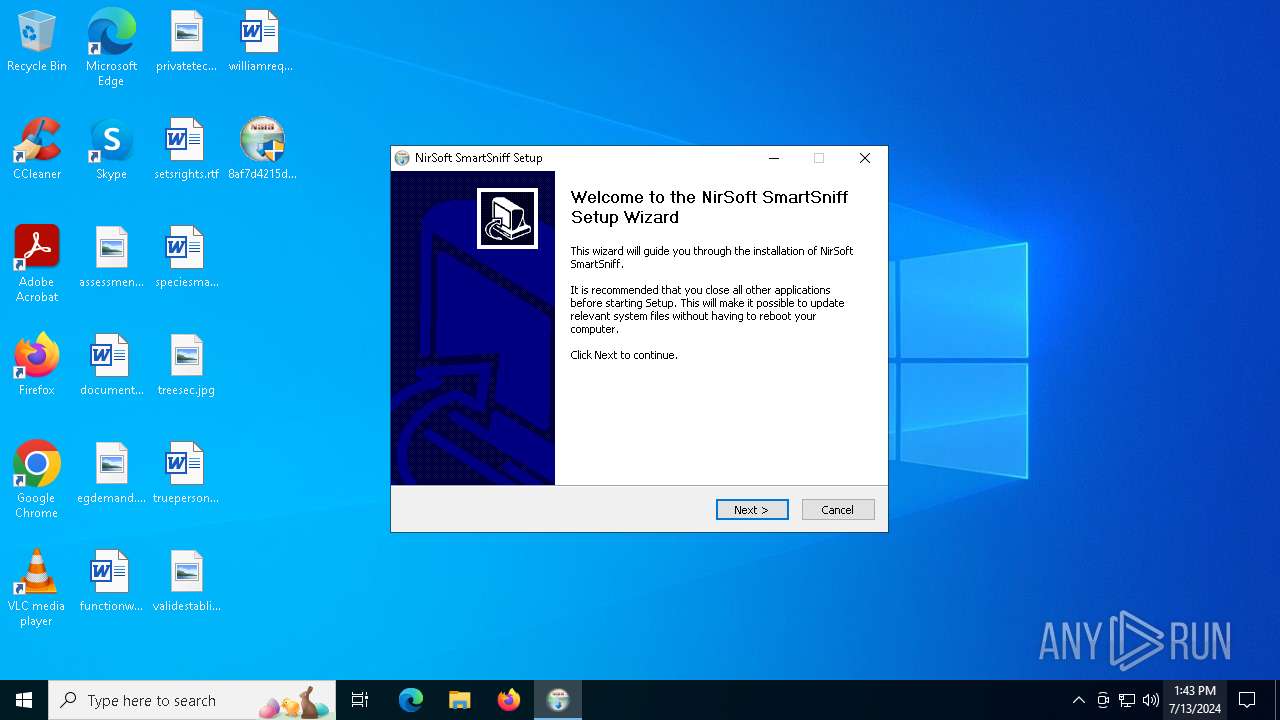
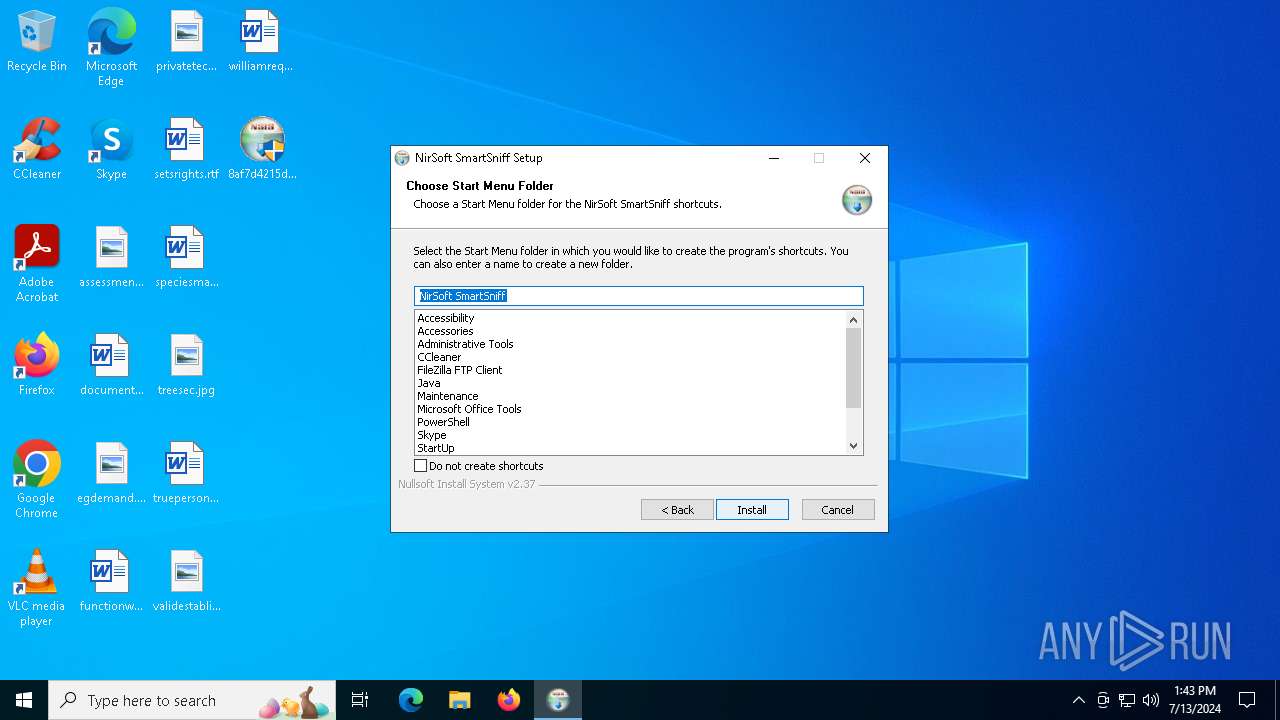
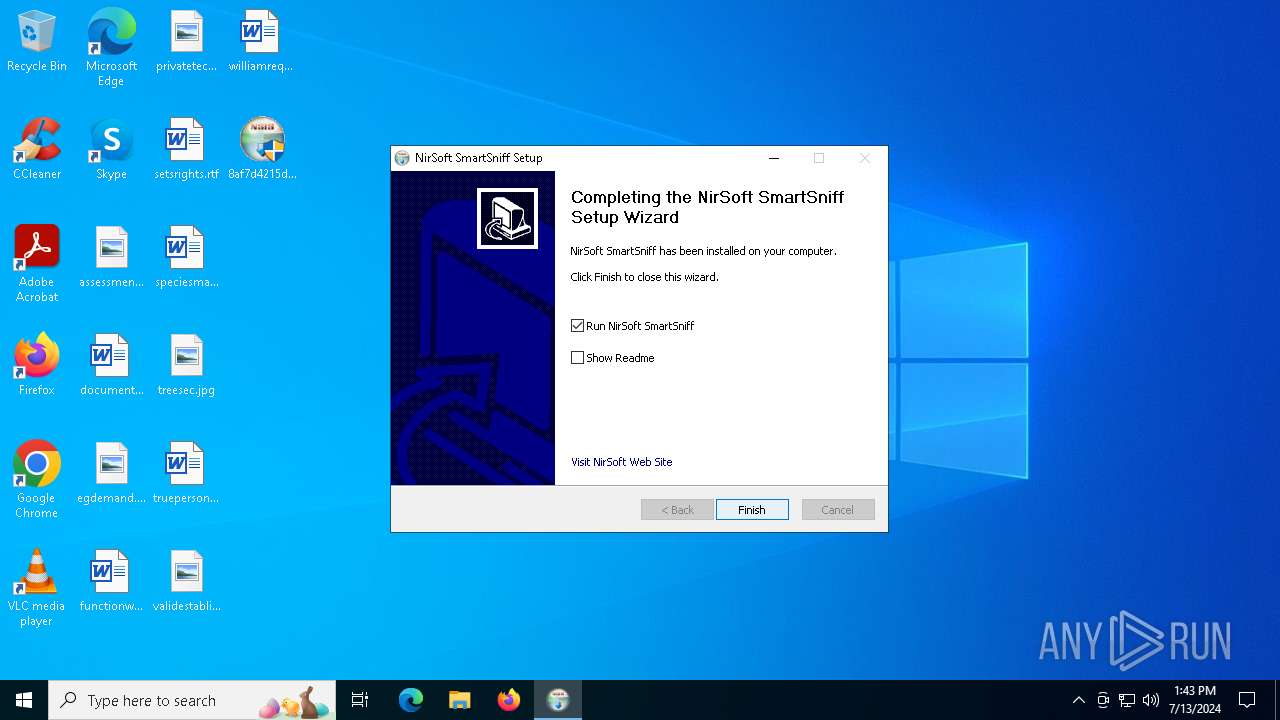
| File name: | 8af7d4215d7c784bc4e675a6e1ffaf82bf7780d3aa06d72eed6043f49024c83c.exe |
| Full analysis: | https://app.any.run/tasks/3a1a7103-a7c0-42b3-9e87-f0340557ef2c |
| Verdict: | Malicious activity |
| Analysis date: | July 13, 2024, 13:43:01 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows, Nullsoft Installer self-extracting archive |
| MD5: | EB6CC0CB208E5178FAFE9F43B738C125 |
| SHA1: | 3BCC2A22DF1CA7507173BCE5C21414CC8955A6A3 |
| SHA256: | 8AF7D4215D7C784BC4E675A6E1FFAF82BF7780D3AA06D72EED6043F49024C83C |
| SSDEEP: | 6144:C4afXJT+yVvtSmYcGbPYtlGw5ibnMv2rfYyy:OT+yVvtSmPGbPY/Gaibn39y |
MALICIOUS
Drops the executable file immediately after the start
- 8af7d4215d7c784bc4e675a6e1ffaf82bf7780d3aa06d72eed6043f49024c83c.exe (PID: 5532)
SUSPICIOUS
Executable content was dropped or overwritten
- 8af7d4215d7c784bc4e675a6e1ffaf82bf7780d3aa06d72eed6043f49024c83c.exe (PID: 5532)
Creates a software uninstall entry
- 8af7d4215d7c784bc4e675a6e1ffaf82bf7780d3aa06d72eed6043f49024c83c.exe (PID: 5532)
INFO
Checks supported languages
- 8af7d4215d7c784bc4e675a6e1ffaf82bf7780d3aa06d72eed6043f49024c83c.exe (PID: 5532)
- smsniff.exe (PID: 1572)
Create files in a temporary directory
- 8af7d4215d7c784bc4e675a6e1ffaf82bf7780d3aa06d72eed6043f49024c83c.exe (PID: 5532)
Reads the computer name
- 8af7d4215d7c784bc4e675a6e1ffaf82bf7780d3aa06d72eed6043f49024c83c.exe (PID: 5532)
- smsniff.exe (PID: 1572)
Creates files in the program directory
- 8af7d4215d7c784bc4e675a6e1ffaf82bf7780d3aa06d72eed6043f49024c83c.exe (PID: 5532)
Creates files or folders in the user directory
- 8af7d4215d7c784bc4e675a6e1ffaf82bf7780d3aa06d72eed6043f49024c83c.exe (PID: 5532)
NirSoft software is detected
- smsniff.exe (PID: 1572)
UPX packer has been detected
- smsniff.exe (PID: 1572)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | NSIS - Nullsoft Scriptable Install System (91.9) |
|---|---|---|
| .exe | | | Win32 Executable MS Visual C++ (generic) (3.3) |
| .exe | | | Win64 Executable (generic) (3) |
| .dll | | | Win32 Dynamic Link Library (generic) (0.7) |
| .exe | | | Win32 Executable (generic) (0.4) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2008:05:03 14:08:42+00:00 |
| ImageFileCharacteristics: | No relocs, Executable, No line numbers, No symbols, 32-bit |
| PEType: | PE32 |
| LinkerVersion: | 6 |
| CodeSize: | 23040 |
| InitializedDataSize: | 119808 |
| UninitializedDataSize: | 1024 |
| EntryPoint: | 0x3225 |
| OSVersion: | 4 |
| ImageVersion: | - |
| SubsystemVersion: | 4 |
| Subsystem: | Windows GUI |
Total processes
126
Monitored processes
3
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1296 | "C:\Users\admin\Desktop\8af7d4215d7c784bc4e675a6e1ffaf82bf7780d3aa06d72eed6043f49024c83c.exe" | C:\Users\admin\Desktop\8af7d4215d7c784bc4e675a6e1ffaf82bf7780d3aa06d72eed6043f49024c83c.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 3221226540 Modules
| |||||||||||||||
| 1572 | "C:\Program Files (x86)\NirSoft\SmartSniff\smsniff.exe" | C:\Program Files (x86)\NirSoft\SmartSniff\smsniff.exe | 8af7d4215d7c784bc4e675a6e1ffaf82bf7780d3aa06d72eed6043f49024c83c.exe | ||||||||||||
User: admin Company: NirSoft Integrity Level: HIGH Description: SmartSniff Version: 2.30 Modules
| |||||||||||||||
| 5532 | "C:\Users\admin\Desktop\8af7d4215d7c784bc4e675a6e1ffaf82bf7780d3aa06d72eed6043f49024c83c.exe" | C:\Users\admin\Desktop\8af7d4215d7c784bc4e675a6e1ffaf82bf7780d3aa06d72eed6043f49024c83c.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
Total events
1 599
Read events
1 596
Write events
3
Delete events
0
Modification events
| (PID) Process: | (5532) 8af7d4215d7c784bc4e675a6e1ffaf82bf7780d3aa06d72eed6043f49024c83c.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Windows\CurrentVersion\Uninstall\NirSoft SmartSniff |
| Operation: | write | Name: | UninstallString |
Value: "C:\Program Files (x86)\NirSoft\SmartSniff\uninst.exe" | |||
| (PID) Process: | (5532) 8af7d4215d7c784bc4e675a6e1ffaf82bf7780d3aa06d72eed6043f49024c83c.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Windows\CurrentVersion\Uninstall\NirSoft SmartSniff |
| Operation: | write | Name: | InstallLocation |
Value: C:\Program Files (x86)\NirSoft\SmartSniff | |||
| (PID) Process: | (5532) 8af7d4215d7c784bc4e675a6e1ffaf82bf7780d3aa06d72eed6043f49024c83c.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Windows\CurrentVersion\Uninstall\NirSoft SmartSniff |
| Operation: | write | Name: | DisplayName |
Value: NirSoft SmartSniff | |||
Executable files
4
Suspicious files
5
Text files
3
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 5532 | 8af7d4215d7c784bc4e675a6e1ffaf82bf7780d3aa06d72eed6043f49024c83c.exe | C:\Program Files (x86)\NirSoft\SmartSniff\smsniff.exe | executable | |
MD5:CC160FFCD2A395EC44B8F5BC53CC6233 | SHA256:219F4C201F2261BD84ADD6CDCCE06640DE9D073385F6860D572FCE3C71D43AC2 | |||
| 5532 | 8af7d4215d7c784bc4e675a6e1ffaf82bf7780d3aa06d72eed6043f49024c83c.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Start Menu\Programs\NirSoft SmartSniff\SmartSniff Help.lnk | binary | |
MD5:03096CFE3924884173E455CC8100277E | SHA256:EA6BDD2061DCCCF3D2AC1E4AE6AC7B31497444C68A84C3AB03943FA7052A6EA6 | |||
| 5532 | 8af7d4215d7c784bc4e675a6e1ffaf82bf7780d3aa06d72eed6043f49024c83c.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Start Menu\Programs\NirSoft SmartSniff\SmartSniff.lnk | lnk | |
MD5:0C4F845D4773EF47B33EBA6B21CCA117 | SHA256:3B64457B3C1763E37DEEEECA56AF79D8F3F43A1617823ACCEE8B063FC0E0DFA3 | |||
| 5532 | 8af7d4215d7c784bc4e675a6e1ffaf82bf7780d3aa06d72eed6043f49024c83c.exe | C:\Users\admin\AppData\Local\Temp\nsvF8B1.tmp\modern-wizard.bmp | image | |
MD5:CBE40FD2B1EC96DAEDC65DA172D90022 | SHA256:3AD2DC318056D0A2024AF1804EA741146CFC18CC404649A44610CBF8B2056CF2 | |||
| 5532 | 8af7d4215d7c784bc4e675a6e1ffaf82bf7780d3aa06d72eed6043f49024c83c.exe | C:\Users\admin\AppData\Local\Temp\nsvF8B1.tmp\ioSpecial.ini | ini | |
MD5:E2D5070BC28DB1AC745613689FF86067 | SHA256:D95AED234F932A1C48A2B1B0D98C60CA31F962310C03158E2884AB4DDD3EA1E0 | |||
| 5532 | 8af7d4215d7c784bc4e675a6e1ffaf82bf7780d3aa06d72eed6043f49024c83c.exe | C:\Users\admin\AppData\Local\Temp\nsvF8B1.tmp\StartMenu.dll | executable | |
MD5:8262FBC2A172FF04146E7587649D7091 | SHA256:AC53840D019B746AB5DABAA40D7720C9A4487C861B155926454BF8B10BD0963D | |||
| 5532 | 8af7d4215d7c784bc4e675a6e1ffaf82bf7780d3aa06d72eed6043f49024c83c.exe | C:\Users\admin\AppData\Local\Temp\nsvF8B1.tmp\InstallOptions.dll | executable | |
MD5:3809B1424D53CCB427C88CABAB8B5F94 | SHA256:426EFD56DA4014F12EC8EE2E268F86B848BBCA776333D55482CB3EB71C744088 | |||
| 5532 | 8af7d4215d7c784bc4e675a6e1ffaf82bf7780d3aa06d72eed6043f49024c83c.exe | C:\Program Files (x86)\NirSoft\SmartSniff\readme.txt | text | |
MD5:979798509185A188C45E885B78B5CBFA | SHA256:6002DAE9114AAD50EC738209CC8A11FB8F90A3BABC0C7BB96F68F0D9339B9501 | |||
| 5532 | 8af7d4215d7c784bc4e675a6e1ffaf82bf7780d3aa06d72eed6043f49024c83c.exe | C:\Program Files (x86)\NirSoft\SmartSniff\uninst.exe | executable | |
MD5:95E89B1E4A5D8DEEC95A4CF33A573D2B | SHA256:C63D4002857E41E9AA9527A1C8BA3C7363E73D06907C1F6ECD54BD1F7A1728E9 | |||
| 5532 | 8af7d4215d7c784bc4e675a6e1ffaf82bf7780d3aa06d72eed6043f49024c83c.exe | C:\Users\admin\AppData\Local\Temp\nslF872.tmp | binary | |
MD5:B75B80DD602CA2EC5D7039F2E02D4FC5 | SHA256:5A7B0310F0C9B035F3A40CFBEBC914CCF8CC2ED089FC910613F17A12406167F1 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
13
TCP/UDP connections
38
DNS requests
9
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
1828 | svchost.exe | GET | 200 | 2.16.164.88:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
1792 | MoUsoCoreWorker.exe | GET | 200 | 2.16.164.88:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
1828 | svchost.exe | GET | 200 | 88.221.169.152:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 104.126.37.171:443 | https://www.bing.com/AS/API/WindowsCortanaPane/V2/Suggestions?qry=r&setlang=en-US&cc=US&nohs=1&qfm=1&cp=1&cvid=917f2af1fe65416cbd620a4b992edbf0&ig=8217ecd434a24e319c68e41132cd851d | unknown | binary | 5.15 Kb | unknown |
— | — | GET | 200 | 104.126.37.130:443 | https://www.bing.com/rb/18/jnc,nj/6hU_LneafI_NFLeDvM367ebFaKQ.js?bu=DyIrb3t-gQF4cnWyAbUBK6UBK7gB&or=w | unknown | text | 21.3 Kb | unknown |
— | — | GET | 200 | 104.126.37.160:443 | https://www.bing.com/AS/API/WindowsCortanaPane/V2/Suggestions?qry=regedi&setlang=en-US&cc=US&nohs=1&qfm=1&cp=6&cvid=917f2af1fe65416cbd620a4b992edbf0&ig=46856f19730442d7bfc8a588e4a577aa | unknown | binary | 4.00 Kb | unknown |
— | — | GET | 200 | 104.126.37.161:443 | https://www.bing.com/AS/API/WindowsCortanaPane/V2/Suggestions?qry=reged&setlang=en-US&cc=US&nohs=1&qfm=1&cp=5&cvid=917f2af1fe65416cbd620a4b992edbf0&ig=d9fc350f72484720963919f484813311 | unknown | binary | 4.71 Kb | unknown |
— | — | GET | 200 | 104.126.37.186:443 | https://www.bing.com/AS/API/WindowsCortanaPane/V2/Suggestions?qry=regedit&setlang=en-US&cc=US&nohs=1&qfm=1&cp=7&cvid=917f2af1fe65416cbd620a4b992edbf0&ig=0c07db2ed43b472383863f523ee03420 | unknown | binary | 4.78 Kb | unknown |
— | — | GET | 200 | 104.126.37.130:443 | https://www.bing.com/AS/API/WindowsCortanaPane/V2/Suggestions?qry=rege&setlang=en-US&cc=US&nohs=1&qfm=1&cp=4&cvid=917f2af1fe65416cbd620a4b992edbf0&ig=9e5ca3b8609c45288674b78f53cdefa2 | unknown | binary | 4.99 Kb | unknown |
— | — | GET | 200 | 104.126.37.170:443 | https://www.bing.com/AS/API/WindowsCortanaPane/V2/Suggestions?qry=re&setlang=en-US&cc=US&nohs=1&qfm=1&cp=2&cvid=917f2af1fe65416cbd620a4b992edbf0&ig=886f7dfaf8a943d7ac515843550c84b9 | unknown | binary | 5.00 Kb | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
1828 | svchost.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
4032 | svchost.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
— | — | 192.168.100.255:137 | — | — | — | whitelisted |
2848 | RUXIMICS.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
1792 | MoUsoCoreWorker.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
— | — | 2.23.209.185:443 | www.bing.com | Akamai International B.V. | GB | whitelisted |
4656 | SearchApp.exe | 2.23.209.185:443 | www.bing.com | Akamai International B.V. | GB | whitelisted |
1828 | svchost.exe | 2.16.164.88:80 | crl.microsoft.com | Akamai International B.V. | NL | unknown |
1792 | MoUsoCoreWorker.exe | 2.16.164.88:80 | crl.microsoft.com | Akamai International B.V. | NL | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
www.bing.com |
| whitelisted |
google.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
self.events.data.microsoft.com |
| whitelisted |