| File name: | DOC1699735260.vbs |
| Full analysis: | https://app.any.run/tasks/57bf8f42-3364-4ec6-9faa-c8d48b5c8941 |
| Verdict: | Malicious activity |
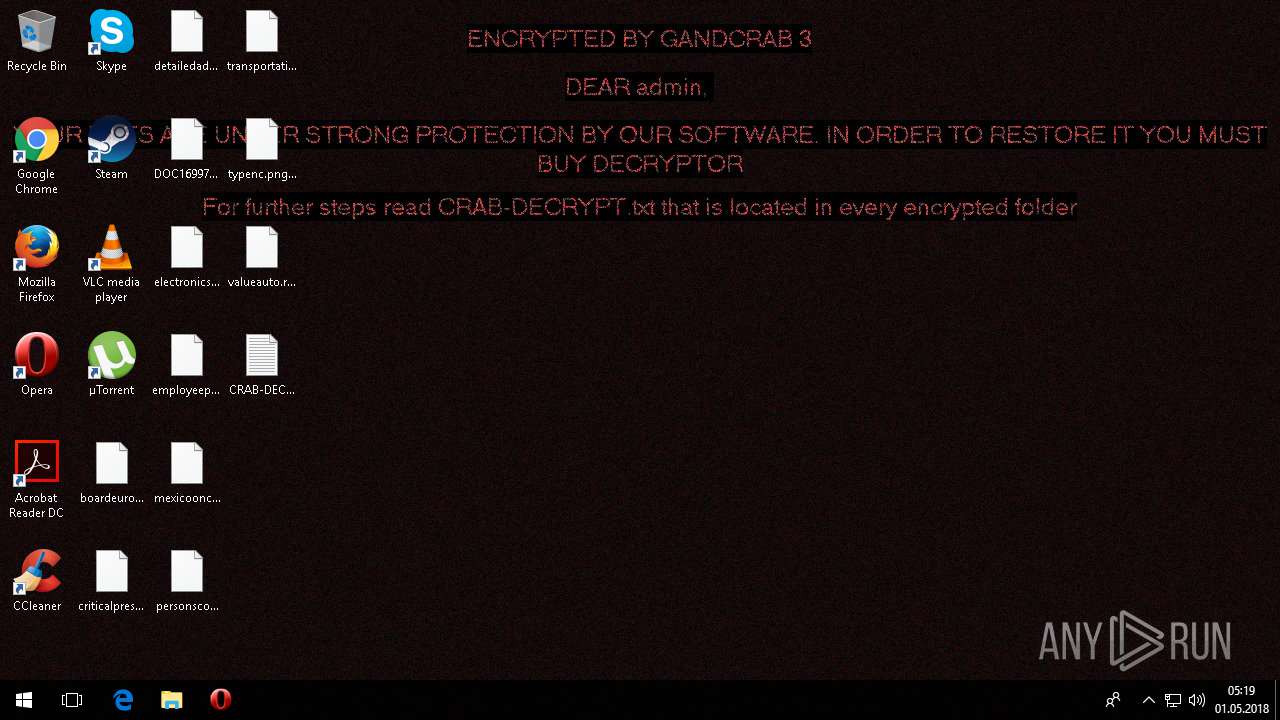
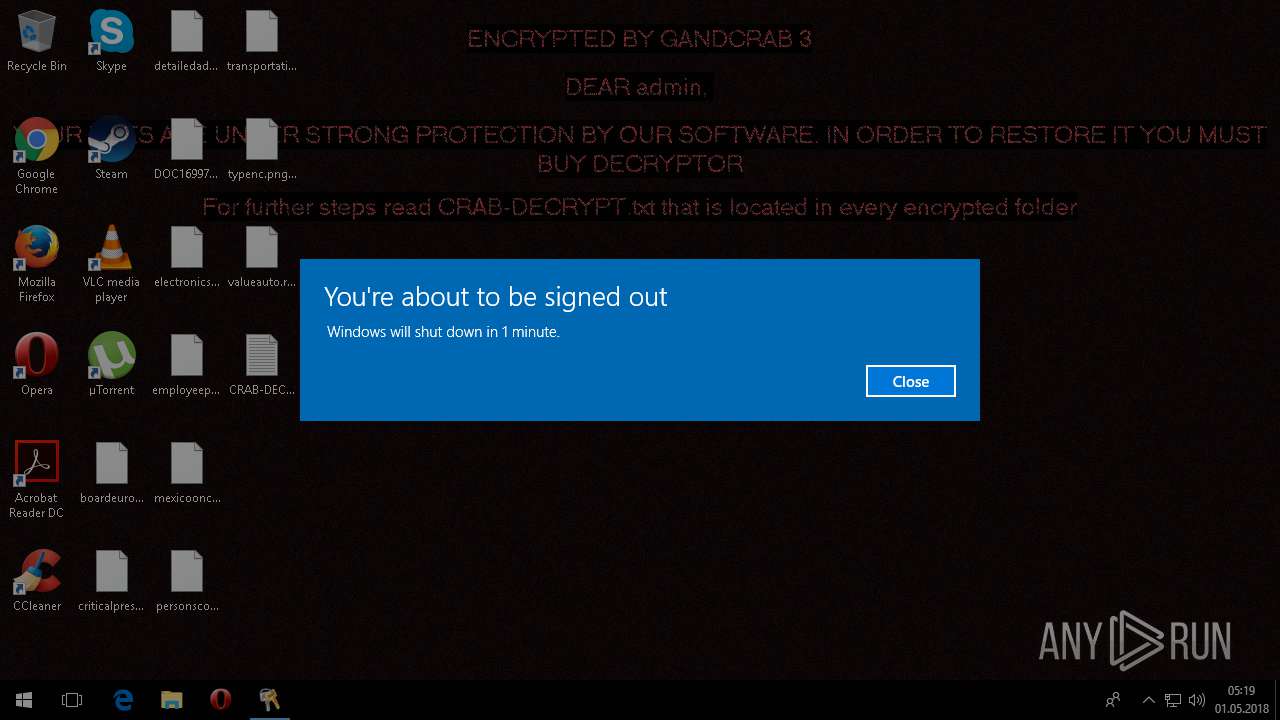
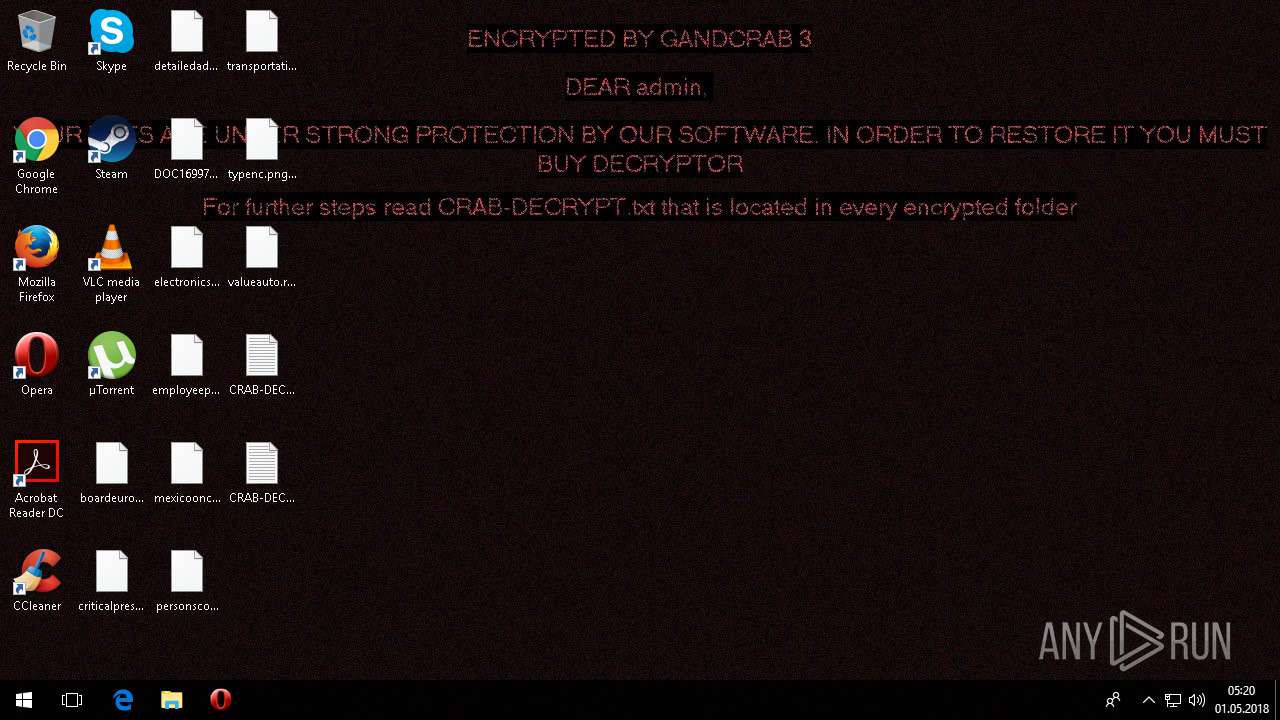
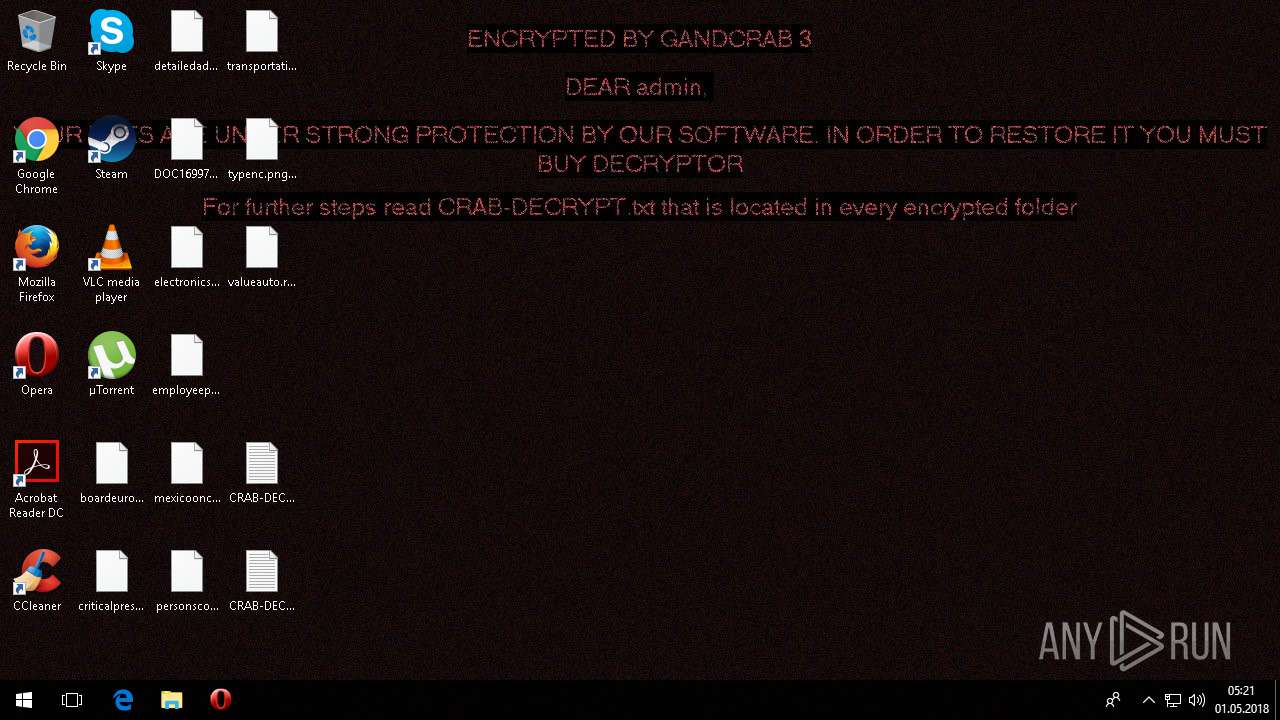
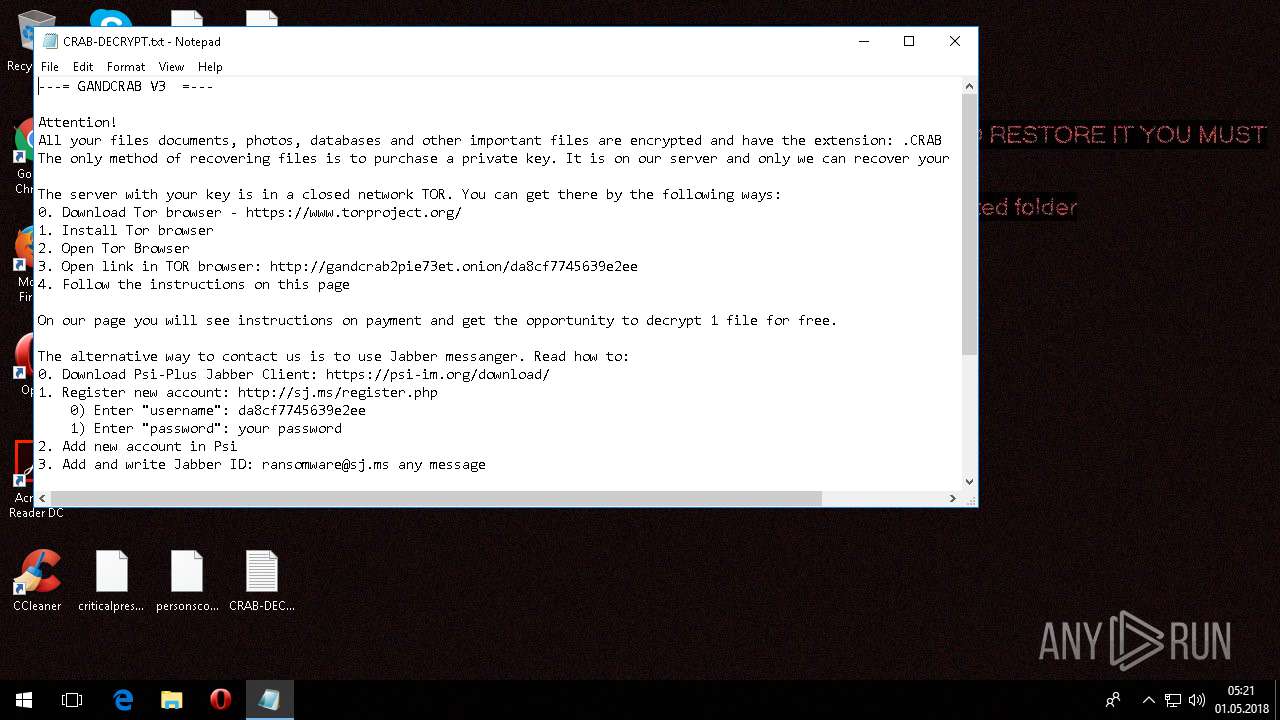
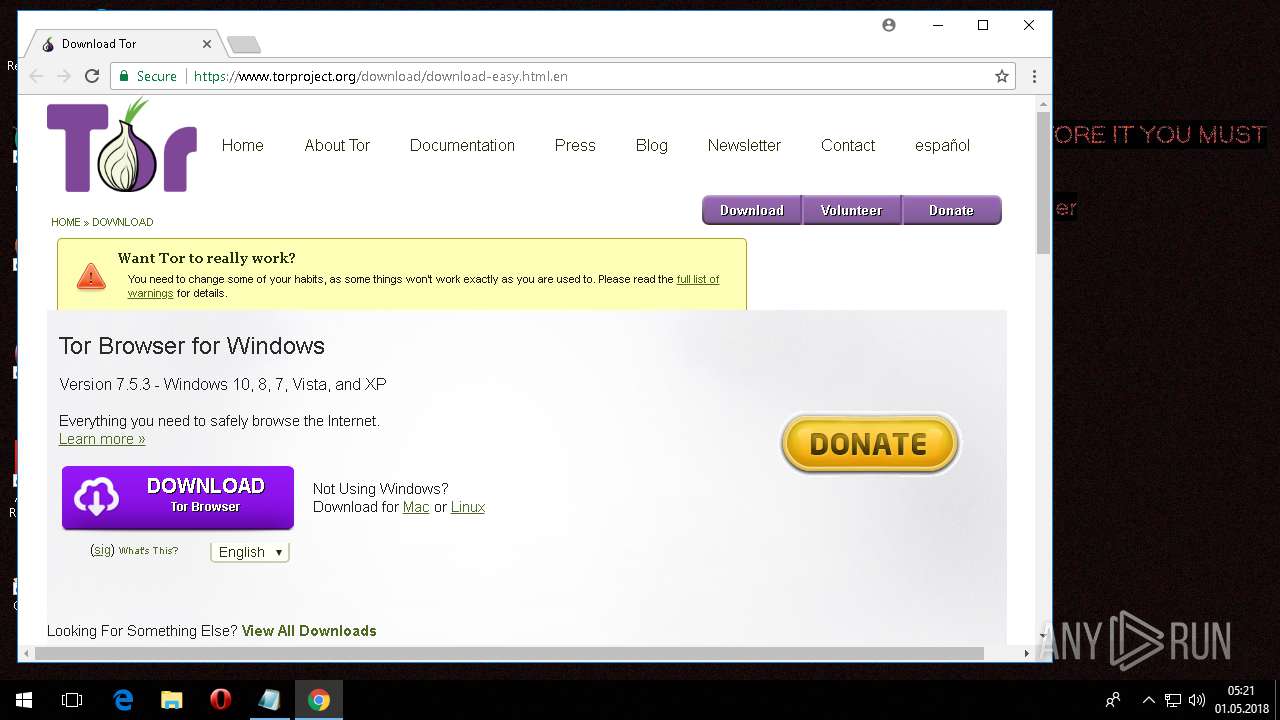
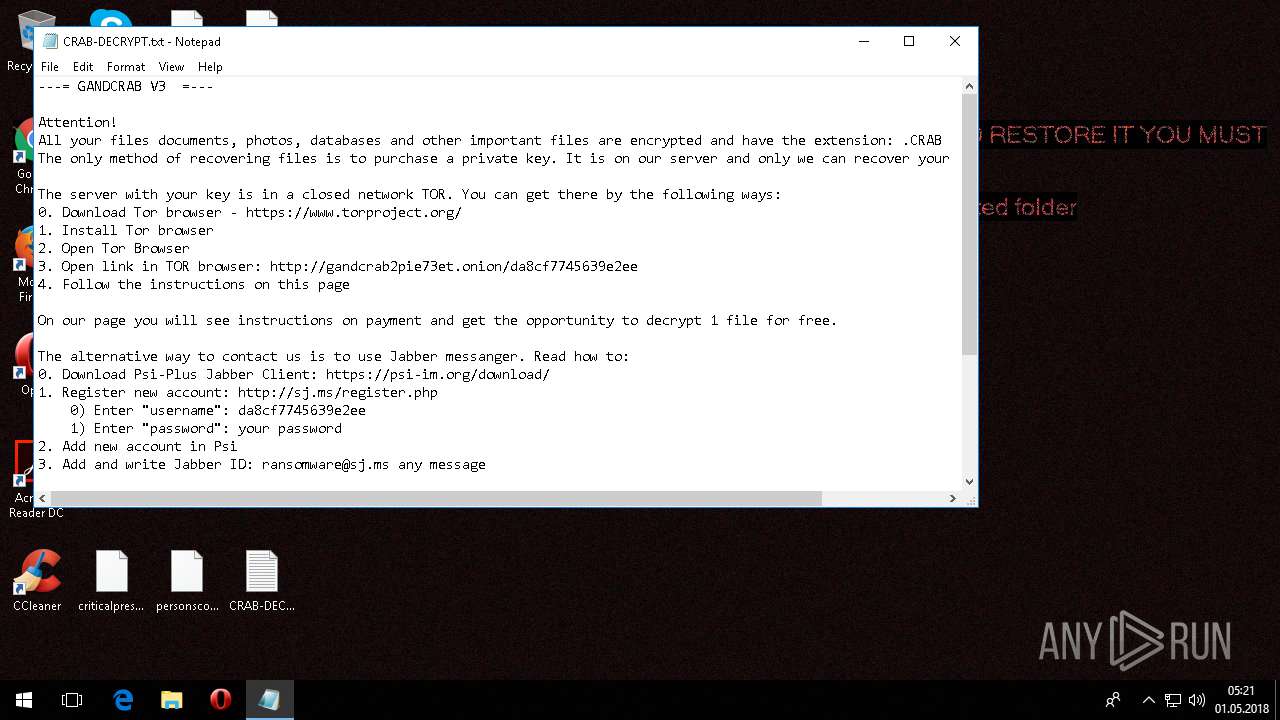
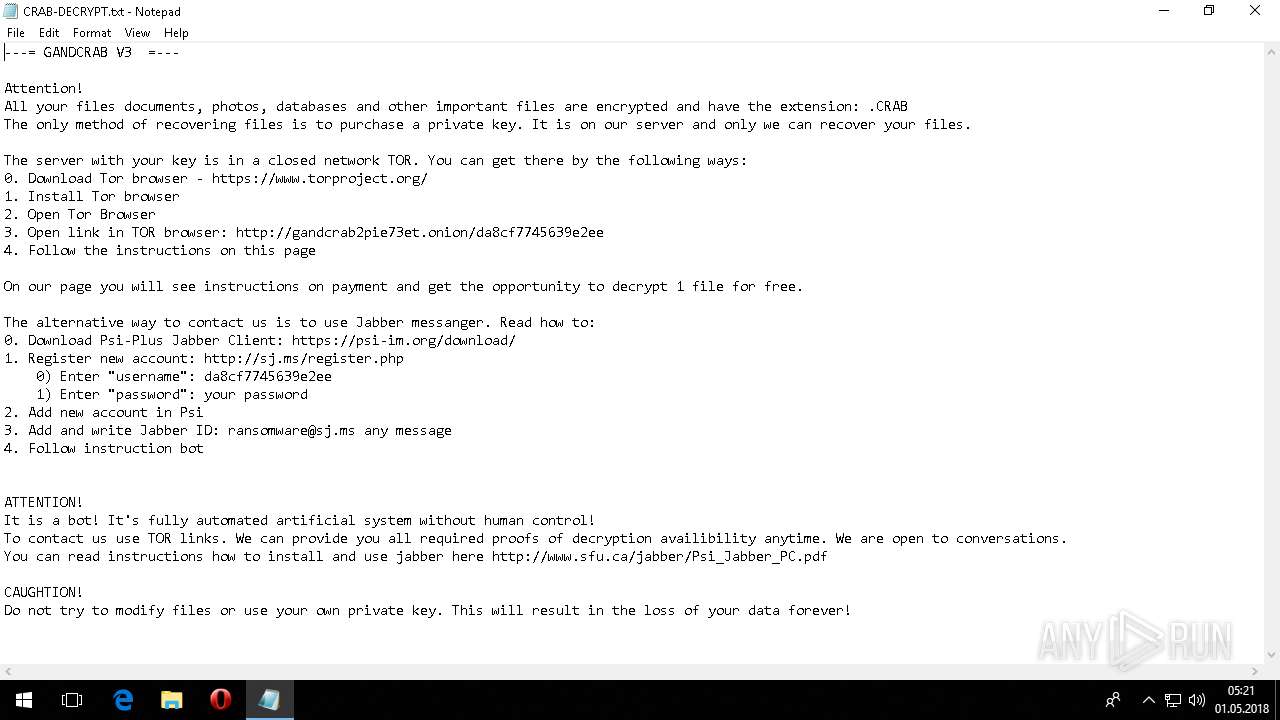
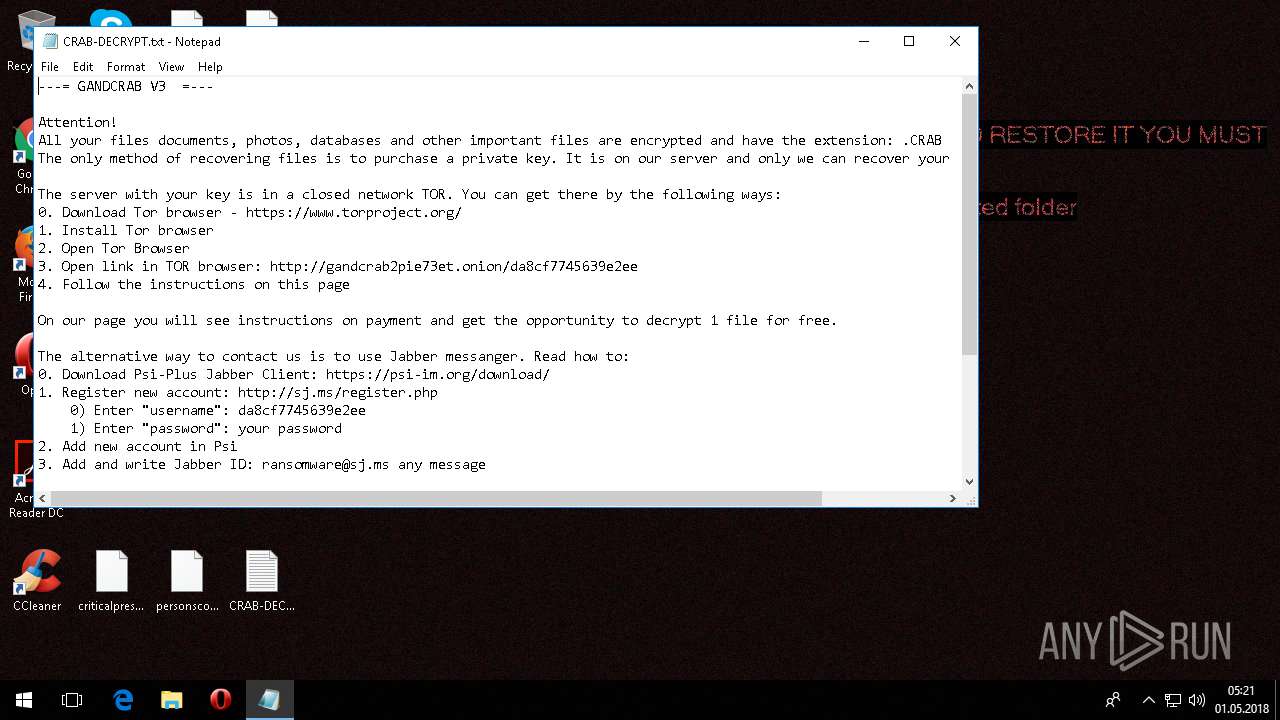
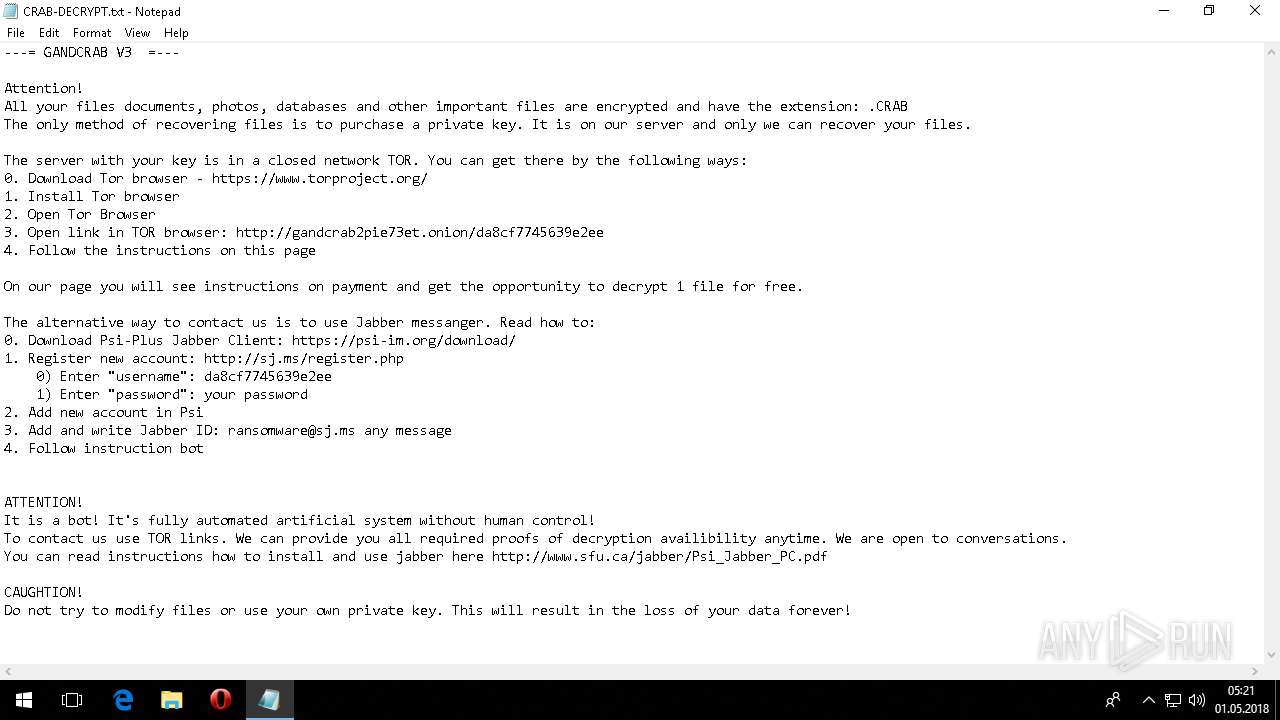
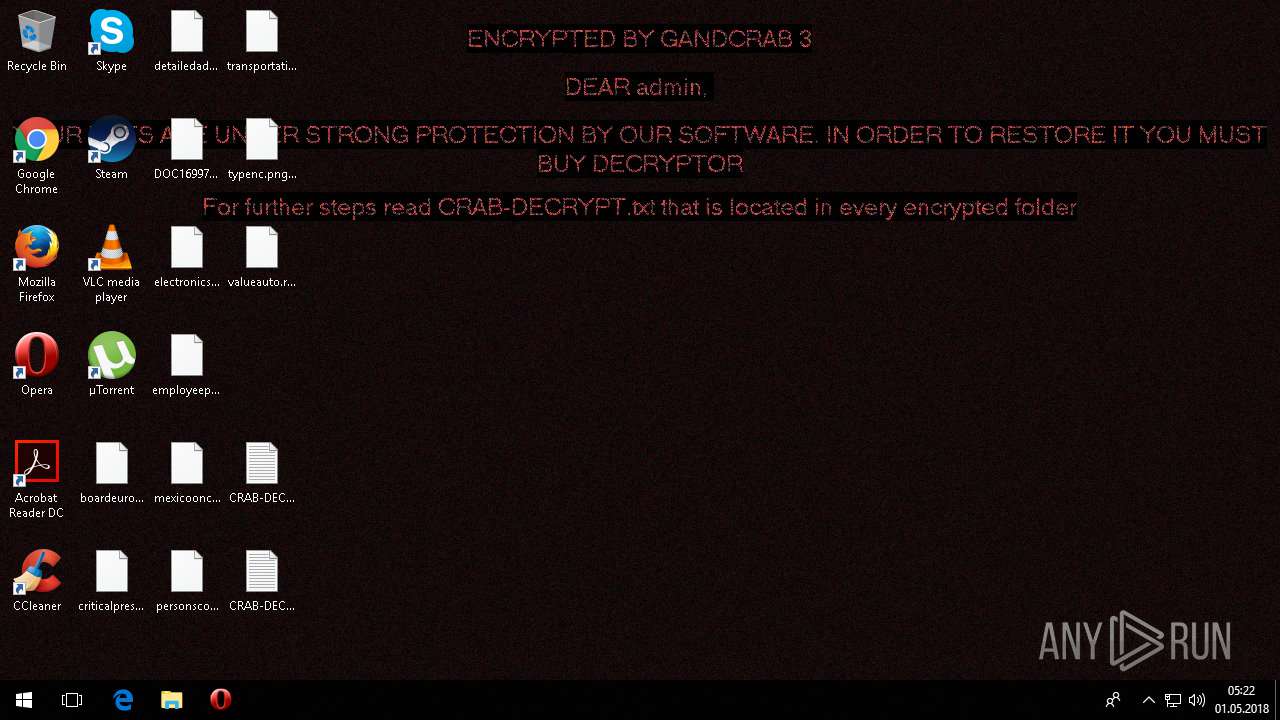
| Threats: | GandCrab is probably one of the most famous Ransomware. A Ransomware is a malware that asks the victim to pay money in order to restore access to encrypted files. If the user does not cooperate the files are forever lost. |
| Analysis date: | May 01, 2018, 05:15:29 |
| OS: | Windows 10 Professional (build: 16299, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | text/plain |
| File info: | ASCII text, with CRLF, CR line terminators |
| MD5: | AB0C2865D5245F2CC08B1513BD35BFB7 |
| SHA1: | 4AEC1BAF6252F726FEC09592E33495F84E3B56F2 |
| SHA256: | 8A97A2C3A0FDB252FBD6C1FA52F83A2230156E0D4EF614861E05B3A80ED471A1 |
| SSDEEP: | 48:IjnNadjYqiiKJDQ5HAIkqAFrBtxVgAFRvy8oU9+YOTSZ3BzshRxVSkU8S+G5:IhadsqYEqtFdtHy8nX8SxBzshRX6885 |
MALICIOUS
Application was dropped or rewritten from another process
- svchost32.exe (PID: 4312)
- svchost32.exe (PID: 4772)
- laxjce.exe (PID: 2052)
- fyaenu.exe (PID: 1292)
Changes the autorun value in the registry
- svchost32.exe (PID: 4312)
- svchost32.exe (PID: 4772)
- laxjce.exe (PID: 2052)
Writes file to Word startup folder
- svchost32.exe (PID: 4312)
Dropped file may contain instructions of ransomware
- svchost32.exe (PID: 4312)
- svchost32.exe (PID: 4772)
Writes to a start menu file
- svchost32.exe (PID: 4772)
Deletes shadow copies
- svchost32.exe (PID: 4772)
- laxjce.exe (PID: 2052)
Modifies files in Chrome extension folder
- svchost32.exe (PID: 4772)
SUSPICIOUS
Creates files in the program directory
- svchost32.exe (PID: 4312)
- svchost32.exe (PID: 4772)
Executes PowerShell scripts
- WScript.exe (PID: 420)
Creates files in the user directory
- svchost32.exe (PID: 4772)
- svchost32.exe (PID: 4312)
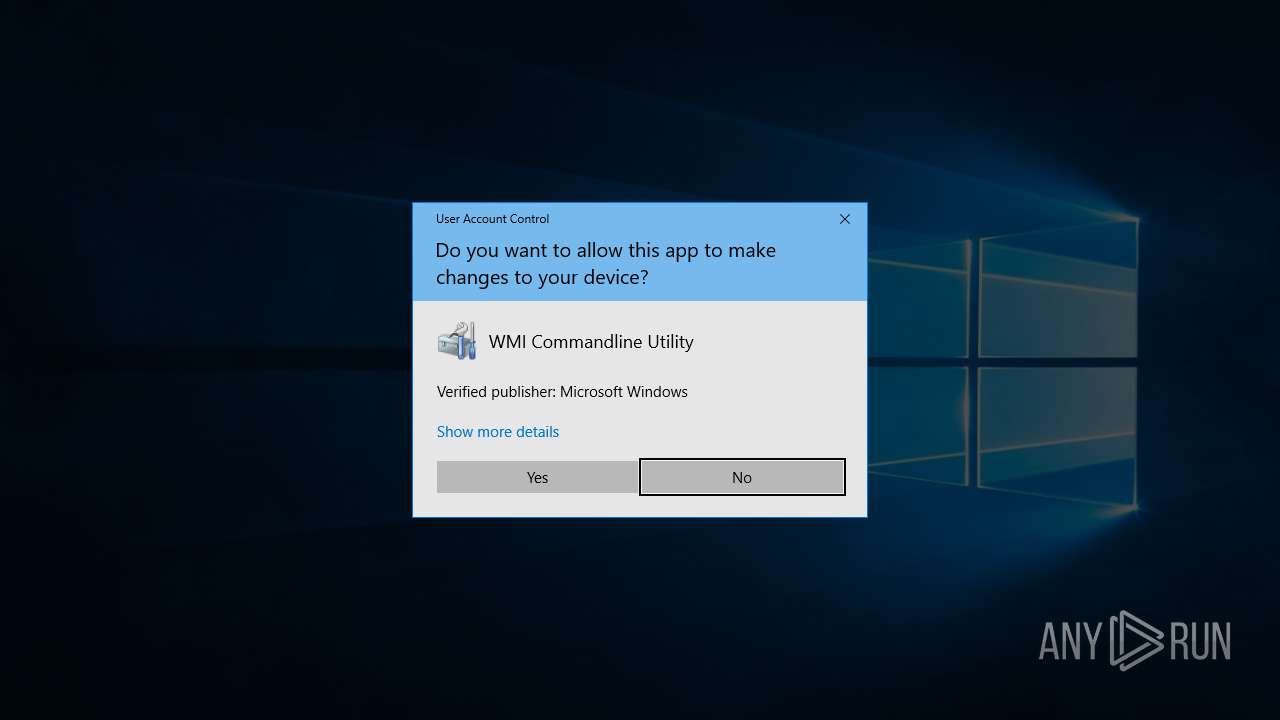
Uses WMIC.EXE to create a new process
- svchost32.exe (PID: 4312)
Creates files like Ransomware instruction
- svchost32.exe (PID: 4312)
- svchost32.exe (PID: 4772)
Starts CMD.EXE for commands execution
- svchost32.exe (PID: 4772)
INFO
Reads the software policy settings
- powershell.exe (PID: 4072)
- chrome.exe (PID: 6016)
- chrome.exe (PID: 6124)
Loads the .NET runtime environment
- powershell.exe (PID: 4072)
Dropped object may contain Bitcoin addresses
- svchost32.exe (PID: 4772)
Application launched itself
- chrome.exe (PID: 6016)
- chrome.exe (PID: 6124)
Dropped object may contain URL's
- chrome.exe (PID: 3904)
- chrome.exe (PID: 4128)
- chrome.exe (PID: 892)
- chrome.exe (PID: 260)
- chrome.exe (PID: 6016)
- chrome.exe (PID: 6124)
- svchost32.exe (PID: 4312)
- chrome.exe (PID: 5112)
- svchost32.exe (PID: 4772)
Dropped object may contain TOR URL's
- svchost32.exe (PID: 4312)
- svchost32.exe (PID: 4772)
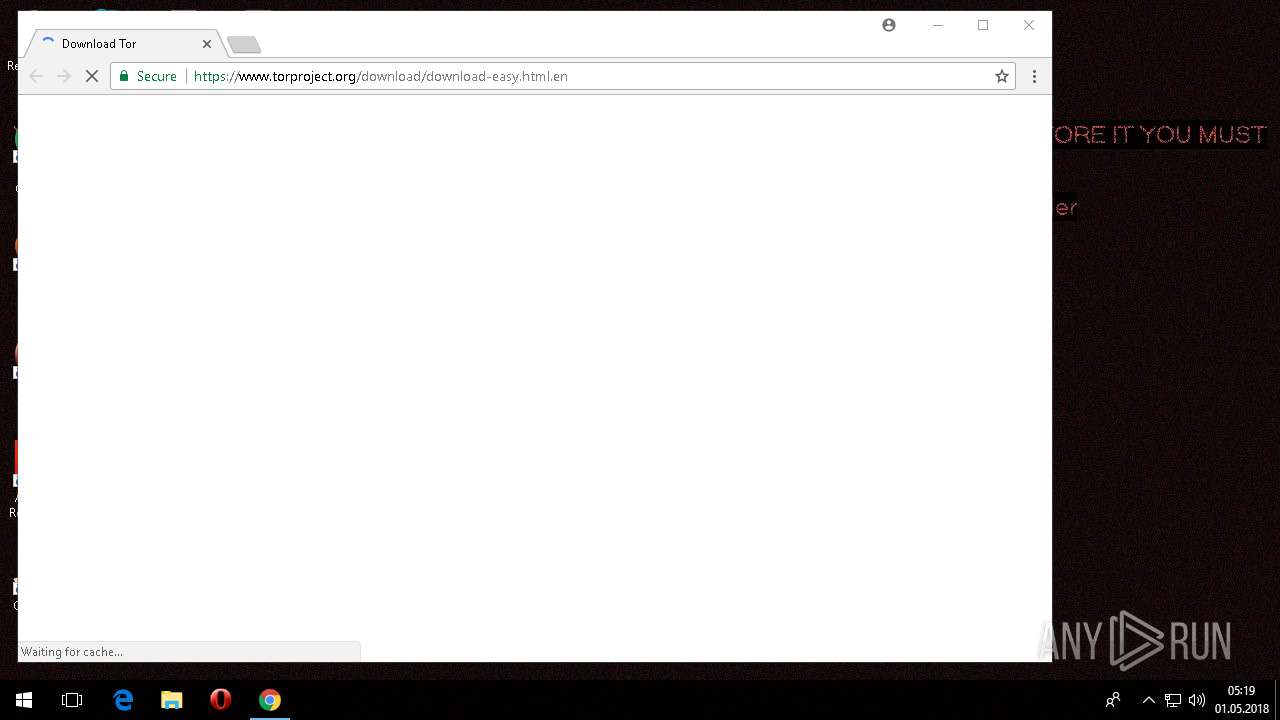
Dropped object may contain URL to Tor Browser
- chrome.exe (PID: 6016)
- chrome.exe (PID: 6124)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
186
Monitored processes
54
Malicious processes
8
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 260 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --field-trial-handle=1364,8728088478550278296,6912453236985616737,131072 --lang=en-US --service-sandbox-type=utility --utility-allowed-dir="C:\Users\admin\AppData\Local\Temp\scoped_dir6016_11742" --service-request-channel-token=1AFB262F1644F58B4ABE014999D8B87A --mojo-platform-channel-handle=5848 --ignored=" --type=renderer " /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google Inc. Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 65.0.3325.181 Modules
| |||||||||||||||
| 264 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=1364,8728088478550278296,6912453236985616737,131072 --service-pipe-token=0656D729D5F84BC89C1E636C9948C37B --lang=en-US --extension-process --enable-offline-auto-reload --enable-offline-auto-reload-visible-only --device-scale-factor=1 --num-raster-threads=1 --service-request-channel-token=0656D729D5F84BC89C1E636C9948C37B --renderer-client-id=6 --mojo-platform-channel-handle=2788 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google Inc. Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 65.0.3325.181 Modules
| |||||||||||||||
| 420 | "C:\WINDOWS\System32\WScript.exe" "C:\Users\admin\Desktop\DOC1699735260.vbs" | C:\WINDOWS\System32\WScript.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft ® Windows Based Script Host Exit code: 0 Version: 5.812.10240.16384 Modules
| |||||||||||||||
| 540 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=watcher --main-thread-id=6040 --on-initialized-event-handle=632 --parent-handle=636 /prefetch:6 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google Inc. Integrity Level: HIGH Description: Google Chrome Exit code: 0 Version: 65.0.3325.181 Modules
| |||||||||||||||
| 852 | cmd /c start C:\Users\admin\AppData\Local\Temp\svchost32.exe | C:\WINDOWS\system32\cmd.exe | — | WmiPrvSE.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 10.0.16299.15 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 892 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --field-trial-handle=1364,8728088478550278296,6912453236985616737,131072 --lang=en-US --service-sandbox-type=utility --utility-allowed-dir="C:\Users\admin\AppData\Local\Temp\scoped_dir6016_17031" --service-request-channel-token=6376899B5FECA3FFD096EB2C35514B1D --mojo-platform-channel-handle=3448 --ignored=" --type=renderer " /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google Inc. Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 65.0.3325.181 Modules
| |||||||||||||||
| 904 | nslookup carder.bit ns1.wowservers.ru | C:\WINDOWS\system32\nslookup.exe | — | svchost32.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: nslookup Exit code: 0 Version: 10.0.16299.15 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1292 | "C:\Users\admin\AppData\Roaming\Microsoft\fyaenu.exe" | C:\Users\admin\AppData\Roaming\Microsoft\fyaenu.exe | — | Explorer.EXE | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 1468 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=1364,8728088478550278296,6912453236985616737,131072 --service-pipe-token=B09B6F03EA972EC2496AAD9C8E6881F7 --lang=en-US --extension-process --enable-offline-auto-reload --enable-offline-auto-reload-visible-only --device-scale-factor=1 --num-raster-threads=1 --service-request-channel-token=B09B6F03EA972EC2496AAD9C8E6881F7 --renderer-client-id=4 --mojo-platform-channel-handle=2720 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google Inc. Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 65.0.3325.181 Modules
| |||||||||||||||
| 2016 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=gpu-process --field-trial-handle=1364,8728088478550278296,6912453236985616737,131072 --gpu-preferences=KAAAAAAAAAAABwAAAQAAAAAAAAAAAGAAAQAAAAAAAAAIAAAAAAAAACgAAAAEAAAAIAAAAAAAAAAoAAAAAAAAADAAAAAAAAAAOAAAAAAAAAAQAAAAAAAAAAAAAAAKAAAAEAAAAAAAAAAAAAAACwAAABAAAAAAAAAAAQAAAAoAAAAQAAAAAAAAAAEAAAALAAAA --gpu-vendor-id=0x1234 --gpu-device-id=0x1111 --gpu-driver-vendor=Microsoft --gpu-driver-version=10.0.16299.15 --gpu-driver-date=6-21-2006 --service-request-channel-token=C8BEADB5C94FEB80D25F14B53FBCBD94 --mojo-platform-channel-handle=1276 --ignored=" --type=renderer " /prefetch:2 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google Inc. Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 65.0.3325.181 Modules
| |||||||||||||||
Total events
31 882
Read events
31 629
Write events
244
Delete events
9
Modification events
| (PID) Process: | (420) WScript.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (420) WScript.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
| (PID) Process: | (420) WScript.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 1 | |||
| (PID) Process: | (420) WScript.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 0 | |||
| (PID) Process: | (4072) powershell.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\22\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (4072) powershell.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\powershell_RASAPI32 |
| Operation: | write | Name: | EnableFileTracing |
Value: 0 | |||
| (PID) Process: | (4072) powershell.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\powershell_RASAPI32 |
| Operation: | write | Name: | EnableAutoFileTracing |
Value: 0 | |||
| (PID) Process: | (4072) powershell.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\powershell_RASAPI32 |
| Operation: | write | Name: | EnableConsoleTracing |
Value: 0 | |||
| (PID) Process: | (4072) powershell.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\powershell_RASAPI32 |
| Operation: | write | Name: | FileTracingMask |
Value: 4294901760 | |||
| (PID) Process: | (4072) powershell.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\powershell_RASAPI32 |
| Operation: | write | Name: | ConsoleTracingMask |
Value: 4294901760 | |||
Executable files
18
Suspicious files
5 058
Text files
3 320
Unknown types
180
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 4072 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_xinwim5k.3vz.ps1 | — | |
MD5:— | SHA256:— | |||
| 4072 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_uvfguber.4yz.psm1 | — | |
MD5:— | SHA256:— | |||
| 4312 | svchost32.exe | C:\Users\admin\AppData\Roaming\Microsoft\Crypto\RSA\S-1-5-21-3775154099-3075979740-599700546-1001\0f5007522459c86e95ffcc62f32308f1_a5a43bce-52d4-40cd-b07e-dea4b2ef1ca3 | — | |
MD5:— | SHA256:— | |||
| 4312 | svchost32.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\INetCache\IE\B713ULK5\66KVJES0.htm | — | |
MD5:— | SHA256:— | |||
| 4312 | svchost32.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\INetCache\IE\B713ULK5\ssai[1].htm | — | |
MD5:— | SHA256:— | |||
| 4072 | powershell.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\PowerShell\StartupProfileData-NonInteractive | binary | |
MD5:— | SHA256:— | |||
| 4072 | powershell.exe | C:\Users\admin\AppData\Local\Temp\svchost32.exe | executable | |
MD5:— | SHA256:— | |||
| 4312 | svchost32.exe | C:\Users\admin\AppData\Local\VirtualStore\CRAB-DECRYPT.txt | text | |
MD5:— | SHA256:— | |||
| 4312 | svchost32.exe | C:\$Recycle.Bin\S-1-5-21-3775154099-3075979740-599700546-1001\CRAB-DECRYPT.txt | text | |
MD5:— | SHA256:— | |||
| 4312 | svchost32.exe | C:\Users\admin\.oracle_jre_usage\CRAB-DECRYPT.txt | text | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
20
TCP/UDP connections
63
DNS requests
39
Threats
45
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
— | — | POST | — | 82.208.161.228:80 | http://carder.bit/ssai | RO | — | — | malicious |
— | — | GET | 200 | 185.189.58.222:80 | http://185.189.58.222/bamm.exe | GB | executable | 232 Kb | malicious |
— | — | GET | 200 | 66.171.248.178:80 | http://carder.bit/ | US | text | 13 b | whitelisted |
— | — | POST | — | 89.133.197.60:80 | http://carder.bit/gheideei | HU | — | — | malicious |
— | — | GET | 200 | 93.184.220.29:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTBL0V27RVZ7LBduom%2FnYB45SPUEwQU5Z1ZMIJHWMys%2BghUNoZ7OrUETfACEAi4elAbvpzaLRZNPjlRv1U%3D | US | der | 471 b | whitelisted |
— | — | GET | 200 | 209.85.230.184:80 | http://r2---sn-h5q7dnld.gvt1.com/edgedl/chromewebstore/L2Nocm9tZV9leHRlbnNpb24vYmxvYnMvYzU3QUFWbnlGT3kzQWtjM3lqNzVJallBUQ/1.0.0.4_nmmhkkegccagdldgiimedpiccmgmieda.crx?cms_redirect=yes&ip=82.102.26.195&ipbits=0&mm=28&mn=sn-h5q7dnld&ms=nvh&mt=1525151748&mv=u&pl=25&shardbypass=yes | US | crx | 184 Kb | whitelisted |
— | — | GET | 200 | 93.184.220.29:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTBL0V27RVZ7LBduom%2FnYB45SPUEwQU5Z1ZMIJHWMys%2BghUNoZ7OrUETfACEAiIzVJfGSRETRSlgpHeuVI%3D | US | der | 471 b | whitelisted |
— | — | POST | — | 46.40.123.136:80 | http://carder.bit/erelfui?geoagh=ghere | BG | — | — | malicious |
— | — | GET | 200 | 74.125.4.44:80 | http://r6---sn-h5q7dnes.gvt1.com/edgedl/chromewebstore/L2Nocm9tZV9leHRlbnNpb24vYmxvYnMvNDk2QUFWbWNTUGRmLWwwLXZWN0QyWVdidw/6518.129.0.1_pkedcjkdefgpdelpbcmbmeomcjbeemfm.crx?cms_redirect=yes&ip=82.102.26.195&ipbits=0&mm=28&mn=sn-h5q7dnes&ms=nvh&mt=1525151748&mv=u&pl=25&shardbypass=yes | US | crx | 804 Kb | whitelisted |
— | — | GET | 200 | 66.171.248.178:80 | http://carder.bit/ | US | text | 13 b | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
— | — | 185.189.58.222:80 | — | — | GB | malicious |
— | — | 66.171.248.178:80 | ipv4bot.whatismyipaddress.com | Alchemy Communications, Inc. | US | malicious |
— | — | 189.75.183.21:53 | ns1.wowservers.ru | Brasil Telecom S/A - Filial Distrito Federal | BR | malicious |
— | — | 93.184.220.29:80 | ocsp.digicert.com | MCI Communications Services, Inc. d/b/a Verizon Business | US | whitelisted |
— | — | 23.211.9.92:80 | www.microsoft.com | Akamai Technologies, Inc. | NL | whitelisted |
— | — | 82.208.161.228:80 | — | Liberty Global Operations B.V. | RO | malicious |
— | — | 46.40.123.136:80 | — | Bulsatcom EAD | BG | suspicious |
— | — | 138.201.14.197:443 | www.torproject.org | Hetzner Online GmbH | DE | unknown |
— | — | 172.217.16.163:443 | clientservices.googleapis.com | Google Inc. | US | whitelisted |
— | — | 172.217.16.206:443 | clients2.google.com | Google Inc. | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
ipv4bot.whatismyipaddress.com |
| shared |
ns1.wowservers.ru |
| malicious |
ocsp.digicert.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
nexus.officeapps.live.com |
| whitelisted |
nexusrules.officeapps.live.com |
| whitelisted |
carder.bit |
| malicious |
www.google.com |
| malicious |
clientservices.googleapis.com |
| whitelisted |
translate.googleapis.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
— | — | A Network Trojan was detected | ET INFO Executable Download from dotted-quad Host |
— | — | Misc activity | ET INFO Packed Executable Download |
— | — | Potential Corporate Privacy Violation | ET POLICY PE EXE or DLL Windows file download HTTP |
— | — | Potentially Bad Traffic | ET INFO Executable Retrieved With Minimal HTTP Headers - Potential Second Stage Download |
— | — | Potentially Bad Traffic | ET INFO SUSPICIOUS Dotted Quad Host MZ Response |
— | — | Misc activity | ET INFO EXE IsDebuggerPresent (Used in Malware Anti-Debugging) |
— | — | A Network Trojan was detected | ET TROJAN Likely GandCrab Ransomware Domain in HTTP Host M1 |
— | — | A Network Trojan was detected | ET TROJAN Observed GandCrab Ransomware Domain (carder .bit in DNS Lookup) |
— | — | Potentially Bad Traffic | ET CURRENT_EVENTS DNS Query Domain .bit |
— | — | A Network Trojan was detected | ET TROJAN Observed GandCrab Ransomware Domain (carder .bit in DNS Lookup) |
Process | Message |
|---|---|
conhost.exe | InitSideBySide failed create an activation context. Error: 1814 |
conhost.exe | InitSideBySide failed create an activation context. Error: 1814 |
conhost.exe | InitSideBySide failed create an activation context. Error: 1814 |
conhost.exe | InitSideBySide failed create an activation context. Error: 1814 |
conhost.exe | InitSideBySide failed create an activation context. Error: 1814 |
conhost.exe | InitSideBySide failed create an activation context. Error: 1814 |