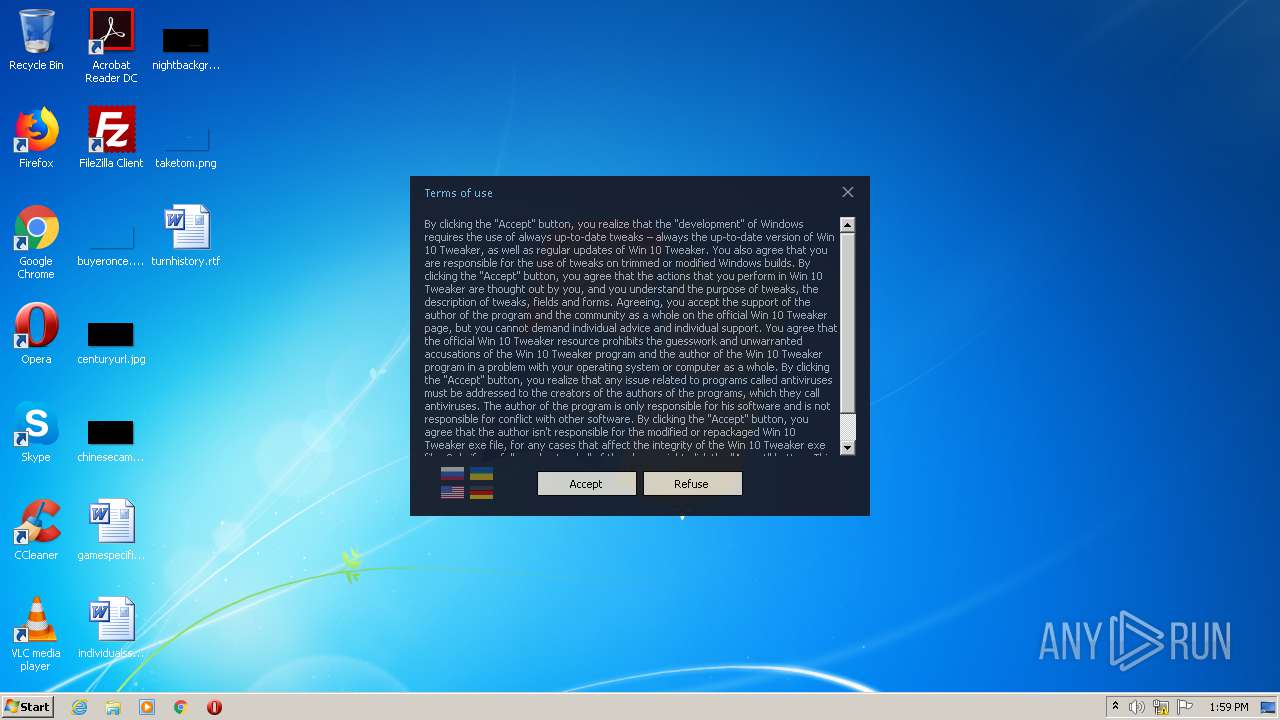
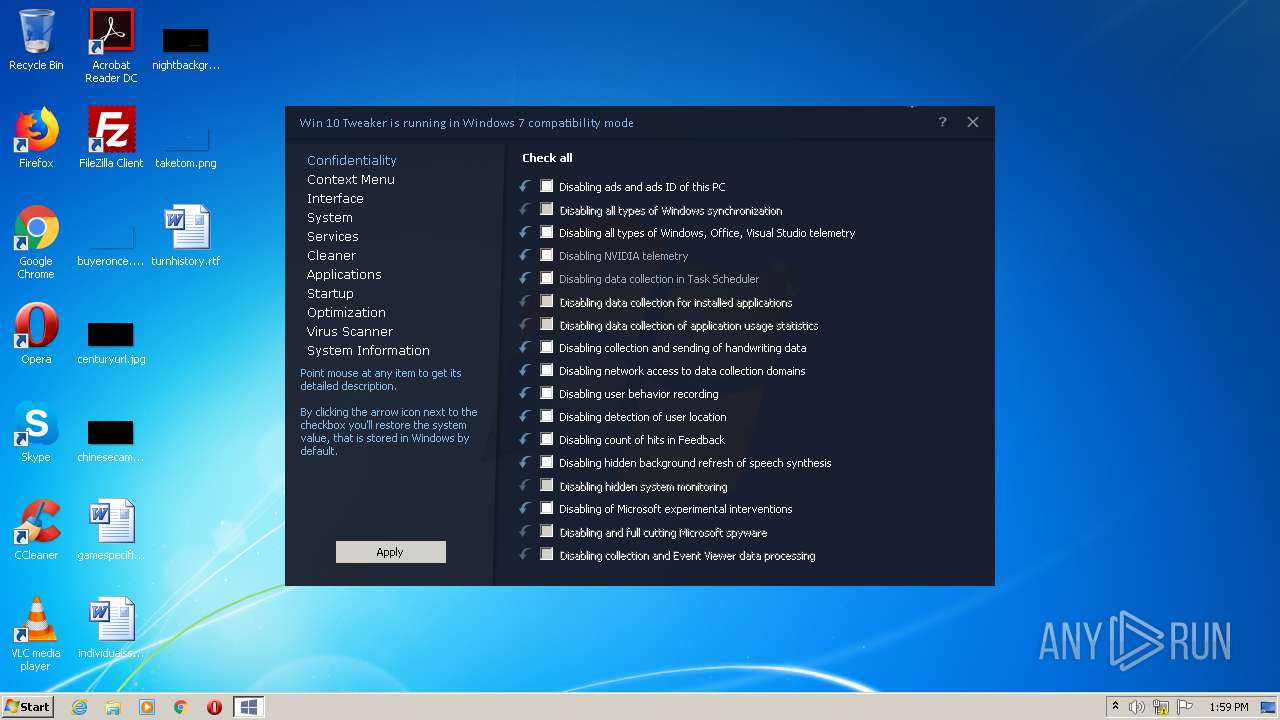
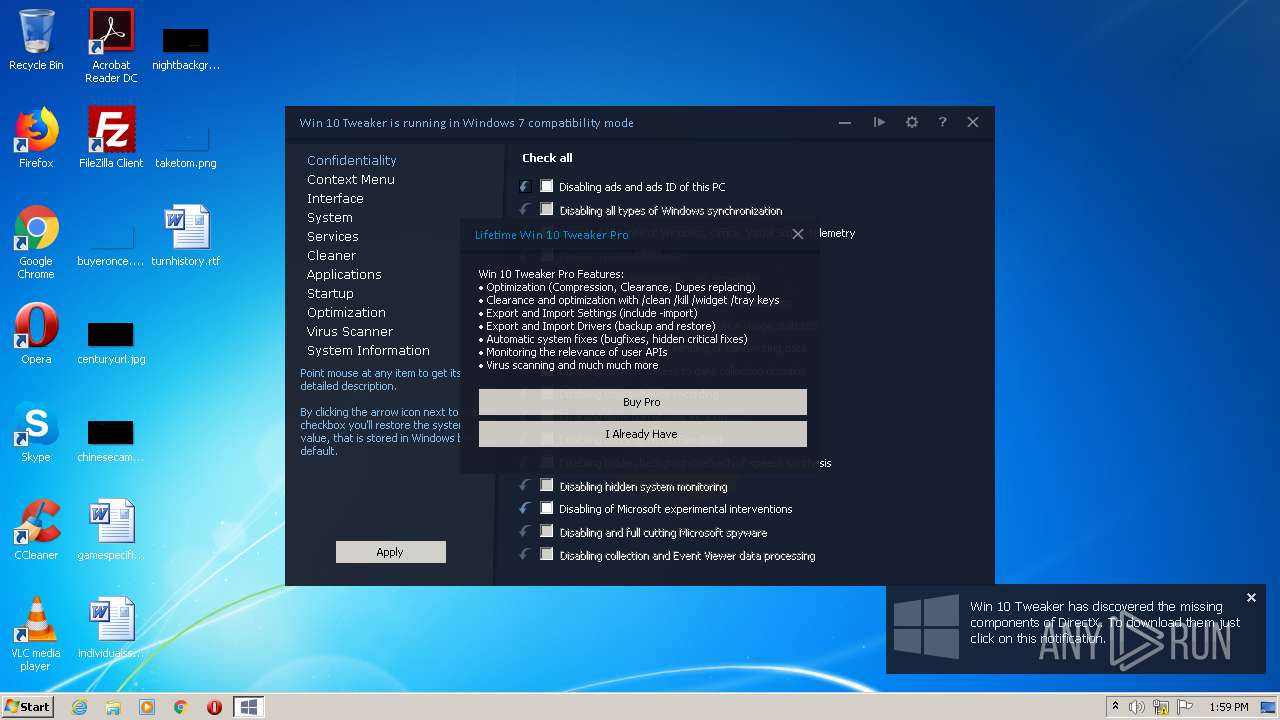
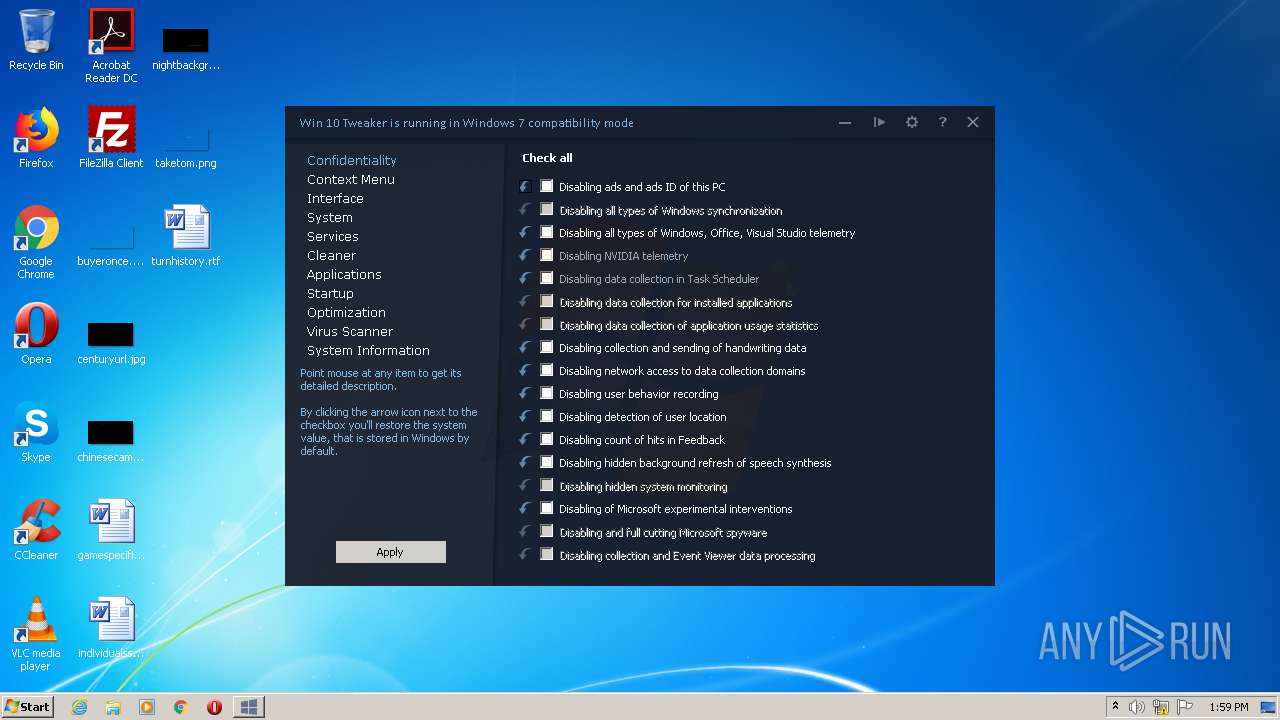
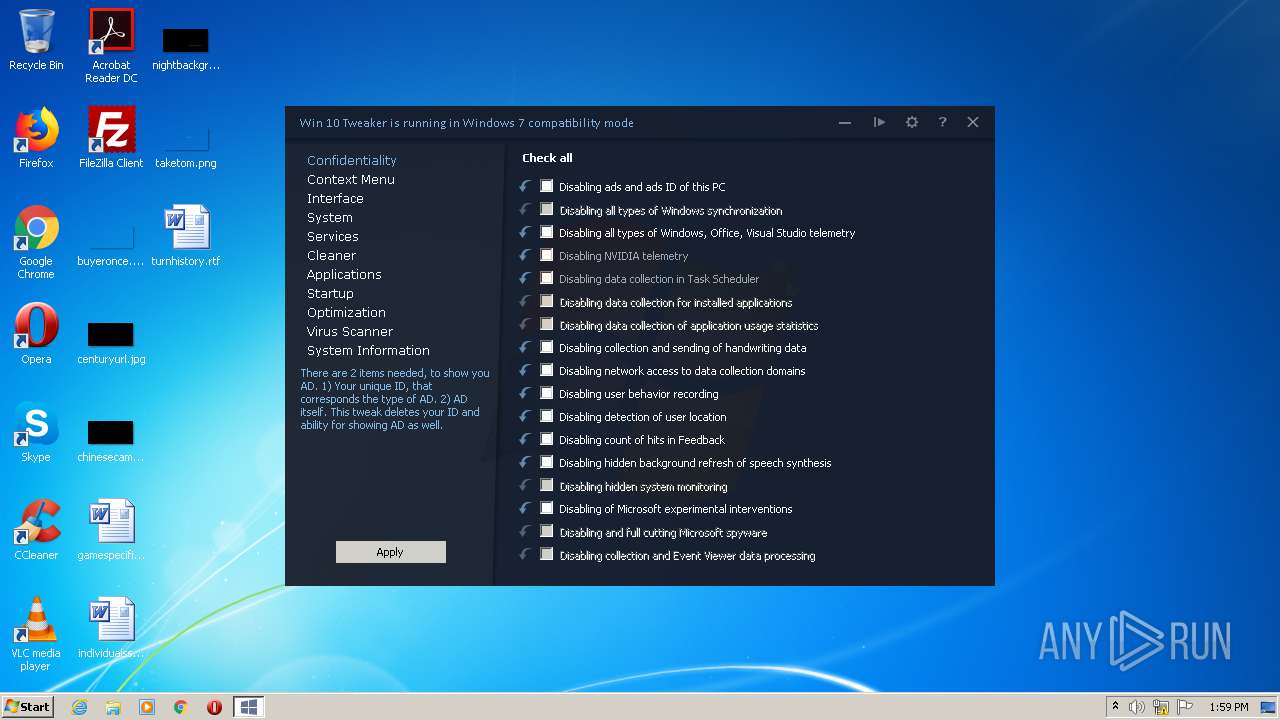
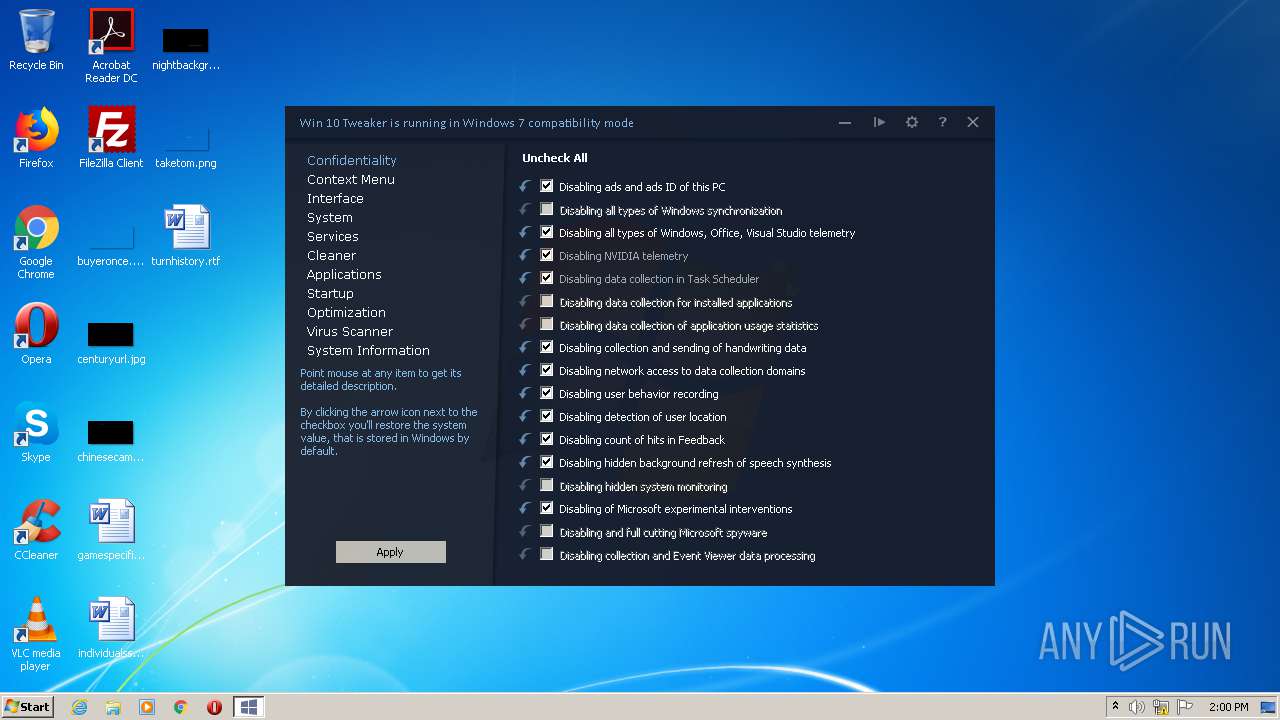
| File name: | Win 10 Tweaker.exe |
| Full analysis: | https://app.any.run/tasks/3daa8df4-9c26-4a79-b48f-cb1bc11de013 |
| Verdict: | Malicious activity |
| Analysis date: | November 29, 2020, 13:59:02 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (GUI) Intel 80386 Mono/.Net assembly, for MS Windows |
| MD5: | 96E7FA5B168A87F0A83BB409AC6C7082 |
| SHA1: | E13E7C0EBDE3678A19C3893CB824FFC9BD07E40E |
| SHA256: | 8AF3D447CE1357846611622D3A8D0A7D08FB7949F83B7C6E2E0BB0CDF47F86C5 |
| SSDEEP: | 24576:3BHpchzD3dekOGMTSIPMT7yM8aorU8SkBnOHwUNpi4c3zPLGxOS+:3BHQ35wMTZ8ao3SkBqvXWZS |
MALICIOUS
Uses Task Scheduler to run other applications
- cmd.exe (PID: 1668)
- cmd.exe (PID: 2216)
- cmd.exe (PID: 2536)
- cmd.exe (PID: 4064)
- cmd.exe (PID: 2184)
- cmd.exe (PID: 3000)
Loads the Task Scheduler COM API
- schtasks.exe (PID: 1980)
- schtasks.exe (PID: 1700)
- schtasks.exe (PID: 2152)
- schtasks.exe (PID: 3396)
- schtasks.exe (PID: 2872)
- schtasks.exe (PID: 2652)
- schtasks.exe (PID: 1788)
- schtasks.exe (PID: 3084)
- schtasks.exe (PID: 2804)
- schtasks.exe (PID: 2568)
- schtasks.exe (PID: 2144)
- schtasks.exe (PID: 2216)
- schtasks.exe (PID: 308)
- schtasks.exe (PID: 2940)
- schtasks.exe (PID: 2504)
- schtasks.exe (PID: 2372)
- schtasks.exe (PID: 3356)
- schtasks.exe (PID: 3576)
- schtasks.exe (PID: 2672)
- schtasks.exe (PID: 2404)
- schtasks.exe (PID: 3660)
- schtasks.exe (PID: 2144)
- schtasks.exe (PID: 2156)
- schtasks.exe (PID: 1380)
- schtasks.exe (PID: 1124)
- schtasks.exe (PID: 2800)
- schtasks.exe (PID: 2832)
- schtasks.exe (PID: 2076)
- schtasks.exe (PID: 2268)
- schtasks.exe (PID: 3948)
Changes Windows auto-update feature
- Win 10 Tweaker.exe (PID: 3008)
Writes to the hosts file
- Win 10 Tweaker.exe (PID: 3008)
Modifies hosts file to block updates
- Win 10 Tweaker.exe (PID: 3008)
Changes Image File Execution Options
- Win 10 Tweaker.exe (PID: 3008)
Starts Visual C# compiler
- Win 10 Tweaker.exe (PID: 3008)
Disables Windows Defender
- Win 10 Tweaker.exe (PID: 3008)
Changes settings of System certificates
- Win 10 Tweaker.exe (PID: 3008)
SUSPICIOUS
Reads CPU info
- Win 10 Tweaker.exe (PID: 3008)
Starts CMD.EXE for commands execution
- Win 10 Tweaker.exe (PID: 3008)
Reads Environment values
- Win 10 Tweaker.exe (PID: 3008)
Starts application with an unusual extension
- cmd.exe (PID: 1668)
- cmd.exe (PID: 2216)
- cmd.exe (PID: 3000)
- cmd.exe (PID: 2184)
Modifies the open verb of a shell class
- Win 10 Tweaker.exe (PID: 3008)
Reads mouse settings
- Win 10 Tweaker.exe (PID: 3008)
Executes PowerShell scripts
- Win 10 Tweaker.exe (PID: 3008)
Creates files in the Windows directory
- Win 10 Tweaker.exe (PID: 3008)
Uses NETSH.EXE for network configuration
- cmd.exe (PID: 964)
- cmd.exe (PID: 748)
- cmd.exe (PID: 2164)
- cmd.exe (PID: 2172)
Creates files in the driver directory
- Win 10 Tweaker.exe (PID: 3008)
Uses TASKKILL.EXE to kill process
- cmd.exe (PID: 1976)
Creates files in the user directory
- powershell.exe (PID: 2348)
Adds / modifies Windows certificates
- Win 10 Tweaker.exe (PID: 3008)
INFO
Reads the hosts file
- Win 10 Tweaker.exe (PID: 3008)
Reads settings of System Certificates
- Win 10 Tweaker.exe (PID: 3008)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Generic CIL Executable (.NET, Mono, etc.) (82.9) |
|---|---|---|
| .dll | | | Win32 Dynamic Link Library (generic) (7.4) |
| .exe | | | Win32 Executable (generic) (5.1) |
| .exe | | | Generic Win/DOS Executable (2.2) |
| .exe | | | DOS Executable Generic (2.2) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2020:11:20 14:02:50+01:00 |
| PEType: | PE32 |
| LinkerVersion: | 11 |
| CodeSize: | 1456128 |
| InitializedDataSize: | 35328 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x16567e |
| OSVersion: | 4 |
| ImageVersion: | - |
| SubsystemVersion: | 4 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 16.2.0.0 |
| ProductVersionNumber: | 16.2.0.0 |
| FileFlagsMask: | 0x003f |
| FileFlags: | (none) |
| FileOS: | Win32 |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | Neutral |
| CharacterSet: | Unicode |
| Comments: | Win 10 Tweaker |
| CompanyName: | JailbreakVideo |
| FileDescription: | Win 10 Tweaker |
| FileVersion: | 16.2 |
| InternalName: | Win 10 Tweaker.exe |
| LegalCopyright: | Copyright © XpucT |
| LegalTrademarks: | XpucT |
| OriginalFileName: | Win 10 Tweaker.exe |
| ProductName: | Win 10 Tweaker |
| ProductVersion: | 16.2 |
| AssemblyVersion: | 16.2.0.0 |
Summary
| Architecture: | IMAGE_FILE_MACHINE_I386 |
|---|---|
| Subsystem: | IMAGE_SUBSYSTEM_WINDOWS_GUI |
| Compilation Date: | 20-Nov-2020 13:02:50 |
| Comments: | Win 10 Tweaker |
| CompanyName: | JailbreakVideo |
| FileDescription: | Win 10 Tweaker |
| FileVersion: | 16.2 |
| InternalName: | Win 10 Tweaker.exe |
| LegalCopyright: | Copyright © XpucT |
| LegalTrademarks: | XpucT |
| OriginalFilename: | Win 10 Tweaker.exe |
| ProductName: | Win 10 Tweaker |
| ProductVersion: | 16.2 |
| Assembly Version: | 16.2.0.0 |
DOS Header
| Magic number: | MZ |
|---|---|
| Bytes on last page of file: | 0x0090 |
| Pages in file: | 0x0003 |
| Relocations: | 0x0000 |
| Size of header: | 0x0004 |
| Min extra paragraphs: | 0x0000 |
| Max extra paragraphs: | 0xFFFF |
| Initial SS value: | 0x0000 |
| Initial SP value: | 0x00B8 |
| Checksum: | 0x0000 |
| Initial IP value: | 0x0000 |
| Initial CS value: | 0x0000 |
| Overlay number: | 0x0000 |
| OEM identifier: | 0x0000 |
| OEM information: | 0x0000 |
| Address of NE header: | 0x00000080 |
PE Headers
| Signature: | PE |
|---|---|
| Machine: | IMAGE_FILE_MACHINE_I386 |
| Number of sections: | 3 |
| Time date stamp: | 20-Nov-2020 13:02:50 |
| Pointer to Symbol Table: | 0x00000000 |
| Number of symbols: | 0 |
| Size of Optional Header: | 0x00E0 |
| Characteristics: |
|
Sections
Name | Virtual Address | Virtual Size | Raw Size | Charateristics | Entropy |
|---|---|---|---|---|---|
.text | 0x00002000 | 0x00163684 | 0x00163800 | IMAGE_SCN_CNT_CODE, IMAGE_SCN_MEM_EXECUTE, IMAGE_SCN_MEM_READ | 7.99855 |
.rsrc | 0x00166000 | 0x00008780 | 0x00008800 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ | 2.9101 |
.reloc | 0x00170000 | 0x0000000C | 0x00000200 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_DISCARDABLE, IMAGE_SCN_MEM_READ | 0.10191 |
Resources
Title | Entropy | Size | Codepage | Language | Type |
|---|---|---|---|---|---|
1 | 5.23212 | 1304 | UNKNOWN | UNKNOWN | RT_MANIFEST |
2 | 2.46876 | 9640 | UNKNOWN | UNKNOWN | RT_ICON |
3 | 2.53566 | 4264 | UNKNOWN | UNKNOWN | RT_ICON |
4 | 2.67435 | 1128 | UNKNOWN | UNKNOWN | RT_ICON |
32512 | 2.62308 | 62 | UNKNOWN | UNKNOWN | RT_GROUP_ICON |
Imports
mscoree.dll |
Total processes
110
Monitored processes
55
Malicious processes
3
Suspicious processes
4
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 308 | schtasks /change /tn "\Microsoft\Office\OfficeTelemetryAgentFallBack" /disable | C:\Windows\system32\schtasks.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Manages scheduled tasks Exit code: 1 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 600 | netsh advfirewall firewall add rule name="Win 10 Tweaker – Privacy rules 🕵" action=block dir=out remoteip=13.68.31.193,13.66.56.243,13.68.82.8,13.68.92.143,13.73.26.107,13.78.130.220,13.78.232.226,13.78.233.133,13.88.21.125,13.92.194.212,20.44.86.43,20.49.150.241,20.189.74.153,23.99.49.121,23.102.4.253,23.102.21.4,23.103.182.126,40.68.222.212,40.69.153.67,40.70.184.83,40.70.220.248,40.70.221.249,40.77.228.47,40.77.228.87,40.77.228.92,40.77.232.101,40.78.128.150,40.79.85.125,40.90.221.9,40.112.209.200,40.115.3.210,40.115.119.185,40.119.211.203,40.124.34.70,40.127.240.158,51.104.136.2,51.124.78.146,51.140.40.236,51.140.157.153,51.143.53.152,51.143.111.7,51.143.111.81,52.138.204.217,52.138.216.83,52.155.172.105,52.157.234.37,52.158.208.111,52.164.241.205,52.169.189.83,52.170.83.19,52.174.22.246,52.178.147.240,52.178.151.212,52.178.178.16,52.178.223.23,52.183.114.173,52.184.221.185,52.229.39.152,52.230.85.180,52.236.42.239,52.236.43.202,65.52.100.7,65.52.100.9,65.52.100.11,65.52.100.91,65.52.100.92,65.52.100.93,65.52.100.94,65.52.161.64,65.55.29.238,65.55.44.51,65.55.44.54,65.55.44.108,65.55.44.109,65.55.83.120,65.55.113.11,65.55.113.12,65.55.113.13,65.55.176.90,65.55.252.43,65.55.252.63,65.55.252.70,65.55.252.71,65.55.252.72,65.55.252.93,65.55.252.190,65.55.252.202,66.119.147.131,104.41.207.73,104.43.137.66,104.43.139.21,104.43.140.223,104.43.228.53,104.43.228.202,104.43.237.169,104.45.11.195,104.45.214.112,104.46.1.211,104.46.38.64,104.210.4.77,104.210.40.87,104.210.212.243,104.214.35.244,104.214.78.152,131.253.6.87,131.253.6.103,131.253.34.230,131.253.34.234,131.253.34.237,131.253.34.243,131.253.34.246,131.253.34.247,131.253.34.249,131.253.34.252,131.253.34.255,131.253.40.37,134.170.30.202,134.170.30.203,134.170.30.204,134.170.30.221,134.170.52.151,134.170.235.16,157.56.74.250,157.56.91.77,157.56.106.184,157.56.106.185,157.56.106.189,157.56.113.217,157.56.121.89,157.56.124.87,157.56.149.250,157.56.194.72,157.56.194.73,157.56.194.74,168.61.24.141,168.61.146.25,168.61.149.17,168.61.172.71,168.62.187.13,168.63.100.61,168.63.108.233,191.236.155.80,191.237.218.239,191.239.50.18,191.239.50.77,191.239.52.100,191.239.54.52,207.68.166.254 | C:\Windows\system32\netsh.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Network Command Shell Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 748 | "C:\Windows\System32\cmd.exe" /c netsh advfirewall firewall add rule name="Win 10 Tweaker – Privacy rules 🕵" action=block dir=out remoteip=13.68.31.193,13.66.56.243,13.68.82.8,13.68.92.143,13.73.26.107,13.78.130.220,13.78.232.226,13.78.233.133,13.88.21.125,13.92.194.212,20.44.86.43,20.49.150.241,20.189.74.153,23.99.49.121,23.102.4.253,23.102.21.4,23.103.182.126,40.68.222.212,40.69.153.67,40.70.184.83,40.70.220.248,40.70.221.249,40.77.228.47,40.77.228.87,40.77.228.92,40.77.232.101,40.78.128.150,40.79.85.125,40.90.221.9,40.112.209.200,40.115.3.210,40.115.119.185,40.119.211.203,40.124.34.70,40.127.240.158,51.104.136.2,51.124.78.146,51.140.40.236,51.140.157.153,51.143.53.152,51.143.111.7,51.143.111.81,52.138.204.217,52.138.216.83,52.155.172.105,52.157.234.37,52.158.208.111,52.164.241.205,52.169.189.83,52.170.83.19,52.174.22.246,52.178.147.240,52.178.151.212,52.178.178.16,52.178.223.23,52.183.114.173,52.184.221.185,52.229.39.152,52.230.85.180,52.236.42.239,52.236.43.202,65.52.100.7,65.52.100.9,65.52.100.11,65.52.100.91,65.52.100.92,65.52.100.93,65.52.100.94,65.52.161.64,65.55.29.238,65.55.44.51,65.55.44.54,65.55.44.108,65.55.44.109,65.55.83.120,65.55.113.11,65.55.113.12,65.55.113.13,65.55.176.90,65.55.252.43,65.55.252.63,65.55.252.70,65.55.252.71,65.55.252.72,65.55.252.93,65.55.252.190,65.55.252.202,66.119.147.131,104.41.207.73,104.43.137.66,104.43.139.21,104.43.140.223,104.43.228.53,104.43.228.202,104.43.237.169,104.45.11.195,104.45.214.112,104.46.1.211,104.46.38.64,104.210.4.77,104.210.40.87,104.210.212.243,104.214.35.244,104.214.78.152,131.253.6.87,131.253.6.103,131.253.34.230,131.253.34.234,131.253.34.237,131.253.34.243,131.253.34.246,131.253.34.247,131.253.34.249,131.253.34.252,131.253.34.255,131.253.40.37,134.170.30.202,134.170.30.203,134.170.30.204,134.170.30.221,134.170.52.151,134.170.235.16,157.56.74.250,157.56.91.77,157.56.106.184,157.56.106.185,157.56.106.189,157.56.113.217,157.56.121.89,157.56.124.87,157.56.149.250,157.56.194.72,157.56.194.73,157.56.194.74,168.61.24.141,168.61.146.25,168.61.149.17,168.61.172.71,168.62.187.13,168.63.100.61,168.63.108.233,191.236.155.80,191.237.218.239,191.239.50.18,191.239.50.77,191.239.52.100,191.239.54.52,207.68.166.254 | C:\Windows\System32\cmd.exe | — | Win 10 Tweaker.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 876 | netsh int ipv6 isatap show state | C:\Windows\system32\netsh.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Network Command Shell Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 964 | "C:\Windows\System32\cmd.exe" /c netsh advfirewall firewall delete rule name="Win 10 Tweaker – Privacy rules 🕵" | C:\Windows\System32\cmd.exe | — | Win 10 Tweaker.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 1 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 1124 | schtasks /change /tn "\Microsoft\Windows\NetTrace\GatherNetworkInfo" /disable | C:\Windows\system32\schtasks.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Manages scheduled tasks Exit code: 1 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1380 | schtasks /TN \Microsoft\Windows\Maintenance\WinSAT | C:\Windows\system32\schtasks.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Manages scheduled tasks Exit code: 1 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1668 | "cmd.exe" /c chcp 65001 & schtasks /TN \Microsoft\Windows\Maintenance\WinSAT | C:\Windows\system32\cmd.exe | — | Win 10 Tweaker.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 1 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 1696 | taskkill /f /pid "3008" | C:\Windows\system32\taskkill.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Terminates Processes Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1700 | schtasks /TN \Microsoft\Windows\MemoryDiagnostic\CorruptionDetector | C:\Windows\system32\schtasks.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Manages scheduled tasks Exit code: 1 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
Total events
1 013
Read events
478
Write events
535
Delete events
0
Modification events
| (PID) Process: | (3008) Win 10 Tweaker.exe | Key: | HKEY_CURRENT_USER\Software\Win 10 Tweaker |
| Operation: | write | Name: | Skin |
Value: DarkSkin | |||
| (PID) Process: | (3008) Win 10 Tweaker.exe | Key: | HKEY_CURRENT_USER\Software\Win 10 Tweaker |
| Operation: | write | Name: | First Run Agreement |
Value: false | |||
| (PID) Process: | (3008) Win 10 Tweaker.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Classes\w10t |
| Operation: | write | Name: | URL protocol |
Value: | |||
| (PID) Process: | (3008) Win 10 Tweaker.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Classes\w10t\shell\open\command |
| Operation: | write | Name: | (default) |
Value: "C:\Users\admin\AppData\Local\Temp\Win 10 Tweaker.exe" buyknow | |||
| (PID) Process: | (2716) netsh.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\13B\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (2716) netsh.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\13B\52C64B7E |
| Operation: | write | Name: | @%SystemRoot%\system32\dhcpqec.dll,-100 |
Value: DHCP Quarantine Enforcement Client | |||
| (PID) Process: | (2716) netsh.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\13B\52C64B7E |
| Operation: | write | Name: | @%SystemRoot%\system32\dhcpqec.dll,-101 |
Value: Provides DHCP based enforcement for NAP | |||
| (PID) Process: | (2716) netsh.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\13B\52C64B7E |
| Operation: | write | Name: | @%SystemRoot%\system32\dhcpqec.dll,-103 |
Value: 1.0 | |||
| (PID) Process: | (2716) netsh.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\13B\52C64B7E |
| Operation: | write | Name: | @%SystemRoot%\system32\dhcpqec.dll,-102 |
Value: Microsoft Corporation | |||
| (PID) Process: | (2716) netsh.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\13B\52C64B7E |
| Operation: | write | Name: | @%SystemRoot%\system32\napipsec.dll,-1 |
Value: IPsec Relying Party | |||
Executable files
0
Suspicious files
20
Text files
59
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2348 | powershell.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\KIZL9JV2EPMNTJ9IJQCJ.temp | — | |
MD5:— | SHA256:— | |||
| 2604 | csc.exe | C:\Users\admin\AppData\Local\Temp\eoba4xhg\CSC5F864882A3DB4BC29733DBC5522B665.TMP | — | |
MD5:— | SHA256:— | |||
| 3060 | cvtres.exe | C:\Users\admin\AppData\Local\Temp\RES9116.tmp | — | |
MD5:— | SHA256:— | |||
| 2604 | csc.exe | C:\Users\admin\AppData\Local\Temp\eoba4xhg\eoba4xhg.dll | — | |
MD5:— | SHA256:— | |||
| 2604 | csc.exe | C:\Users\admin\AppData\Local\Temp\eoba4xhg\eoba4xhg.out | — | |
MD5:— | SHA256:— | |||
| 2348 | powershell.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\d93f411851d7c929.customDestinations-ms | binary | |
MD5:— | SHA256:— | |||
| 2348 | powershell.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\d93f411851d7c929.customDestinations-ms~RF100496.TMP | binary | |
MD5:— | SHA256:— | |||
| 3008 | Win 10 Tweaker.exe | C:\Windows\System32\GroupPolicy\Machine\Registry.pol | binary | |
MD5:— | SHA256:— | |||
| 3008 | Win 10 Tweaker.exe | C:\Windows\System32\GroupPolicy\GPT.INI | text | |
MD5:— | SHA256:— | |||
| 3008 | Win 10 Tweaker.exe | C:\Windows\System32\GroupPolicy\gpt.ini | text | |
MD5:6427E1627FB697E73DF506A2B5F77D72 | SHA256:3D7852515A0BF5FB21E7BD617587B28631BF49DFE21BA731D567C4C55A6F2F16 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
4
DNS requests
3
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
3008 | Win 10 Tweaker.exe | 87.236.16.98:443 | win10tweaker.pro | Beget Ltd | RU | suspicious |
3008 | Win 10 Tweaker.exe | 151.101.0.133:443 | raw.githubusercontent.com | Fastly | US | malicious |
DNS requests
Domain | IP | Reputation |
|---|---|---|
win10tweaker.pro |
| suspicious |
win10tweaker.com |
| suspicious |
raw.githubusercontent.com |
| shared |