| File name: | Receipt(998).docm |
| Full analysis: | https://app.any.run/tasks/a2db28dd-41c0-4429-86eb-a510bc4c502f |
| Verdict: | Malicious activity |
| Analysis date: | December 14, 2018, 12:49:35 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/vnd.openxmlformats-officedocument.wordprocessingml.document |
| File info: | Microsoft Word 2007+ |
| MD5: | 7B34D88349EF75082B746CBD42BB8202 |
| SHA1: | 6F792EBFAD913B98D23BDEE33C796A822209A99B |
| SHA256: | 8AABB3E77B4D3A75A6CC1C7A5EF7C2D9FC7231EF0D890A2C14C8ADF13D3CCCA4 |
| SSDEEP: | 768:3FJVdNrh6q5+F76htUy59j1Ji8JoBXQbV/T:37hy7MhJI2 |
MALICIOUS
Unusual execution from Microsoft Office
- WINWORD.EXE (PID: 2964)
SUSPICIOUS
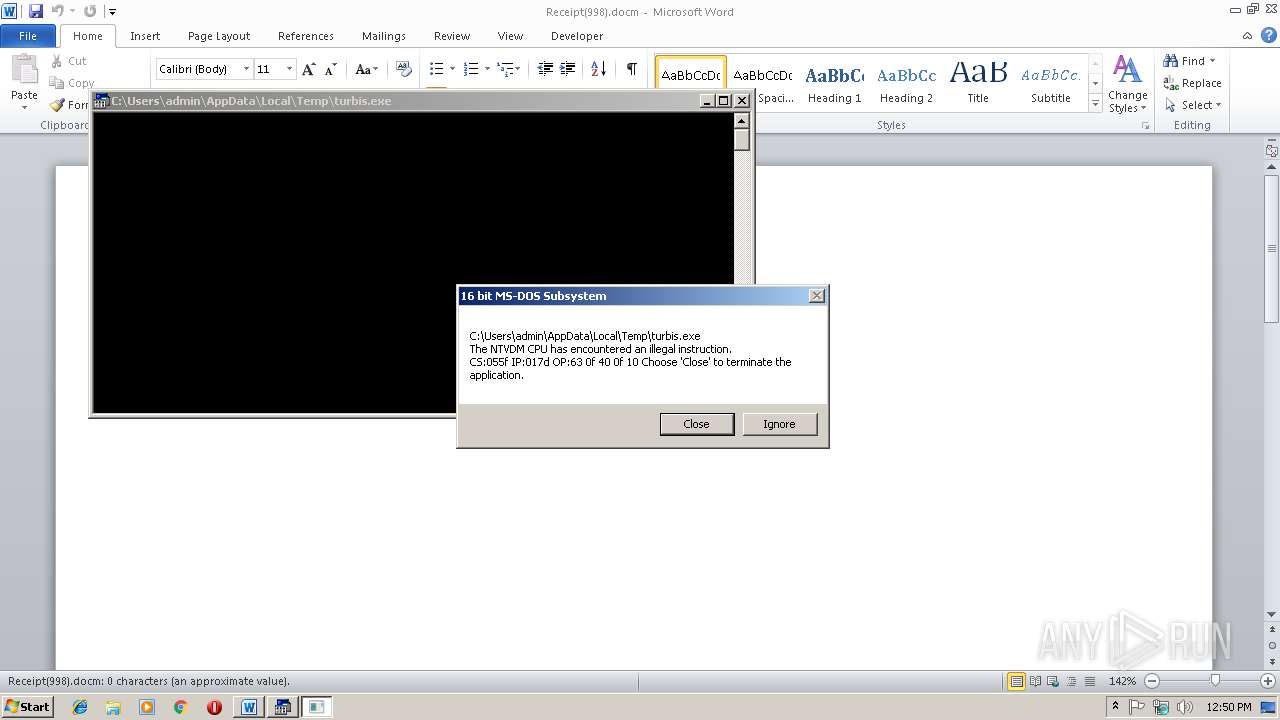
Executes application which crashes
- WINWORD.EXE (PID: 2964)
Unusual connect from Microsoft Office
- WINWORD.EXE (PID: 2964)
INFO
Reads Microsoft Office registry keys
- WINWORD.EXE (PID: 2964)
Creates files in the user directory
- WINWORD.EXE (PID: 2964)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .docm | | | Word Microsoft Office Open XML Format document (with Macro) (53.6) |
|---|---|---|
| .docx | | | Word Microsoft Office Open XML Format document (24.2) |
| .zip | | | Open Packaging Conventions container (18) |
| .zip | | | ZIP compressed archive (4.1) |
EXIF
ZIP
| ZipRequiredVersion: | 20 |
|---|---|
| ZipBitFlag: | 0x0006 |
| ZipCompression: | Deflated |
| ZipModifyDate: | 1980:01:01 00:00:00 |
| ZipCRC: | 0x4dc12e6a |
| ZipCompressedSize: | 419 |
| ZipUncompressedSize: | 1563 |
| ZipFileName: | [Content_Types].xml |
XMP
| Creator: | 1 |
|---|
XML
| LastModifiedBy: | 1 |
|---|---|
| RevisionNumber: | 2 |
| CreateDate: | 2016:08:11 12:37:00Z |
| ModifyDate: | 2016:08:11 12:37:00Z |
| Template: | Normal |
| TotalEditTime: | - |
| Pages: | 1 |
| Words: | - |
| Characters: | - |
| Application: | Microsoft Office Word |
| DocSecurity: | None |
| Lines: | - |
| Paragraphs: | - |
| ScaleCrop: | No |
| Company: | Home |
| LinksUpToDate: | No |
| CharactersWithSpaces: | - |
| SharedDoc: | No |
| HyperlinksChanged: | No |
| AppVersion: | 14 |
Total processes
33
Monitored processes
2
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1824 | "C:\Windows\system32\ntvdm.exe" -i1 | C:\Windows\system32\ntvdm.exe | — | WINWORD.EXE | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: NTVDM.EXE Exit code: 255 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2964 | "C:\Program Files\Microsoft Office\Office14\WINWORD.EXE" /n "C:\Users\admin\AppData\Local\Temp\Receipt(998).docm" | C:\Program Files\Microsoft Office\Office14\WINWORD.EXE | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Word Exit code: 0 Version: 14.0.6024.1000 Modules
| |||||||||||||||
Total events
1 061
Read events
731
Write events
325
Delete events
5
Modification events
| (PID) Process: | (2964) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Word\Resiliency\StartupItems |
| Operation: | write | Name: | j#% |
Value: 6A232500940B0000010000000000000000000000 | |||
| (PID) Process: | (2964) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1033 |
Value: Off | |||
| (PID) Process: | (2964) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1033 |
Value: On | |||
| (PID) Process: | (2964) WINWORD.EXE | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Installer\UserData\S-1-5-18\Products\00004109D30000000000000000F01FEC\Usage |
| Operation: | write | Name: | WORDFiles |
Value: 1301151774 | |||
| (PID) Process: | (2964) WINWORD.EXE | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Installer\UserData\S-1-5-18\Products\00004109D30000000000000000F01FEC\Usage |
| Operation: | write | Name: | ProductFiles |
Value: 1301151888 | |||
| (PID) Process: | (2964) WINWORD.EXE | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Installer\UserData\S-1-5-18\Products\00004109D30000000000000000F01FEC\Usage |
| Operation: | write | Name: | ProductFiles |
Value: 1301151889 | |||
| (PID) Process: | (2964) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Word |
| Operation: | write | Name: | MTTT |
Value: 940B00001CAC3E84AB93D40100000000 | |||
| (PID) Process: | (2964) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Word\Resiliency\StartupItems |
| Operation: | write | Name: | !%% |
Value: 21252500940B000004000000000000008C00000001000000840000003E0043003A005C00550073006500720073005C00610064006D0069006E005C0041007000700044006100740061005C0052006F0061006D0069006E0067005C004D006900630072006F0073006F00660074005C00540065006D0070006C0061007400650073005C004E006F0072006D0061006C002E0064006F0074006D00000000000000 | |||
| (PID) Process: | (2964) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Word\Resiliency\StartupItems |
| Operation: | delete value | Name: | !%% |
Value: 21252500940B000004000000000000008C00000001000000840000003E0043003A005C00550073006500720073005C00610064006D0069006E005C0041007000700044006100740061005C0052006F0061006D0069006E0067005C004D006900630072006F0073006F00660074005C00540065006D0070006C0061007400650073005C004E006F0072006D0061006C002E0064006F0074006D00000000000000 | |||
| (PID) Process: | (2964) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 0 | |||
Executable files
0
Suspicious files
1
Text files
1
Unknown types
2
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2964 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\CVR8BEA.tmp.cvr | — | |
MD5:— | SHA256:— | |||
| 1824 | ntvdm.exe | C:\Users\admin\AppData\Local\Temp\scs9793.tmp | — | |
MD5:— | SHA256:— | |||
| 1824 | ntvdm.exe | C:\Users\admin\AppData\Local\Temp\scs9794.tmp | — | |
MD5:— | SHA256:— | |||
| 2964 | WINWORD.EXE | C:\Users\admin\AppData\Roaming\Microsoft\Templates\~$Normal.dotm | pgc | |
MD5:— | SHA256:— | |||
| 2964 | WINWORD.EXE | C:\Users\admin\AppData\Local\Tempweffvxcvw | html | |
MD5:— | SHA256:— | |||
| 2964 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\~$ceipt(998).docm | pgc | |
MD5:— | SHA256:— | |||
| 2964 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\turbis.exe | binary | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
1
TCP/UDP connections
1
DNS requests
1
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
2964 | WINWORD.EXE | GET | 404 | 213.205.40.169:80 | http://www.fasulo.org/4GBrdf6 | IT | html | 181 b | suspicious |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
2964 | WINWORD.EXE | 213.205.40.169:80 | www.fasulo.org | Tiscali SpA | IT | suspicious |
DNS requests
Domain | IP | Reputation |
|---|---|---|
www.fasulo.org |
| suspicious |