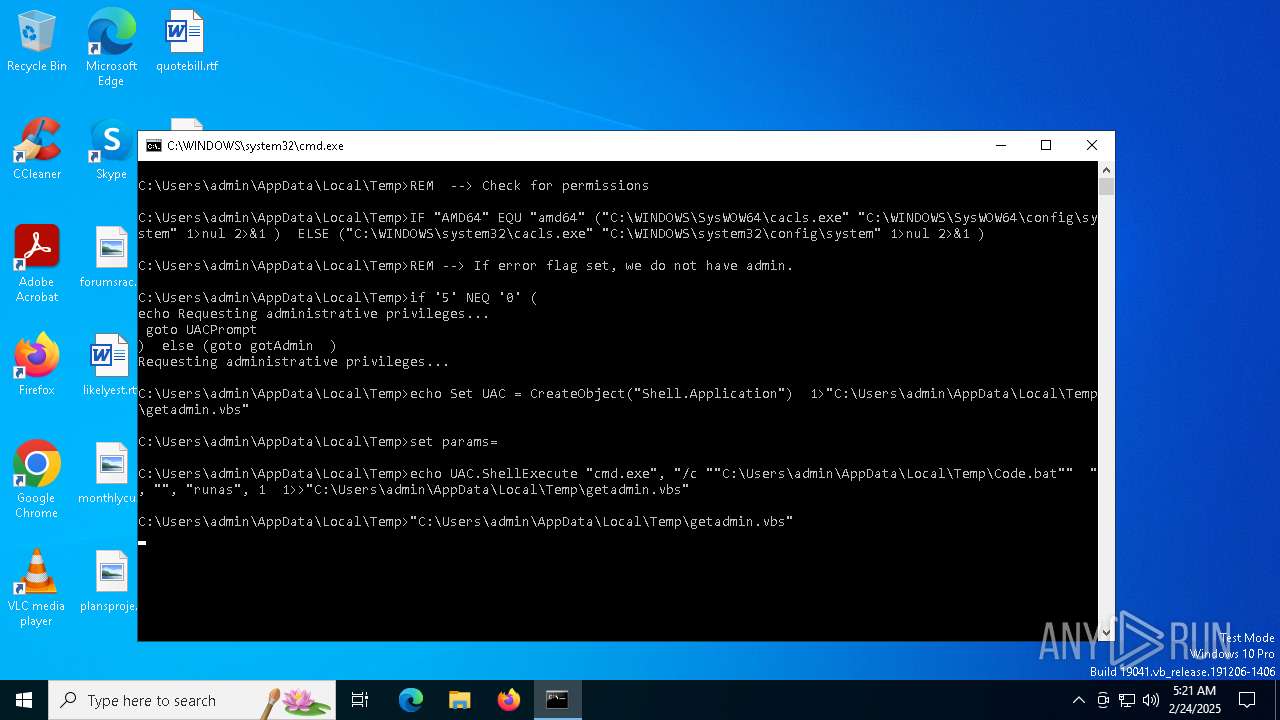
| File name: | Code.bat |
| Full analysis: | https://app.any.run/tasks/6e5e99bd-aea8-4ddf-b8cb-ea2cb76f2002 |
| Verdict: | Malicious activity |
| Analysis date: | February 24, 2025, 05:21:02 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | text/plain |
| File info: | ASCII text, with CRLF line terminators |
| MD5: | 6AB9333091BA7E49709E7A035EAA7475 |
| SHA1: | B7CCF02E32C7CB01DBE5C71EDAA4F18C92A97E66 |
| SHA256: | 8ACD3B3BD702A773C70F7F03750091635A1C9991A41F0A8565D721EA30655723 |
| SSDEEP: | 96:lVeGI8hYOF4/dfyVMS1mpLYwwdio4Pg4cstOtAQ:lVeGIHi4/dfye9VYjn4I4csI |
MALICIOUS
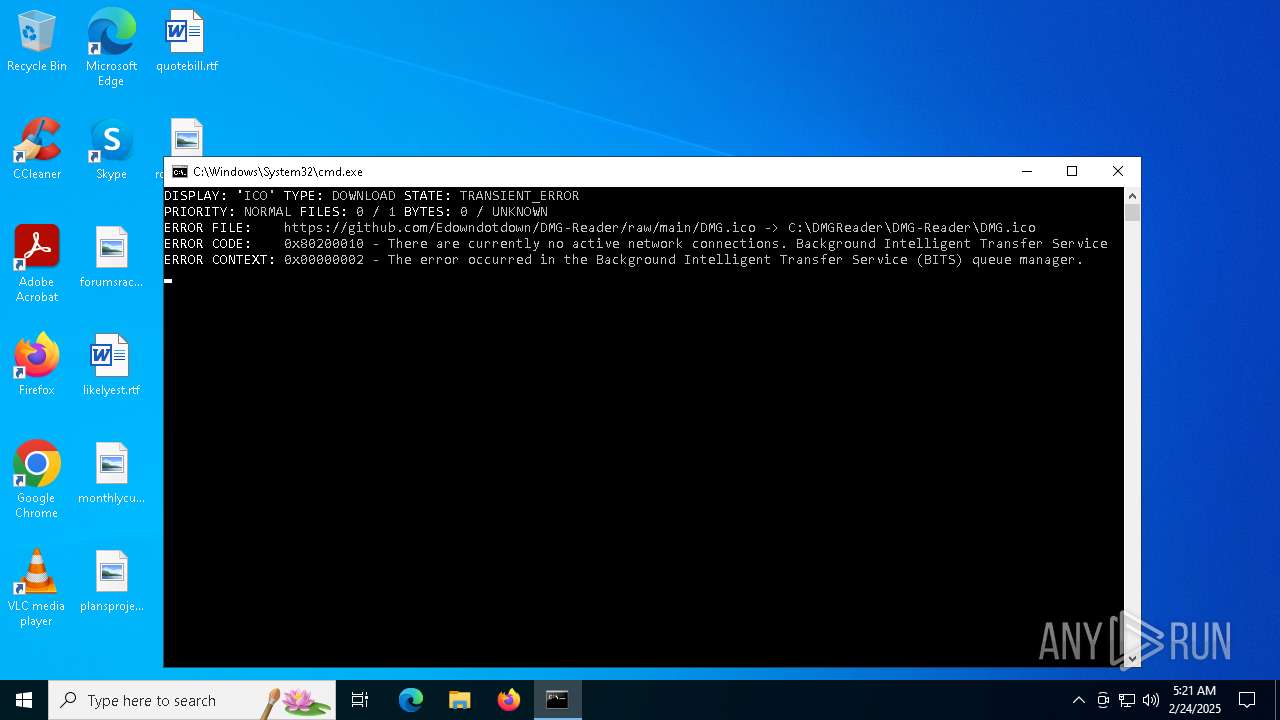
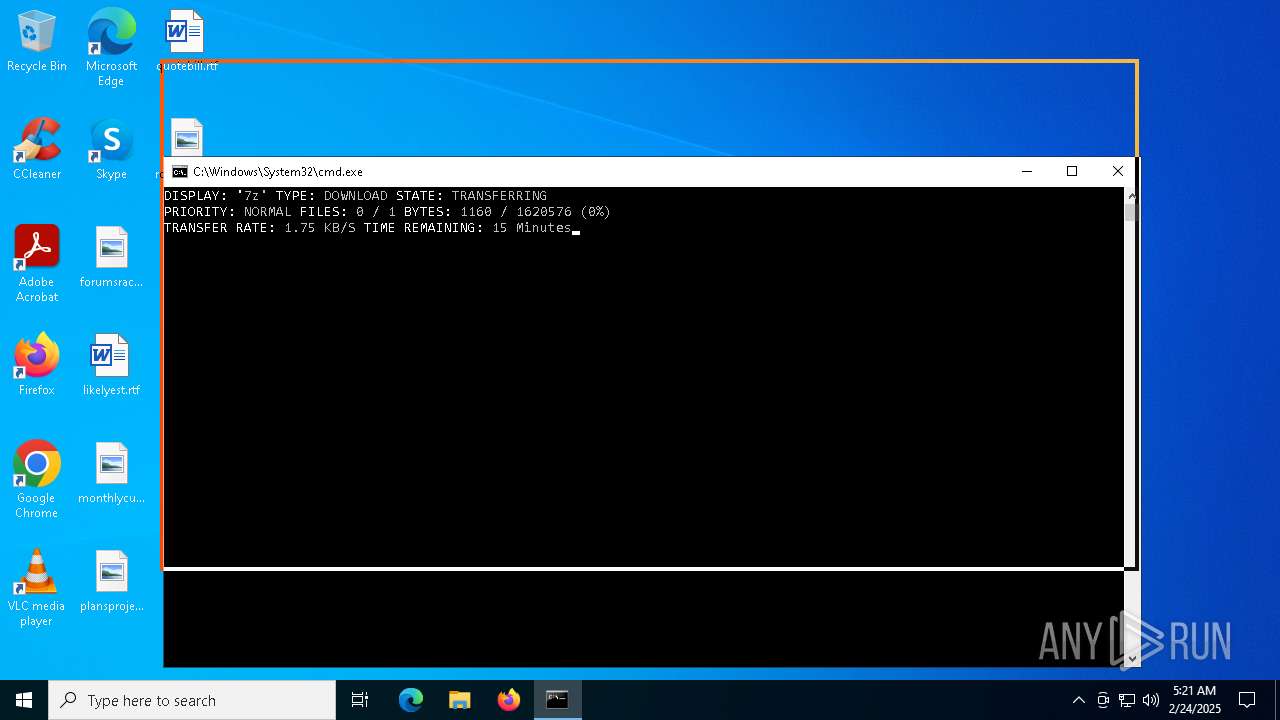
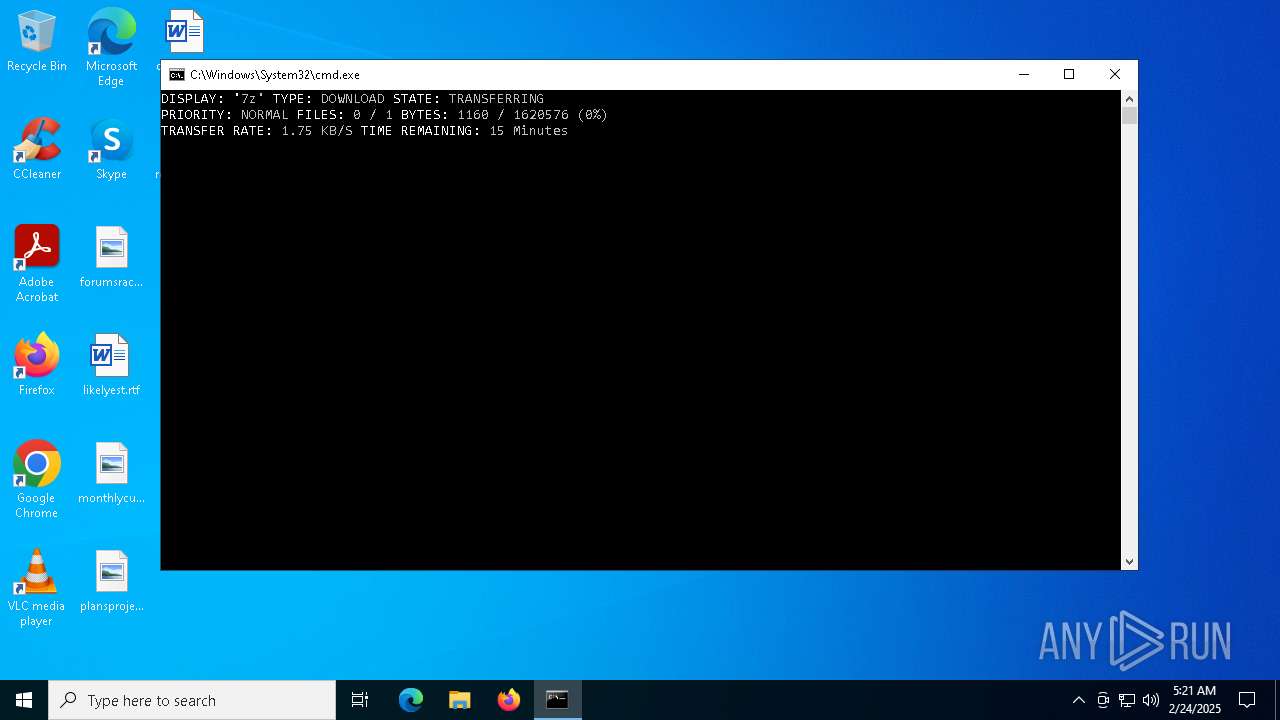
Downloads files via BITSADMIN.EXE
- cmd.exe (PID: 6696)
SUSPICIOUS
Runs shell command (SCRIPT)
- wscript.exe (PID: 6472)
The process executes VB scripts
- cmd.exe (PID: 6336)
Uses ICACLS.EXE to modify access control lists
- cmd.exe (PID: 6336)
- cmd.exe (PID: 6696)
Executing commands from a ".bat" file
- wscript.exe (PID: 6472)
Starts CMD.EXE for commands execution
- wscript.exe (PID: 6472)
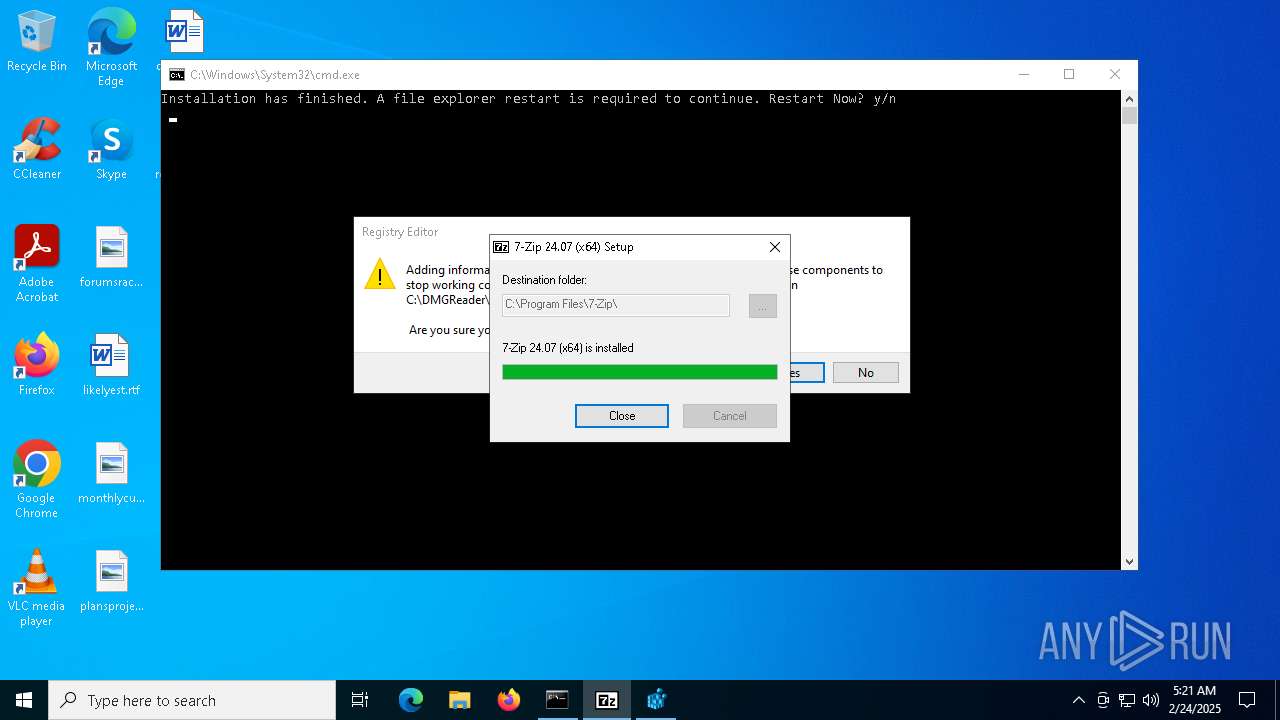
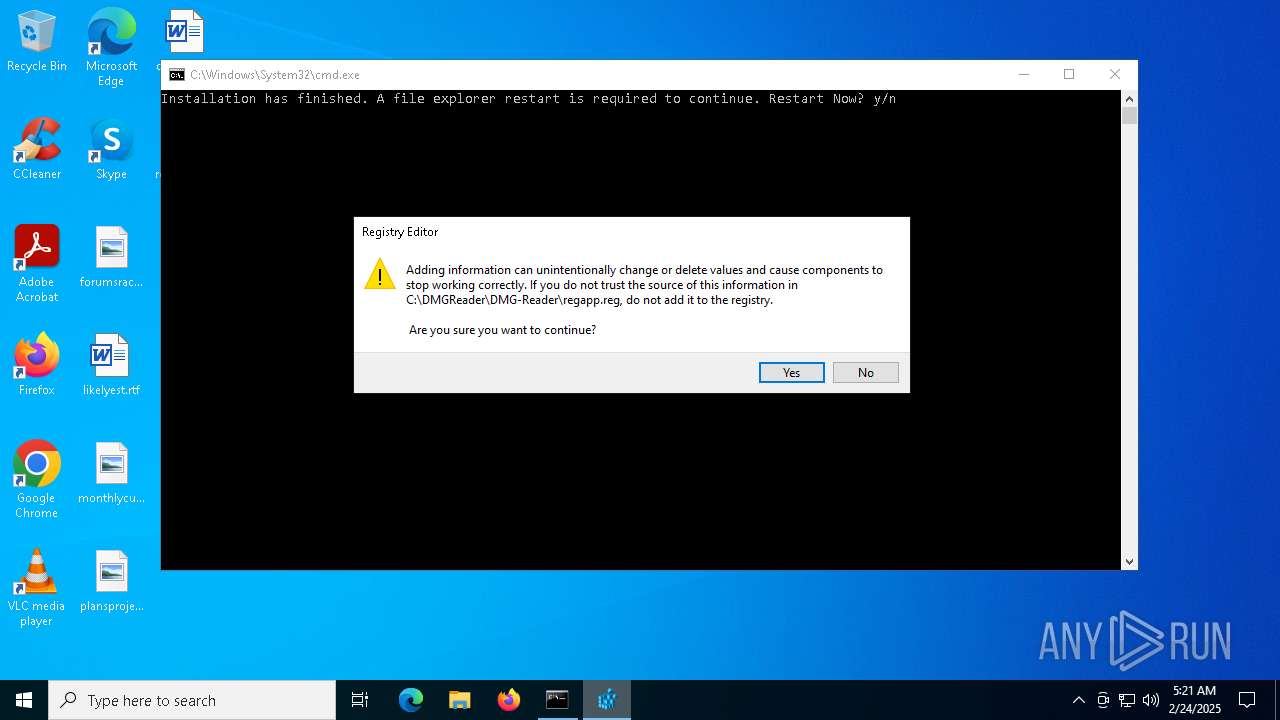
Uses REG/REGEDIT.EXE to modify registry
- cmd.exe (PID: 6696)
Executable content was dropped or overwritten
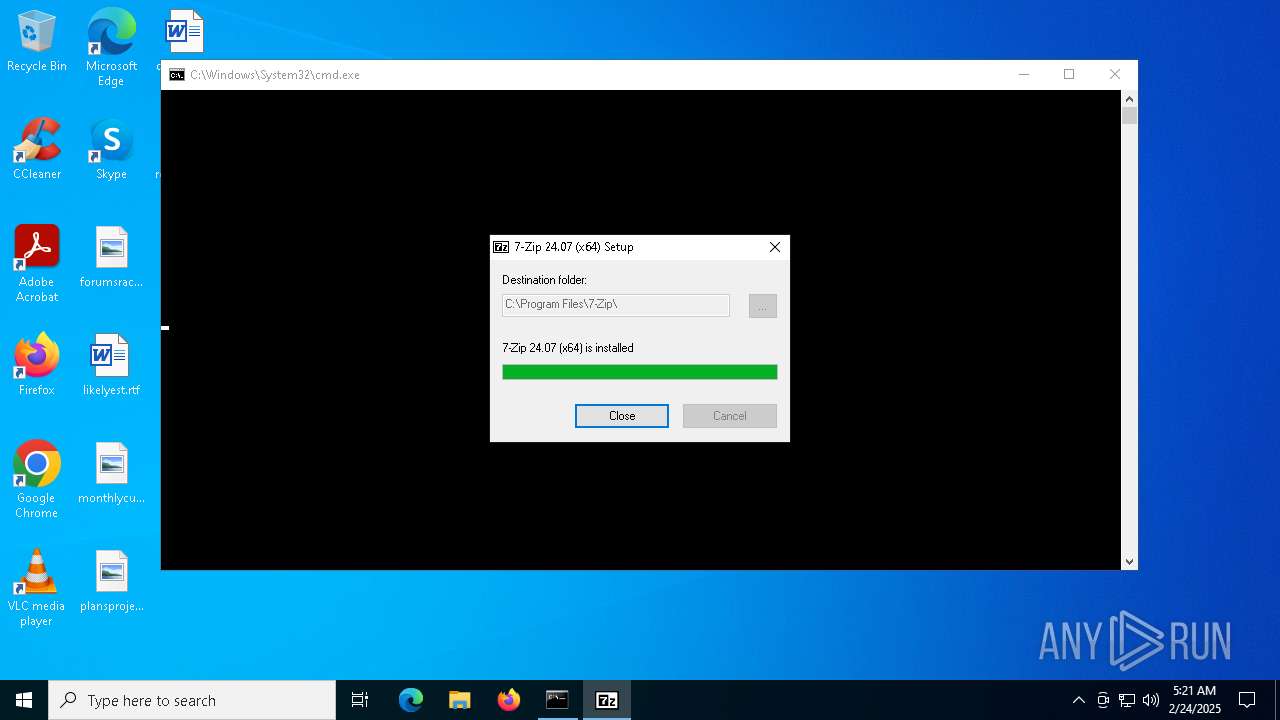
- 7z.exe (PID: 6448)
Creates/Modifies COM task schedule object
- 7z.exe (PID: 6448)
Creates a software uninstall entry
- 7z.exe (PID: 6448)
- regedit.exe (PID: 4932)
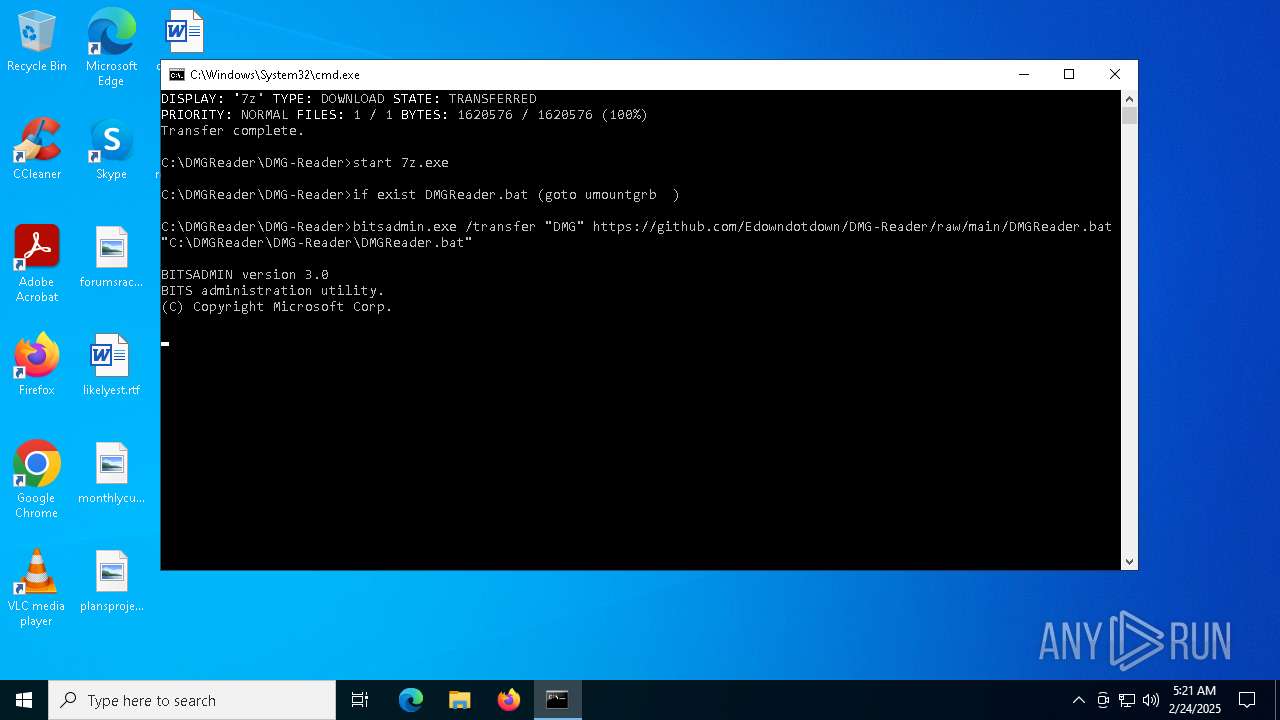
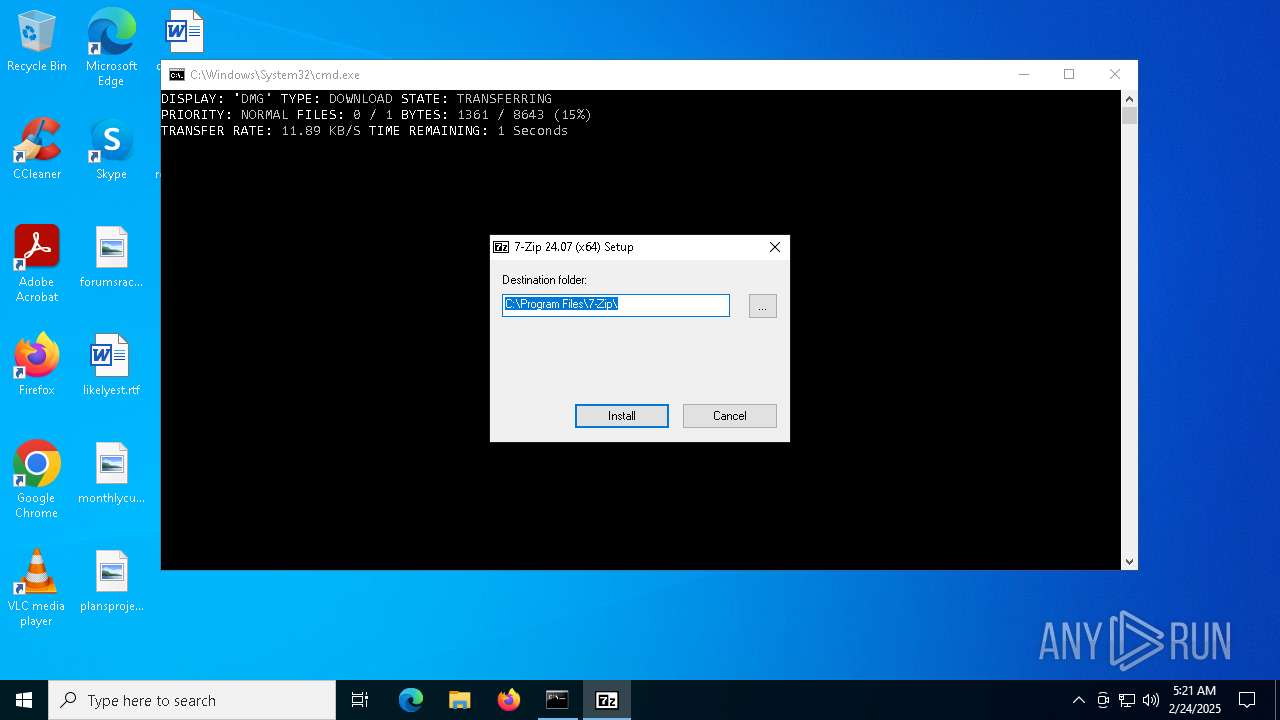
Drops 7-zip archiver for unpacking
- 7z.exe (PID: 6448)
Process copies executable file
- cmd.exe (PID: 6696)
Uses TASKKILL.EXE to kill process
- cmd.exe (PID: 6696)
The process executes via Task Scheduler
- explorer.exe (PID: 5604)
Reads security settings of Internet Explorer
- StartMenuExperienceHost.exe (PID: 3772)
Reads the date of Windows installation
- StartMenuExperienceHost.exe (PID: 3772)
- SearchApp.exe (PID: 1576)
INFO
Checks supported languages
- 7z.exe (PID: 6448)
- StartMenuExperienceHost.exe (PID: 3772)
- TextInputHost.exe (PID: 6460)
- SearchApp.exe (PID: 1576)
Reads the computer name
- 7z.exe (PID: 6448)
- TextInputHost.exe (PID: 6460)
- StartMenuExperienceHost.exe (PID: 3772)
- SearchApp.exe (PID: 1576)
Creates files in the program directory
- 7z.exe (PID: 6448)
The sample compiled with english language support
- 7z.exe (PID: 6448)
Reads security settings of Internet Explorer
- explorer.exe (PID: 5604)
Checks proxy server information
- SearchApp.exe (PID: 1576)
- explorer.exe (PID: 5604)
Process checks computer location settings
- StartMenuExperienceHost.exe (PID: 3772)
- SearchApp.exe (PID: 1576)
Reads the machine GUID from the registry
- SearchApp.exe (PID: 1576)
Reads Environment values
- SearchApp.exe (PID: 1576)
Reads the software policy settings
- SearchApp.exe (PID: 1576)
Creates files or folders in the user directory
- explorer.exe (PID: 5604)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
164
Monitored processes
26
Malicious processes
4
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1576 | "C:\WINDOWS\SystemApps\Microsoft.Windows.Search_cw5n1h2txyewy\SearchApp.exe" -ServerName:CortanaUI.AppX8z9r6jm96hw4bsbneegw0kyxx296wr9t.mca | C:\Windows\SystemApps\Microsoft.Windows.Search_cw5n1h2txyewy\SearchApp.exe | svchost.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Search application Version: 10.0.19041.3996 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2324 | xcopy "C:\Users\admin\AppData\Local\Temp\Setup.bat" "C:\DMGReader\DMG-Reader" | C:\Windows\System32\xcopy.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Extended Copy Utility Exit code: 4 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3772 | "C:\WINDOWS\SystemApps\Microsoft.Windows.StartMenuExperienceHost_cw5n1h2txyewy\StartMenuExperienceHost.exe" -ServerName:App.AppXywbrabmsek0gm3tkwpr5kwzbs55tkqay.mca | C:\Windows\SystemApps\Microsoft.Windows.StartMenuExperienceHost_cw5n1h2txyewy\StartMenuExperienceHost.exe | — | svchost.exe | |||||||||||
User: admin Integrity Level: MEDIUM Modules
| |||||||||||||||
| 4624 | explorer | C:\Windows\explorer.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Explorer Exit code: 2 Version: 10.0.19041.3758 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4888 | C:\WINDOWS\System32\mobsync.exe -Embedding | C:\Windows\System32\mobsync.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Sync Center Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
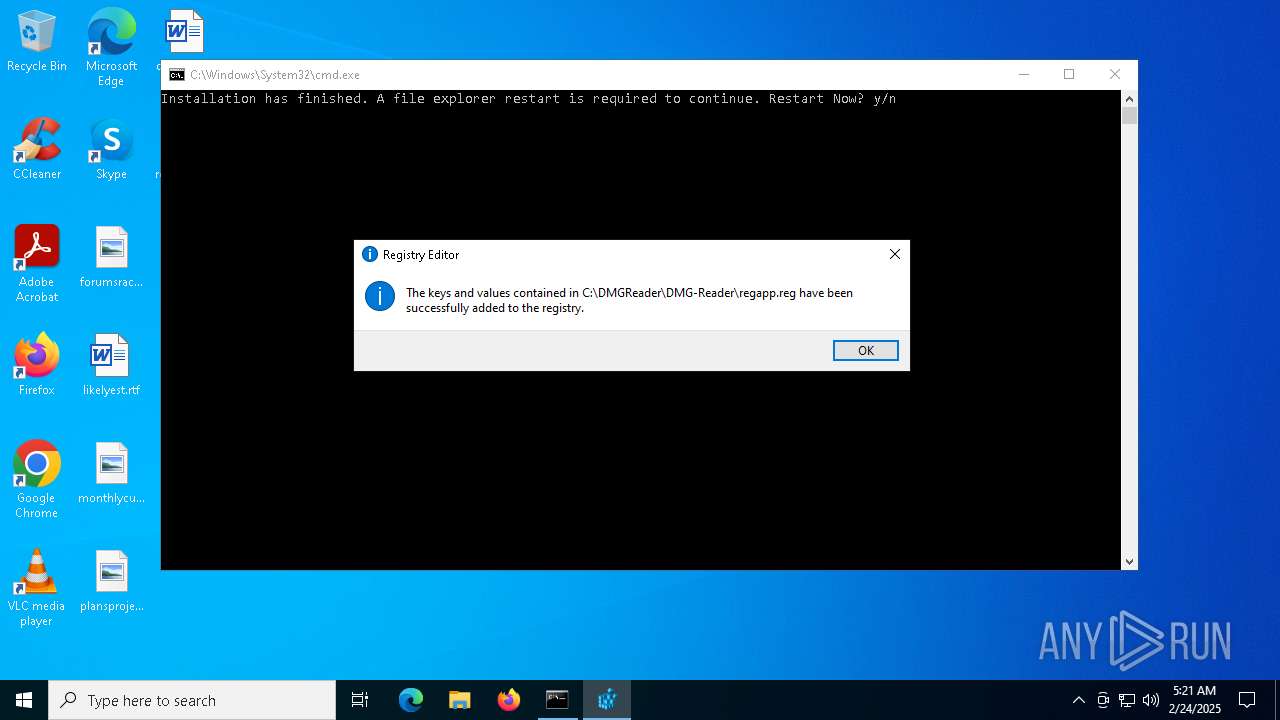
| 4932 | "regedit.exe" "C:\DMGReader\DMG-Reader\regapp.reg" | C:\Windows\regedit.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Registry Editor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4944 | choice /c yn /n /m " " | C:\Windows\System32\choice.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Offers the user a choice Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5604 | "C:\WINDOWS\explorer.exe" /NoUACCheck | C:\Windows\explorer.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Explorer Version: 10.0.19041.3758 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5748 | taskkill /im explorer.exe /f | C:\Windows\System32\taskkill.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Terminates Processes Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6336 | C:\WINDOWS\system32\cmd.exe /c ""C:\Users\admin\AppData\Local\Temp\Code.bat" " | C:\Windows\System32\cmd.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
26 977
Read events
26 705
Write events
247
Delete events
25
Modification events
| (PID) Process: | (6336) cmd.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\FileExts\.vbs\OpenWithProgids |
| Operation: | write | Name: | VBSFile |
Value: | |||
| (PID) Process: | (6696) cmd.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer |
| Operation: | write | Name: | GlobalAssocChangedCounter |
Value: 18 | |||
| (PID) Process: | (6812) setx.exe | Key: | HKEY_CURRENT_USER\Environment |
| Operation: | write | Name: | WorkingDIRDMG |
Value: C:\DMGReader\DMG-Reader | |||
| (PID) Process: | (6448) 7z.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\7-Zip |
| Operation: | write | Name: | Path64 |
Value: C:\Program Files\7-Zip\ | |||
| (PID) Process: | (6448) 7z.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\7-Zip |
| Operation: | write | Name: | Path |
Value: C:\Program Files\7-Zip\ | |||
| (PID) Process: | (6448) 7z.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\7-Zip |
| Operation: | write | Name: | Path64 |
Value: C:\Program Files\7-Zip\ | |||
| (PID) Process: | (6448) 7z.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\7-Zip |
| Operation: | write | Name: | Path |
Value: C:\Program Files\7-Zip\ | |||
| (PID) Process: | (6448) 7z.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Classes\WOW6432Node\CLSID\{23170F69-40C1-278A-1000-000100020000}\InprocServer32 |
| Operation: | write | Name: | ThreadingModel |
Value: Apartment | |||
| (PID) Process: | (6448) 7z.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Classes\CLSID\{23170F69-40C1-278A-1000-000100020000}\InprocServer32 |
| Operation: | write | Name: | ThreadingModel |
Value: Apartment | |||
| (PID) Process: | (6448) 7z.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Windows\CurrentVersion\Shell Extensions\Approved |
| Operation: | write | Name: | {23170F69-40C1-278A-1000-000100020000} |
Value: 7-Zip Shell Extension | |||
Executable files
13
Suspicious files
56
Text files
206
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 6448 | 7z.exe | C:\Program Files\7-Zip\7-zip.chm | binary | |
MD5:B79894FBEE3C882C3EFC71FF3D4A21BB | SHA256:2D55CA494A8B6DCC739D84BDD112F5C50D612F8ABF409C9FB5F2B5C2C84C37A0 | |||
| 6336 | cmd.exe | C:\Users\admin\AppData\Local\Temp\getadmin.vbs | text | |
MD5:D14A6C18536B08C2D91CC10129CEC2CA | SHA256:88F0E55BE41422957E8F4FEC8CAF0F9ED4E68D1F0290171BA8F4BD26C19FA17D | |||
| 6448 | 7z.exe | C:\Program Files\7-Zip\descript.ion | text | |
MD5:EB7E322BDC62614E49DED60E0FB23845 | SHA256:1DA513F5A4E8018B9AE143884EB3EAF72454B606FD51F2401B7CFD9BE4DBBF4F | |||
| 6448 | 7z.exe | C:\Program Files\7-Zip\Lang\ba.txt | text | |
MD5:387FF78CF5F524FC44640F3025746145 | SHA256:8A85C3FCB5F81157490971EE4F5E6B9E4F80BE69A802EBED04E6724CE859713F | |||
| 6448 | 7z.exe | C:\Program Files\7-Zip\Lang\ar.txt | text | |
MD5:5747381DC970306051432B18FB2236F2 | SHA256:85A26C7B59D6D9932F71518CCD03ECEEBA42043CB1707719B72BFC348C1C1D72 | |||
| 6448 | 7z.exe | C:\Program Files\7-Zip\History.txt | text | |
MD5:553A02739D516379833451440076F884 | SHA256:83B1AE6D3486C2653766A28806AC110C9A0AFDE17020CA6AA0B7550A2F10E147 | |||
| 6448 | 7z.exe | C:\Program Files\7-Zip\Lang\an.txt | text | |
MD5:F16218139E027338A16C3199091D0600 | SHA256:3AB9F7AACD38C4CDE814F86BC37EEC2B9DF8D0DDDB95FC1D09A5F5BCB11F0EEB | |||
| 6448 | 7z.exe | C:\Program Files\7-Zip\Lang\az.txt | text | |
MD5:3C297FBE9B1ED5582BEABFC112B55523 | SHA256:055EC86AED86ABBDBD52D8E99FEC6E868D073A6DF92C60225ADD16676994C314 | |||
| 6448 | 7z.exe | C:\Program Files\7-Zip\Lang\af.txt | text | |
MD5:DF216FAE5B13D3C3AFE87E405FD34B97 | SHA256:9CF684EA88EA5A479F510750E4089AEE60BBB2452AA85285312BAFCC02C10A34 | |||
| 6448 | 7z.exe | C:\Program Files\7-Zip\Lang\ast.txt | text | |
MD5:1CF6411FF9154A34AFB512901BA3EE02 | SHA256:F5F2174DAF36E65790C7F0E9A4496B12E14816DAD2EE5B1D48A52307076BE35F | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
10
TCP/UDP connections
48
DNS requests
27
Threats
1
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
4712 | MoUsoCoreWorker.exe | GET | 200 | 23.216.77.25:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
904 | svchost.exe | GET | 200 | 23.216.77.25:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
4712 | MoUsoCoreWorker.exe | GET | 200 | 2.23.181.156:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
904 | svchost.exe | GET | 200 | 2.23.181.156:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
5064 | SearchApp.exe | GET | 200 | 184.30.131.245:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
6340 | SIHClient.exe | GET | 200 | 23.219.150.101:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
1176 | svchost.exe | GET | 200 | 184.30.131.245:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
6340 | SIHClient.exe | GET | 200 | 23.219.150.101:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
4124 | backgroundTaskHost.exe | GET | 200 | 2.23.77.188:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAUZZSZEml49Gjh0j13P68w%3D | unknown | — | — | whitelisted |
7108 | backgroundTaskHost.exe | GET | 200 | 2.23.77.188:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAUZZSZEml49Gjh0j13P68w%3D | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
1224 | RUXIMICS.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
— | — | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4712 | MoUsoCoreWorker.exe | 23.216.77.25:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
904 | svchost.exe | 23.216.77.25:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
4712 | MoUsoCoreWorker.exe | 2.23.181.156:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
904 | svchost.exe | 2.23.181.156:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
3160 | svchost.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
904 | svchost.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
www.bing.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
github.com |
| whitelisted |
raw.githubusercontent.com |
| whitelisted |
go.microsoft.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2192 | svchost.exe | Not Suspicious Traffic | INFO [ANY.RUN] Attempting to access raw user content on GitHub |