID: 3968)
Executable content was dropped or overwritten
- cmd.exe (PID: 2996)
- CSGOhack.exe (PID: 3968)
- WinRAR.exe (PID: 3024)
Uses REG.EXE to modify Windows registry
- cmd.exe (PID: 2996)
INFO
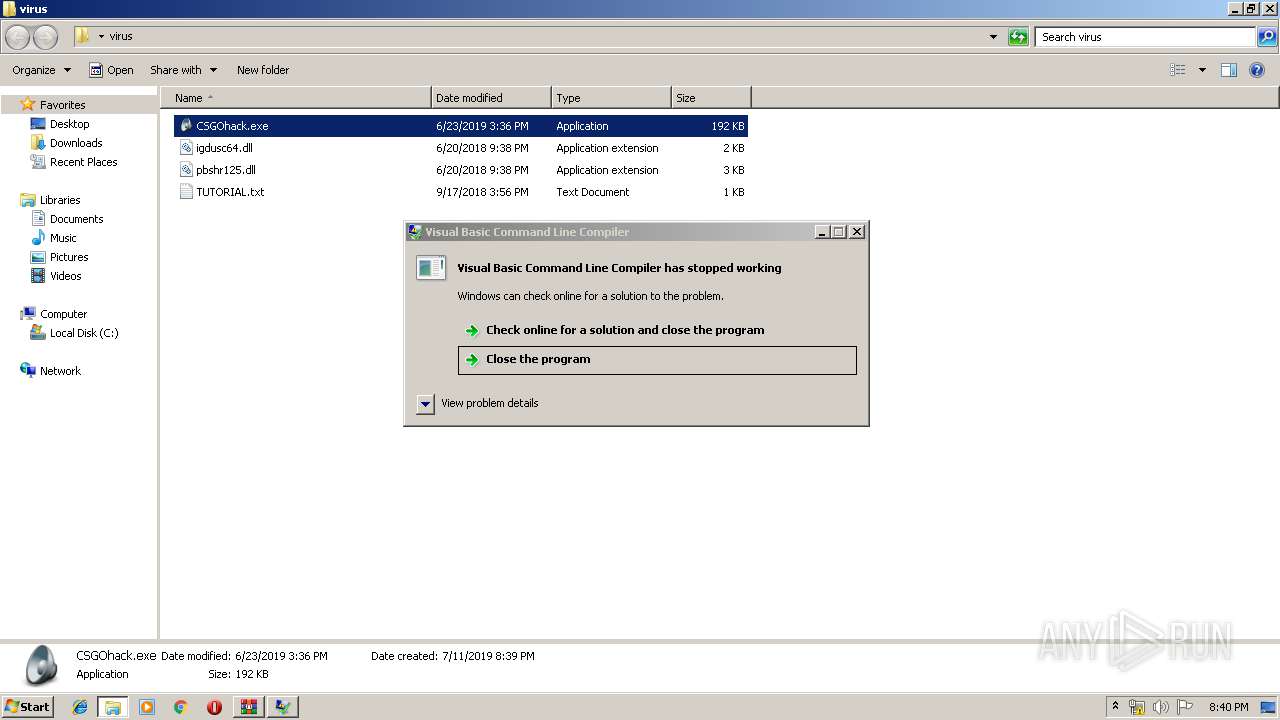
Application was crashed
- svhost.exe (PID: 588)
Manual execution by user
- CSGOhack.exe (PID: 3968)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 20 |
|---|---|
| ZipBitFlag: | - |
| ZipCompression: | Deflated |
| ZipModifyDate: | 2018:06:20 23:38:20 |
| ZipCRC: | 0x00d076fa |
| ZipCompressedSize: | 292 |
| ZipUncompressedSize: | 1945 |
| ZipFileName: | igdusc64.dll |
Total processes
45
Monitored processes
5
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 588 | "C:\Users\admin\AppData\Local\Temp\svhost.exe" | C:\Users\admin\AppData\Local\Temp\svhost.exe | CSGOhack.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Visual Basic Command Line Compiler Exit code: 0 Version: 9.0.30729.5420 Modules
| |||||||||||||||
| 2996 | "cmd.exe" | C:\Windows\system32\cmd.exe | CSGOhack.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 3024 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\AppData\Local\Temp\CSGOhack(6.0).zip" | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.60.0 Modules
| |||||||||||||||
| 3968 | "C:\Users\admin\Desktop\virus\CSGOhack.exe" | C:\Users\admin\Desktop\virus\CSGOhack.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Antimalware Service Executable Exit code: 0 Version: 4.18.1807.18075 (GitEnlistment(winpbld).180719-0853) Modules
| |||||||||||||||
| 4008 | reg add "HKCU\Software\Microsoft\Windows NT\CurrentVersion\Windows" /v Load /t REG_SZ /d "C:\Users\admin\AppData\Local\Temp\FolderN\name.exe.lnk" /f | C:\Windows\system32\reg.exe | cmd.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Registry Console Tool Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
Total events
633
Read events
616
Write events
17
Delete events
0
Modification events
| (PID) Process: | (3024) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (3024) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (3024) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\70\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (3024) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\CSGOhack(6.0).zip | |||
| (PID) Process: | (3024) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (3024) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (3024) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (3024) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (3024) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\70\52C64B7E |
| Operation: | write | Name: | @C:\Program Files\Common Files\system\wab32res.dll,-10100 |
Value: Contacts | |||
| (PID) Process: | (3024) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\DialogEditHistory\ExtrPath |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Desktop\virus | |||
Executable files
3
Suspicious files
0
Text files
4
Unknown types
1
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3024 | WinRAR.exe | C:\Users\admin\Desktop\virus\igdusc64.dll | text | |
MD5:— | SHA256:— | |||
| 3024 | WinRAR.exe | C:\Users\admin\Desktop\virus\TUTORIAL.txt | text | |
MD5:— | SHA256:— | |||
| 3024 | WinRAR.exe | C:\Users\admin\Desktop\virus\CSGOhack.exe | executable | |
MD5:— | SHA256:— | |||
| 2996 | cmd.exe | C:\Users\admin\AppData\Local\Temp\FolderN\name.exe | executable | |
MD5:— | SHA256:— | |||
| 3024 | WinRAR.exe | C:\Users\admin\Desktop\virus\pbshr125.dll | text | |
MD5:— | SHA256:— | |||
| 3968 | CSGOhack.exe | C:\Users\admin\AppData\Local\Temp\svhost.exe | executable | |
MD5:32827E69B293B99013BBBE37D029245D | SHA256:9250B89157770E3AB59A2C7E2DD6B12B3C61D9B7C6620C3B4727E4BFFF10F01F | |||
| 3968 | CSGOhack.exe | C:\Users\admin\AppData\Local\Temp\FolderN\name.exe.lnk | lnk | |
MD5:B7F2CFEC6823A438DBA7530A8F4AE648 | SHA256:612F6D646DAAA368D40443AB894042EBB8B93AC485658E78682731BAD9AB52CC | |||
| 2996 | cmd.exe | C:\Users\admin\AppData\Local\Temp\FolderN\name.exe:Zone.Identifier | text | |
MD5:130A75A932A2FE57BFEA6A65B88DA8F6 | SHA256:F2B79CAE559D6772AFC1C2ED9468988178F8B6833D5028A15DEA73CE47D0196E | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
0
DNS requests
0
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report