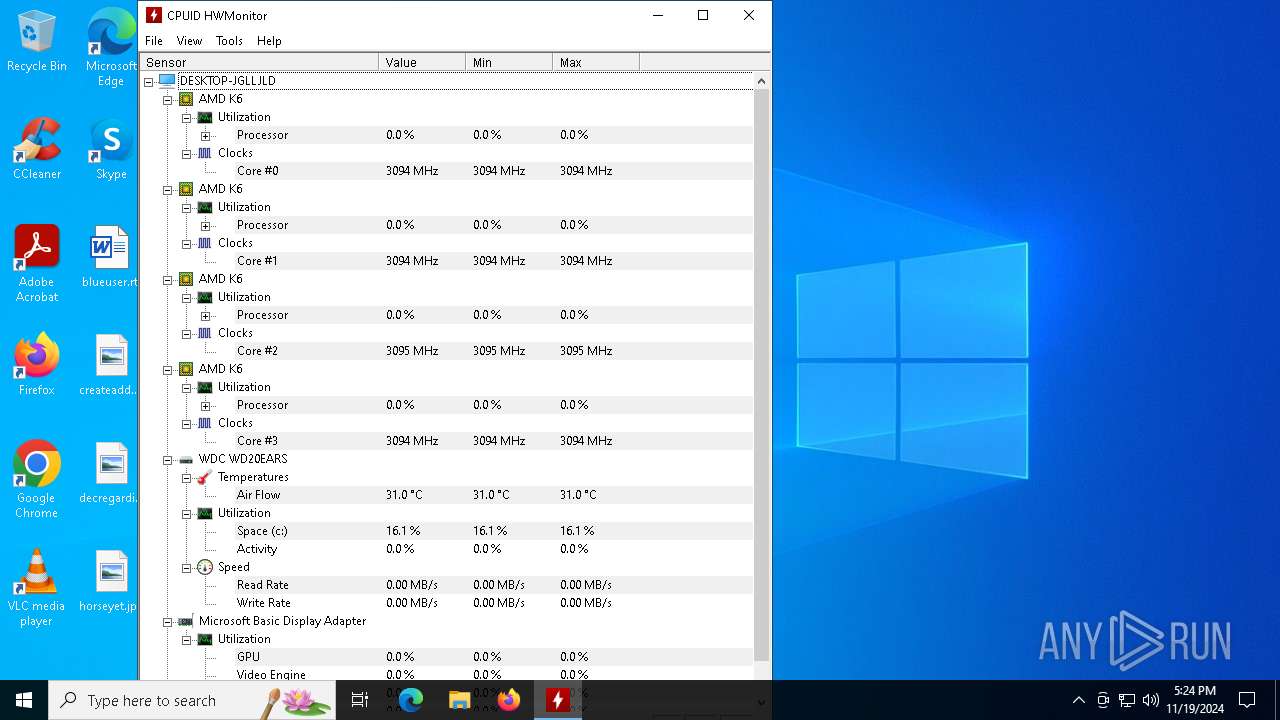
| File name: | HWMonitor_x64.exe |
| Full analysis: | https://app.any.run/tasks/e0038c61-10c7-4b06-bd05-3d404e11201b |
| Verdict: | Malicious activity |
| Analysis date: | November 19, 2024, 17:23:38 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Indicators: | |
| MIME: | application/vnd.microsoft.portable-executable |
| File info: | PE32+ executable (GUI) x86-64, for MS Windows, 5 sections |
| MD5: | 38E5BF546D2FBA945C7B1B46364C28D9 |
| SHA1: | C6A61A00AD881FFAF8A380EF6CB4515347BABE78 |
| SHA256: | 8ABF71CB17E24BCAF33BA47C0C65DC91D4E2CB3FD9DE0F08228CBED303991FC2 |
| SSDEEP: | 98304:IEnT1pjdLr2tyf9YrRONmbVrEO+IAMFn4F1SyFrI4+CkLOR1qx:PU |
MALICIOUS
No malicious indicators.SUSPICIOUS
Executable content was dropped or overwritten
- HWMonitor_x64.exe (PID: 644)
Drops a system driver (possible attempt to evade defenses)
- HWMonitor_x64.exe (PID: 644)
INFO
No info indicators.
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win64 Executable (generic) (18) |
|---|---|---|
| .exe | | | Win32 Executable (generic) (2.9) |
| .exe | | | Generic Win/DOS Executable (1.3) |
| .exe | | | DOS Executable Generic (1.3) |
EXIF
EXE
| MachineType: | AMD AMD64 |
|---|---|
| TimeStamp: | 2023:09:01 14:49:13+00:00 |
| ImageFileCharacteristics: | No relocs, Executable, Large address aware |
| PEType: | PE32+ |
| LinkerVersion: | 9 |
| CodeSize: | 1613312 |
| InitializedDataSize: | 1306112 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x149198 |
| OSVersion: | 5.2 |
| ImageVersion: | - |
| SubsystemVersion: | 5.2 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 1.5.2.0 |
| ProductVersionNumber: | 1.5.2.0 |
| FileFlagsMask: | 0x003f |
| FileFlags: | (none) |
| FileOS: | Win32 |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | English (U.S.) |
| CharacterSet: | Windows, Latin1 |
| CompanyName: | CPUID |
| FileDescription: | HWMonitor |
| FileVersion: | 1, 5, 2, 0 |
| InternalName: | HWMonitor.exe |
| LegalCopyright: | (c)2008-2023 CPUID. All rights reserved. |
| OriginalFileName: | HWMonitor.exe |
| ProductName: | CPUID Hardware Monitor |
| ProductVersion: | 1, 5, 2, 0 |
Total processes
118
Monitored processes
2
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 644 | "C:\Users\admin\Desktop\HWMonitor_x64.exe" | C:\Users\admin\Desktop\HWMonitor_x64.exe | explorer.exe | ||||||||||||
User: admin Company: CPUID Integrity Level: HIGH Description: HWMonitor Version: 1, 5, 2, 0 Modules
| |||||||||||||||
| 772 | "C:\Users\admin\Desktop\HWMonitor_x64.exe" | C:\Users\admin\Desktop\HWMonitor_x64.exe | — | explorer.exe | |||||||||||
User: admin Company: CPUID Integrity Level: MEDIUM Description: HWMonitor Exit code: 3221226540 Version: 1, 5, 2, 0 Modules
| |||||||||||||||
Total events
3 507
Read events
3 504
Write events
3
Delete events
0
Modification events
| (PID) Process: | (644) HWMonitor_x64.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Content |
| Operation: | write | Name: | CachePrefix |
Value: | |||
| (PID) Process: | (644) HWMonitor_x64.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (644) HWMonitor_x64.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
Executable files
1
Suspicious files
2
Text files
1
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 644 | HWMonitor_x64.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\INetCache\IE\RR3E01RZ\cpuid[1].ver | text | |
MD5:03227385FB57A2325464E3259C1D0BD1 | SHA256:1B1D07CB419EDA8BAED1C9309B849025DCBD3696880D93B74F85AEDB75A26855 | |||
| 644 | HWMonitor_x64.exe | C:\Windows\Temp\cpuz158\cpuz158_x64.sys | executable | |
MD5:2A5A72F76452C1DF305B868457324C9E | SHA256:B14C360AF8730CDE304650E925824190EB2D5147A2620F325A3BB5BBCEE2ED14 | |||
| 644 | HWMonitor_x64.exe | C:\Windows\INF\basicrender.PNF | binary | |
MD5:0BB5B50091E98FCFFCD0D9DD769EBEBA | SHA256:52B29BB8ADA5E61AA19E6007583E10814BB12DE04EB0FE2091B0D9F84201AD6E | |||
| 644 | HWMonitor_x64.exe | C:\Windows\INF\display.PNF | binary | |
MD5:DD37478797865A32A1737EF5B1EB28A2 | SHA256:EA142340830BE9D9C18B962E2AFB853244336AAE95E404B13140078901C0A0E2 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
5
TCP/UDP connections
18
DNS requests
7
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
2396 | RUXIMICS.exe | GET | 200 | 23.53.40.176:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
2396 | RUXIMICS.exe | GET | 200 | 23.37.237.227:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 195.154.81.43:443 | https://download.cpuid.com/cpuid.ver | unknown | text | 142 b | whitelisted |
4712 | MoUsoCoreWorker.exe | GET | 200 | 23.53.40.176:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
4712 | MoUsoCoreWorker.exe | GET | 200 | 23.37.237.227:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
2396 | RUXIMICS.exe | 40.127.240.158:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | IE | unknown |
4712 | MoUsoCoreWorker.exe | 40.127.240.158:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | IE | unknown |
4932 | svchost.exe | 40.127.240.158:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | IE | unknown |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
644 | HWMonitor_x64.exe | 195.154.81.43:443 | download.cpuid.com | Online S.a.s. | FR | whitelisted |
2396 | RUXIMICS.exe | 23.53.40.176:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
4712 | MoUsoCoreWorker.exe | 23.53.40.176:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
4932 | svchost.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4712 | MoUsoCoreWorker.exe | 23.37.237.227:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
google.com |
| whitelisted |
download.cpuid.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
settings-win.data.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
self.events.data.microsoft.com |
| whitelisted |