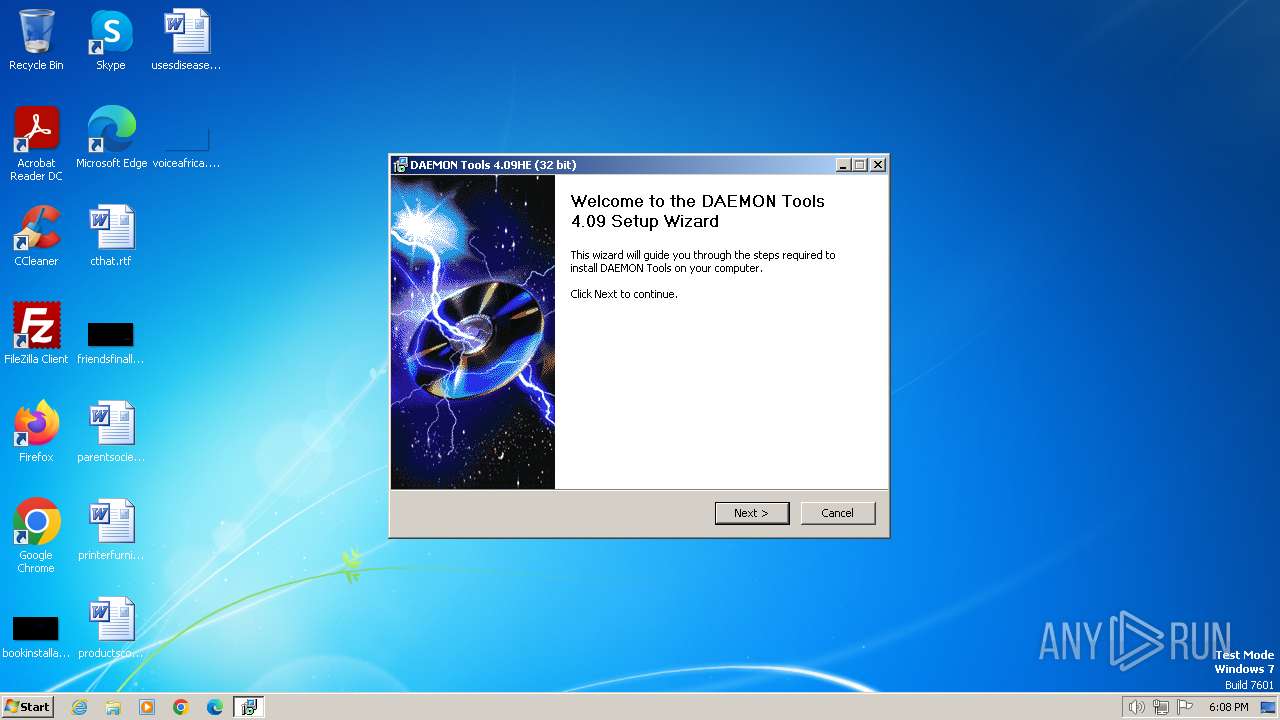
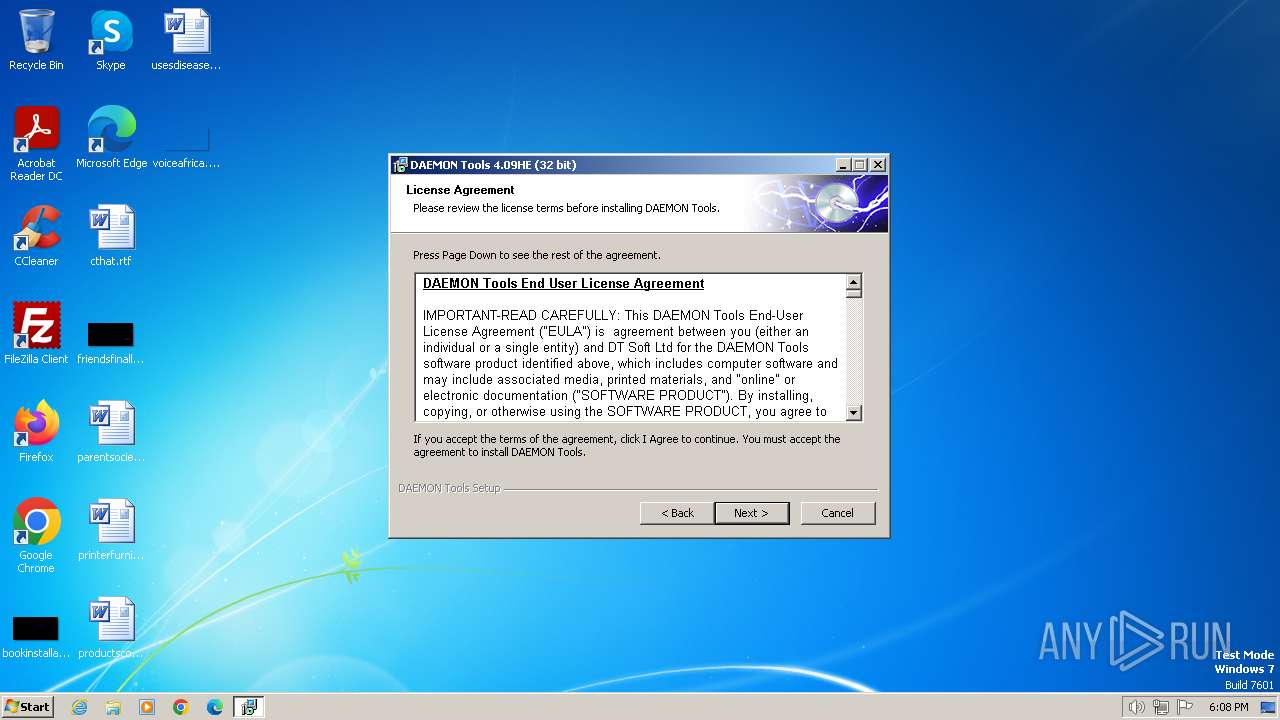
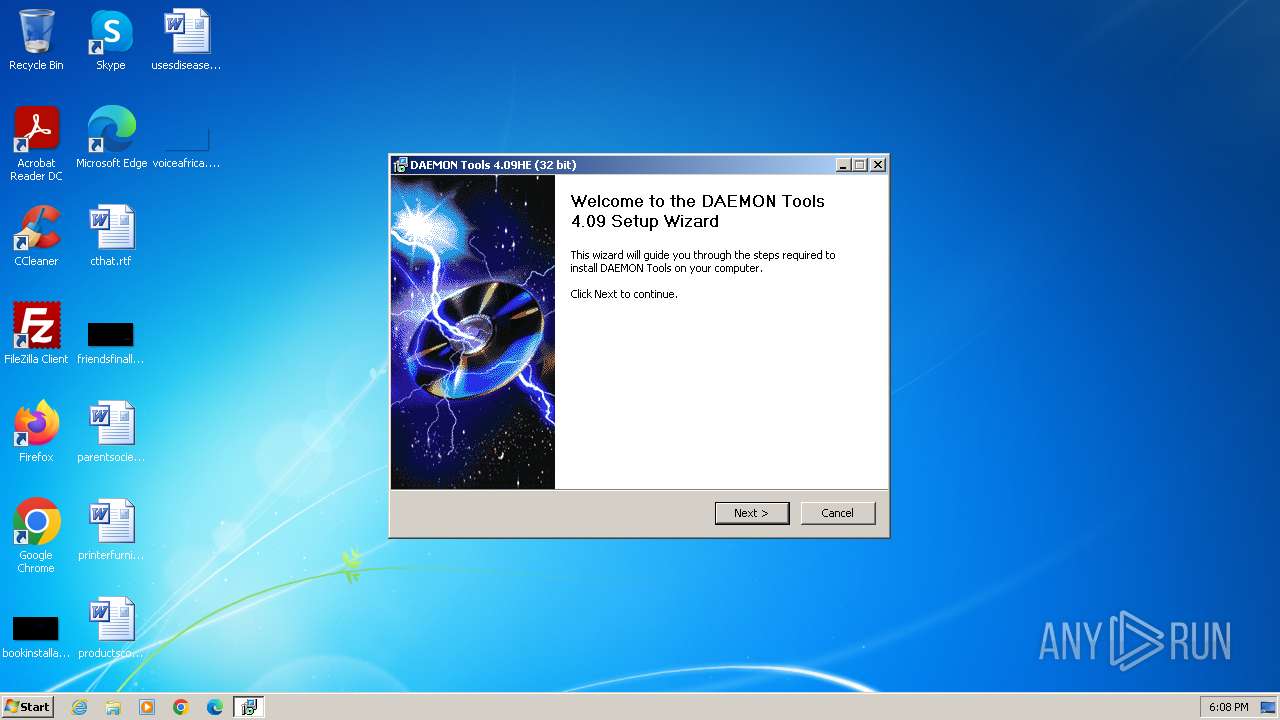
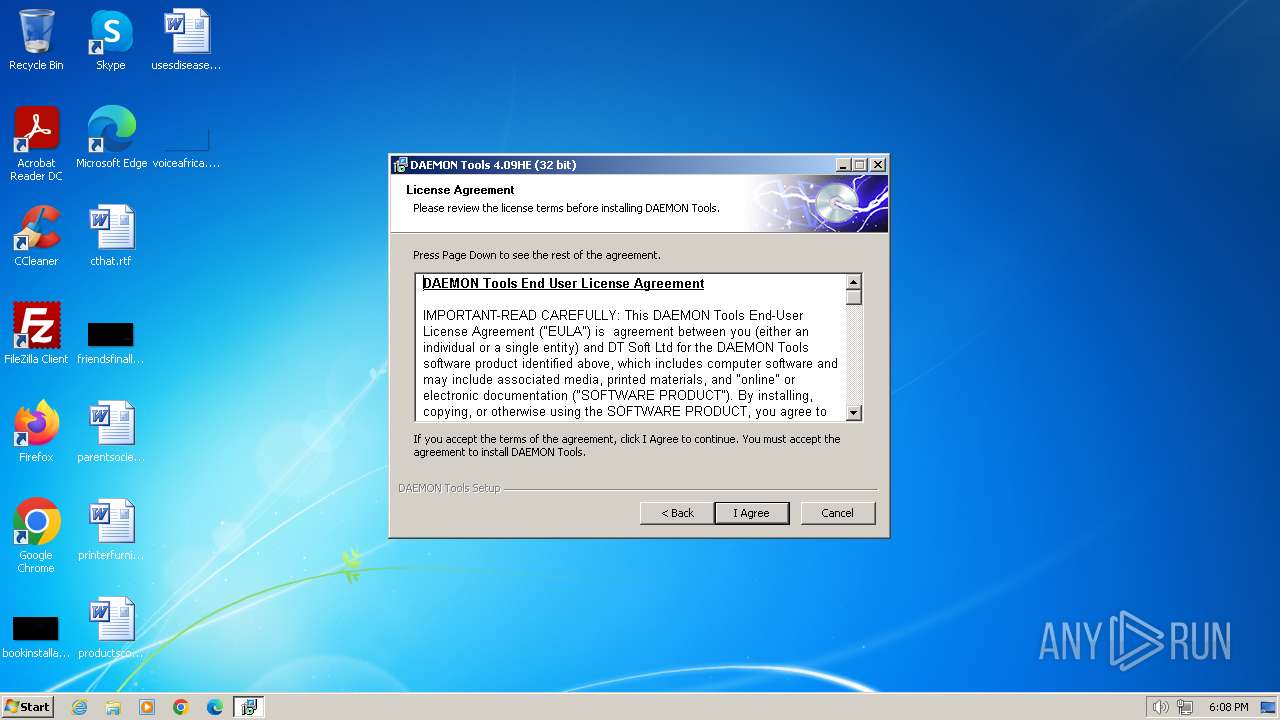
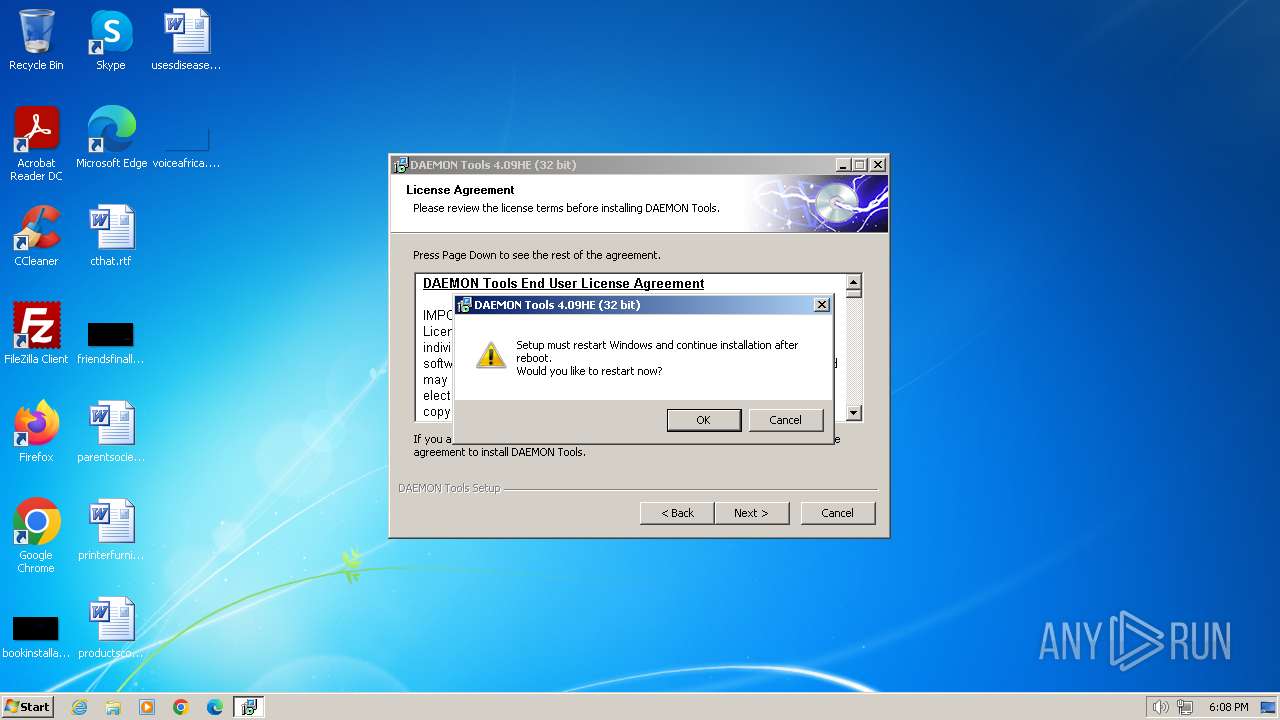
| File name: | daemon4091-x86.exe |
| Full analysis: | https://app.any.run/tasks/53b183ba-681e-4665-a866-679df72f5410 |
| Verdict: | Malicious activity |
| Analysis date: | January 27, 2024, 18:07:52 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows |
| MD5: | 473C6FC92E4FEEDDB691ECED0DDF4BE2 |
| SHA1: | FF8D540B43CF22B0E622E5712F4285032C0B2560 |
| SHA256: | 8AFAACAECA2BF8877D8A0976C211F8C902E181B9435C99BF7D804FCAC4BCF96E |
| SSDEEP: | 98304:nos41/5sb5RofavXw2gUGhelcAoMDsXwxkWmn57cG3Ph518Cj0RbucnWElUuvfNj:G2 |
MALICIOUS
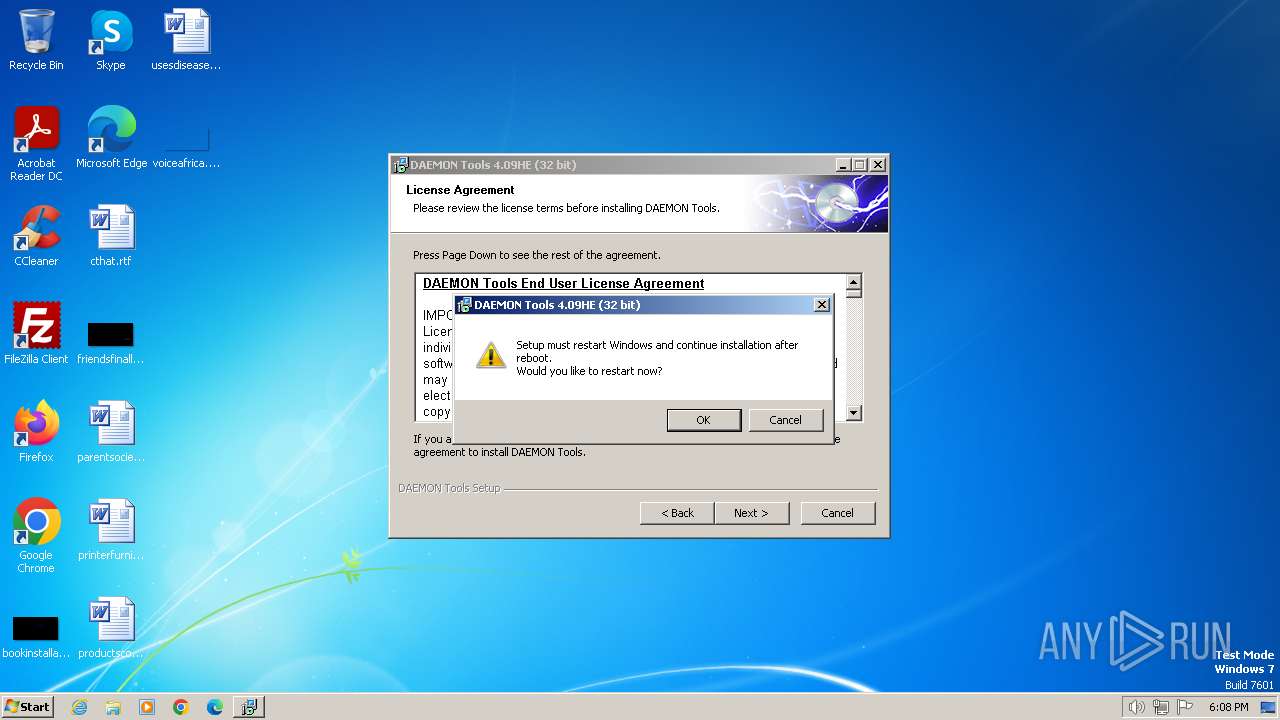
Creates a writable file in the system directory
- SPTDinst-x86.exe (PID: 2260)
Drops the executable file immediately after the start
- SPTDinst-x86.exe (PID: 2260)
- daemon4091-x86.exe (PID: 2204)
- SPTDinst-x86.exe (PID: 2508)
- daemon4091-x86.exe (PID: 1880)
SUSPICIOUS
Searches for installed software
- SPTDinst-x86.exe (PID: 2260)
- dllhost.exe (PID: 2688)
- SPTDinst-x86.exe (PID: 2508)
Creates files in the driver directory
- SPTDinst-x86.exe (PID: 2260)
Creates or modifies Windows services
- SPTDinst-x86.exe (PID: 2260)
Executable content was dropped or overwritten
- SPTDinst-x86.exe (PID: 2260)
- daemon4091-x86.exe (PID: 2204)
- SPTDinst-x86.exe (PID: 2508)
- daemon4091-x86.exe (PID: 1880)
The process executes via Task Scheduler
- sipnotify.exe (PID: 1632)
- ctfmon.exe (PID: 1564)
Adds/modifies Windows certificates
- SPTDinst-x86.exe (PID: 2260)
- sipnotify.exe (PID: 1632)
Drops a system driver (possible attempt to evade defenses)
- SPTDinst-x86.exe (PID: 2260)
- SPTDinst-x86.exe (PID: 2508)
Reads the Internet Settings
- sipnotify.exe (PID: 1632)
Reads settings of System Certificates
- sipnotify.exe (PID: 1632)
INFO
Checks supported languages
- daemon4091-x86.exe (PID: 1880)
- SPTDinst-x86.exe (PID: 2260)
- IMEKLMG.EXE (PID: 1412)
- IMEKLMG.EXE (PID: 356)
- daemon4091-x86.exe (PID: 2204)
- wmpnscfg.exe (PID: 2344)
- wmpnscfg.exe (PID: 2388)
- SPTDinst-x86.exe (PID: 2508)
Reads the computer name
- SPTDinst-x86.exe (PID: 2260)
- daemon4091-x86.exe (PID: 1880)
- IMEKLMG.EXE (PID: 1412)
- IMEKLMG.EXE (PID: 356)
- SPTDinst-x86.exe (PID: 2508)
- wmpnscfg.exe (PID: 2388)
- wmpnscfg.exe (PID: 2344)
Manual execution by a user
- IMEKLMG.EXE (PID: 356)
- IMEKLMG.EXE (PID: 1412)
- daemon4091-x86.exe (PID: 1020)
- daemon4091-x86.exe (PID: 2204)
- wmpnscfg.exe (PID: 2388)
- wmpnscfg.exe (PID: 2344)
Process checks whether UAC notifications are on
- IMEKLMG.EXE (PID: 1412)
- IMEKLMG.EXE (PID: 356)
Create files in a temporary directory
- daemon4091-x86.exe (PID: 2204)
- daemon4091-x86.exe (PID: 1880)
Reads security settings of Internet Explorer
- sipnotify.exe (PID: 1632)
Reads the machine GUID from the registry
- SPTDinst-x86.exe (PID: 2508)
- SPTDinst-x86.exe (PID: 2260)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | NSIS - Nullsoft Scriptable Install System (91.9) |
|---|---|---|
| .exe | | | Win32 Executable MS Visual C++ (generic) (3.3) |
| .exe | | | Win64 Executable (generic) (3) |
| .dll | | | Win32 Dynamic Link Library (generic) (0.7) |
| .exe | | | Win32 Executable (generic) (0.4) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2007:04:24 21:17:01+02:00 |
| ImageFileCharacteristics: | No relocs, Executable, No line numbers, No symbols, 32-bit |
| PEType: | PE32 |
| LinkerVersion: | 7.1 |
| CodeSize: | 23552 |
| InitializedDataSize: | 121344 |
| UninitializedDataSize: | 1024 |
| EntryPoint: | 0x3fb9 |
| OSVersion: | 4 |
| ImageVersion: | - |
| SubsystemVersion: | 4 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 4.9.1.0 |
| ProductVersionNumber: | 4.9.1.0 |
| FileFlagsMask: | 0x0000 |
| FileFlags: | (none) |
| FileOS: | Win32 |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | English (U.S.) |
| CharacterSet: | Windows, Latin1 |
| CompanyName: | DT Soft Ltd. |
| FileDescription: | DAEMON Tools Setup |
| FileVersion: | 4.09.1.0 |
| InternalName: | daemon409.exe |
| LegalCopyright: | Copyright (C) 2000-2007 |
| OriginalFileName: | daemon409.exe |
| ProductName: | DAEMON Tools |
| ProductVersion: | 4.09.1.0 |
Total processes
100
Monitored processes
13
Malicious processes
6
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 356 | "C:\Program Files\Common Files\microsoft shared\IME14\SHARED\IMEKLMG.EXE" /SetPreload /JPN /Log | C:\Program Files\Common Files\microsoft shared\IME14\SHARED\IMEKLMG.EXE | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Office IME 2010 Exit code: 1 Version: 14.0.4734.1000 Modules
| |||||||||||||||
| 984 | "C:\Users\admin\AppData\Local\Temp\daemon4091-x86.exe" | C:\Users\admin\AppData\Local\Temp\daemon4091-x86.exe | — | explorer.exe | |||||||||||
User: admin Company: DT Soft Ltd. Integrity Level: MEDIUM Description: DAEMON Tools Setup Exit code: 3221226540 Version: 4.09.1.0 Modules
| |||||||||||||||
| 1020 | "C:\Users\admin\AppData\Local\Temp\daemon4091-x86.exe" | C:\Users\admin\AppData\Local\Temp\daemon4091-x86.exe | — | explorer.exe | |||||||||||
User: admin Company: DT Soft Ltd. Integrity Level: MEDIUM Description: DAEMON Tools Setup Exit code: 3221226540 Version: 4.09.1.0 Modules
| |||||||||||||||
| 1412 | "C:\Program Files\Common Files\microsoft shared\IME14\SHARED\IMEKLMG.EXE" /SetPreload /KOR /Log | C:\Program Files\Common Files\microsoft shared\IME14\SHARED\IMEKLMG.EXE | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Office IME 2010 Exit code: 1 Version: 14.0.4734.1000 Modules
| |||||||||||||||
| 1564 | C:\Windows\System32\ctfmon.exe | C:\Windows\System32\ctfmon.exe | — | taskeng.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: CTF Loader Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1632 | C:\Windows\system32\sipnotify.exe -LogonOrUnlock | C:\Windows\System32\sipnotify.exe | taskeng.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: sipnotify Exit code: 0 Version: 6.1.7602.20480 (win7sp1_ldr_escrow.191010-1716) Modules
| |||||||||||||||
| 1880 | "C:\Users\admin\AppData\Local\Temp\daemon4091-x86.exe" | C:\Users\admin\AppData\Local\Temp\daemon4091-x86.exe | explorer.exe | ||||||||||||
User: admin Company: DT Soft Ltd. Integrity Level: HIGH Description: DAEMON Tools Setup Exit code: 0 Version: 4.09.1.0 Modules
| |||||||||||||||
| 2204 | "C:\Users\admin\AppData\Local\Temp\daemon4091-x86.exe" | C:\Users\admin\AppData\Local\Temp\daemon4091-x86.exe | explorer.exe | ||||||||||||
User: admin Company: DT Soft Ltd. Integrity Level: HIGH Description: DAEMON Tools Setup Exit code: 0 Version: 4.09.1.0 Modules
| |||||||||||||||
| 2260 | "C:\Users\admin\AppData\Local\Temp\SPTDinst-x86.exe" add /q | C:\Users\admin\AppData\Local\Temp\SPTDinst-x86.exe | daemon4091-x86.exe | ||||||||||||
User: admin Company: Duplex Secure Ltd. Integrity Level: HIGH Description: SCSI Pass Through Direct setup Exit code: 1 Version: 1.43.0.0 Modules
| |||||||||||||||
| 2344 | "C:\Program Files\Windows Media Player\wmpnscfg.exe" | C:\Program Files\Windows Media Player\wmpnscfg.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Media Player Network Sharing Service Configuration Application Exit code: 0 Version: 12.0.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
Total events
5 700
Read events
5 608
Write events
85
Delete events
7
Modification events
| (PID) Process: | (2260) SPTDinst-x86.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\services\VSS\Diag\SystemRestore |
| Operation: | write | Name: | SrCreateRp (Enter) |
Value: 40000000000000003811FC442B2FDA01740A0000480C0000D5070000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (2260) SPTDinst-x86.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\services\VSS\Diag\SPP |
| Operation: | write | Name: | SppCreate (Enter) |
Value: 40000000000000003811FC442B2FDA01740A0000480C0000D0070000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (2260) SPTDinst-x86.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\SPP |
| Operation: | write | Name: | LastIndex |
Value: 74 | |||
| (PID) Process: | (2260) SPTDinst-x86.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\services\VSS\Diag\SPP |
| Operation: | write | Name: | SppGatherWriterMetadata (Enter) |
Value: 400000000000000086834F452B2FDA01740A0000480C0000D3070000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (2260) SPTDinst-x86.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\services\VSS\Diag\VssapiPublisher |
| Operation: | write | Name: | IDENTIFY (Enter) |
Value: 4000000000000000E0E551452B2FDA01740A0000340B0000E8030000010000000000000000000000C3E45FD4C91B4942AEB82FA6735F4DE60000000000000000 | |||
| (PID) Process: | (2260) SPTDinst-x86.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\services\VSS\Diag\VssapiPublisher |
| Operation: | write | Name: | IDENTIFY (Leave) |
Value: 4000000000000000A63F0E462B2FDA01740A0000340B0000E8030000000000000000000000000000C3E45FD4C91B4942AEB82FA6735F4DE60000000000000000 | |||
| (PID) Process: | (2260) SPTDinst-x86.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\services\VSS\Diag\SPP |
| Operation: | write | Name: | SppGatherWriterMetadata (Leave) |
Value: 4000000000000000F070E2462B2FDA01740A0000480C0000D3070000010000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (2260) SPTDinst-x86.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\services\VSS\Diag\SPP |
| Operation: | write | Name: | SppCreate (Leave) |
Value: 40000000000000006417CC472B2FDA01740A0000480C0000D0070000010000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (2260) SPTDinst-x86.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\services\VSS\Diag\SystemRestore |
| Operation: | write | Name: | SrCreateRp (Leave) |
Value: 40000000000000006417CC472B2FDA01740A0000480C0000D5070000010000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (2260) SPTDinst-x86.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\services\VSS\Diag\SystemRestore |
| Operation: | write | Name: | SrCreateRp (Enter) |
Value: 40000000000000007AB3F5C74B51DA01D408000014060000D5070000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
Executable files
10
Suspicious files
5
Text files
11
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2688 | dllhost.exe | C:\System Volume Information\SPP\metadata-2 | — | |
MD5:— | SHA256:— | |||
| 1880 | daemon4091-x86.exe | C:\Users\admin\AppData\Local\Temp\nsz93F3.tmp\dtsetup.ini | text | |
MD5:CE819CC71C59C4F69933159285E8E727 | SHA256:AE10F55E6EEE0C64AD9DC5AB9998ED8DDE13F3EA050913B66CC5350DB7A6385E | |||
| 1880 | daemon4091-x86.exe | C:\Users\admin\AppData\Local\Temp\nsz93F3.tmp\setuphlp.dll | executable | |
MD5:ECE12FA4A88CAB1E743C534E4F4B91DC | SHA256:00A6658AE50896C118A77AC5FBA398B98A3BFE9F488333FEDBB288E7B7C42743 | |||
| 1880 | daemon4091-x86.exe | C:\Users\admin\AppData\Local\Temp\nsz93F3.tmp\modern-header.bmp | image | |
MD5:24B108615B4A85E4DE2828FB7A474D61 | SHA256:01C8E6395C2402B341192752EA7FF020A4D803DF6B74D693337A386F200692E9 | |||
| 2204 | daemon4091-x86.exe | C:\Users\admin\AppData\Local\Temp\nsg2992.tmp\modern-wizard.bmp | image | |
MD5:6ABE238A2C611B2654F46372DEF62E91 | SHA256:8EA43E465FE6EAF22974EF0AE4B53C112CFF3DB1E6D7ACF8557321823E78DDD2 | |||
| 1880 | daemon4091-x86.exe | C:\Users\admin\AppData\Local\Temp\nsz93F3.tmp\InstallOptions.dll | executable | |
MD5:07F3B3445F66E1089567796BF3C8BE78 | SHA256:A505E6C537A5CE0166227DDA9F7671605395592AC9F1A3764E8A01B713939DB1 | |||
| 2688 | dllhost.exe | C:\System Volume Information\SPP\OnlineMetadataCache\{d34101f0-2ef2-4b8a-bb03-cfc75b925fe5}_OnDiskSnapshotProp | binary | |
MD5:568A4EA80DA52B19AC941EAB2B34E6B7 | SHA256:0610432E1DF395DFD60DBE3E38F9572D9CE8BB9D9E1582E8D34B530A60C5EA5C | |||
| 1880 | daemon4091-x86.exe | C:\Users\admin\AppData\Local\Temp\nsz93F3.tmp\modern-wizard.bmp | image | |
MD5:6ABE238A2C611B2654F46372DEF62E91 | SHA256:8EA43E465FE6EAF22974EF0AE4B53C112CFF3DB1E6D7ACF8557321823E78DDD2 | |||
| 2260 | SPTDinst-x86.exe | C:\Windows\SYSTEM32\Drivers\sptd.sys | executable | |
MD5:4F576E516CC76EC50A244586BCFA1C78 | SHA256:75BCA3475AF5E211307EE3FEEB523A935971F56884F1174FD117E4AFE0B0DBD6 | |||
| 1880 | daemon4091-x86.exe | C:\Users\admin\AppData\Local\Temp\nsz93F2.tmp | binary | |
MD5:88D7CDF25CF711B54173D8C39C66269F | SHA256:EBAE682DAF1C288BD74EC2C368F22ABD97DF9F4060A895AA3CB9EA6E014775CC | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
1
TCP/UDP connections
8
DNS requests
1
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
1632 | sipnotify.exe | HEAD | 200 | 88.221.61.151:80 | http://query.prod.cms.rt.microsoft.com/cms/api/am/binary/RE2JgkA?v=133508525140460000 | unknown | — | — | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
1080 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |
1104 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |
1632 | sipnotify.exe | 88.221.61.151:80 | query.prod.cms.rt.microsoft.com | AKAMAI-AS | DE | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
query.prod.cms.rt.microsoft.com |
| whitelisted |