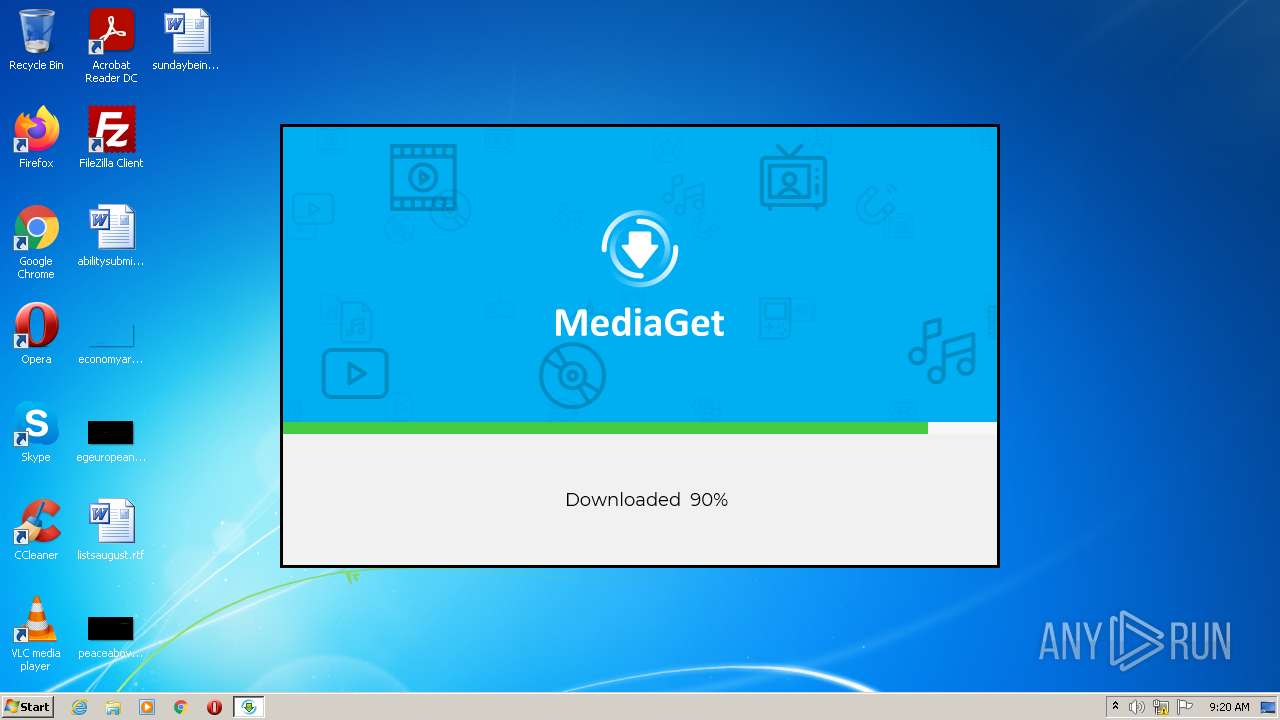
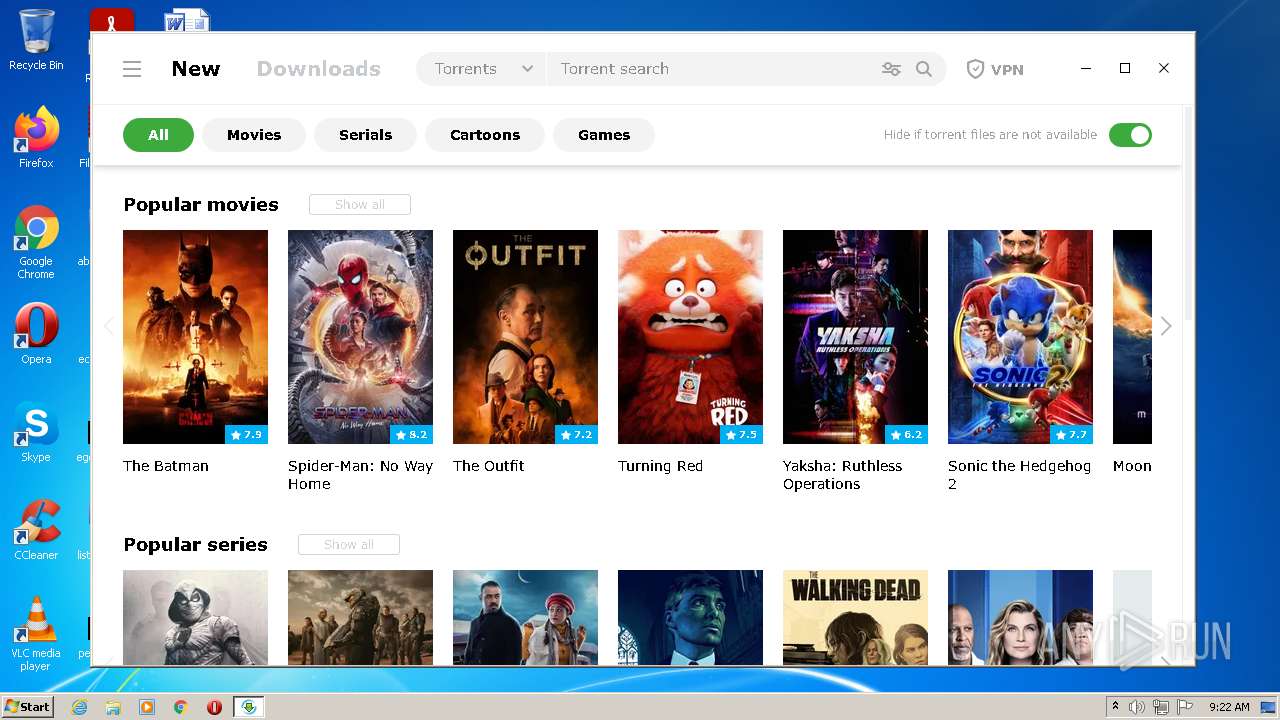
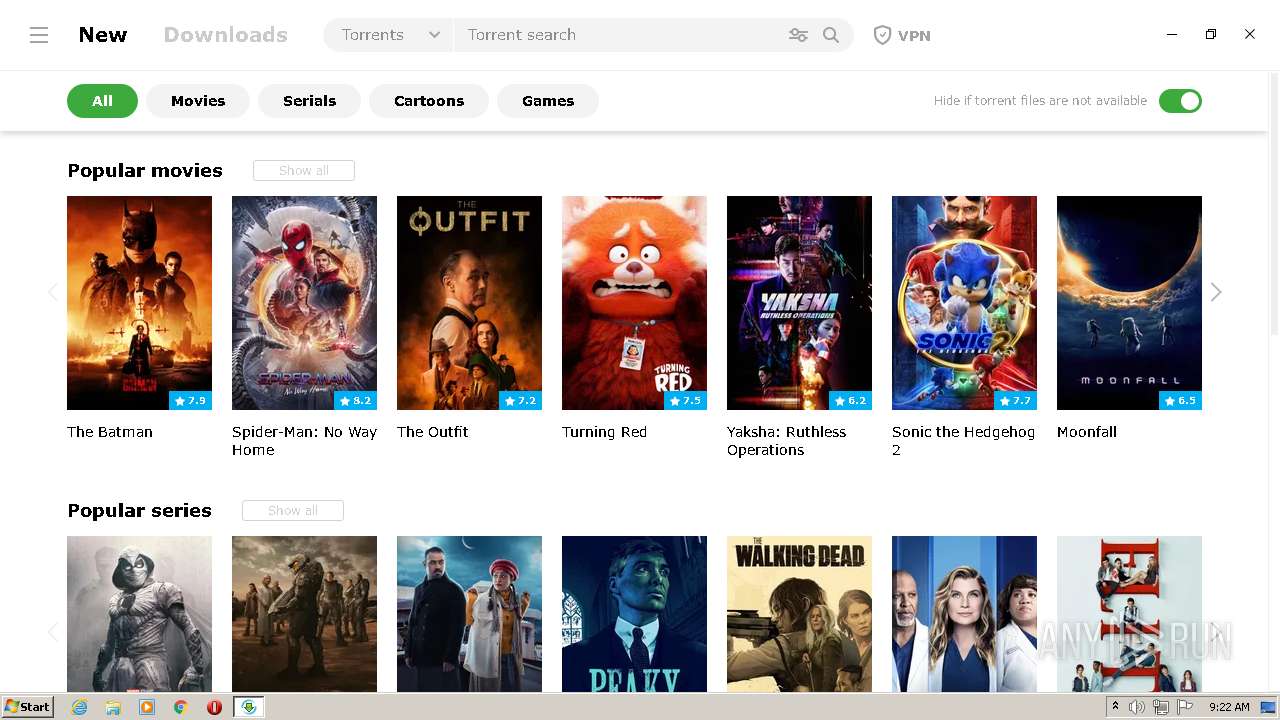
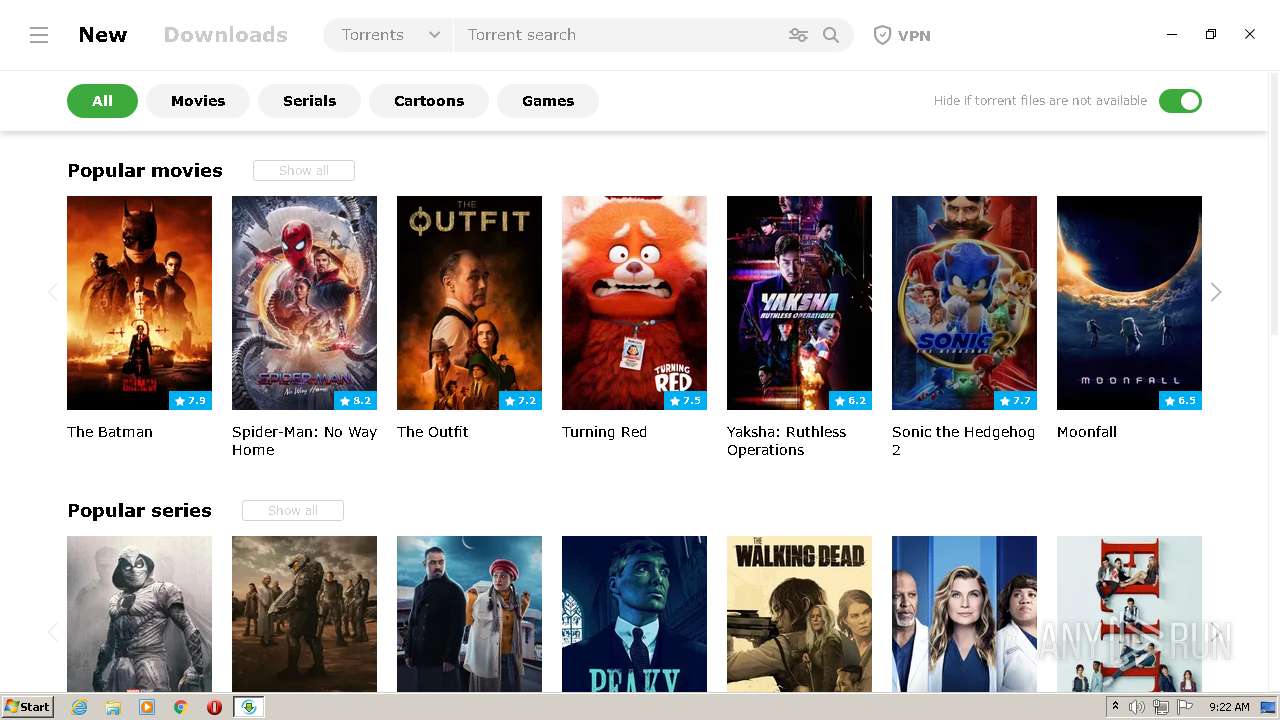
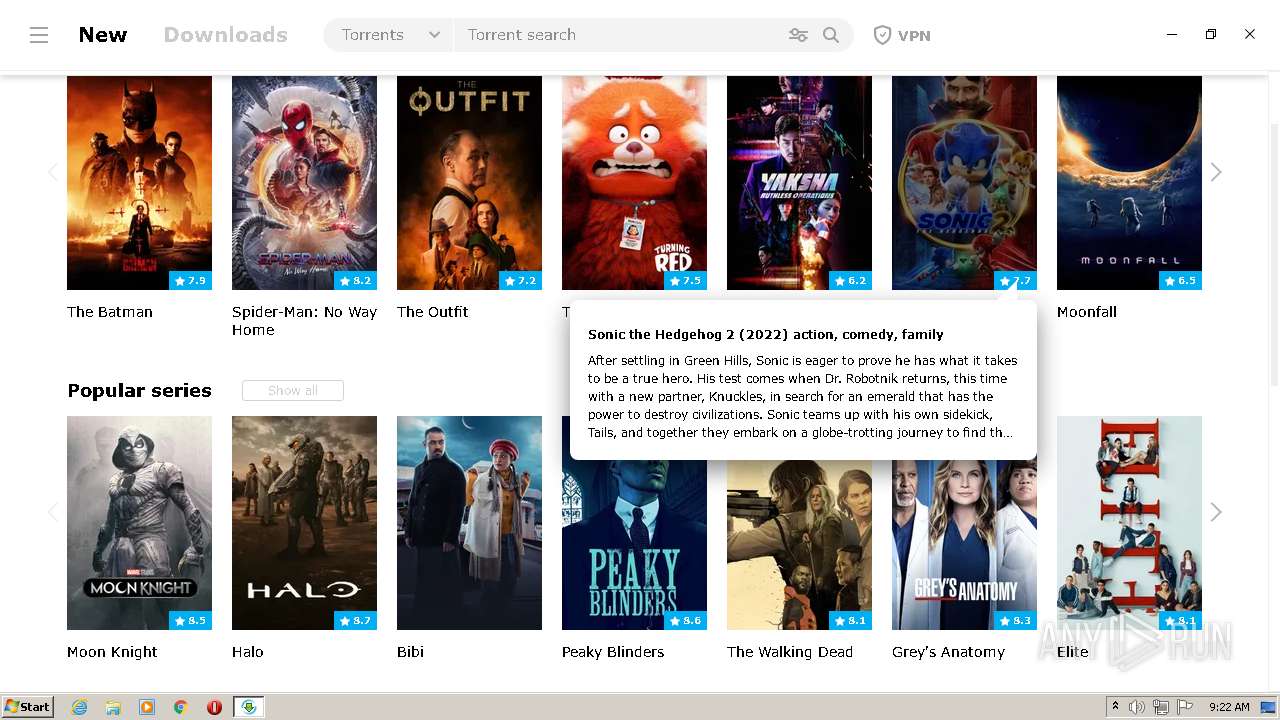
| File name: | mediaget.exe |
| Full analysis: | https://app.any.run/tasks/db66afc1-e6da-4308-8b19-284fca99c712 |
| Verdict: | Malicious activity |
| Analysis date: | April 27, 2022, 08:19:10 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows |
| MD5: | 544725B23EB551987754536D7382A351 |
| SHA1: | D3FCC81F80948E88E79767F9E757E207E0FD8373 |
| SHA256: | 8A88AA6F4067F71232C1453085F8A0C26E1BBA42AF83179B60D7053B87496283 |
| SSDEEP: | 98304:lbmKWAy7Q/DsuILFWUkrcmqWfxnxgCkUc4ppd:586/DzI5rmqaDgfUNppd |
MALICIOUS
Actions looks like stealing of personal data
- mediaget.exe (PID: 604)
Loads dropped or rewritten executable
- SearchProtocolHost.exe (PID: 3648)
- net_updater32.exe (PID: 328)
- mediaget.exe (PID: 2720)
- mediaget_crashpad_handler.exe (PID: 2604)
- QtWebEngineProcess.exe (PID: 3668)
- QtWebEngineProcess.exe (PID: 1024)
- net_updater32.exe (PID: 3612)
- QtWebEngineProcess.exe (PID: 3344)
- SearchProtocolHost.exe (PID: 2068)
- luminati-m-controller.exe (PID: 1644)
- QtWebEngineProcess.exe (PID: 880)
Drops executable file immediately after starts
- mediaget.exe (PID: 604)
- lum_inst.exe (PID: 3104)
- net_updater32.exe (PID: 328)
- lum_inst.tmp (PID: 2856)
- net_updater32.exe (PID: 3612)
- luminati-m-controller.exe (PID: 1644)
- mediaget.exe (PID: 2720)
Application was dropped or rewritten from another process
- lum_inst.exe (PID: 3104)
- net_updater32.exe (PID: 328)
- test_wpf.exe (PID: 3244)
- net_updater32.exe (PID: 3960)
- mediaget.exe (PID: 2720)
- net_updater32.exe (PID: 3612)
- mediaget_crashpad_handler.exe (PID: 2604)
- QtWebEngineProcess.exe (PID: 3668)
- QtWebEngineProcess.exe (PID: 1024)
- QtWebEngineProcess.exe (PID: 3344)
- test_wpf.exe (PID: 2500)
- luminati-m-controller.exe (PID: 1644)
- test_wpf.exe (PID: 2356)
- idle_report.exe (PID: 3484)
- net_svc.exe (PID: 3844)
- idle_report.exe (PID: 2084)
- net_svc.exe (PID: 3236)
- net_svc.exe (PID: 3360)
- QtWebEngineProcess.exe (PID: 880)
- net_svc.exe (PID: 3528)
- idle_report.exe (PID: 3608)
- net_svc.exe (PID: 3192)
Changes settings of System certificates
- net_updater32.exe (PID: 328)
- QtWebEngineProcess.exe (PID: 3668)
Changes the autorun value in the registry
- mediaget.exe (PID: 2720)
SUSPICIOUS
Reads Microsoft Outlook installation path
- mediaget.exe (PID: 604)
Executable content was dropped or overwritten
- mediaget.exe (PID: 604)
- lum_inst.exe (PID: 3104)
- net_updater32.exe (PID: 328)
- lum_inst.tmp (PID: 2856)
- net_updater32.exe (PID: 3612)
- luminati-m-controller.exe (PID: 1644)
- mediaget.exe (PID: 2720)
Drops a file with a compile date too recent
- mediaget.exe (PID: 604)
- lum_inst.exe (PID: 3104)
- lum_inst.tmp (PID: 2856)
- net_updater32.exe (PID: 328)
- net_updater32.exe (PID: 3612)
- luminati-m-controller.exe (PID: 1644)
- mediaget.exe (PID: 2720)
Checks supported languages
- mediaget.exe (PID: 604)
- lum_inst.exe (PID: 3104)
- lum_inst.tmp (PID: 2856)
- net_updater32.exe (PID: 328)
- test_wpf.exe (PID: 3244)
- net_updater32.exe (PID: 3960)
- mediaget.exe (PID: 2720)
- net_updater32.exe (PID: 3612)
- mediaget_crashpad_handler.exe (PID: 2604)
- QtWebEngineProcess.exe (PID: 3668)
- QtWebEngineProcess.exe (PID: 1024)
- test_wpf.exe (PID: 2500)
- QtWebEngineProcess.exe (PID: 3344)
- luminati-m-controller.exe (PID: 1644)
- test_wpf.exe (PID: 2356)
- QtWebEngineProcess.exe (PID: 880)
- idle_report.exe (PID: 2084)
- net_svc.exe (PID: 3236)
- net_svc.exe (PID: 3360)
- net_svc.exe (PID: 3528)
- idle_report.exe (PID: 3484)
- net_svc.exe (PID: 3844)
- net_svc.exe (PID: 3192)
- idle_report.exe (PID: 3608)
Creates files in the user directory
- mediaget.exe (PID: 604)
Reads the computer name
- mediaget.exe (PID: 604)
- lum_inst.tmp (PID: 2856)
- net_updater32.exe (PID: 328)
- test_wpf.exe (PID: 3244)
- net_updater32.exe (PID: 3960)
- mediaget.exe (PID: 2720)
- net_updater32.exe (PID: 3612)
- QtWebEngineProcess.exe (PID: 3668)
- test_wpf.exe (PID: 2500)
- test_wpf.exe (PID: 2356)
- luminati-m-controller.exe (PID: 1644)
- net_svc.exe (PID: 3360)
- idle_report.exe (PID: 2084)
- idle_report.exe (PID: 3484)
- idle_report.exe (PID: 3608)
Reads internet explorer settings
- mediaget.exe (PID: 604)
Creates a software uninstall entry
- mediaget.exe (PID: 604)
Reads the Windows organization settings
- lum_inst.tmp (PID: 2856)
Reads Windows owner or organization settings
- lum_inst.tmp (PID: 2856)
Adds / modifies Windows certificates
- net_updater32.exe (PID: 328)
- QtWebEngineProcess.exe (PID: 3668)
Reads Environment values
- net_updater32.exe (PID: 328)
- mediaget.exe (PID: 2720)
- net_updater32.exe (PID: 3612)
- luminati-m-controller.exe (PID: 1644)
Creates files in the program directory
- net_updater32.exe (PID: 328)
Application launched itself
- net_updater32.exe (PID: 328)
- net_svc.exe (PID: 3360)
Executed as Windows Service
- net_updater32.exe (PID: 3612)
Changes default file association
- mediaget.exe (PID: 604)
- mediaget.exe (PID: 2720)
Creates files in the Windows directory
- net_updater32.exe (PID: 3612)
Removes files from Windows directory
- net_updater32.exe (PID: 3612)
INFO
Dropped object may contain Bitcoin addresses
- mediaget.exe (PID: 604)
- mediaget.exe (PID: 2720)
Reads settings of System Certificates
- net_updater32.exe (PID: 328)
- net_updater32.exe (PID: 3960)
- net_updater32.exe (PID: 3612)
- mediaget.exe (PID: 2720)
- QtWebEngineProcess.exe (PID: 3668)
Application was dropped or rewritten from another process
- lum_inst.tmp (PID: 2856)
Checks Windows Trust Settings
- net_updater32.exe (PID: 328)
- net_updater32.exe (PID: 3612)
Checks supported languages
- WISPTIS.EXE (PID: 2788)
- SearchProtocolHost.exe (PID: 2068)
Reads the computer name
- WISPTIS.EXE (PID: 2788)
- SearchProtocolHost.exe (PID: 2068)
Reads the hosts file
- mediaget.exe (PID: 2720)
- QtWebEngineProcess.exe (PID: 3668)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win64 Executable (generic) (64.6) |
|---|---|---|
| .dll | | | Win32 Dynamic Link Library (generic) (15.4) |
| .exe | | | Win32 Executable (generic) (10.5) |
| .exe | | | Generic Win/DOS Executable (4.6) |
| .exe | | | DOS Executable Generic (4.6) |
EXIF
EXE
| ProductVersion: | 1 |
|---|---|
| ProductName: | - |
| OriginalFileName: | - |
| LegalCopyright: | - |
| InternalName: | - |
| FileVersion: | 1 |
| FileDescription: | - |
| CompanyName: | - |
| Comments: | - |
| CharacterSet: | Unicode |
| LanguageCode: | English (U.S.) |
| FileSubtype: | - |
| ObjectFileType: | Executable application |
| FileOS: | Win32 |
| FileFlags: | (none) |
| FileFlagsMask: | 0x003f |
| ProductVersionNumber: | 1.0.0.1 |
| FileVersionNumber: | 1.0.0.0 |
| Subsystem: | Windows GUI |
| SubsystemVersion: | 5 |
| ImageVersion: | - |
| OSVersion: | 5 |
| EntryPoint: | 0x1635a2 |
| UninitializedDataSize: | - |
| InitializedDataSize: | 2150400 |
| CodeSize: | 1497088 |
| LinkerVersion: | 9 |
| PEType: | PE32 |
| TimeStamp: | 2022:01:20 08:40:18+01:00 |
| MachineType: | Intel 386 or later, and compatibles |
Summary
| Architecture: | IMAGE_FILE_MACHINE_I386 |
|---|---|
| Subsystem: | IMAGE_SUBSYSTEM_WINDOWS_GUI |
| Compilation Date: | 20-Jan-2022 07:40:18 |
| Detected languages: |
|
| Comments: | - |
| CompanyName: | - |
| FileDescription: | - |
| FileVersion: | 1.0 |
| InternalName: | - |
| LegalCopyright: | - |
| OriginalFilename: | - |
| ProductName: | - |
| ProductVersion: | 1.0 |
DOS Header
| Magic number: | MZ |
|---|---|
| Bytes on last page of file: | 0x0090 |
| Pages in file: | 0x0003 |
| Relocations: | 0x0000 |
| Size of header: | 0x0004 |
| Min extra paragraphs: | 0x0000 |
| Max extra paragraphs: | 0xFFFF |
| Initial SS value: | 0x0000 |
| Initial SP value: | 0x00B8 |
| Checksum: | 0x0000 |
| Initial IP value: | 0x0000 |
| Initial CS value: | 0x0000 |
| Overlay number: | 0x0000 |
| OEM identifier: | 0x0000 |
| OEM information: | 0x0000 |
| Address of NE header: | 0x00000110 |
PE Headers
| Signature: | PE |
|---|---|
| Machine: | IMAGE_FILE_MACHINE_I386 |
| Number of sections: | 5 |
| Time date stamp: | 20-Jan-2022 07:40:18 |
| Pointer to Symbol Table: | 0x00000000 |
| Number of symbols: | 0 |
| Size of Optional Header: | 0x00E0 |
| Characteristics: |
|
Sections
Name | Virtual Address | Virtual Size | Raw Size | Charateristics | Entropy |
|---|---|---|---|---|---|
.text | 0x00001000 | 0x0016D644 | 0x0016D800 | IMAGE_SCN_CNT_CODE, IMAGE_SCN_MEM_EXECUTE, IMAGE_SCN_MEM_READ | 6.6234 |
.rdata | 0x0016F000 | 0x000739E2 | 0x00073A00 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ | 6.14887 |
.data | 0x001E3000 | 0x0000F4E0 | 0x00009600 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ, IMAGE_SCN_MEM_WRITE | 5.12399 |
.rsrc | 0x001F3000 | 0x001794FC | 0x00179600 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ | 7.95134 |
.reloc | 0x0036D000 | 0x00016960 | 0x00016A00 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_DISCARDABLE, IMAGE_SCN_MEM_READ | 5.98892 |
Resources
Title | Entropy | Size | Codepage | Language | Type |
|---|---|---|---|---|---|
1 | 5.22706 | 820 | Latin 1 / Western European | English - United States | RT_MANIFEST |
2 | 5.18073 | 4264 | Latin 1 / Western European | English - United States | RT_ICON |
3 | 5.05232 | 2440 | Latin 1 / Western European | English - United States | RT_ICON |
4 | 4.75162 | 1128 | Latin 1 / Western European | English - United States | RT_ICON |
128 | 2.62308 | 62 | Latin 1 / Western European | English - United States | RT_GROUP_ICON |
129 | 1.67172 | 170 | Latin 1 / Western European | English - United States | UNKNOWN |
HTML | 7.99985 | 1207109 | Latin 1 / Western European | Russian - Russia | ARCHIVE_7Z |
PRELOADER-EN | 7.99581 | 44770 | Latin 1 / Western European | Russian - Russia | ARCHIVE_7Z |
PRELOADER-RU | 7.99601 | 45960 | Latin 1 / Western European | Russian - Russia | ARCHIVE_7Z |
CABUNDLE | 6.0253 | 227153 | Latin 1 / Western European | Russian - Russia | CRT |
Imports
ADVAPI32.dll |
COMCTL32.dll |
CRYPT32.dll |
GDI32.dll |
KERNEL32.dll |
MSVCR90.dll |
OLEAUT32.dll |
OPENGL32.dll |
PSAPI.DLL |
SHELL32.dll |
Total processes
75
Monitored processes
29
Malicious processes
17
Suspicious processes
6
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
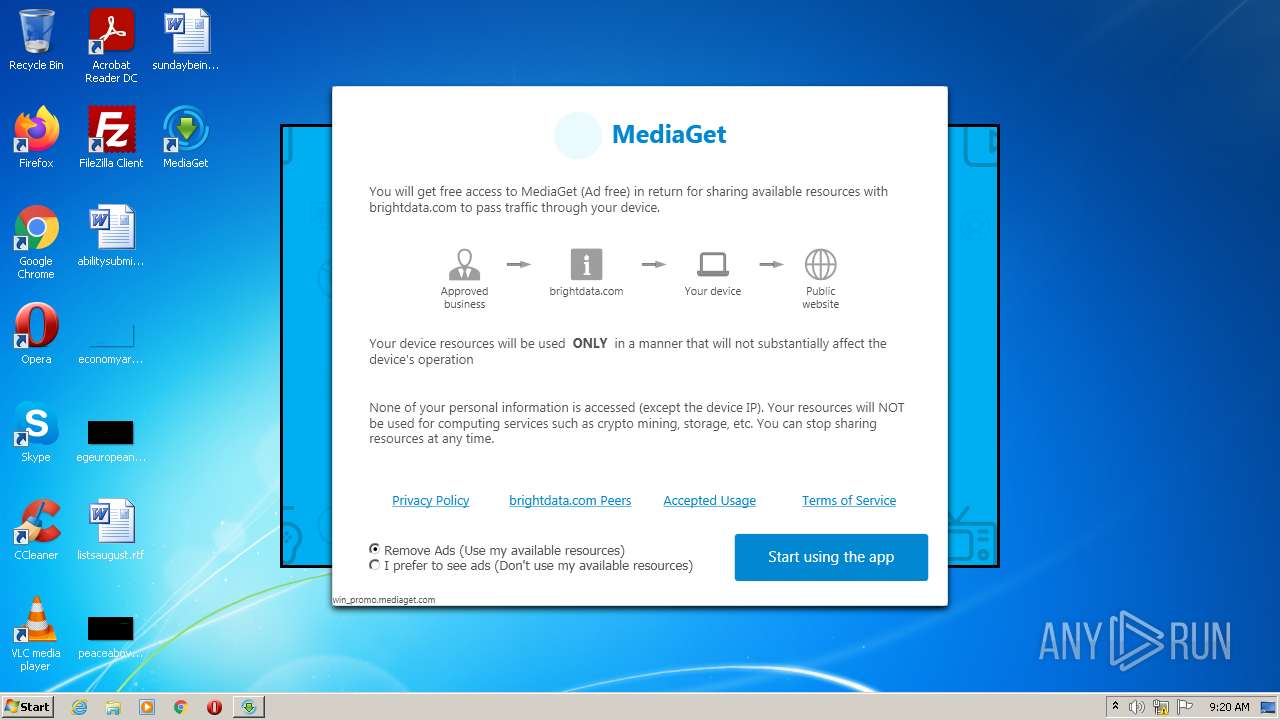
| 328 | "C:\Users\admin\MediaGet2\Luminati-m\net_updater32.exe" --install-ui win_promo.mediaget.com --dlg-app-name MediaGet --dlg-tos-link "https://mediaget.com/license" --dlg-benefit-txt "MediaGet (Ad free)" --dlg-logo-link "https://mediaget.com/installer/binaries/mg-icon-400.png" --dlg-not-peer-txt ads --dlg-peer-txt remove_ads | C:\Users\admin\MediaGet2\Luminati-m\net_updater32.exe | lum_inst.tmp | ||||||||||||
User: admin Company: Luminati Networks Ltd. Integrity Level: HIGH Description: Luminati SDK Updater Exit code: 1 Version: 1.240.55 Modules
| |||||||||||||||
| 604 | "C:\Users\admin\AppData\Local\Temp\mediaget.exe" | C:\Users\admin\AppData\Local\Temp\mediaget.exe | Explorer.EXE | ||||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Version: 1.0 Modules
| |||||||||||||||
| 880 | "C:\Users\admin\MediaGet2\QtWebEngineProcess.exe" --type=renderer --disable-speech-api --enable-threaded-compositing --enable-features=AllowContentInitiatedDataUrlNavigations,TracingServiceInProcess --disable-features=BackgroundFetch,ConsolidatedMovementXY,DnsOverHttpsUpgrade,FormControlsRefresh,MojoVideoCapture,PictureInPicture,SmsReceiver,UseSkiaRenderer,WebPayments,WebUSB --disable-gpu-compositing --lang=en-US --webengine-schemes=qrc:sLV --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=5 --mojo-platform-channel-handle=3196 /prefetch:1 | C:\Users\admin\MediaGet2\QtWebEngineProcess.exe | — | mediaget.exe | |||||||||||
User: admin Company: The Qt Company Ltd. Integrity Level: LOW Description: C++ Application Development Framework Exit code: 0 Version: 5.15.2.0 Modules
| |||||||||||||||
| 1024 | "C:\Users\admin\MediaGet2\QtWebEngineProcess.exe" --type=renderer --disable-speech-api --enable-threaded-compositing --enable-features=AllowContentInitiatedDataUrlNavigations,TracingServiceInProcess --disable-features=BackgroundFetch,ConsolidatedMovementXY,DnsOverHttpsUpgrade,FormControlsRefresh,MojoVideoCapture,PictureInPicture,SmsReceiver,UseSkiaRenderer,WebPayments,WebUSB --disable-gpu-compositing --lang=en-US --webengine-schemes=qrc:sLV --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=3 --mojo-platform-channel-handle=2448 /prefetch:1 | C:\Users\admin\MediaGet2\QtWebEngineProcess.exe | — | mediaget.exe | |||||||||||
User: admin Company: The Qt Company Ltd. Integrity Level: LOW Description: C++ Application Development Framework Exit code: 0 Version: 5.15.2.0 Modules
| |||||||||||||||
| 1644 | C:\Users\admin\MediaGet2\Luminati-m\luminati-m-controller.exe is_switch_on | C:\Users\admin\MediaGet2\Luminati-m\luminati-m-controller.exe | mediaget.exe | ||||||||||||
User: admin Integrity Level: HIGH Exit code: 101 Modules
| |||||||||||||||
| 1892 | "C:\Windows\SYSTEM32\WISPTIS.EXE" /ManualLaunch; | C:\Windows\SYSTEM32\WISPTIS.EXE | — | net_updater32.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Microsoft Pen and Touch Input Component Exit code: 3221226540 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2068 | "C:\Windows\system32\SearchProtocolHost.exe" Global\UsGthrFltPipeMssGthrPipe5_ Global\UsGthrCtrlFltPipeMssGthrPipe5 1 -2147483646 "Software\Microsoft\Windows Search" "Mozilla/4.0 (compatible; MSIE 6.0; Windows NT; MS Search 4.0 Robot)" "C:\ProgramData\Microsoft\Search\Data\Temp\usgthrsvc" "DownLevelDaemon" | C:\Windows\system32\SearchProtocolHost.exe | — | SearchIndexer.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Microsoft Windows Search Protocol Host Exit code: 0 Version: 7.00.7601.24542 (win7sp1_ldr_escrow.191209-2211) Modules
| |||||||||||||||
| 2084 | C:\Users\admin\MediaGet2\Luminati-m\luminati\idle_report.exe 75119 | C:\Users\admin\MediaGet2\Luminati-m\luminati\idle_report.exe | — | net_updater32.exe | |||||||||||
User: admin Company: Luminati Networks Ltd. Integrity Level: MEDIUM Description: idle_report Exit code: 0 Version: 1.240.55 Modules
| |||||||||||||||
| 2356 | C:\Users\admin\MediaGet2\Luminati-m\test_wpf.exe | C:\Users\admin\MediaGet2\Luminati-m\test_wpf.exe | — | luminati-m-controller.exe | |||||||||||
User: admin Company: Luminati Networks Ltd. Integrity Level: HIGH Description: test_wpf Exit code: 0 Version: 1.240.55 Modules
| |||||||||||||||
| 2500 | C:\Users\admin\MediaGet2\Luminati-m\test_wpf.exe | C:\Users\admin\MediaGet2\Luminati-m\test_wpf.exe | — | net_updater32.exe | |||||||||||
User: SYSTEM Company: Luminati Networks Ltd. Integrity Level: SYSTEM Description: test_wpf Exit code: 0 Version: 1.240.55 Modules
| |||||||||||||||
Total events
43 985
Read events
43 124
Write events
793
Delete events
68
Modification events
| (PID) Process: | (604) mediaget.exe | Key: | HKEY_CURRENT_USER\Software\Media Get LLC\MediaGet2-systemScope\mediaget_info |
| Operation: | write | Name: | hasDownloadedUpdate |
Value: false | |||
| (PID) Process: | (604) mediaget.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (604) mediaget.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
| (PID) Process: | (604) mediaget.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 1 | |||
| (PID) Process: | (604) mediaget.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 0 | |||
| (PID) Process: | (604) mediaget.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Content |
| Operation: | write | Name: | CachePrefix |
Value: | |||
| (PID) Process: | (604) mediaget.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (604) mediaget.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
| (PID) Process: | (604) mediaget.exe | Key: | HKEY_CURRENT_USER\Software\MediaGet |
| Operation: | write | Name: | (default) |
Value: C:\Users\admin\MediaGet2\mediaget.exe | |||
| (PID) Process: | (604) mediaget.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Uninstall\MediaGet |
| Operation: | write | Name: | InstallLocation |
Value: C:\Users\admin\MediaGet2\ | |||
Executable files
499
Suspicious files
130
Text files
358
Unknown types
100
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 604 | mediaget.exe | C:\Users\admin\AppData\Local\Temp\mediaget-installer-tmp\archive.7z | compressed | |
MD5:— | SHA256:— | |||
| 604 | mediaget.exe | C:\Users\admin\AppData\Local\Temp\mediaget-installer-tmp\img2\cancel-page-new-en.png | image | |
MD5:— | SHA256:— | |||
| 604 | mediaget.exe | C:\Users\admin\AppData\Local\Temp\mediaget-installer-tmp\img2\cancel-page-new2-ru.png | image | |
MD5:— | SHA256:— | |||
| 604 | mediaget.exe | C:\Users\admin\AppData\Local\Temp\mediaget-installer-tmp\preloader.html | html | |
MD5:— | SHA256:— | |||
| 604 | mediaget.exe | C:\Users\admin\AppData\Local\Temp\mediaget-installer-tmp\img2\cancel-page-new-in.png | image | |
MD5:— | SHA256:— | |||
| 604 | mediaget.exe | C:\Users\admin\AppData\Local\Temp\mediaget-installer-tmp\img2\main-cont-shadow-hover-ru.png | image | |
MD5:— | SHA256:— | |||
| 604 | mediaget.exe | C:\Users\admin\AppData\Local\Temp\mediaget-installer-tmp\img2\install-lenta-2.png | image | |
MD5:— | SHA256:— | |||
| 604 | mediaget.exe | C:\Users\admin\AppData\Local\Temp\mediaget-installer-tmp\img2\install-lenta-308.png | image | |
MD5:— | SHA256:— | |||
| 604 | mediaget.exe | C:\Users\admin\AppData\Local\Temp\mediaget-installer-tmp\page-wait.png | image | |
MD5:260D2169A4421CBB34EACDA43319AB36 | SHA256:F8F5F8F933F389C156703E00DC00205B7991E87AB0D3CDD6F65FBDAB2697671B | |||
| 604 | mediaget.exe | C:\Users\admin\AppData\Local\Temp\mediaget-installer-tmp\curl-ca-bundle.crt | text | |
MD5:BE2B0736EA029FFF398559FA7DF4E646 | SHA256:C05A79296D61E3B2A2EBAF5AF476839B976D69A5ACB6F581A667E60E681049A2 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
25
TCP/UDP connections
110
DNS requests
66
Threats
11
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
— | — | GET | 200 | 3.94.72.89:80 | http://lumtest.com/myip.json | US | binary | 276 b | suspicious |
3612 | net_updater32.exe | GET | 200 | 104.18.32.68:80 | http://ocsp.sectigo.com/MFIwUDBOMEwwSjAJBgUrDgMCGgUABBQ5suEceKjAJbxseAmHFkQ9FrhTWQQUDuE6qFM6MdWKvsG7rWcaA4WtNA4CEQDvy%2BOQ74w4P7l1LJtfioaI | US | der | 510 b | whitelisted |
3668 | QtWebEngineProcess.exe | GET | 200 | 142.250.186.99:80 | http://ocsp.pki.goog/gts1c3/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTHLnmK3f9hNLO67UdCuLvGwCQHYwQUinR%2Fr4XN7pXNPZzQ4kYU83E1HScCEA5dqOk6ERH4CnbQPjlleuw%3D | US | der | 471 b | whitelisted |
328 | net_updater32.exe | GET | 200 | 93.184.221.240:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/authrootstl.cab?a9175c20762a2f91 | US | compressed | 59.5 Kb | whitelisted |
3668 | QtWebEngineProcess.exe | GET | 200 | 104.18.21.226:80 | http://ocsp.globalsign.com/rootr1/MFEwTzBNMEswSTAJBgUrDgMCGgUABBS3V7W2nAf4FiMTjpDJKg6%2BMgGqMQQUYHtmGkUNl8qJUC99BM00qP%2F8%2FUsCEHUeP1PjGFkz6V8I7O6tApc%3D | US | der | 1.41 Kb | whitelisted |
3612 | net_updater32.exe | GET | 200 | 104.18.32.68:80 | http://ocsp.comodoca.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBRTtU9uFqgVGHhJwXZyWCNXmVR5ngQUoBEKIz6W8Qfs4q8p74Klf9AwpLQCEDlyRDr5IrdR19NsEN0xNZU%3D | US | der | 471 b | whitelisted |
3668 | QtWebEngineProcess.exe | GET | 200 | 5.45.205.245:80 | http://yandex.ocsp-responder.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBStniMGfahyWUWDEeSLUFbNR9JLAgQUN1zjGeCyjqGoTtLPq9Dc4wtcNU0CEGlTKIPuh018TJJ9M3J8QXw%3D | RU | der | 1.48 Kb | whitelisted |
3612 | net_updater32.exe | GET | 200 | 104.18.32.68:80 | http://ocsp.usertrust.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTNMNJMNDqCqx8FcBWK16EHdimS6QQUU3m%2FWqorSs9UgOHYm8Cd8rIDZssCEB2iSDBvmyYY0ILgln0z02o%3D | US | der | 727 b | whitelisted |
3668 | QtWebEngineProcess.exe | GET | 200 | 142.250.186.99:80 | http://ocsp.pki.goog/gts1c3/MFIwUDBOMEwwSjAJBgUrDgMCGgUABBTHLnmK3f9hNLO67UdCuLvGwCQHYwQUinR%2Fr4XN7pXNPZzQ4kYU83E1HScCEQDhmOeGwgbrsxIlyFxpp0C8 | US | der | 472 b | whitelisted |
3668 | QtWebEngineProcess.exe | GET | 200 | 23.36.162.85:80 | http://subca.ocsp-certum.com/MFIwUDBOMEwwSjAJBgUrDgMCGgUABBTYOkzrrCGQj08njZXbUQQpkoUmuQQUCHbNywf%2FJPbFze27kLzihDdGdfcCEQDkBUeDDgxkUpdvejVJwN1I | NL | der | 1.54 Kb | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
604 | mediaget.exe | 51.15.98.239:443 | mediaget.com | Online S.a.s. | FR | suspicious |
— | — | 51.15.98.239:443 | mediaget.com | Online S.a.s. | FR | suspicious |
604 | mediaget.exe | 51.15.126.59:443 | mediaget.com | Online S.a.s. | FR | unknown |
328 | net_updater32.exe | 162.125.66.18:443 | www.dropbox.com | Dropbox, Inc. | DE | suspicious |
— | — | 162.125.66.15:443 | uc97c7ad57c0221882993ef25506.dl.dropboxusercontent.com | Dropbox, Inc. | DE | malicious |
604 | mediaget.exe | 51.15.85.51:443 | mediaget.com | Online S.a.s. | FR | unknown |
328 | net_updater32.exe | 167.172.28.221:443 | perr.l-err.biz | — | GB | suspicious |
328 | net_updater32.exe | 93.184.221.240:80 | ctldl.windowsupdate.com | MCI Communications Services, Inc. d/b/a Verizon Business | US | whitelisted |
3960 | net_updater32.exe | 159.223.133.120:443 | perr.l-err.biz | — | US | suspicious |
3960 | net_updater32.exe | 162.125.66.18:443 | www.dropbox.com | Dropbox, Inc. | DE | suspicious |
DNS requests
Domain | IP | Reputation |
|---|---|---|
mediaget.com |
| suspicious |
www.dropbox.com |
| shared |
uc97c7ad57c0221882993ef25506.dl.dropboxusercontent.com |
| malicious |
perr.l-err.biz |
| suspicious |
perr.lum-sdk.io |
| suspicious |
clientsdk.lum-sdk.io |
| suspicious |
ctldl.windowsupdate.com |
| whitelisted |
uc73dc140bd15a6355fa64e1ddda.dl.dropboxusercontent.com |
| malicious |
dht.libtorrent.org |
| suspicious |
router.bittorrent.com |
| shared |
Threats
PID | Process | Class | Message |
|---|---|---|---|
328 | net_updater32.exe | Potential Corporate Privacy Violation | ET POLICY Dropbox.com Offsite File Backup in Use |
328 | net_updater32.exe | Misc activity | ET INFO DropBox User Content Download Access over SSL M2 |
— | — | Potentially Bad Traffic | ET INFO Observed DNS Query to .biz TLD |
3612 | net_updater32.exe | Misc activity | ET INFO DropBox User Content Download Access over SSL M2 |
— | — | Potential Corporate Privacy Violation | ET P2P BitTorrent DHT ping request |
— | — | Potential Corporate Privacy Violation | ET P2P Vuze BT UDP Connection (5) |
— | — | Potentially Bad Traffic | ET DNS Query for .to TLD |
— | — | Potentially Bad Traffic | ET DNS Query to a .tk domain - Likely Hostile |
3 ETPRO signatures available at the full report
Process | Message |
|---|---|
mediaget.exe | AUTOSELECT OGL
|
mediaget.exe | > __thiscall Application::Application(int &,char *[])
|
mediaget.exe | os version: "6.1.7601v" __ os name: "Windows 7 Version 6.1 (Build 7601: SP 1)"
|
mediaget.exe | > int __thiscall Application::exec(void)
|
mediaget.exe | > __thiscall MediagetServerSettings::MediagetServerSettings(void)
|
mediaget.exe | INSTALL ID: "" _ OLD ID: ""
|
mediaget.exe | reseller - "" installId ""
|
mediaget.exe | > void __thiscall MediagetServerSettings::flushSettings(void)
|
mediaget.exe | main libvlc debug: VLC media player - 3.0.16 Vetinari
|
mediaget.exe | main libvlc debug: Copyright © 1996-2021 the VideoLAN team
|